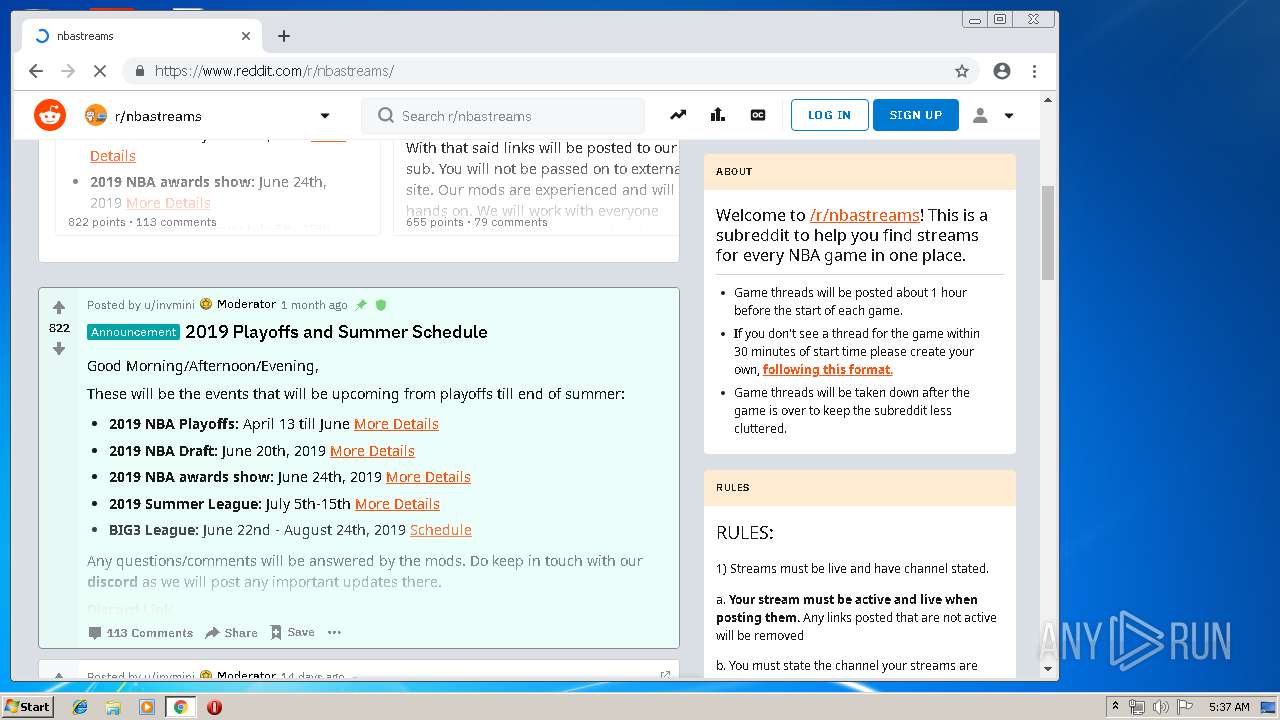
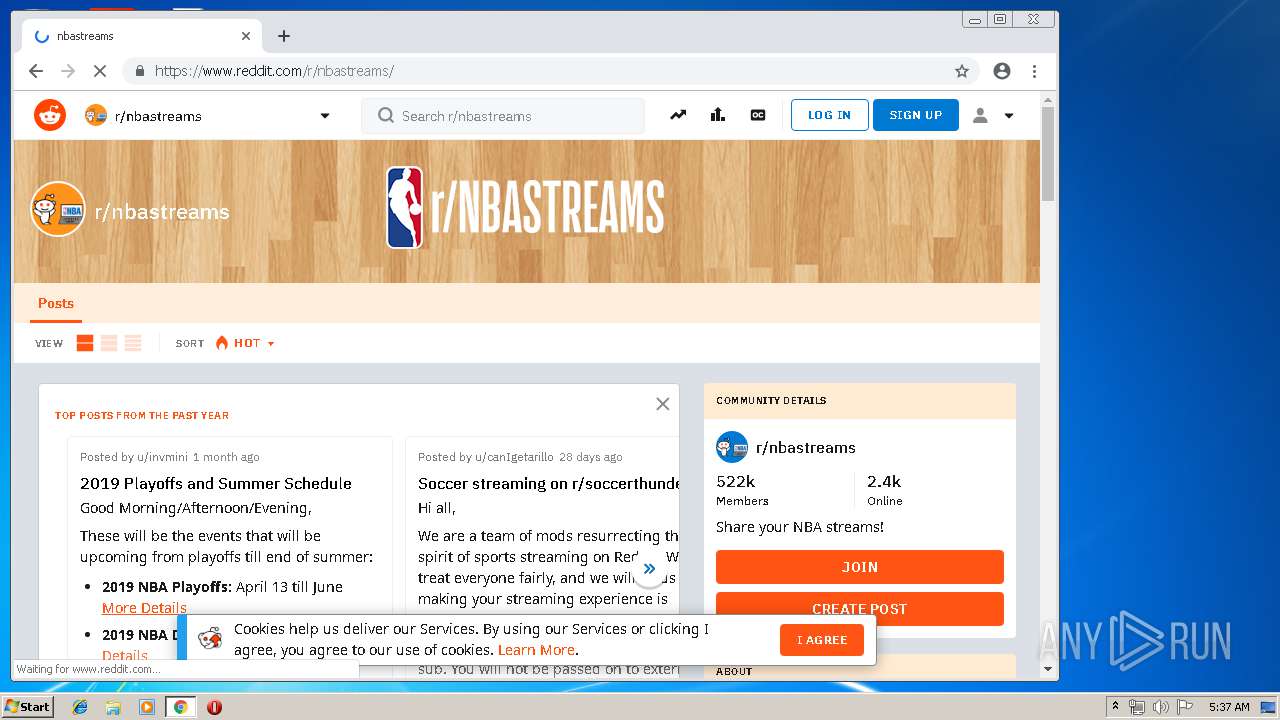
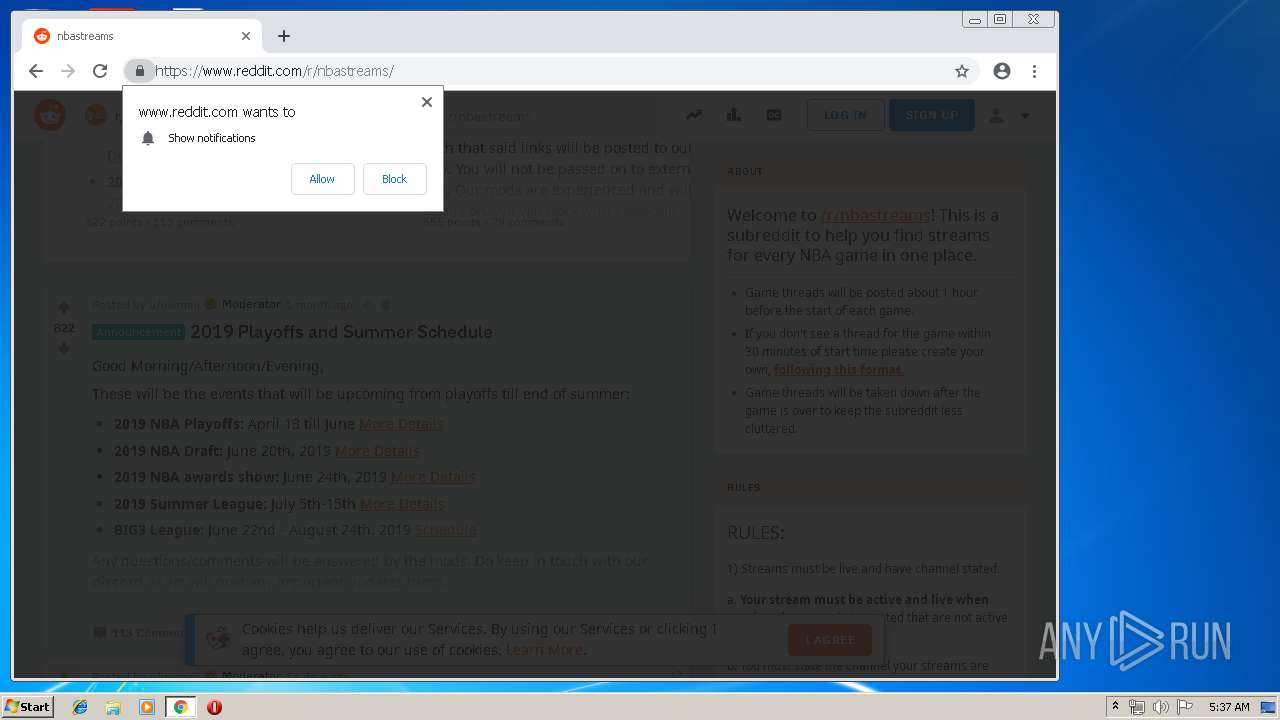
| URL: | http://google.com |
| Full analysis: | https://app.any.run/tasks/0b93dda8-7d28-4fac-8f0b-b37a2102ff37 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 04:36:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C7B920F57E553DF2BB68272F61570210 |
| SHA1: | 234988566C9A0A9CF952CEC82B143BF9C207AC16 |
| SHA256: | AA2239C17609B21EBA034C564AF878F3EEC8CE83ED0F2768597D2BC2FD4E4DA5 |
| SSDEEP: | 3:N1KZK3uK:C03uK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 836)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 908)
- iexplore.exe (PID: 2836)
Changes internet zones settings
- iexplore.exe (PID: 908)
Reads internet explorer settings
- iexplore.exe (PID: 2836)
Reads settings of System Certificates
- chrome.exe (PID: 836)
Application launched itself
- chrome.exe (PID: 836)
Creates files in the user directory
- iexplore.exe (PID: 2836)
Changes settings of System certificates
- chrome.exe (PID: 836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
69
Monitored processes
36
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 908 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,3263014147117543043,17238796621676962347,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=10102156813839235811 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10102156813839235811 --renderer-client-id=30 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=6160 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1260 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,3263014147117543043,17238796621676962347,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=15059530705415268387 --mojo-platform-channel-handle=6004 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1352 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,3263014147117543043,17238796621676962347,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=6646748266709645056 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=6646748266709645056 --renderer-client-id=29 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=6492 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1492 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,3263014147117543043,17238796621676962347,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12067319825700231822 --mojo-platform-channel-handle=4872 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1556 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,3263014147117543043,17238796621676962347,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=15125467313632978763 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15125467313632978763 --renderer-client-id=21 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3348 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2056 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=960,3263014147117543043,17238796621676962347,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=16370566046459954870 --mojo-platform-channel-handle=3292 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2060 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,3263014147117543043,17238796621676962347,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=4886003972134795183 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4886003972134795183 --renderer-client-id=24 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4976 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 2300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=960,3263014147117543043,17238796621676962347,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=4708743555519560215 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4708743555519560215 --renderer-client-id=23 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=4952 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
1 007
Read events
843
Write events
156
Delete events
8
Modification events
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {06320B97-76CB-11E9-A370-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307050003000F000400240026009700 | |||
Executable files
0
Suspicious files
438
Text files
262
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 908 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 908 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@google[2].txt | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\V964VV2X\google_com[1].txt | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 908 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF5F3E62D4F08D6CBD.TMP | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | smt | |
MD5:— | SHA256:— | |||
| 908 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFD4087177A13274FE.TMP | — | |
MD5:— | SHA256:— | |||
| 2836 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\V964VV2X\google_com[1].htm | html | |
MD5:— | SHA256:— | |||
| 908 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA17AD24466934C3F.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
183
DNS requests
142
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
836 | chrome.exe | GET | 302 | 151.101.0.166:80 | http://bh.contextweb.com/bh/rtset?do=add&pid=534889&ev=xib5nfoositcw&rurl=http%3A%2F%2Fdpm.demdex.net%2Fibs%3Adpid%3D640%26dpuuid%3Dxib5nfoositcw | US | — | — | whitelisted |
836 | chrome.exe | GET | 200 | 8.248.121.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 56.1 Kb | whitelisted |
836 | chrome.exe | GET | 200 | 185.148.72.100:80 | http://www.nkjesenice.si/ | SI | html | 1.14 Kb | unknown |
836 | chrome.exe | GET | 302 | 216.58.205.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvMjJlQUFXRC12Ny1ldUFnMXF3SDlXZDlFZw/7319.128.0.1_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 502 b | whitelisted |
836 | chrome.exe | GET | 302 | 31.186.247.145:80 | http://nan.netmng.com/pixel/redirect.php?url=http%3A%2F%2Fbh.contextweb.com%2Fbh%2Frtset%3Fdo%3Dadd%26pid%3D534889%26ev%3DNM_UUID_MACRO%26rurl%3Dhttp%253A%252F%252Fdpm.demdex.net%252Fibs%253Adpid%253D640%2526dpuuid%253DNM_UUID_MACRO | GB | — | — | whitelisted |
2836 | iexplore.exe | GET | 302 | 172.217.21.228:80 | http://www.google.com/ | US | html | 231 b | malicious |
836 | chrome.exe | GET | 200 | 185.148.72.100:80 | http://www.nkjesenice.si/ | SI | html | 1.14 Kb | unknown |
2836 | iexplore.exe | GET | 301 | 172.217.22.110:80 | http://google.com/ | US | html | 219 b | whitelisted |
836 | chrome.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAKXB1YM1Knrv%2BJy8eCW2II%3D | US | der | 471 b | whitelisted |
836 | chrome.exe | GET | 200 | 13.35.254.34:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2836 | iexplore.exe | 172.217.22.110:80 | — | Google Inc. | US | whitelisted |
836 | chrome.exe | 172.217.18.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
2836 | iexplore.exe | 172.217.21.228:80 | www.google.com | Google Inc. | US | whitelisted |
2836 | iexplore.exe | 172.217.21.228:443 | www.google.com | Google Inc. | US | whitelisted |
836 | chrome.exe | 172.217.16.195:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
836 | chrome.exe | 216.58.210.3:443 | www.google.com.ua | Google Inc. | US | whitelisted |
836 | chrome.exe | 216.58.206.14:443 | clients1.google.com | Google Inc. | US | whitelisted |
836 | chrome.exe | 172.217.22.35:443 | www.gstatic.com | Google Inc. | US | whitelisted |
836 | chrome.exe | 172.217.18.110:443 | consent.google.com | Google Inc. | US | whitelisted |
836 | chrome.exe | 216.58.210.14:443 | apis.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.google.com |
| malicious |
clientservices.googleapis.com |
| whitelisted |
www.google.com.ua |
| whitelisted |
accounts.google.com |
| shared |
clients1.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
consent.google.com |
| shared |