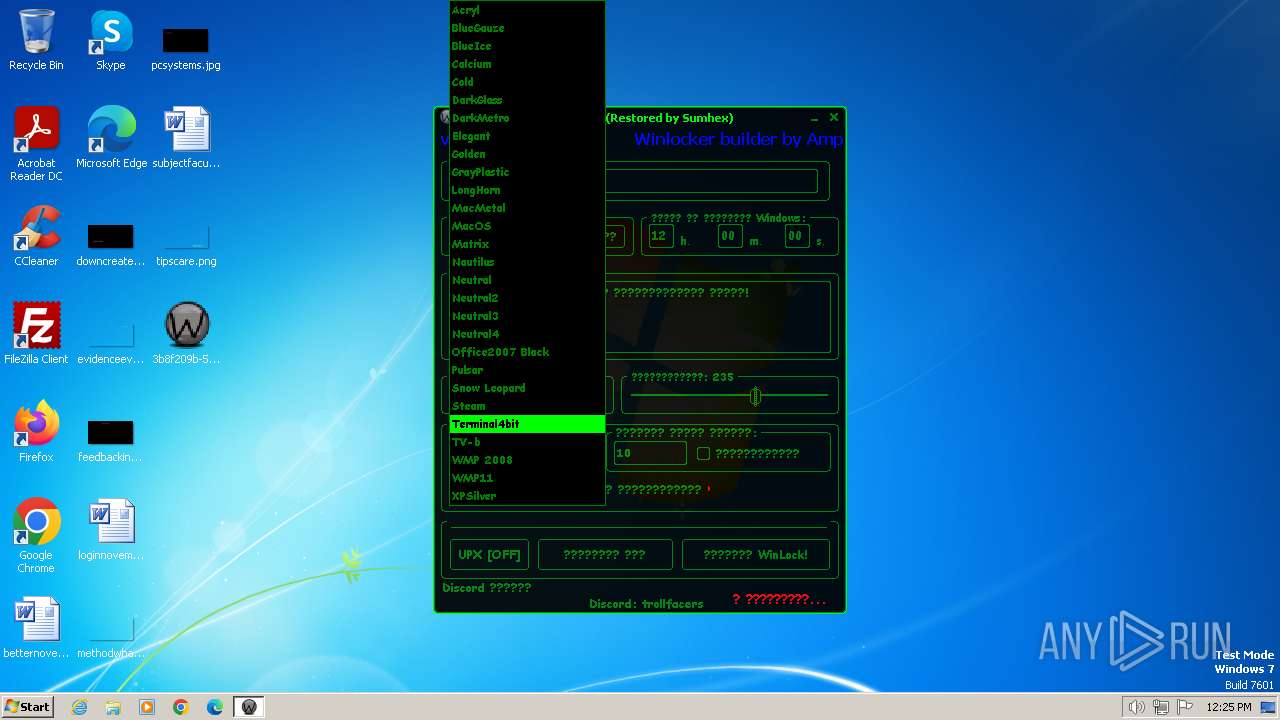
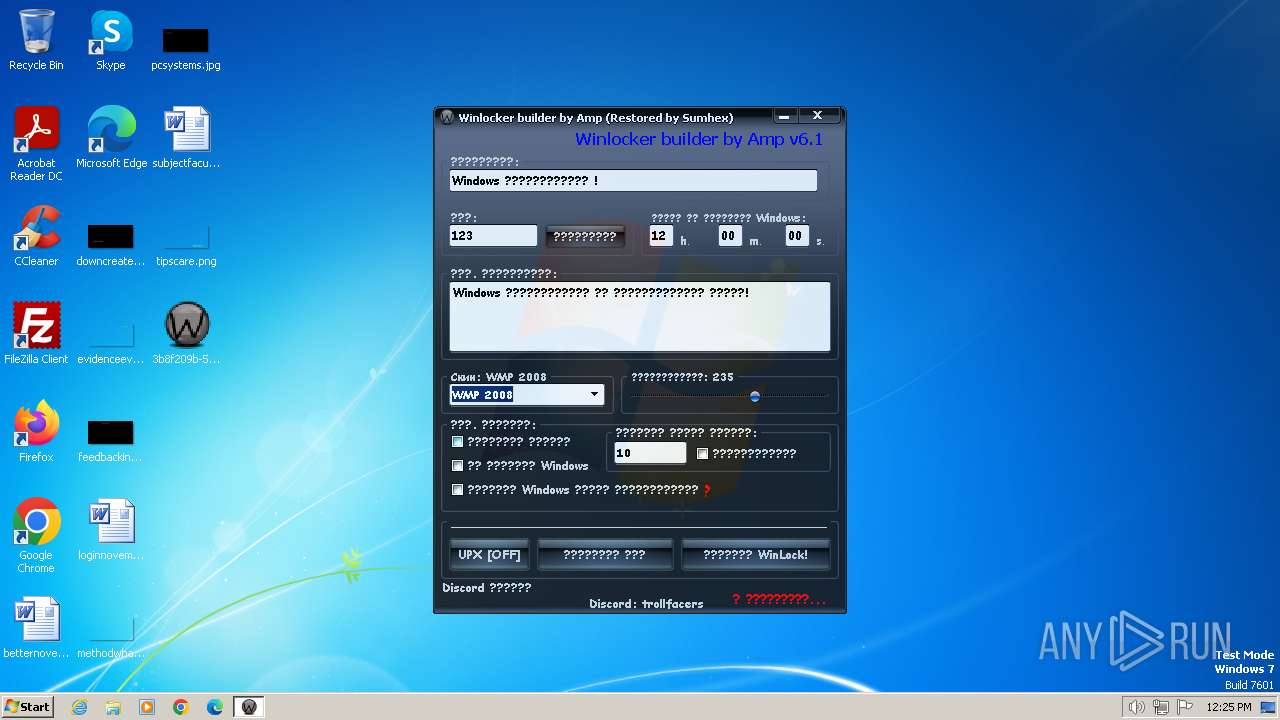
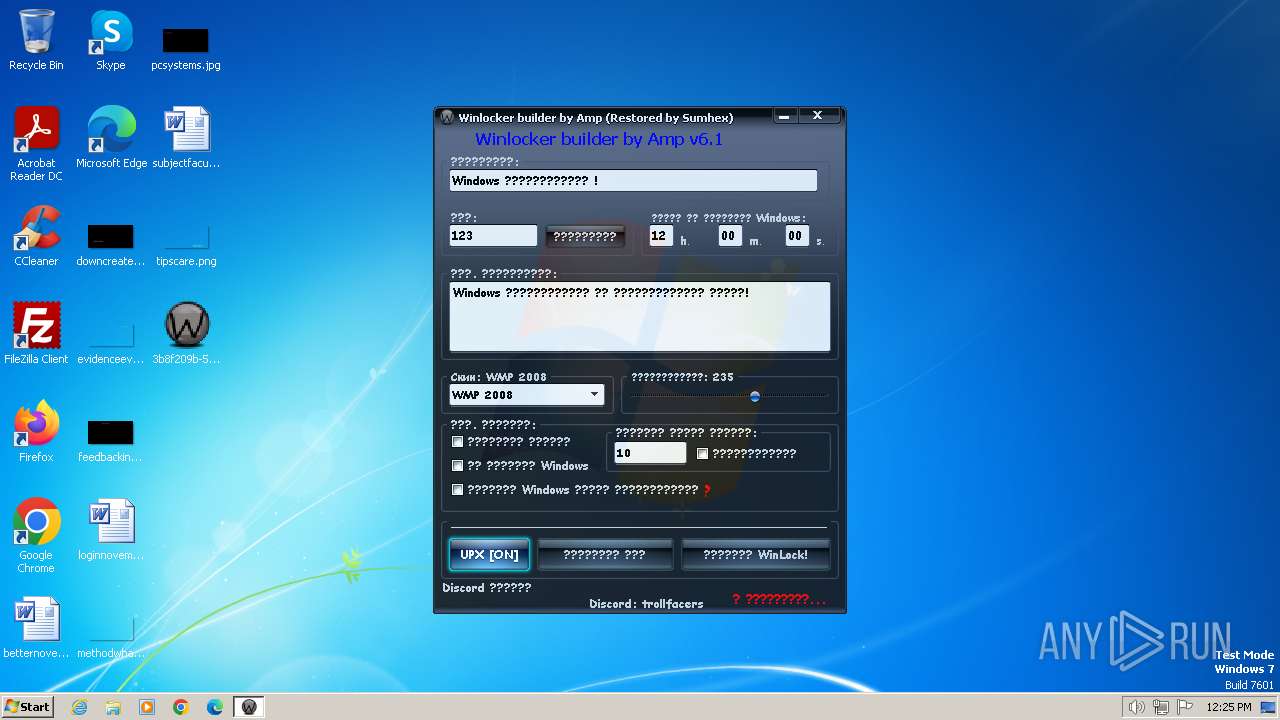
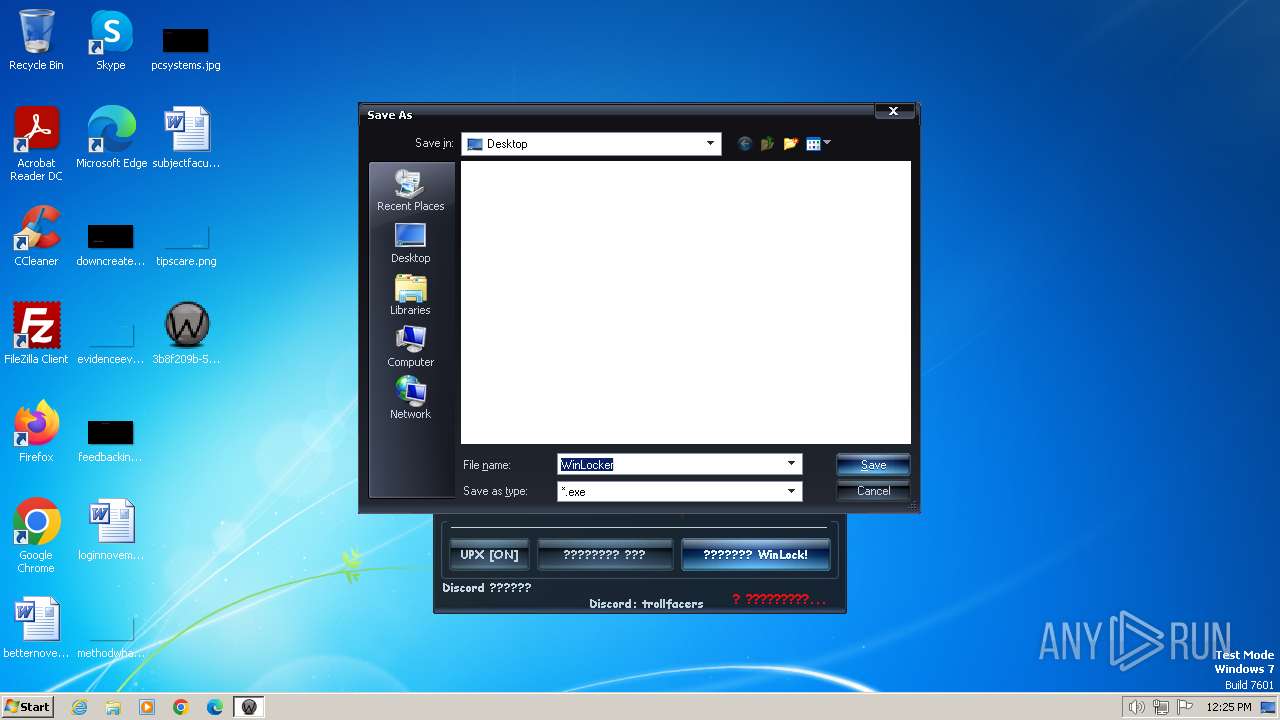
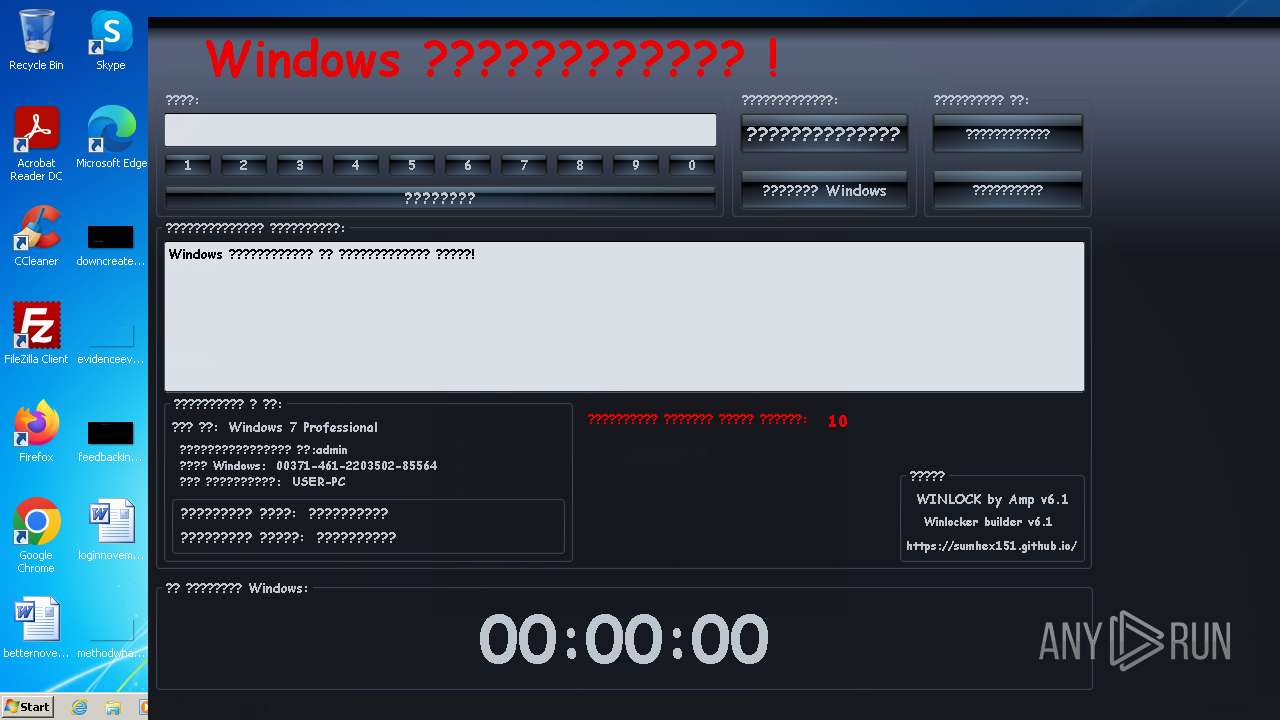
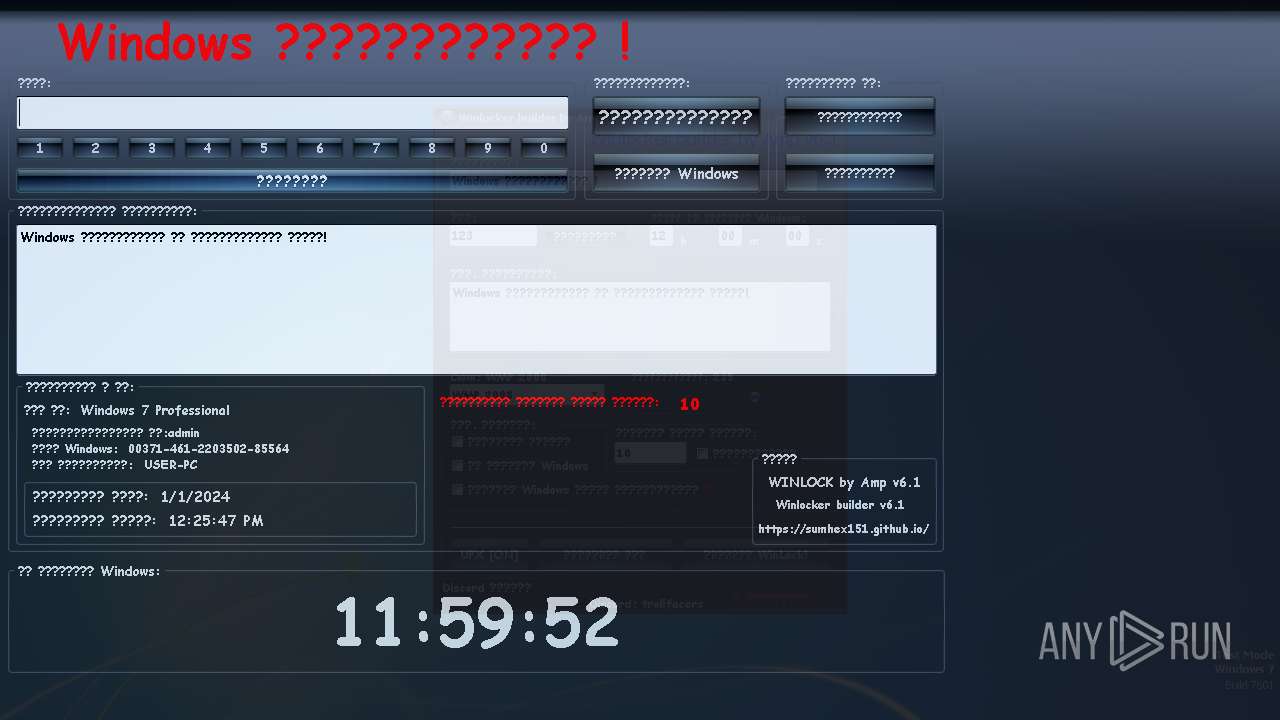
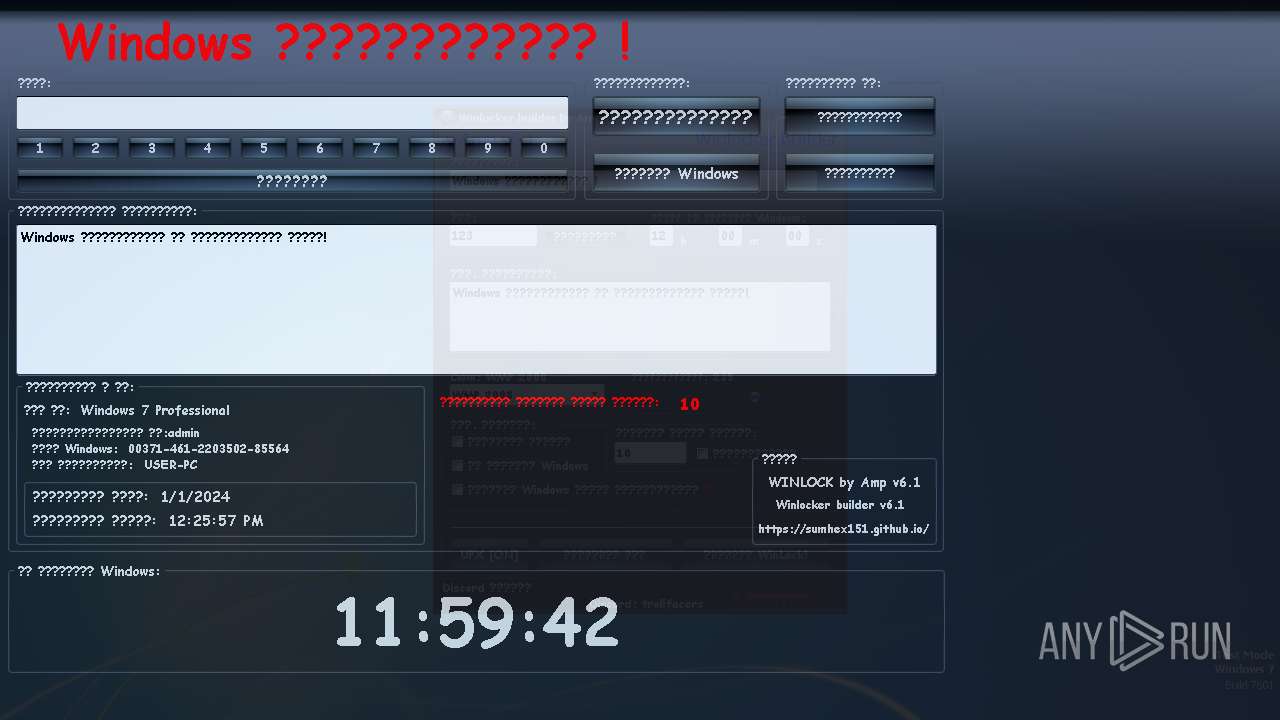
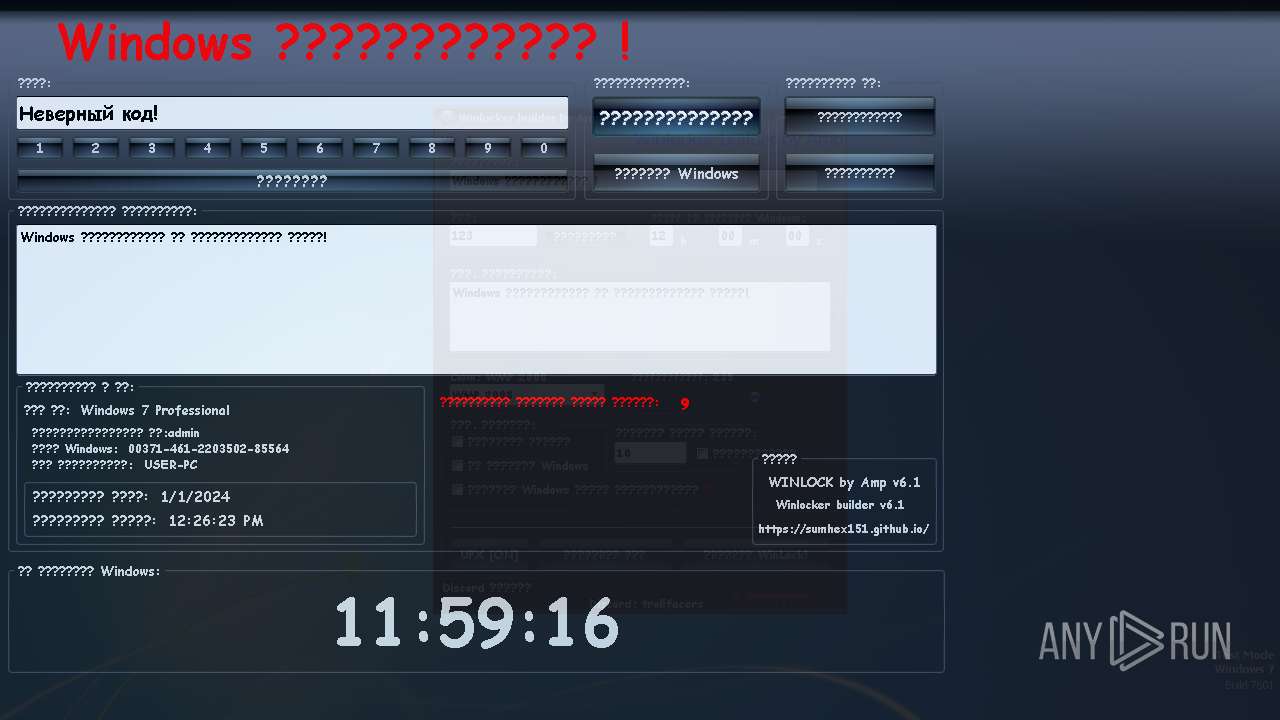
| download: | /sumhex151/sumhex151.github.io/raw/main/Winlocker%20builder%20by%20Amp%20v6.1.exe |
| Full analysis: | https://app.any.run/tasks/3b8f209b-58fa-457b-8ab6-f284a2ab9844 |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2024, 12:24:36 |
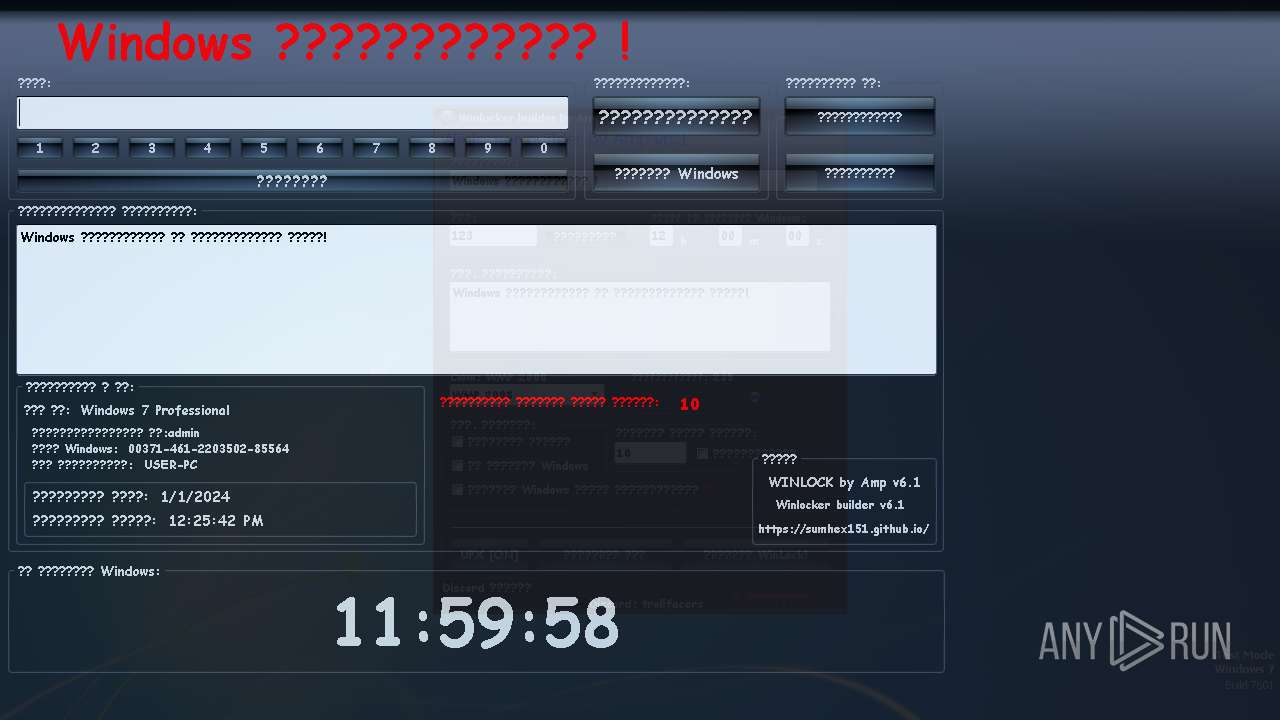
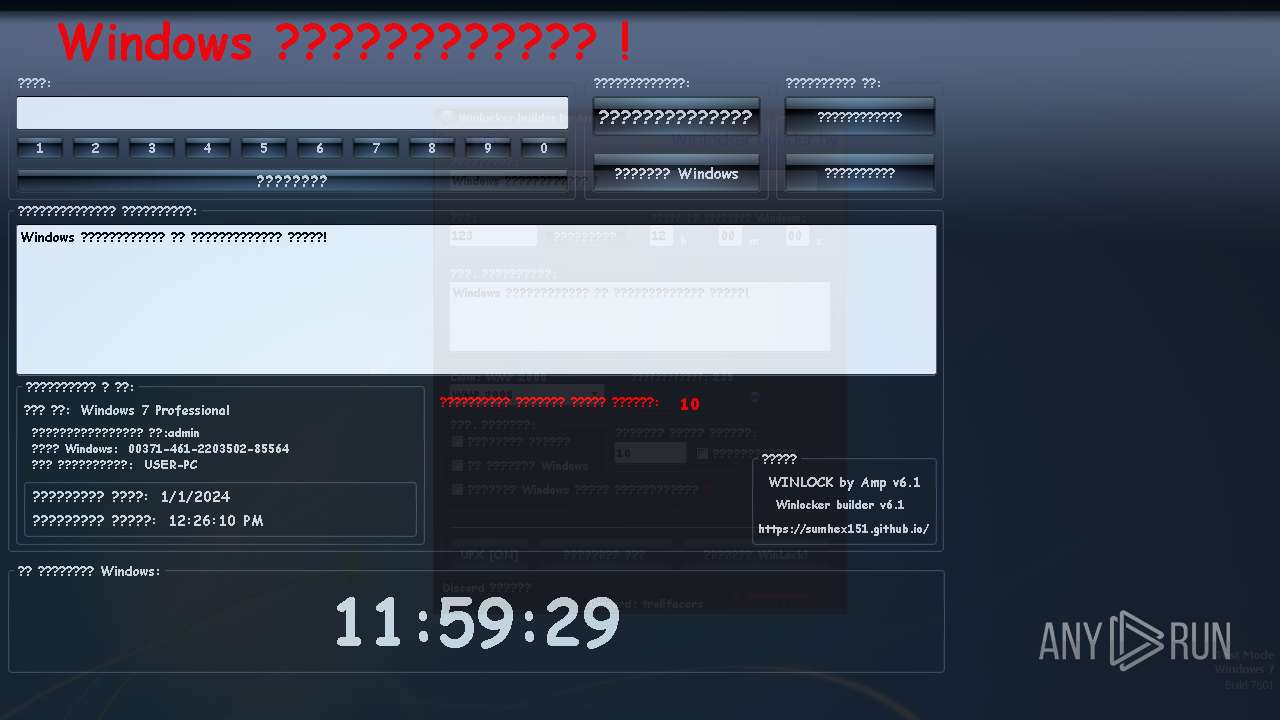
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | FREE-DOS executable (COM), UPX compressed |
| MD5: | AFCA5C840F8D1185AA0ABFC13246FACC |
| SHA1: | 08F016B334F10C7A572B9CF4255DFE173D652FD7 |
| SHA256: | A9982CD42F6560CC1739AE2C1315894A3DDA02A19821F652FC0B0D41E3C3FA9E |
| SSDEEP: | 98304:y/DGbDy5BTb/E/fB0G6tPKUDotlpgn4Ox/kY1PkWVvF7gl3t1lcTN6UgXOzf2HBW:gvT |
MALICIOUS
UAC/LUA settings modification
- WinLocker.exe (PID: 1736)
SUSPICIOUS
Reads the Internet Settings
- 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe (PID: 2036)
Reads the Windows owner or organization settings
- WinLocker.exe (PID: 1736)
INFO
Reads the machine GUID from the registry
- 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe (PID: 2036)
Checks supported languages
- 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe (PID: 2036)
- upx.exe (PID: 784)
- WinLocker.exe (PID: 1736)
Reads the computer name
- 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe (PID: 2036)
- WinLocker.exe (PID: 1736)
Drops the executable file immediately after the start
- 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe (PID: 2036)
- upx.exe (PID: 784)
Manual execution by a user
- WinLocker.exe (PID: 1736)
- WinLocker.exe (PID: 1112)
Reads Windows Product ID
- WinLocker.exe (PID: 1736)
Reads product name
- WinLocker.exe (PID: 1736)
Reads Environment values
- WinLocker.exe (PID: 1736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:20 00:22:17+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 2342912 |
| InitializedDataSize: | 94208 |
| UninitializedDataSize: | 11104256 |
| EntryPoint: | 0xcd2f90 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
46
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 784 | "C:\Users\admin\Desktop\upx.exe" WinLocker.exe | C:\Users\admin\Desktop\upx.exe | — | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | |||||||||||
User: admin Company: The UPX Team https://upx.github.io Integrity Level: MEDIUM Description: UPX executable packer Exit code: 0 Version: 3.96 (2020-01-23) Modules
| |||||||||||||||
| 1112 | "C:\Users\admin\Desktop\WinLocker.exe" | C:\Users\admin\Desktop\WinLocker.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1736 | "C:\Users\admin\Desktop\WinLocker.exe" | C:\Users\admin\Desktop\WinLocker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 2036 | "C:\Users\admin\Desktop\3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe" | C:\Users\admin\Desktop\3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1073807364 Modules
| |||||||||||||||
Total events
779
Read events
743
Write events
35
Delete events
1
Modification events
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 06000000000000000B0000000100000002000000070000000C0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRULegacy |
| Operation: | write | Name: | MRUListEx |
Value: 0000000001000000FFFFFFFF | |||
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | MRUListEx |
Value: 0B0000000A00000009000000080000000700000006000000050000000400000003000000020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | 4 |
Value: 330062003800660032003000390062002D0035003800660061002D0034003500370062002D0038006100620036002D006600320038003400610032006100620039003800340034002E006500780065000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000006601000066000000990300000202000000000000000000000000000000000000000000000000000000000000000000000100000000000000 | |||
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000030000000000000001000000FFFFFFFF | |||
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlgLegacy\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | Mode |
Value: 6 | |||
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlgLegacy\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | LogicalViewMode |
Value: 2 | |||
| (PID) Process: | (2036) 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\82\ComDlgLegacy\{5C4F28B5-F869-4E84-8E60-F11DB97C5CC7} |
| Operation: | write | Name: | FFlags |
Value: 1 | |||
Executable files
21
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2036 | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | C:\Users\admin\Desktop\RCX669A.tmp | executable | |
MD5:677798487E432EDFCD392E8E84B7E5A2 | SHA256:B4159C748576F60D66254AF28879BCDE32AD96518882084539072FAF9B018EFF | |||
| 2036 | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | C:\Users\admin\Desktop\RCX656D.tmp | executable | |
MD5:B3B74CAC87B15A085EDAAB978C007A4F | SHA256:269DF235ACE3D6ED3DD506BC6C0AC889A1EA008108C3B846A4610B5834DBC3B4 | |||
| 2036 | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | C:\Users\admin\Desktop\RCX650F.tmp | executable | |
MD5:D342228BB11A3F6699ABE05A173D0024 | SHA256:13B6F188A577CD393DF7489B49F659103401C3F04E6CA89457AD1A99461583CB | |||
| 2036 | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | C:\Users\admin\Desktop\RCX65FC.tmp | executable | |
MD5:229D61D40B12C137A9B349E45B81815A | SHA256:7F5D0B7077FE6B8C74A8286AC63C309AF7624449CCCF66DAAF13A529523A5538 | |||
| 2036 | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | C:\Users\admin\Desktop\WinLocker.exe | executable | |
MD5:9CC109BE225CDF1B79F0A3E2E2E8F13C | SHA256:84CF5AE88E5A032D0F76213AC6E45AC13EDAEB93A8FBBC9D02C9D9F7EFED2BB3 | |||
| 2036 | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | C:\Users\admin\Desktop\RCX66F9.tmp | executable | |
MD5:7CFB7CF3AC6D8A442F929FEE6240BF57 | SHA256:0705CF63DF2C54E6A8A0FB9AA45A619FDC6EFEB104ADCB010D467E915F2A673B | |||
| 2036 | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | C:\Users\admin\Desktop\RCX664B.tmp | executable | |
MD5:A3B781CC37EB7D1BEE902BB4CC63941C | SHA256:16643EDA9D21D20F2545EE0F62311014E0663B8C3D57417538B4A19535C66A71 | |||
| 2036 | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | C:\Users\admin\Desktop\RCX6738.tmp | executable | |
MD5:9A360ABDD468983DD5FC4DA657A40606 | SHA256:4711A269306382C44F890DA0596B1889529B62342E081CCD624BB7AFD5151B45 | |||
| 2036 | 3b8f209b-58fa-457b-8ab6-f284a2ab9844.exe | C:\Users\admin\Desktop\RCX65BC.tmp | executable | |
MD5:0B869D7866516D5B8E61C8DD64EB2D2B | SHA256:1B485E5BB5CB5D87DF65DF11DD2DC916534514B2EA094A0087A7D4EA298D1544 | |||
| 1736 | WinLocker.exe | C:\Users\admin\Desktop\Time2.ini | text | |
MD5:97ABE1980F4EA3804340CCA16CD914EC | SHA256:DCBF287018F6ACDF68B133E4DBC9A910F8078C7A425FE6CDA2322307FE86E305 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |