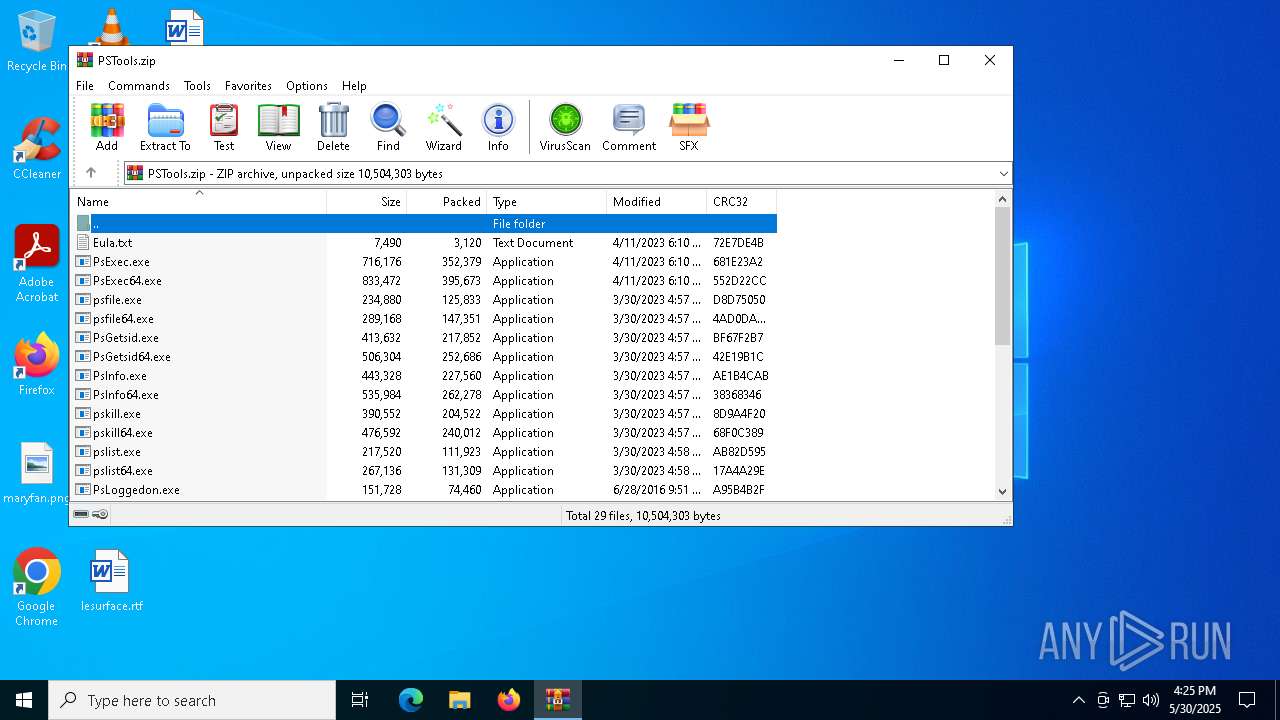
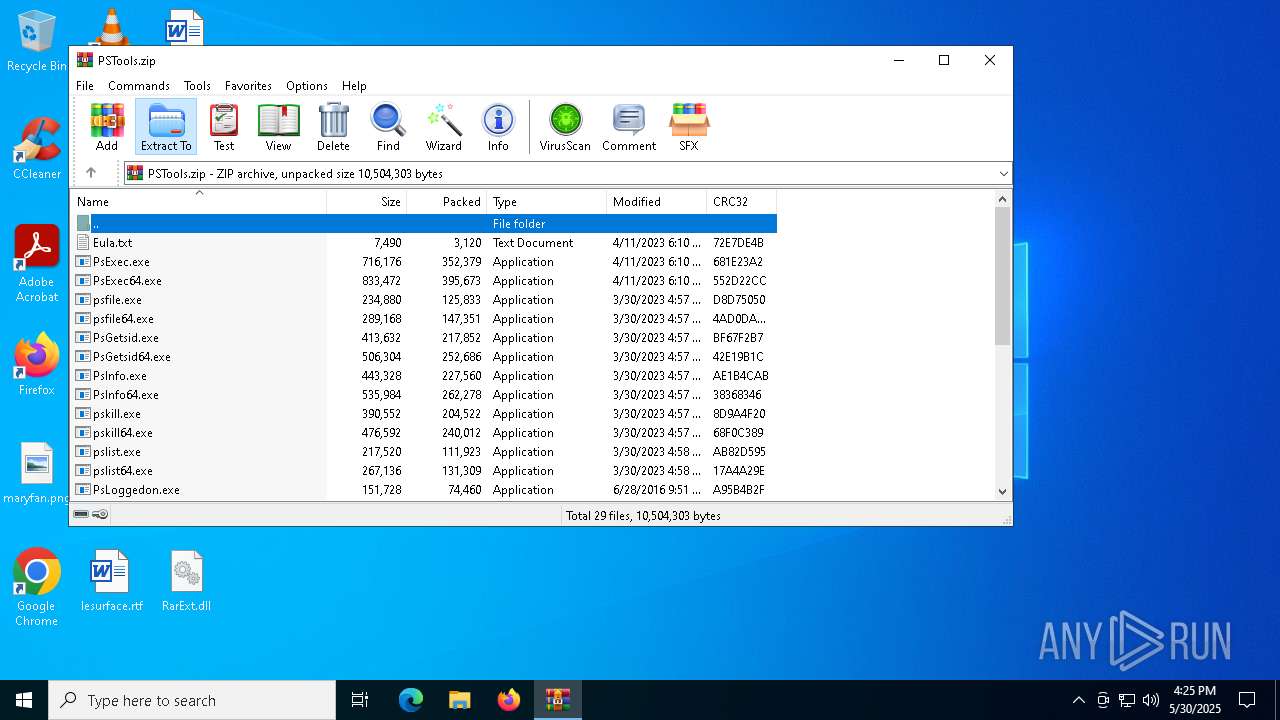
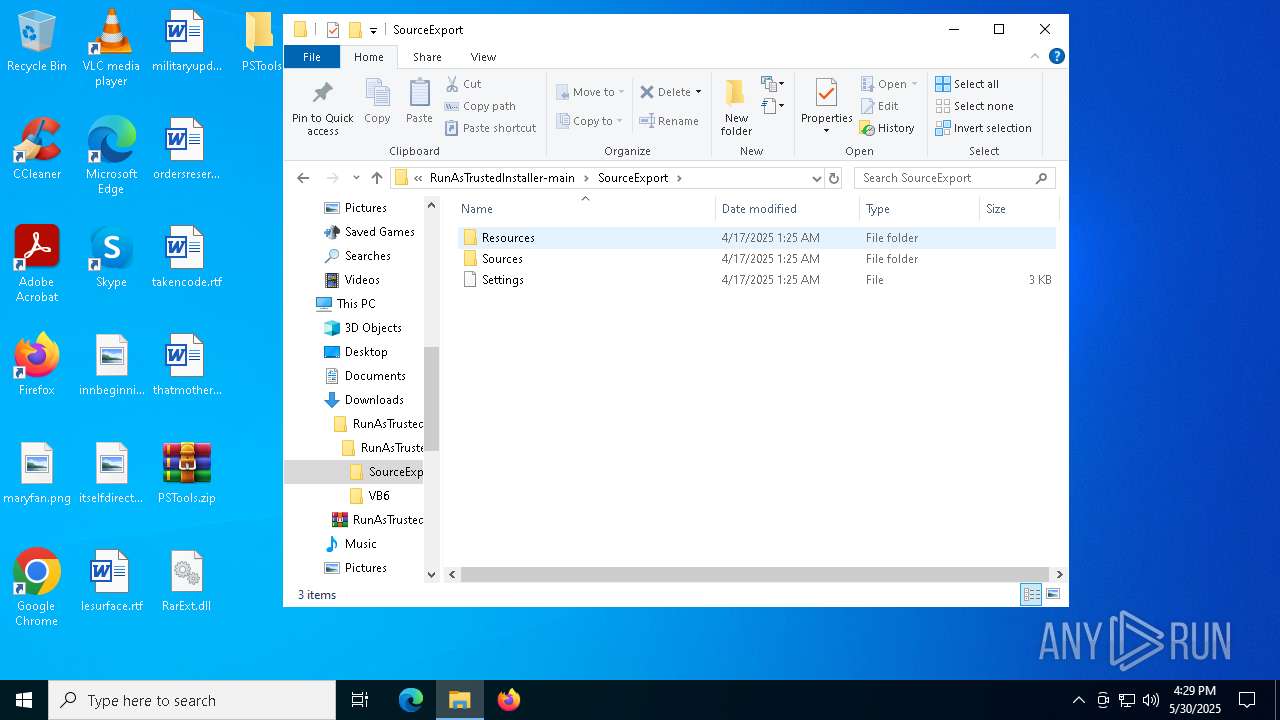
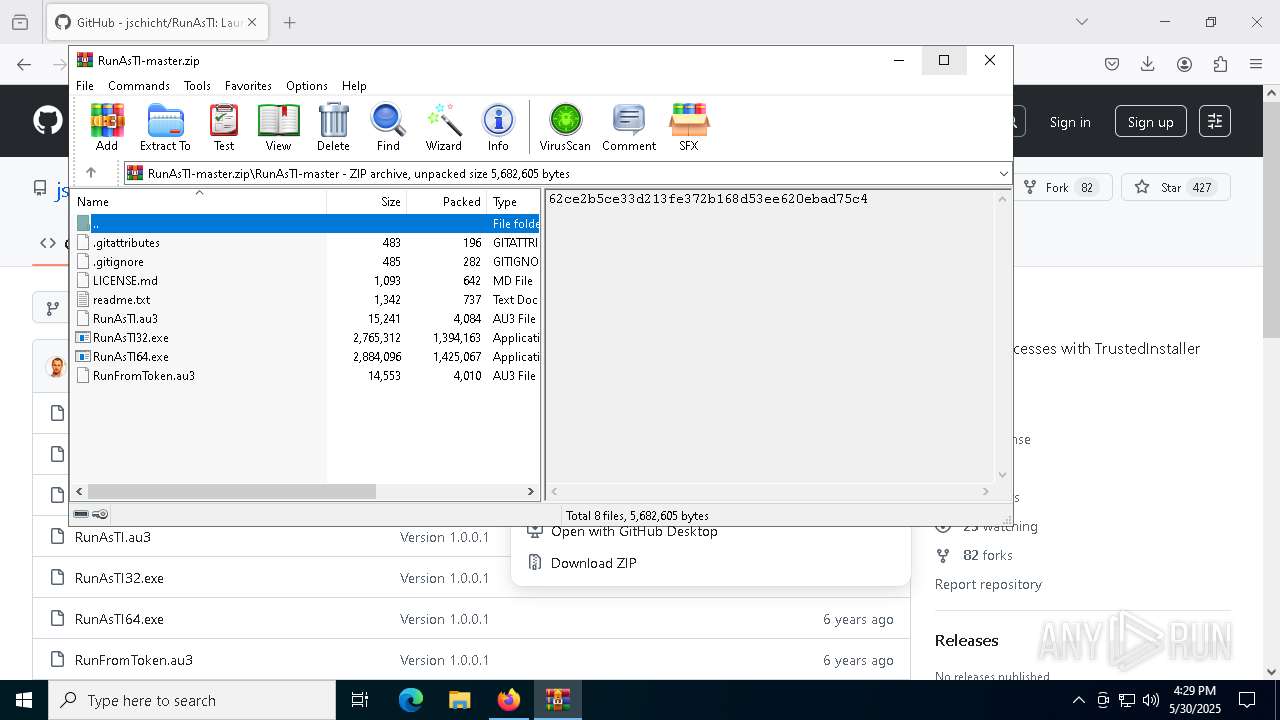
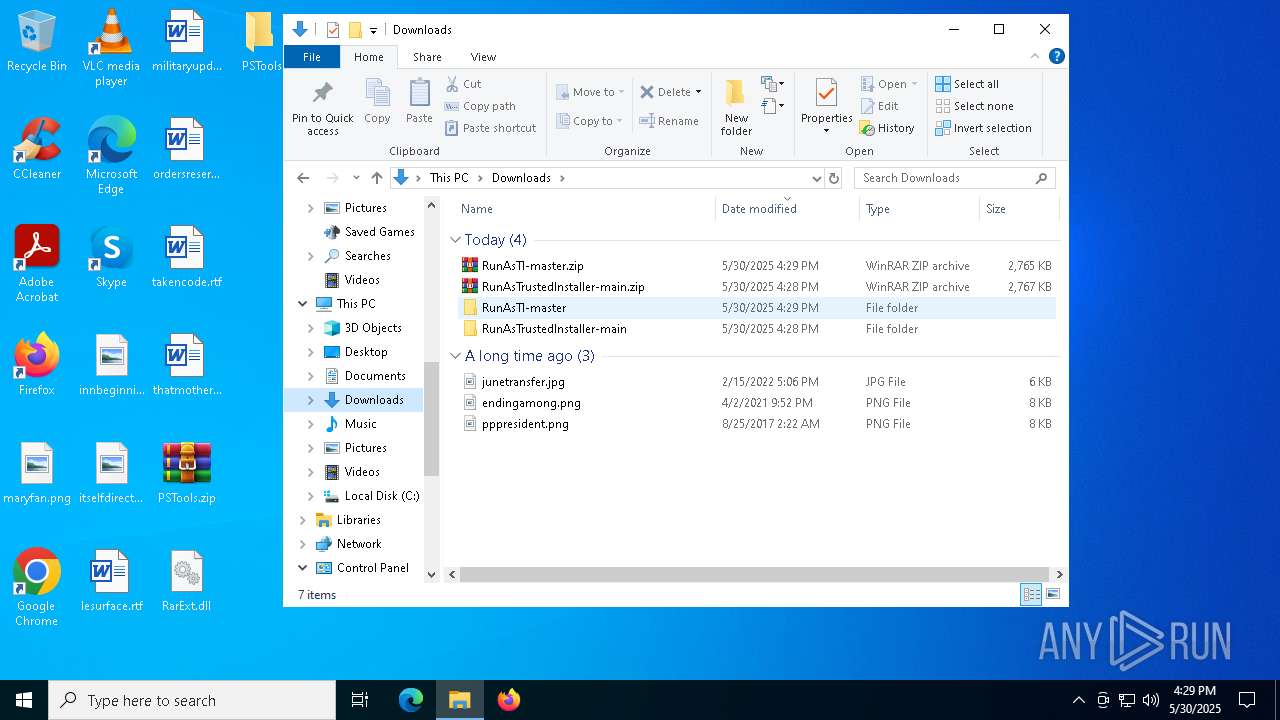
| File name: | PSTools.zip |
| Full analysis: | https://app.any.run/tasks/d85945e1-1d93-44e2-bb11-6af41718b612 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2025, 16:25:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
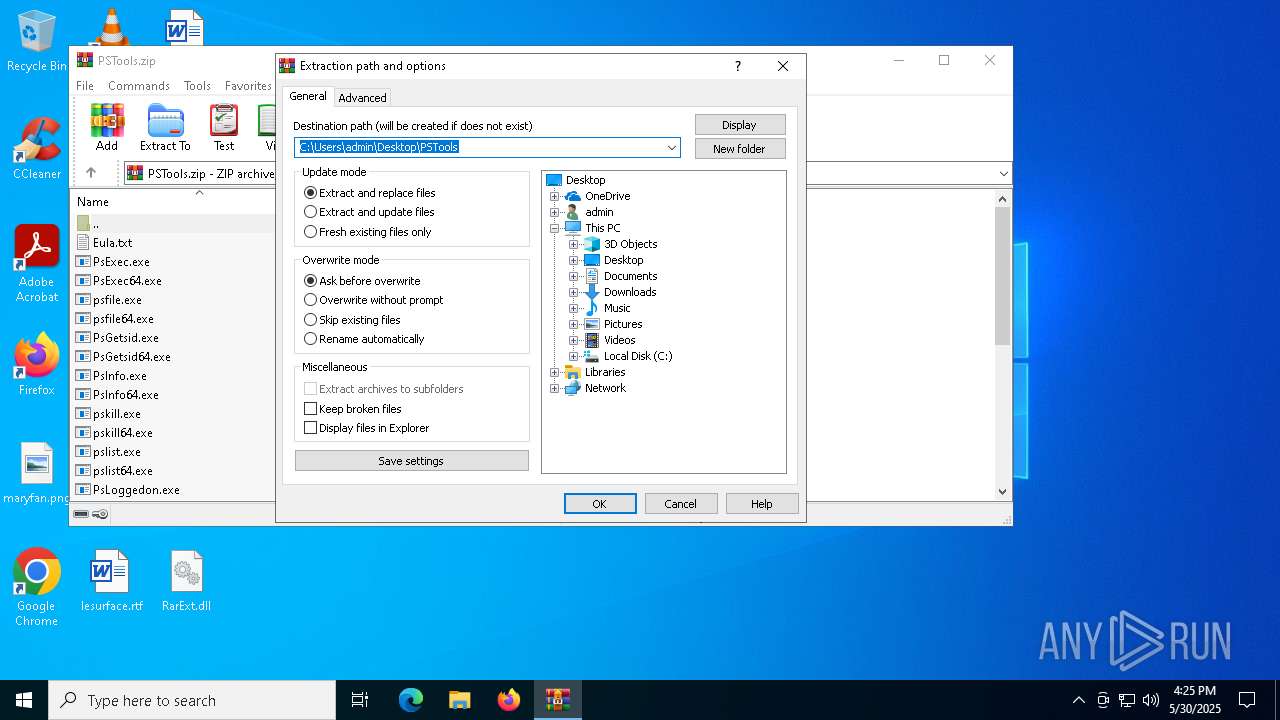
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 41EBDADC06B18164DC571F9DB251C01B |
| SHA1: | DDFB009F8B92226AA45C467F8D0EEBB29A8E2FF5 |
| SHA256: | A9CA77DFE03CE15004157727BB43BA66F00CEB215362C9B3D199F000EDAA8D61 |
| SSDEEP: | 98304:w8SK6YhPu87Ci2jqrAAQiu9fffhwqZ4qxIL48xtg6TK/nUjqbprp7sg:wU/h3h0qrAL9fCqZO1Kycbprp7P |
MALICIOUS
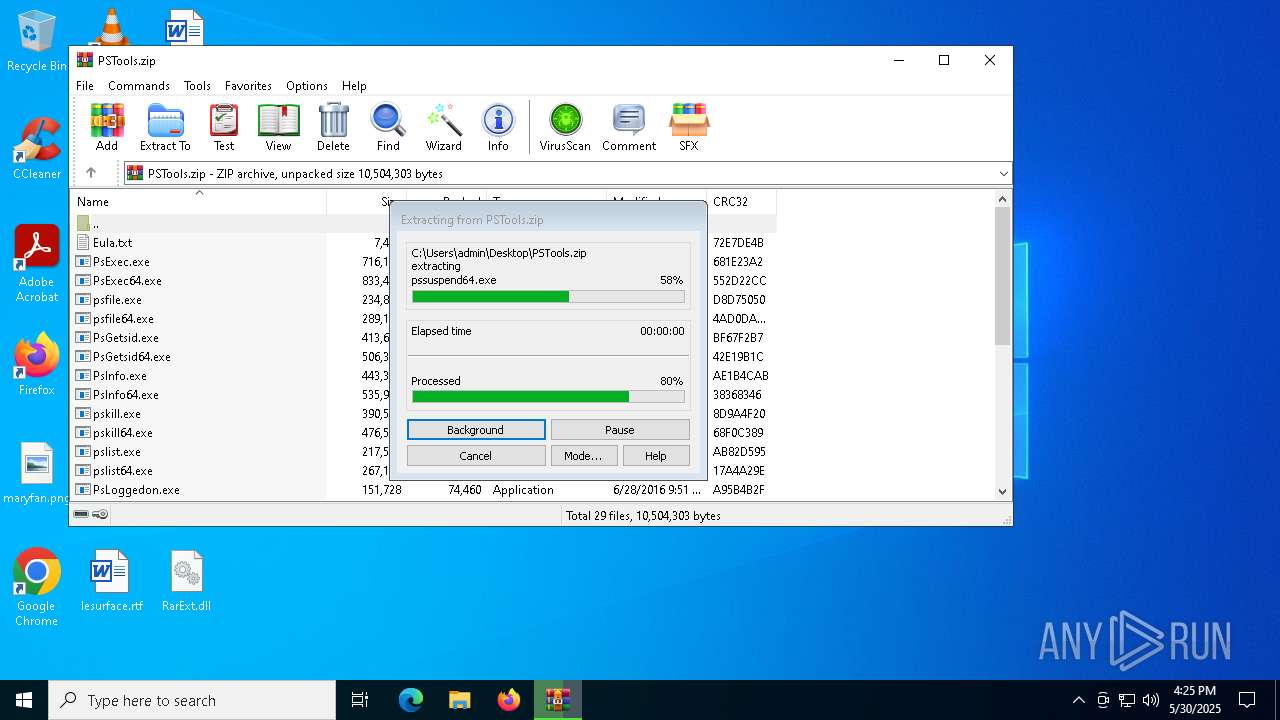
Generic archive extractor
- WinRAR.exe (PID: 1176)
SUSPICIOUS
The process creates files with name similar to system file names
- WinRAR.exe (PID: 1176)
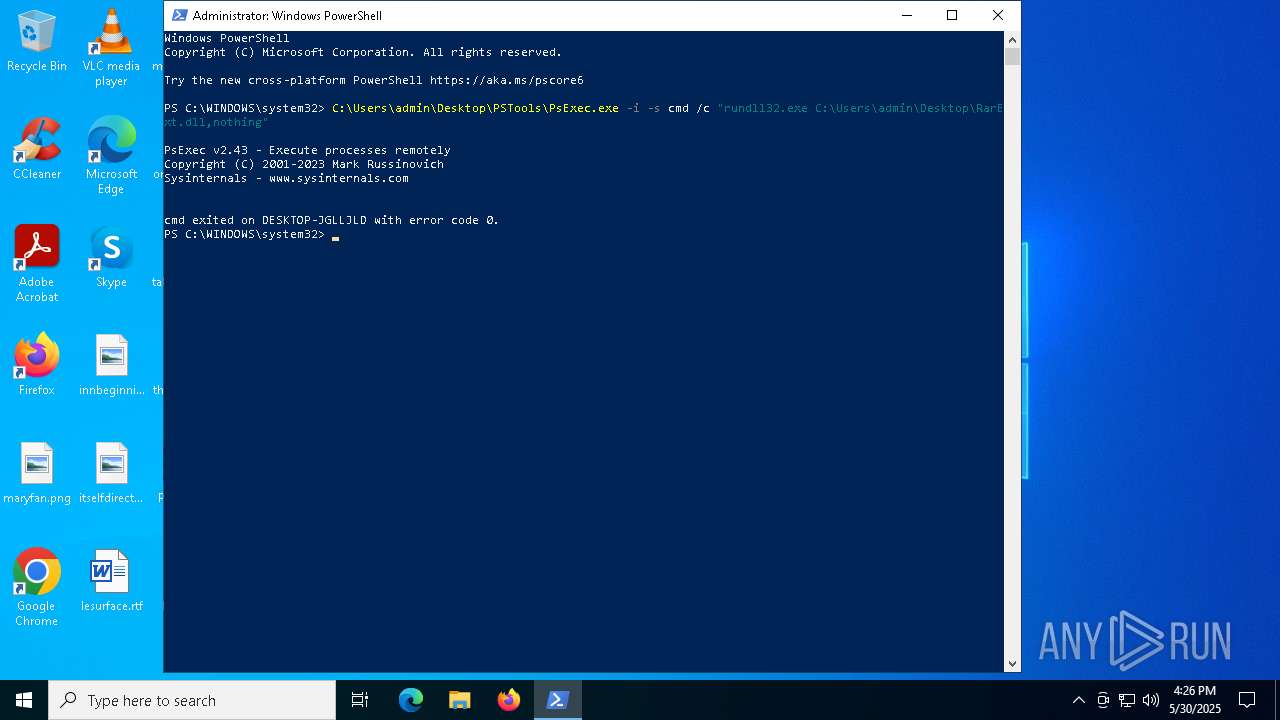
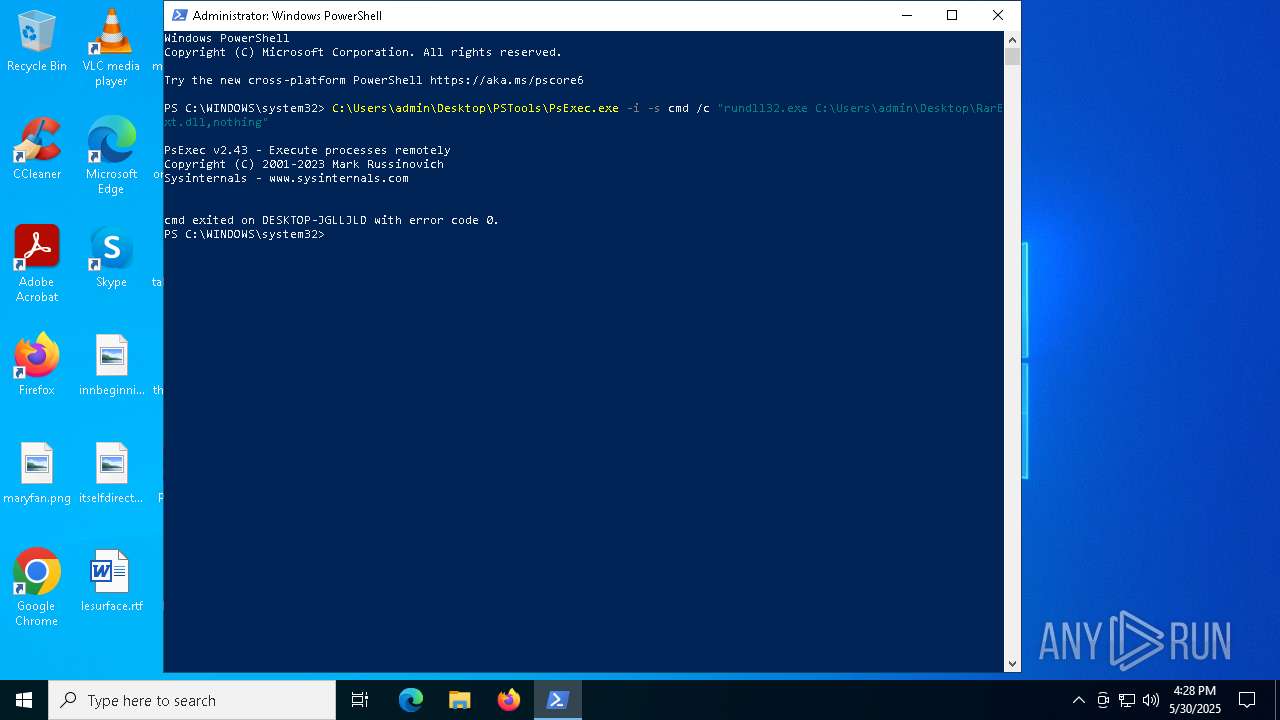
PSEXEC has been detected
- PsExec.exe (PID: 7468)
Executes as Windows Service
- PSEXESVC.exe (PID: 7776)
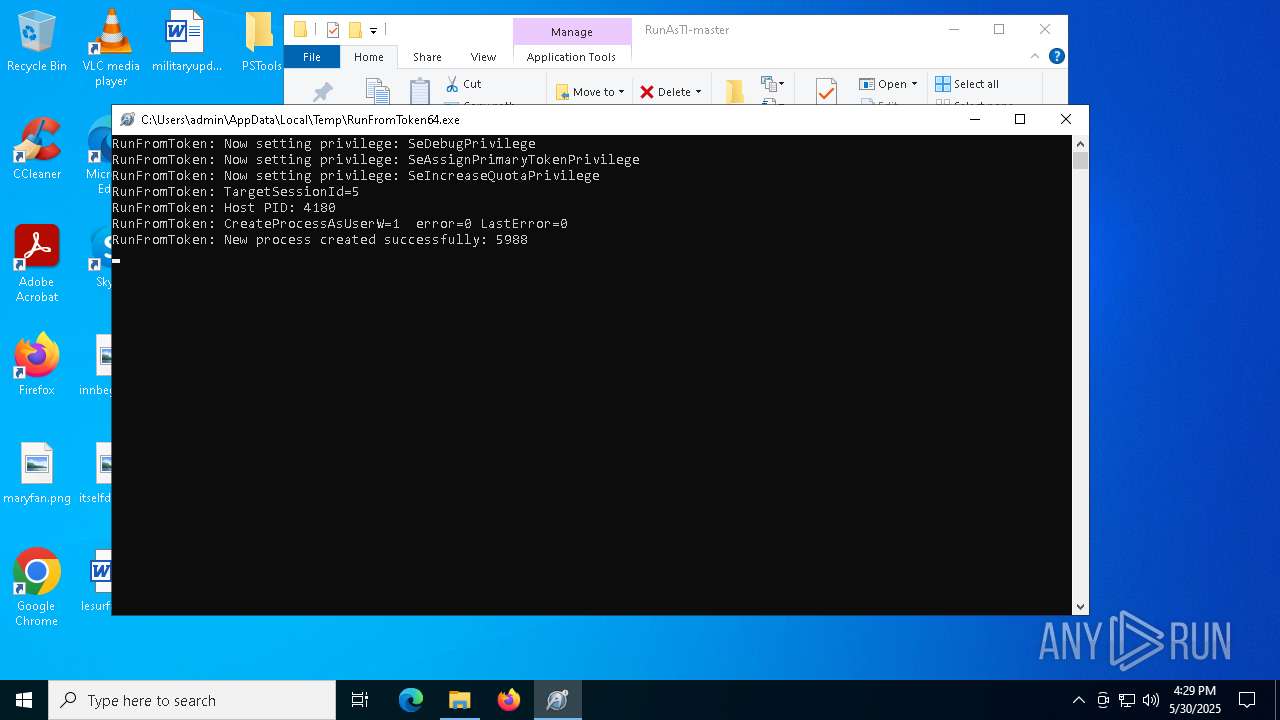
Starts CMD.EXE for commands execution
- PSEXESVC.exe (PID: 7776)
- RunAsTI64.exe (PID: 2148)
- RunFromToken64.exe (PID: 7520)
Executable content was dropped or overwritten
- PsExec.exe (PID: 7468)
- RunAsTI64.exe (PID: 2148)
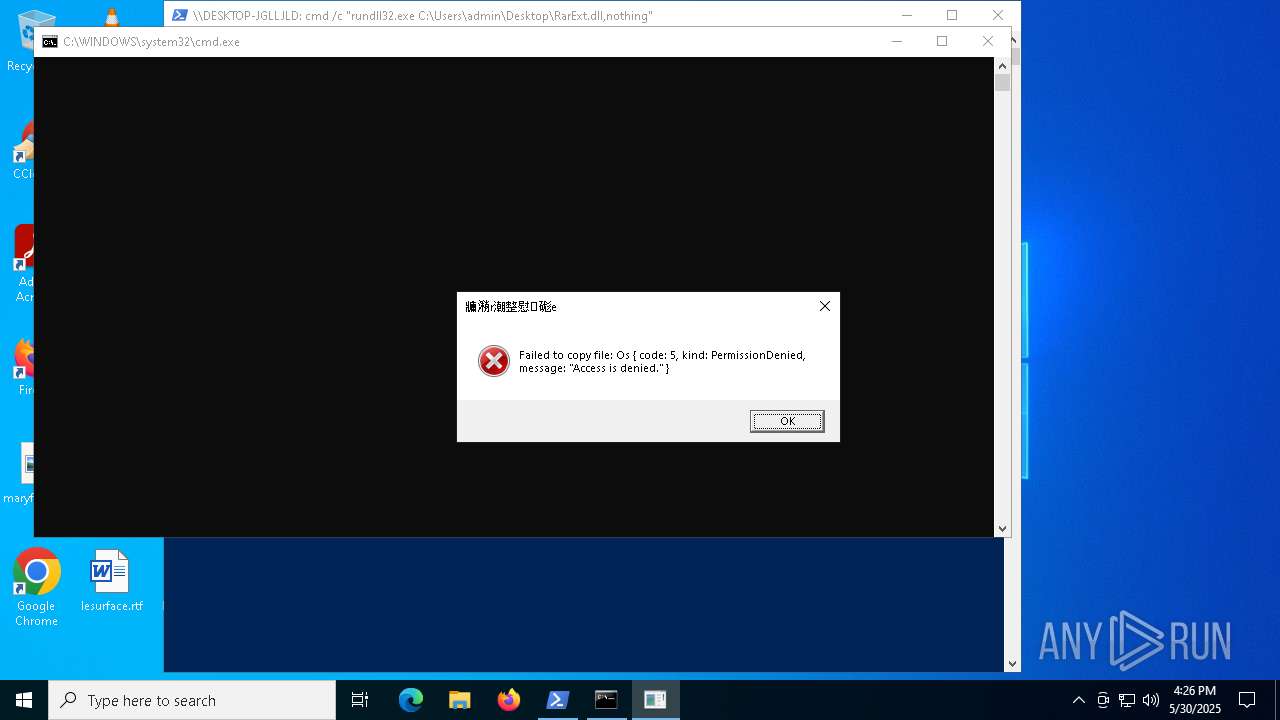
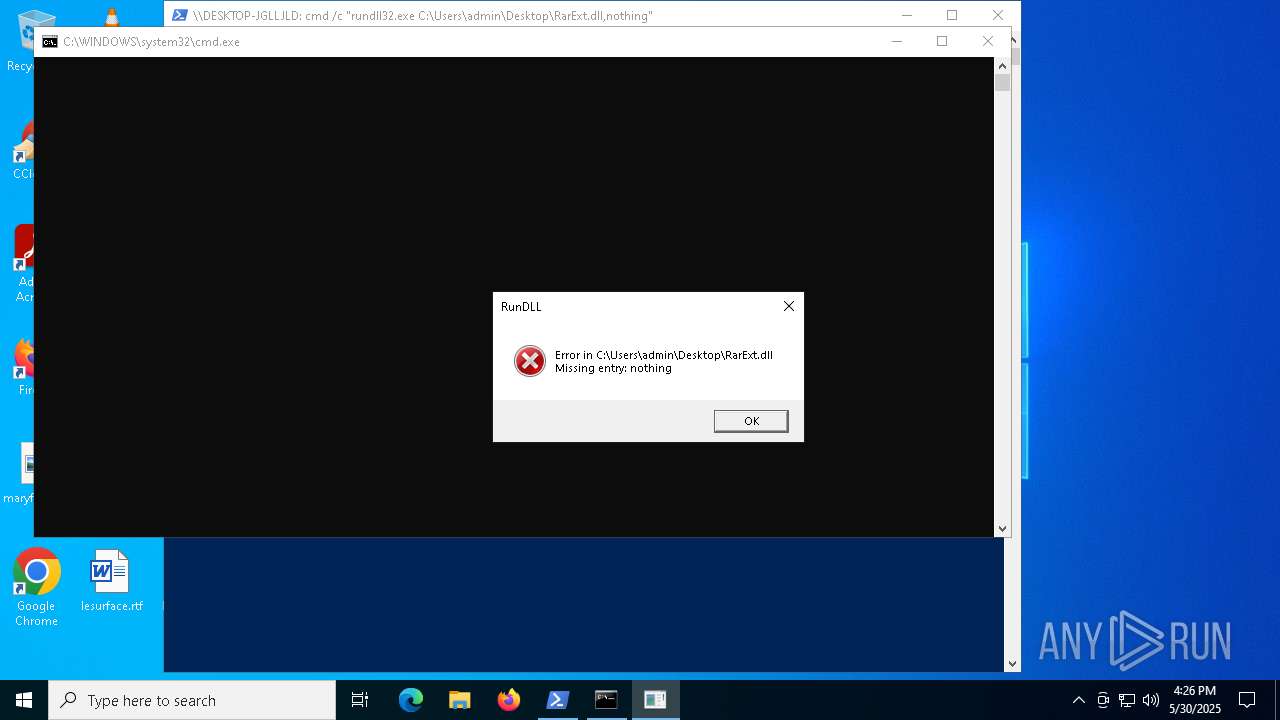
- rundll32.exe (PID: 6532)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 7940)
- cmd.exe (PID: 5988)
Application launched itself
- RunAsTI64.exe (PID: 8124)
Windows service management via SC.EXE
- sc.exe (PID: 5376)
Starts SC.EXE for service management
- cmd.exe (PID: 4844)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 1176)
- PsExec.exe (PID: 7468)
- firefox.exe (PID: 5384)
- WinRAR.exe (PID: 632)
- RunAsTI64.exe (PID: 2148)
Reads the computer name
- PsExec.exe (PID: 7468)
- PSEXESVC.exe (PID: 7776)
Manual execution by a user
- powershell.exe (PID: 2868)
- WinRAR.exe (PID: 3016)
- firefox.exe (PID: 7368)
- firefox.exe (PID: 6676)
- RunAsTI64.exe (PID: 8124)
- WinRAR.exe (PID: 632)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1176)
- WinRAR.exe (PID: 632)
Checks supported languages
- PsExec.exe (PID: 7468)
- PSEXESVC.exe (PID: 7776)
Checks current location (POWERSHELL)
- powershell.exe (PID: 2868)
Checks proxy server information
- slui.exe (PID: 7820)
Reads the software policy settings
- slui.exe (PID: 7820)
- slui.exe (PID: 7588)
Launch of the file from Downloads directory
- firefox.exe (PID: 5812)
- firefox.exe (PID: 5384)
Application launched itself
- firefox.exe (PID: 6676)
- firefox.exe (PID: 5812)
- firefox.exe (PID: 7368)
- firefox.exe (PID: 5384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:06:28 09:51:40 |
| ZipCRC: | 0xa95b4b2f |
| ZipCompressedSize: | 74460 |
| ZipUncompressedSize: | 151728 |
| ZipFileName: | PsLoggedon.exe |
Total processes
183
Monitored processes
53
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RunFromToken64.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 632 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\RunAsTI-master.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1176 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\PSTools.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1616 | "notepad.exe" | C:\Windows\System32\notepad.exe | — | rundll32.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5084 -childID 3 -isForBrowser -prefsHandle 4832 -prefMapHandle 5052 -prefsLen 31243 -prefMapSize 244583 -jsInitHandle 1460 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {071d8ca0-2ef4-4116-b32e-48868ff6cb8d} 5812 "\\.\pipe\gecko-crash-server-pipe.5812" 20dd36def50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
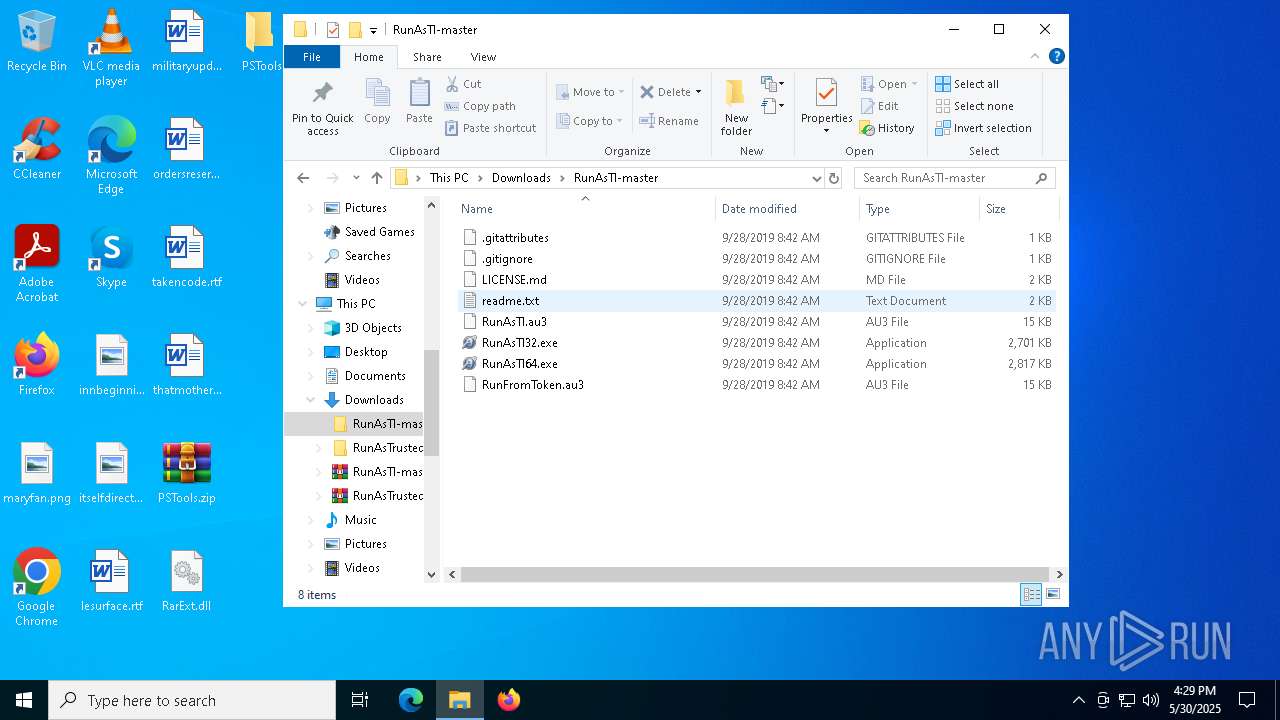
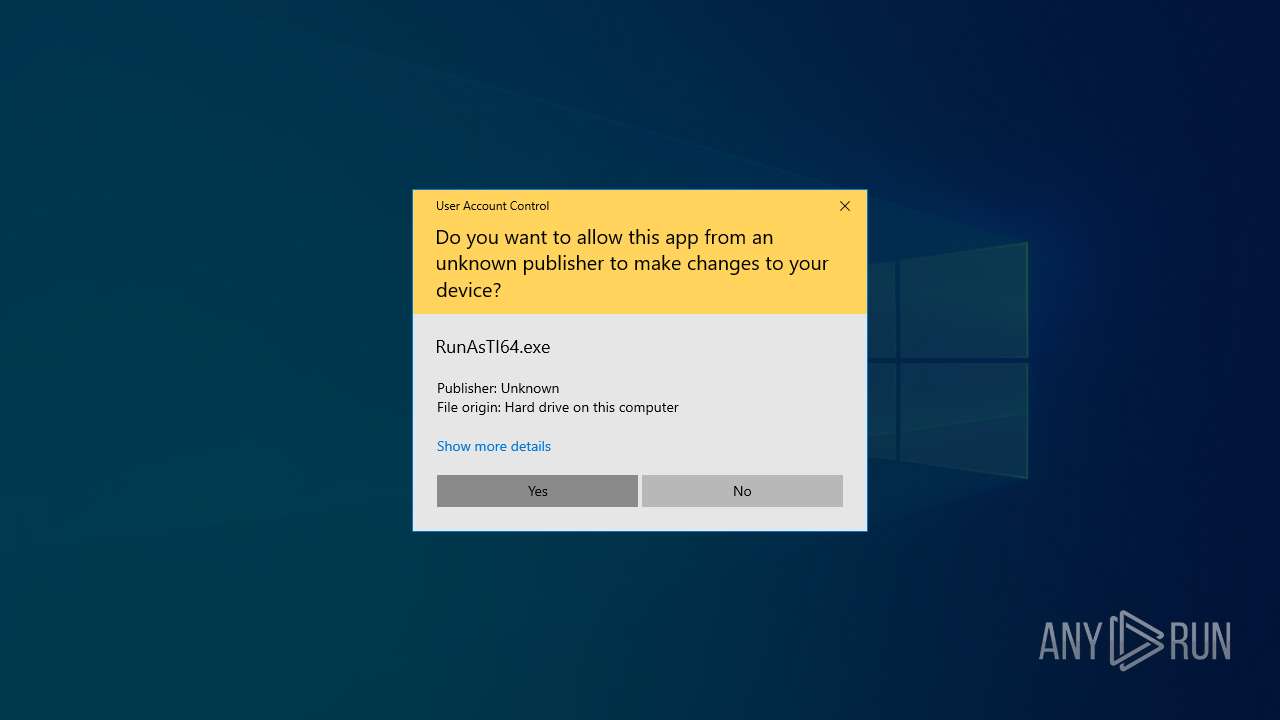
| 2148 | "C:\Users\admin\Downloads\RunAsTI-master\RunAsTI64.exe" ! | C:\Users\admin\Downloads\RunAsTI-master\RunAsTI64.exe | RunAsTI64.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Start program with same privileges as TrustedInstaller Exit code: 0 Version: 1.0.0.1 Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=4376 -childID 8 -isForBrowser -prefsHandle 5436 -prefMapHandle 4480 -prefsLen 31506 -prefMapSize 244583 -jsInitHandle 1460 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {f673f984-e21e-4a20-bffe-0195bc2a0e1b} 5812 "\\.\pipe\gecko-crash-server-pipe.5812" 20dcca3c310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 2868 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3016 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\RunAsTrustedInstaller-main.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3124 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=5660 -childID 6 -isForBrowser -prefsHandle 5700 -prefMapHandle 5696 -prefsLen 31382 -prefMapSize 244583 -jsInitHandle 1460 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {edbc37a2-d157-4ebe-8620-fee43c4cb7b7} 5384 "\\.\pipe\gecko-crash-server-pipe.5384" 226e30df310 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
Total events
41 363
Read events
41 247
Write events
80
Delete events
36
Modification events
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\PSTools.zip | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (1176) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
31
Suspicious files
217
Text files
60
Unknown types
61
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\PsLoggedon64.exe | executable | |
MD5:07ED30D2343BF8914DAAED872B681118 | SHA256:FDADB6E15C52C41A31E3C22659DD490D5B616E017D1B1AA6070008CE09ED27EA | |||
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\PsLoggedon.exe | executable | |
MD5:E3EA271E748CCDAD6A6D3E692D6F337E | SHA256:D689CB1DBD2E4C06CD15E51A6871C406C595790DDCDCD7DC8D0401C7183720EF | |||
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\psfile.exe | executable | |
MD5:A0C7585C86AB8BFE6D55A2547E7C9382 | SHA256:4243DC8B991F5F8B3C0F233CA2110A1E03A1D716C3F51E88FAF1D59B8242D329 | |||
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\PsGetsid.exe | executable | |
MD5:3D4112B92A8285D8661BBC29125BDBF5 | SHA256:A48AC157609888471BF8578FB8B2AEF6B0068F7E0742FCCF2E0E288B0B2CFDFB | |||
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\psshutdown.exe | executable | |
MD5:31E8E12D02A6CAC9088D89215CF4552C | SHA256:13FD3AD690C73CF0AD26C6716D4E9D1581B47C22FB7518B1D3BF9CFB8F9E9123 | |||
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\psfile64.exe | executable | |
MD5:880ED8C97E6BDB64A342FAD25094049B | SHA256:BE922312978A53C92A49FEFD2C9F9CC098767B36F0E4D2E829D24725DF65BC21 | |||
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\psping.exe | executable | |
MD5:93F162D9E1AE290F47695E71589FD4D4 | SHA256:355B4A82313074999BD8FA1332B1ED00034E63BD2A0D0367E2622F35D75CF140 | |||
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\psping64.exe | executable | |
MD5:AD7E3DDF557E1DE0170E384031D3A221 | SHA256:D1F718D219930E57794BDADF9DDA61406294B0759038CEF282F7544B44B92285 | |||
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\PsInfo64.exe | executable | |
MD5:86A65CFA9F258B0A46ED54E1AD235078 | SHA256:DE73B73EEB156F877DE61F4A6975D06759292ED69F31AAF06C9811F3311E03E7 | |||
| 1176 | WinRAR.exe | C:\Users\admin\Desktop\PSTools\psshutdown64.exe | executable | |
MD5:B5B4ABC85D5D8C817CE552C3C6A0ABA5 | SHA256:4226738489C2A67852D51DBF96574F33E44E509BC265B950D495DA79BB457400 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
53
TCP/UDP connections
181
DNS requests
207
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5812 | firefox.exe | POST | — | 142.250.185.163:80 | http://o.pki.goog/s/wr3/3H4 | unknown | — | — | whitelisted |
5812 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
5812 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
5812 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
5812 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
5812 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
5812 | firefox.exe | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/we2 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7308 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
5496 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2516 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |