| File name: | aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1 |
| Full analysis: | https://app.any.run/tasks/af2d27be-f409-4a01-8986-c17ce0d5265c |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2022, 04:12:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | FEF4457233CA1E5C0786650A679402B4 |
| SHA1: | 64250C907712275F12F97A9B971F7AE17BE1BD8F |
| SHA256: | AA5B7F3A9B1A8A3A91F49E991B68779264814F0B70CA95ADD165F0586B799BE1 |
| SSDEEP: | 24576:zJSfxf+iXGTRQx13AU/36w6IhLLbsmvVmGHdKQnvL3kz:zgfxmmx1QM36J0fZH7jUz |
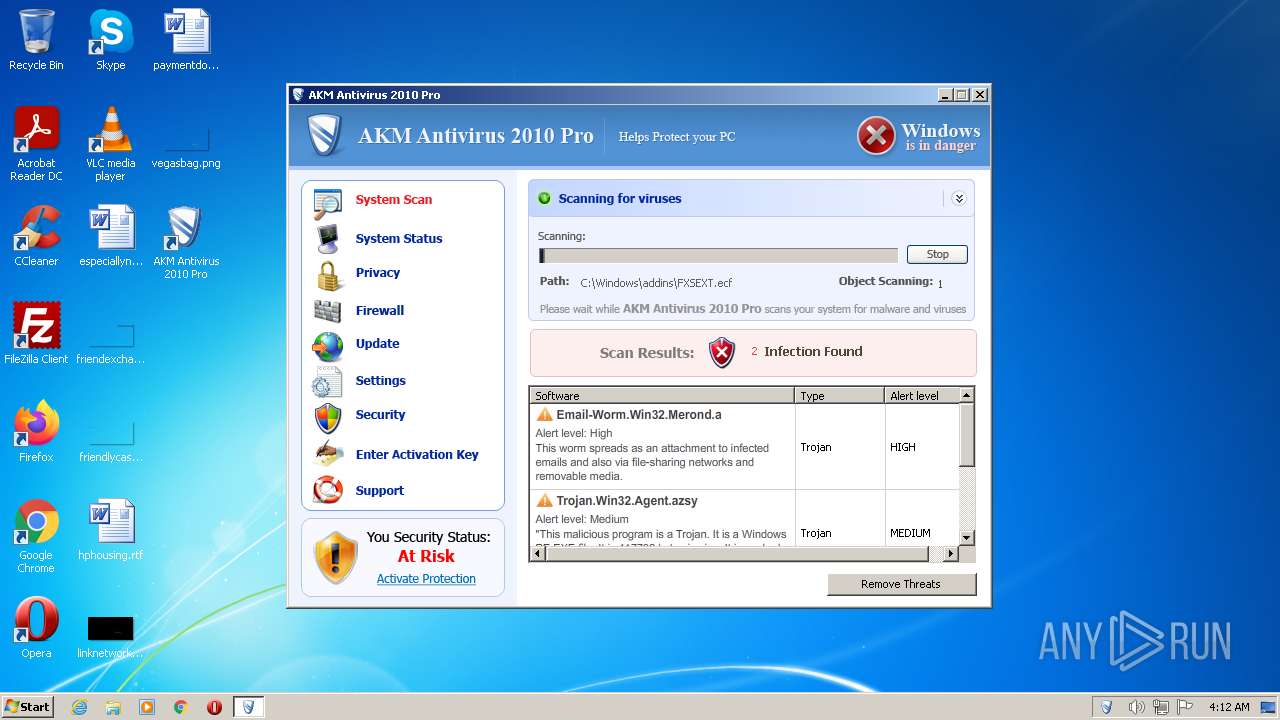
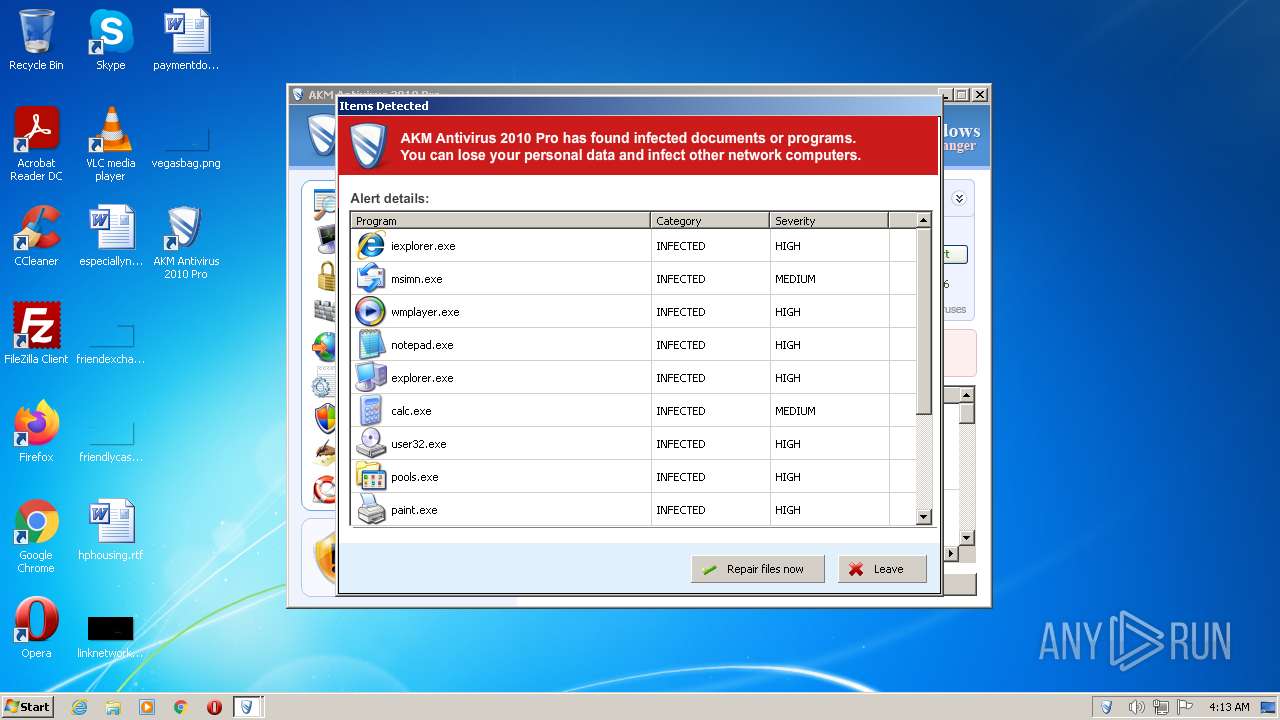
MALICIOUS
Drops the executable file immediately after the start
- aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe (PID: 1328)
- AKM Antivirus 2010 Pro.exe (PID: 2204)
Application was dropped or rewritten from another process
- svchost.exe (PID: 3444)
- svchost.exe (PID: 4052)
- win36C1.tmp (PID: 3944)
- alggui.exe (PID: 2776)
- alggui.exe (PID: 2880)
- svchost.exe (PID: 2976)
- svchost.exe (PID: 1884)
- svchost.exe (PID: 1968)
- svchost.exe (PID: 3392)
Application was injected by another process
- Explorer.EXE (PID: 1084)
- Dwm.exe (PID: 612)
Runs injected code in another process
- win36C1.tmp (PID: 3944)
SUSPICIOUS
Starts itself from another location
- aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe (PID: 1328)
- svchost.exe (PID: 3444)
- svchost.exe (PID: 2976)
Application launched itself
- aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe (PID: 1328)
- AKM Antivirus 2010 Pro.exe (PID: 2204)
- svchost.exe (PID: 3444)
- alggui.exe (PID: 2776)
- AKM Antivirus 2010 Pro.exe (PID: 2992)
- svchost.exe (PID: 2976)
- svchost.exe (PID: 1884)
- AKM Antivirus 2010 Pro.exe (PID: 4020)
Executable content was dropped or overwritten
- aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe (PID: 1328)
- AKM Antivirus 2010 Pro.exe (PID: 2204)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2010-May-04 12:51:01 |
| Detected languages: |
|
| CompanyName: | ADC ltd. |
| FileVersion: | 1.0.0.1 |
| InternalName: | wpp.exe |
| LegalCopyright: | (c) ADC ltd. All rights reserved. |
| ProductVersion: | 1.0.0.1 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 232 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 3 |
| TimeDateStamp: | 2010-May-04 12:51:01 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 4096 | 7086080 | 0 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
UPX1 | 7090176 | 1028096 | 1026048 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.95629 |
.rsrc | 8118272 | 24576 | 23040 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.96274 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.17624 | 7336 | UNKNOWN | Russian - Russia | RT_ICON |
2 | 4.27942 | 3240 | UNKNOWN | Russian - Russia | RT_ICON |
3 | 4.20139 | 872 | UNKNOWN | Russian - Russia | RT_ICON |
4 | 7.81066 | 3240 | UNKNOWN | Russian - Russia | RT_ICON |
5 | 7.81324 | 3240 | UNKNOWN | Russian - Russia | RT_ICON |
6 | 7.64942 | 872 | UNKNOWN | Russian - Russia | RT_ICON |
7 | 7.65907 | 872 | UNKNOWN | Russian - Russia | RT_ICON |
8 | 7.67007 | 1128 | UNKNOWN | Russian - Russia | RT_ICON |
9 | 7.76091 | 2040 | UNKNOWN | Russian - Russia | RT_ICON |
10 | 7.76721 | 2040 | UNKNOWN | Russian - Russia | RT_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.DLL |
OLEAUT32.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
WINMM.dll |
WINSPOOL.DRV |
Total processes
52
Monitored processes
19
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | "C:\Windows\system32\Dwm.exe" | C:\Windows\system32\Dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 984 | "C:\Users\admin\AppData\Roaming\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro.exe" | C:\Users\admin\AppData\Roaming\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro.exe | — | AKM Antivirus 2010 Pro.exe | |||||||||||
User: admin Company: ADC ltd. Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1084 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1328 | "C:\Users\admin\AppData\Local\Temp\aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe" | C:\Users\admin\AppData\Local\Temp\aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe | Explorer.EXE | ||||||||||||
User: admin Company: ADC ltd. Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 1884 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1968 | "C:\Users\admin\AppData\Roaming\svchost.exe" | C:\Users\admin\AppData\Roaming\svchost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2204 | "C:\Users\admin\AppData\Roaming\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro.exe" | C:\Users\admin\AppData\Roaming\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro.exe | aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe | ||||||||||||
User: admin Company: ADC ltd. Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\AppData\Local\Temp\aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe" | C:\Users\admin\AppData\Local\Temp\aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe | — | aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe | |||||||||||
User: admin Company: ADC ltd. Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2512 | "C:\Users\admin\AppData\Roaming\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro.exe" | C:\Users\admin\AppData\Roaming\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro.exe | — | AKM Antivirus 2010 Pro.exe | |||||||||||
User: admin Company: ADC ltd. Integrity Level: MEDIUM Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2776 | "C:\Users\admin\AppData\Roaming\alggui.exe" | C:\Users\admin\AppData\Roaming\alggui.exe | — | AKM Antivirus 2010 Pro.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
3 715
Read events
3 614
Write events
97
Delete events
4
Modification events
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro\setdata |
| Operation: | write | Name: | scantime |
Value: 6.12.2022 4:12:42 | |||
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro\setdata |
| Operation: | write | Name: | scncnt |
Value: 1 | |||
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003D010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2204) AKM Antivirus 2010 Pro.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
5
Suspicious files
2
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1328 | aa5b7f3a9b1a8a3a91f49e991b68779264814f0b70ca95add165f0586b799be1.exe | C:\Users\admin\AppData\Roaming\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro.exe | executable | |
MD5:— | SHA256:— | |||
| 2204 | AKM Antivirus 2010 Pro.exe | C:\Users\admin\AppData\Roaming\svchost.exe | executable | |
MD5:— | SHA256:— | |||
| 2204 | AKM Antivirus 2010 Pro.exe | C:\Users\admin\AppData\Roaming\skynet.dat | binary | |
MD5:— | SHA256:— | |||
| 2204 | AKM Antivirus 2010 Pro.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\AKM Antivirus 2010 Pro\AKM Antivirus 2010 Pro.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2204 | AKM Antivirus 2010 Pro.exe | C:\Users\admin\Desktop\AKM Antivirus 2010 Pro.lnk | lnk | |
MD5:— | SHA256:— | |||
| 2204 | AKM Antivirus 2010 Pro.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\svchost.exe | executable | |
MD5:— | SHA256:— | |||
| 2204 | AKM Antivirus 2010 Pro.exe | C:\Users\admin\AppData\Roaming\wp3.dat | binary | |
MD5:CFCD208495D565EF66E7DFF9F98764DA | SHA256:5FECEB66FFC86F38D952786C6D696C79C2DBC239DD4E91B46729D73A27FB57E9 | |||
| 2204 | AKM Antivirus 2010 Pro.exe | C:\Users\admin\AppData\Roaming\wp4.dat | text | |
MD5:48A8ED30532B2D13B7144224FC8BE28D | SHA256:CFF79721D13BB4FC11D40E25C02DF8DADF288097D5A55280B84C65C45E4C1856 | |||
| 2204 | AKM Antivirus 2010 Pro.exe | C:\Users\admin\AppData\Roaming\alggui.exe | executable | |
MD5:— | SHA256:— | |||
| 2204 | AKM Antivirus 2010 Pro.exe | C:\Users\admin\AppData\Local\Temp\win36C1.tmp | executable | |
MD5:ED21B352D000691F00EBBE08B265DB66 | SHA256:62ED3C2009D67DF1D28E8C80E311B2243F94E10D4A83ED014166257F734D7B24 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
2
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
time.windows.com |
| whitelisted |
core2637.instituteofbianco.com |
| unknown |