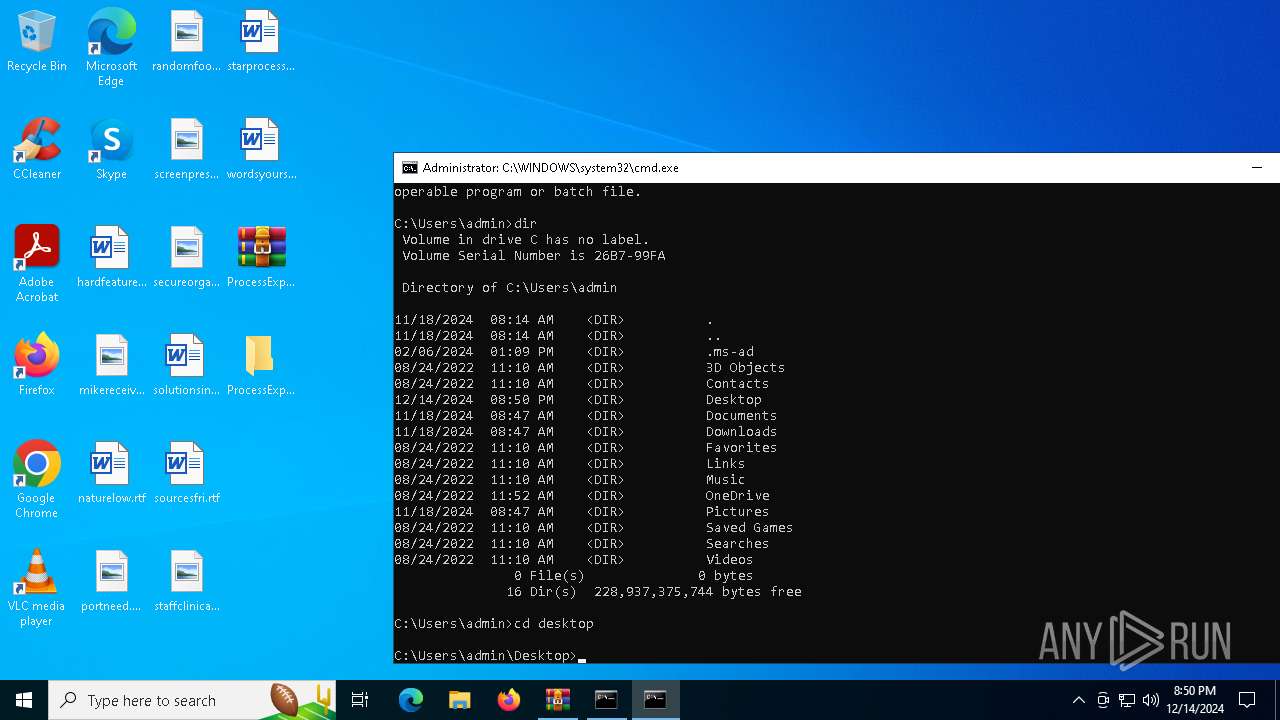
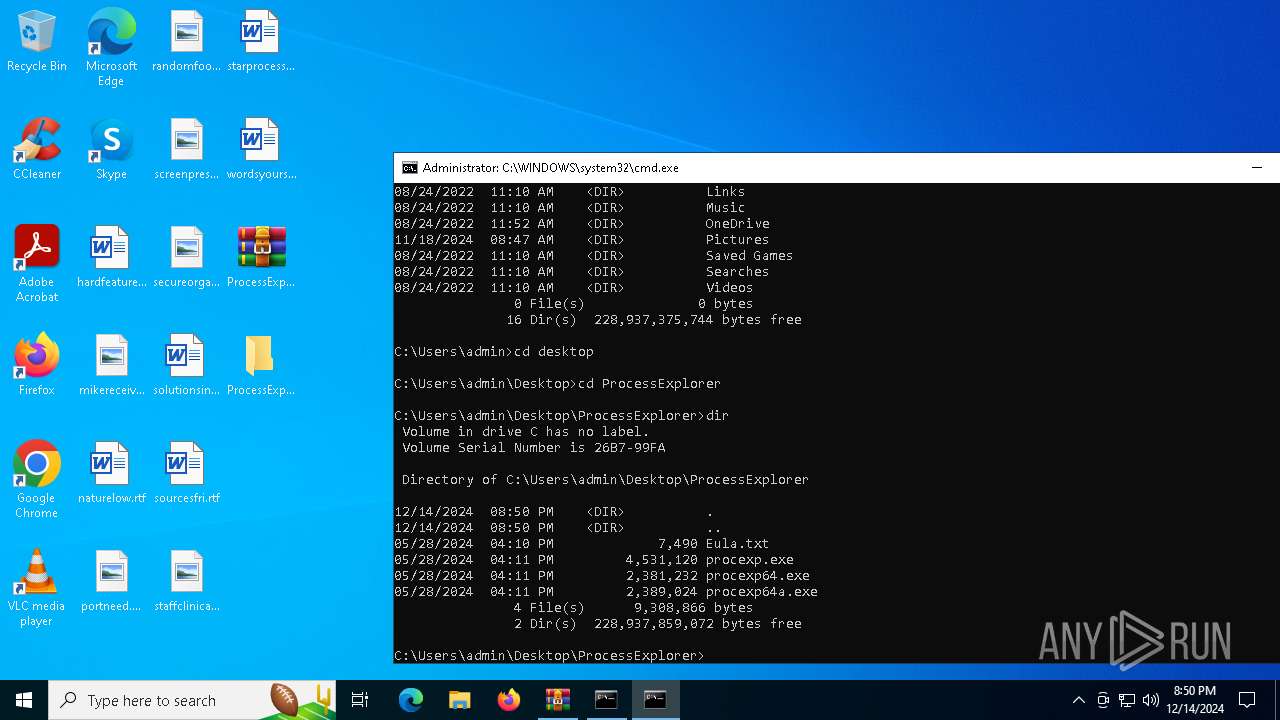
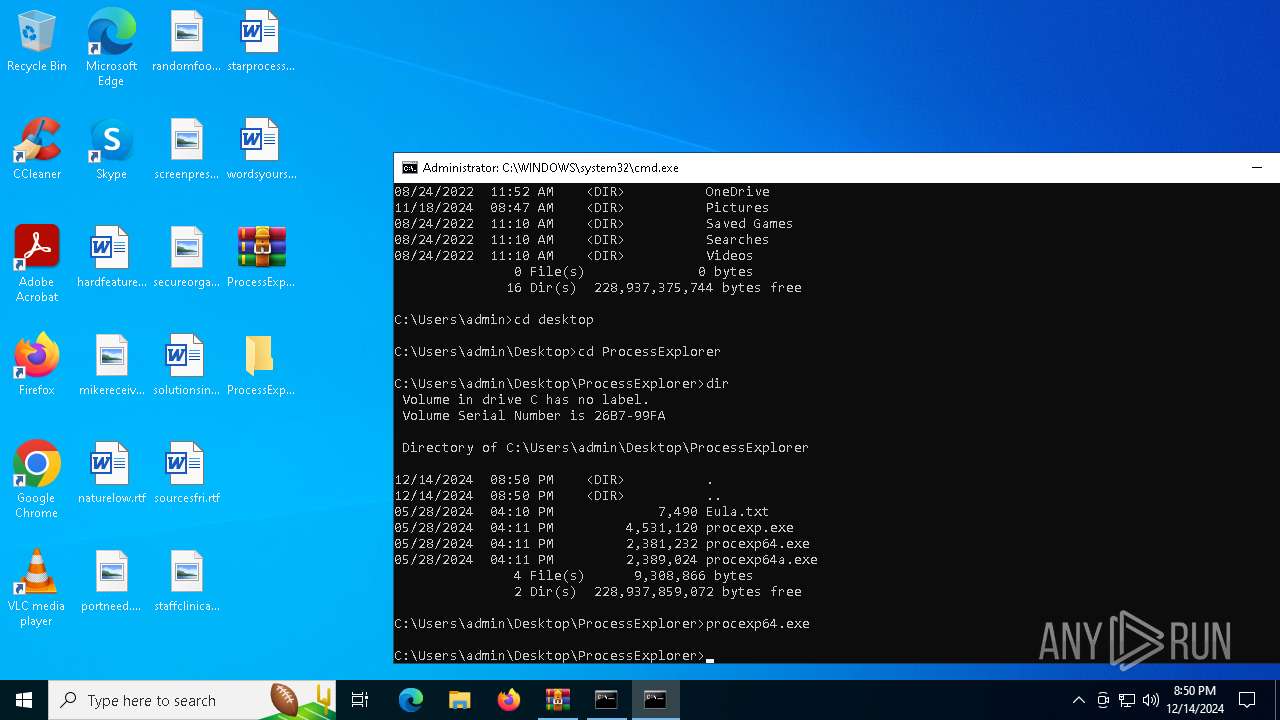
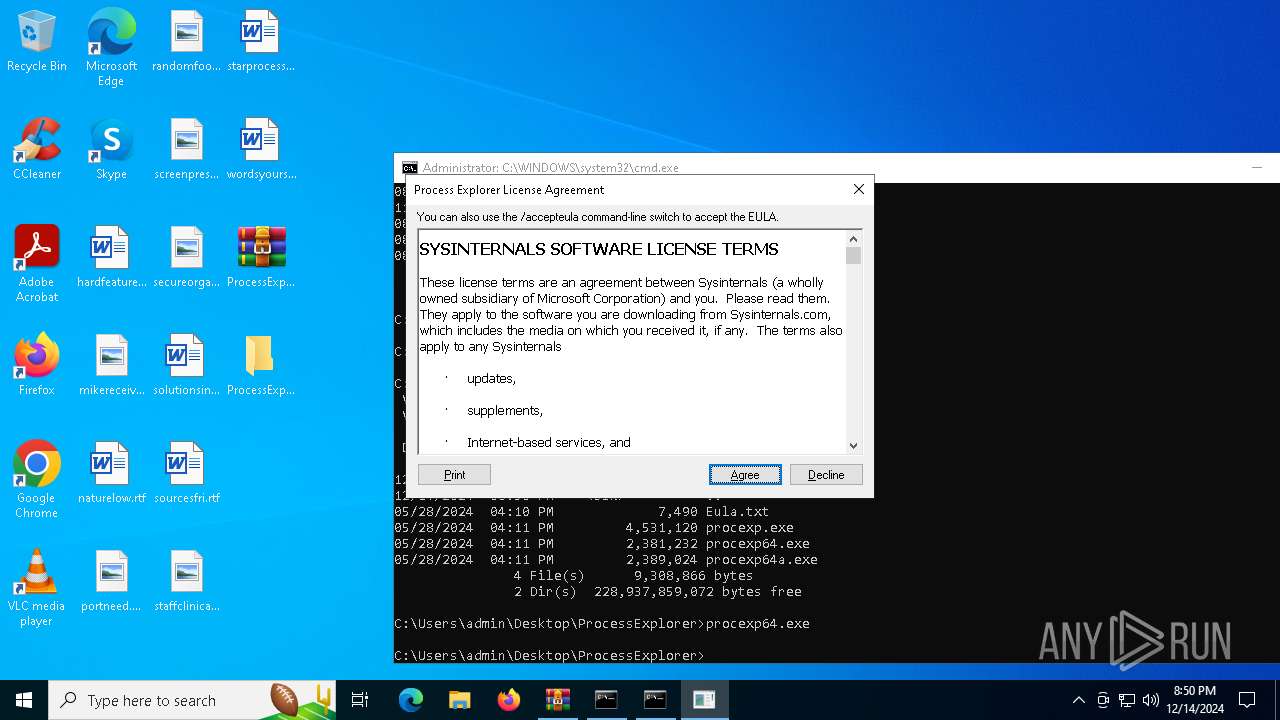
| File name: | PSTools.zip |
| Full analysis: | https://app.any.run/tasks/48535b93-d163-4519-bfa1-503ea57a7db0 |
| Verdict: | Malicious activity |
| Analysis date: | December 14, 2024, 20:49:01 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 41EBDADC06B18164DC571F9DB251C01B |
| SHA1: | DDFB009F8B92226AA45C467F8D0EEBB29A8E2FF5 |
| SHA256: | A9CA77DFE03CE15004157727BB43BA66F00CEB215362C9B3D199F000EDAA8D61 |
| SSDEEP: | 98304:w8SK6YhPu87Ci2jqrAAQiu9fffhwqZ4qxIL48xtg6TK/nUjqbprp7sg:wU/h3h0qrAL9fCqZO1Kycbprp7P |
MALICIOUS
No malicious indicators.SUSPICIOUS
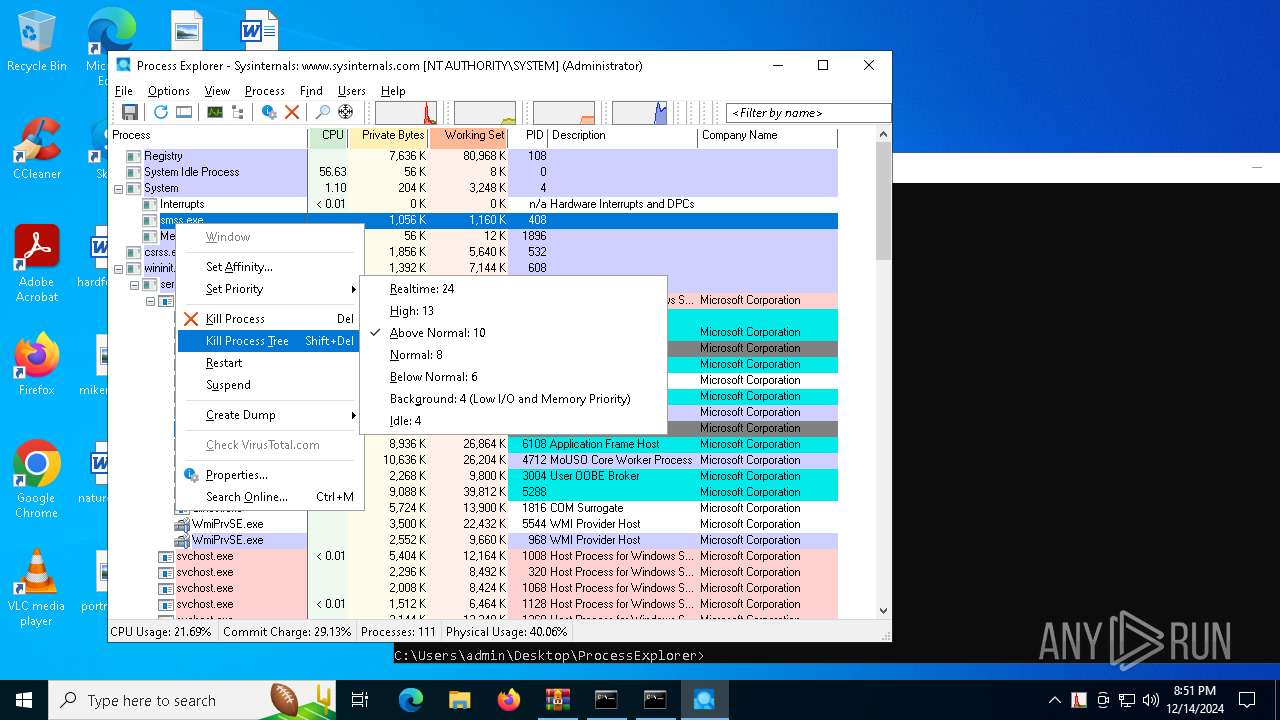
Executes as Windows Service
- PSEXESVC.exe (PID: 7000)
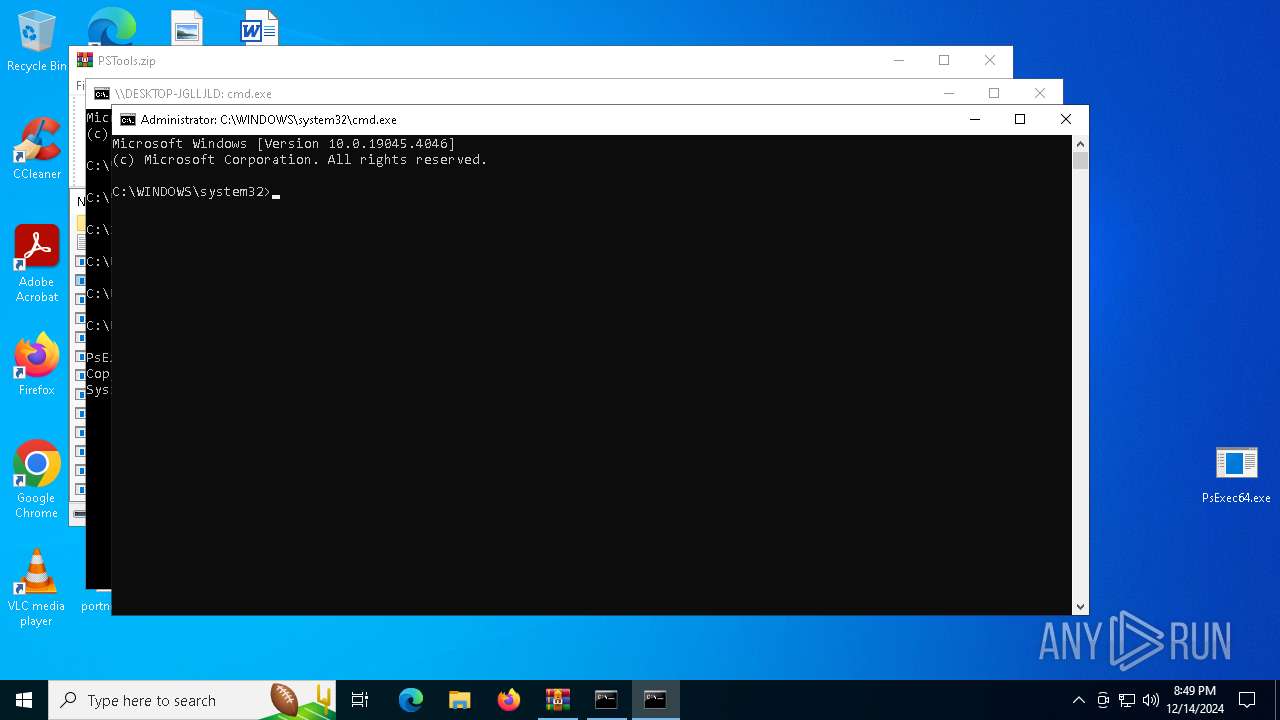
PSEXEC has been detected
- PsExec64.exe (PID: 5536)
- PsExec64.exe (PID: 6976)
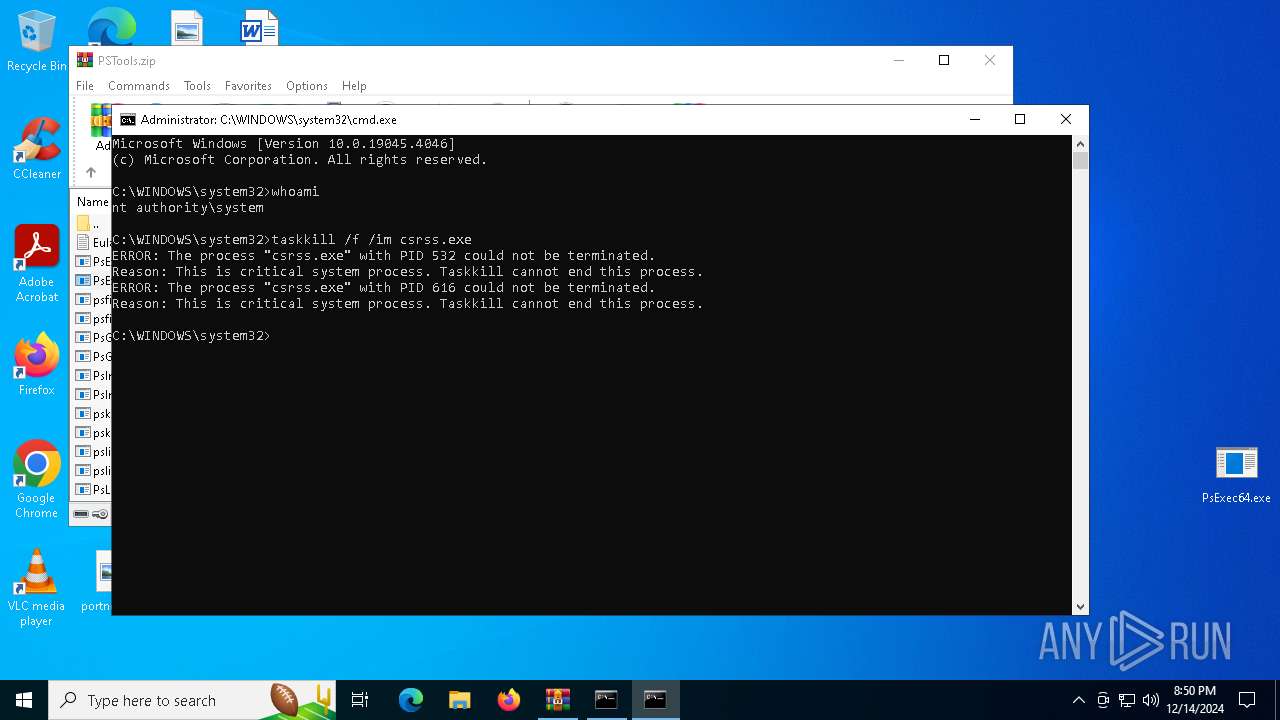
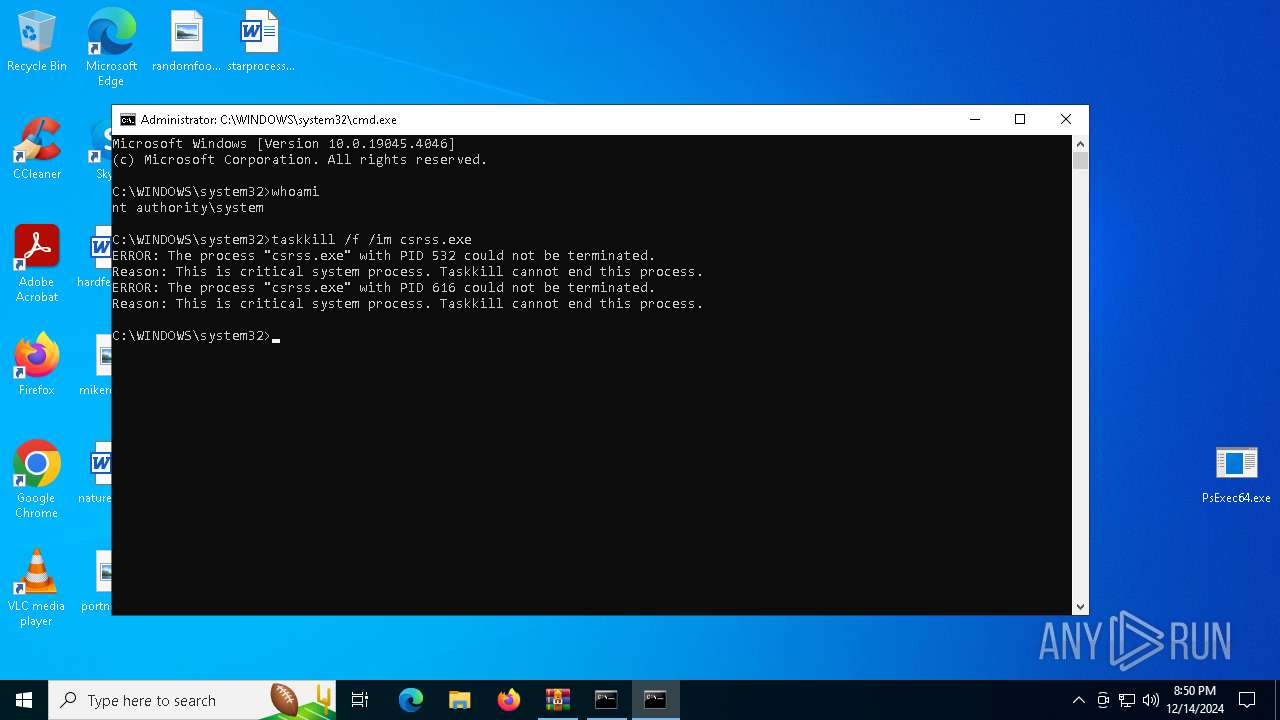
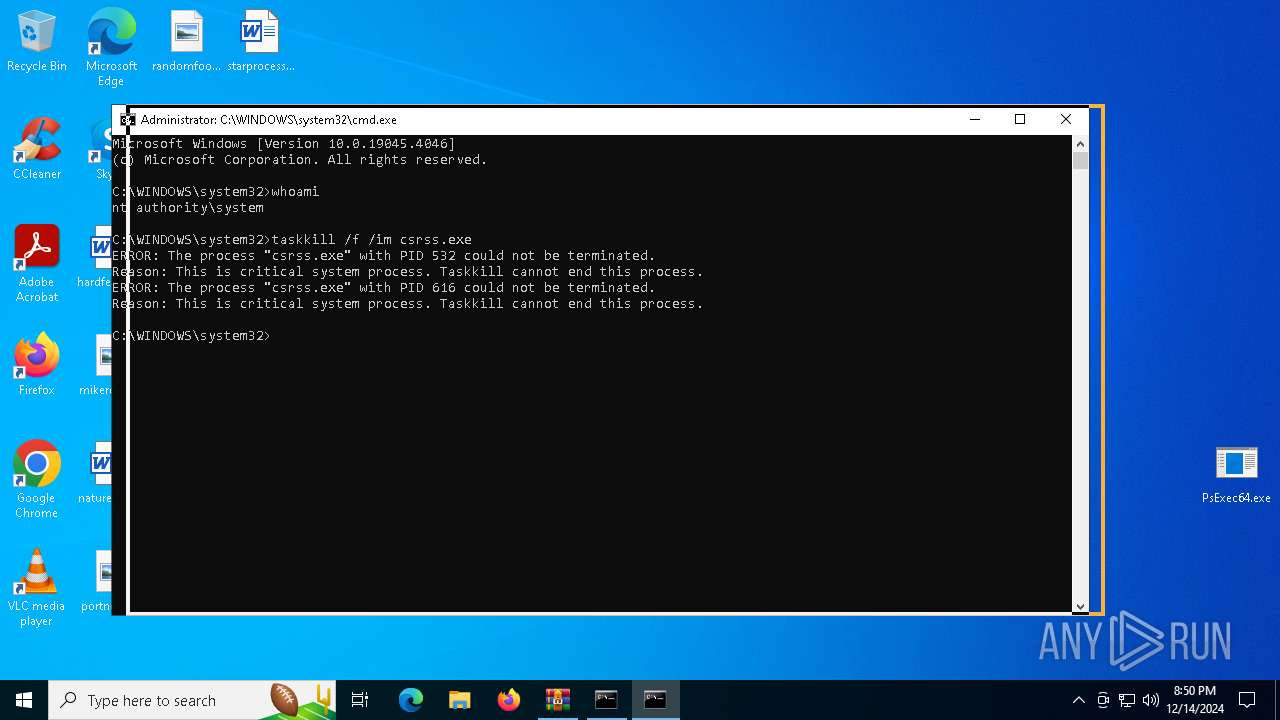
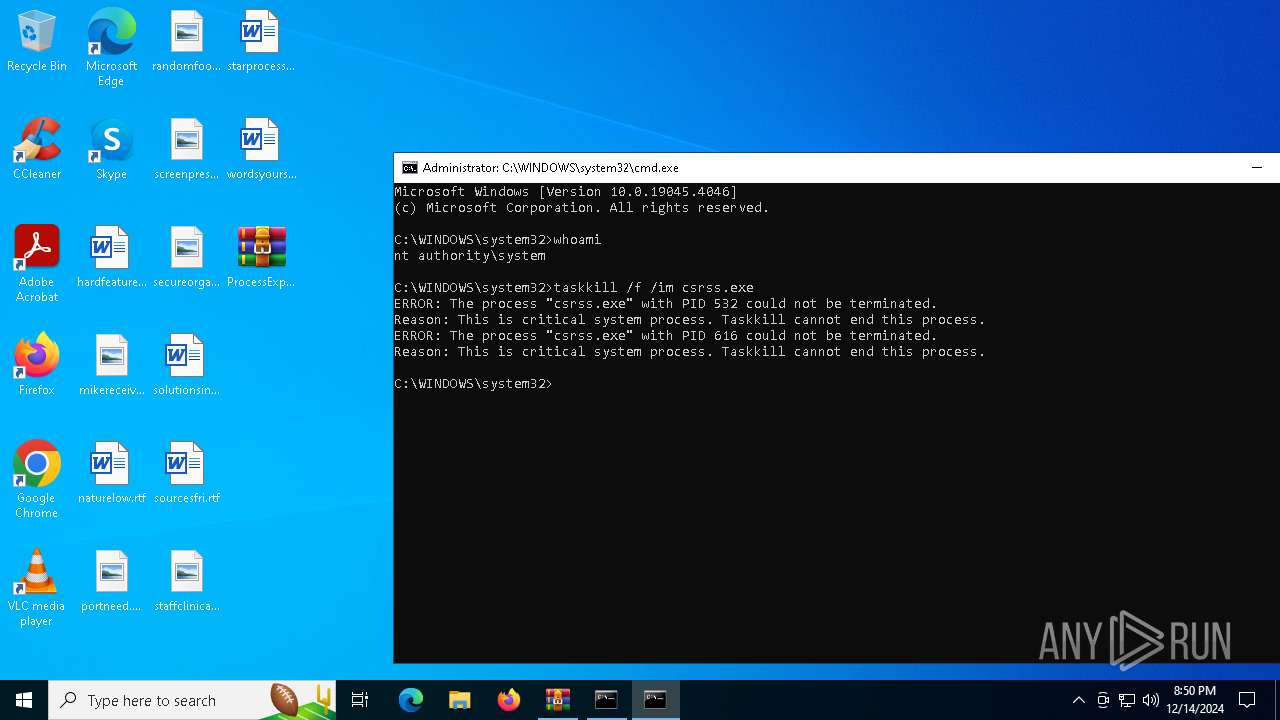
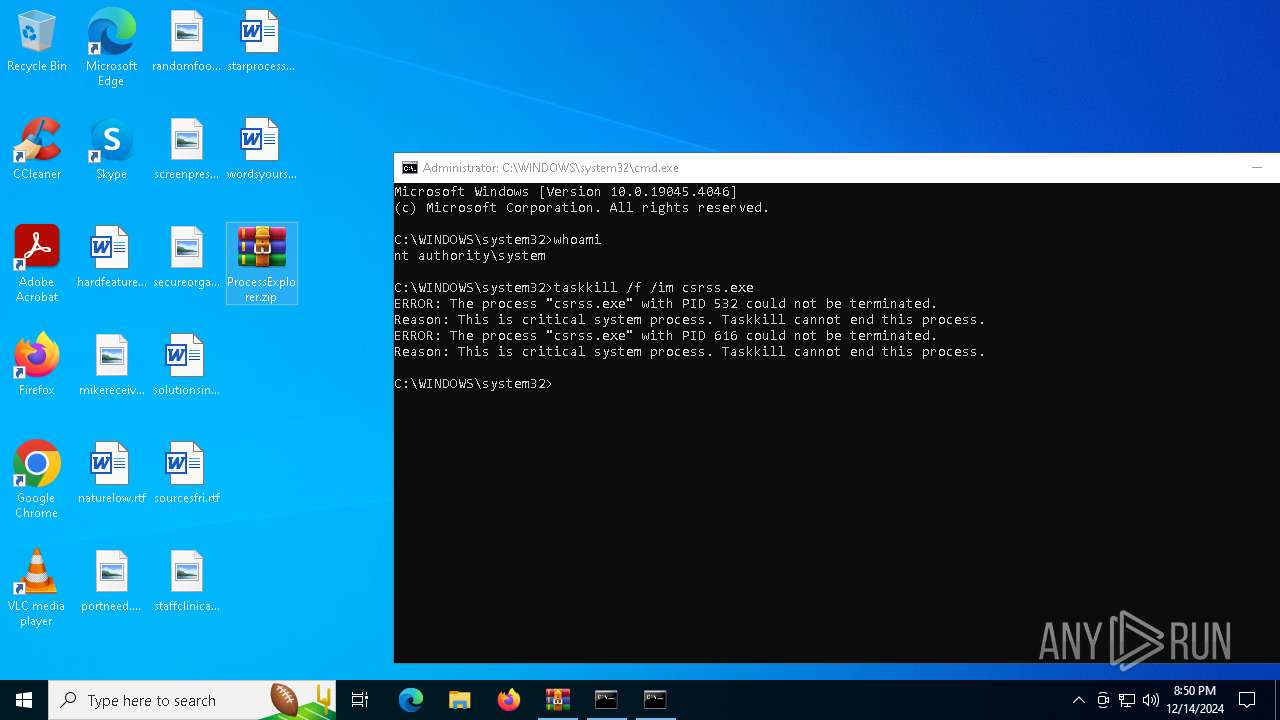
Identifying current user with WHOAMI command
- cmd.exe (PID: 7020)
- cmd.exe (PID: 1380)
Starts CMD.EXE for commands execution
- PSEXESVC.exe (PID: 7000)
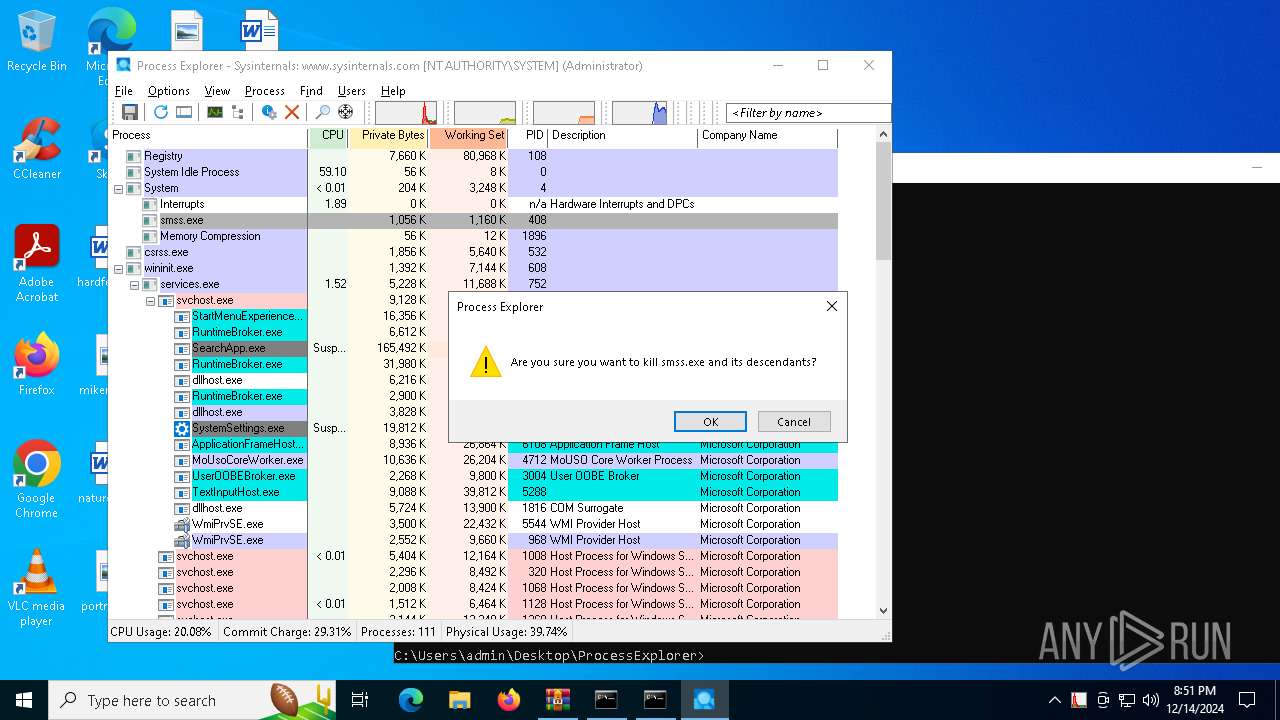
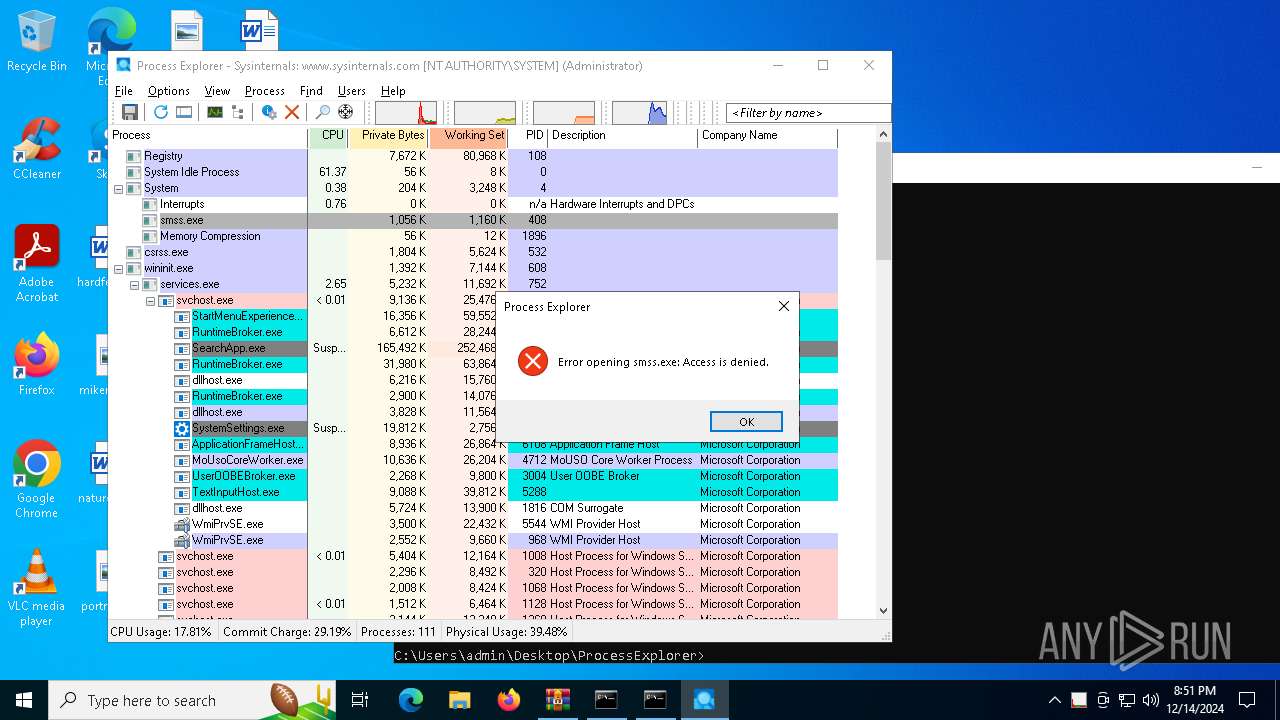
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 1380)
Creates or modifies Windows services
- procexp64.exe (PID: 3772)
The process checks if it is being run in the virtual environment
- procexp64.exe (PID: 3772)
Executable content was dropped or overwritten
- procexp64.exe (PID: 3772)
- PsExec64.exe (PID: 6976)
Creates files in the driver directory
- procexp64.exe (PID: 3772)
Drops a system driver (possible attempt to evade defenses)
- procexp64.exe (PID: 3772)
Reads security settings of Internet Explorer
- procexp64.exe (PID: 3772)
Adds/modifies Windows certificates
- procexp64.exe (PID: 3772)
Checks Windows Trust Settings
- procexp64.exe (PID: 3772)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5092)
- PsExec64.exe (PID: 6976)
- WinRAR.exe (PID: 4164)
- procexp64.exe (PID: 3772)
Checks supported languages
- PsExec64.exe (PID: 6976)
- SearchApp.exe (PID: 5064)
- PsExec64.exe (PID: 5536)
- PSEXESVC.exe (PID: 7000)
- procexp64.exe (PID: 3772)
Reads the computer name
- PSEXESVC.exe (PID: 7000)
- procexp64.exe (PID: 3772)
- PsExec64.exe (PID: 5536)
- PsExec64.exe (PID: 6976)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5064)
- procexp64.exe (PID: 3772)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5092)
- WinRAR.exe (PID: 4164)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
The process uses the downloaded file
- WinRAR.exe (PID: 5092)
- WinRAR.exe (PID: 4164)
Manual execution by a user
- cmd.exe (PID: 7020)
- WinRAR.exe (PID: 4164)
- cmd.exe (PID: 6692)
Reads Environment values
- procexp64.exe (PID: 3772)
Reads product name
- procexp64.exe (PID: 3772)
Reads the software policy settings
- procexp64.exe (PID: 3772)
- SearchApp.exe (PID: 5064)
Reads the time zone
- procexp64.exe (PID: 3772)
Reads CPU info
- procexp64.exe (PID: 3772)
Reads Microsoft Office registry keys
- procexp64.exe (PID: 3772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2016:06:28 09:51:40 |
| ZipCRC: | 0xa95b4b2f |
| ZipCompressedSize: | 74460 |
| ZipUncompressedSize: | 151728 |
| ZipFileName: | PsLoggedon.exe |
Total processes
146
Monitored processes
16
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 644 | whoami | C:\Windows\System32\whoami.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: whoami - displays logged on user information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1380 | "cmd.exe" | C:\Windows\System32\cmd.exe | — | PSEXESVC.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
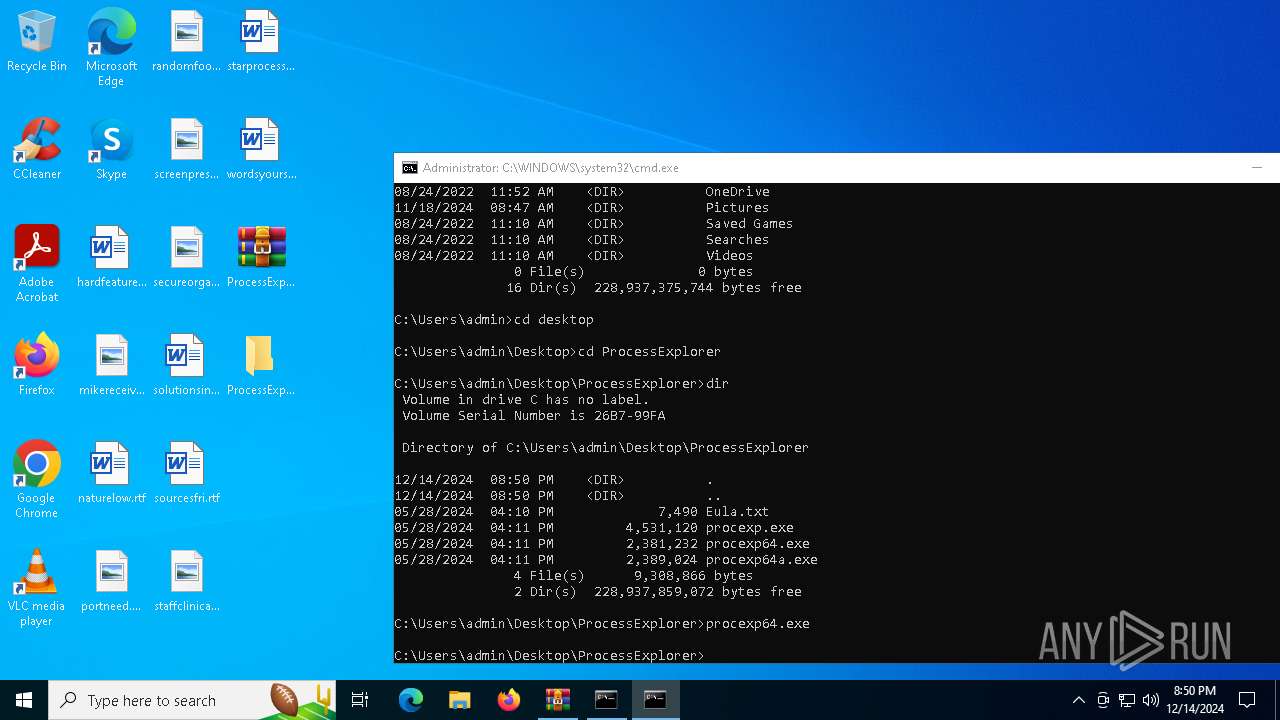
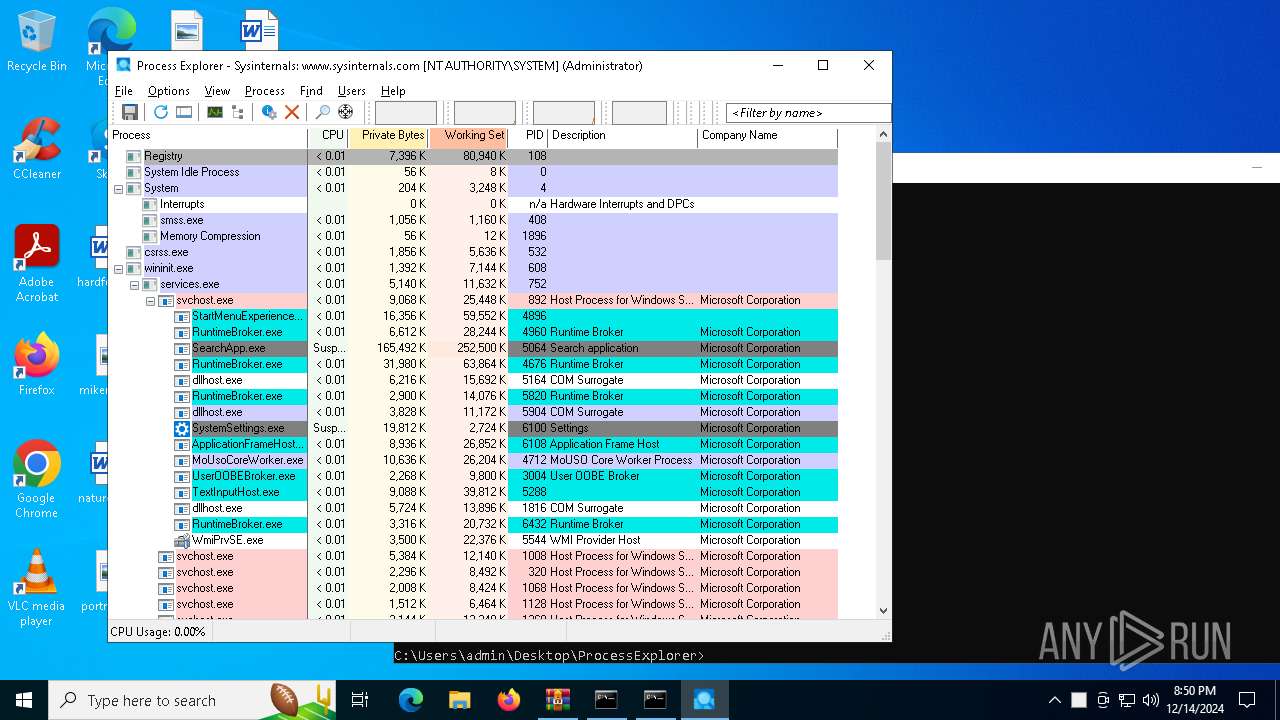
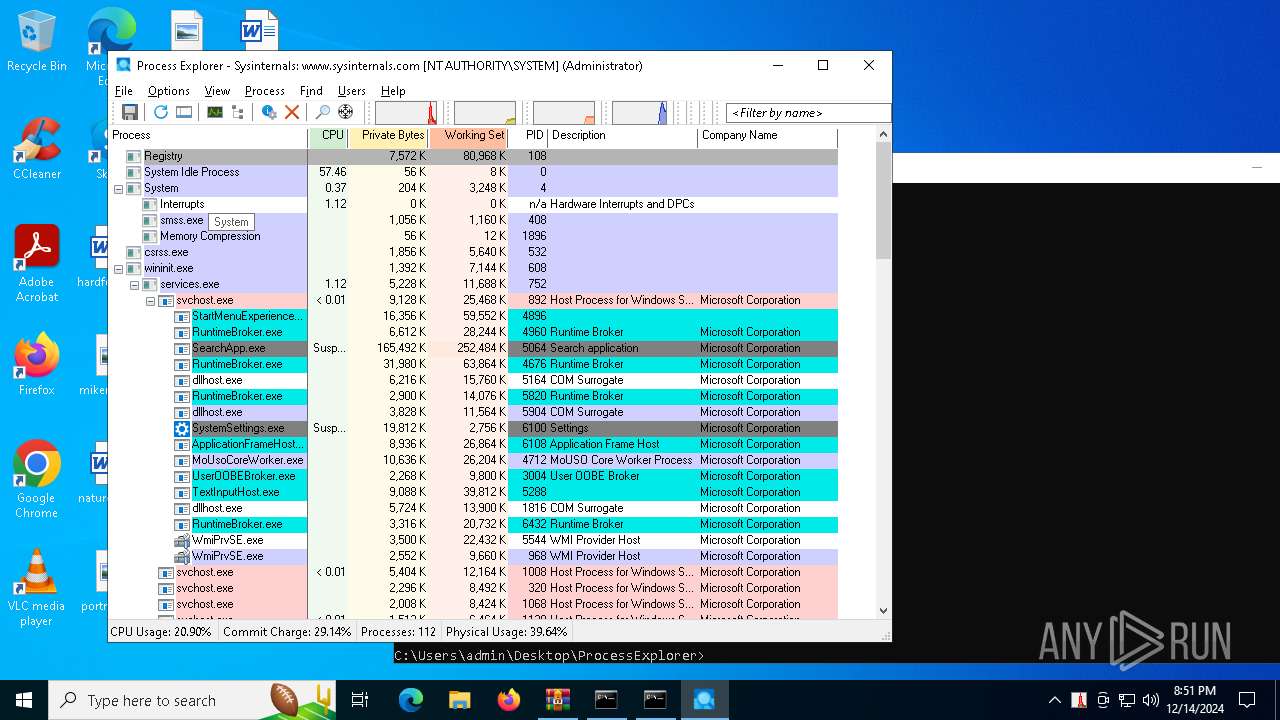
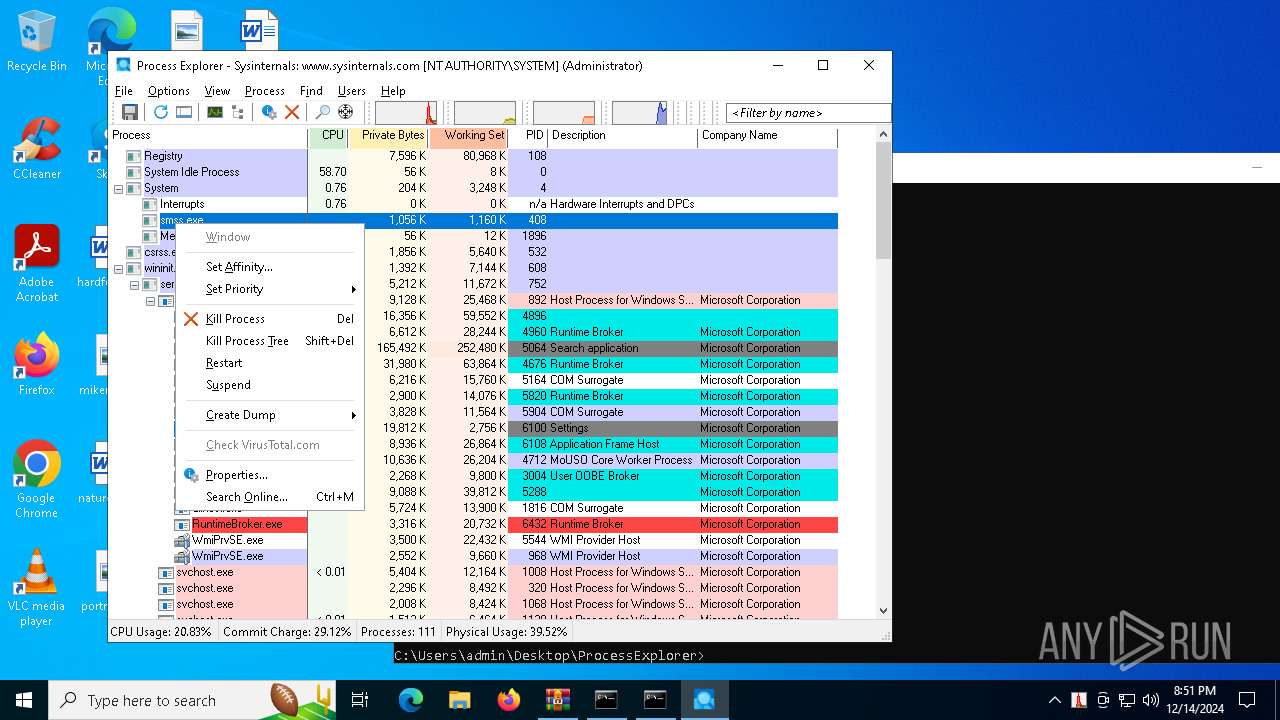
| 3772 | procexp64.exe | C:\Users\admin\Desktop\ProcessExplorer\procexp64.exe | cmd.exe | ||||||||||||
User: SYSTEM Company: Sysinternals - www.sysinternals.com Integrity Level: SYSTEM Description: Sysinternals Process Explorer Version: 17.06 Modules
| |||||||||||||||
| 3992 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4164 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\ProcessExplorer.zip" C:\Users\admin\Desktop\ProcessExplorer\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5092 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\PSTools.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5536 | PsExec64.exe -s -i cmd.exe | C:\Users\admin\Desktop\PsExec64.exe | cmd.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Execute processes remotely Exit code: 5 Version: 2.43 Modules
| |||||||||||||||
| 6204 | taskkill /f /im csrss.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Terminates Processes Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6568 | whoami | C:\Windows\System32\whoami.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: whoami - displays logged on user information Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
43 335
Read events
43 185
Write events
141
Delete events
9
Modification events
| (PID) Process: | (5092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\PSTools.zip | |||
| (PID) Process: | (5092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicText |
Value: | |||
| (PID) Process: | (5064) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | DynamicTextTruncated |
Value: | |||
Executable files
8
Suspicious files
120
Text files
219
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133786829593171106.txt~RF138197.TMP | — | |
MD5:— | SHA256:— | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{ca30f373-f96a-4d08-b3ee-91b6e01c109a}\0.2.filtertrie.intermediate.txt | text | |
MD5:C204E9FAAF8565AD333828BEFF2D786E | SHA256:D65B6A3BF11A27A1CED1F7E98082246E40CF01289FD47FE4A5ED46C221F2F73F | |||
| 5092 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5092.16653\PsExec64.exe | executable | |
MD5:DB89EC570E6281934A5C5FCF7F4C8967 | SHA256:EDFAE1A69522F87B12C6DAC3225D930E4848832E3C551EE1E7D31736BF4525EF | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{ca30f373-f96a-4d08-b3ee-91b6e01c109a}\0.1.filtertrie.intermediate.txt | text | |
MD5:34BD1DFB9F72CF4F86E6DF6DA0A9E49A | SHA256:8E1E6A3D56796A245D0C7B0849548932FEE803BBDB03F6E289495830E017F14C | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\9mPvCZxJ_M6qXqPOckJnlPKda1w[1].js | binary | |
MD5:D311944C8E8FD4D967010526ED103B12 | SHA256:1B6CEE7997ABFB5BD6127AA68056EF8FF4ACFADCE02A1BAD8A85AA9F8D23FD49 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\FgBbpIj0thGWZOh_xFnM9i4O7ek[1].css | text | |
MD5:908111EB0FFB1360D5DD61279C21703E | SHA256:1ED87CF425DED994B05A842271AB4D28A76F399E571688CF2E7B186F70DC3059 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\kV5W-w634MXeK28vXZ57TRvCF9k[1].css | text | |
MD5:F03BB26D71058E2A764EC4EA458CF041 | SHA256:8DBAC6415F3B0A0A93A2FC33299E60DB9A799E28CB77D1C955E8384F55091BDB | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\AptopUBu7_oVDubJxwvaIprW-lI[1].css | text | |
MD5:4E0E75684C84C0102CED12948B95609B | SHA256:4D18E491B2DE4DA34F6C15F0574911613E902F791FE72501E4404802760D1BCA | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\QNBBNqWD9F_Blep-UqQSqnMp-FI[1].css | text | |
MD5:77373397A17BD1987DFCA2E68D022ECF | SHA256:A319AF2E953E7AFDA681B85A62F629A5C37344AF47D2FCD23AB45E1D99497F13 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133786829593171106.txt.~tmp | text | |
MD5:281AA6CF59081346ABB9A47EE8C10EBE | SHA256:A8C0112D4E2DD893A886EB819ACC21276CDD8CB16CA9A21955753A246F1FD06F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
55
DNS requests
37
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6240 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5000 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3772 | procexp64.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4536 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.154:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
fp.msedge.net |
| whitelisted |