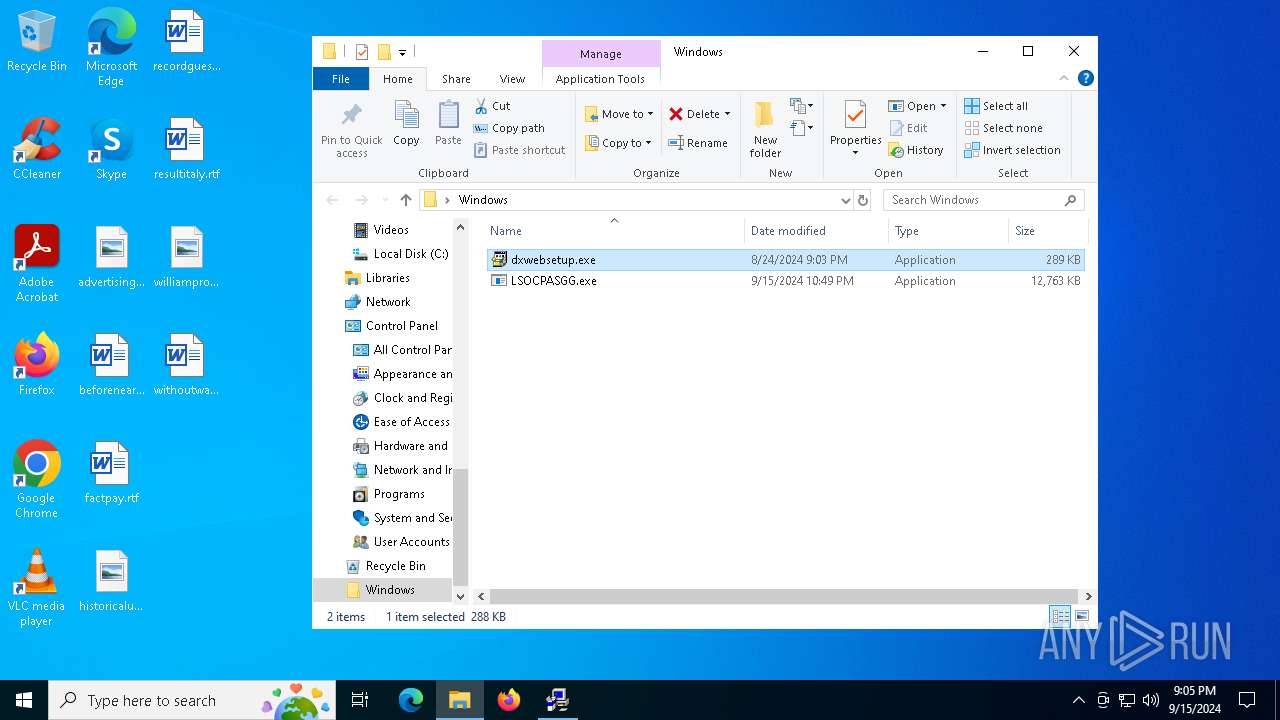
| File name: | Windows.zip |
| Full analysis: | https://app.any.run/tasks/4669a584-f71c-444f-b1ec-3cb938dc81e8 |
| Verdict: | Malicious activity |
| Analysis date: | September 15, 2024, 21:02:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | D6028AD913F71516CC979C9E2529ED3C |
| SHA1: | A056091F7C867597EF333E634BB5DEF099509C30 |
| SHA256: | A9E2838E0F0CB902123509CC8F36B9C29327ED98A02A54668D12FCB75690CD30 |
| SSDEEP: | 98304:tHg/35WrcDDikbINDkksjrNRXdQ0IZuUWTf05fi8+1ICVQDq2KzbZetx2t1sop3t:taIF33PtorgJ6+K |
MALICIOUS
Changes the autorun value in the registry
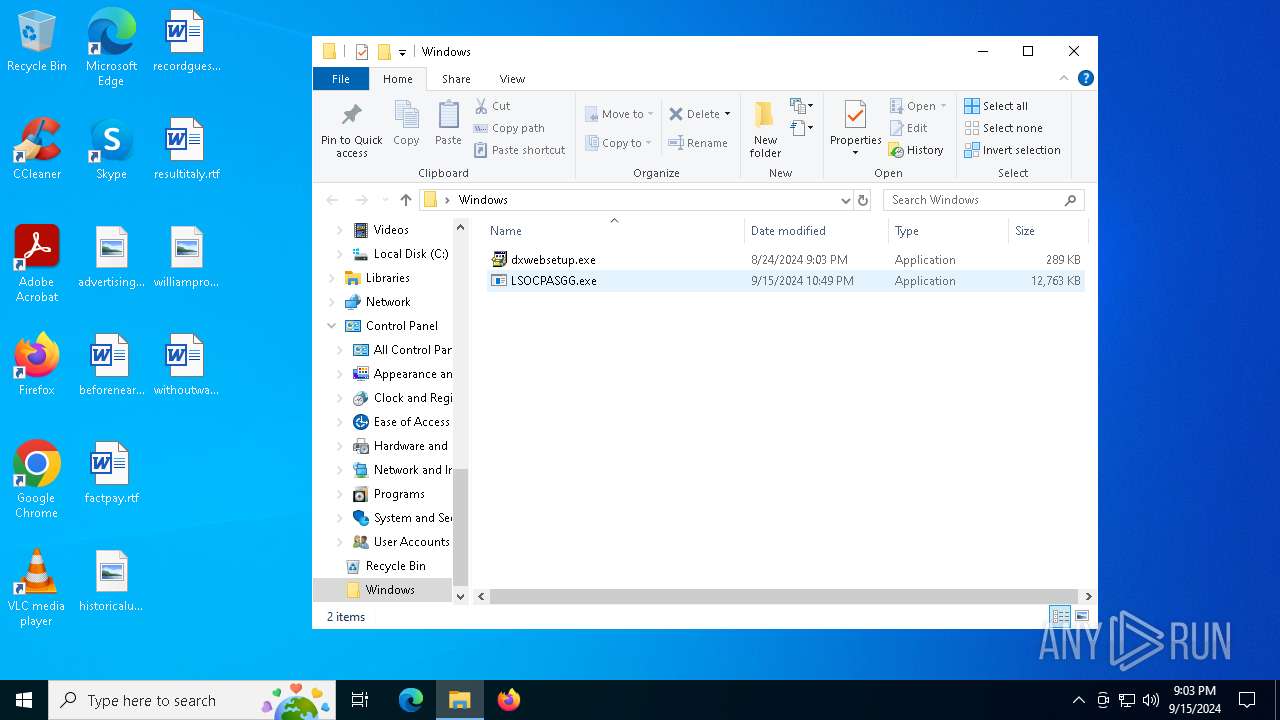
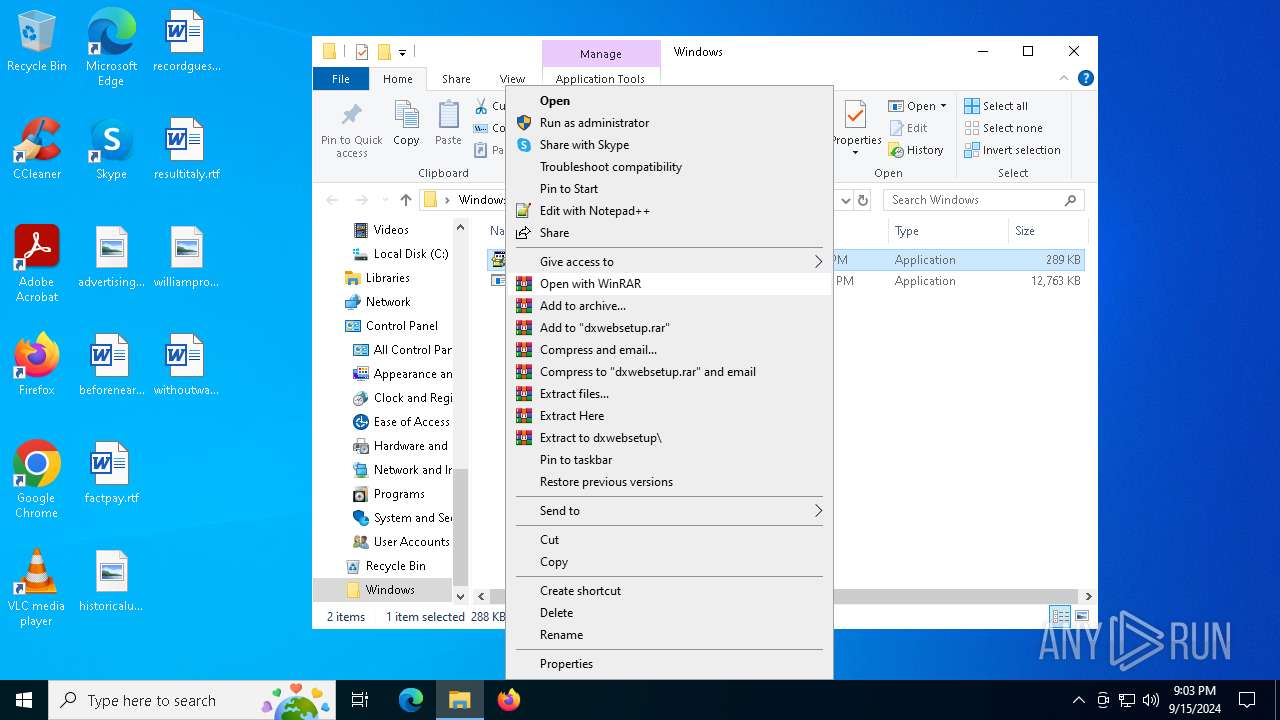
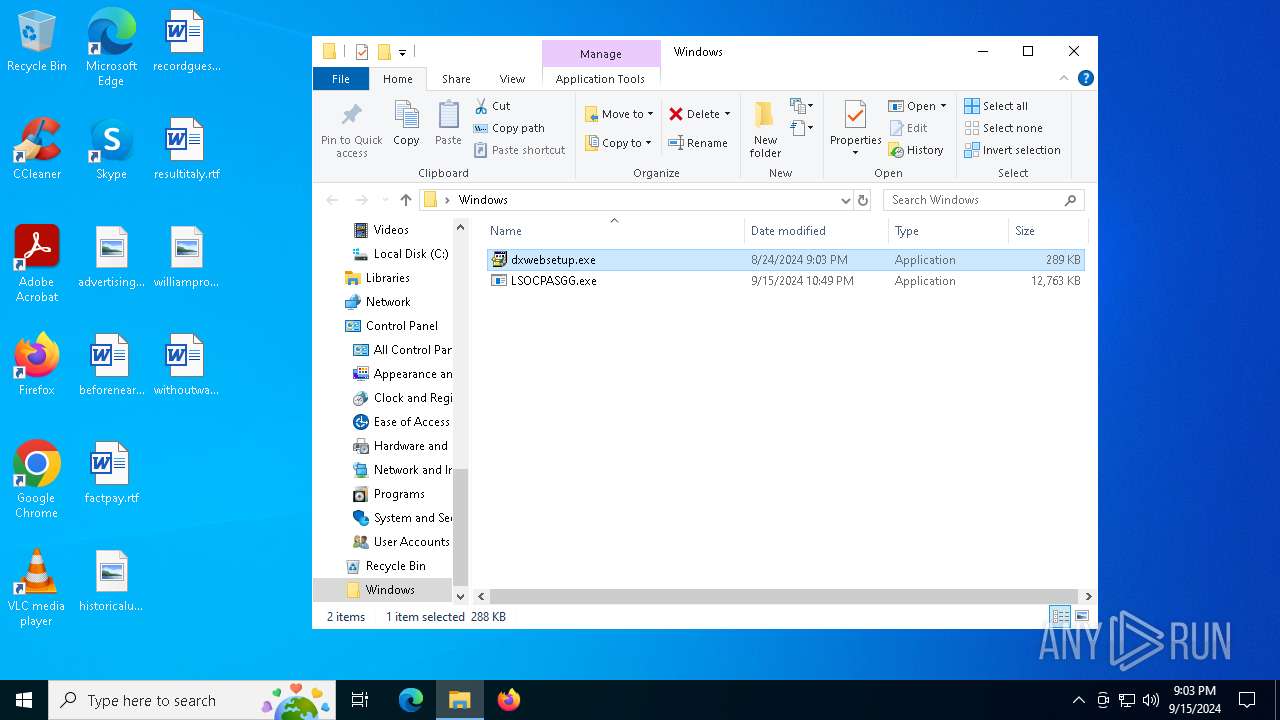
- dxwebsetup.exe (PID: 6212)
- dxwebsetup.exe (PID: 6100)
SUSPICIOUS
Starts a Microsoft application from unusual location
- dxwsetup.exe (PID: 6928)
- dxwebsetup.exe (PID: 6212)
- dxwebsetup.exe (PID: 2228)
- dxwebsetup.exe (PID: 6100)
- dxwsetup.exe (PID: 4524)
Executable content was dropped or overwritten
- dxwebsetup.exe (PID: 6212)
- dxwsetup.exe (PID: 6928)
- dxwebsetup.exe (PID: 6100)
- infinst.exe (PID: 6208)
- infinst.exe (PID: 6340)
- infinst.exe (PID: 5984)
Reads security settings of Internet Explorer
- dxwsetup.exe (PID: 6928)
Write to the desktop.ini file (may be used to cloak folders)
- dxwsetup.exe (PID: 6928)
Searches for installed software
- dllhost.exe (PID: 6572)
Executes as Windows Service
- VSSVC.exe (PID: 5988)
Checks Windows Trust Settings
- dxwsetup.exe (PID: 6928)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7004)
Checks supported languages
- dxwebsetup.exe (PID: 6212)
- dxwsetup.exe (PID: 6928)
- dxwebsetup.exe (PID: 6100)
- dxwsetup.exe (PID: 4524)
- infinst.exe (PID: 6208)
- infinst.exe (PID: 6340)
- infinst.exe (PID: 5984)
Manual execution by a user
- dxwebsetup.exe (PID: 6212)
- dxwebsetup.exe (PID: 2228)
- dxwebsetup.exe (PID: 6100)
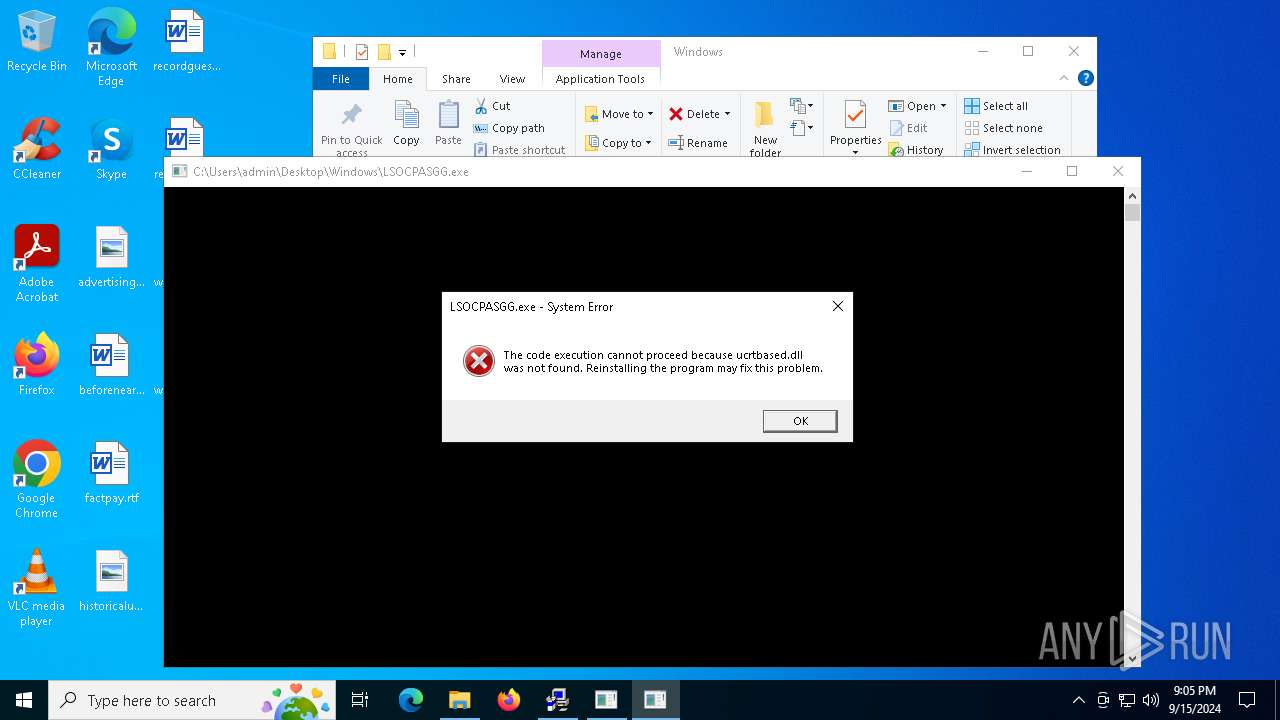
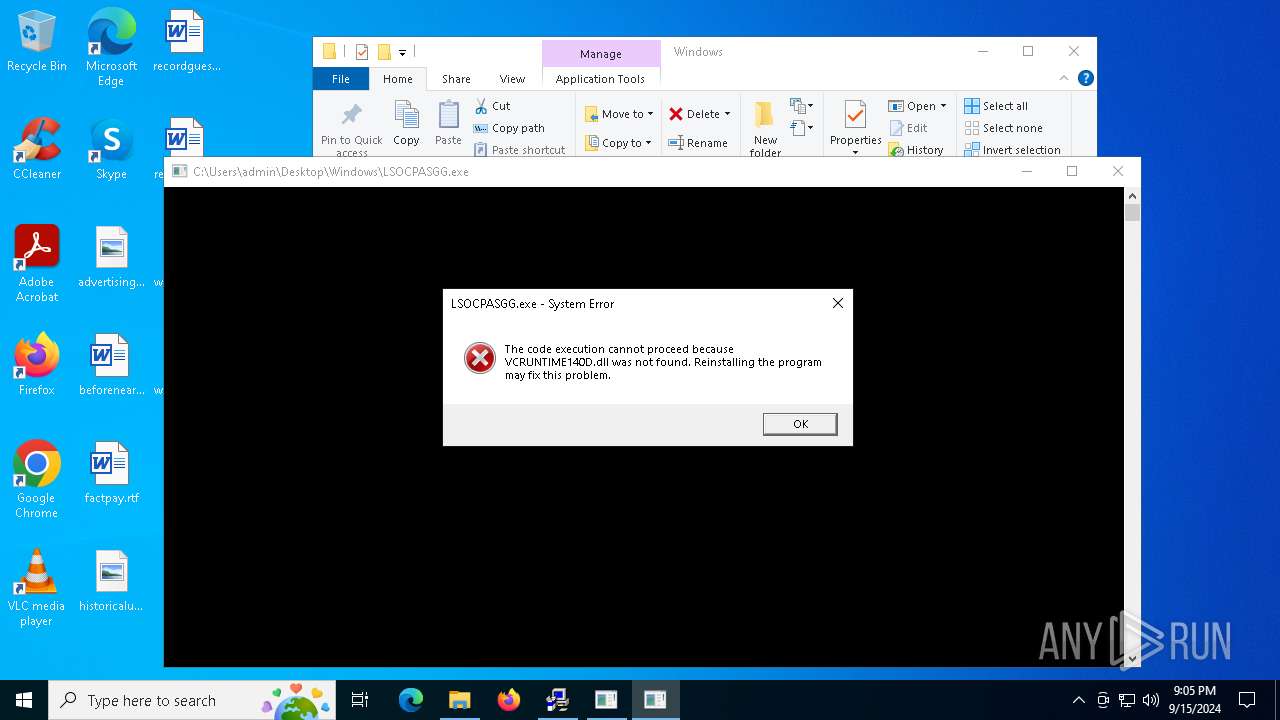
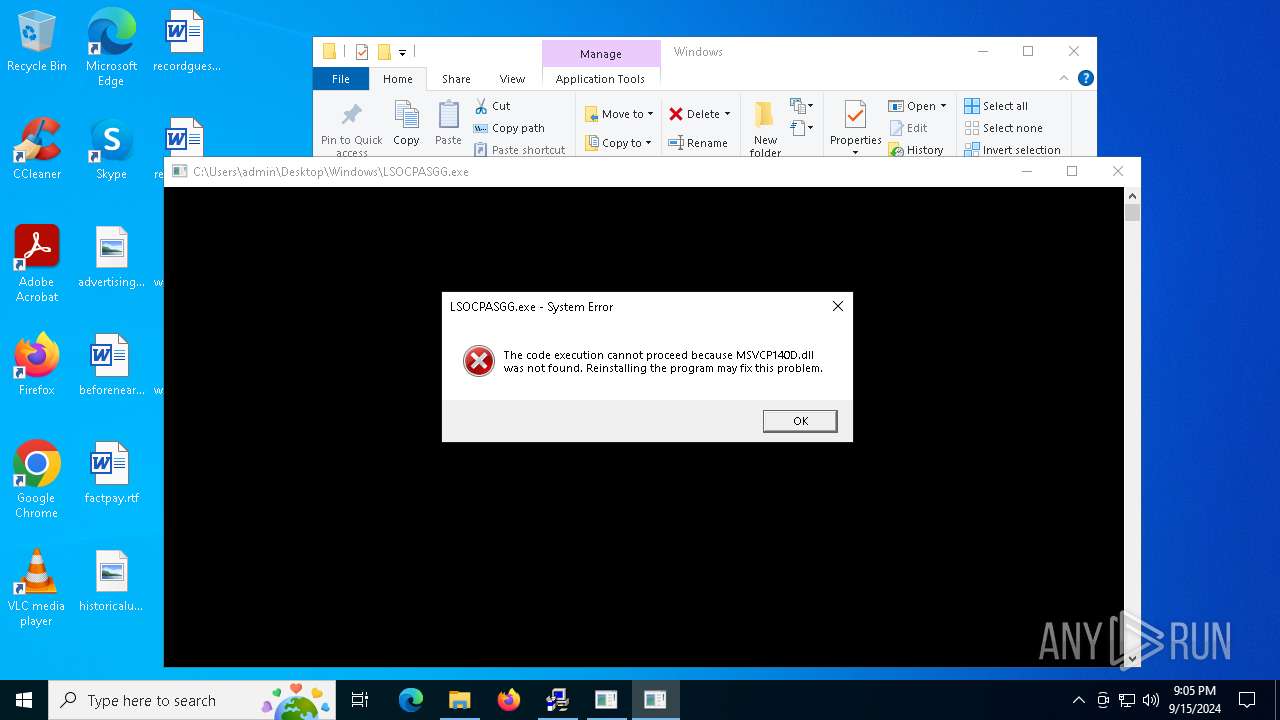
- LSOCPASGG.exe (PID: 3852)
Create files in a temporary directory
- dxwebsetup.exe (PID: 6212)
- dxwsetup.exe (PID: 6928)
- dxwebsetup.exe (PID: 6100)
The process uses the downloaded file
- WinRAR.exe (PID: 7004)
Reads the computer name
- dxwsetup.exe (PID: 6928)
Sends debugging messages
- dxwsetup.exe (PID: 6928)
Checks proxy server information
- dxwsetup.exe (PID: 6928)
Reads the machine GUID from the registry
- dxwsetup.exe (PID: 6928)
Reads the software policy settings
- dxwsetup.exe (PID: 6928)
- slui.exe (PID: 4392)
Creates files or folders in the user directory
- dxwsetup.exe (PID: 6928)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:09:15 23:00:56 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Windows/ |
Total processes
153
Monitored processes
19
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2228 | "C:\Users\admin\Desktop\Windows\dxwebsetup.exe" | C:\Users\admin\Desktop\Windows\dxwebsetup.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DirectX 9.0 Web setup Exit code: 3221226540 Version: 9.29.1974.0 Modules
| |||||||||||||||
| 3352 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3852 | "C:\Users\admin\Desktop\Windows\LSOCPASGG.exe" | C:\Users\admin\Desktop\Windows\LSOCPASGG.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3908 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4252 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4392 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4524 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\dxwsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\dxwsetup.exe | — | dxwebsetup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DirectX Setup Exit code: 0 Version: 4.9.0.0904 Modules
| |||||||||||||||
| 5468 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5692 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | LSOCPASGG.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 443
Read events
11 215
Write events
209
Delete events
19
Modification events
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Windows.zip | |||
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF800000088000000B804000051020000 | |||
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7004) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
67
Suspicious files
663
Text files
27
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6928 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\SETE670.tmp | executable | |
MD5:984CAD22FA542A08C5D22941B888D8DC | SHA256:57BC22850BB8E0BCC511A9B54CD3DA18EEC61F3088940C07D63B9B74E7FE2308 | |||
| 6928 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\dsetup.dll | executable | |
MD5:984CAD22FA542A08C5D22941B888D8DC | SHA256:57BC22850BB8E0BCC511A9B54CD3DA18EEC61F3088940C07D63B9B74E7FE2308 | |||
| 6212 | dxwebsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dsetup32.dll | executable | |
MD5:A5412A144F63D639B47FCC1BA68CB029 | SHA256:8A011DA043A4B81E2B3D41A332E0FF23A65D546BD7636E8BC74885E8746927D6 | |||
| 7004 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa7004.48719\Windows\LSOCPASGG.exe | executable | |
MD5:8CF5FA0C67AC335DFB36E93E0ABC94AA | SHA256:224261449A1996B6B3D670811682DA2A3890F84833A5F0F3DBF045535CB898E1 | |||
| 6212 | dxwebsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.cif | text | |
MD5:7B1FBE9F5F43B2261234B78FE115CF8E | SHA256:762FF640013DB2BD4109D7DF43A867303093815751129BD1E33F16BF02E52CCE | |||
| 6212 | dxwebsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.inf | text | |
MD5:AD8982EAA02C7AD4D7CDCBC248CAA941 | SHA256:D63C35E9B43EB0F28FFC28F61C9C9A306DA9C9DE3386770A7EB19FAA44DBFC00 | |||
| 6928 | dxwsetup.exe | C:\Windows\Logs\DirectX.log | text | |
MD5:846244249A89D1C9EC9B662032DF6AA0 | SHA256:B38F62906C87C3B6448B2A2AA38286AB9EB515D4C15B3B4FF717DCDB499FF52F | |||
| 6212 | dxwebsetup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\dxwsetup.exe | executable | |
MD5:AC3A5F7BE8CD13A863B50AB5FE00B71C | SHA256:8F5E89298E3DC2E22D47515900C37CCA4EE121C5BA06A6D962D40AD6E1A595DA | |||
| 6928 | dxwsetup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:98ADD340FAC9B974175F9CCA49BD6285 | SHA256:01DF4441395F5BC676ABBDAAF5A7455154BCD055E7CD66BE3B66D57FAF11998B | |||
| 6928 | dxwsetup.exe | C:\Windows\SysWOW64\directx\websetup\dxupdate.cab | compressed | |
MD5:4AFD7F5C0574A0EFD163740ECB142011 | SHA256:6E39B3FDB6722EA8AA0DC8F46AE0D8BD6496DD0F5F56BAC618A0A7DD22D6CFB2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
165
TCP/UDP connections
41
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6012 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1404 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6928 | dxwsetup.exe | GET | 302 | 23.32.101.194:80 | http://download.microsoft.com/download/1/7/1/1718CCC4-6315-4D8E-9543-8E28A4E18C4C/dxupdate.cab | unknown | — | — | whitelisted |
6928 | dxwsetup.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6928 | dxwsetup.exe | GET | 302 | 23.32.101.194:80 | http://download.microsoft.com/download/1/7/1/1718CCC4-6315-4D8E-9543-8E28A4E18C4C/Apr2006_xinput_x86.cab | unknown | — | — | whitelisted |
6928 | dxwsetup.exe | GET | 302 | 23.32.101.194:80 | http://download.microsoft.com/download/1/7/1/1718CCC4-6315-4D8E-9543-8E28A4E18C4C/Apr2006_xinput_x64.cab | unknown | — | — | whitelisted |
236 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
236 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6928 | dxwsetup.exe | GET | 302 | 23.32.101.194:80 | http://download.microsoft.com/download/1/7/1/1718CCC4-6315-4D8E-9543-8E28A4E18C4C/Aug2006_xinput_x86.cab | unknown | — | — | whitelisted |
6928 | dxwsetup.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6428 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6012 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6012 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6012 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1404 | svchost.exe | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
download.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
dxwsetup.exe | DLL_PROCESS_ATTACH |
dxwsetup.exe | DLL_PROCESS_ATTACH |
dxwsetup.exe | Invalid parameter passed to C runtime function.
|
dxwsetup.exe | Invalid parameter passed to C runtime function.
|
dxwsetup.exe | DLL_PROCESS_DETACH |
dxwsetup.exe | DLL_PROCESS_DETACH |
dxwsetup.exe | DLL_PROCESS_ATTACH |
dxwsetup.exe | DLL_PROCESS_ATTACH |