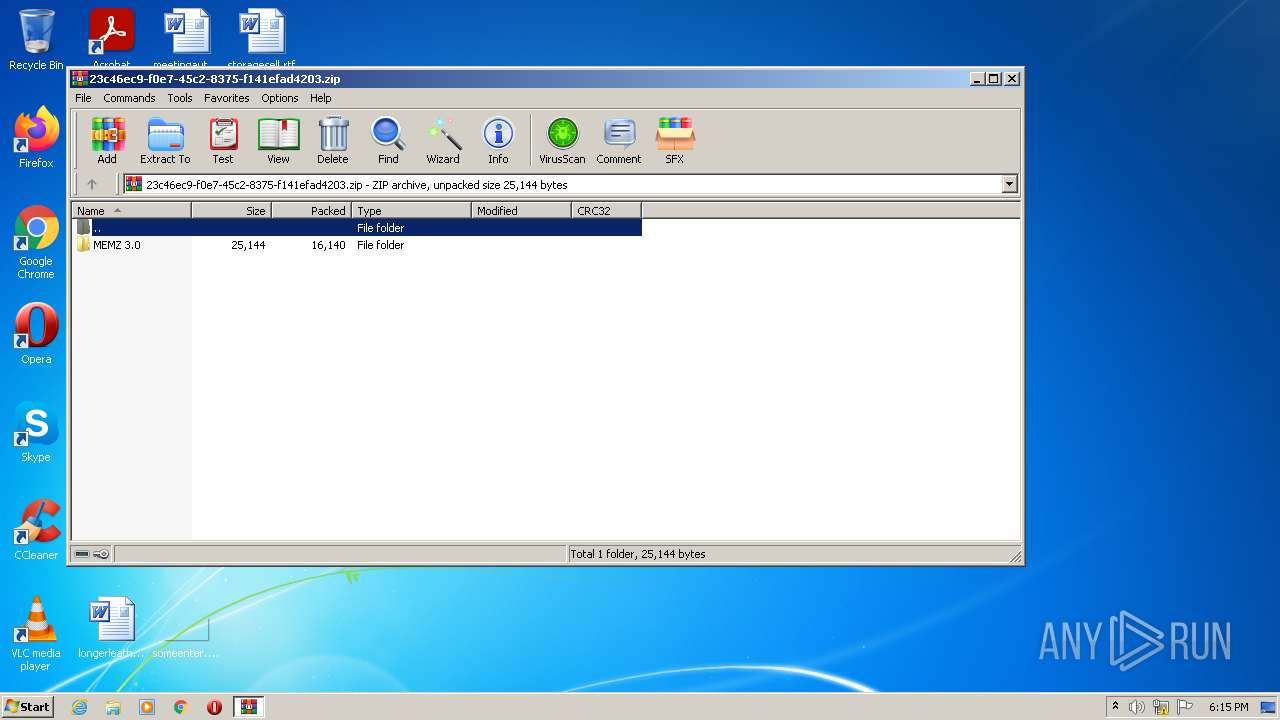
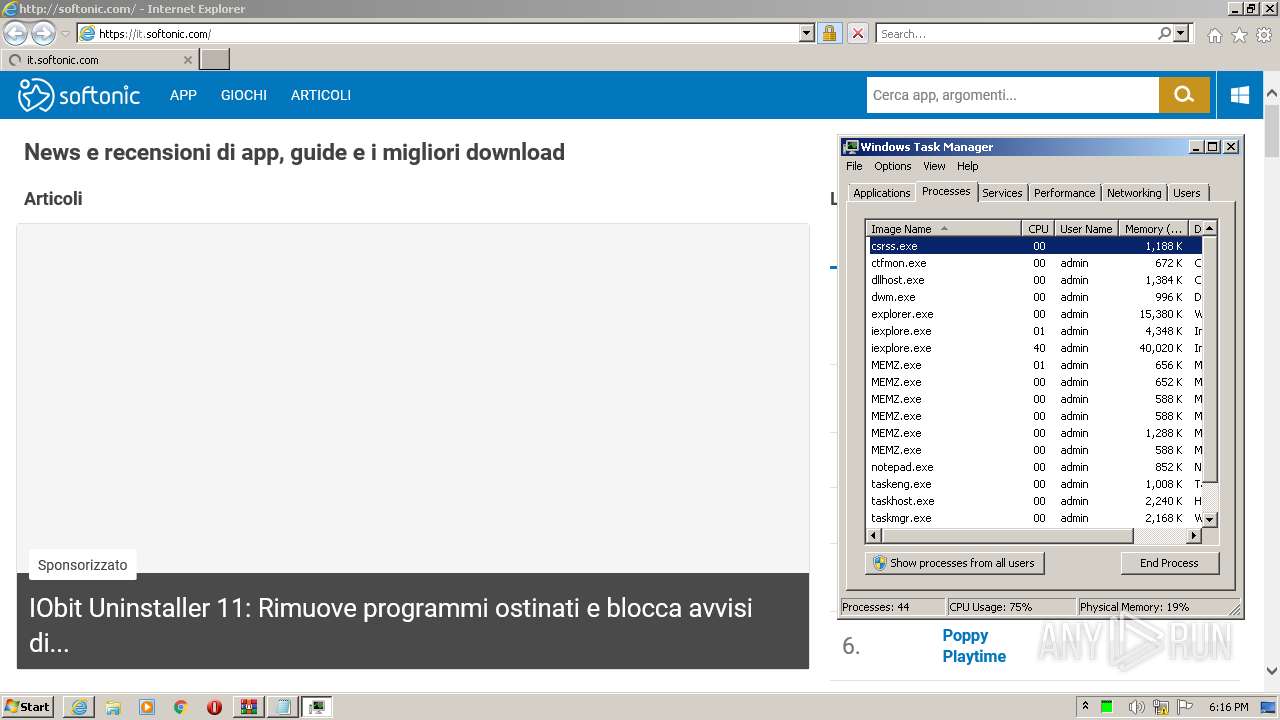
| File name: | MEMZ%203.0.zip |
| Full analysis: | https://app.any.run/tasks/aec95e24-5ba7-4305-88ff-ef8b63dd365f |
| Verdict: | Malicious activity |
| Analysis date: | December 25, 2021, 18:15:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 230D7DCB83B67DEFF379A563ABBBD536 |
| SHA1: | DC032D6A626F57B542613FDE876715765E0B1A42 |
| SHA256: | A9CD3D966D453AFD424D9AC54DF414B80073BB51D249F4089185976FB316E254 |
| SSDEEP: | 384:+gTgSLZ5WpPu3944wiiNIw2nbI6B/PvpITFkvbWa:+cvLZ5n9Sb9ytp6kl |
MALICIOUS
Application was dropped or rewritten from another process
- MEMZ.exe (PID: 4004)
- MEMZ.exe (PID: 3268)
- MEMZ.exe (PID: 3220)
- MEMZ.exe (PID: 1780)
- MEMZ.exe (PID: 188)
- MEMZ.exe (PID: 2188)
- MEMZ.exe (PID: 1964)
- MEMZ.exe (PID: 3828)
SUSPICIOUS
Checks supported languages
- MEMZ.exe (PID: 3268)
- MEMZ.exe (PID: 1780)
- MEMZ.exe (PID: 188)
- MEMZ.exe (PID: 2188)
- WinRAR.exe (PID: 3296)
- MEMZ.exe (PID: 4004)
- MEMZ.exe (PID: 3828)
- MEMZ.exe (PID: 3220)
Application launched itself
- MEMZ.exe (PID: 3268)
Reads the computer name
- WinRAR.exe (PID: 3296)
- MEMZ.exe (PID: 3268)
- MEMZ.exe (PID: 3828)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3296)
Starts Internet Explorer
- MEMZ.exe (PID: 3828)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3584)
INFO
Checks supported languages
- notepad.exe (PID: 2256)
- taskmgr.exe (PID: 3004)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 3584)
Manual execution by user
- taskmgr.exe (PID: 3004)
Reads the computer name
- taskmgr.exe (PID: 3004)
- iexplore.exe (PID: 3284)
- iexplore.exe (PID: 3584)
Application launched itself
- iexplore.exe (PID: 3284)
Changes settings of System certificates
- iexplore.exe (PID: 3584)
Creates files in the user directory
- iexplore.exe (PID: 3584)
Reads settings of System Certificates
- iexplore.exe (PID: 3584)
Reads internet explorer settings
- iexplore.exe (PID: 3584)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3584)
Changes internet zones settings
- iexplore.exe (PID: 3284)
Checks Windows Trust Settings
- iexplore.exe (PID: 3584)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
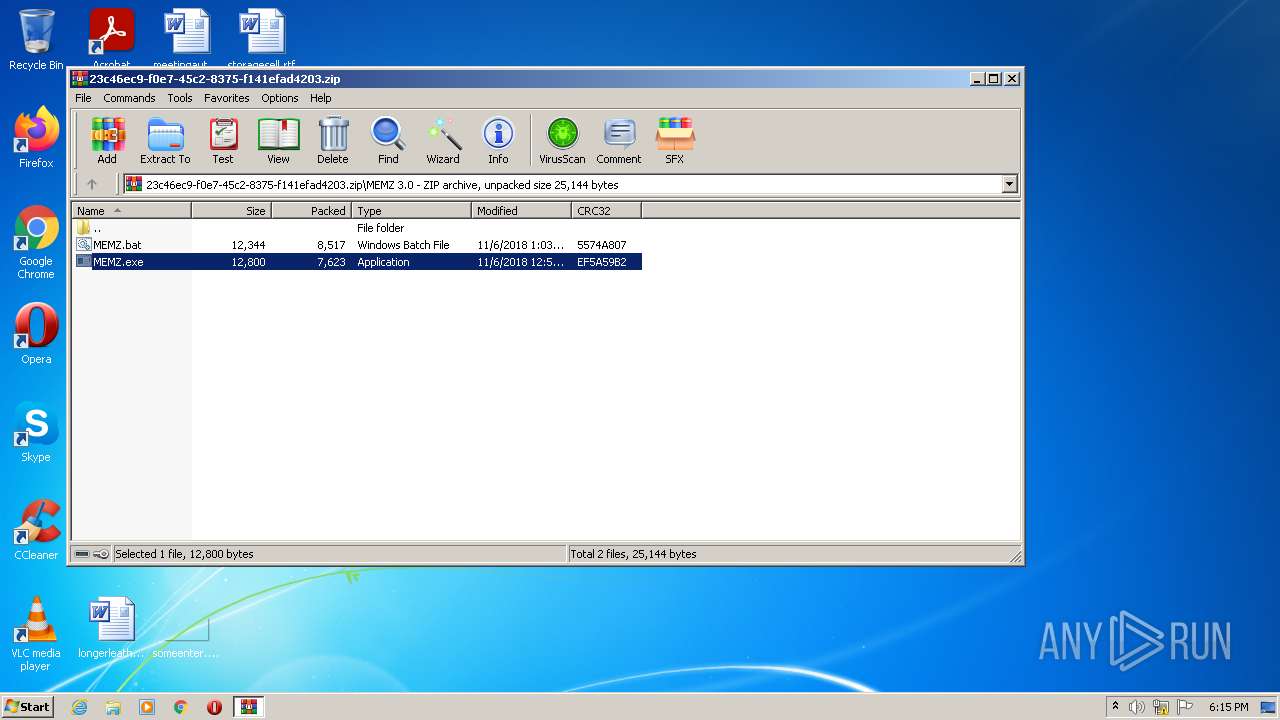
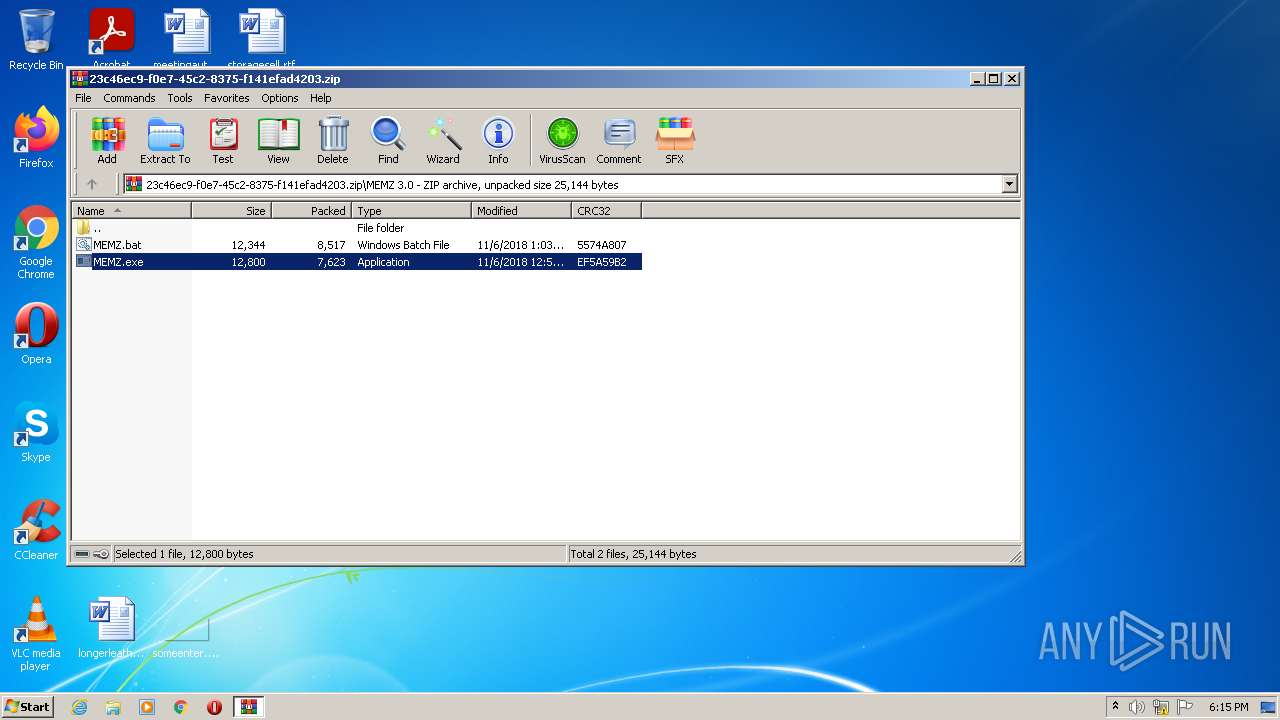
| ZipFileName: | MEMZ 3.0/MEMZ.bat |
|---|---|
| ZipUncompressedSize: | 12344 |
| ZipCompressedSize: | 8517 |
| ZipCRC: | 0x5574a807 |
| ZipModifyDate: | 2018:11:06 13:03:29 |
| ZipCompression: | Deflated |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
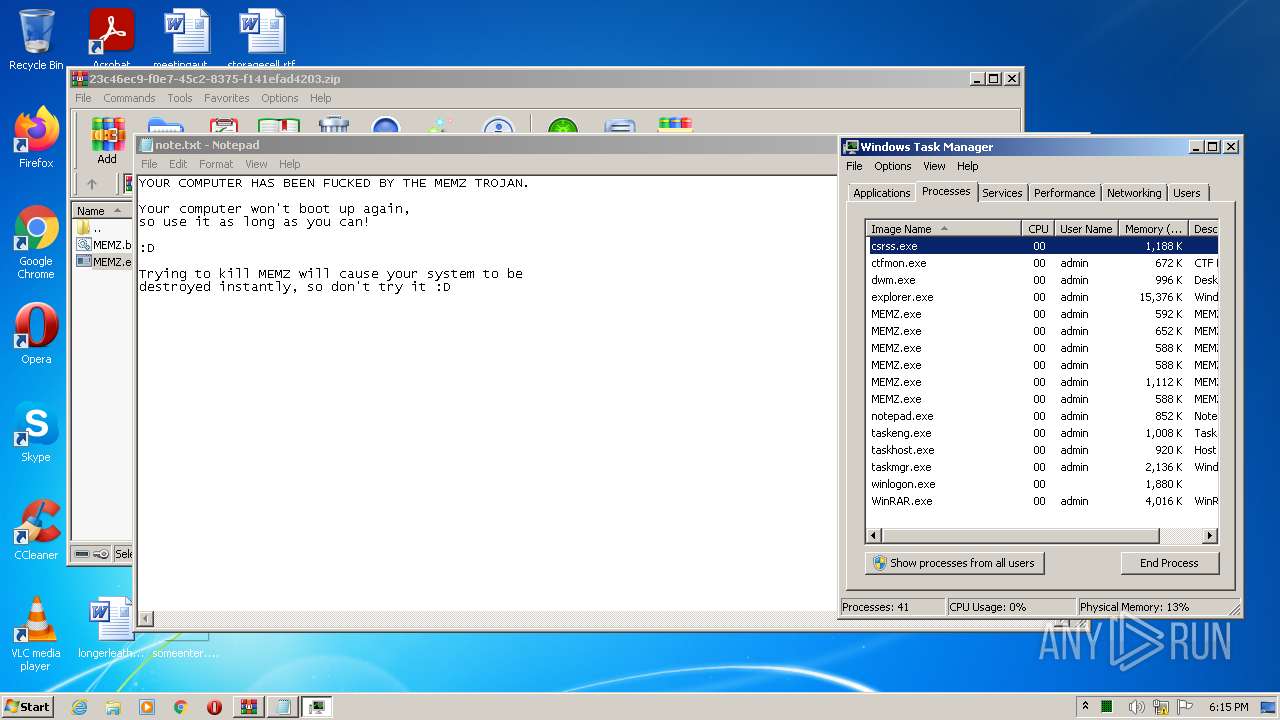
Total processes
51
Monitored processes
13
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1780 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 2188 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
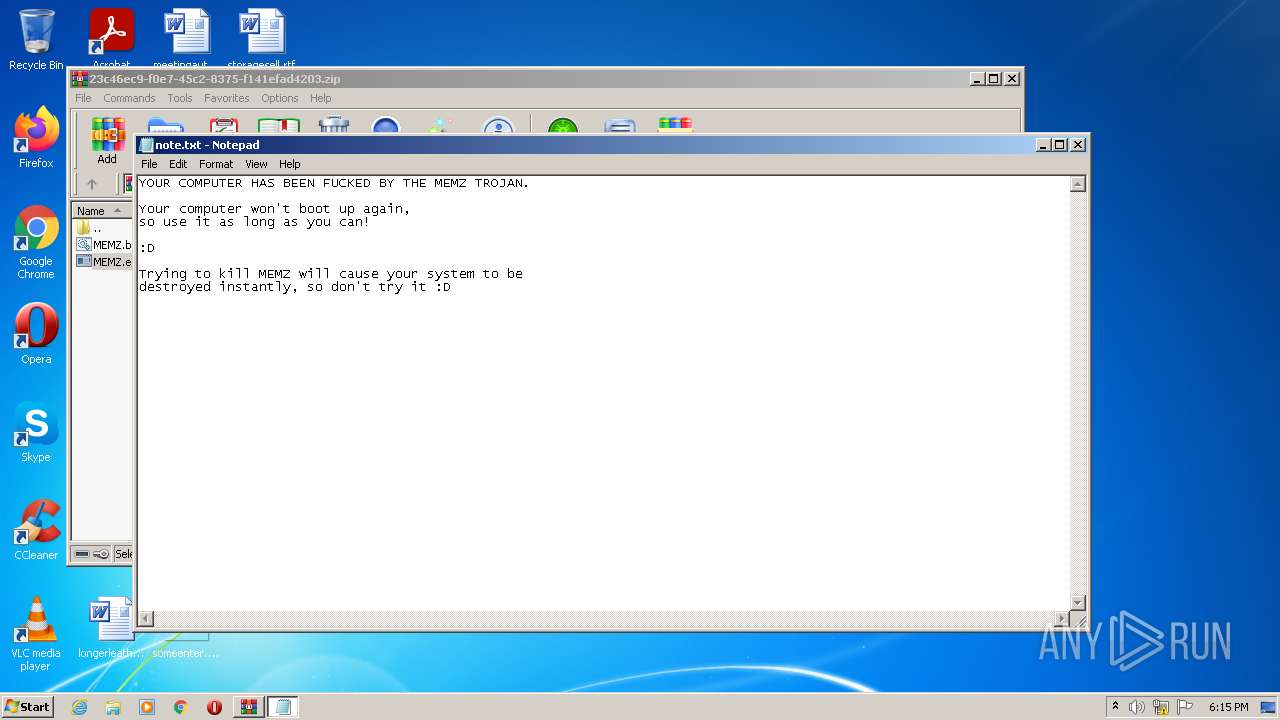
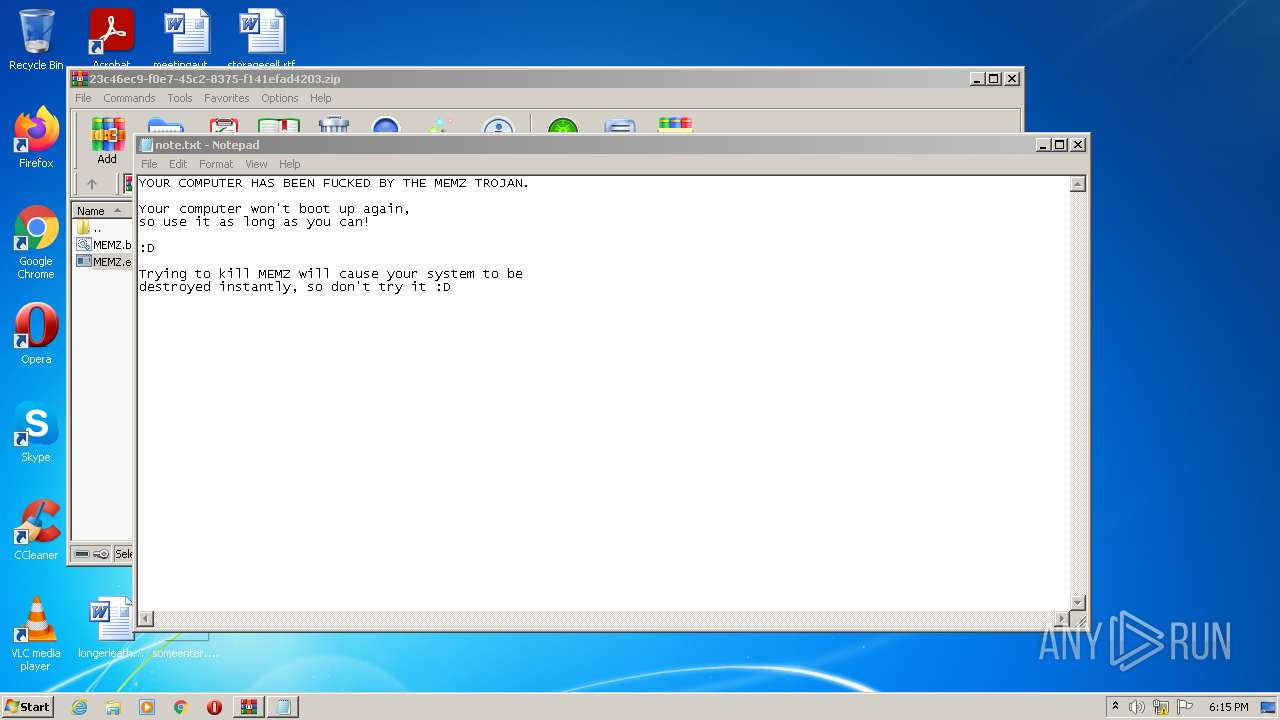
| 2256 | "C:\Windows\System32\notepad.exe" \note.txt | C:\Windows\System32\notepad.exe | — | MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
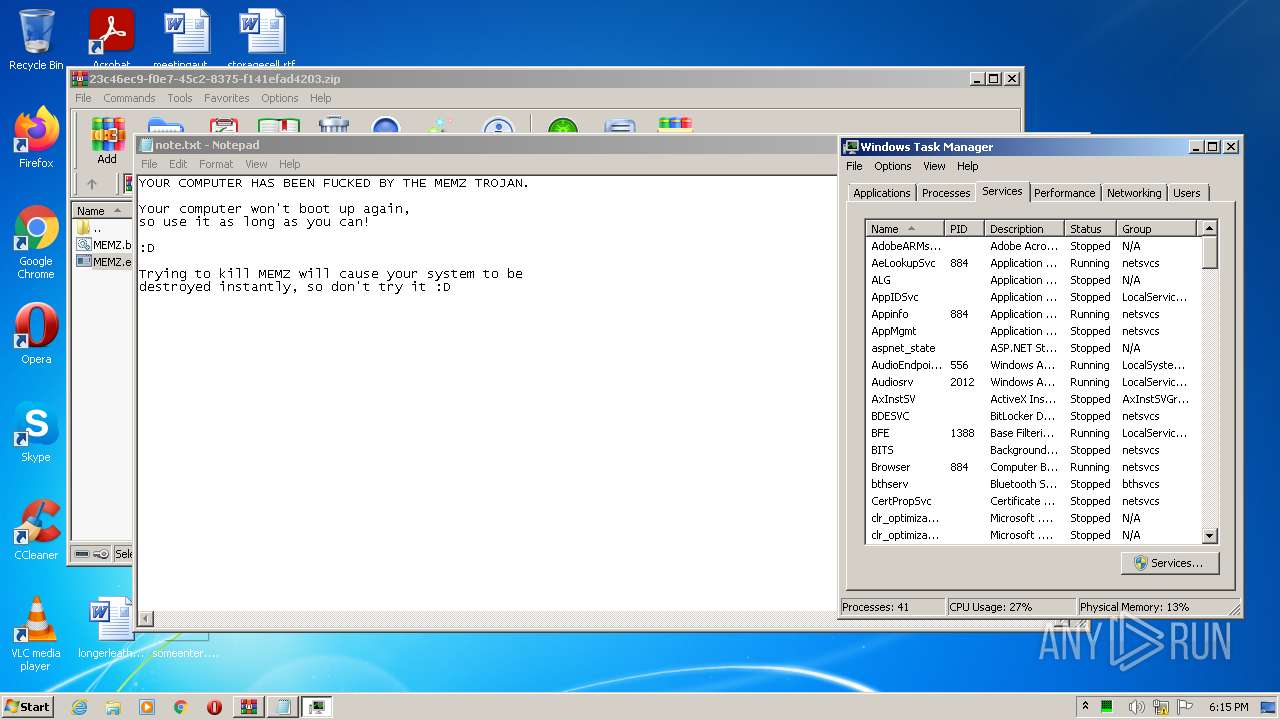
| 3004 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3220 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3268 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
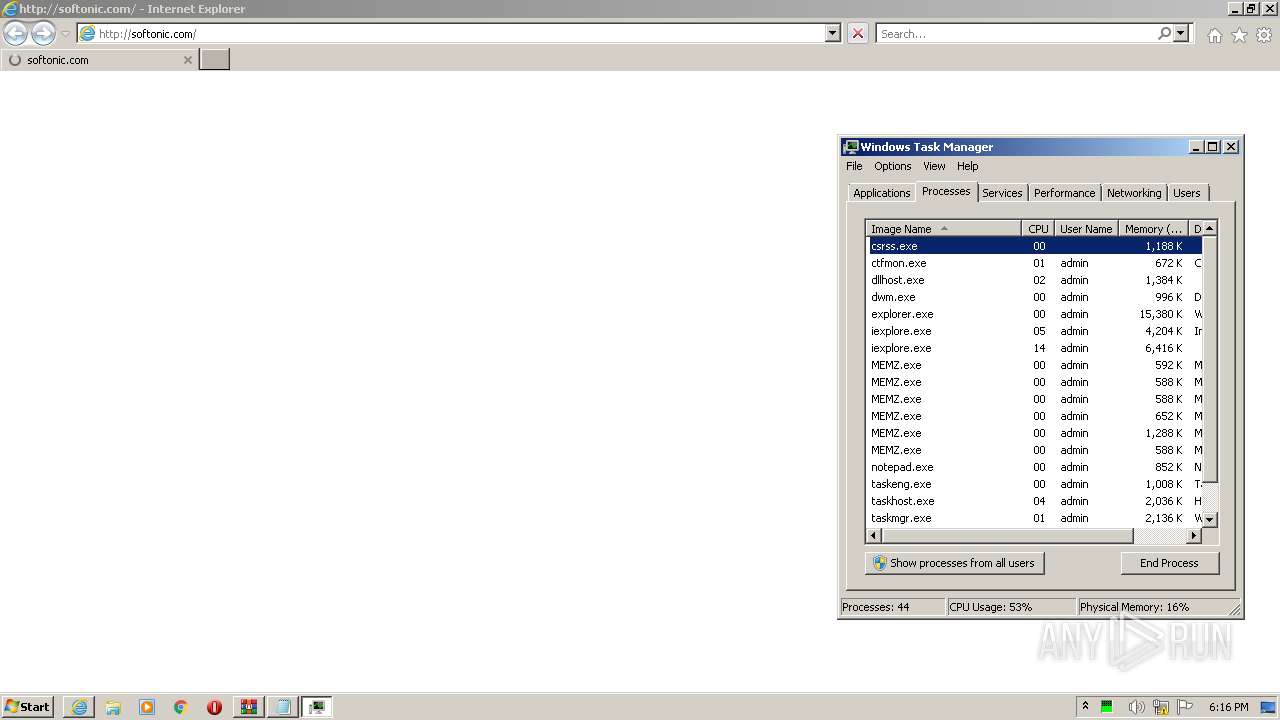
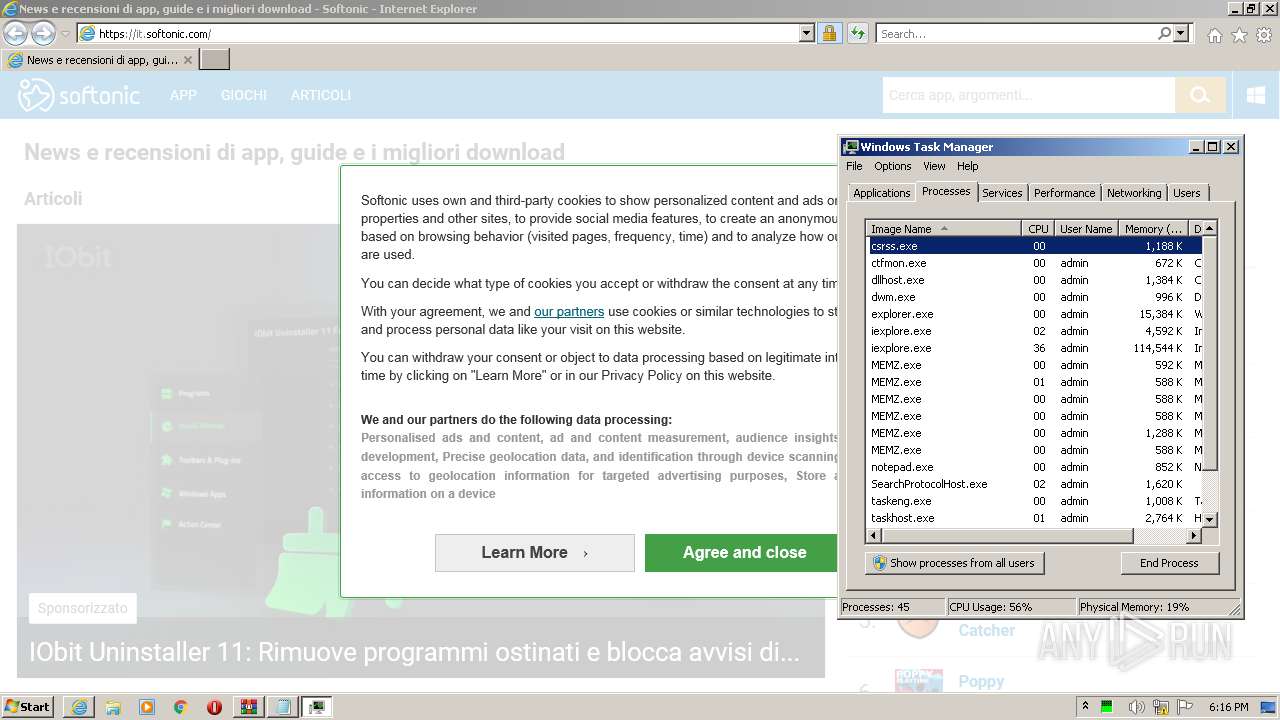
| 3284 | "C:\Program Files\Internet Explorer\iexplore.exe" http://softonic.com/ | C:\Program Files\Internet Explorer\iexplore.exe | — | MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3296 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\23c46ec9-f0e7-45c2-8375-f141efad4203.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
13 949
Read events
13 764
Write events
185
Delete events
0
Modification events
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\23c46ec9-f0e7-45c2-8375-f141efad4203.zip | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3296) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
1
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.bat | text | |
MD5:13A43C26BB98449FD82D2A552877013A | SHA256:5F52365ACCB76D679B2B3946870439A62EB8936B9A0595F0FB0198138106B513 | |||
| 3828 | MEMZ.exe | C:\note.txt | binary | |
MD5:AFA6955439B8D516721231029FB9CA1B | SHA256:8E9F20F6864C66576536C0B866C6FFDCF11397DB67FE120E972E244C3C022270 | |||
| 3584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3296 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3296.29479\MEMZ 3.0\MEMZ.exe | executable | |
MD5:A7BCF7EA8E9F3F36EBFB85B823E39D91 | SHA256:3FF64F10603F0330FA2386FF99471CA789391ACE969BD0EC1C1B8CE1B4A6DB42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
83
DNS requests
41
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3584 | iexplore.exe | GET | — | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?019cd3607c62f9cd | US | — | — | whitelisted |
3584 | iexplore.exe | GET | — | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?8a1820cfded1a04f | US | — | — | whitelisted |
3584 | iexplore.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEQC0eKdRMTzmwh4ySFgYIPuD | US | der | 472 b | whitelisted |
3584 | iexplore.exe | GET | — | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?6d7b3136f86260d8 | US | — | — | whitelisted |
3584 | iexplore.exe | GET | — | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?dfc5895ad440e33f | US | — | — | whitelisted |
3584 | iexplore.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
3584 | iexplore.exe | GET | — | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?cb78a8b6b23c9532 | US | — | — | whitelisted |
3584 | iexplore.exe | GET | — | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?335db83299a4ea98 | US | — | — | whitelisted |
3584 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?1aa136a6ef1cfe8f | US | compressed | 59.9 Kb | whitelisted |
3584 | iexplore.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3584 | iexplore.exe | 35.227.233.104:443 | softonic.com | — | US | malicious |
3584 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3584 | iexplore.exe | 104.18.30.182:80 | ocsp.comodoca.com | Cloudflare Inc | US | suspicious |
3584 | iexplore.exe | 151.101.2.133:443 | sc.sftcdn.net | Fastly | US | malicious |
3584 | iexplore.exe | 13.224.193.7:443 | sdk.privacy-center.org | — | US | suspicious |
3584 | iexplore.exe | 13.224.198.4:443 | c.amazon-adsystem.com | — | US | unknown |
3584 | iexplore.exe | 142.250.186.72:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
3584 | iexplore.exe | 142.250.184.226:443 | securepubads.g.doubleclick.net | Google Inc. | US | whitelisted |
3584 | iexplore.exe | 104.109.90.33:443 | images.sftcdn.net | Akamai International B.V. | NL | unknown |
3584 | iexplore.exe | 2.16.186.160:443 | articles-img.sftcdn.net | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
softonic.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
www.softonic.com |
| malicious |
it.softonic.com |
| malicious |
sc.sftcdn.net |
| whitelisted |
sdk.privacy-center.org |
| shared |
www.googletagmanager.com |
| whitelisted |