| File name: | Avast.exe |
| Full analysis: | https://app.any.run/tasks/efba1e29-5d3c-4a12-9adb-3150fccf8f2a |
| Verdict: | Malicious activity |
| Analysis date: | September 14, 2024, 10:03:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 2669B87C087004B50E01CD3B964E736A |
| SHA1: | BBA6066233F8800AFDB456C94706A78C5950C23E |
| SHA256: | AA6215E4FB1E233B56ED57703656B1C96ACFD3926659C49332C75AC978B3A6E0 |
| SSDEEP: | 98304:uEWwTombg4tqaO9zVhaY96eKNhRgbJnIB+p74S5Jp/Oj84MdylHPLPwx5eD4aSgQ:k4X4XJHEVQabvSaj |
MALICIOUS
No malicious indicators.SUSPICIOUS
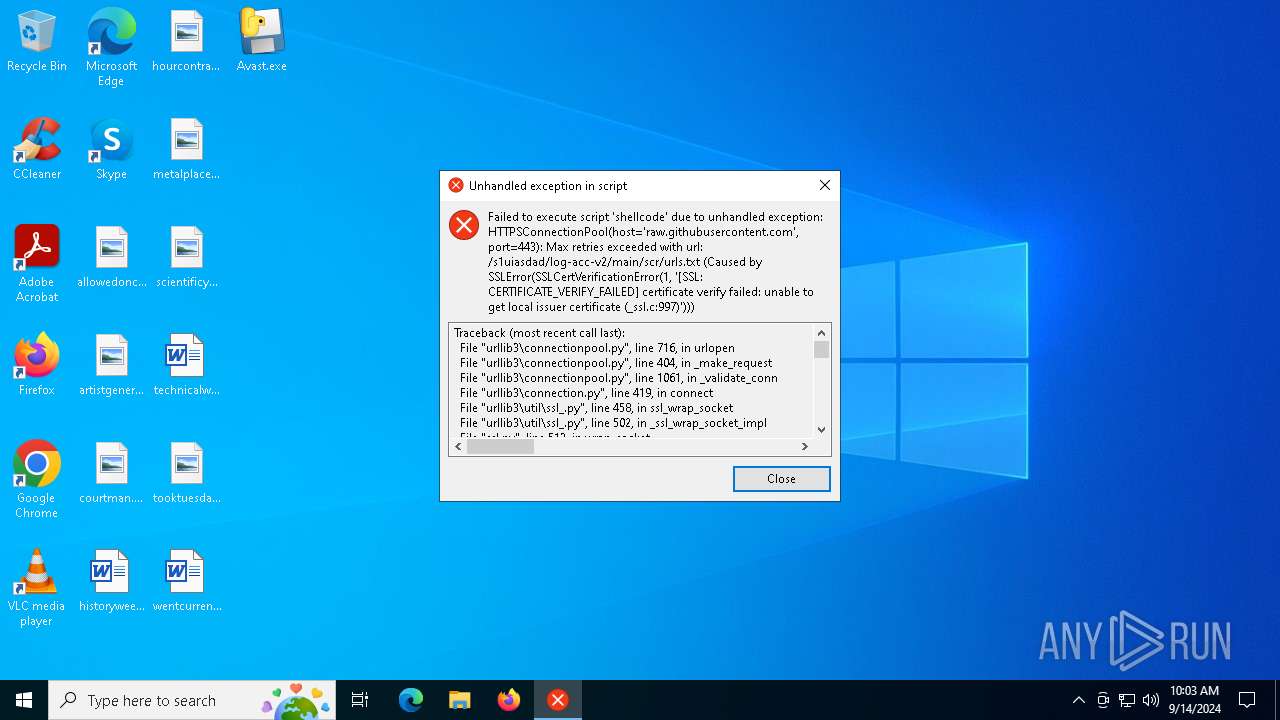
Process drops python dynamic module
- Avast.exe (PID: 6684)
Application launched itself
- Avast.exe (PID: 6684)
Loads Python modules
- Avast.exe (PID: 6460)
Executable content was dropped or overwritten
- Avast.exe (PID: 6684)
INFO
Checks supported languages
- Avast.exe (PID: 6684)
- Avast.exe (PID: 6460)
Reads the computer name
- Avast.exe (PID: 6684)
- Avast.exe (PID: 6460)
Create files in a temporary directory
- Avast.exe (PID: 6684)
Reads the machine GUID from the registry
- Avast.exe (PID: 6460)
Checks proxy server information
- Avast.exe (PID: 6460)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2024:09:14 08:56:47+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.4 |
| CodeSize: | 168960 |
| InitializedDataSize: | 153600 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc0d0 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
122
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6460 | "C:\Users\admin\Desktop\Avast.exe" | C:\Users\admin\Desktop\Avast.exe | Avast.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 6684 | "C:\Users\admin\Desktop\Avast.exe" | C:\Users\admin\Desktop\Avast.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
Total events
325
Read events
325
Write events
0
Delete events
0
Modification events
Executable files
61
Suspicious files
1
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:6E84207402F5CD66E00ABB1689DED080 | SHA256:301A110ED905F10243437C5BC2A92CDF7C8609C19CB8BAFF92C99D8645C8D6F0 | |||
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\_hashlib.pyd | executable | |
MD5:D856A545A960BF2DCA1E2D9BE32E5369 | SHA256:CD33F823E608D3BDA759AD441F583A20FC0198119B5A62A8964F172559ACB7D3 | |||
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\_ctypes.pyd | executable | |
MD5:CA4CEF051737B0E4E56B7D597238DF94 | SHA256:E60A2B100C4FA50B0B144CF825FE3CDE21A8B7B60B92BFC326CB39573CE96B2B | |||
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\_ssl.pyd | executable | |
MD5:9DDB64354EF0B91C6999A4B244A0A011 | SHA256:E33B7A4AA5CDD5462EE66830636FDD38048575A43D06EB7E2F688358525DDEAB | |||
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:5E43B4314980EB7F19506613D4523E63 | SHA256:DAAACD2FDF366E2C36B42398E850412C8BE3093E5B7A8F608684A656D27E4D6E | |||
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:8C717AD4C92FC26B40EC6830FD9289C7 | SHA256:C119A34D7AC08ECCB645A85415B4ABFA5A8FB05AFE20838EB6FFB558F01657FD | |||
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\_queue.pyd | executable | |
MD5:52D0A6009D3DE40F4FA6EC61DB98C45C | SHA256:007BCF19D9B036A7E73F5EF31F39BFB1910F72C9C10E4A1B0658352CFE7A8B75 | |||
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\api-ms-win-core-file-l1-2-0.dll | executable | |
MD5:AC28EDB5AD8EAA70ECBC64BAF3E70BD4 | SHA256:FBD5E958F6EFB4D78FD61EE9EE4B4D1B6F43C1210301668F654A880C65A1BE86 | |||
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\api-ms-win-core-handle-l1-1-0.dll | executable | |
MD5:3486DE24E09BC08B324C1C3E9E03B35C | SHA256:1E7A0823130CA36E2F061ED8C40554CEB5FAA906E10B6C042628E8EE6C776B4A | |||
| 6684 | Avast.exe | C:\Users\admin\AppData\Local\Temp\_MEI66842\_decimal.pyd | executable | |
MD5:6339FA92584252C3B24E4CCE9D73EF50 | SHA256:4AE6F6FB3992BB878416211221B3D62515E994D78F72EAB51E0126CA26D0EE96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
19
DNS requests
5
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6440 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6248 | RUXIMICS.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6440 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6248 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6440 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6248 | RUXIMICS.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6460 | Avast.exe | 185.199.110.133:443 | raw.githubusercontent.com | FASTLY | US | shared |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4324 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |