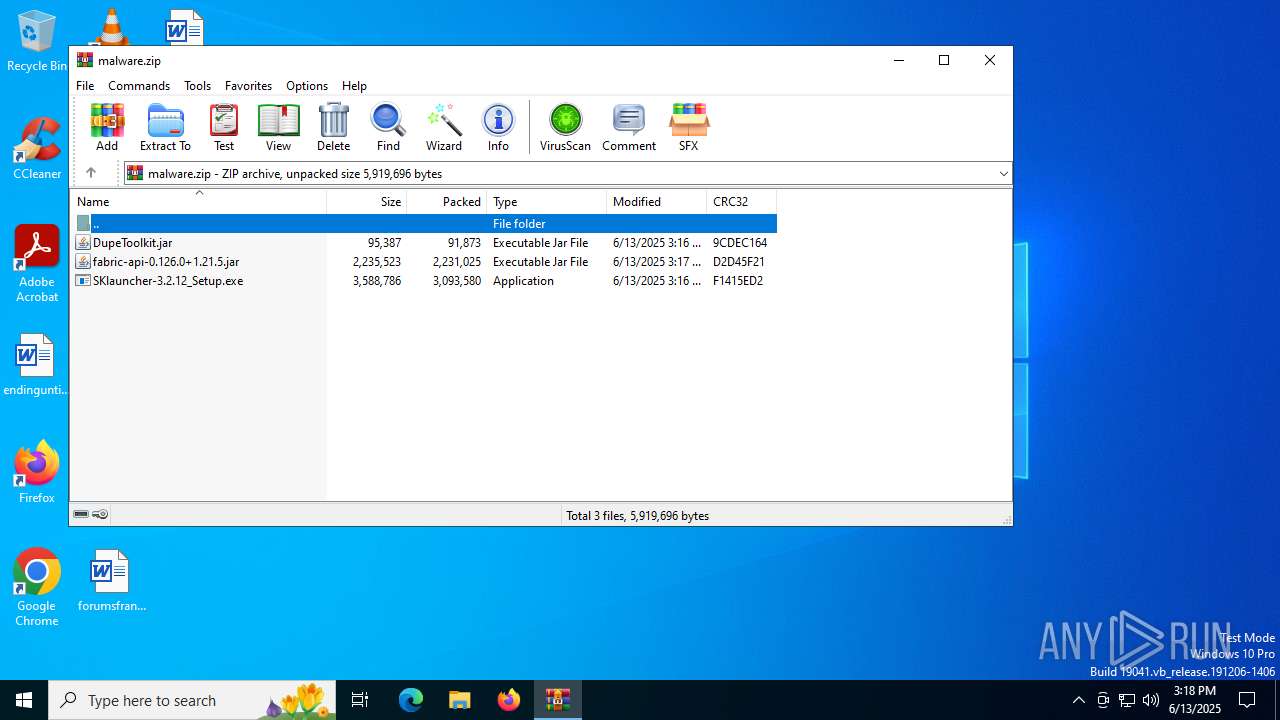
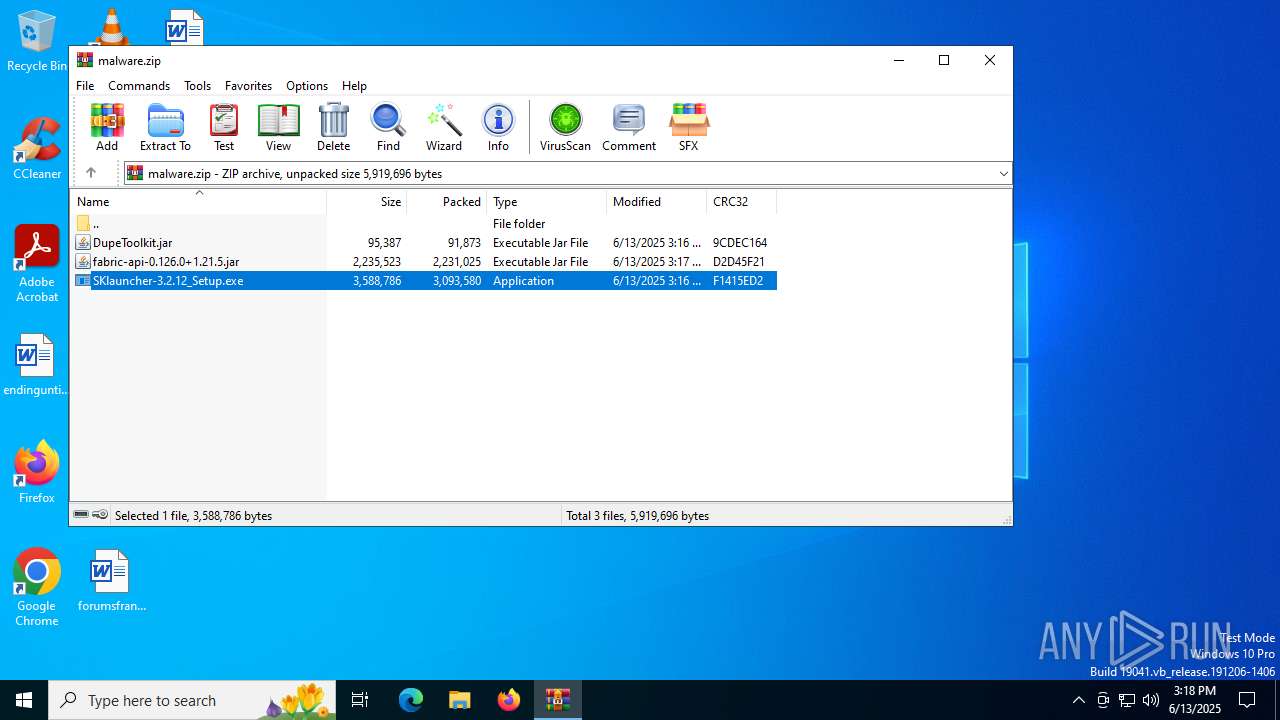
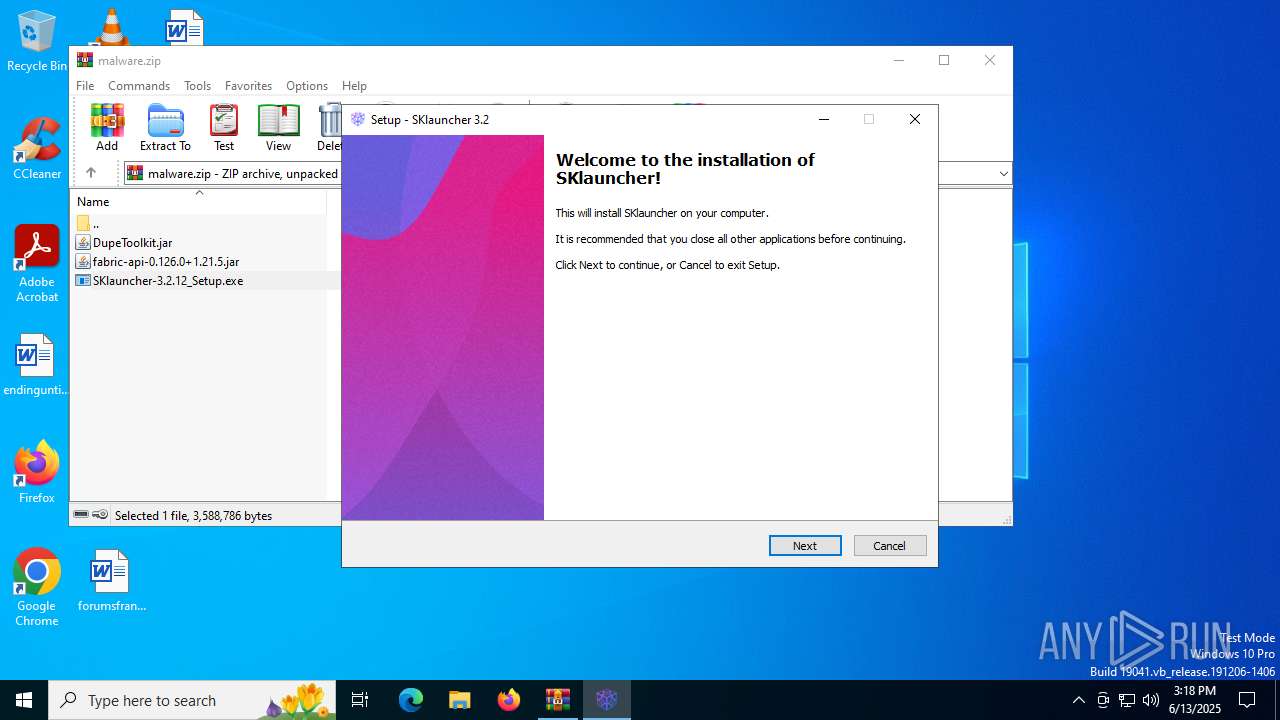
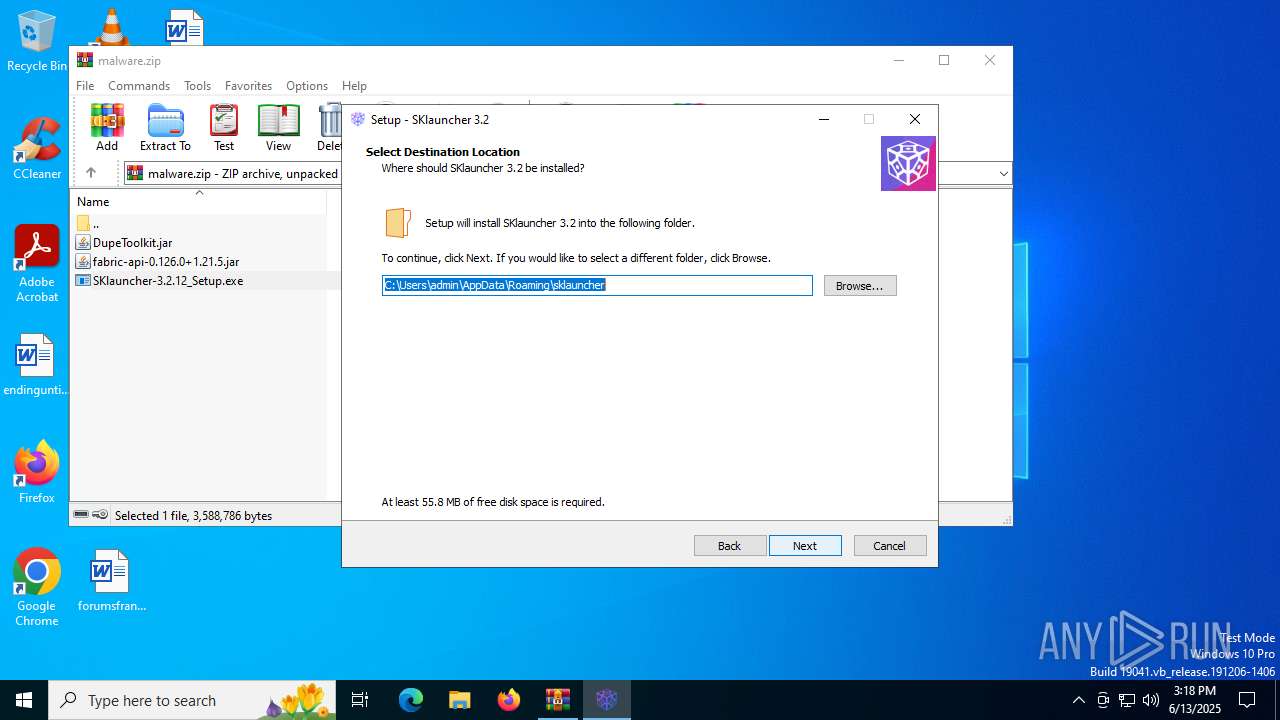
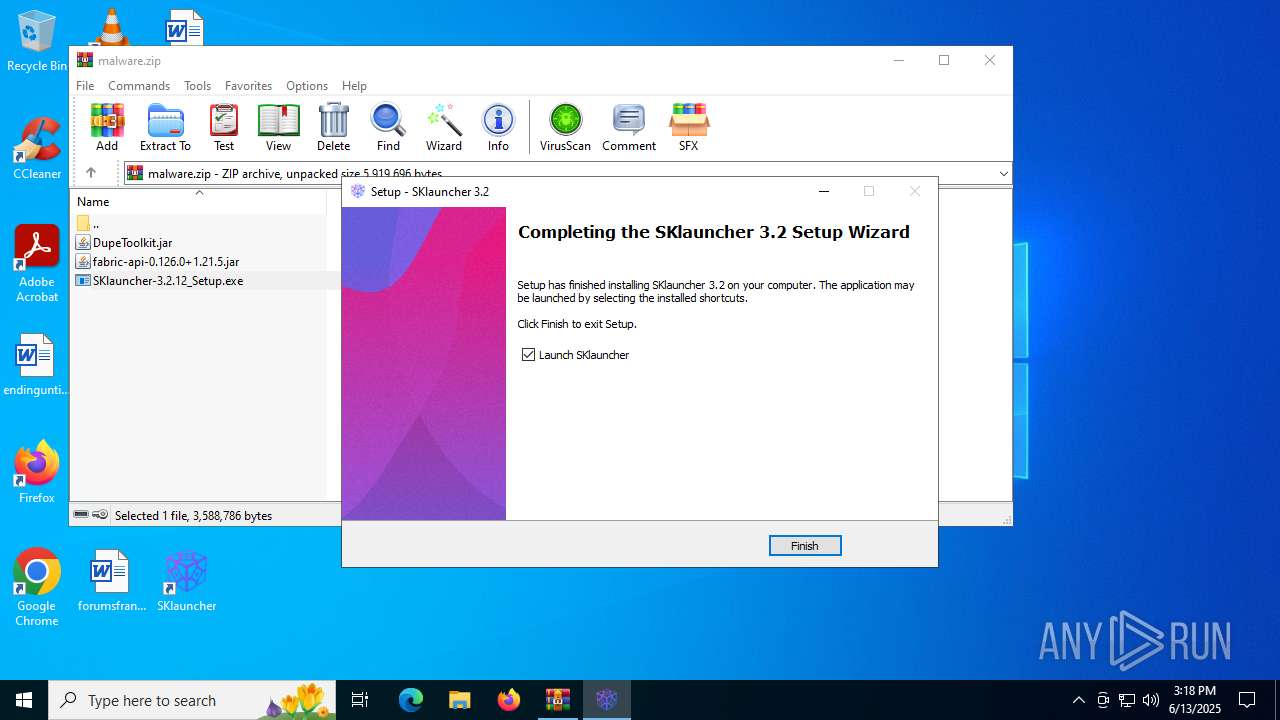
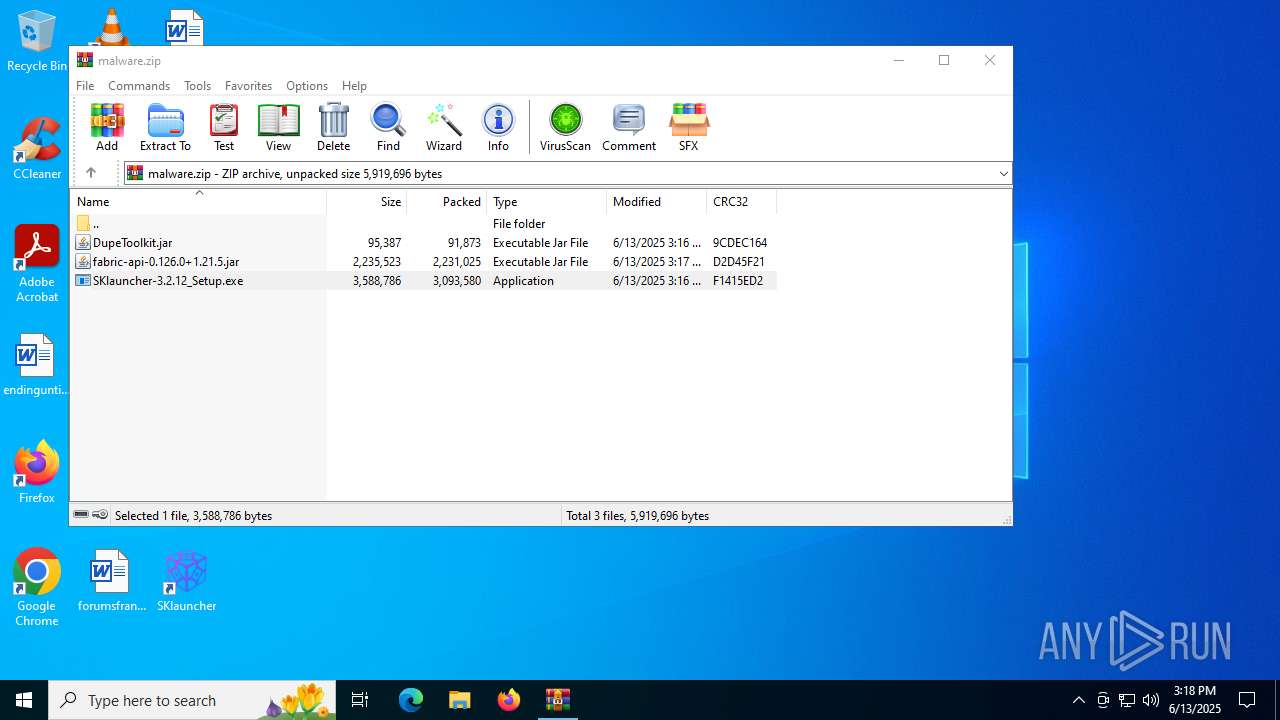
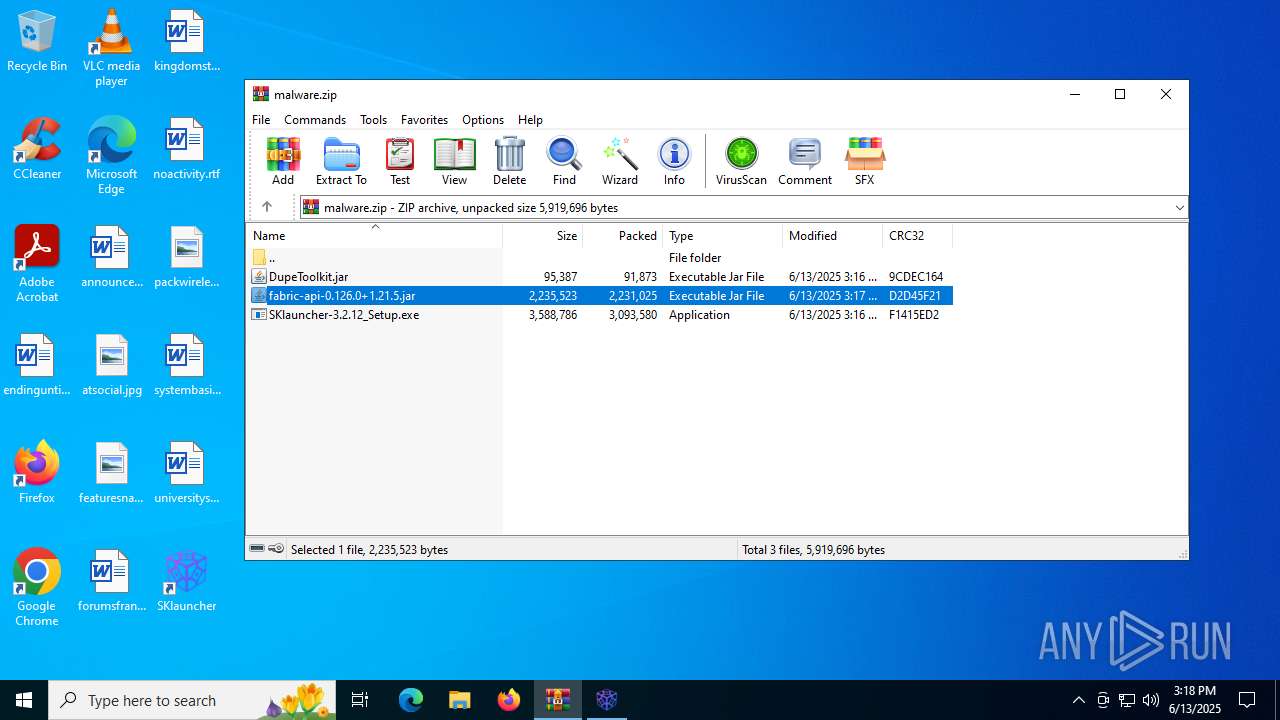
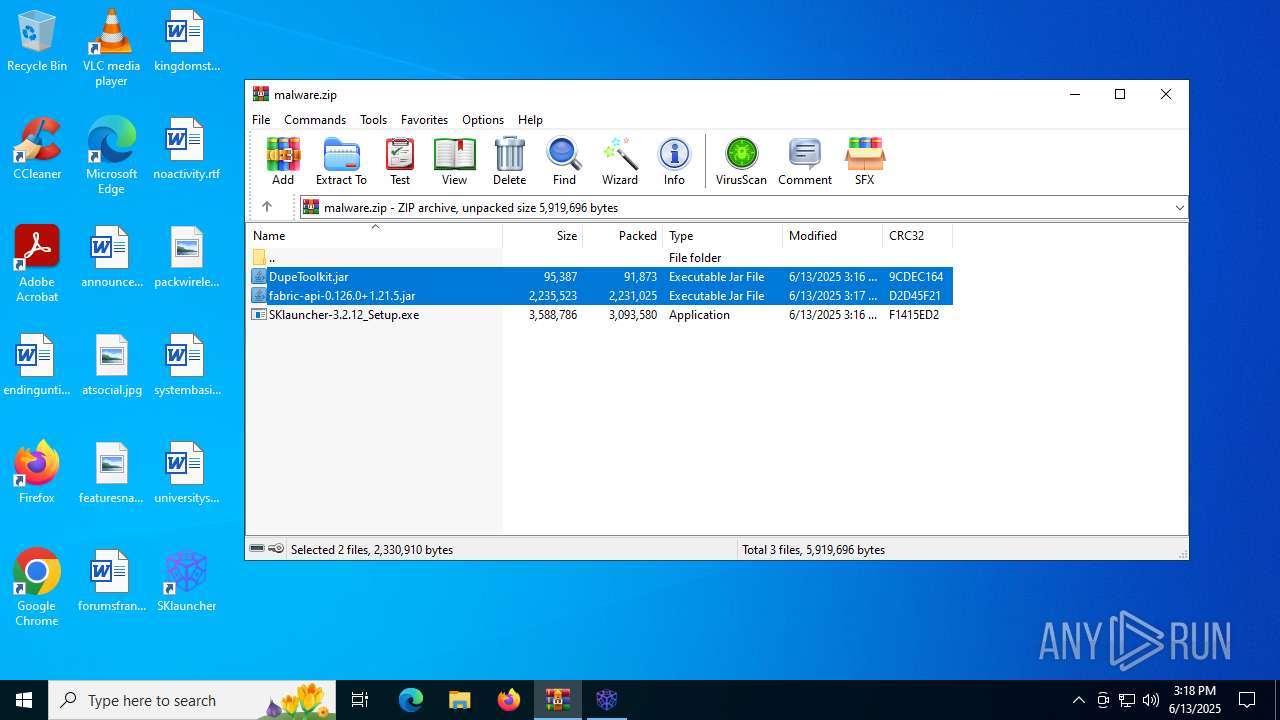
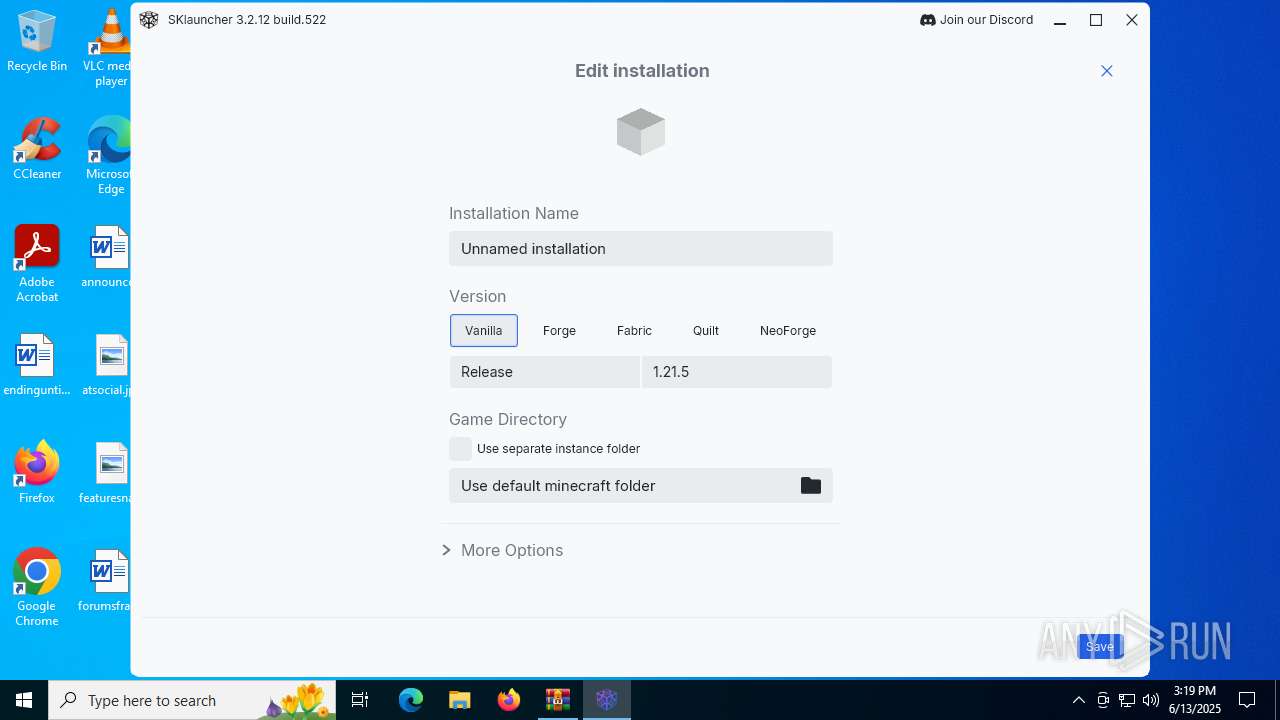
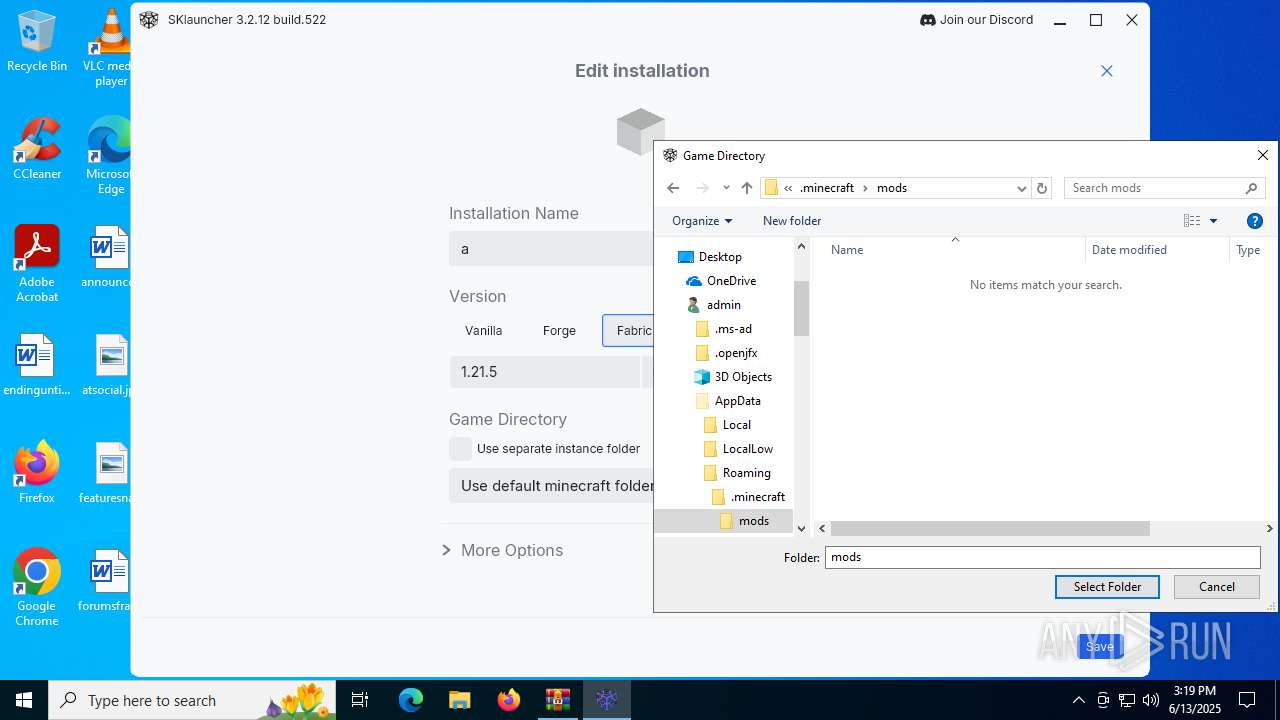
| File name: | malware.zip |
| Full analysis: | https://app.any.run/tasks/69f75e1b-5ba8-412d-bcea-8e1a88015955 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 15:17:55 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 27414B404803B738BB12F0B9104529CB |
| SHA1: | A6E3CA0308BC057917665F122B01323A090B8356 |
| SHA256: | AA55951CC57AC36852FD982332CC33E76B4EC27A8D78E1FBCF2E760434CBF31C |
| SSDEEP: | 98304:if0NinOMpPkIP7hUG8zG1eES2SnmEsgeziqyauY/52Vc+eC4YvFr5FvgJCAM6+wj:30mioNUDu6MT7pe2Q/P |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2076)
SUSPICIOUS
Executable content was dropped or overwritten
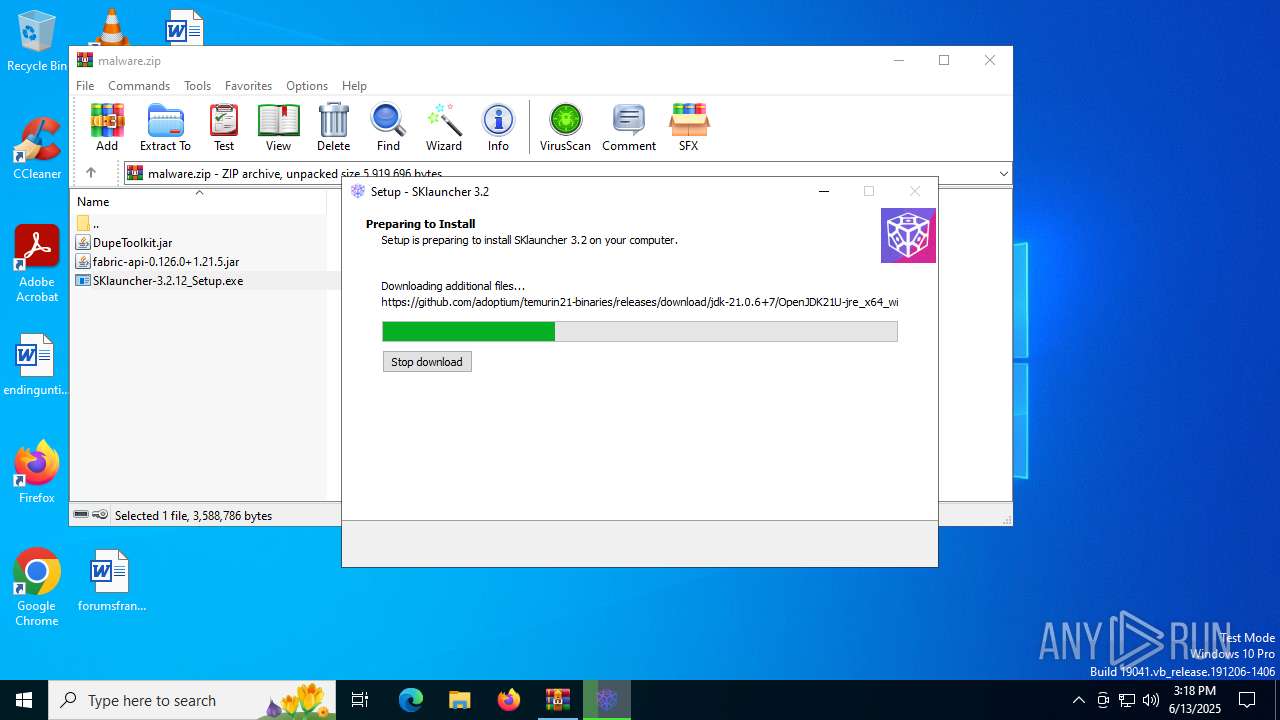
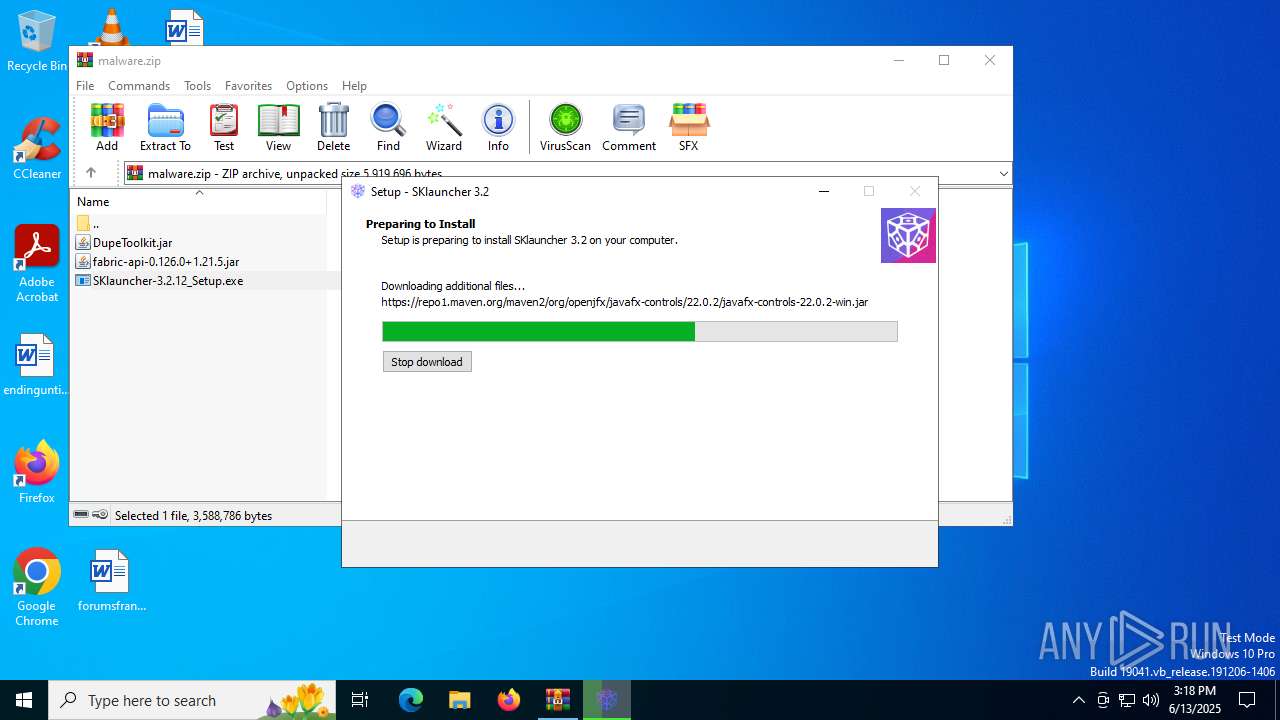
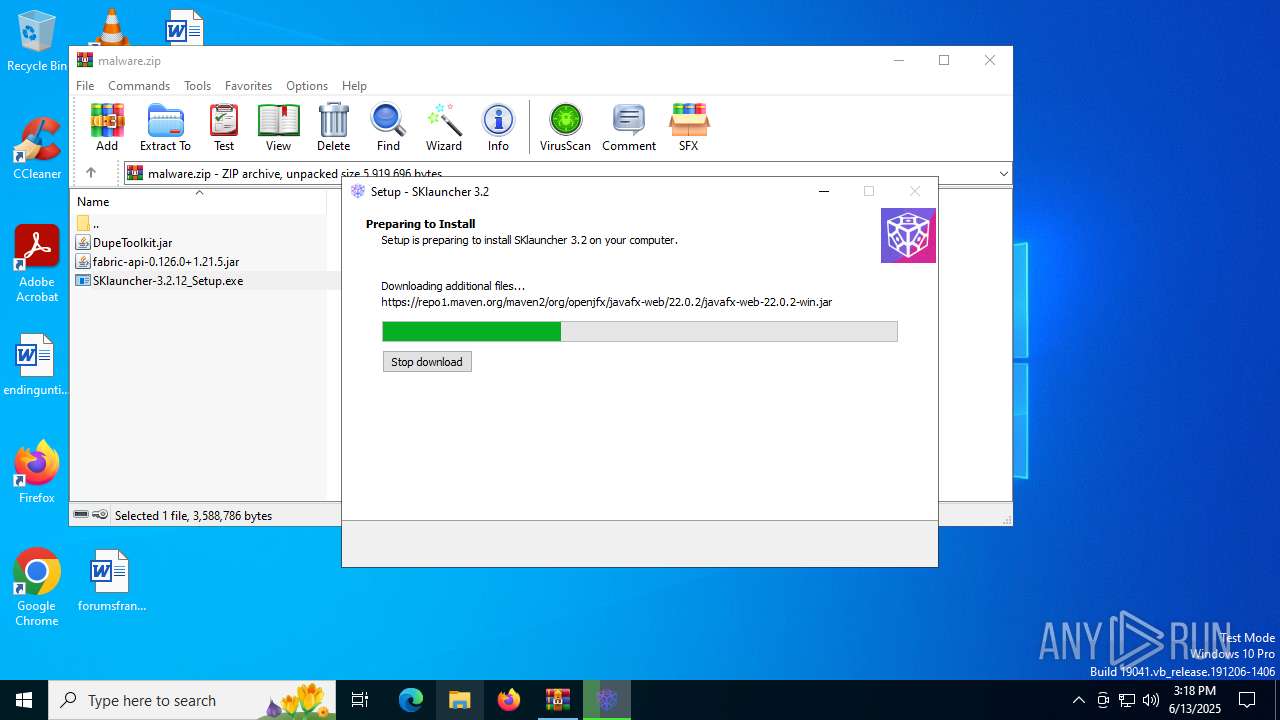
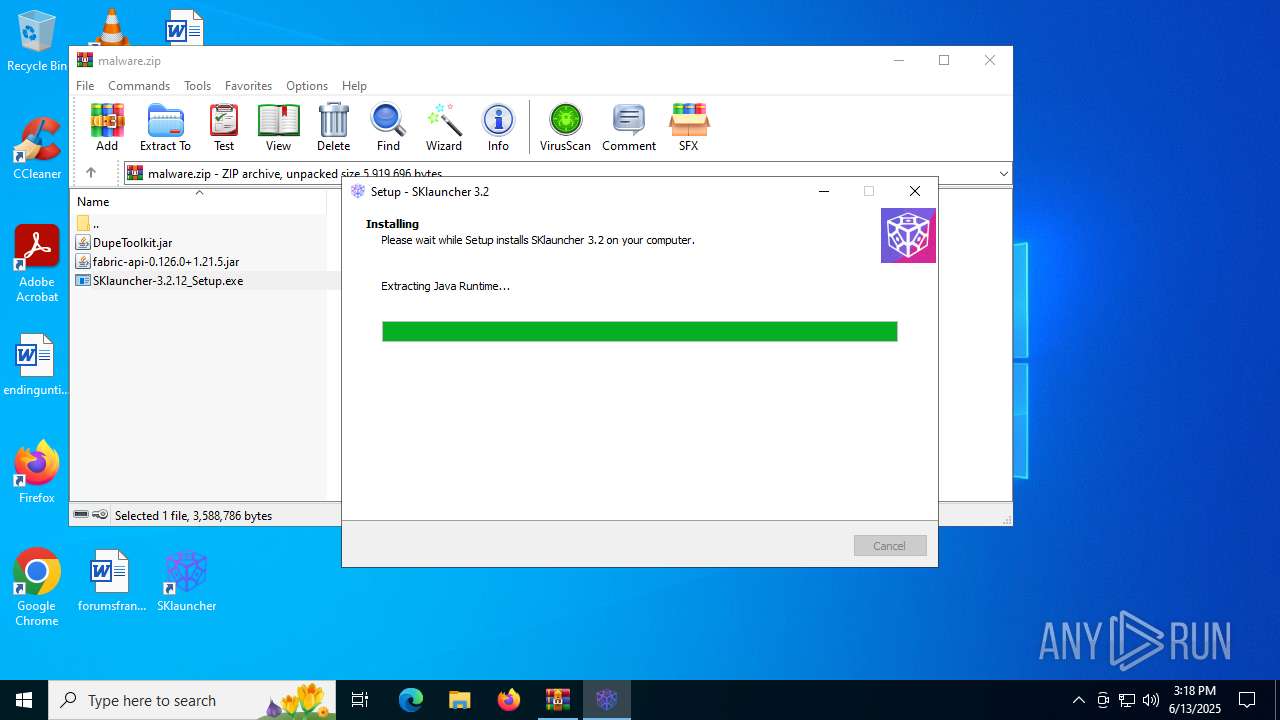
- SKlauncher-3.2.12_Setup.exe (PID: 5496)
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
- 7za.exe (PID: 4816)
- javaw.exe (PID: 1652)
Reads the Windows owner or organization settings
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
Drops 7-zip archiver for unpacking
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
Process drops legitimate windows executable
- 7za.exe (PID: 4816)
- javaw.exe (PID: 1652)
The process drops C-runtime libraries
- 7za.exe (PID: 4816)
- javaw.exe (PID: 1652)
There is functionality for VM detection antiVM strings (YARA)
- javaw.exe (PID: 1652)
There is functionality for VM detection VirtualBox (YARA)
- javaw.exe (PID: 1652)
There is functionality for VM detection VMWare (YARA)
- javaw.exe (PID: 1652)
Reads security settings of Internet Explorer
- javaw.exe (PID: 1652)
- WinRAR.exe (PID: 2076)
There is functionality for taking screenshot (YARA)
- javaw.exe (PID: 1652)
INFO
Create files in a temporary directory
- SKlauncher-3.2.12_Setup.exe (PID: 5496)
- javaw.exe (PID: 1652)
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
Reads the computer name
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
- 7za.exe (PID: 4816)
- javaw.exe (PID: 1652)
Checks supported languages
- SKlauncher-3.2.12_Setup.exe (PID: 5496)
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
- 7za.exe (PID: 4816)
- javaw.exe (PID: 1652)
Checks proxy server information
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
Compiled with Borland Delphi (YARA)
- SKlauncher-3.2.12_Setup.exe (PID: 5496)
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
Detects InnoSetup installer (YARA)
- SKlauncher-3.2.12_Setup.exe (PID: 5496)
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
Reads the software policy settings
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
The sample compiled with english language support
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
- 7za.exe (PID: 4816)
- javaw.exe (PID: 1652)
Creates a software uninstall entry
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
Creates files or folders in the user directory
- 7za.exe (PID: 4816)
- javaw.exe (PID: 1652)
- SKlauncher-3.2.12_Setup.tmp (PID: 5008)
Reads Environment values
- javaw.exe (PID: 1652)
Reads CPU info
- javaw.exe (PID: 1652)
Reads the machine GUID from the registry
- javaw.exe (PID: 1652)
Process checks computer location settings
- javaw.exe (PID: 1652)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2076)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0008 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:13 17:17:30 |
| ZipCRC: | 0xd2d45f21 |
| ZipCompressedSize: | 2231025 |
| ZipUncompressedSize: | 2235523 |
| ZipFileName: | fabric-api-0.126.0+1.21.5.jar |
Total processes
148
Monitored processes
10
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7za.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
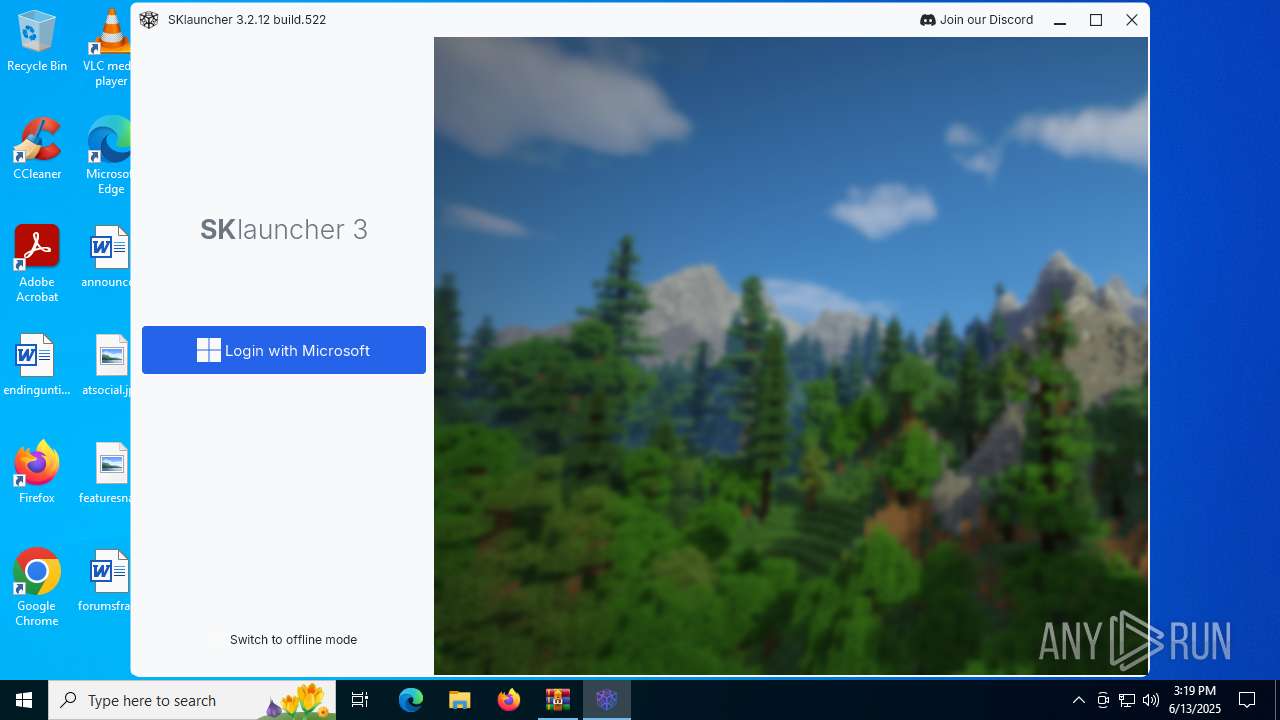
| 1652 | "C:\Users\admin\AppData\Roaming\sklauncher\jre\bin\javaw.exe" -Xmx512M -jar "C:\Users\admin\AppData\Roaming\sklauncher\SKlauncher.jar" | C:\Users\admin\AppData\Roaming\sklauncher\jre\bin\javaw.exe | SKlauncher-3.2.12_Setup.tmp | ||||||||||||
User: admin Company: Eclipse Adoptium Integrity Level: MEDIUM Description: OpenJDK Platform binary Version: 21.0.6.0 Modules
| |||||||||||||||
| 2076 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\malware.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2792 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3760 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4476 | reg query "HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Themes\Personalize" /v AppsUseLightTheme | C:\Windows\System32\reg.exe | — | javaw.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4816 | "C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\7za.exe" x -y C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\jre.zip | C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\7za.exe | SKlauncher-3.2.12_Setup.tmp | ||||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Standalone Console Exit code: 0 Version: 24.09 Modules
| |||||||||||||||
| 5008 | "C:\Users\admin\AppData\Local\Temp\is-A01KO.tmp\SKlauncher-3.2.12_Setup.tmp" /SL5="$50304,2553666,803840,C:\Users\admin\AppData\Local\Temp\Rar$EXa2076.19380\SKlauncher-3.2.12_Setup.exe" | C:\Users\admin\AppData\Local\Temp\is-A01KO.tmp\SKlauncher-3.2.12_Setup.tmp | SKlauncher-3.2.12_Setup.exe | ||||||||||||
User: admin Company: skmedix.pl Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 5496 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2076.19380\SKlauncher-3.2.12_Setup.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2076.19380\SKlauncher-3.2.12_Setup.exe | WinRAR.exe | ||||||||||||
User: admin Company: skmedix.pl Integrity Level: MEDIUM Description: SKlauncher 3.2 Setup Exit code: 0 Version: 3.2.12.0 Modules
| |||||||||||||||
Total events
9 910
Read events
9 794
Write events
110
Delete events
6
Modification events
| (PID) Process: | (2076) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2076) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2076) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2076) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\malware.zip | |||
| (PID) Process: | (2076) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2076) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2076) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2076) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5008) SKlauncher-3.2.12_Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{A151427E-7A46-4D6D-8534-C4C04BADA77A}_is1 |
| Operation: | write | Name: | DisplayVersion |
Value: 3.2.12.0 | |||
| (PID) Process: | (5008) SKlauncher-3.2.12_Setup.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{A151427E-7A46-4D6D-8534-C4C04BADA77A}_is1 |
| Operation: | write | Name: | Publisher |
Value: skmedix.pl | |||
Executable files
164
Suspicious files
31
Text files
233
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5008 | SKlauncher-3.2.12_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\is-U02VC.tmp | — | |
MD5:— | SHA256:— | |||
| 5008 | SKlauncher-3.2.12_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\jre.zip | — | |
MD5:— | SHA256:— | |||
| 2076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2076.19380\fabric-api-0.126.0+1.21.5.jar | java | |
MD5:4A392901E20767B652262FE6E555A6C4 | SHA256:F58FD28F0104153BC074E6E7DEFDFA59482A86D6020D1606C358F92A97CD5DD8 | |||
| 5008 | SKlauncher-3.2.12_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\javafx-0.jar | compressed | |
MD5:239410D2A0EBE901C2BAED127E865453 | SHA256:90E581C31638FBB041015C360D9EC6083AF7B666AC08EF03CD94CF274447F614 | |||
| 5008 | SKlauncher-3.2.12_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\is-Q4TFQ.tmp | compressed | |
MD5:239410D2A0EBE901C2BAED127E865453 | SHA256:90E581C31638FBB041015C360D9EC6083AF7B666AC08EF03CD94CF274447F614 | |||
| 5008 | SKlauncher-3.2.12_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\javafx-1.jar.sha1 | text | |
MD5:CB19A3834C52905BBC7AAE9B0CB884D8 | SHA256:D8E035498BA5918ACB7899067177FDEFB3300D7690419EC6B564E49902AB0160 | |||
| 2076 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2076.19380\DupeToolkit.jar | compressed | |
MD5:20EBD7C98CD84D5546C911AF1A765705 | SHA256:B2CA7776D219E4386EBF6538E7FD30459ACB06E4FC9C8DA79D35D18A7E3C807E | |||
| 5008 | SKlauncher-3.2.12_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 5008 | SKlauncher-3.2.12_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\is-C1SD3.tmp | compressed | |
MD5:6AD87D83A49A3B25FB5E137038B2C5DE | SHA256:6828F4FD83AC7CAEB7E25C21E4050606D384BAEBB18BC3B1F35CD866020757CC | |||
| 5008 | SKlauncher-3.2.12_Setup.tmp | C:\Users\admin\AppData\Local\Temp\is-1AS0O.tmp\is-N5L8T.tmp | compressed | |
MD5:481E60FF6432B3816D78DD3A94D6C89B | SHA256:0AB89FA8531F5D6F1A15B6C76CF5A7D44E60E273932AD282B29B8DD324E725FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
59
DNS requests
33
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7020 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6292 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6292 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4156 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7020 | svchost.exe | 40.126.31.128:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7020 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5008 | SKlauncher-3.2.12_Setup.tmp | 140.82.121.3:443 | github.com | GITHUB | US | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
github.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1652 | javaw.exe | Misc activity | ET INFO Observed Google DNS over HTTPS Domain (dns .google in TLS SNI) |
2200 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Tag Manager analytics (googletagmanager .com) |