| File name: | $RBQBPOU.bat |
| Full analysis: | https://app.any.run/tasks/983d672d-1e61-4c60-aca3-7bcc411f684b |
| Verdict: | Malicious activity |
| Analysis date: | January 21, 2024, 18:08:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | A490C94DCE1E2FBFA50DBE459CC6F4B7 |
| SHA1: | 192D83A6AD0C432523E071453F0DD14EA113E861 |
| SHA256: | AA6D26A7A6404C6FDA8166117201021A3A52DD656E183C0058FEB895292173EF |
| SSDEEP: | 6144:qxSr9NbUCOte2Gx5eesnb1KzBONfYrGPfFy2ChiqSHMzqL/rFcpvn980oL0:lR+f+7YnEVyeyy/Ub5cfAL0 |
MALICIOUS
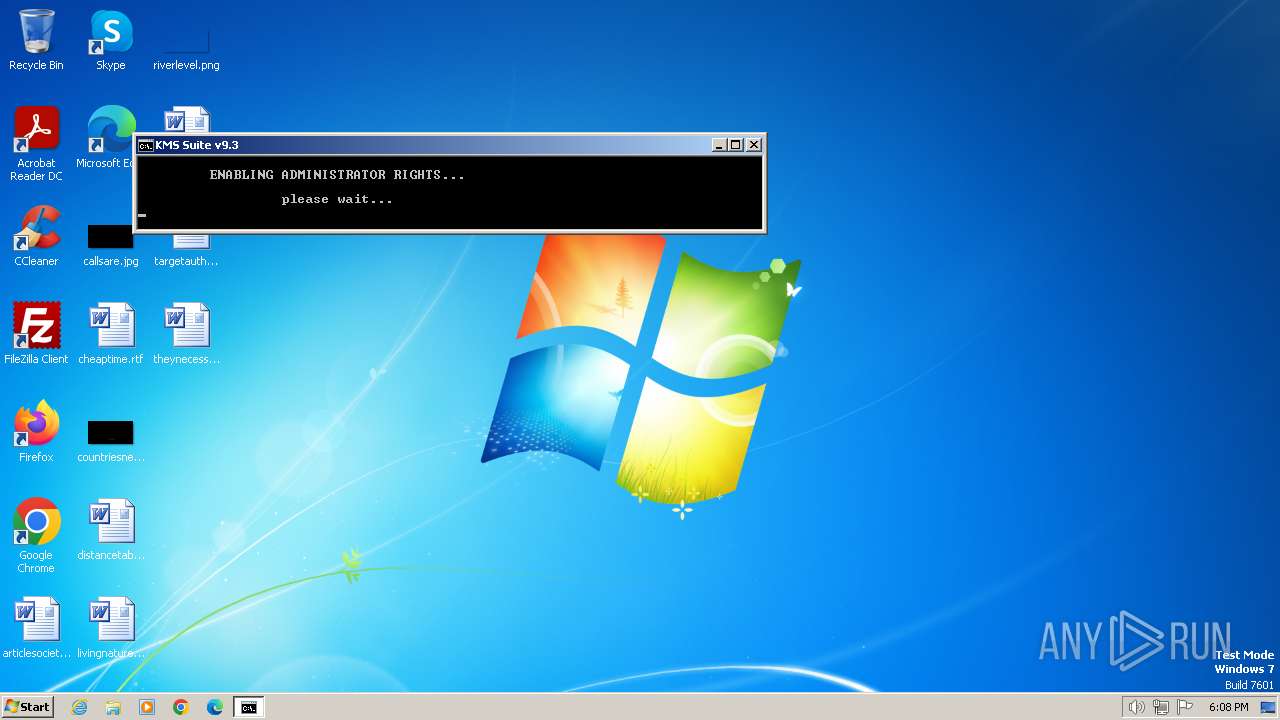
Starts Visual C# compiler
- powershell.exe (PID: 2088)
Drops the executable file immediately after the start
- csc.exe (PID: 548)
SUSPICIOUS
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 2040)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 2040)
- cmd.exe (PID: 1588)
- cmd.exe (PID: 1636)
- cmd.exe (PID: 664)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 2040)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 2040)
- cmd.exe (PID: 1588)
- cmd.exe (PID: 1636)
- cmd.exe (PID: 664)
Uses .NET C# to load dll
- powershell.exe (PID: 2088)
Executable content was dropped or overwritten
- csc.exe (PID: 548)
- expand.exe (PID: 480)
- xcopy.exe (PID: 1632)
Process drops legitimate windows executable
- expand.exe (PID: 480)
- xcopy.exe (PID: 1632)
Application launched itself
- cmd.exe (PID: 2040)
- cmd.exe (PID: 1636)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2040)
- cmd.exe (PID: 1636)
- powershell.exe (PID: 1836)
Executing commands from a ".bat" file
- cmd.exe (PID: 2040)
- powershell.exe (PID: 1836)
Powershell scripting: start process
- cmd.exe (PID: 1588)
Reads the Internet Settings
- powershell.exe (PID: 1836)
- wscript.exe (PID: 2592)
- cmd.exe (PID: 1636)
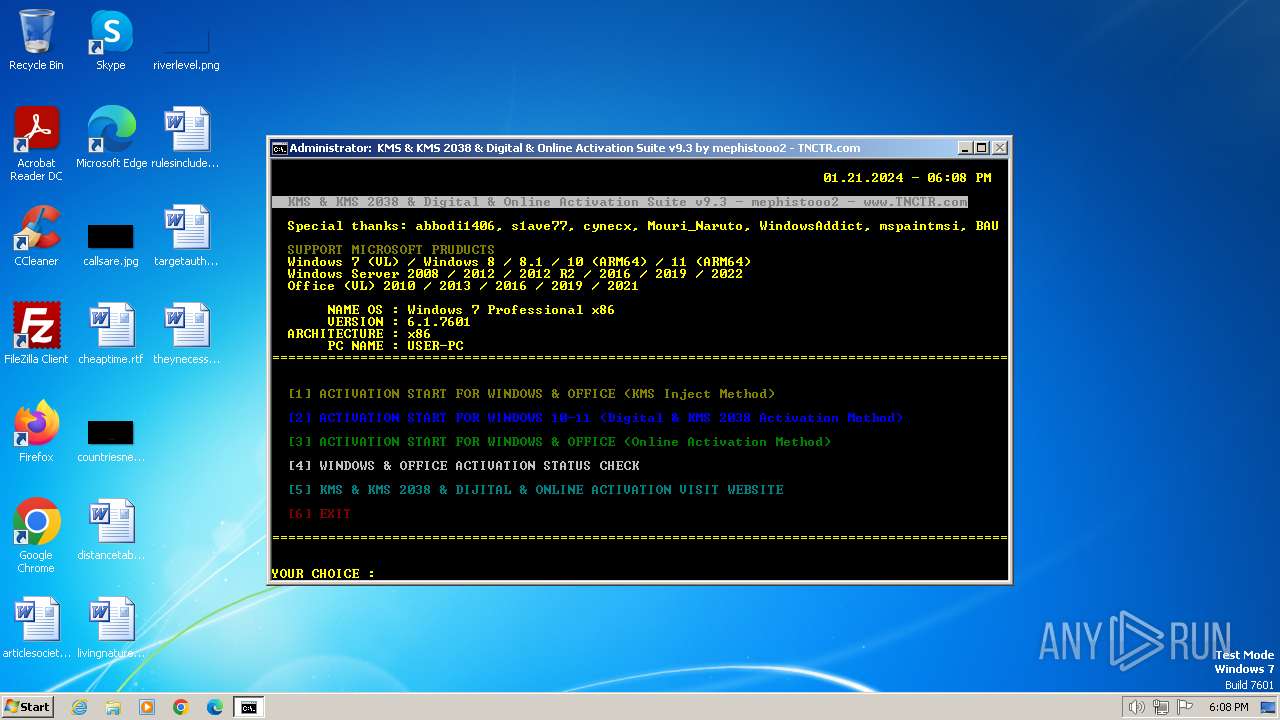
The executable file from the user directory is run by the CMD process
- center.exe (PID: 1924)
The process executes VB scripts
- cmd.exe (PID: 1636)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 2592)
Runs shell command (SCRIPT)
- wscript.exe (PID: 2592)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1636)
INFO
Checks supported languages
- mode.com (PID: 324)
- csc.exe (PID: 548)
- cvtres.exe (PID: 532)
- mode.com (PID: 2668)
- mode.com (PID: 2056)
- center.exe (PID: 1924)
- DisableX.exe (PID: 2464)
- mode.com (PID: 2688)
- mode.com (PID: 2536)
Reads the machine GUID from the registry
- csc.exe (PID: 548)
- cvtres.exe (PID: 532)
Create files in a temporary directory
- csc.exe (PID: 548)
- cvtres.exe (PID: 532)
- expand.exe (PID: 480)
- xcopy.exe (PID: 1632)
Drops the executable file immediately after the start
- expand.exe (PID: 480)
- xcopy.exe (PID: 1632)
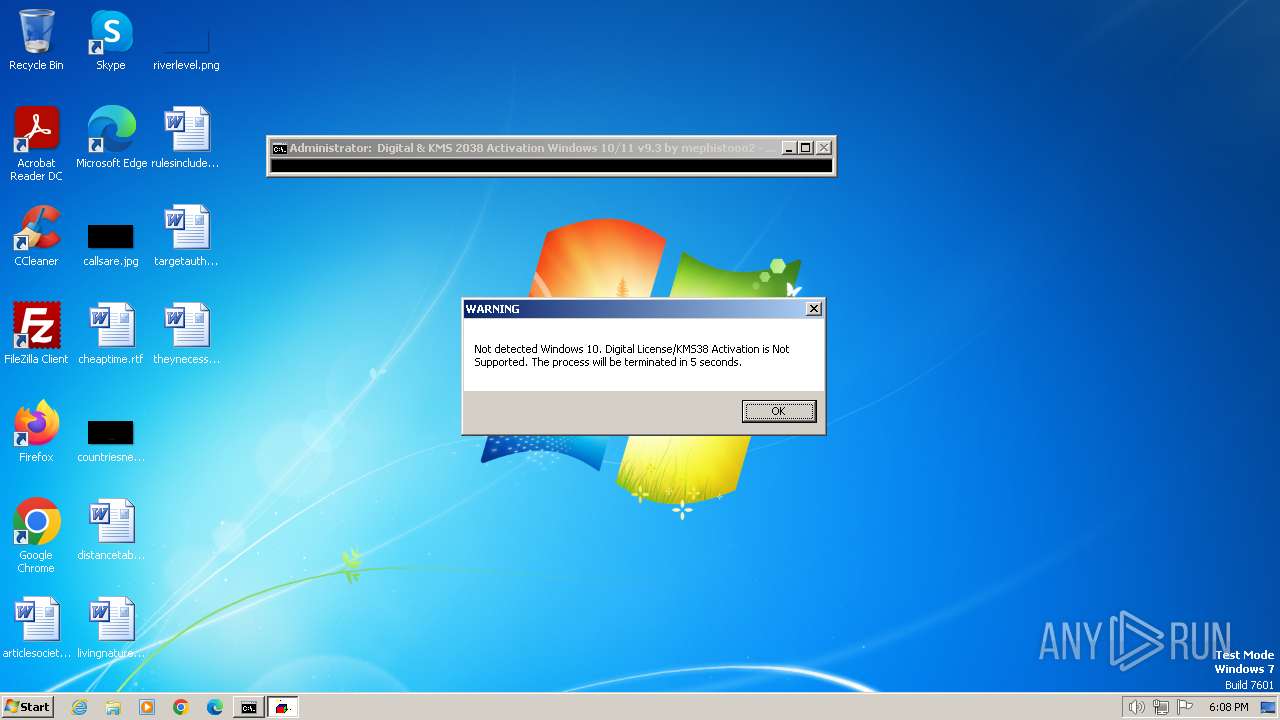
Checks operating system version
- cmd.exe (PID: 1636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
77
Monitored processes
39
Malicious processes
4
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 324 | mode con cols=78 lines=6 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 480 | "C:\Windows\system32\expand.exe" -R 1 -F:* . | C:\Windows\System32\expand.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: LZ Expansion Utility Exit code: 0 Version: 6.1.7601.24535 (win7sp1_ldr_escrow.191105-1059) Modules
| |||||||||||||||
| 532 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESF889.tmp" "c:\Users\admin\AppData\Local\Temp\CSC315E6F0E38D84CDDBFF72310F25499D4.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
| 548 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\c440ejs0.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 572 | REG QUERY HKU\S-1-5-19\Environment | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | C:\Windows\system32\cmd.exe /c powershell -nop -c "(([WMISEARCHER]'Select Version from Win32_OperatingSystem').Get()).Version" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 908 | C:\Windows\system32\cmd.exe /c ver | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1000 | findstr /v /a:4 /R "^f7f81a39-5f63-5b42-9efd-1f13b5431005quot; " [6] EXIT" nul | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1196 | REG QUERY HKU\S-1-5-19\Environment | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1356 | C:\Windows\system32\net1 session | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
5 259
Read events
5 227
Write events
32
Delete events
0
Modification events
| (PID) Process: | (1836) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1836) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1836) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1836) powershell.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1636) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (1636) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (1636) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (1636) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2592) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2592) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
28
Suspicious files
12
Text files
46
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\c440ejs0.cmdline | text | |
MD5:FB11D5E87227D03BFCEE7A09BFAADA19 | SHA256:A5ABE8EFE0437E891193C53C8B0734DE809AF3662269966860DDC70F80EF2F32 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\3gqhjizl.fym.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\c440ejs0.0.cs | text | |
MD5:2619C2087E535BD9EF20A732A58BFA84 | SHA256:85835D9BE283D806347DB25628B7E5108A11F46F9EF540656DF28F09F66CA0FB | |||
| 548 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSC315E6F0E38D84CDDBFF72310F25499D4.TMP | binary | |
MD5:03C5F2D99A3C6BC027FF772E80BAA5AA | SHA256:D7C42EBC0D8F51BB2EA13B5041A31D759BC26532A693FA63F31D462E0D7DB60B | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\svqdxepn.ls2.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 480 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\KMS_Suite.bat | text | |
MD5:F825DCC537D39BEFD3A38D3558AF19EC | SHA256:2A6A60CC19BDE03D9EF004B0413CE9C73B1ABB71BB21A7A14EBAA41636CB561B | |||
| 548 | csc.exe | C:\Users\admin\AppData\Local\Temp\c440ejs0.out | text | |
MD5:908A385B3B711A14F1F6A67126A836E4 | SHA256:283AFE4BE153E206164F988D3713BC826A81B908128C64A0F49BD8FA39B287F4 | |||
| 532 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RESF889.tmp | binary | |
MD5:59733BD365A50E36A2FFEC4143558510 | SHA256:0194CAD23F9FB6DA89DD8BA4069F5D73C096F5BEA4D816C4B42FAD59AE202866 | |||
| 2088 | powershell.exe | C:\Users\admin\AppData\Local\Temp\1 | compressed | |
MD5:436D8D09DC86C53BE0486371400BD951 | SHA256:586AA43770695B63537A434AD7835FD5B10C8D513EB1743255CF5B68CB5586B2 | |||
| 480 | expand.exe | C:\Users\admin\AppData\Local\Temp\KMS_Suite\bin\Digital\OEM_Digital\$OEM$\$\Setup\Scripts\digi.bat | text | |
MD5:CD8967FB093C71A77B9A897A63849350 | SHA256:6079F56DAEA065542154B86CD33C17BCE62B6D961FB432BF5C334F8864067CD0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |