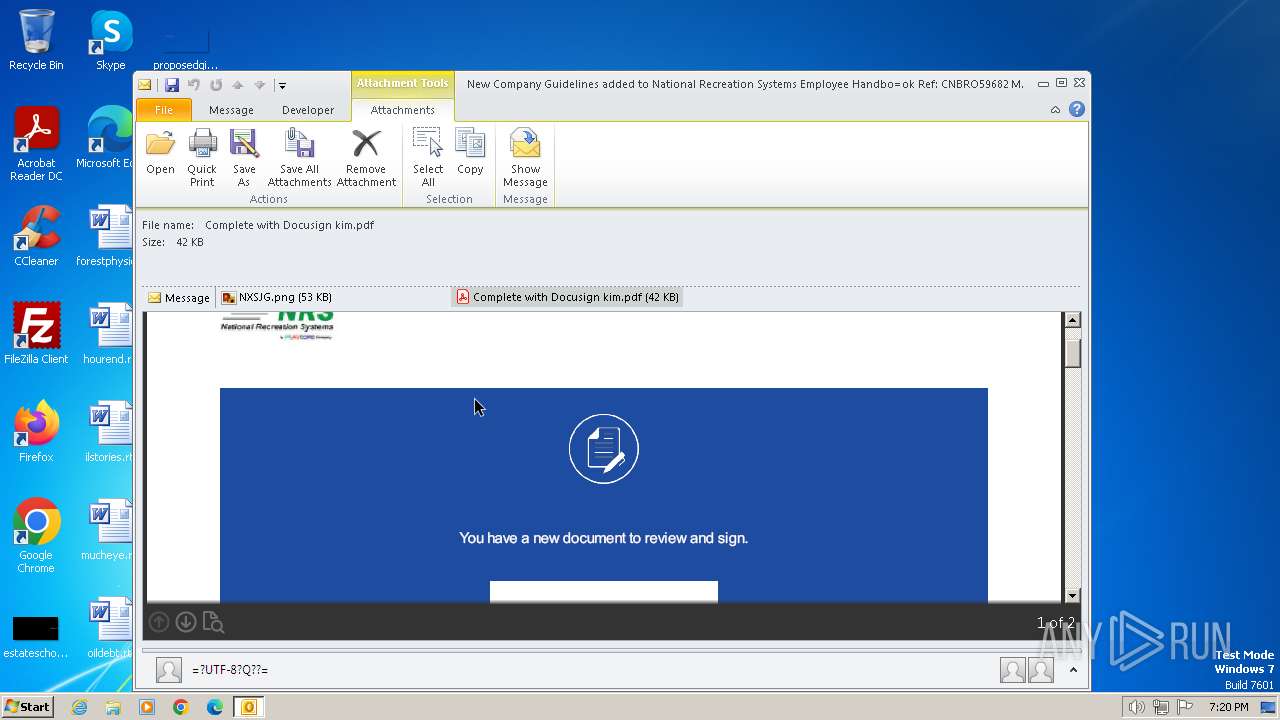
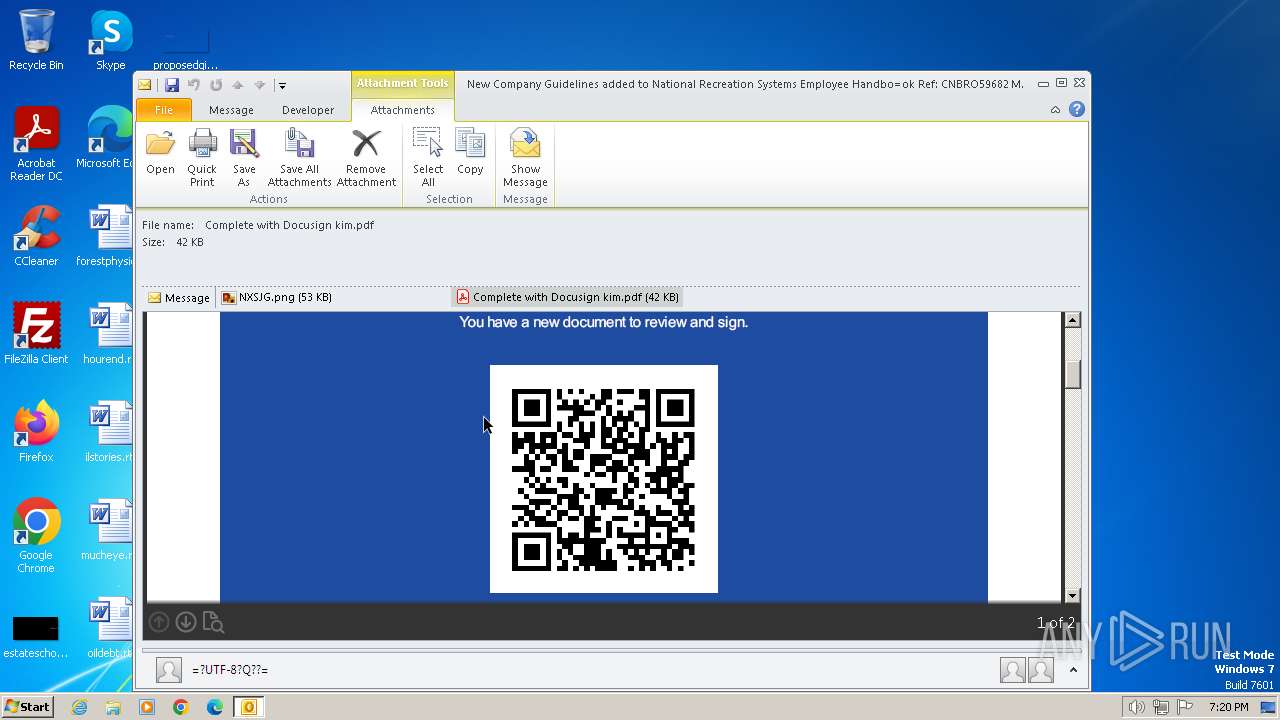
| File name: | phish_alert_iocp_v1.10.14.eml |
| Full analysis: | https://app.any.run/tasks/b99c004b-67a6-4770-9e6b-7754bfef9800 |
| Verdict: | Malicious activity |
| Analysis date: | July 10, 2024, 18:20:08 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines (348), with CRLF line terminators |
| MD5: | 74C597F2CC5505CE7261A2C49F96AA10 |
| SHA1: | 5FDE4E98CC0E28BB1B417E1914B4A2D4EC207FE2 |
| SHA256: | AA18B0183E37F849A785E065DF30FF5F440C203E84440AF5B7DEBFCBDBBB8385 |
| SSDEEP: | 3072:/wTOlYZWRmNLBGjSJQ8rrSSvexjPYbGax0pRrWqRZx3r61JEO+xXjn:/wHWRmNASq6+SOPZ8AWqRj3r61Jl+xXz |
MALICIOUS
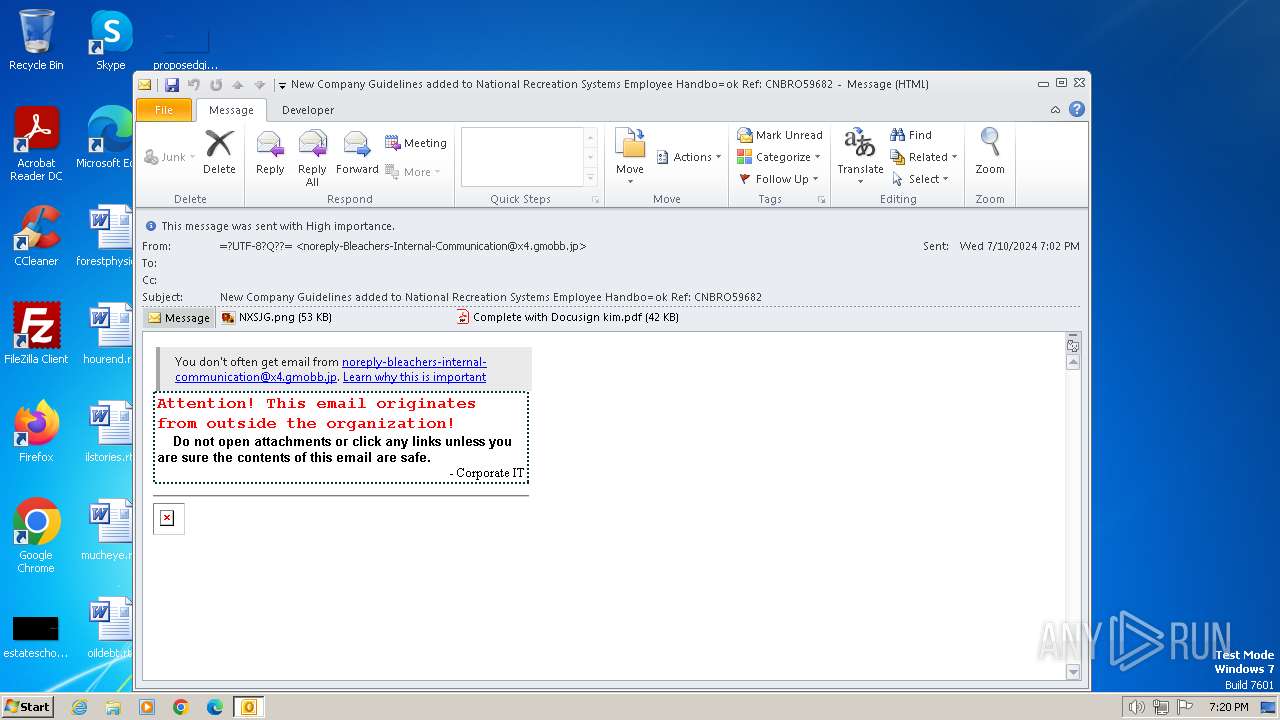
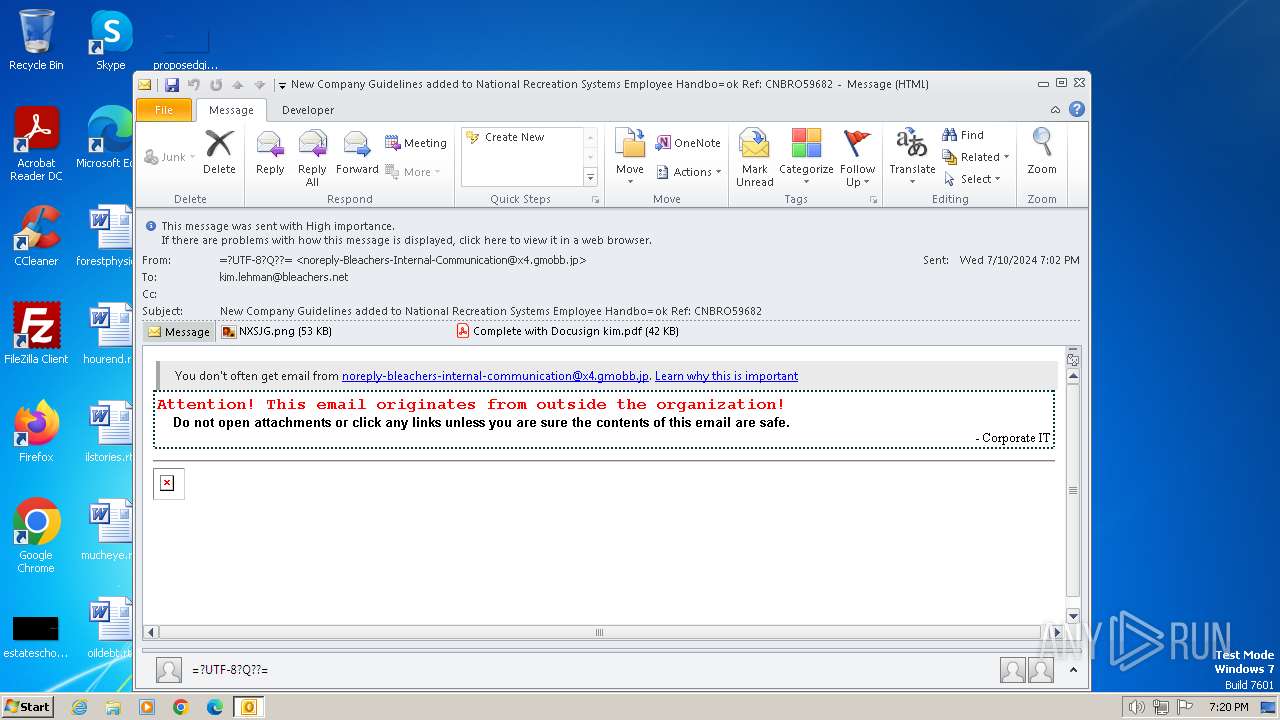
Phishing has been detected
- OUTLOOK.EXE (PID: 3400)
- OUTLOOK.EXE (PID: 3400)
SUSPICIOUS
Creates file in the systems drive root
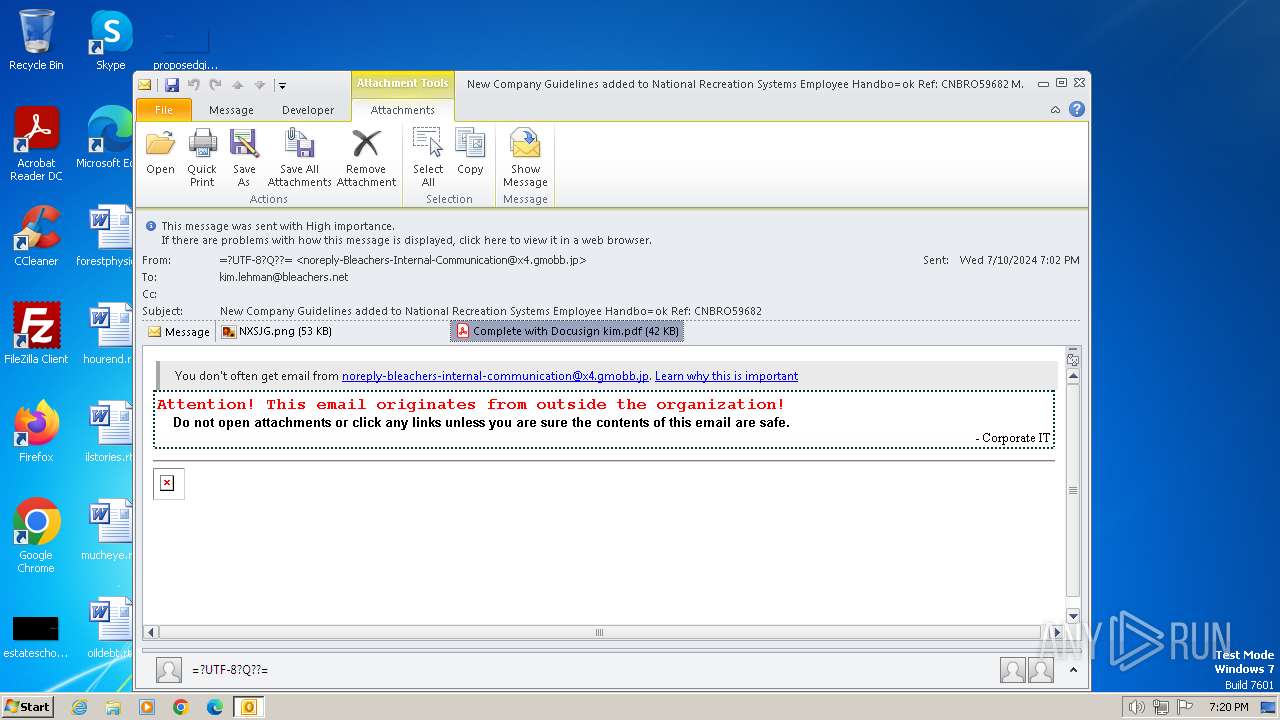
- AcroRd32.exe (PID: 3684)
INFO
Application launched itself
- AcroRd32.exe (PID: 2432)
The process uses the downloaded file
- OUTLOOK.EXE (PID: 3400)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
44
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2432 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /b /id 3696_398771019 /if pdfshell_prevf69d3a62-7b63-45da-a48a-8746817a5f88 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | prevhost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3400 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\phish_alert_iocp_v1.10.14.eml | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3684 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer /b /id 3696_398771019 /if pdfshell_prevf69d3a62-7b63-45da-a48a-8746817a5f88 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3696 | C:\Windows\system32\prevhost.exe {DC6EFB56-9CFA-464D-8880-44885D7DC193} -Embedding | C:\Windows\System32\prevhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Preview Handler Surrogate Host Version: 6.1.7601.17562 (win7sp1_gdr.110217-1504) Modules
| |||||||||||||||
Total events
9 423
Read events
8 845
Write events
542
Delete events
36
Modification events
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3400) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
3
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE4DE.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3400 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 3400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\1JCULFXS\Complete with Docusign kim.pdf:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\{74C8D3EE-0AE3-485D-94FE-3AE59DBE5414}\{1C306CB1-771E-4B4B-A902-86E897877F5B}.png | image | |
MD5:4C61C12EDBC453D7AE184976E95258E1 | SHA256:296526F9A716C1AA91BA5D6F69F0EB92FDF79C2CB2CFCF0CEB22B7CCBC27035F | |||
| 3400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\1JCULFXS\Complete with Docusign kim.pdf | ||
MD5:DD63D802E7958F4158A8B5ACBA05BFAB | SHA256:77549BEE617FCA8320E43735FDB72906BFAAE27175CD4C56234A94B884292164 | |||
| 3400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3400 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:24B6EFD3FC88E8BCDE7691295497FDF6 | SHA256:E075A116D0000A0435F4F89BD5B41364B576D7AEB95D08FCE434EFF0AEF59CDA | |||
| 3400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\1JCULFXS\Complete with Docusign kim (2).pdf:Zone.Identifier:$DATA | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 3400 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\1JCULFXS\Complete with Docusign kim (2).pdf | ||
MD5:DD63D802E7958F4158A8B5ACBA05BFAB | SHA256:77549BEE617FCA8320E43735FDB72906BFAAE27175CD4C56234A94B884292164 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
14
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1060 | svchost.exe | GET | 304 | 23.209.125.30:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f69642324cc87bd | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 95.101.54.122:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 304 | 23.209.125.30:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1372 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3400 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1372 | svchost.exe | 23.209.125.30:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
1372 | svchost.exe | 95.101.54.122:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.messenger.msn.com |
| whitelisted |
dns.msftncsi.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |