| File name: | memz3-0 |
| Full analysis: | https://app.any.run/tasks/81986486-7a03-4d0b-be2f-9626c0016345 |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2024, 05:52:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 230D7DCB83B67DEFF379A563ABBBD536 |
| SHA1: | DC032D6A626F57B542613FDE876715765E0B1A42 |
| SHA256: | A9CD3D966D453AFD424D9AC54DF414B80073BB51D249F4089185976FB316E254 |
| SSDEEP: | 384:+gTgSLZ5WpPu3944wiiNIw2nbI6B/PvpITFkvbWa:+cvLZ5n9Sb9ytp6kl |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 1264)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- cscript.exe (PID: 2028)
Uses base64 encoding (SCRIPT)
- cscript.exe (PID: 2028)
SUSPICIOUS
Executing commands from a ".bat" file
- WinRAR.exe (PID: 1264)
The process executes JS scripts
- cmd.exe (PID: 3988)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 1264)
Script creates XML DOM node (SCRIPT)
- cscript.exe (PID: 2028)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 2028)
Creates XML DOM element (SCRIPT)
- cscript.exe (PID: 2028)
Saves data to a binary file (SCRIPT)
- cscript.exe (PID: 2028)
Creates a Folder object (SCRIPT)
- cscript.exe (PID: 2028)
Executable content was dropped or overwritten
- cscript.exe (PID: 2028)
The executable file from the user directory is run by the CMD process
- MEMZ.exe (PID: 2784)
- MEMZ.exe (PID: 1408)
- MEMZ.exe (PID: 3024)
Reads the Internet Settings
- cmd.exe (PID: 3988)
- cscript.exe (PID: 2028)
- MEMZ.exe (PID: 3024)
- MEMZ.exe (PID: 3588)
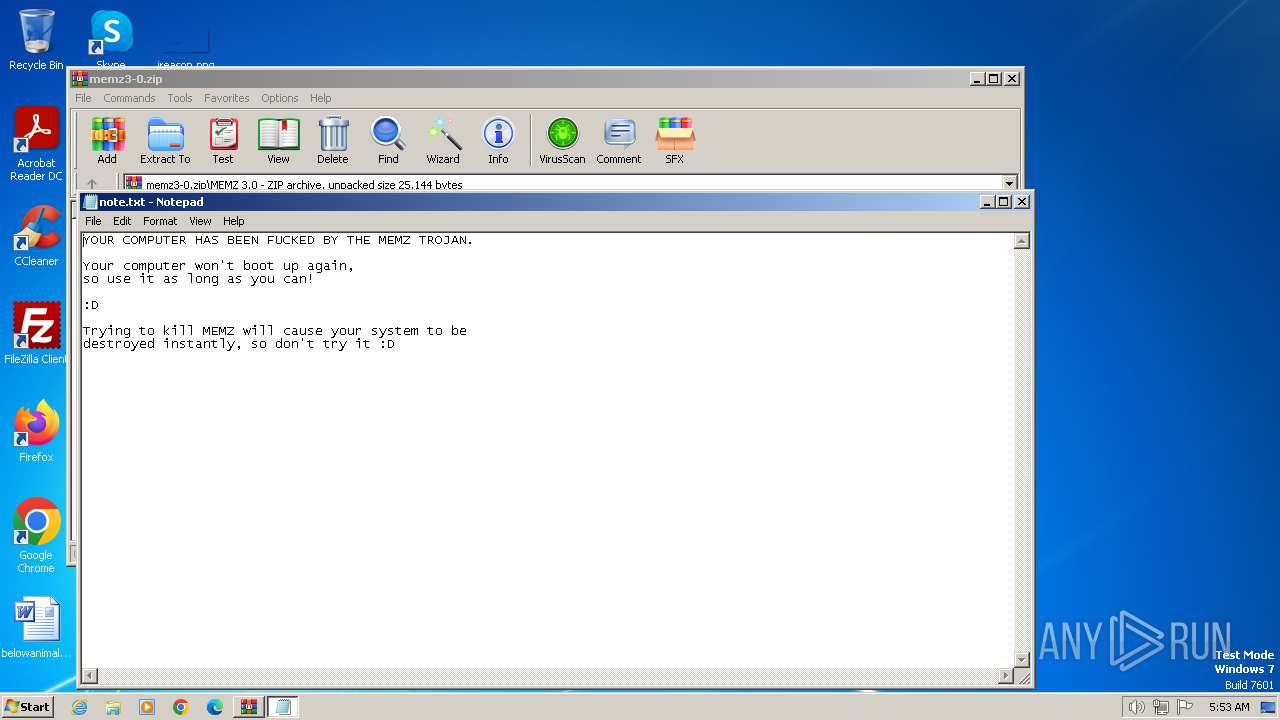
Start notepad (likely ransomware note)
- MEMZ.exe (PID: 3588)
Application launched itself
- MEMZ.exe (PID: 3024)
Writes binary data to a Stream object (SCRIPT)
- cscript.exe (PID: 2028)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 2028)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 2028)
INFO
Reads the computer name
- wmpnscfg.exe (PID: 1588)
- MEMZ.exe (PID: 3024)
- MEMZ.exe (PID: 3588)
Checks supported languages
- wmpnscfg.exe (PID: 1588)
- MEMZ.exe (PID: 3584)
- MEMZ.exe (PID: 3440)
- MEMZ.exe (PID: 3412)
- MEMZ.exe (PID: 3388)
- MEMZ.exe (PID: 3024)
- MEMZ.exe (PID: 3604)
- MEMZ.exe (PID: 3588)
Manual execution by a user
- wmpnscfg.exe (PID: 1588)
Create files in a temporary directory
- cscript.exe (PID: 2028)
Drops the executable file immediately after the start
- cscript.exe (PID: 2028)
Creates files or folders in the user directory
- cscript.exe (PID: 2028)
Reads security settings of Internet Explorer
- cscript.exe (PID: 2028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2018:11:06 13:03:58 |
| ZipCRC: | 0x5574a807 |
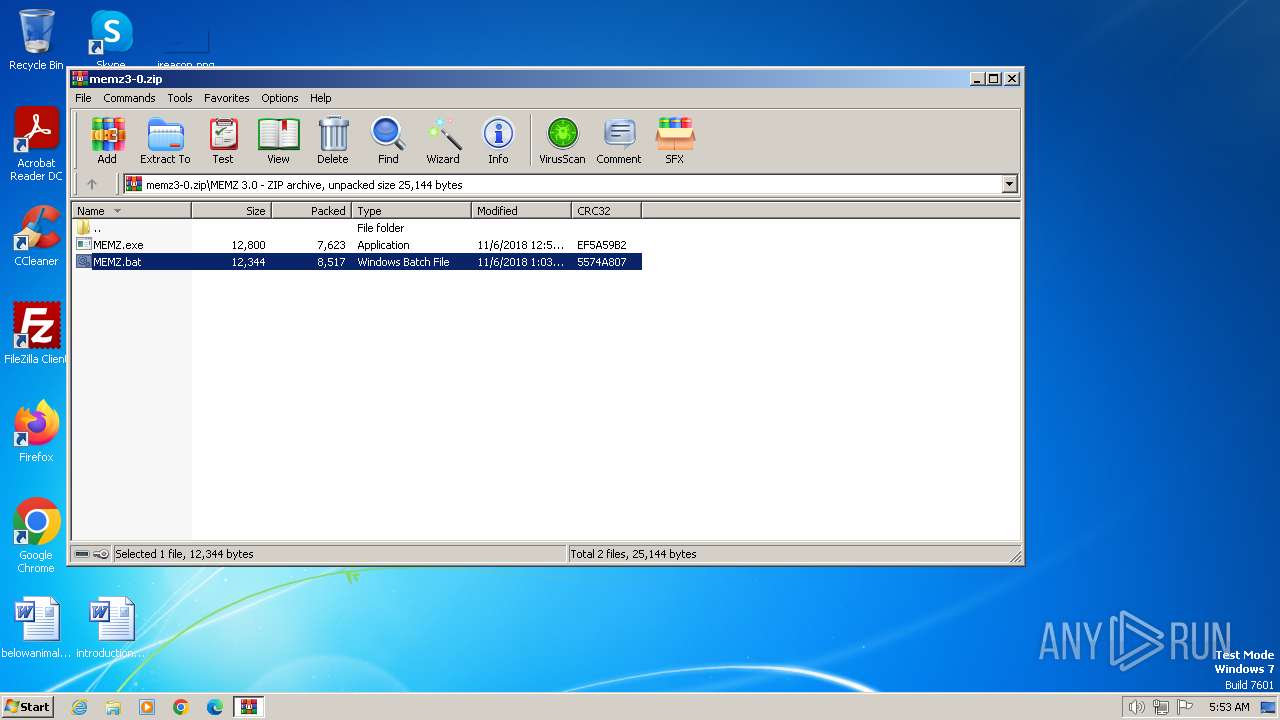
| ZipCompressedSize: | 8517 |
| ZipUncompressedSize: | 12344 |
| ZipFileName: | MEMZ 3.0/MEMZ.bat |
Total processes
53
Monitored processes
14
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1264 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\memz3-0.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1408 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1588 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2028 | cscript x.js | C:\Windows\System32\cscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2784 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3024 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3388 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3412 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3440 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3548 | "C:\Windows\System32\notepad.exe" \note.txt | C:\Windows\System32\notepad.exe | — | MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 537
Read events
3 446
Write events
91
Delete events
0
Modification events
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1264) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
2
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3588 | MEMZ.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 1264 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa1264.20184\MEMZ.bat | text | |
MD5:13A43C26BB98449FD82D2A552877013A | SHA256:5F52365ACCB76D679B2B3946870439A62EB8936B9A0595F0FB0198138106B513 | |||
| 3988 | cmd.exe | C:\Users\admin\AppData\Local\Temp\x.js | text | |
MD5:D94C93F882CF030ED9D66CC35796731D | SHA256:F7941E6BE49D757B46B9D6FB5ECB15392EC36A64E8906692D2EEB2BA9FC67CB6 | |||
| 3588 | MEMZ.exe | C:\note.txt | binary | |
MD5:AFA6955439B8D516721231029FB9CA1B | SHA256:8E9F20F6864C66576536C0B866C6FFDCF11397DB67FE120E972E244C3C022270 | |||
| 2028 | cscript.exe | C:\Users\admin\AppData\Local\Temp\z.zip | compressed | |
MD5:CF0C19EF6909E5C1F10C8460BA9299D8 | SHA256:ABB834EBD4B7D7F8DDF545976818F41B3CB51D2B895038A56457616D3A2C6776 | |||
| 3988 | cmd.exe | C:\Users\admin\AppData\Local\Temp\x | text | |
MD5:B2C77680F74E7D11B3A3A559F2A683BB | SHA256:7B628FE341F65759C53C149A6607242E610E8A7077FD815B68C1415621BFDB6E | |||
| 2028 | cscript.exe | C:\Users\admin\AppData\Roaming\MEMZ.exe | executable | |
MD5:A7BCF7EA8E9F3F36EBFB85B823E39D91 | SHA256:3FF64F10603F0330FA2386FF99471CA789391ACE969BD0EC1C1B8CE1B4A6DB42 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |