| download: | /files/Autopoisk-1.0.0.12.zip |
| Full analysis: | https://app.any.run/tasks/8c8621a0-6654-41ff-b8fd-31eb040e55da |
| Verdict: | Malicious activity |
| Analysis date: | January 23, 2025, 12:34:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
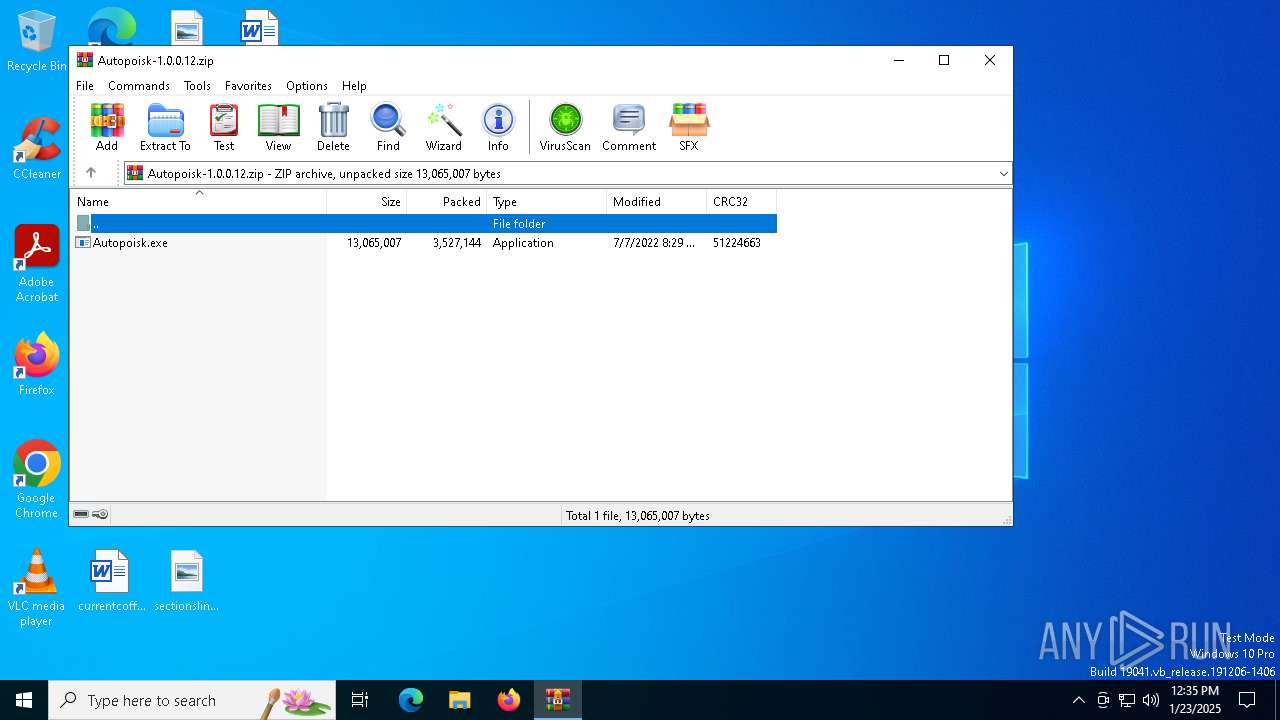
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F3043E5083C37651E743F4C533BA6201 |
| SHA1: | 1C4CAEF3DCE550C05684BFEA893912F0C475651E |
| SHA256: | AA74F38FC6C18E67FA83E6FBAC025F76B13D8FA174BC8F87F042FE462F4FFA13 |
| SSDEEP: | 98304:Zc80ookIZUZ0gBGcFg4XgQbrjy4ujLUGnk1WNG6eh05YYXYmgMvdLXkXfnm0c+wi:GLkj995 |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6296)
SUSPICIOUS
Connects to unusual port
- mstsc.exe (PID: 1480)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6296)
Reads the history of recent RDP connections
- mstsc.exe (PID: 4308)
- mstsc.exe (PID: 1480)
INFO
Creates files or folders in the user directory
- Autopoisk.exe (PID: 6712)
- mstsc.exe (PID: 1480)
Reads the computer name
- Autopoisk.exe (PID: 6712)
Checks supported languages
- Autopoisk.exe (PID: 6712)
The sample compiled with english language support
- WinRAR.exe (PID: 6296)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6296)
Reads security settings of Internet Explorer
- mstsc.exe (PID: 4308)
- mstsc.exe (PID: 1480)
Reads the software policy settings
- mstsc.exe (PID: 1480)
Checks proxy server information
- mstsc.exe (PID: 1480)
The process uses the downloaded file
- WinRAR.exe (PID: 6296)
Compiled with Borland Delphi (YARA)
- Autopoisk.exe (PID: 6712)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2022:07:07 11:29:44 |
| ZipCRC: | 0x51224663 |
| ZipCompressedSize: | 3527144 |
| ZipUncompressedSize: | 13065007 |
| ZipFileName: | Autopoisk.exe |
Total processes
127
Monitored processes
4
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
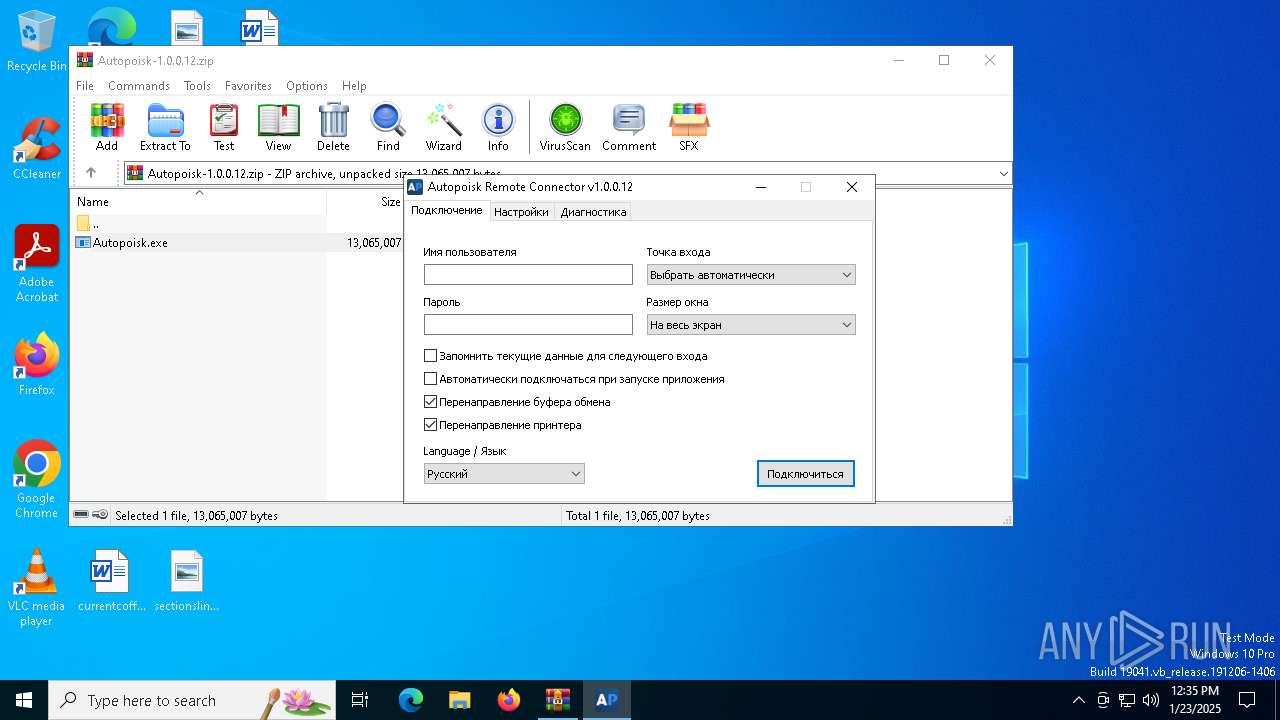
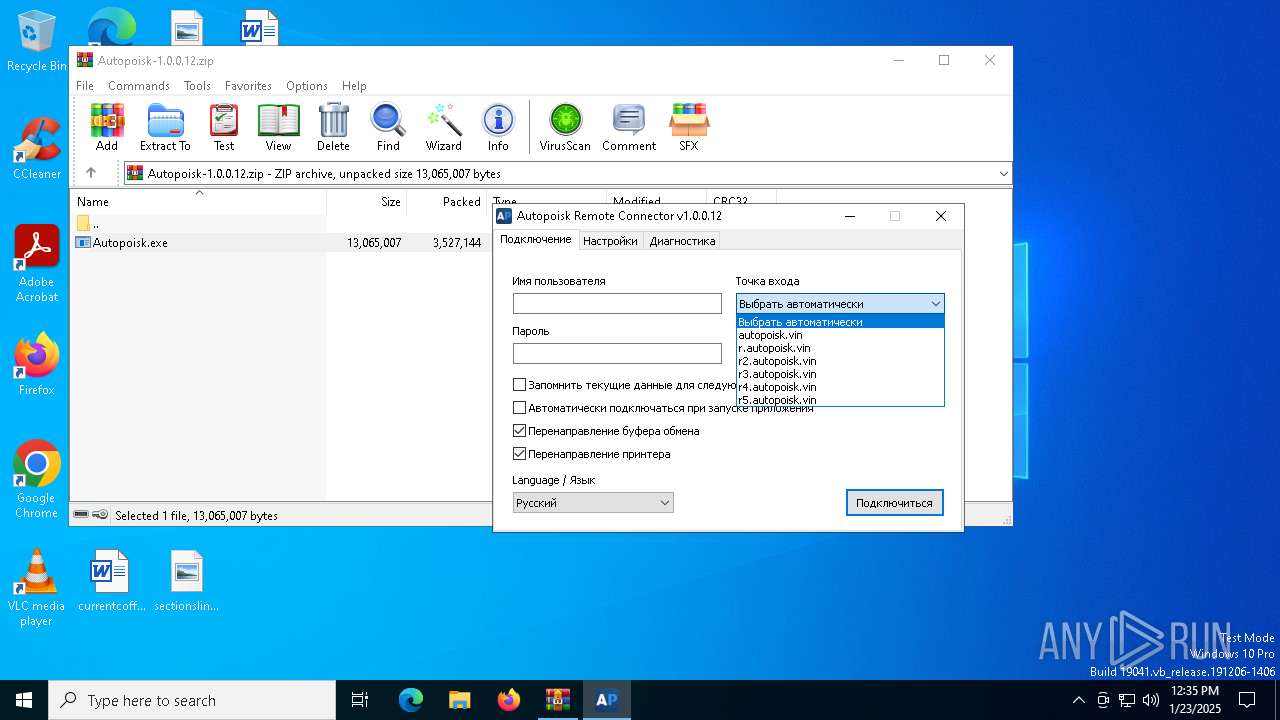
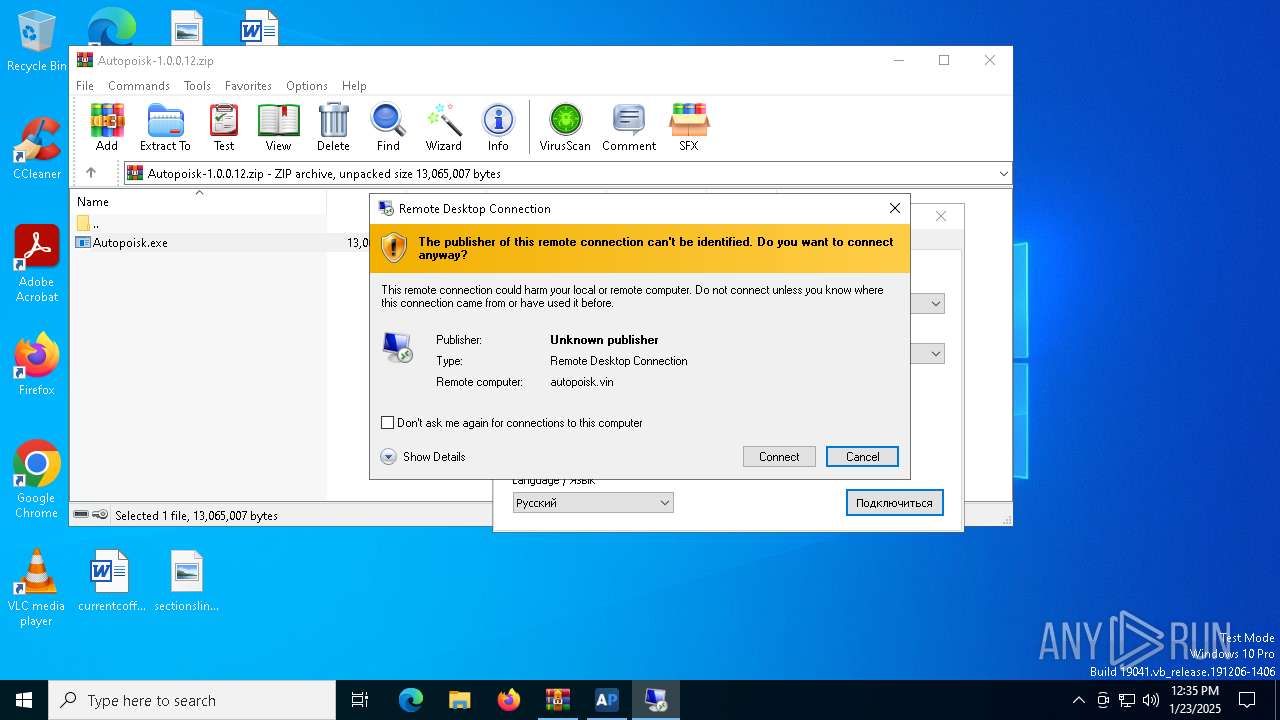
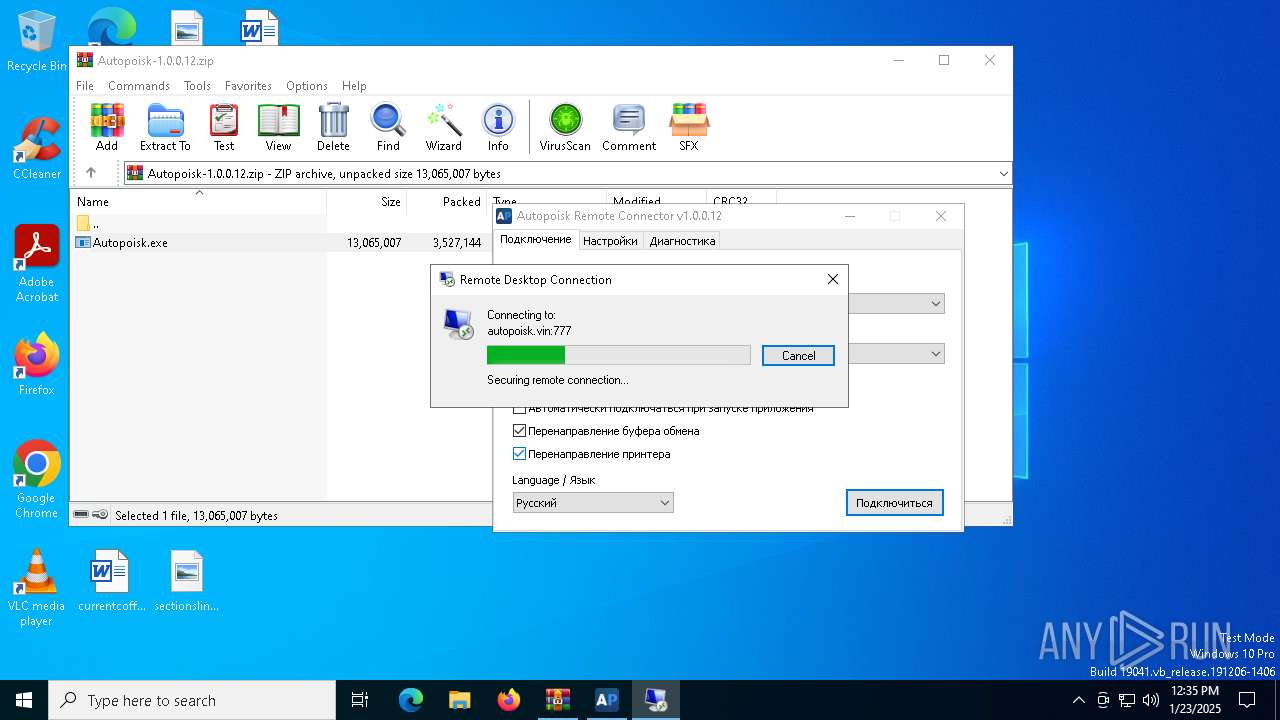
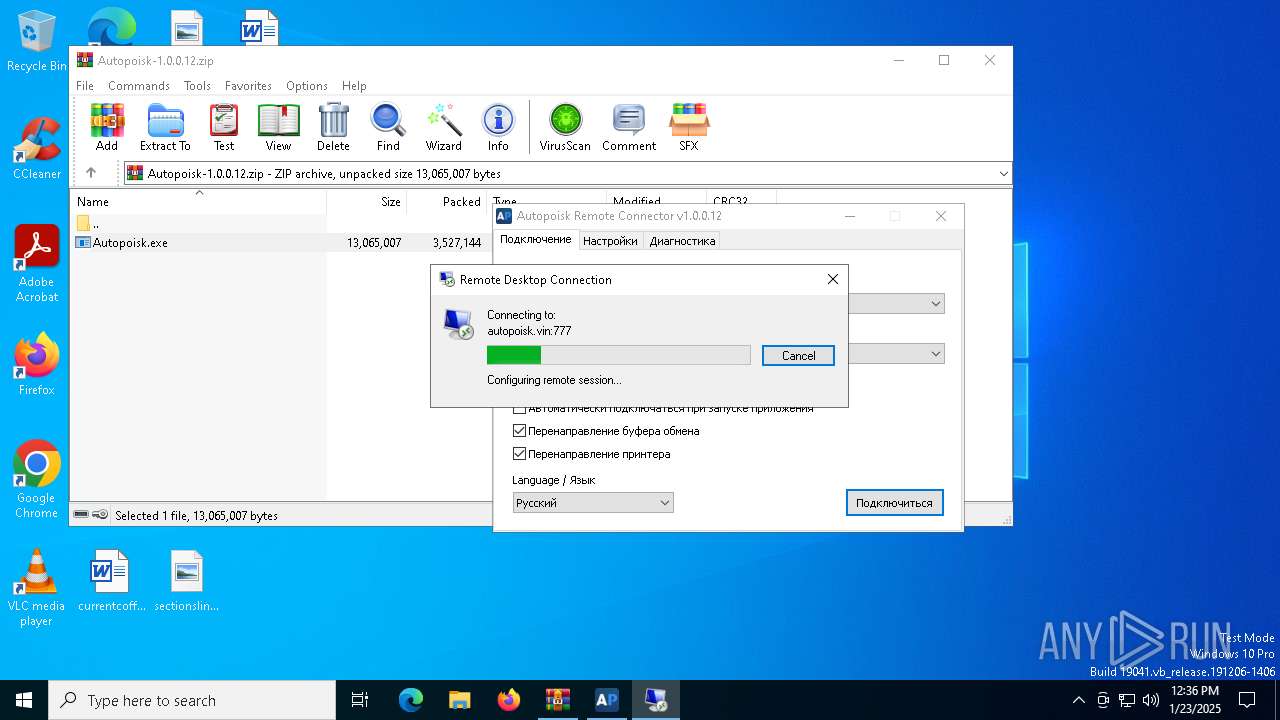
| 1480 | mstsc.exe "C:\Users\admin\AppData\Local\ARC\Autopoisk.rdp" /v:autopoisk.vin:777 | C:\Windows\System32\mstsc.exe | mstsc.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Connection Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4308 | mstsc.exe "C:\Users\admin\AppData\Local\ARC\Autopoisk.rdp" /v:autopoisk.vin:777 | C:\Windows\SysWOW64\mstsc.exe | — | Autopoisk.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Connection Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6296 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Autopoisk-1.0.0.12.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
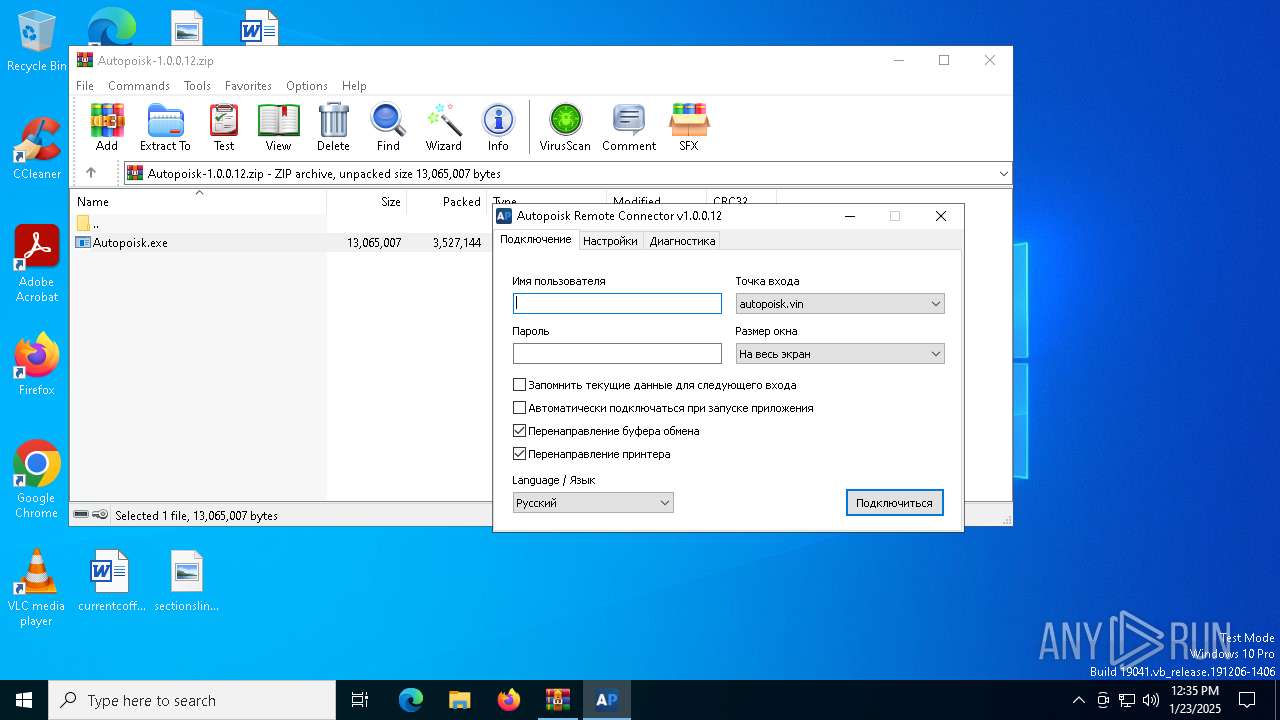
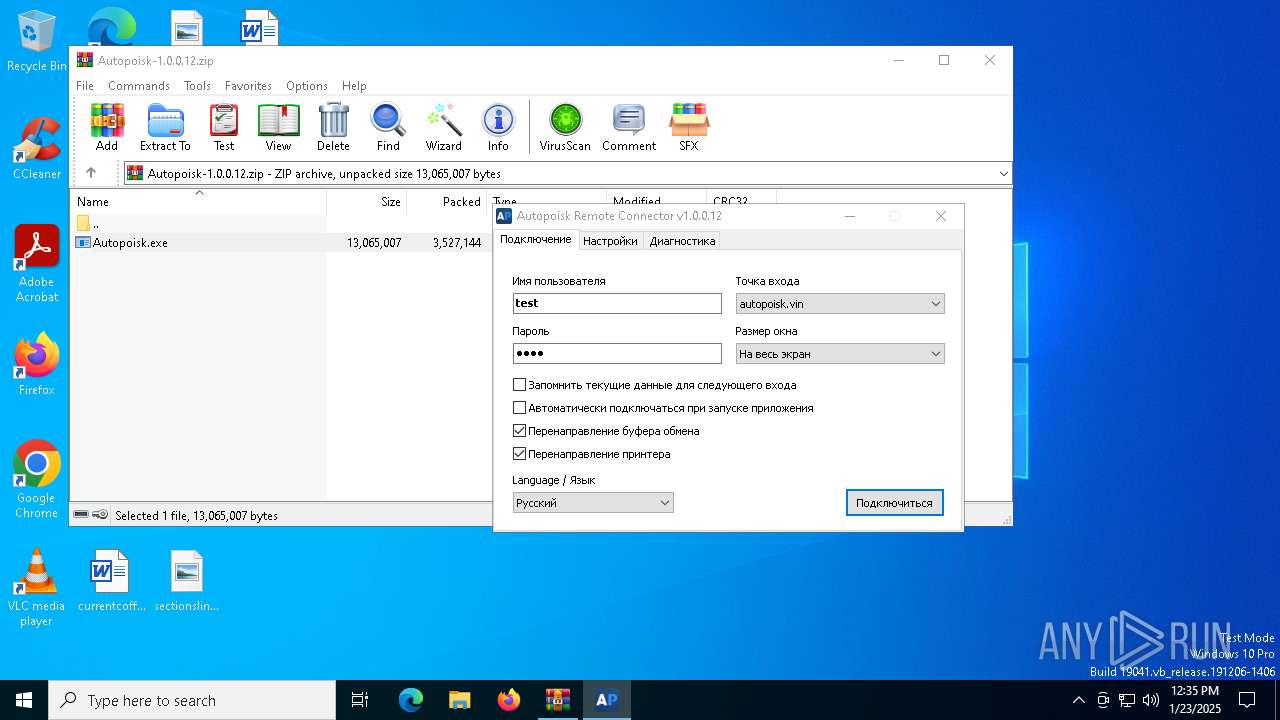
| 6712 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6296.3139\Autopoisk.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6296.3139\Autopoisk.exe | WinRAR.exe | ||||||||||||
User: admin Company: Autopoisk Integrity Level: MEDIUM Description: Autopoisk Remote Connector Version: 1.0.0.12 Modules
| |||||||||||||||
Total events
4 376
Read events
4 368
Write events
8
Delete events
0
Modification events
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Autopoisk-1.0.0.12.zip | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6296) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6296.3139\Autopoisk.exe | executable | |
MD5:E66D46D21CFD0EEBFBFD8A1D5C5B66A7 | SHA256:A9BDA3E785367821BE8AEA456B52A3A722486DDE3F5AB106E8B982A500850447 | |||
| 1480 | mstsc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\439F613B3D55693954E1B080DE3085B4_13A9E648A032C61467BDA0380F67EA43 | binary | |
MD5:753BC8B769D02B0DDA60D99BD80E260B | SHA256:C07F46A419CF1C1E2755465C2FB2EE11CBBEE10D40576BE0F4E848FFCCE597B2 | |||
| 6712 | Autopoisk.exe | C:\Users\admin\AppData\Local\ARC\Autopoisk.rdp | binary | |
MD5:F85158161CA75613B529BA256CDB53C9 | SHA256:EDE366CCD1E2DE09CEB9EBB381B587A5E7706802FA1553D9F1F883814737D410 | |||
| 1480 | mstsc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\94929790B3119AF4B3F5D66C747B122B_22A8AFCA6D1D25543ACF1AAD994E51F3 | binary | |
MD5:354B3DD3F8AD0A37D58EA8657FA5F1AC | SHA256:226845E6B2085E3A04A1AD5B49444F9970D86530E436970DEF7BB05ADEBA1F0E | |||
| 1480 | mstsc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\439F613B3D55693954E1B080DE3085B4_13A9E648A032C61467BDA0380F67EA43 | binary | |
MD5:4D3E5399AB8E1824E9082F2FC554FDBC | SHA256:5BF2BFC313EB97F7A3A9EF0C37726267E26FB90B89642BD025B3A1F6AFEFCCD0 | |||
| 1480 | mstsc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\94929790B3119AF4B3F5D66C747B122B_22A8AFCA6D1D25543ACF1AAD994E51F3 | binary | |
MD5:19A9FD13033154D543274312C434E49B | SHA256:1FD8AE7DC142728B56E5A2B440465B9E2D3D06F72C913E4277A696B0F76A5CFB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
38
DNS requests
23
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6712 | Autopoisk.exe | GET | 301 | 82.97.242.231:80 | http://upd.autopoisk.su/files/version | unknown | — | — | unknown |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6812 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr6/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRi%2B7TJbHYn9EmJ9W03lecB7P%2BG7QQUrmwFo5MT4qLn4tcc1sfwf8hnU6ACEH8fLJAug9Djtvs77keLXoA%3D | unknown | — | — | whitelisted |
6148 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6148 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1480 | mstsc.exe | GET | 200 | 104.18.21.226:80 | http://ocsp.globalsign.com/gsgccr6alphasslca2023/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBTYuQbxgZqJCf3D06HBxH57o5XEXgQUvQW384qTPHPLefoPhRKhd5YYkXQCDAjiLNTtTYgsXQ%2B4CA%3D%3D | unknown | — | — | whitelisted |
1480 | mstsc.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr6/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRi%2B7TJbHYn9EmJ9W03lecB7P%2BG7QQUrmwFo5MT4qLn4tcc1sfwf8hnU6ACEH8fLJAug9Djtvs77keLXoA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 104.126.37.136:443 | — | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2092 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 104.126.37.153:443 | — | Akamai International B.V. | DE | unknown |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
r3.autopoisk.vin |
| unknown |
r2.autopoisk.vin |
| unknown |
r4.autopoisk.vin |
| unknown |
autopoisk.vin |
| unknown |
r5.autopoisk.vin |
| unknown |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6712 | Autopoisk.exe | Potentially Bad Traffic | ET INFO HTTP Request to .su TLD (Soviet Union) Often Malware Related |