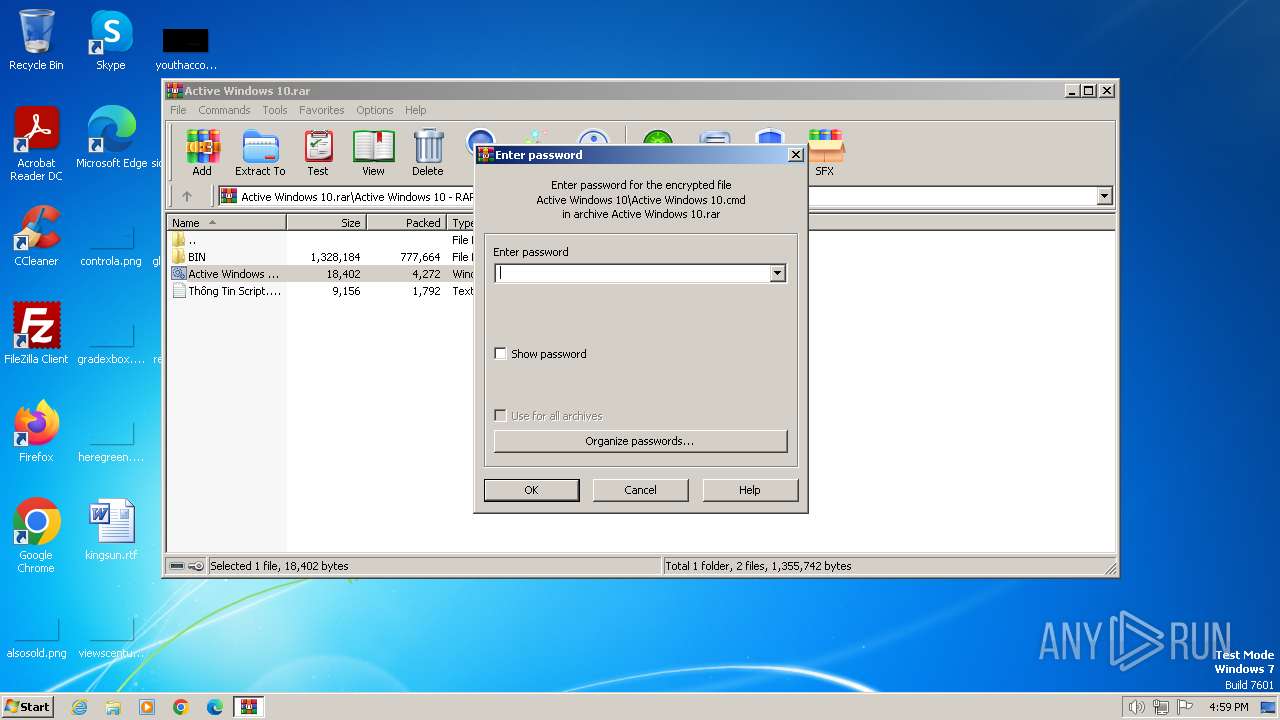
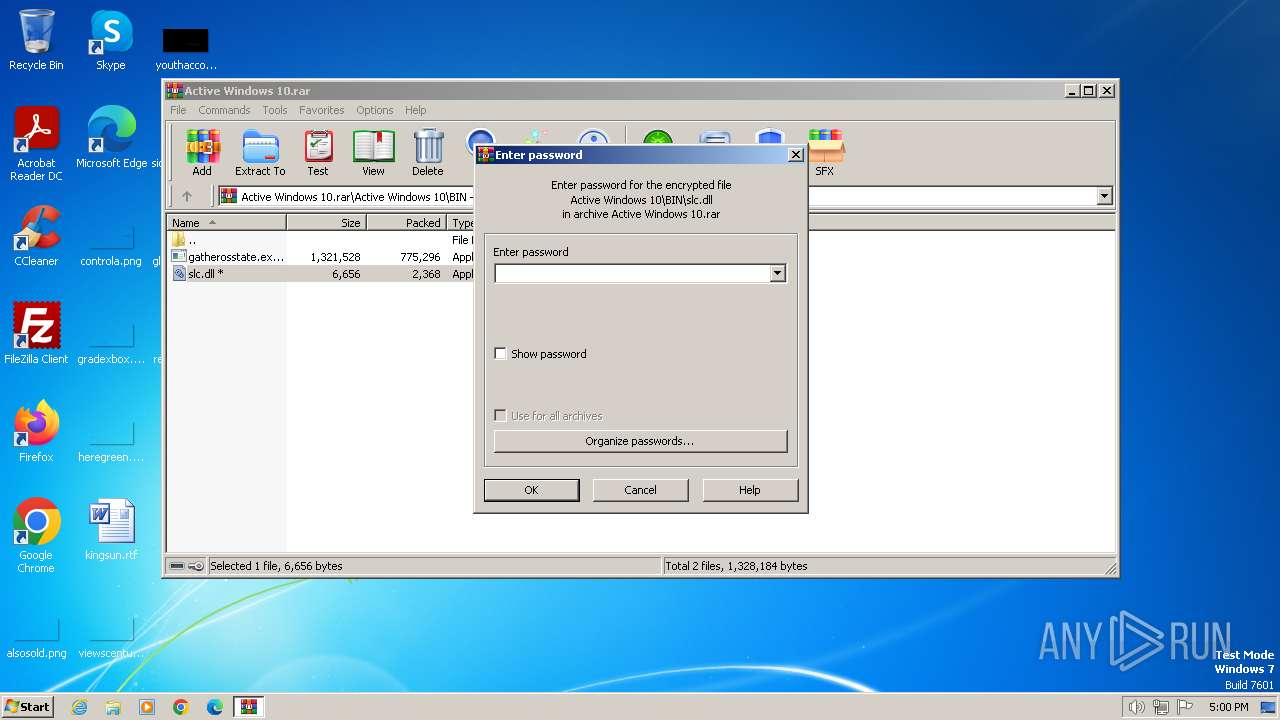
| File name: | Active Windows 10.rar |
| Full analysis: | https://app.any.run/tasks/8e5a88c5-43ed-45df-b8b4-1cf372f3e66a |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2023, 16:58:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 29E9708706CF5609C7FAA8820707C17B |
| SHA1: | 874D29B6E9BF554DC0BA849D9EB0D8DEC9BC4A92 |
| SHA256: | AA3D5C5BE1392738525151CA25B18AE94A0C2FDBAE0593DA4933E570FF7D9D7F |
| SSDEEP: | 24576:5TQSIFRx82EDTH8aAwEzEQAS9thmScMEK8sfGZ8szviPFkjAhq6LOzwZTzk1w++e:5TQScRx82EDTH8aAwEzEQAythmScMEK+ |
MALICIOUS
No malicious indicators.SUSPICIOUS
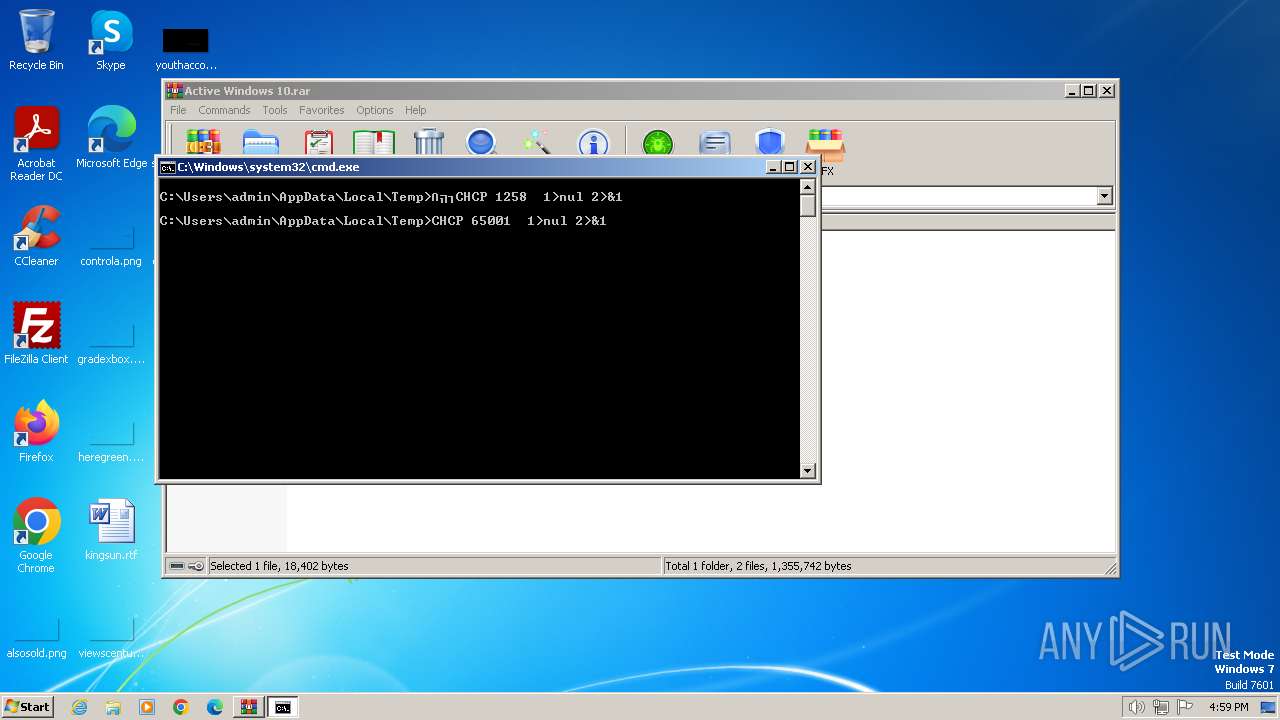
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2040)
- cmd.exe (PID: 2256)
- wscript.exe (PID: 1344)
- cmd.exe (PID: 1796)
Application launched itself
- cmd.exe (PID: 2256)
- cmd.exe (PID: 1796)
Starts application with an unusual extension
- cmd.exe (PID: 2256)
- cmd.exe (PID: 1796)
Executing commands from ".cmd" file
- cmd.exe (PID: 2256)
- WinRAR.exe (PID: 2040)
- wscript.exe (PID: 1344)
Reads the Internet Settings
- cmd.exe (PID: 2256)
- wscript.exe (PID: 1344)
- WMIC.exe (PID: 2308)
- WMIC.exe (PID: 2640)
- WMIC.exe (PID: 996)
- WMIC.exe (PID: 2568)
- WMIC.exe (PID: 2240)
- WMIC.exe (PID: 2316)
The process executes VB scripts
- cmd.exe (PID: 2256)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1344)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 1636)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 2588)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2628)
- cmd.exe (PID: 1556)
Process drops legitimate windows executable
- WinRAR.exe (PID: 2040)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 1796)
INFO
Checks supported languages
- chcp.com (PID: 2016)
- chcp.com (PID: 1740)
- gatherosstate.exe (PID: 2900)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2040)
Reads the computer name
- gatherosstate.exe (PID: 2900)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
63
Monitored processes
24
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 492 | fsutil dirty query C: | C:\Windows\System32\fsutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: fsutil.exe Exit code: 1 Version: 6.1.7601.17577 (win7sp1_gdr.110310-1504) Modules
| |||||||||||||||
| 532 | cmd /u /c echo Set UAC = CreateObject("Shell.Application") : UAC.ShellExecute "cmd.exe", "/k cd ""C:\Users\admin\AppData\Local\Temp\RAR$DI~1.342\"" && ""C:\Users\admin\AppData\Local\Temp\RAR$DI~1.342\ACTIVE~1.CMD""", "", "runas", 1 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 996 | wmic path SoftwareLicensingProduct where (LicenseStatus='1' and GracePeriodRemaining='0' and PartialProductKey is not NULL) get Name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1344 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\getadmin.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1388 | findstr /i "Windows" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1544 | fsutil dirty query C: | C:\Windows\System32\fsutil.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: fsutil.exe Exit code: 0 Version: 6.1.7601.17577 (win7sp1_gdr.110310-1504) Modules
| |||||||||||||||
| 1556 | C:\Windows\system32\cmd.exe /c "wmic Path Win32_OperatingSystem Get Version /format:LIST" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1636 | C:\Windows\system32\cmd.exe /c "WMIC PATH SoftwareLicensingProduct WHERE (Name LIKE 'Windows%' AND PartialProductKey is not NULL) GET LicenseFamily /VALUE" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1740 | CHCP 65001 | C:\Windows\System32\chcp.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Change CodePage Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1796 | "C:\Windows\System32\cmd.exe" /k cd "C:\Users\admin\AppData\Local\Temp\RAR$DI~1.342\" && "C:\Users\admin\AppData\Local\Temp\RAR$DI~1.342\ACTIVE~1.CMD" | C:\Windows\System32\cmd.exe | wscript.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 587
Read events
2 539
Write events
48
Delete events
0
Modification events
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2040) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
3
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2040.34264\Active Windows 10.cmd | text | |
MD5:4B644739EC82400EE90CD58DC8042E97 | SHA256:20D39EA94E66098DEEF7F163AFB9B01F9D926B6216A085A60EFFBA3B12568263 | |||
| 2256 | cmd.exe | C:\Users\admin\AppData\Local\Temp\getadmin.vbs | binary | |
MD5:64A9B3DCDC210F2F09FF632C4F443612 | SHA256:F8D8F7957DC4D57959D4914C67C43034E96D7B9B34B6DB997F9400276D17ADAB | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2040.39494\Active Windows 10\Thông Tin Script.txt | text | |
MD5:303A845E886BCC3596EFDC2407E7DF01 | SHA256:684470FC9A0E500A56E9A3EF08B971EE8E6FB1F3A9E6FE0BC5D5D960F7CA796E | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2040.39494\Active Windows 10\Active Windows 10.cmd | text | |
MD5:4B644739EC82400EE90CD58DC8042E97 | SHA256:20D39EA94E66098DEEF7F163AFB9B01F9D926B6216A085A60EFFBA3B12568263 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2040.38230\slc.dll | executable | |
MD5:E2840606372AB67B7107CE757D506C28 | SHA256:37E20A504ADE965184D92ED5CA415CDE899090A6A20EA3ABF8C85FF9648B66F4 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2040.39494\Active Windows 10\BIN\slc.dll | executable | |
MD5:E2840606372AB67B7107CE757D506C28 | SHA256:37E20A504ADE965184D92ED5CA415CDE899090A6A20EA3ABF8C85FF9648B66F4 | |||
| 2040 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2040.39494\Active Windows 10\BIN\gatherosstate.exe | executable | |
MD5:B13BC5B62F54607C334A6464D9B85CC8 | SHA256:51791625054B01802FD5AAA6C4A929827B369DFEF7B2891B5F55E0FA61AF0C7D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |