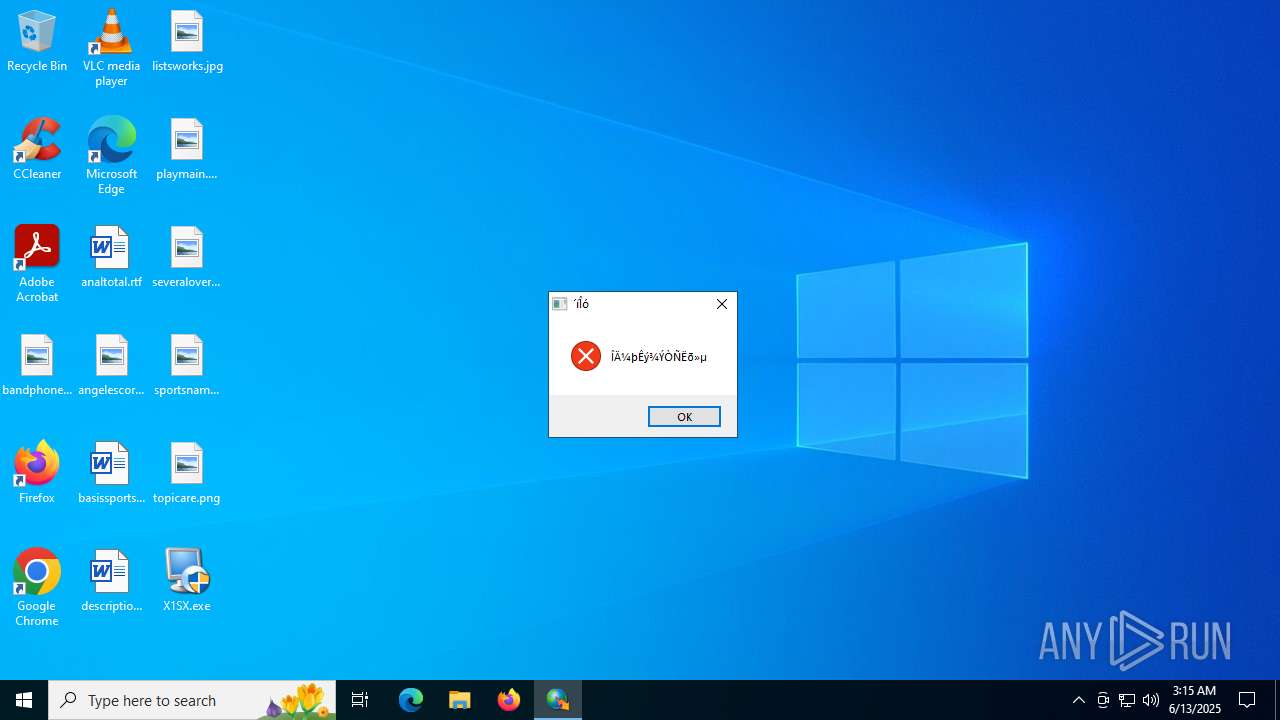
| File name: | X1SX.exe |
| Full analysis: | https://app.any.run/tasks/d1ae9e96-48aa-4551-832b-5bb58397d4df |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 03:15:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | C286118DDD5ABE7A7325D34E22FF722B |
| SHA1: | B59E99D0F7432A00591D3E060A773441867FE0F8 |
| SHA256: | AA749D399EA42A429468BC0CBE9DECCB0CAE199CF62DFABD46D0EFEDD0C8B341 |
| SSDEEP: | 98304:EhKB2bwMCVrwRMlgo606iLTVDTjia9Faw3mzUNzlHPs5gwHFf7JONkCLmYDEC05g:UfTk |
MALICIOUS
Executing a file with an untrusted certificate
- un.exe (PID: 6672)
- un.exe (PID: 1096)
- un.exe (PID: 3576)
SUSPICIOUS
Reads security settings of Internet Explorer
- X1SX.exe (PID: 2680)
- irsetup.exe (PID: 6224)
Executable content was dropped or overwritten
- X1SX.exe (PID: 2680)
- irsetup.exe (PID: 6224)
- un.exe (PID: 3576)
- iusb3mon.exe (PID: 7100)
Creates file in the systems drive root
- irsetup.exe (PID: 6224)
- un.exe (PID: 6672)
- conhost.exe (PID: 1752)
- un.exe (PID: 1096)
- conhost.exe (PID: 3048)
- conhost.exe (PID: 3668)
- un.exe (PID: 3576)
- iusb3mon.exe (PID: 7100)
- cmd.exe (PID: 856)
Starts itself from another location
- iusb3mon.exe (PID: 7100)
Starts CMD.EXE for commands execution
- iusb3mon.exe (PID: 7100)
Creates or modifies Windows services
- iusb3mon.exe (PID: 7100)
Connects to unusual port
- iusb3mon.exe (PID: 7100)
There is functionality for taking screenshot (YARA)
- iusb3mon.exe (PID: 7100)
INFO
The sample compiled with english language support
- X1SX.exe (PID: 2680)
- un.exe (PID: 3576)
- iusb3mon.exe (PID: 7100)
Reads the computer name
- X1SX.exe (PID: 2680)
- irsetup.exe (PID: 6224)
- iusb3mon.exe (PID: 7100)
- microsoft.exe (PID: 1720)
Process checks computer location settings
- X1SX.exe (PID: 2680)
- irsetup.exe (PID: 6224)
Checks supported languages
- irsetup.exe (PID: 6224)
- un.exe (PID: 6672)
- X1SX.exe (PID: 2680)
- un.exe (PID: 1096)
- iusb3mon.exe (PID: 7100)
- un.exe (PID: 3576)
- microsoft.exe (PID: 1720)
Create files in a temporary directory
- X1SX.exe (PID: 2680)
- irsetup.exe (PID: 6224)
- iusb3mon.exe (PID: 7100)
- microsoft.exe (PID: 1720)
Creates files in the program directory
- irsetup.exe (PID: 6224)
- un.exe (PID: 6672)
- un.exe (PID: 1096)
- iusb3mon.exe (PID: 7100)
The sample compiled with chinese language support
- irsetup.exe (PID: 6224)
- iusb3mon.exe (PID: 7100)
Reads the machine GUID from the registry
- iusb3mon.exe (PID: 7100)
- microsoft.exe (PID: 1720)
UPX packer has been detected
- iusb3mon.exe (PID: 7100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:06:14 16:16:10+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 22528 |
| InitializedDataSize: | 48128 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x29e1 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.1.0.0 |
| ProductVersionNumber: | 9.1.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | Created with Setup Factory |
| FileDescription: | Setup Application |
| FileVersion: | 9.1.0.0 |
| InternalName: | suf_launch |
| LegalCopyright: | Setup Engine Copyright © 2004-2012 Indigo Rose Corporation |
| LegalTrademarks: | Setup Factory is a trademark of Indigo Rose Corporation. |
| OriginalFileName: | suf_launch.exe |
| ProductName: | Setup Factory Runtime |
| ProductVersion: | 9.1.0.0 |
Total processes
150
Monitored processes
13
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | cmd /c echo.>c:\inst.ini | C:\Windows\SysWOW64\cmd.exe | — | iusb3mon.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "C:\un.exe" x -o+ -ppoiuytrewq C:\ProgramData\Data\upx.rar ziliao.jpg C:\ProgramData\Microsoft\Program\ | C:\un.exe | — | irsetup.exe | |||||||||||
User: admin Company: WinRAR 压缩管理软件中文版 Integrity Level: HIGH Description: 命令行 RAR Exit code: 0 Version: 5.20.0 Modules
| |||||||||||||||
| 1296 | "C:\Users\admin\Desktop\X1SX.exe" | C:\Users\admin\Desktop\X1SX.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup Application Exit code: 3221226540 Version: 9.1.0.0 Modules
| |||||||||||||||
| 1720 | C:\ProgramData\Microsoft\microsoft.exe | C:\ProgramData\Microsoft\microsoft.exe | — | iusb3mon.exe | |||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: HIGH Description: TrueUpdate Client Version: 3.8.0.0 Modules
| |||||||||||||||
| 1752 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | un.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2632 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2680 | "C:\Users\admin\Desktop\X1SX.exe" | C:\Users\admin\Desktop\X1SX.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup Application Exit code: 0 Version: 9.1.0.0 Modules
| |||||||||||||||
| 3048 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | un.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3576 | "C:\un.exe" x -o+ -ppoiuytrewq C:\ProgramData\Data\upx.rar iusb3mon.exe iusb3mon.dat C:\Microsoft\ | C:\un.exe | irsetup.exe | ||||||||||||
User: admin Company: WinRAR 压缩管理软件中文版 Integrity Level: HIGH Description: 命令行 RAR Exit code: 0 Version: 5.20.0 Modules
| |||||||||||||||
| 3668 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | un.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
1 557
Read events
1 554
Write events
3
Delete events
0
Modification events
| (PID) Process: | (7100) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Cdefgh |
| Operation: | write | Name: | Groupfenzhu |
Value: | |||
| (PID) Process: | (7100) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Cdefgh |
| Operation: | write | Name: | Remarkbeizhu |
Value: | |||
| (PID) Process: | (7100) iusb3mon.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\Cdefgh |
| Operation: | write | Name: | MarkTime |
Value: 2025-06-13 03:15 | |||
Executable files
6
Suspicious files
11
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1096 | un.exe | C:\ProgramData\Microsoft\Program\ziliao.jpg | binary | |
MD5:15B1BD7573C9E94C1C11EE9FE51F586D | SHA256:7381A34956C33FCEE8AED43C9958285E285468329D1DE1387B7D59B7B5898C7D | |||
| 6224 | irsetup.exe | C:\ProgramData\data\rar.ini | text | |
MD5:51C11DB1054DD4650A33BF481EC27060 | SHA256:FC835086345B170AC995C35F24546E1B7268E3D3524A125A9396A4EC8B7D3F35 | |||
| 2680 | X1SX.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | executable | |
MD5:5FDD43E3AB3CE33ECD67B7FCEF9C6B00 | SHA256:98AE390BBE7652CADF1AA618DD269D271AF4CE1170A038A198B5B374F94FC84A | |||
| 6224 | irsetup.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\IRIMG1.JPG | image | |
MD5:3220A6AEFB4FC719CC8849F060859169 | SHA256:988CF422CBF400D41C48FBE491B425A827A1B70691F483679C1DF02FB9352765 | |||
| 3576 | un.exe | C:\Microsoft\iusb3mon.dat | compressed | |
MD5:7DB8E66EF74C2BA301C9DE02A08AAB79 | SHA256:9897994028E66EBA4C5691FE6AB4D9DF527580C8A48F42066E51A82BB6AE2EE9 | |||
| 7100 | iusb3mon.exe | C:\Users\admin\AppData\Local\Temp\_ir_tu2_temp_0\_TUProjDT.dat | text | |
MD5:67BF1F80834081FC794C6ED1F7C2FED5 | SHA256:54FD2361602E82DB016D6EA62FBADC3984B566399DFAAC7E0A1181E4C70B90C2 | |||
| 7100 | iusb3mon.exe | C:\Users\admin\AppData\Local\Temp\_ir_tu2_temp_0\IRIMG3.JPG | binary | |
MD5:9CA19B0ABBD0BBF8C01D835AABE36C0E | SHA256:568BA3C29FFB6BC581602235D46210989831B00689F369B965ABBA061A042C02 | |||
| 7100 | iusb3mon.exe | C:\ProgramData\Microsoft\microsoft.dat | compressed | |
MD5:7DB8E66EF74C2BA301C9DE02A08AAB79 | SHA256:9897994028E66EBA4C5691FE6AB4D9DF527580C8A48F42066E51A82BB6AE2EE9 | |||
| 2680 | X1SX.exe | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\lua5.1.dll | executable | |
MD5:B5FC476C1BF08D5161346CC7DD4CB0BA | SHA256:12CB9B8F59C00EF40EA8F28BFC59A29F12DC28332BF44B1A5D8D6A8823365650 | |||
| 6224 | irsetup.exe | C:\ProgramData\data\UPX.rar | compressed | |
MD5:3683CAC253CDB42CBFAF80015818AC67 | SHA256:08C98E30EC1FDAB33F177739D3C98FFA9FC8FAB98D27DCEA9639415087A1DF0F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
24
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2764 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5712 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5712 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4380 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7100 | iusb3mon.exe | 118.107.42.181:36061 | — | BGPNET Global ASN | SG | unknown |
2764 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2764 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|
iusb3mon.exe | Thread running...
|