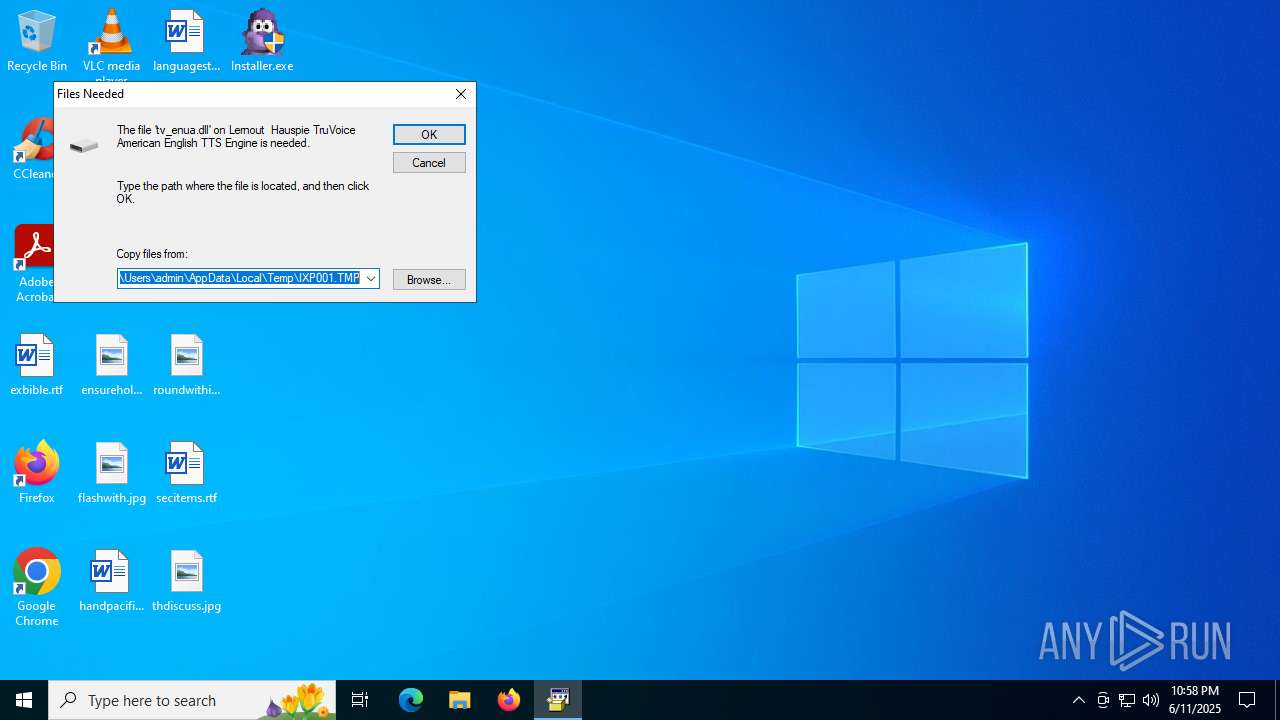
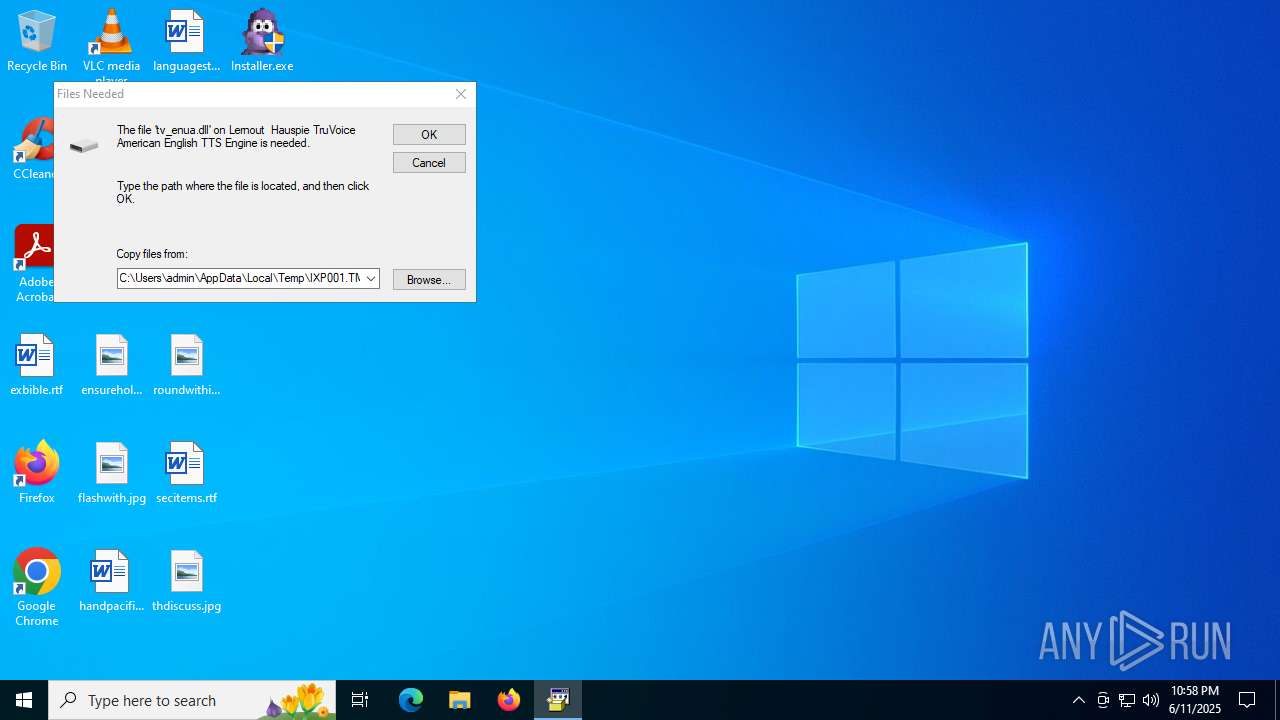
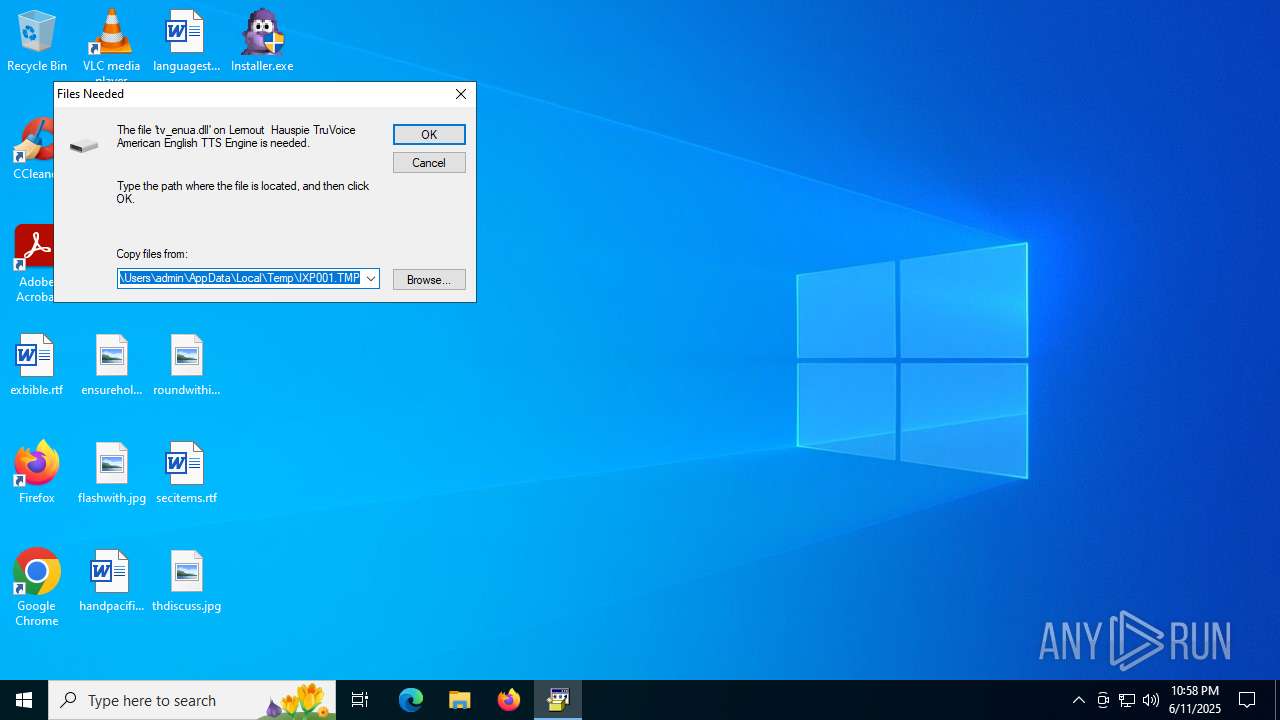
| File name: | Installer.exe |
| Full analysis: | https://app.any.run/tasks/099aaac3-bc13-413a-9c0d-70c2ee56452e |
| Verdict: | Malicious activity |
| Analysis date: | June 11, 2025, 22:57:56 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 67EF199E6C93989B373DE3EE2CE94E25 |
| SHA1: | 08076272182F7500DA86AC6F8AD8098A5599FE58 |
| SHA256: | AA824BFE2AB69C665808258D502D953DBBBA2E1301B12B947D9C3AE7BA60502A |
| SSDEEP: | 98304:IFAkKIOBkraB3XqgTiqvGRuOEkjM4YPqIF/QvdffxjScp/igCbL7YjqP3UVr4+dY:LI/Ew5Emw+9ulKTVHEr |
MALICIOUS
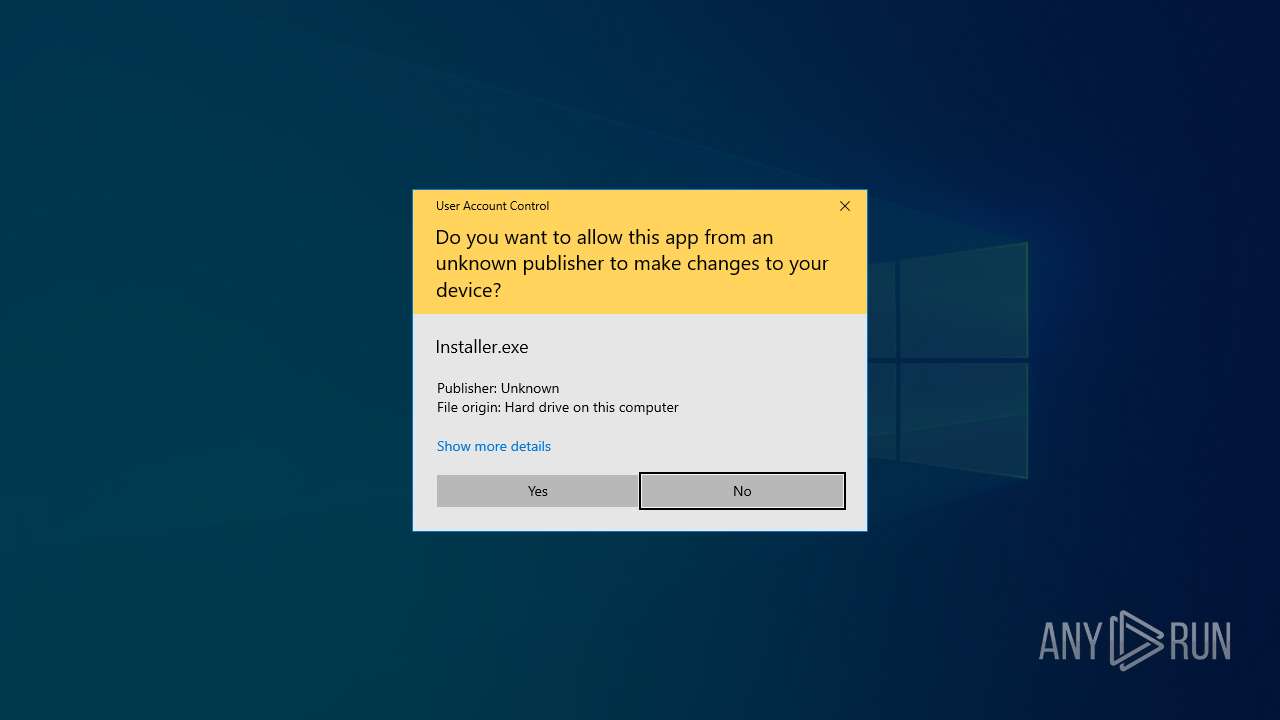
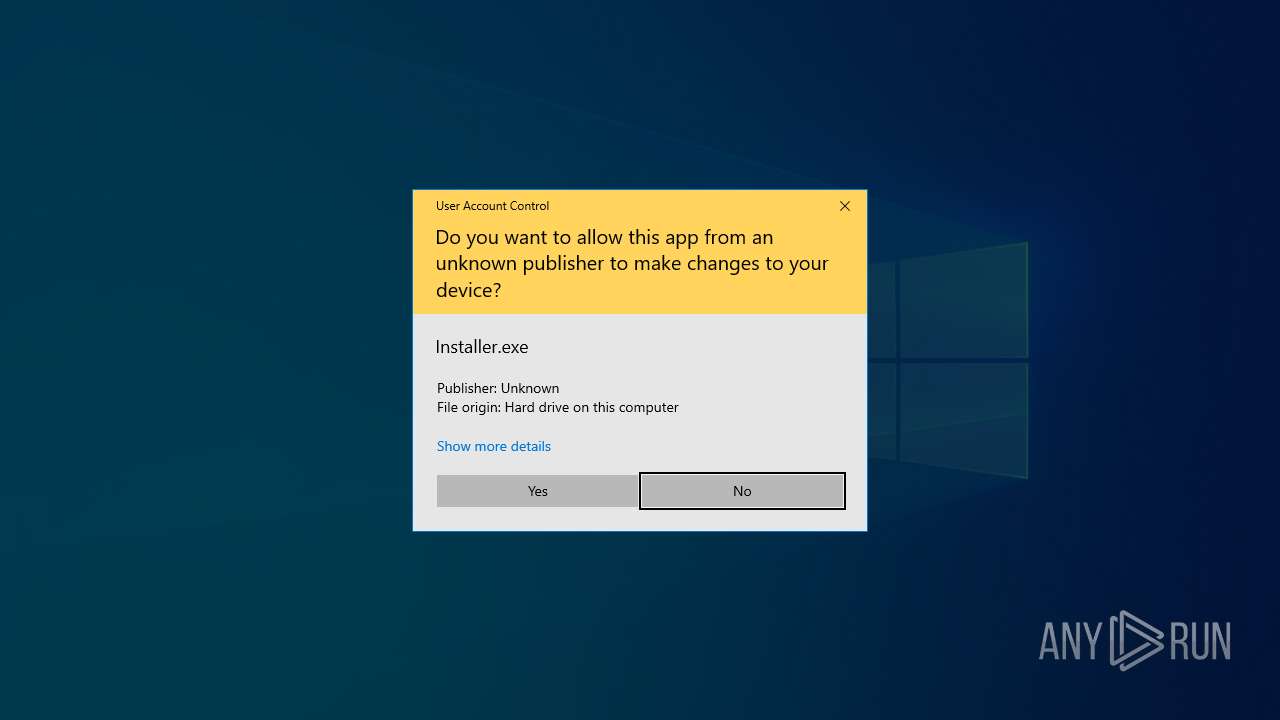
Executing a file with an untrusted certificate
- MSAGENT.EXE (PID: 6672)
- MSAGENT.EXE (PID: 5332)
- tv_enua.exe (PID: 7140)
- tv_enua.exe (PID: 5428)
Registers / Runs the DLL via REGSVR32.EXE
- MSAGENT.EXE (PID: 5332)
- tv_enua.exe (PID: 5428)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Installer.exe (PID: 6160)
Process drops legitimate windows executable
- Installer.exe (PID: 6160)
- MSAGENT.EXE (PID: 6672)
- tv_enua.exe (PID: 7140)
- Installer.exe (PID: 4528)
- MSAGENT.EXE (PID: 5332)
- tv_enua.exe (PID: 5428)
Executable content was dropped or overwritten
- Installer.exe (PID: 6160)
- Installer.exe (PID: 4528)
- tv_enua.exe (PID: 7140)
- MSAGENT.EXE (PID: 6672)
- MSAGENT.EXE (PID: 5332)
- tv_enua.exe (PID: 5428)
The process executes VB scripts
- Installer.exe (PID: 6160)
- Installer.exe (PID: 4528)
Executes application which crashes
- SearchApp.exe (PID: 2212)
Starts a Microsoft application from unusual location
- MSAGENT.EXE (PID: 6672)
- MSAGENT.EXE (PID: 5332)
- tv_enua.exe (PID: 7140)
- tv_enua.exe (PID: 5428)
INFO
Checks supported languages
- Installer.exe (PID: 6160)
Create files in a temporary directory
- Installer.exe (PID: 6160)
Manual execution by a user
- Installer.exe (PID: 1036)
- Installer.exe (PID: 4528)
The sample compiled with english language support
- Installer.exe (PID: 6160)
- tv_enua.exe (PID: 7140)
- Installer.exe (PID: 4528)
- MSAGENT.EXE (PID: 6672)
- MSAGENT.EXE (PID: 5332)
- tv_enua.exe (PID: 5428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:02:24 19:20:04+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 29696 |
| InitializedDataSize: | 489984 |
| UninitializedDataSize: | 16896 |
| EntryPoint: | 0x38af |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | - |
| FileVersion: | 1.0.0.0 |
| LegalCopyright: | PC |
| ProductVersion: | 1.0.0.0 |
Total processes
188
Monitored processes
29
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1036 | "C:\Users\admin\Desktop\Installer.exe" | C:\Users\admin\Desktop\Installer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1480 | grpconv.exe -o | C:\Windows\SysWOW64\grpconv.exe | — | MSAGENT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1560 | "C:\Users\admin\Desktop\Installer.exe" | C:\Users\admin\Desktop\Installer.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1688 | regsvr32 /s "C:\WINDOWS\msagent\AgentMPx.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | MSAGENT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | regsvr32 /s "C:\WINDOWS\msagent\mslwvtts.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | MSAGENT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | grpconv.exe -o | C:\Windows\SysWOW64\grpconv.exe | — | tv_enua.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Progman Group Converter Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2212 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Exit code: 3221226107 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | regsvr32 /s "C:\WINDOWS\msagent\AgentPsh.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | MSAGENT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2696 | C:\WINDOWS\system32\WerFault.exe -u -p 2212 -s 1716 | C:\Windows\System32\WerFault.exe | SearchApp.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3148 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 901
Read events
5 360
Write events
525
Delete events
16
Modification events
| (PID) Process: | (2212) SearchApp.exe | Key: | \REGISTRY\A\{7b1ef490-16a1-272f-c37a-8a443724aaa6}\2814751015243726\281535107058273\CortanaUI\44a65413067acd61cb60e74ea5537a73 |
| Operation: | write | Name: | SnapshotCaptured |
Value: 0 | |||
| (PID) Process: | (6160) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall |
| Operation: | write | Name: | DisplayName |
Value: | |||
| (PID) Process: | (6160) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall |
| Operation: | write | Name: | DisplayVersion |
Value: 1.0 | |||
| (PID) Process: | (6160) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall |
| Operation: | write | Name: | Publisher |
Value: PC | |||
| (PID) Process: | (6160) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall |
| Operation: | write | Name: | VersionMajor |
Value: 1 | |||
| (PID) Process: | (6160) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall |
| Operation: | write | Name: | VersionMinor |
Value: 0 | |||
| (PID) Process: | (6160) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall |
| Operation: | write | Name: | ProductID |
Value: {A8A2B9AE-0B2F-43B6-B700-19AF732344A9} | |||
| (PID) Process: | (6160) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (6160) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
| (PID) Process: | (6160) Installer.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall |
| Operation: | write | Name: | UninstallString |
Value: "C:\Users\admin\AppData\Local\uninst.exe" | |||
Executable files
120
Suspicious files
61
Text files
116
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\Temp\nsp8108.tmp\UAC.dll | executable | |
MD5:ADB29E6B186DAA765DC750128649B63D | SHA256:2F7F8FC05DC4FD0D5CDA501B47E4433357E887BBFED7292C028D99C73B52DC08 | |||
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\uninst.exe | executable | |
MD5:6207AEFC46AC857F836BF3669D91F7BD | SHA256:F01ECAAA5BFB32D500A79EA28A64C5A25EC81C03F7CBF4206706E7580508CE4E | |||
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\Temp\BonziCheckers.ocx | executable | |
MD5:66551C972574F86087032467AA6FEBB4 | SHA256:9028075603C66CA2E906ECAC3275E289D8857411A288C992E8EEF793ED71A75B | |||
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\Temp\BonziBDY.vbw | text | |
MD5:B4D876161A7ABB7BCAEA37003DAE158F | SHA256:4DD98F95113B70772308A4671A482B9B59BBA5FBF41E928F2A833366C54424E4 | |||
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\Temp\empop3.dll | executable | |
MD5:A0FDD2077934C34F08D48AA214DA2C4E | SHA256:F198EC842CF9B9D1E9E3F4BB6864FAE7EEA98D6919E0C6609E139E00C262D6BC | |||
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\Temp\AUTPRX32.DLL | executable | |
MD5:6E62806F4121EED119EF7D361F3322CA | SHA256:0563E77B6BD63EB0561F6264BADB5D07DACB7287CE029DC3CA3279A964EA6A6D | |||
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\Temp\j2.nbd | binary | |
MD5:788B0EC30CC5FAE75D2A6EE0A3EF10FA | SHA256:C032C71A49E0CB05072602C99251E6B1D76CA2DB57120FC402B93D3392DF7C3C | |||
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\Temp\emsmtp.dll | executable | |
MD5:365920B74D38322571E16F66686EF56B | SHA256:743857C8BE216893265C231AD45F4FFD3BABB67C024EF8CEB5A698E292464263 | |||
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\Temp\BonziCTB.dll | executable | |
MD5:6A4C7D730AED29B0405B03E128C1655A | SHA256:F85525A3EBE334F7403F031EC47C2B32461650224223EE728107DCE0E879EA93 | |||
| 6160 | Installer.exe | C:\Users\admin\AppData\Local\Temp\j001.nbd | binary | |
MD5:98C9159B828CBCD8F13A0491218BF537 | SHA256:E312728E0491E1A15405566C8F591CF3CA6128CA17E5E022A7550494A600AD27 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
46
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.169:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5080 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2696 | WerFault.exe | GET | 200 | 23.48.23.194:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2696 | WerFault.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
620 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
620 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6840 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 2.19.105.127:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2552 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.48.23.169:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5080 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |