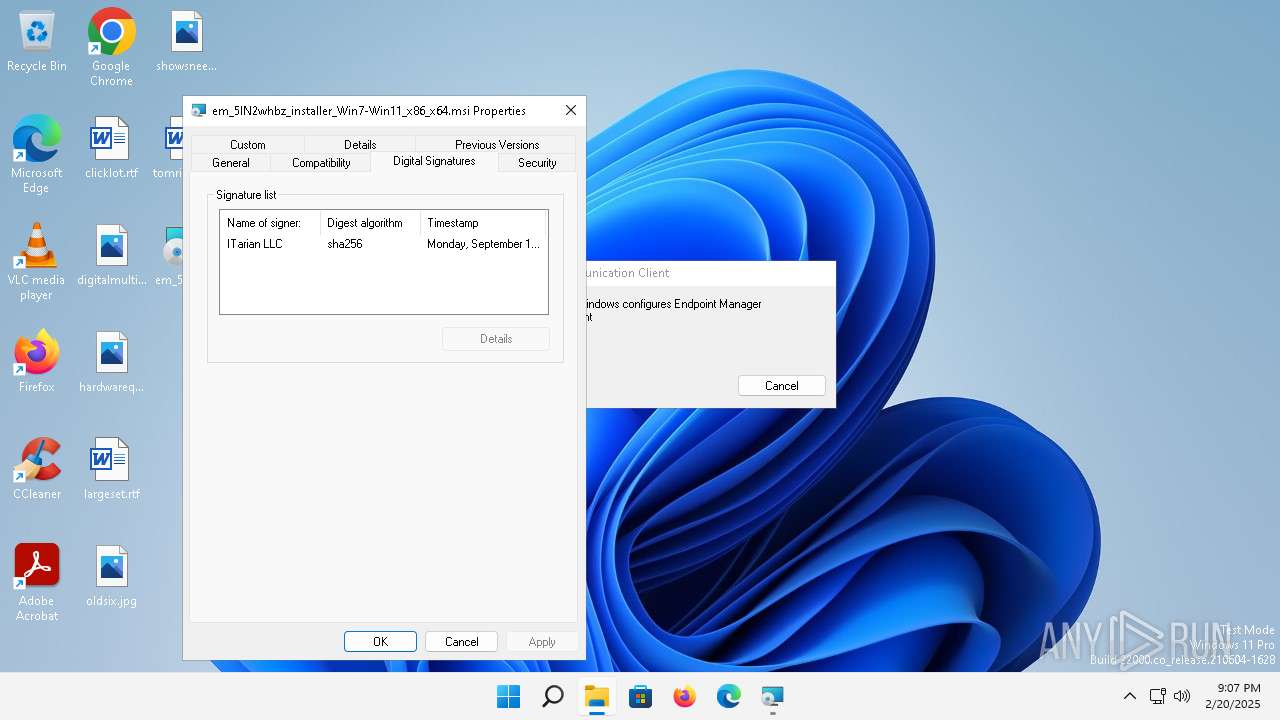
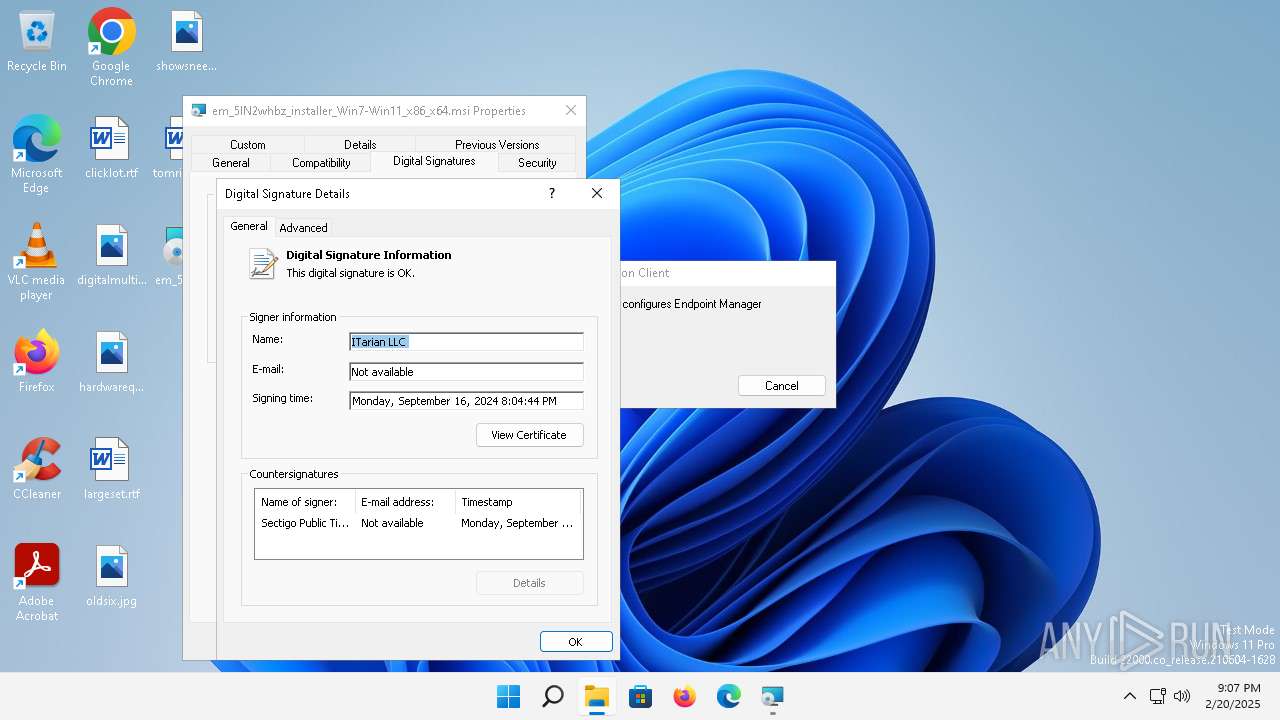
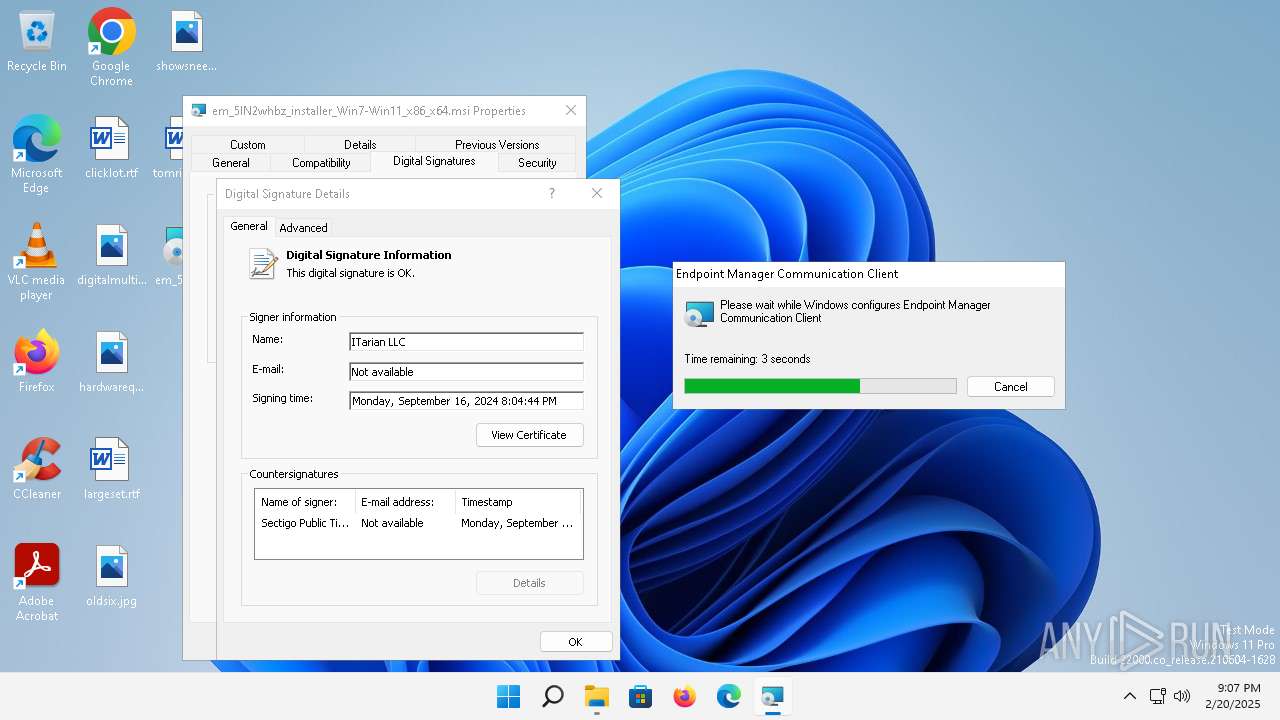
| File name: | em_5IN2whbz_installer_Win7-Win11_x86_x64.msi |
| Full analysis: | https://app.any.run/tasks/3a88da83-5509-4b4c-a560-7a1c258fe7ef |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2025, 21:05:56 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: Endpoint Manager Communication Client, Author: ITarian LLC, Keywords: Installer, Comments: Version 9.2.49090.24060, Template: Intel;0, Revision Number: {C7630387-EB33-424A-A543-BE5617F676DD}, Create Time/Date: Mon Sep 16 19:55:22 2024, Last Saved Time/Date: Mon Sep 16 19:55:22 2024, Number of Pages: 301, Number of Words: 2, Name of Creating Application: Windows Installer XML Toolset (3.11.4330.19070), Security: 2 |
| MD5: | 8F7EA7BE4386DA8059546CC2A0646DE1 |
| SHA1: | 4E0812D11EE4344E599D5C8A5F52E3E0664D2642 |
| SHA256: | A9C42F11E75C3525D8D0F3F036C2F603E60FE102FC68B8F22A8B4C81779652A2 |
| SSDEEP: | 786432:i74NR4XVuHySZut2tIbSyFjsYGvBIPFY2SNrrMAIx:i74NR4XVuSSZMIIbS4jSvBIPFYHFQz |
MALICIOUS
Changes the autorun value in the registry
- msiexec.exe (PID: 1508)
Executing a file with an untrusted certificate
- ITSMService.exe (PID: 2996)
- python_x86_Lib.exe (PID: 3444)
- ITSMAgent.exe (PID: 2692)
- ITSMAgent.exe (PID: 6516)
- ITSMAgent.exe (PID: 5084)
- RmmService.exe (PID: 1160)
- RmmService.exe (PID: 3172)
- ITSMAgent.exe (PID: 6036)
- ITSMAgent.exe (PID: 4376)
SUSPICIOUS
Checks Windows Trust Settings
- msiexec.exe (PID: 1508)
Executes as Windows Service
- VSSVC.exe (PID: 1452)
- WmiApSrv.exe (PID: 872)
- ITSMService.exe (PID: 2996)
- RmmService.exe (PID: 1160)
- WmiApSrv.exe (PID: 6044)
- WmiApSrv.exe (PID: 2700)
- WmiApSrv.exe (PID: 5064)
- WmiApSrv.exe (PID: 6080)
- WmiApSrv.exe (PID: 452)
- WmiApSrv.exe (PID: 2980)
- WmiApSrv.exe (PID: 4320)
- WmiApSrv.exe (PID: 2568)
- WmiApSrv.exe (PID: 1144)
- WmiApSrv.exe (PID: 6028)
- WmiApSrv.exe (PID: 2200)
- WmiApSrv.exe (PID: 5880)
Reads the Internet Settings
- msiexec.exe (PID: 7140)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 1508)
The process drops C-runtime libraries
- msiexec.exe (PID: 1508)
Process drops legitimate windows executable
- msiexec.exe (PID: 1508)
The process creates files with name similar to system file names
- msiexec.exe (PID: 1508)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 3128)
- python_x86_Lib.exe (PID: 3444)
There is functionality for taking screenshot (YARA)
- python_x86_Lib.exe (PID: 3444)
- ITSMAgent.exe (PID: 6516)
- ITSMAgent.exe (PID: 6036)
- ITSMAgent.exe (PID: 4376)
Executable content was dropped or overwritten
- python_x86_Lib.exe (PID: 3444)
Reads security settings of Internet Explorer
- python_x86_Lib.exe (PID: 3444)
Executing commands from ".cmd" file
- python_x86_Lib.exe (PID: 3444)
Process drops python dynamic module
- python_x86_Lib.exe (PID: 3444)
Found regular expressions for crypto-addresses (YARA)
- ITSMService.exe (PID: 2996)
- ITSMAgent.exe (PID: 4376)
Searches for installed software
- ITSMService.exe (PID: 2996)
Creates a software uninstall entry
- ITSMService.exe (PID: 2996)
The process checks if it is being run in the virtual environment
- RmmService.exe (PID: 1160)
INFO
Reads the computer name
- msiexec.exe (PID: 1508)
- msiexec.exe (PID: 4964)
- msiexec.exe (PID: 3128)
- python_x86_Lib.exe (PID: 3444)
- ITSMAgent.exe (PID: 5084)
- ITSMAgent.exe (PID: 6516)
- ITSMAgent.exe (PID: 2692)
- ITSMService.exe (PID: 2996)
- RmmService.exe (PID: 1160)
- RmmService.exe (PID: 3172)
- ITSMAgent.exe (PID: 6036)
- ITSMAgent.exe (PID: 4376)
Creates files or folders in the user directory
- msiexec.exe (PID: 7140)
Reads the software policy settings
- msiexec.exe (PID: 7140)
- msiexec.exe (PID: 1508)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 7140)
Reads the machine GUID from the registry
- msiexec.exe (PID: 1508)
- ITSMService.exe (PID: 2996)
- RmmService.exe (PID: 1160)
Checks proxy server information
- msiexec.exe (PID: 7140)
Checks supported languages
- msiexec.exe (PID: 1508)
- msiexec.exe (PID: 4964)
- msiexec.exe (PID: 3128)
- python_x86_Lib.exe (PID: 3444)
- ITSMAgent.exe (PID: 6516)
- ITSMAgent.exe (PID: 2692)
- ITSMAgent.exe (PID: 5084)
- ITSMService.exe (PID: 2996)
- RmmService.exe (PID: 3172)
- RmmService.exe (PID: 1160)
- ITSMAgent.exe (PID: 6036)
- ITSMAgent.exe (PID: 4376)
Manages system restore points
- SrTasks.exe (PID: 740)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1508)
The sample compiled with english language support
- msiexec.exe (PID: 1508)
- python_x86_Lib.exe (PID: 3444)
Creates files in the program directory
- python_x86_Lib.exe (PID: 3444)
- ITSMService.exe (PID: 2996)
- RmmService.exe (PID: 1160)
Create files in a temporary directory
- python_x86_Lib.exe (PID: 3444)
Creates a software uninstall entry
- msiexec.exe (PID: 1508)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CodePage: | Windows Latin 1 (Western European) |
|---|---|
| Title: | Installation Database |
| Subject: | Endpoint Manager Communication Client |
| Author: | ITarian LLC |
| Keywords: | Installer |
| Comments: | Version 9.2.49090.24060 |
| Template: | Intel;0 |
| RevisionNumber: | {C7630387-EB33-424A-A543-BE5617F676DD} |
| CreateDate: | 2024:09:16 19:55:22 |
| ModifyDate: | 2024:09:16 19:55:22 |
| Pages: | 301 |
| Words: | 2 |
| Software: | Windows Installer XML Toolset (3.11.4330.19070) |
| Security: | Read-only recommended |
Total processes
154
Monitored processes
34
Malicious processes
5
Suspicious processes
7
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 452 | C:\Windows\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
| 740 | C:\Windows\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:14 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 872 | C:\Windows\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
| 1140 | \??\C:\Windows\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | C:\Windows\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
| 1160 | "C:\Program Files (x86)\ITarian\Endpoint Manager\RmmService.exe" | C:\Program Files (x86)\ITarian\Endpoint Manager\RmmService.exe | — | services.exe | |||||||||||
User: SYSTEM Company: ITarian Integrity Level: SYSTEM Description: Endpoint Manager RMM Service | |||||||||||||||
| 1452 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1508 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2200 | C:\Windows\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
| 2568 | C:\Windows\system32\wbem\WmiApSrv.exe | C:\Windows\System32\wbem\WmiApSrv.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Performance Reverse Adapter Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
29 684
Read events
28 963
Write events
707
Delete events
14
Modification events
| (PID) Process: | (1508) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000FA37075FDB83DB01E405000040100000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1508) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000FA37075FDB83DB01E405000040100000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1508) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000231BB65EDB83DB01E405000040100000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1508) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000231BB65EDB83DB01E405000040100000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1508) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 480000000000000086B5105FDB83DB01E405000040100000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1508) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000CB7C155FDB83DB01E405000040100000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1508) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 14 | |||
| (PID) Process: | (1508) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4800000000000000947BCF5FDB83DB01E405000040100000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1508) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000947BCF5FDB83DB01E40500009C050000E8030000010000000000000000000000409EB93D8FB9FB43A0F7D708EA05464500000000000000000000000000000000 | |||
| (PID) Process: | (1452) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Leave) |
Value: 4800000000000000AE96D65FDB83DB01AC05000020060000E80300000000000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
89
Suspicious files
365
Text files
2 219
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1508 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1508 | msiexec.exe | C:\Windows\Installer\258a98.msi | — | |
MD5:— | SHA256:— | |||
| 7140 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\18E6B4A57A6BC7EC9B861CDF2D6D0D02_EF52C1EC85F21F31CC0157A5C8803013 | binary | |
MD5:FB8A58A6CFC37482D201BDF40589C3B4 | SHA256:4026621377FC48CC595BC862A990B67E04A31513951875B65AA19F4BBC5F08B8 | |||
| 7140 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3AA0DCD5A74331FBD6F344550EC48B87_B2CA343459C05DC728694AF1B28799A4 | binary | |
MD5:4604CF1F1F10D896C46ED4110244C709 | SHA256:3A7CD7F1AA3029F3FF8505B2A20C69964C992FAF70077580716CF108D1BC7735 | |||
| 7140 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\18E6B4A57A6BC7EC9B861CDF2D6D0D02_EF52C1EC85F21F31CC0157A5C8803013 | binary | |
MD5:413AD3F1A4EBB01916317F14E449F5F5 | SHA256:70BB8B6441F62C56D278EB1F42A1E03DACCF89F116C323E877FB75A6FF938D58 | |||
| 7140 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_93702E680A5530C052C8D2BA33A2225F | binary | |
MD5:9AF9BDD0288F647D992FBF0D46D30A86 | SHA256:4E5BAB965F89D514EB519001E17F2869C355FDDF99986630280E7BC46CBA63F3 | |||
| 7140 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_93702E680A5530C052C8D2BA33A2225F | binary | |
MD5:5646A13A82E01FC52BB17C42B61E054C | SHA256:703EB1511B32D44D0DCECAD8F9A367654BF6A9F22CF39DC14ECF84A86AAD1ECA | |||
| 1508 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{3db99e40-b98f-43fb-a0f7-d708ea054645}_OnDiskSnapshotProp | binary | |
MD5:0111DDF89825D61ADB86255564983ACA | SHA256:8A67112C413196D6AF5322A07B12D78BA93E91E649229C7508F6D988D415767E | |||
| 1508 | msiexec.exe | C:\Windows\Installer\MSI9305.tmp | executable | |
MD5:D53B2B818B8C6A2B2BAE3A39E988AF10 | SHA256:2A81878BE73B5C1D7D02C6AFC8A82336D11E5F8749EAACF54576638D81DED6E2 | |||
| 7140 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3AA0DCD5A74331FBD6F344550EC48B87_B2CA343459C05DC728694AF1B28799A4 | der | |
MD5:9682D0FDCE89DE137CCEA3DE4806F183 | SHA256:D3EF7FB215E475318F85DC30E2E04B1A08FE843177BCA6A513C8012818C94EE5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
25
DNS requests
17
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5064 | MoUsoCoreWorker.exe | GET | 200 | 199.232.214.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?199307f0f375a852 | unknown | — | — | whitelisted |
7140 | msiexec.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRd0JozUYXMqqW4y4zJTrLcMCRSkAQUgTKSQSsozUbIxKLGKjkS7EipPxQCEQDFkkwCc%2F6QyRK%2F5PUP8RSE | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.110.216:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 304 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?2553bb07922af752 | unknown | — | — | whitelisted |
7140 | msiexec.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
7140 | msiexec.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEDPXCKiRQFMZ4qW70zm5rW4%3D | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?af3626043367ee40 | unknown | — | — | whitelisted |
1592 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?47d9e591c71f8d01 | unknown | — | — | whitelisted |
2860 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?950f5e50f78247d0 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 88.221.110.147:80 | — | Akamai International B.V. | DE | unknown |
— | — | 88.221.110.216:80 | — | Akamai International B.V. | DE | unknown |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | MoUsoCoreWorker.exe | 199.232.214.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
1592 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1592 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7140 | msiexec.exe | 172.64.149.23:80 | ocsp.comodoca.com | CLOUDFLARENET | US | whitelisted |
7140 | msiexec.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
5036 | svchost.exe | 2.18.97.153:443 | fs.microsoft.com | Akamai International B.V. | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
mdmsupport.cmdm.comodo.com |
| unknown |
spsystem.itsm-us1.comodo.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |
Process | Message |
|---|---|
ITSMService.exe | QCoreApplication::applicationDirPath: Please instantiate the QApplication object first
|
ITSMService.exe | OEM strings file does not exists! "C:/Program Files (x86)/ITarian/Endpoint Manager/oem.strings"
|
ITSMService.exe | Log dir is 'C:/ProgramData/ITarian/Endpoint Manager'
|
ITSMService.exe | Try to find oem.strings in "C:/Program Files (x86)/ITarian/Endpoint Manager/oem.strings"
|
ITSMAgent.exe | Try to find oem.strings in "C:/Program Files (x86)/ITarian/Endpoint Manager/oem.strings"
|
ITSMAgent.exe | OEM strings file does not exists! "C:/Program Files (x86)/ITarian/Endpoint Manager/oem.strings"
|
ITSMAgent.exe | Log dir is 'C:/ProgramData/ITarian/Endpoint Manager'
|