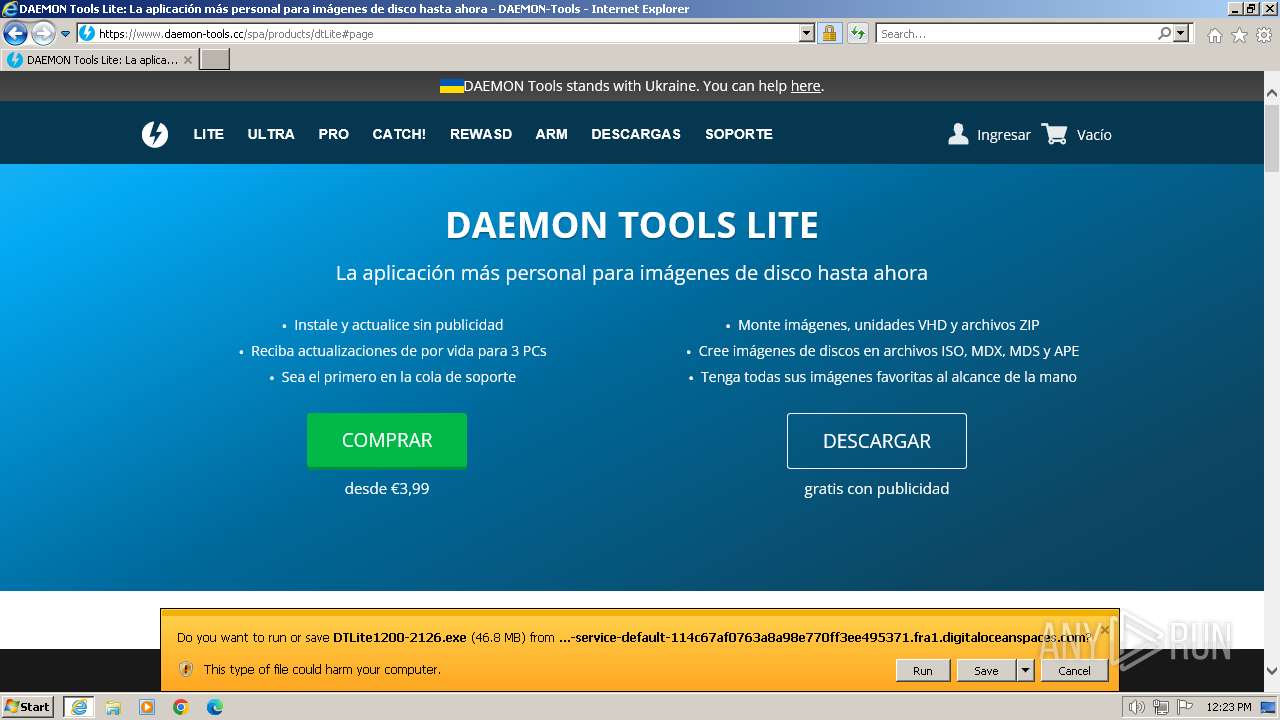
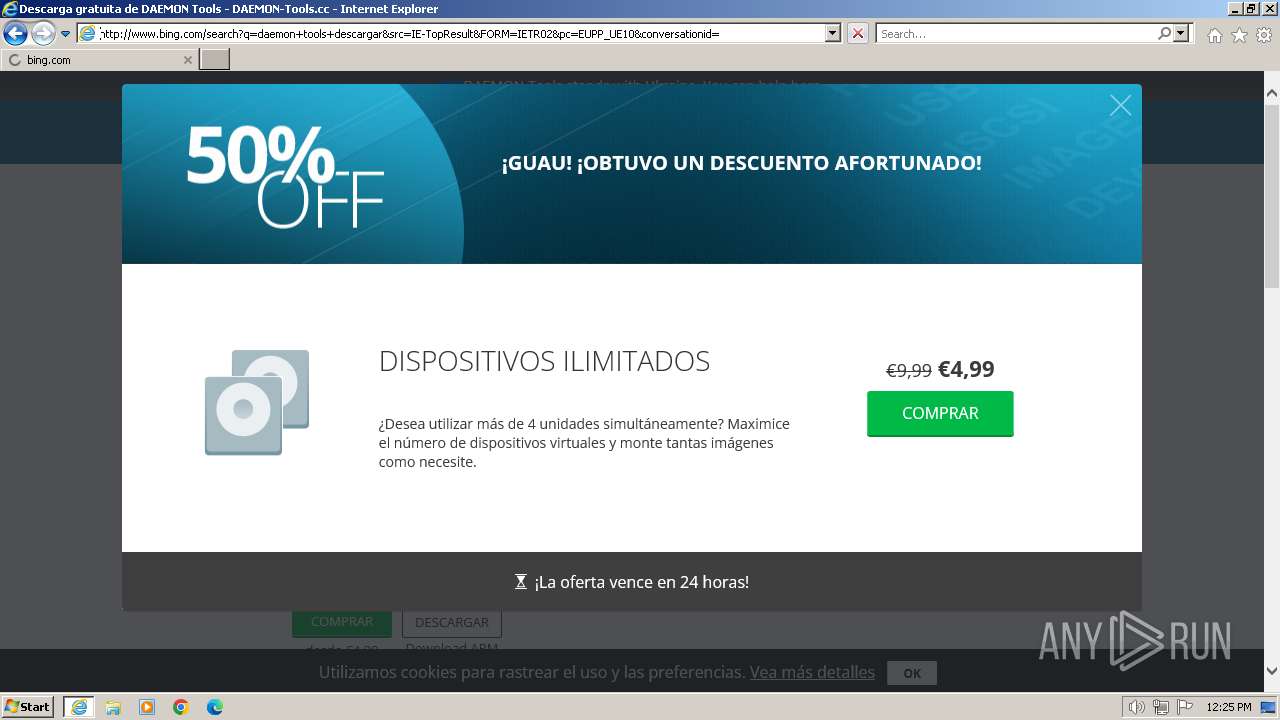
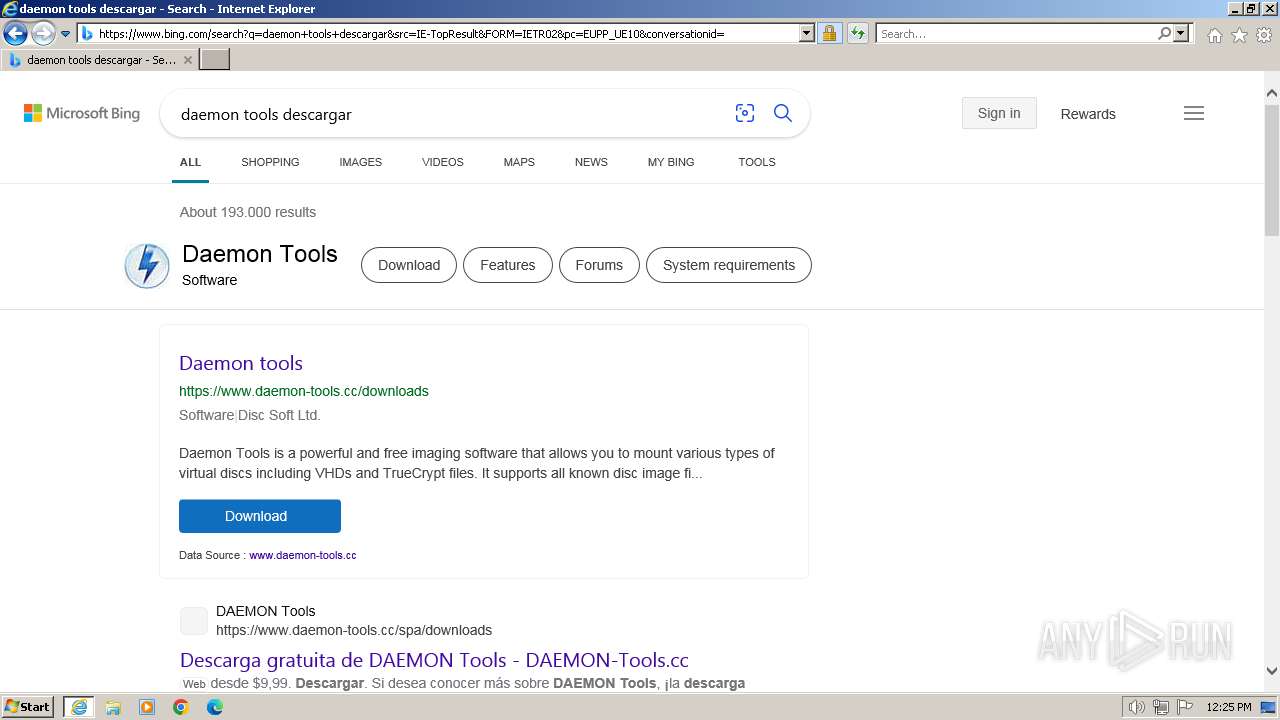
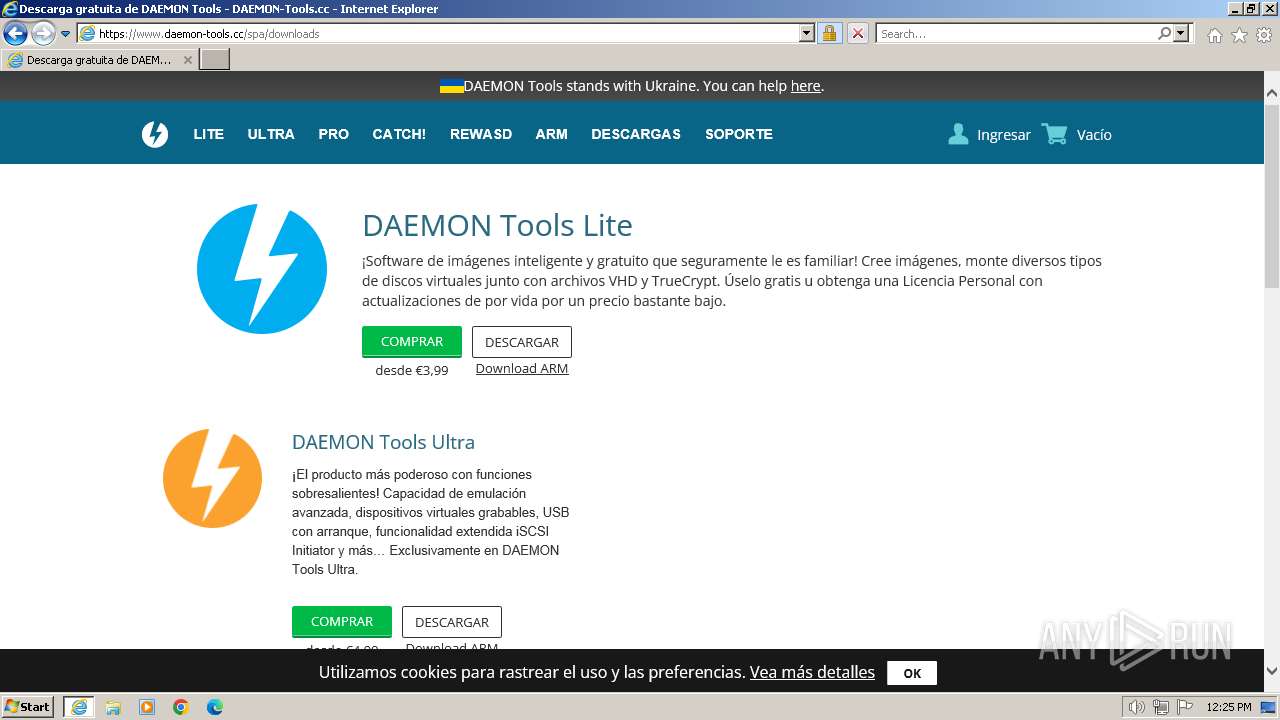
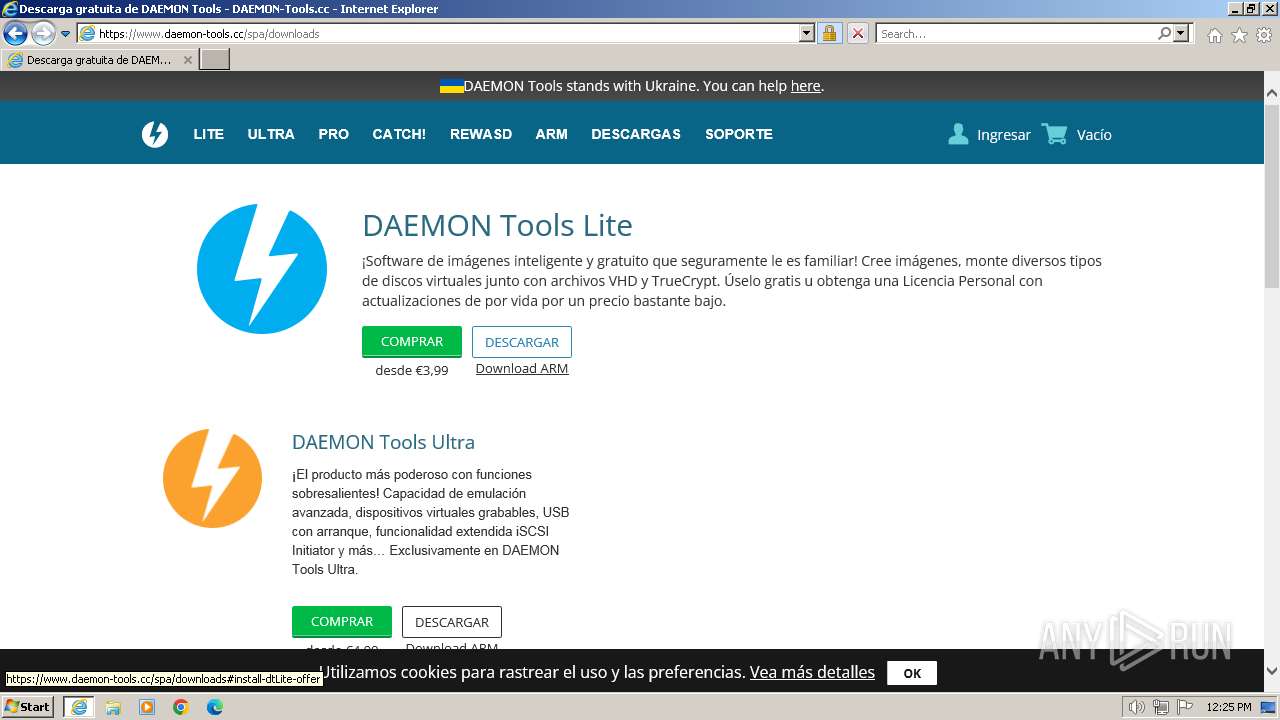
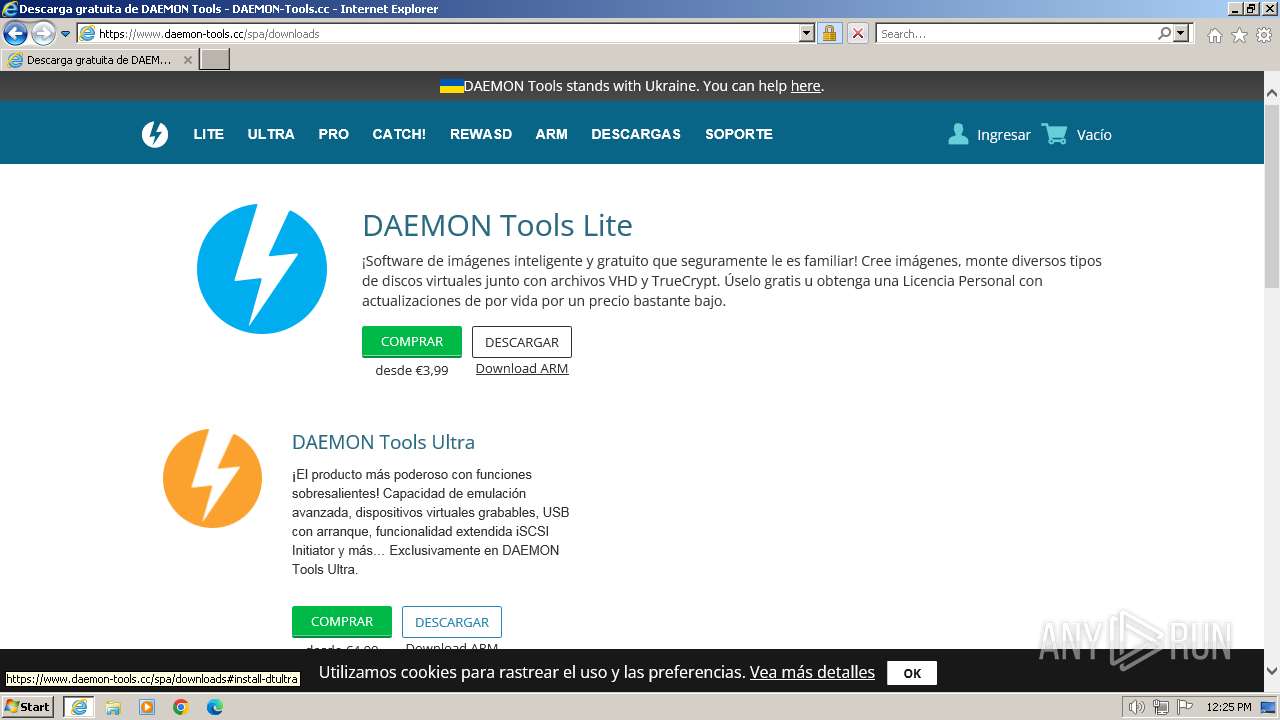
| URL: | https://www.daemon-tools.cc/spa/products/dtLite |
| Full analysis: | https://app.any.run/tasks/2bb4687b-7b4e-4df4-98f3-5df521e2de4d |
| Verdict: | Malicious activity |
| Analysis date: | March 12, 2024, 12:23:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 9BC47B8772409CD2E314960CB031B4AE |
| SHA1: | 6164FDC3259DD08A5A5580F05BE12FAB772064C4 |
| SHA256: | AA543F35A95B1619C7593DB63787B9E1198F3C991465166AC9EA7C0392300C2A |
| SSDEEP: | 3:N8DSL3IRkimGRWaRyA:2OL4RDRWO |
MALICIOUS
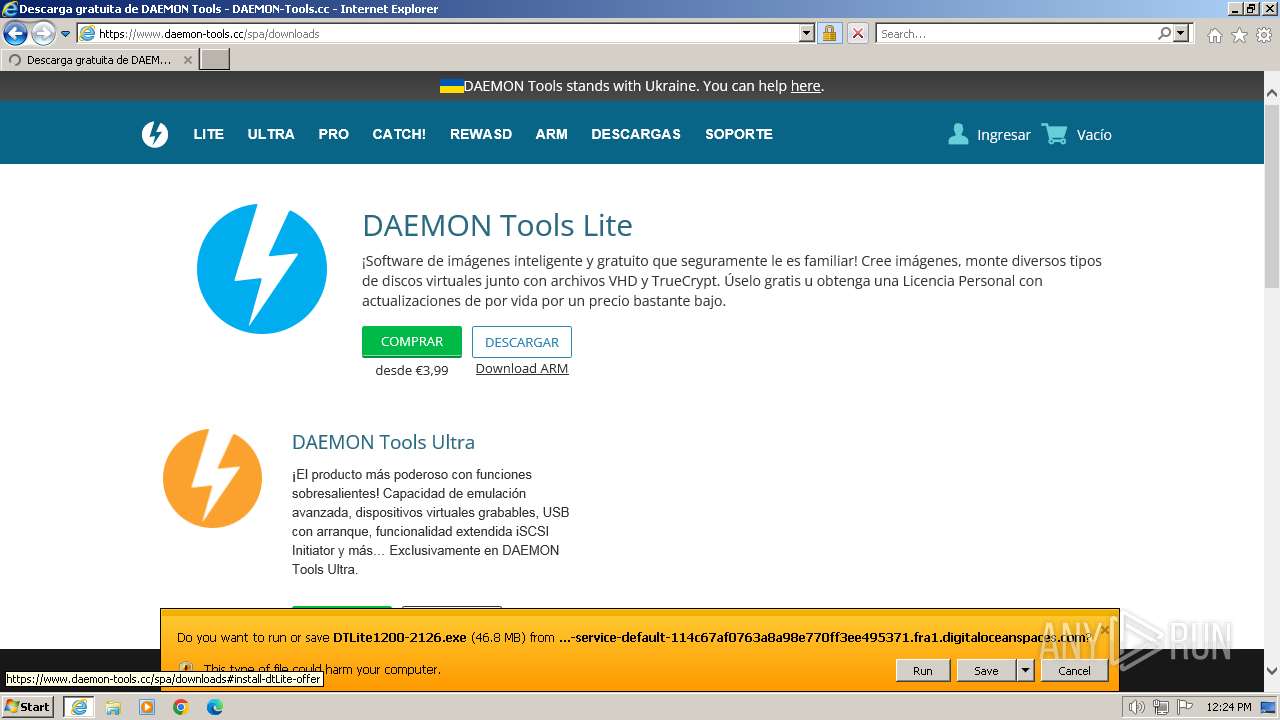
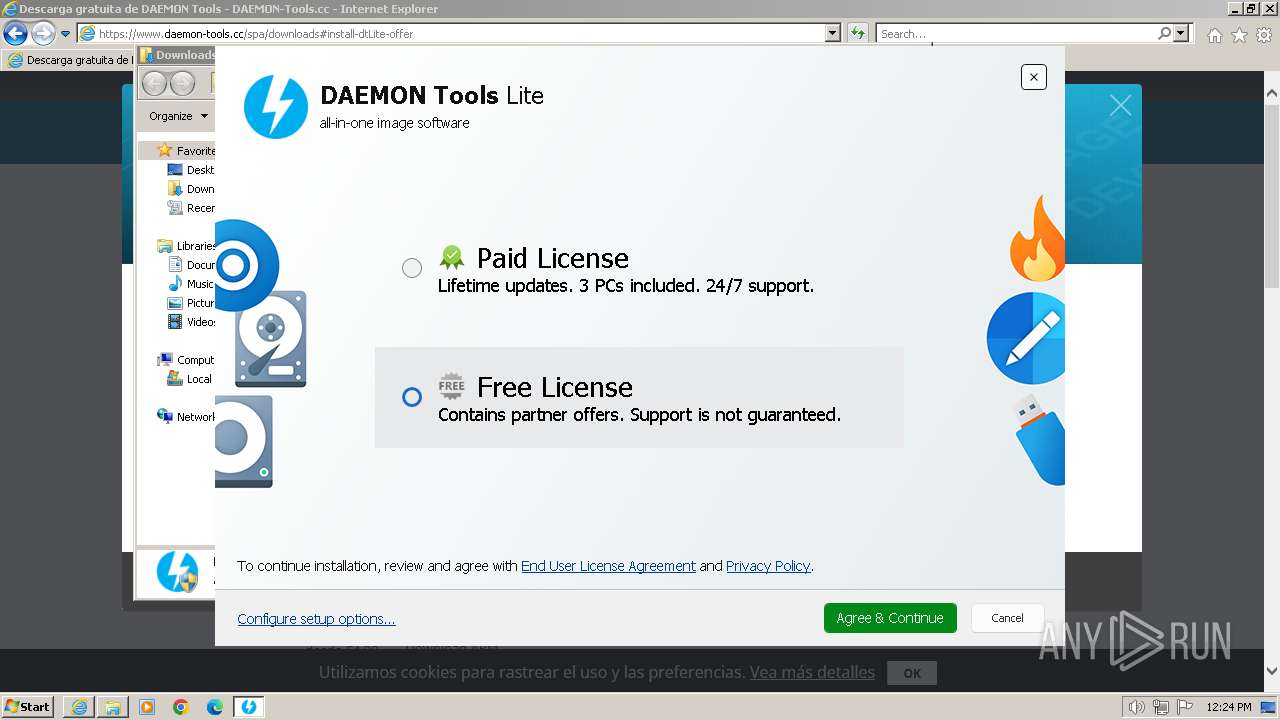
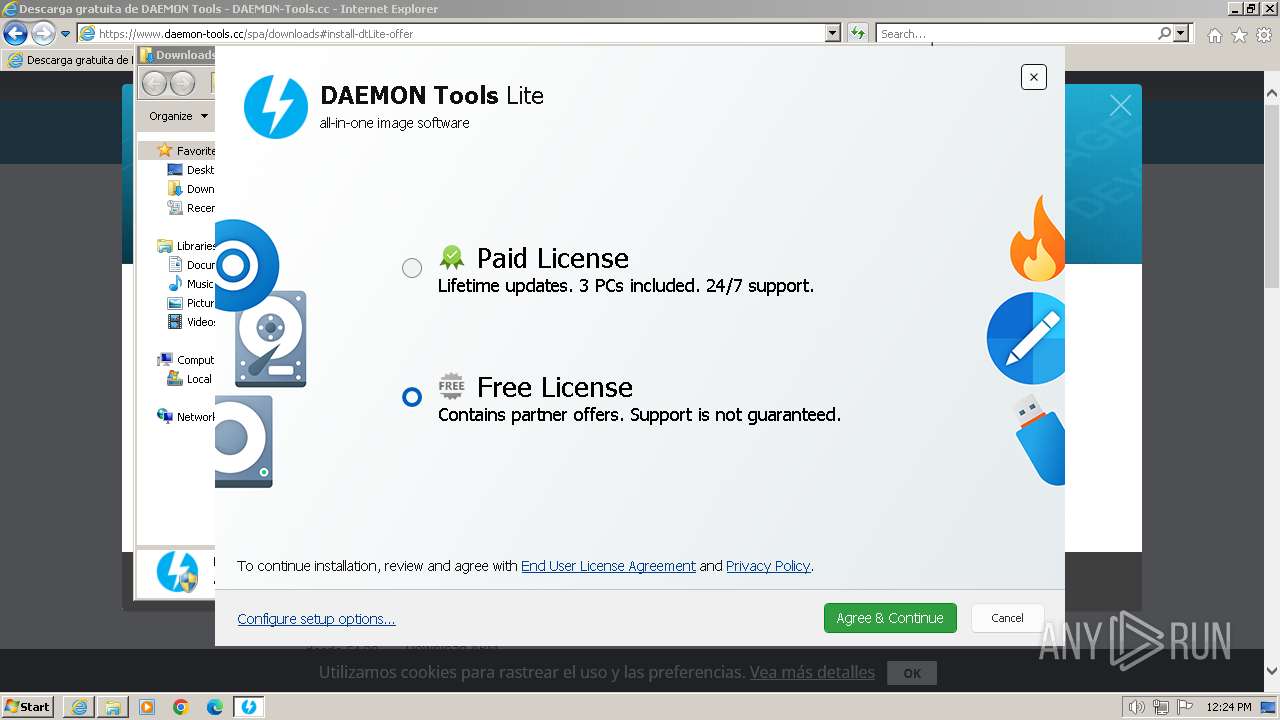
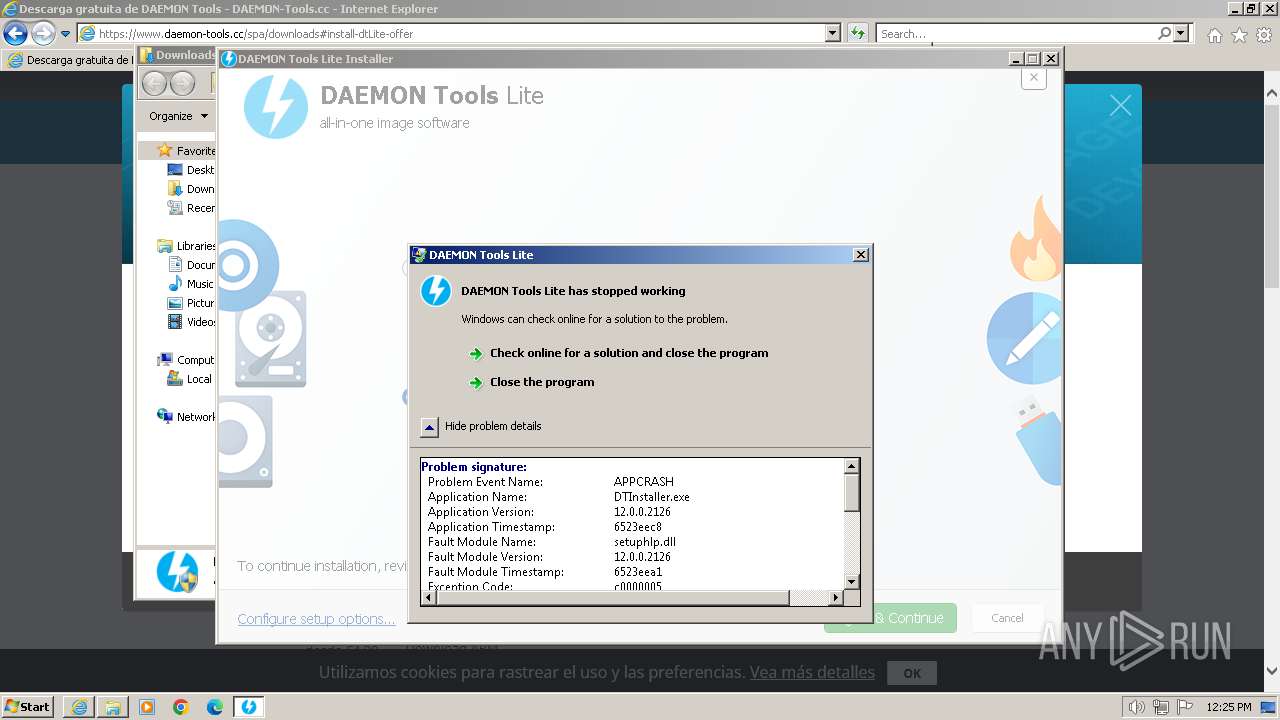
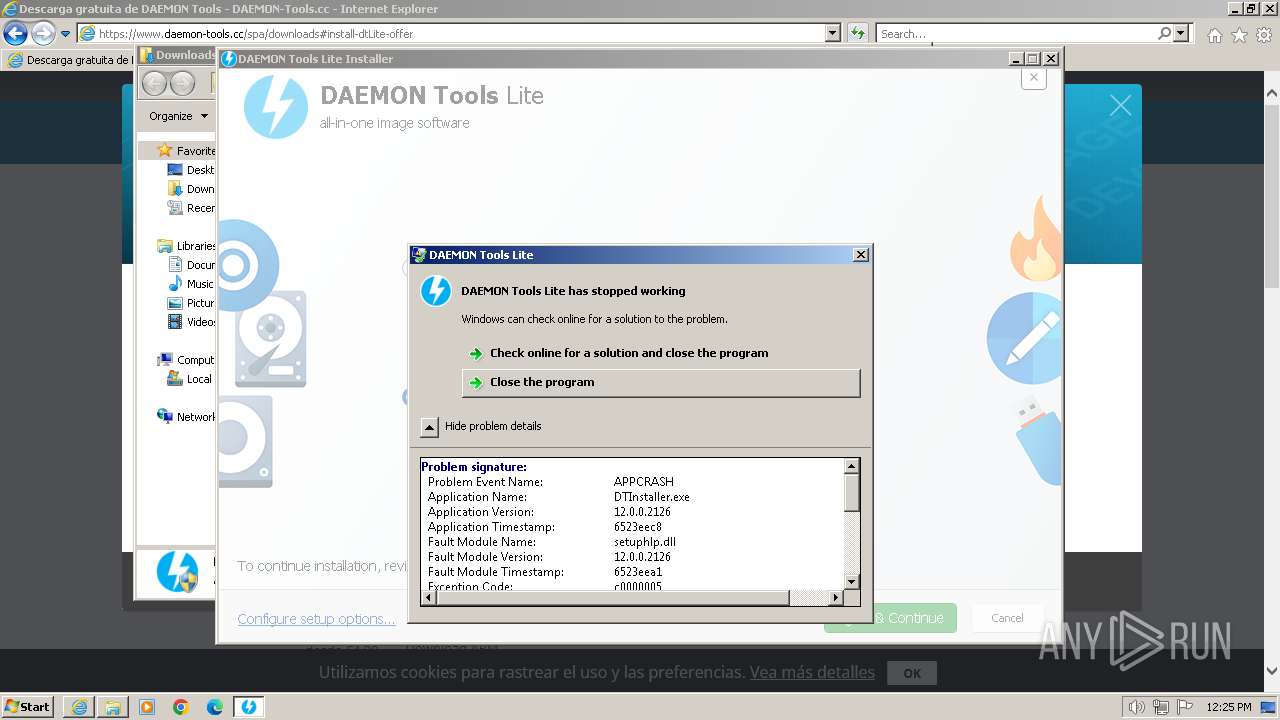
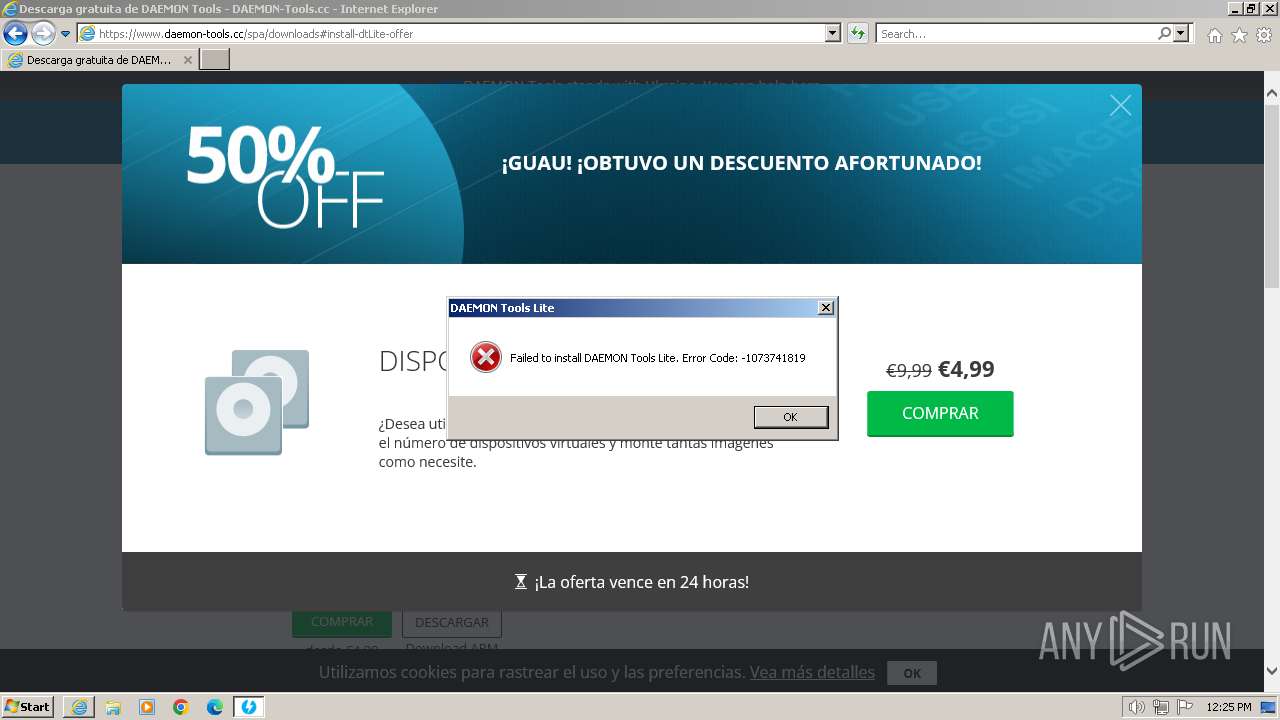
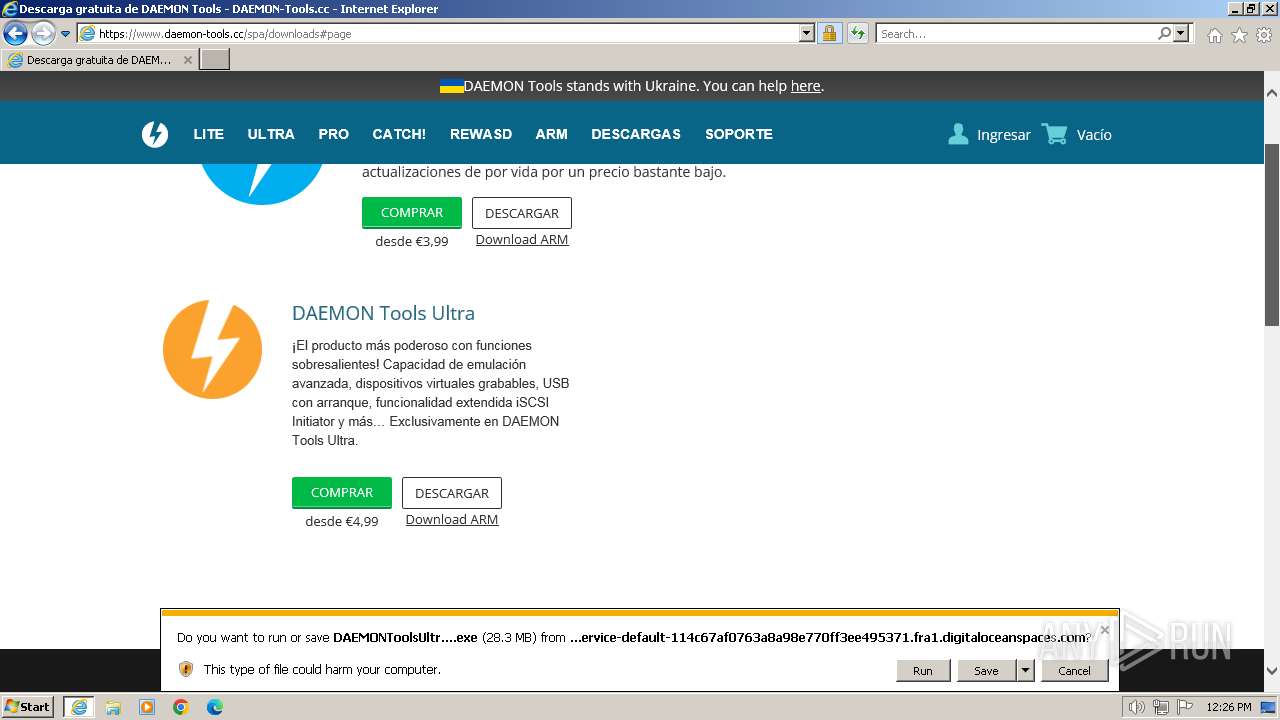
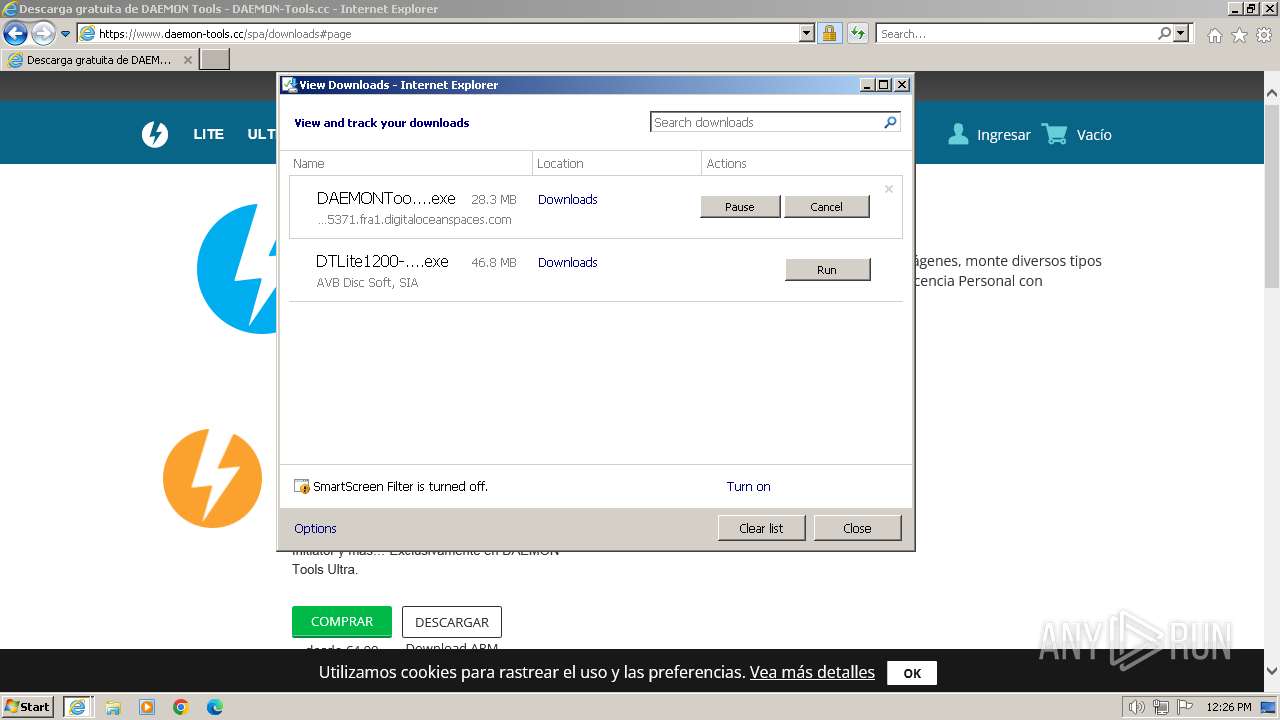
Drops the executable file immediately after the start
- DTInstaller.exe (PID: 712)
SUSPICIOUS
Reads the Internet Settings
- DTLite1200-2126.exe (PID: 492)
- DTInstaller.exe (PID: 712)
Reads security settings of Internet Explorer
- DTLite1200-2126.exe (PID: 492)
- DTInstaller.exe (PID: 712)
Drops 7-zip archiver for unpacking
- DTInstaller.exe (PID: 712)
Executable content was dropped or overwritten
- DTInstaller.exe (PID: 712)
Adds/modifies Windows certificates
- DTInstaller.exe (PID: 712)
Reads settings of System Certificates
- DTInstaller.exe (PID: 712)
Checks Windows Trust Settings
- DTInstaller.exe (PID: 712)
INFO
Application launched itself
- iexplore.exe (PID: 3672)
Manual execution by a user
- DTLite1200-2126.exe (PID: 1900)
- DTLite1200-2126.exe (PID: 492)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3672)
Checks supported languages
- DTLite1200-2126.exe (PID: 492)
- DTInstaller.exe (PID: 712)
Drops the executable file immediately after the start
- iexplore.exe (PID: 3692)
Reads the computer name
- DTLite1200-2126.exe (PID: 492)
- DTInstaller.exe (PID: 712)
Reads Environment values
- DTLite1200-2126.exe (PID: 492)
- DTInstaller.exe (PID: 712)
Reads the machine GUID from the registry
- DTInstaller.exe (PID: 712)
- DTLite1200-2126.exe (PID: 492)
Create files in a temporary directory
- DTLite1200-2126.exe (PID: 492)
- DTInstaller.exe (PID: 712)
Creates files in the program directory
- DTInstaller.exe (PID: 712)
Reads the software policy settings
- DTInstaller.exe (PID: 712)
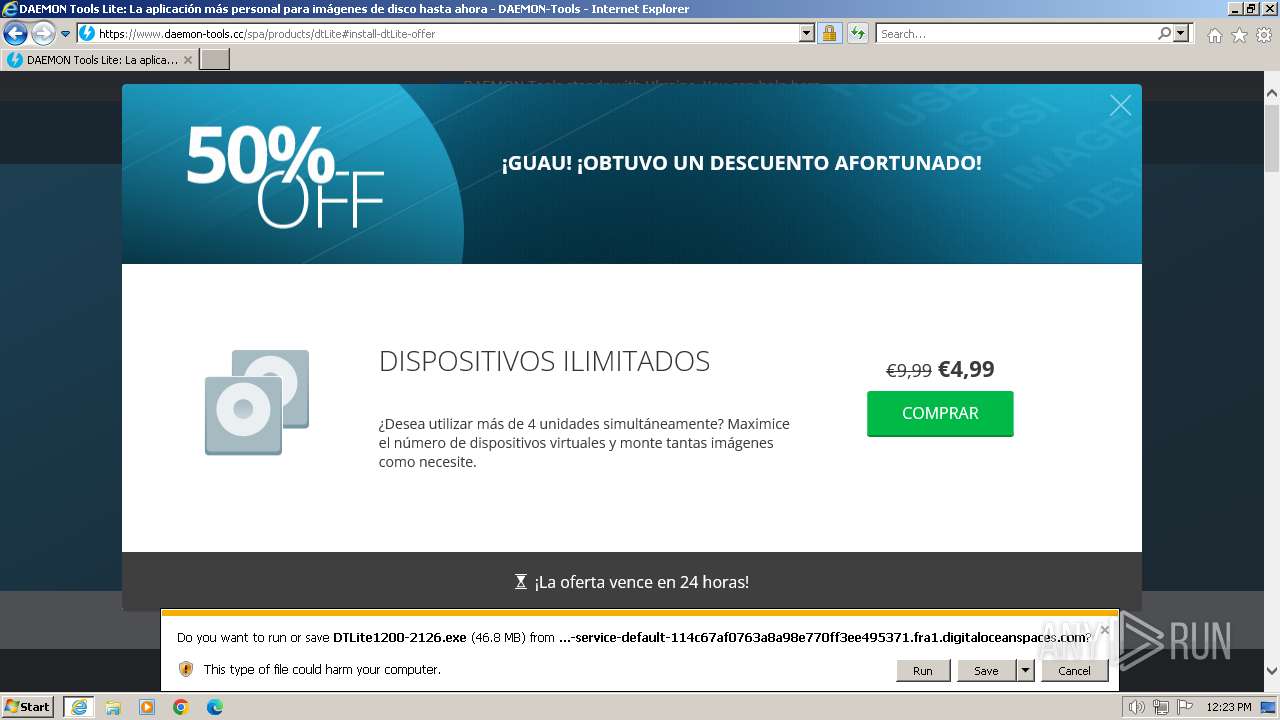
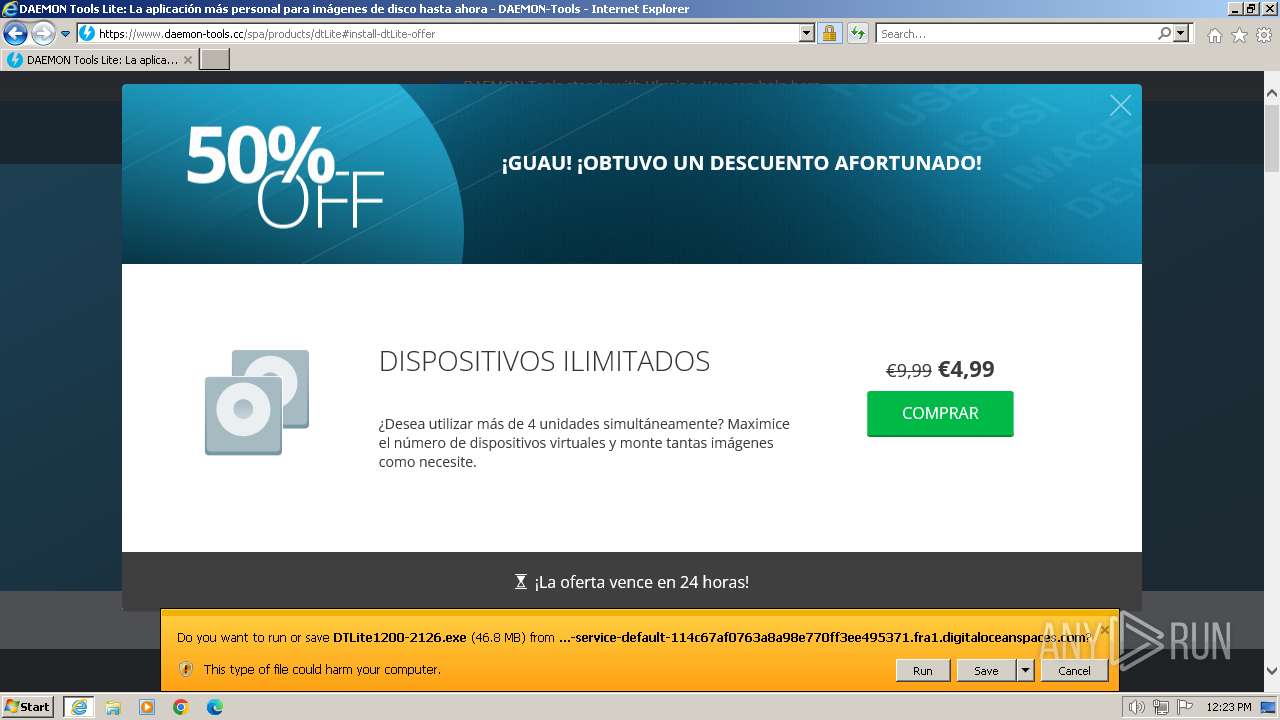
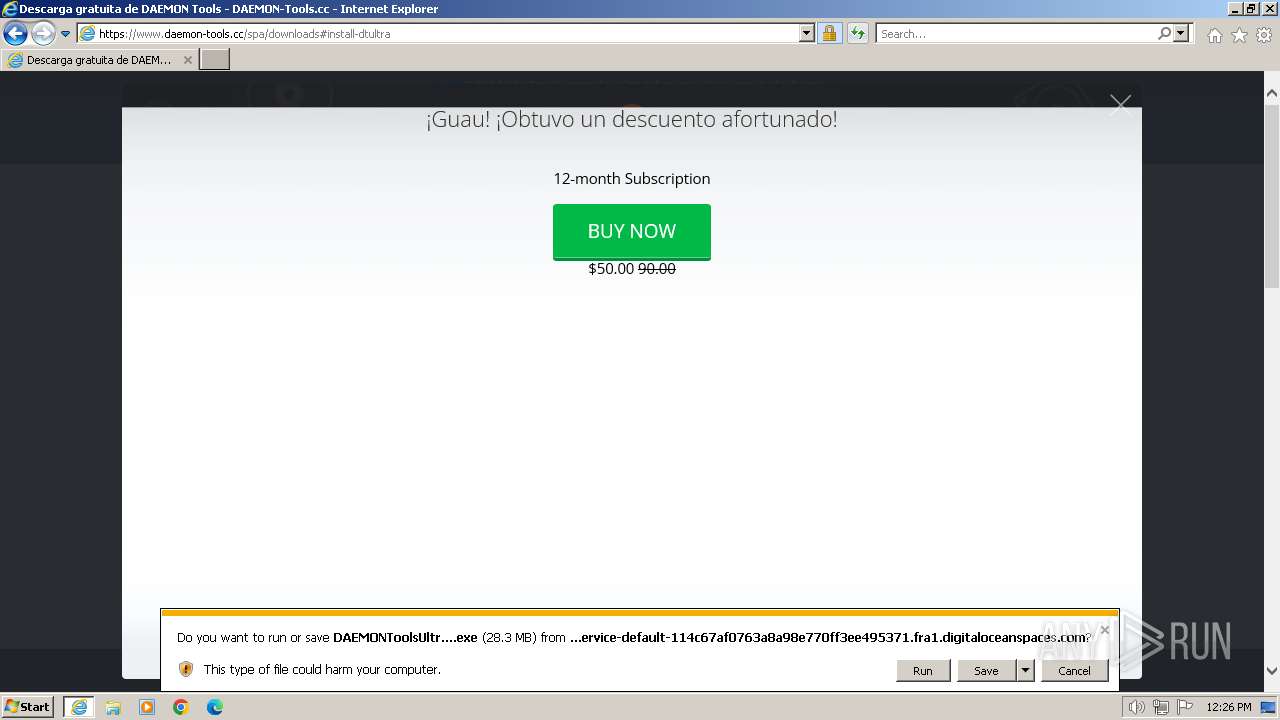
The process uses the downloaded file
- iexplore.exe (PID: 3672)
Executable content was dropped or overwritten
- iexplore.exe (PID: 3692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
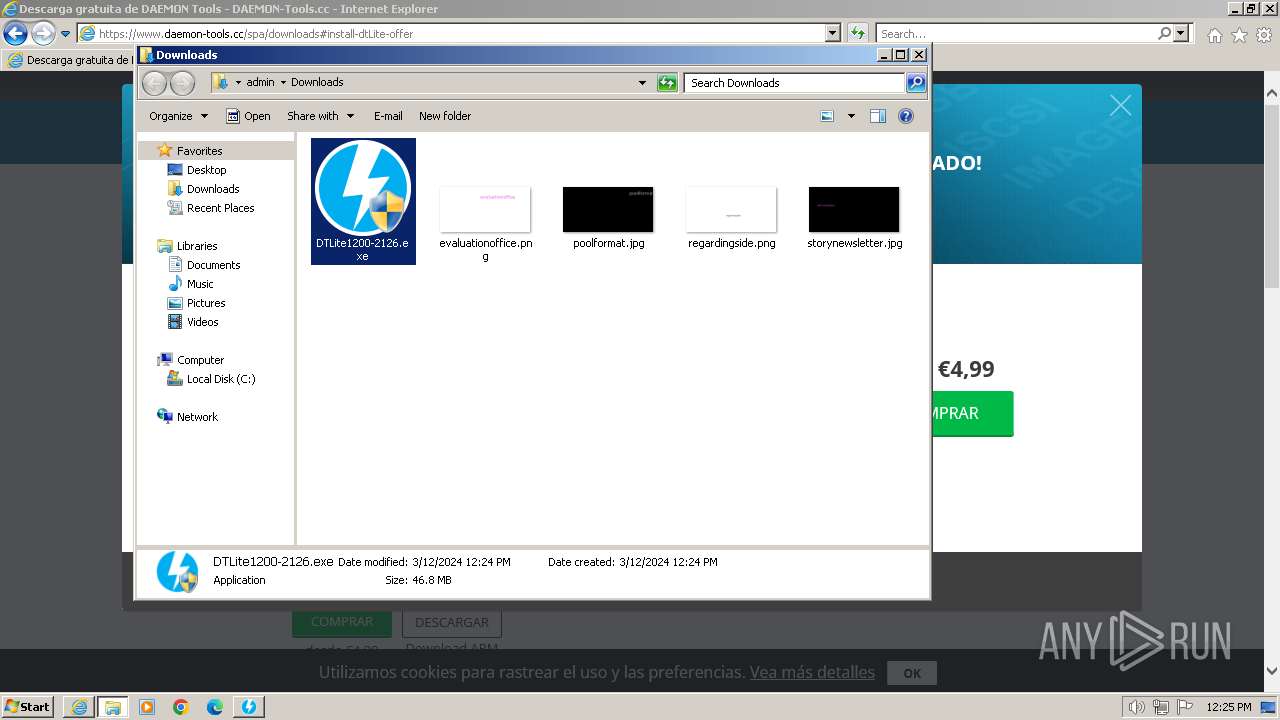
| 492 | "C:\Users\admin\Downloads\DTLite1200-2126.exe" | C:\Users\admin\Downloads\DTLite1200-2126.exe | explorer.exe | ||||||||||||
User: admin Company: Disc Soft FZE LLC Integrity Level: HIGH Description: DAEMON Tools Lite Exit code: 0 Version: 12.0.0.2126 Modules
| |||||||||||||||
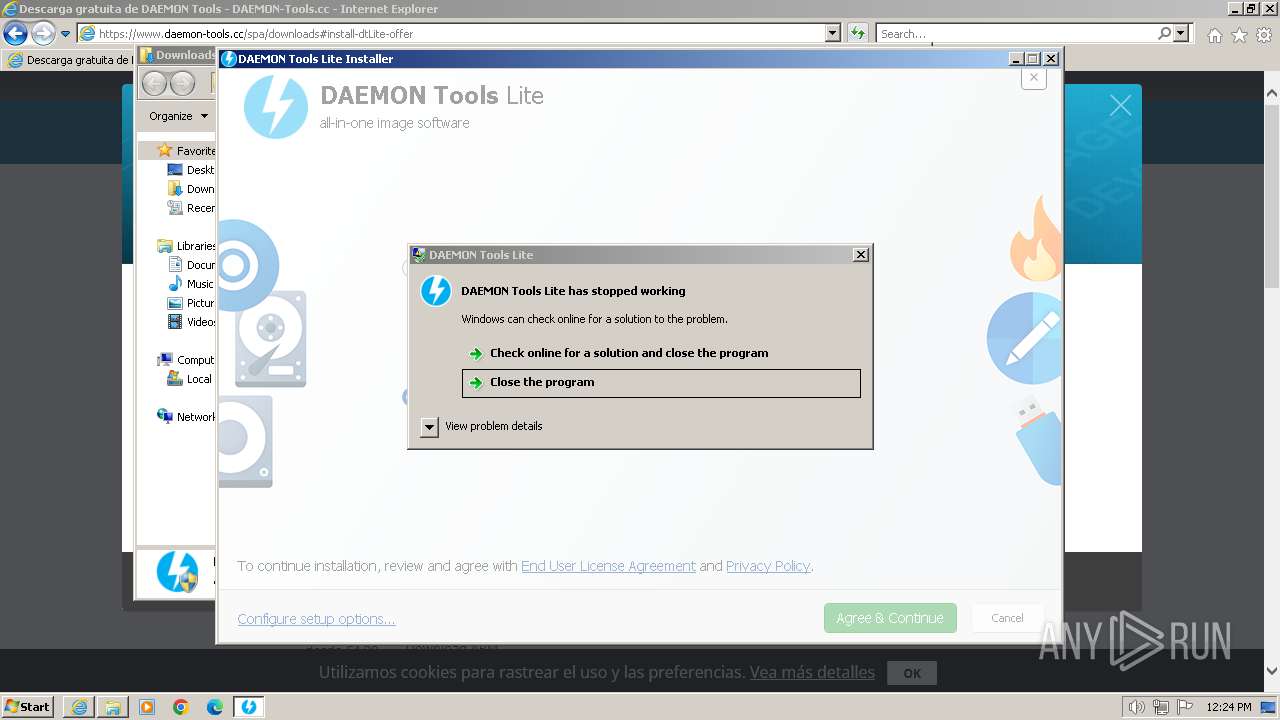
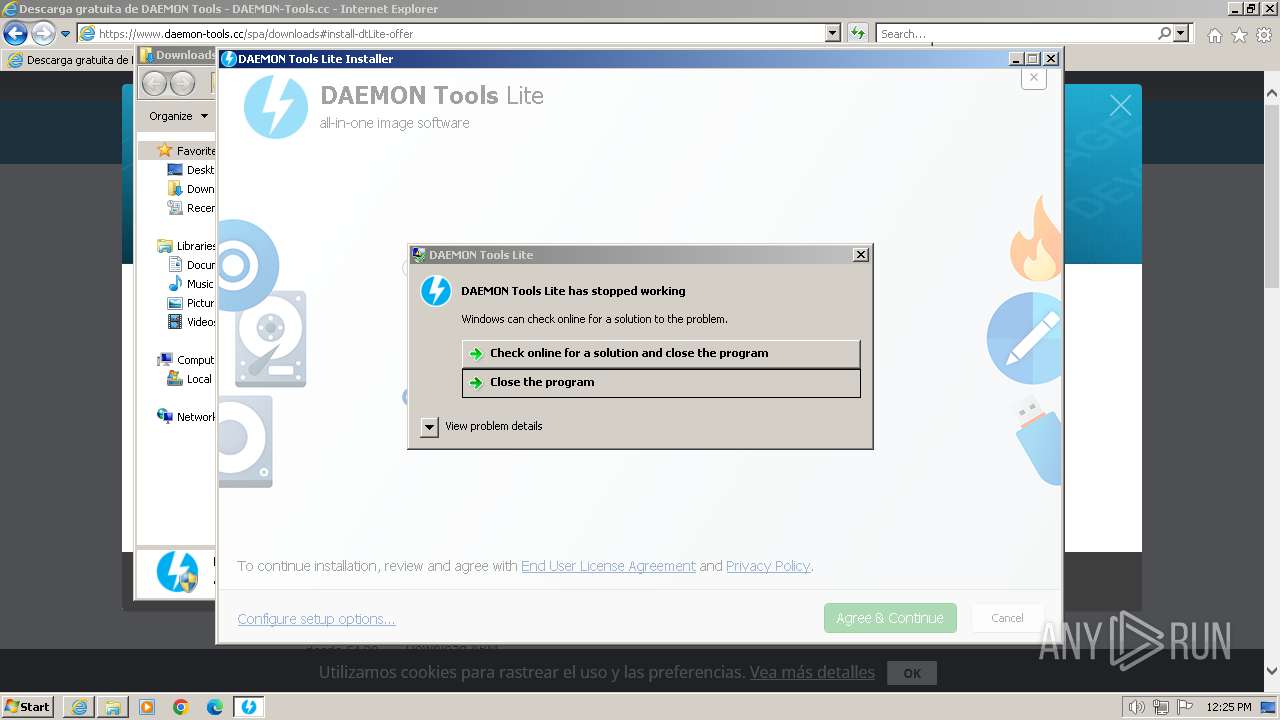
| 712 | "C:\Users\admin\AppData\Local\Temp\DT_INSTALL_TMP\DTInstaller.exe" | C:\Users\admin\AppData\Local\Temp\DT_INSTALL_TMP\DTInstaller.exe | DTLite1200-2126.exe | ||||||||||||
User: admin Company: Disc Soft FZE LLC Integrity Level: HIGH Description: DAEMON Tools Lite Exit code: 3221225477 Version: 12.0.0.2126 Modules
| |||||||||||||||
| 1900 | "C:\Users\admin\Downloads\DTLite1200-2126.exe" | C:\Users\admin\Downloads\DTLite1200-2126.exe | — | explorer.exe | |||||||||||
User: admin Company: Disc Soft FZE LLC Integrity Level: MEDIUM Description: DAEMON Tools Lite Exit code: 3221226540 Version: 12.0.0.2126 Modules
| |||||||||||||||
| 3672 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.daemon-tools.cc/spa/products/dtLite" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3692 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3672 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
48 506
Read events
48 247
Write events
189
Delete events
70
Modification events
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 375541520 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31093880 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 675704020 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31093880 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3672) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
30
Suspicious files
40
Text files
256
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\dtlite-windows10download[1].png | image | |
MD5:2BFBF4806A59359BFD88A83B11B60019 | SHA256:897BE009B2290AB43DF3750978BDBA2626D2DE9D75FE19DB7CF63202099678A8 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:7475AF52C82C91BF03586C97FCF4EB00 | SHA256:F82267A1991A68E88436AFA45CD6F2D0CE636DB5D41175361638BBAA897E7A28 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:8567DE6CD6F739BBEA4DDDECB377F371 | SHA256:65D2D7D6AF9420760ED2BD884ED593CB66A8EA749F6A497AFBF39E69B1BBC511 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\download3k[1].png | image | |
MD5:1EBA794679D0B10C5B3E86448D20DC78 | SHA256:C8EDD9C1F5F79034CB6DA69E6AEAA0314BB877CE39A5D8A821E280F1C30FC24C | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1QNN6R31.txt | text | |
MD5:C309E40F22D8C3781A5C28F43498085B | SHA256:1194C98504B16AE12F1C8862A9DAC016DA7EAEED63328712BEE1DC3E358A9001 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\WZ2XMTUW.txt | text | |
MD5:1EEA678D7597053673033FDE3D514F52 | SHA256:F87CAFEC3D794A35C1654D50300B7A03A91C91B51F7F7E228227449245243E9D | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\softmany[1].png | image | |
MD5:5D404093BC19F98011F84D4FC7F94F25 | SHA256:41B5980AFBC2801E99DEBC5F82B29A2DCFDE2B2B04DF2B867F93D25F35EE2EB7 | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\softpedia[1].png | image | |
MD5:D67B2195DEEC13E18147607DACB8EB4F | SHA256:06F21158FBAD3CDD814F577E23390850C8FF029E1B355794821D43CF3AEBD09A | |||
| 3692 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\dtlite-updatestar[1].png | image | |
MD5:4AC1915869F5B66CFF3C91C67F54815D | SHA256:5735EC9F709EBA7E8E8B13527BFE22045D3EBF91CEC0CED032C81CBF58B5ECB0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
143
DNS requests
47
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3692 | iexplore.exe | GET | 304 | 2.19.126.137:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ca0b0a63504a6d7c | unknown | — | — | unknown |
3692 | iexplore.exe | GET | 304 | 2.19.126.163:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0302b3af7cdfdbed | unknown | — | — | unknown |
3692 | iexplore.exe | GET | 200 | 2.19.105.18:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
3692 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
3692 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | unknown | binary | 1.47 Kb | unknown |
3692 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
3692 | iexplore.exe | GET | 200 | 2.16.202.115:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQQvFNk9WD2uKNQisXT4mRmDA%3D%3D | unknown | binary | 503 b | unknown |
3692 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGP1wnlKU4hqCh2NuNoGiQQ%3D | unknown | binary | 471 b | unknown |
3692 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEH6FWuT3fbHwEAPEHSB2q%2B0%3D | unknown | binary | 471 b | unknown |
3692 | iexplore.exe | GET | 200 | 216.58.206.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEEmjnEcAcBIRCdkf7NhadAI%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3692 | iexplore.exe | 161.35.70.0:443 | www.daemon-tools.cc | DIGITALOCEAN-ASN | DE | unknown |
3692 | iexplore.exe | 2.19.126.137:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3692 | iexplore.exe | 2.19.126.163:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
3692 | iexplore.exe | 2.19.105.18:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
3692 | iexplore.exe | 104.18.215.59:443 | cdn.onesignal.com | CLOUDFLARENET | — | unknown |
3692 | iexplore.exe | 216.58.212.131:443 | www.recaptcha.net | GOOGLE | US | whitelisted |
3692 | iexplore.exe | 161.35.212.100:443 | img.disc-soft.com | DIGITALOCEAN-ASN | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.daemon-tools.cc |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
cdn.daemon-tools.cc |
| unknown |
cdn.onesignal.com |
| whitelisted |
www.recaptcha.net |
| whitelisted |
img.disc-soft.com |
| unknown |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r3.o.lencr.org |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |