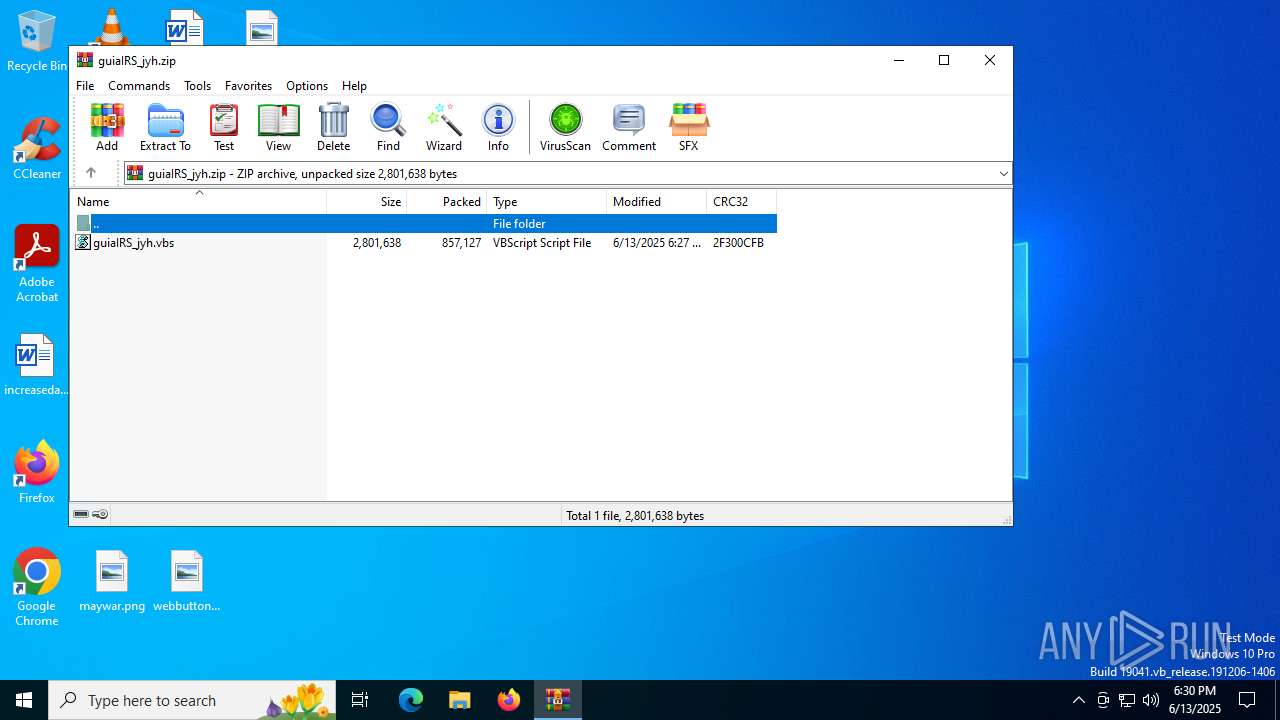
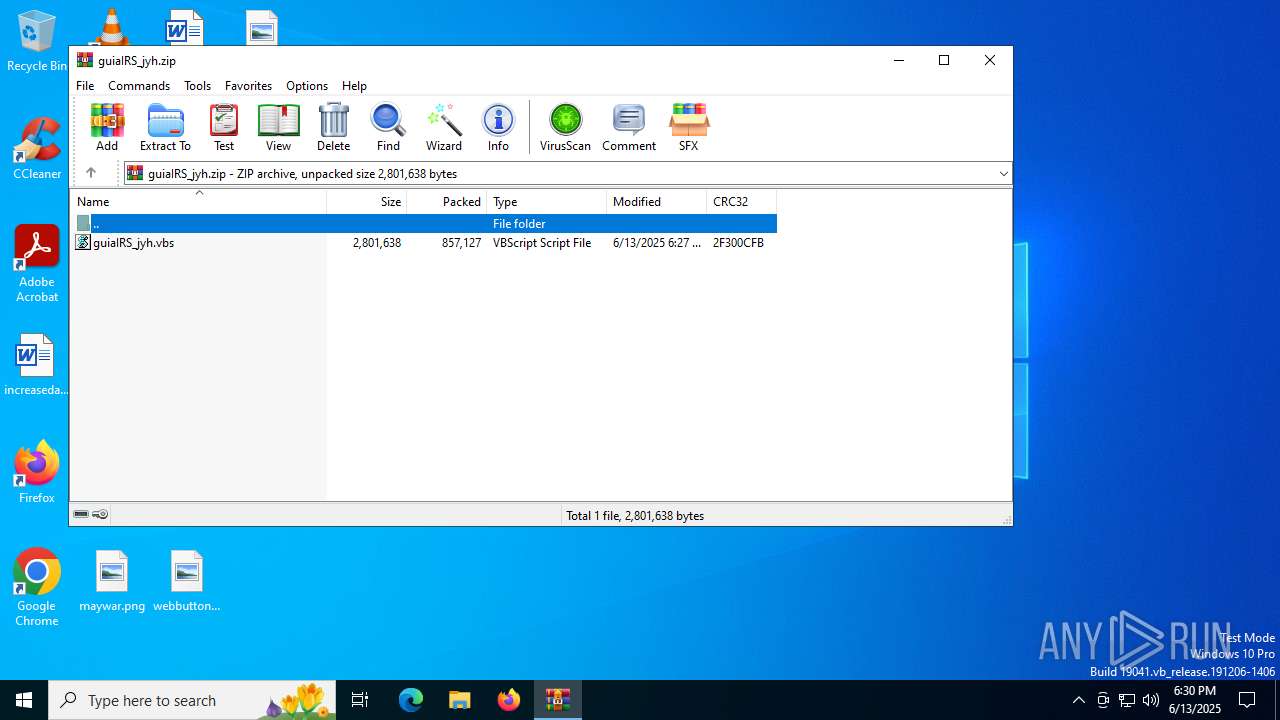
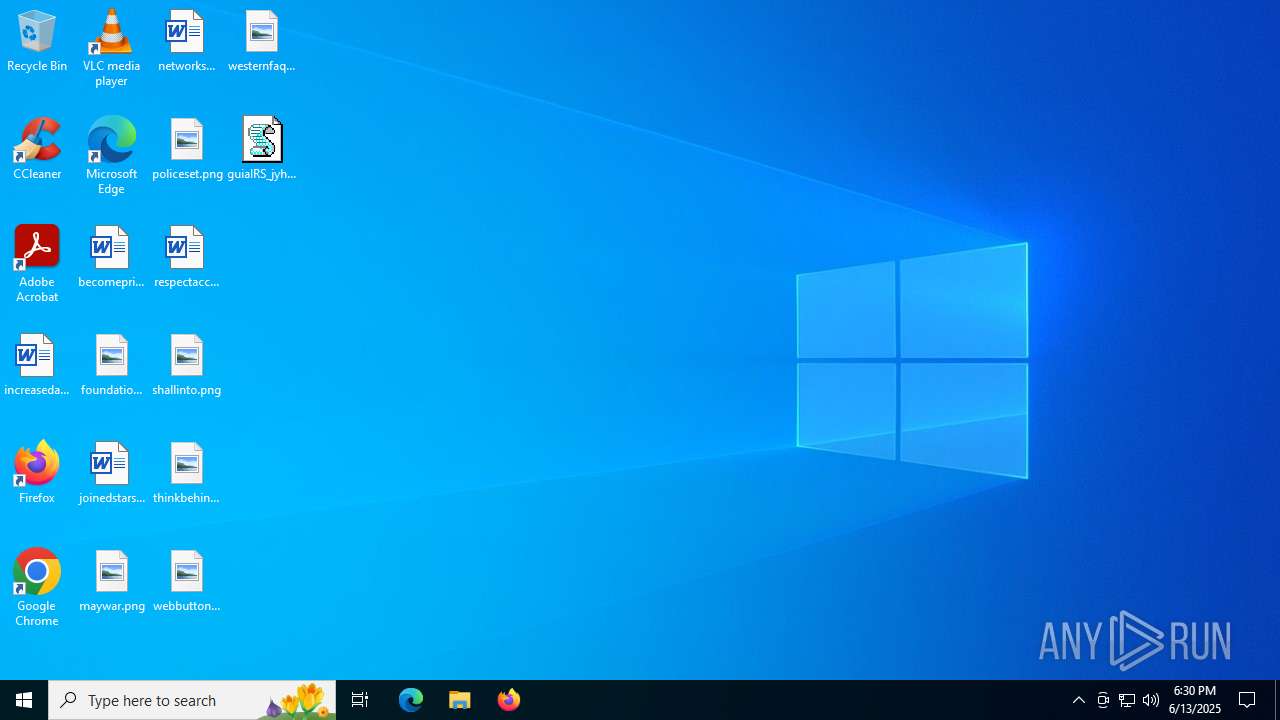
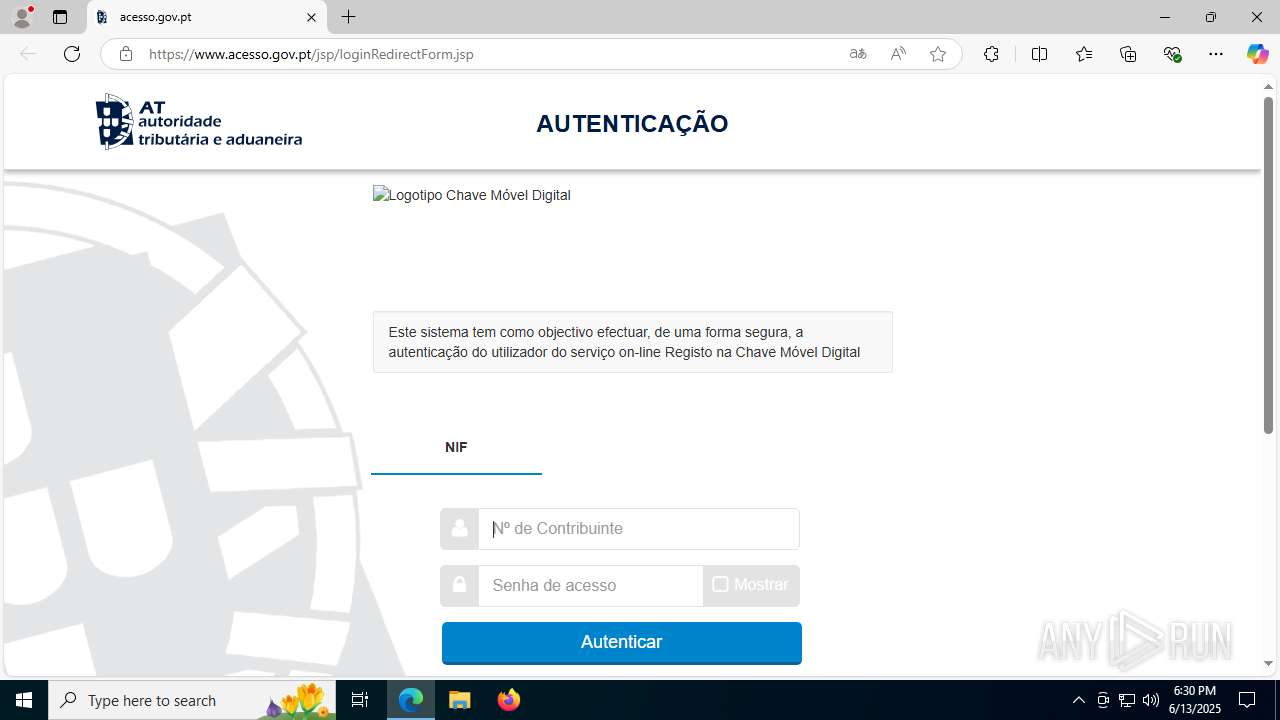
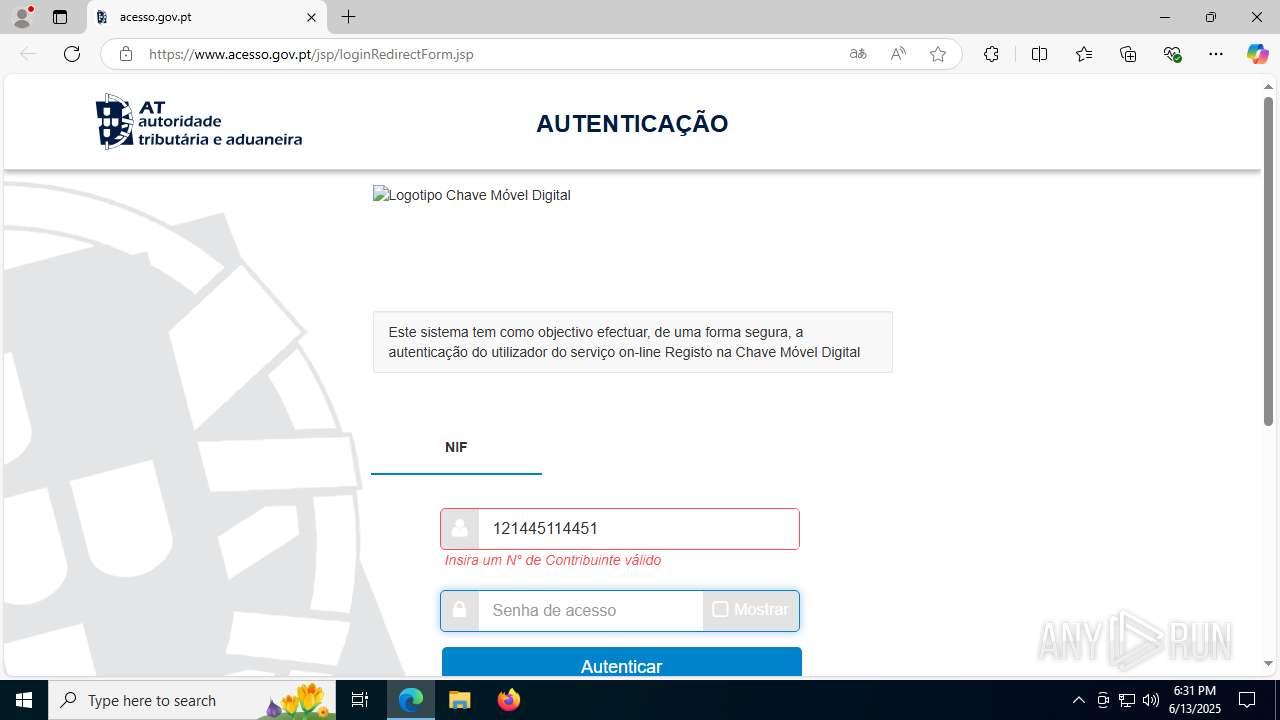
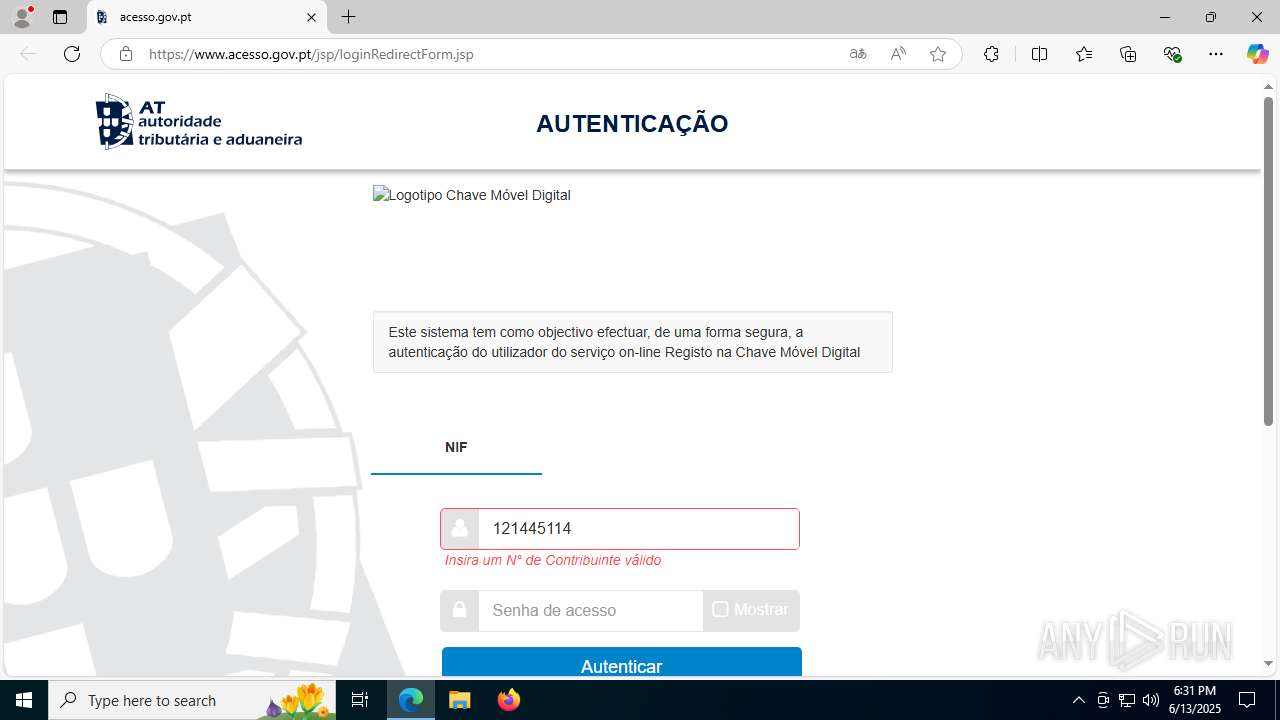
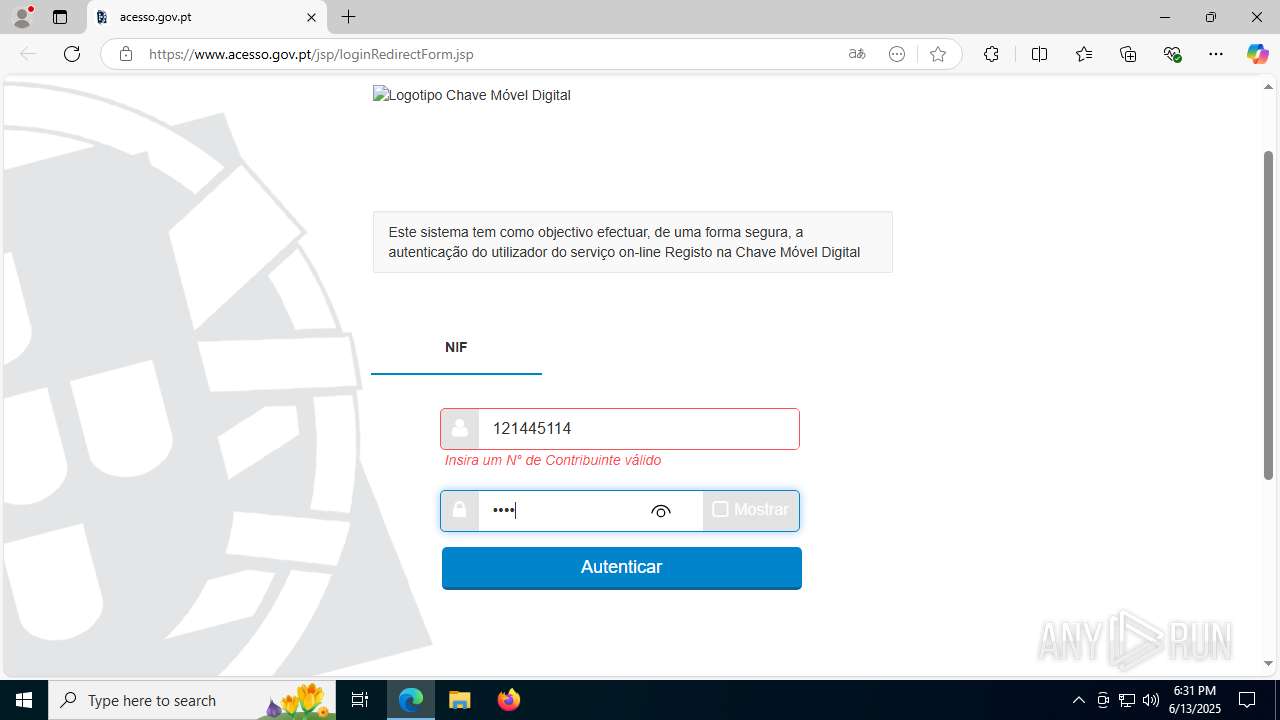
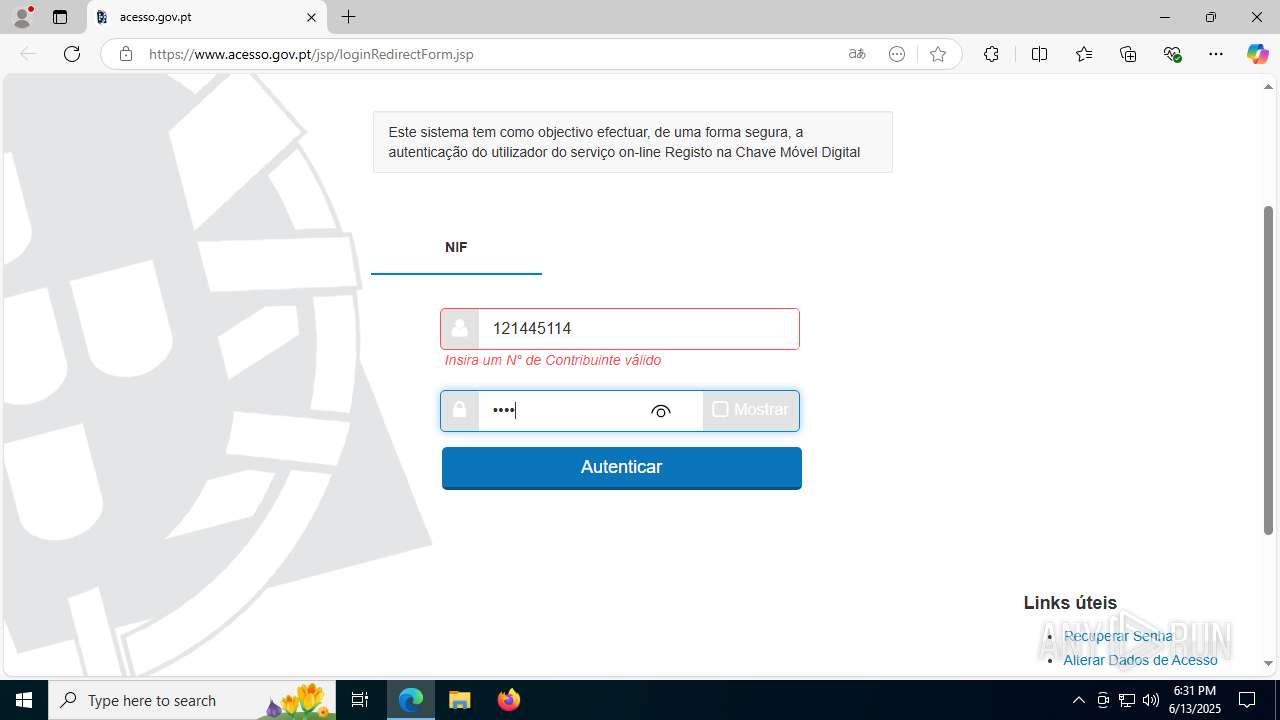
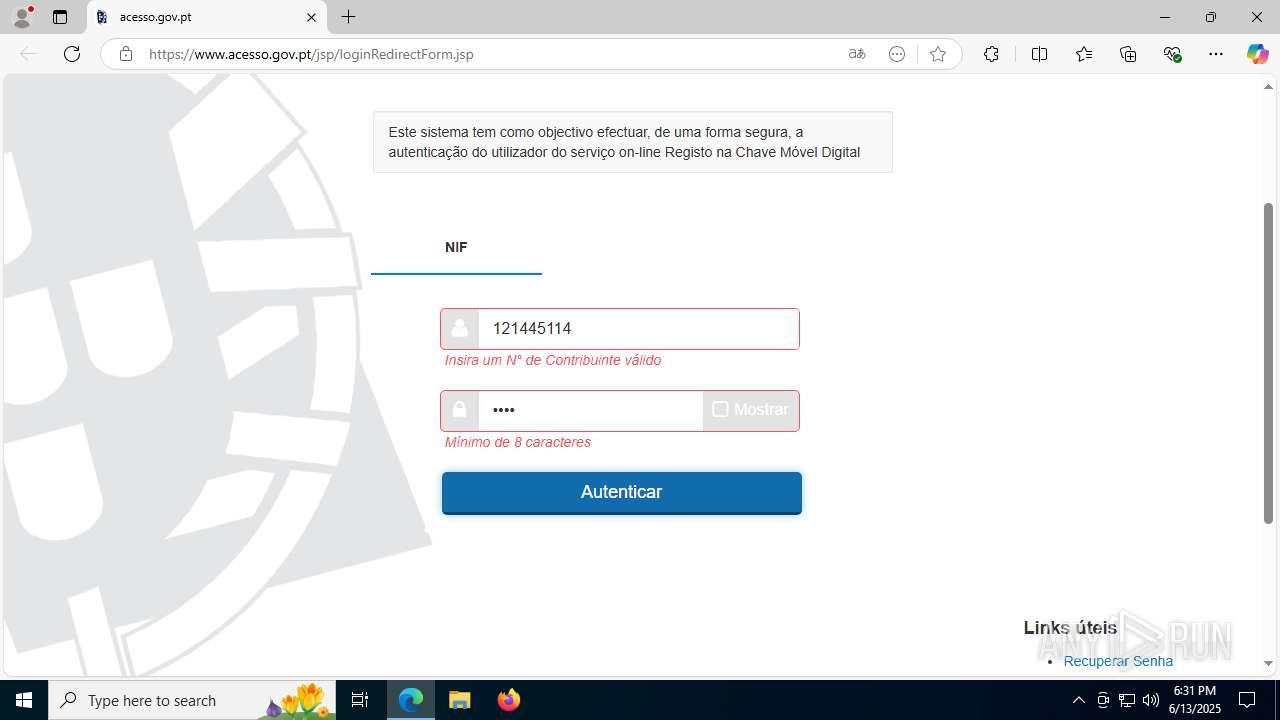
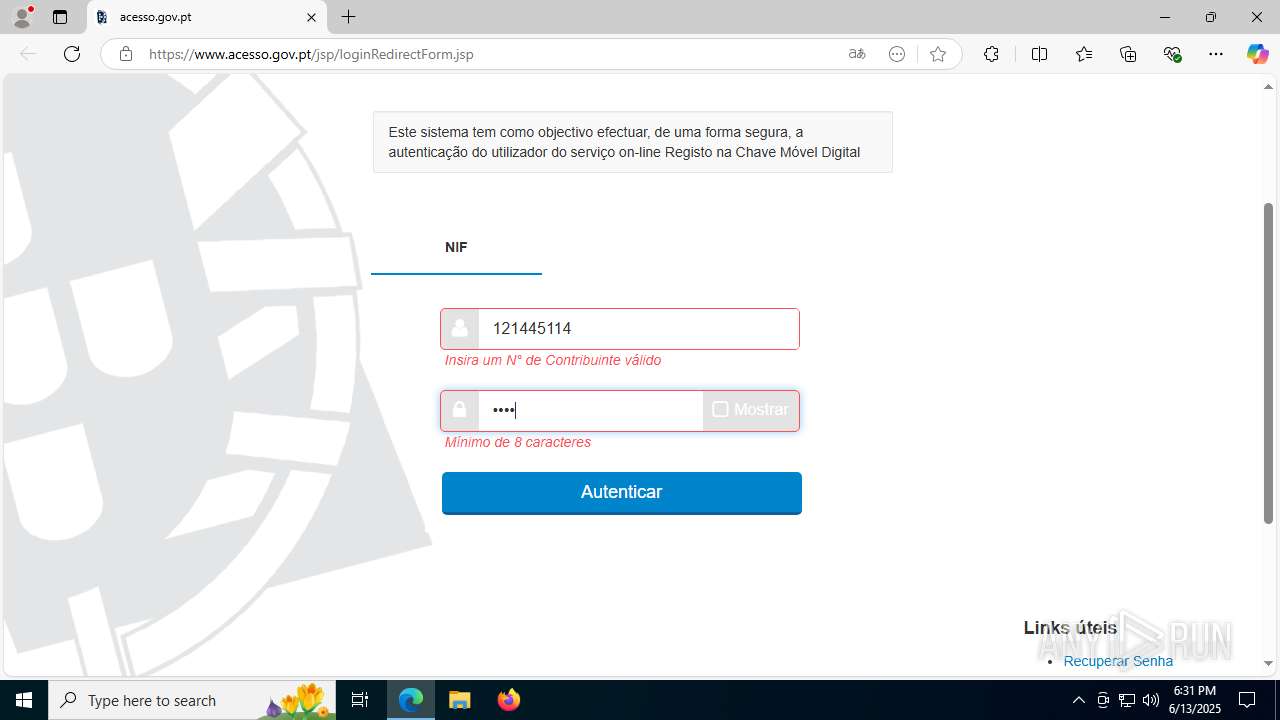
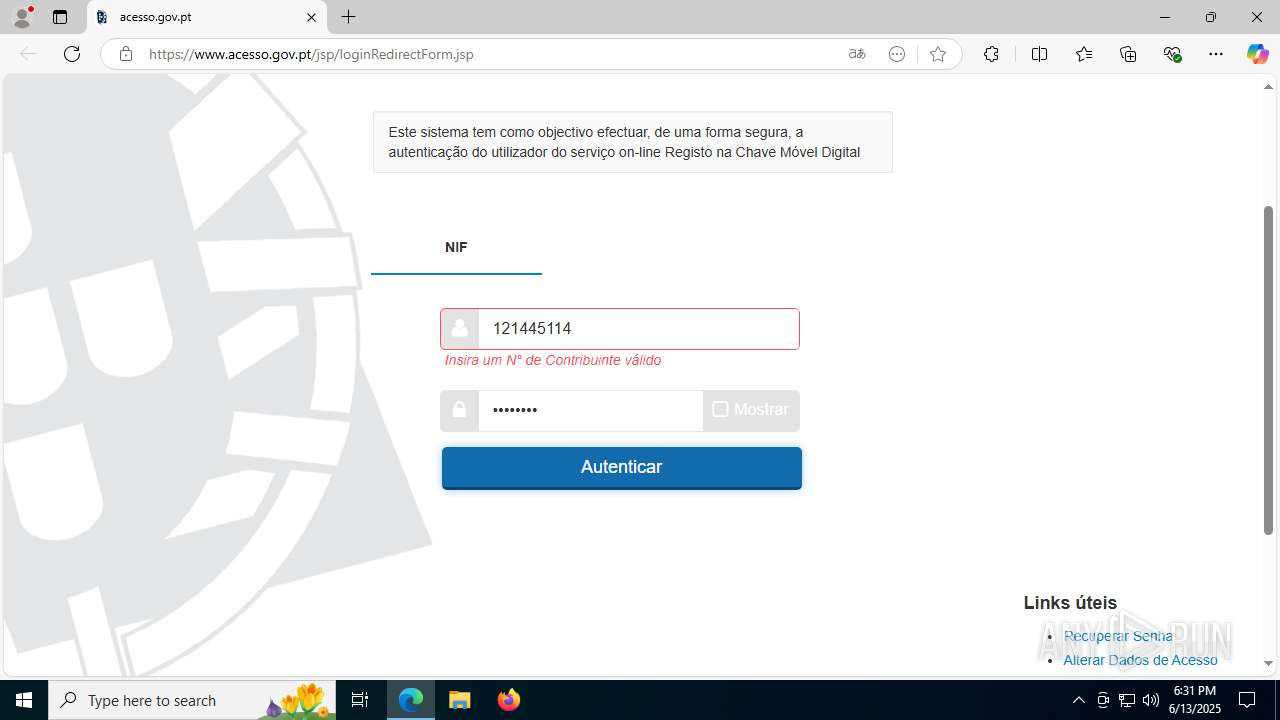
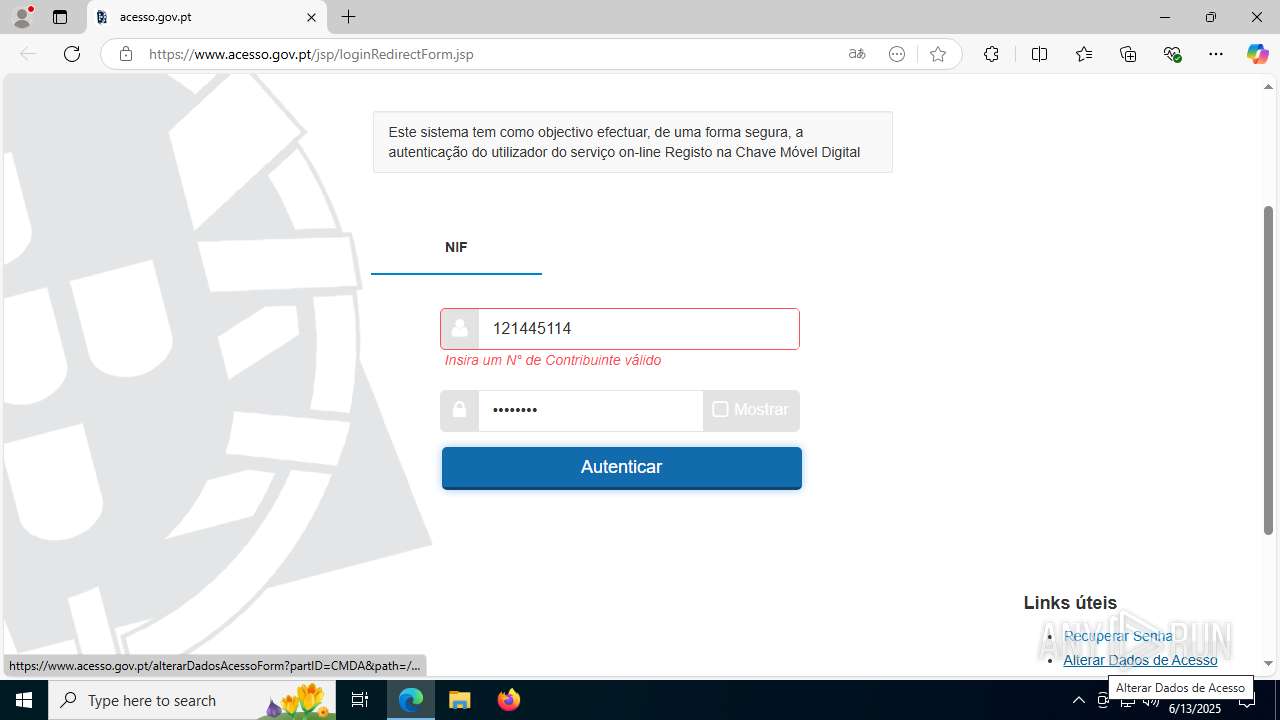
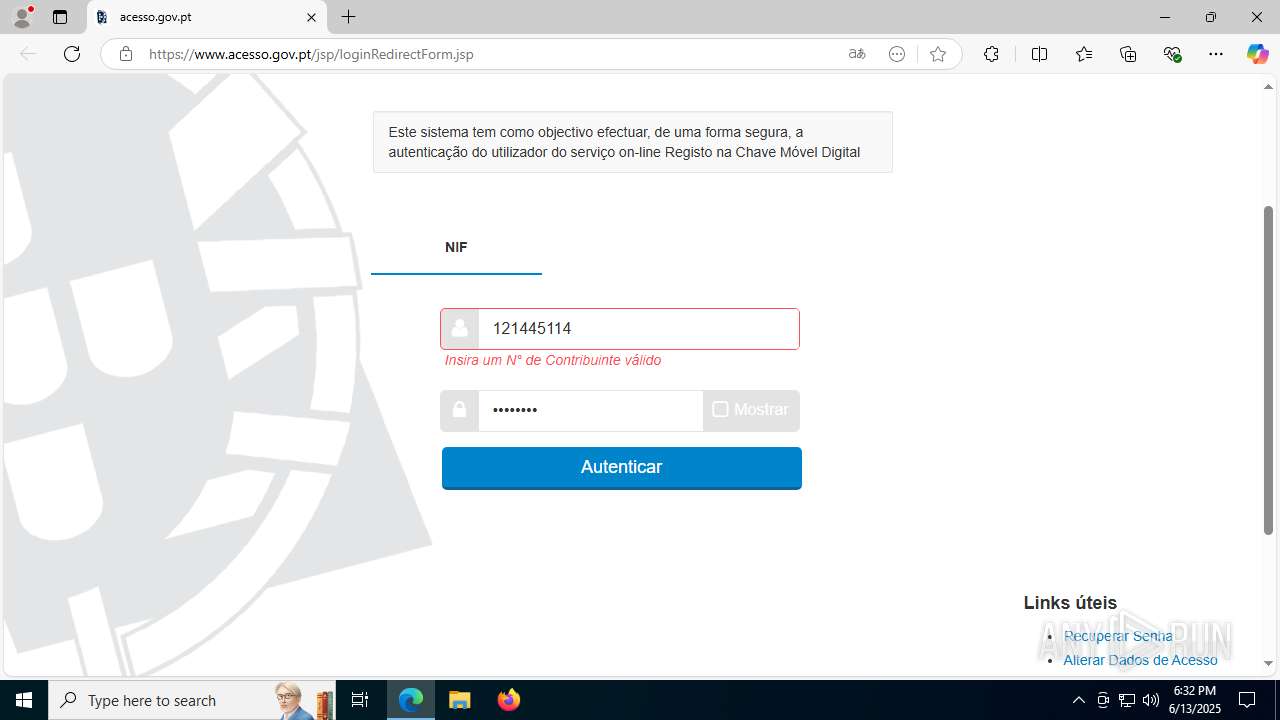
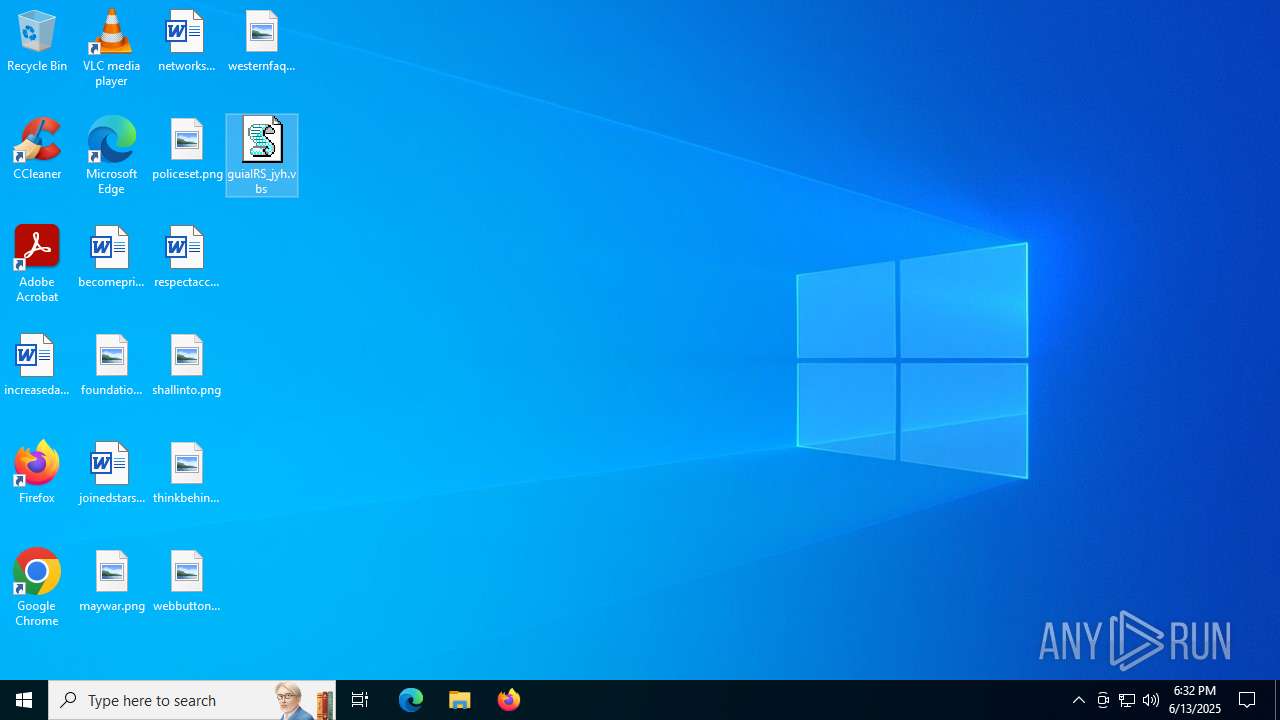
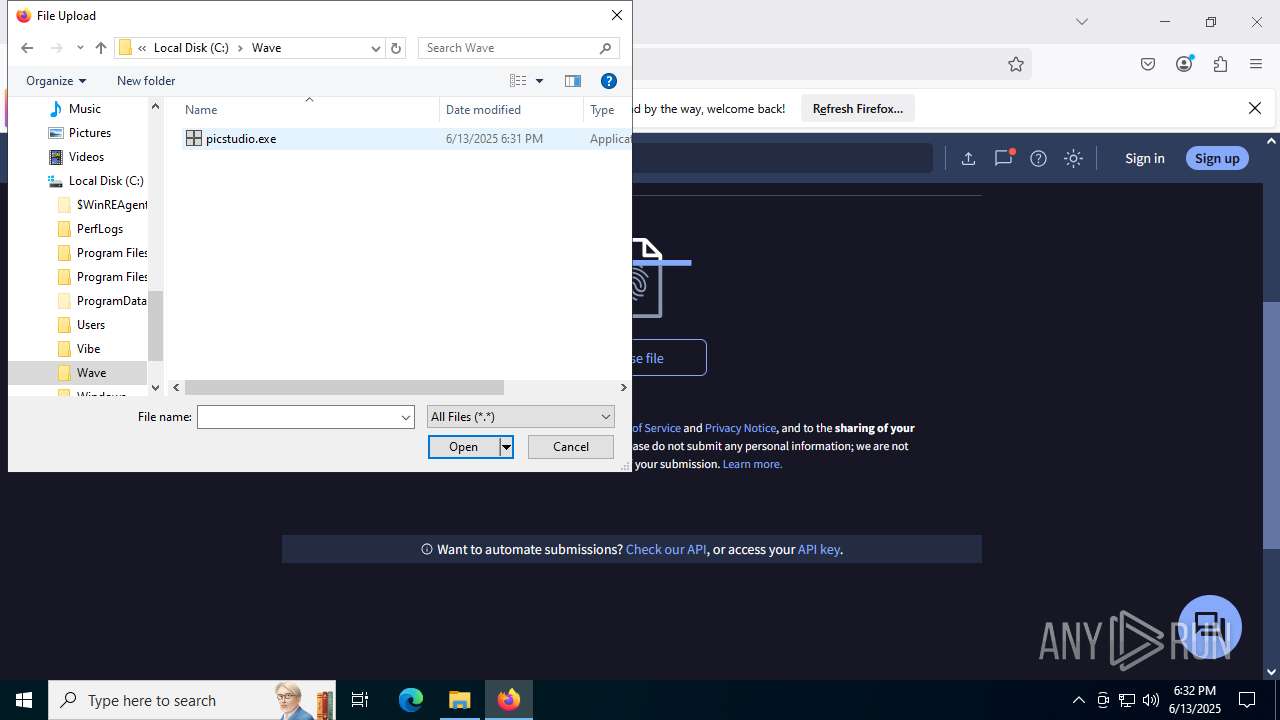
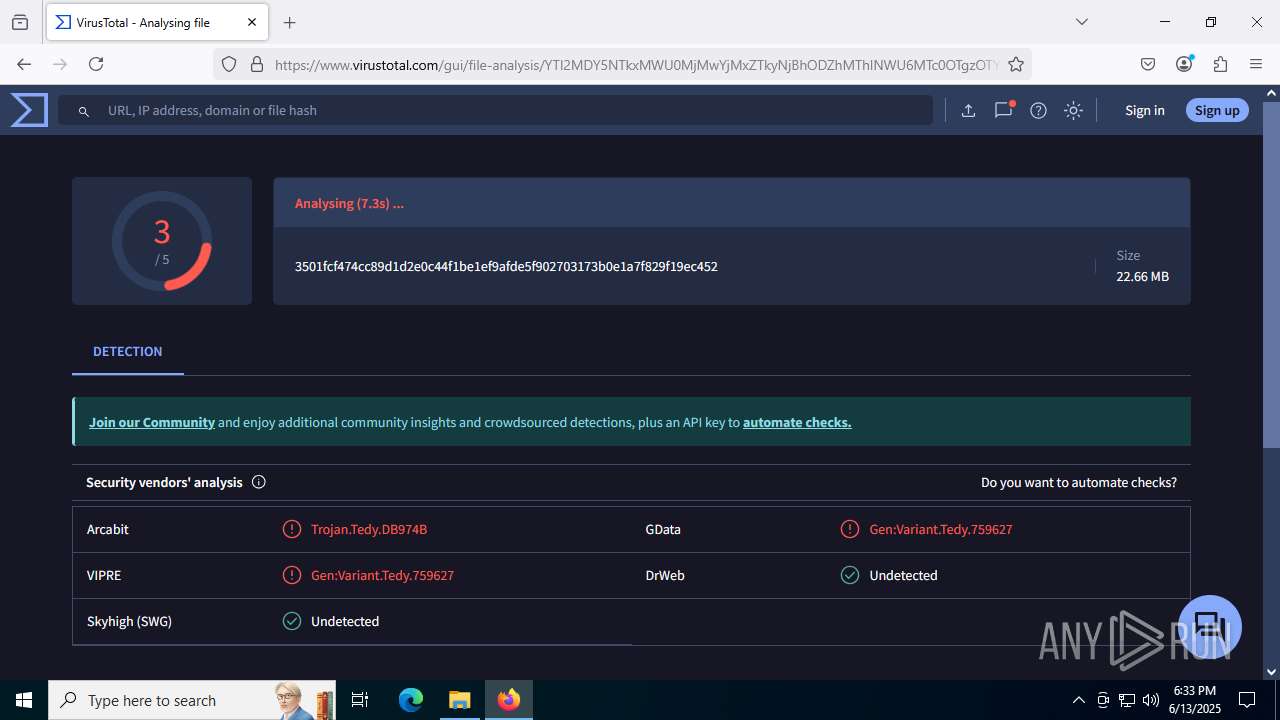
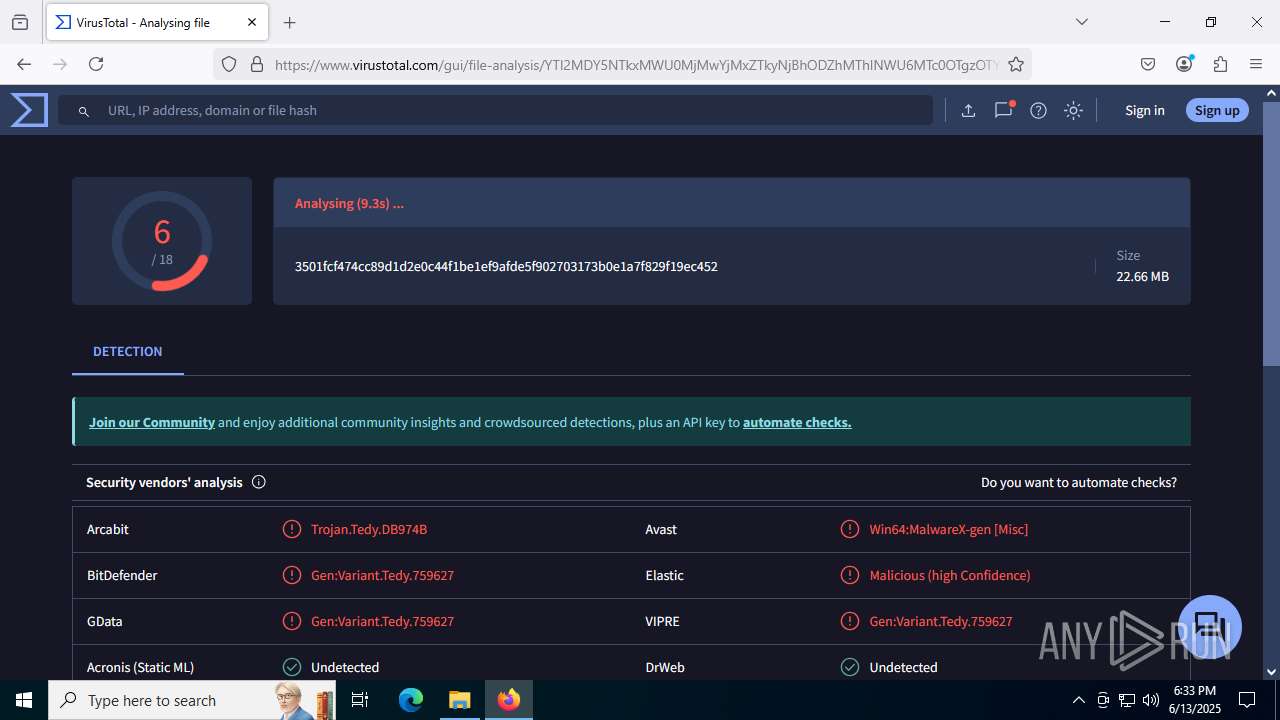
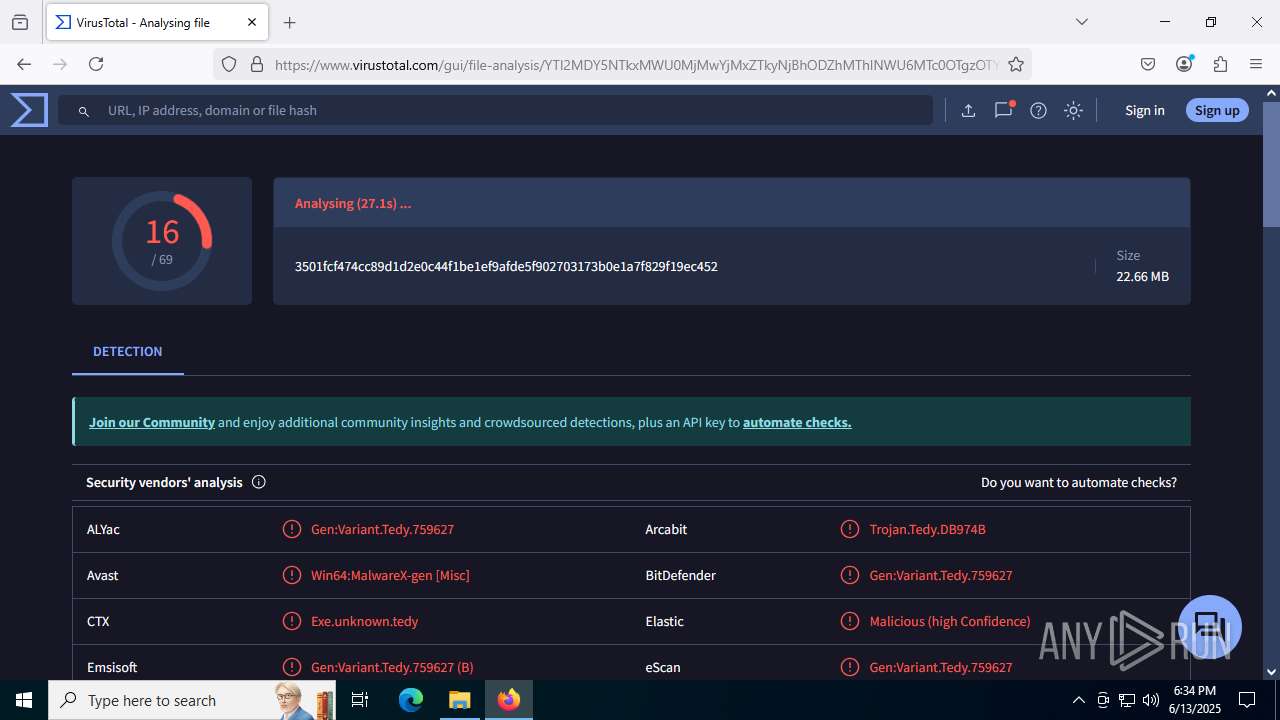
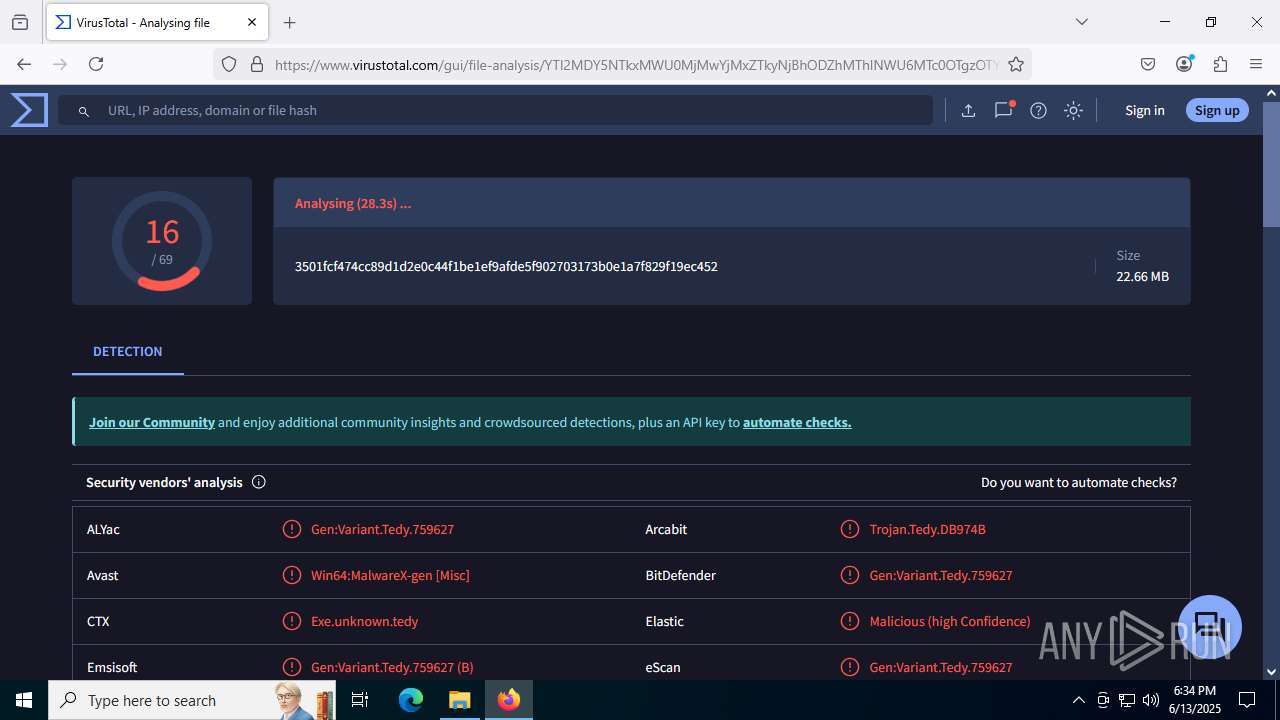
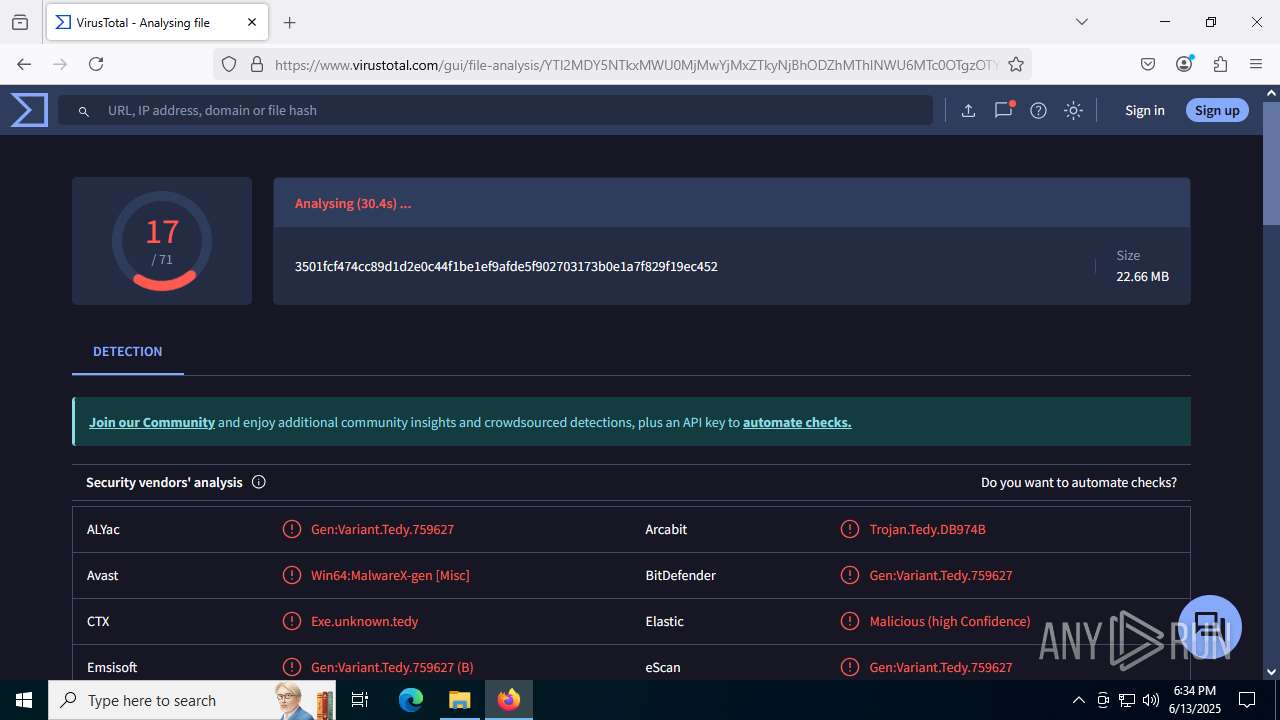
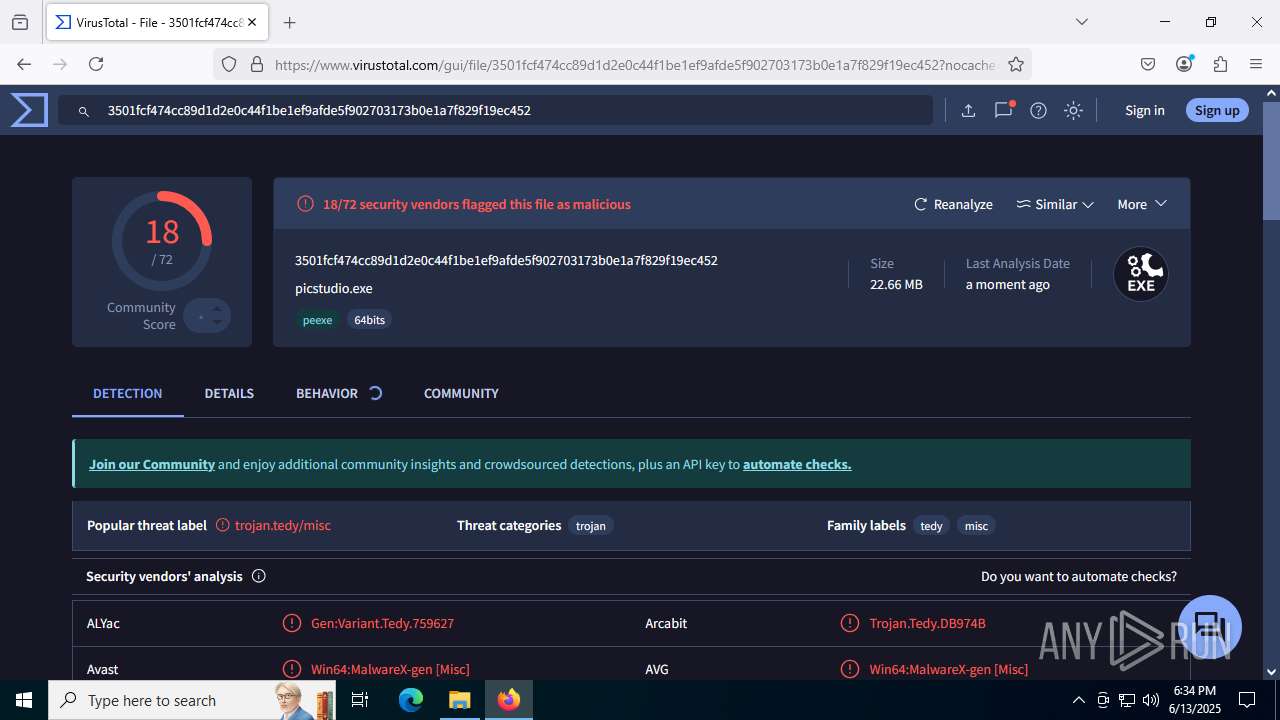
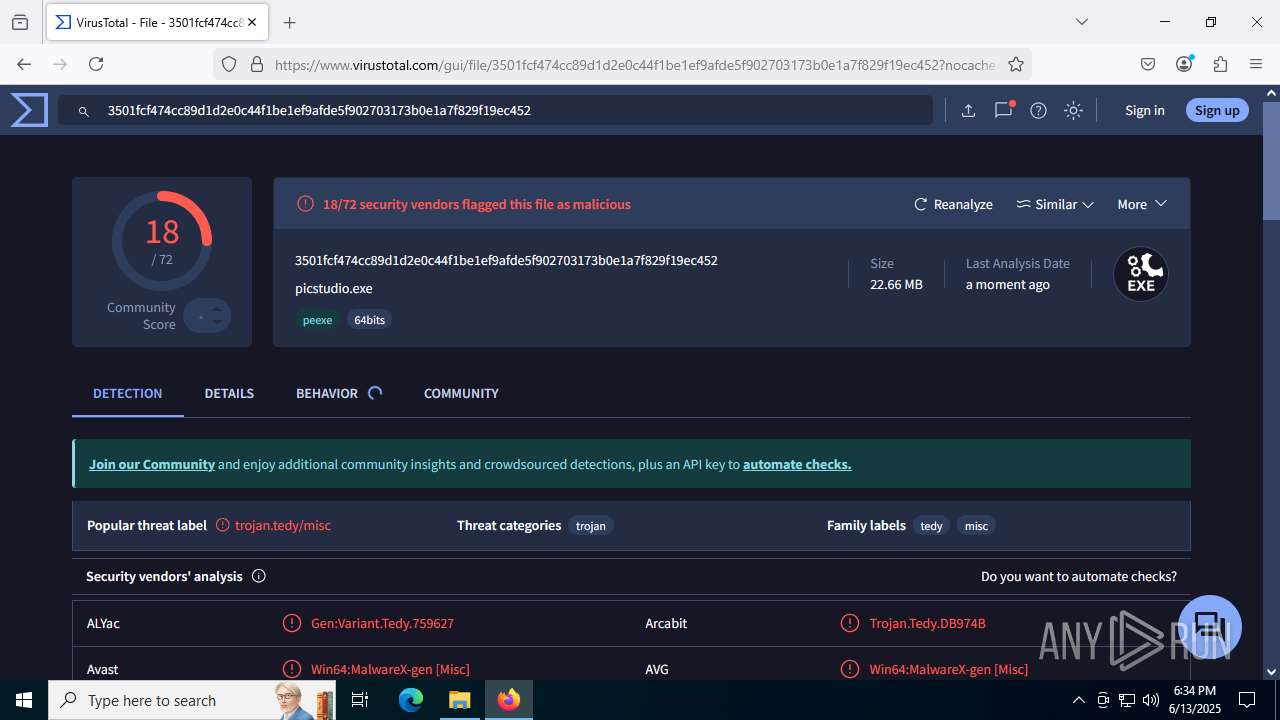
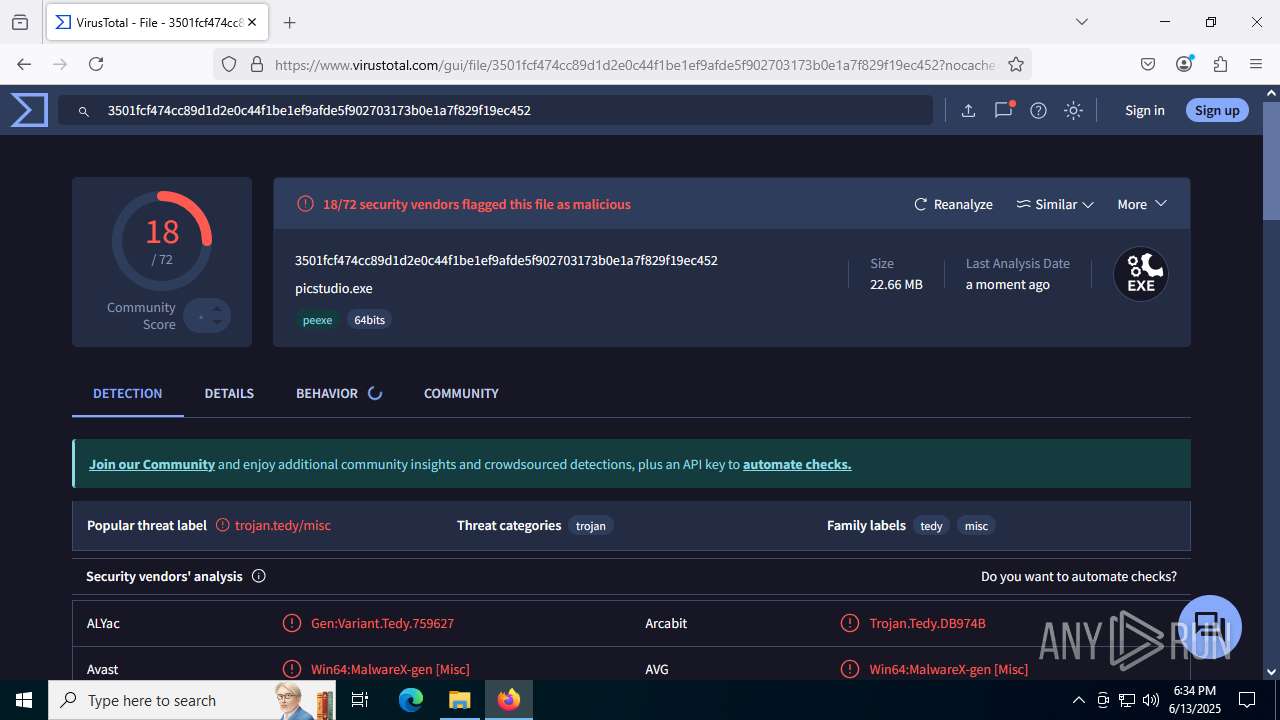
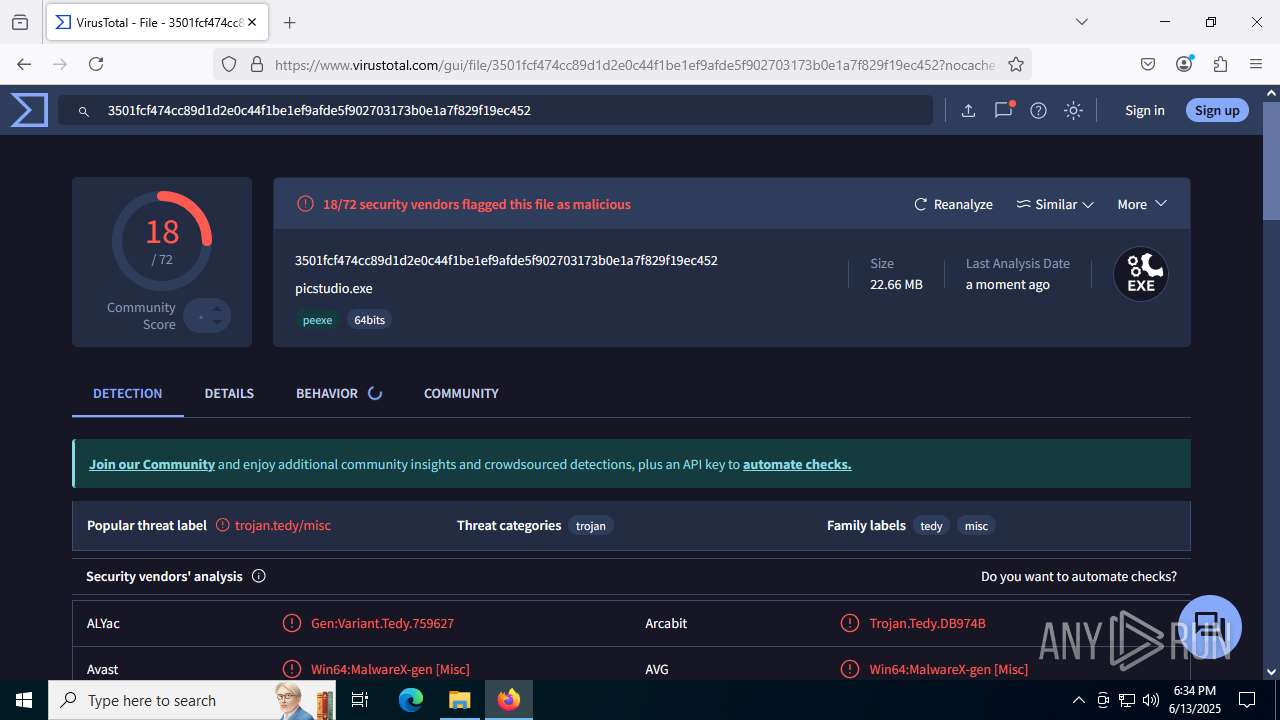
| File name: | guiaIRS_jyh.zip |
| Full analysis: | https://app.any.run/tasks/012844e9-cc5f-4fac-83be-f9a666b12169 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 18:30:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 02E3AF37C4636B7FDA5BFB314739F4CF |
| SHA1: | 73E6DD202BA1556CD1C4B59472BFC81169CBA0D7 |
| SHA256: | A996A01A75BACEB22023B26D1E2733045E98D18AF60254984C6E8DB7FA8C416D |
| SSDEEP: | 24576:q5cf+k4y/EstjgXztCveBD5UOaMtkOUlwSRW3X+H9uy3FdHsY+mPpdAERcMtH3Zh:q52+k4ZstjgXztCvED5UOaMtkOUlwuW8 |
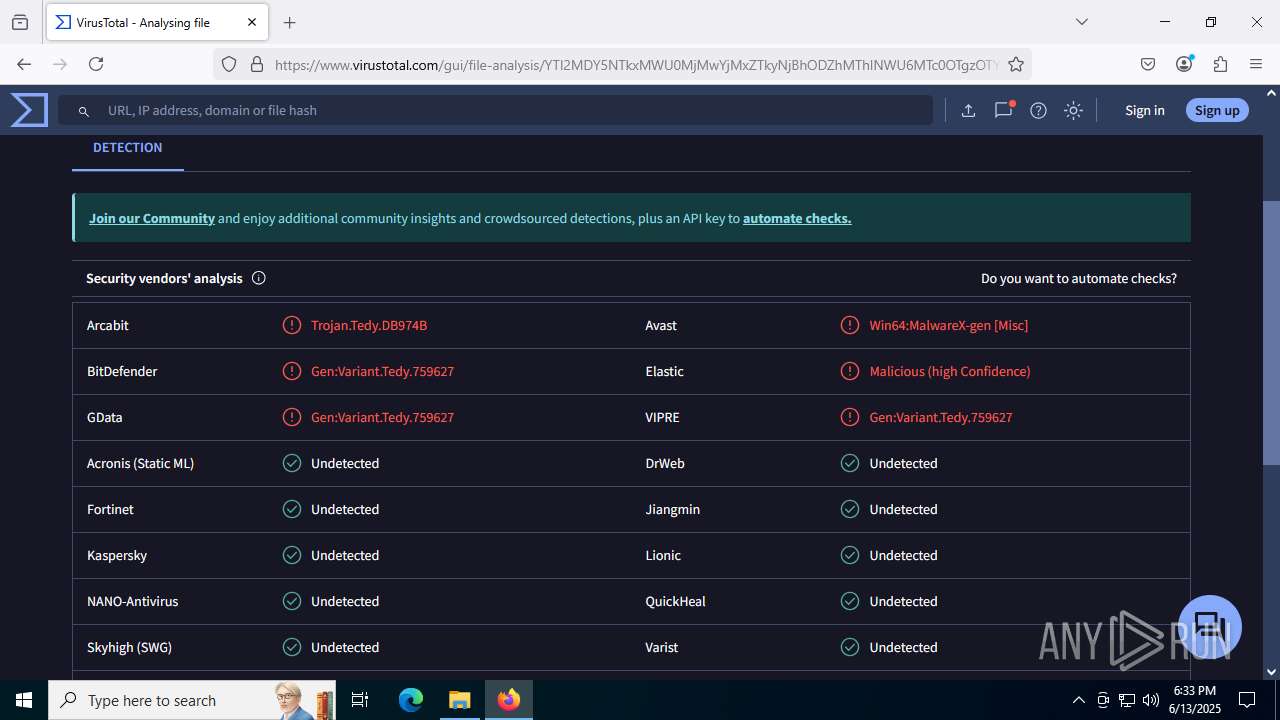
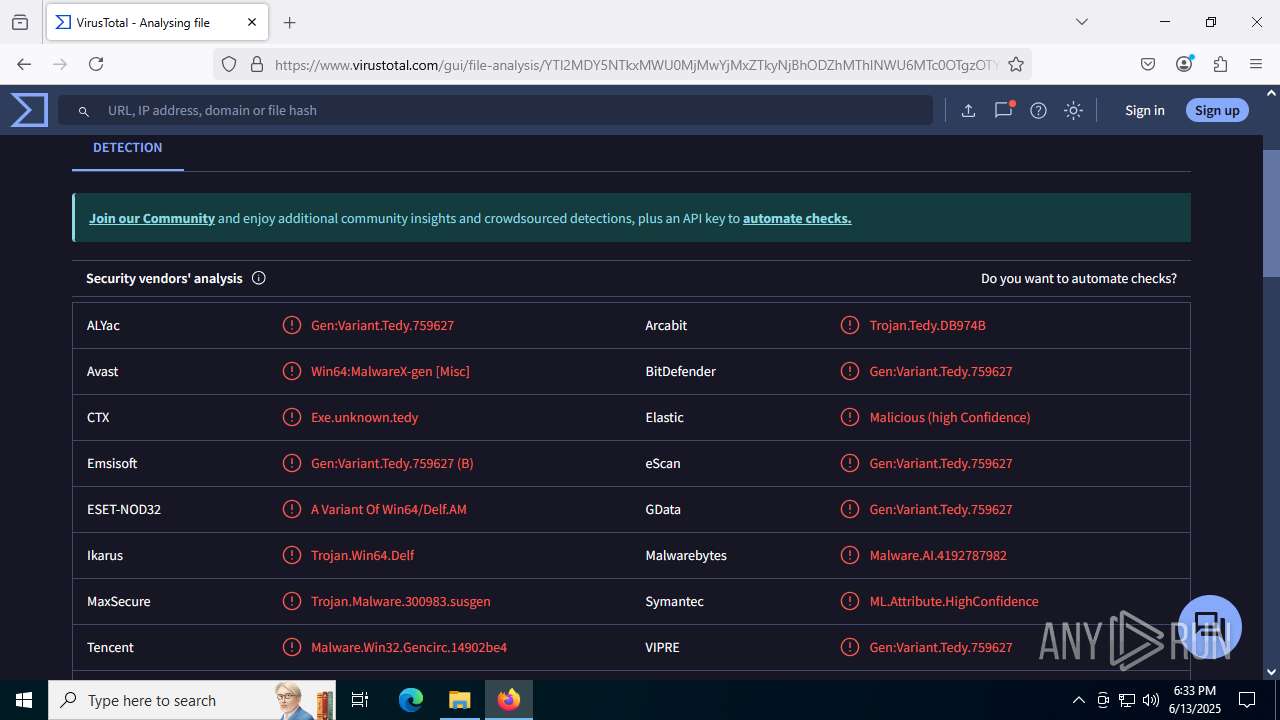
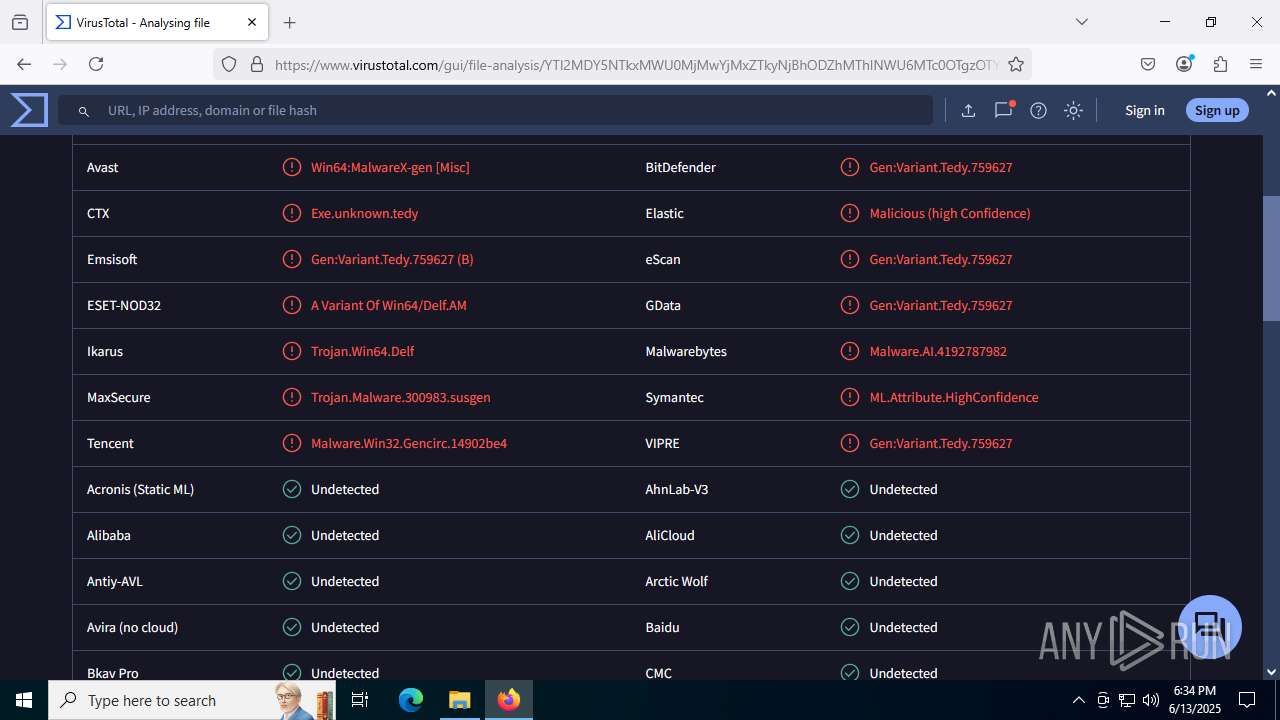
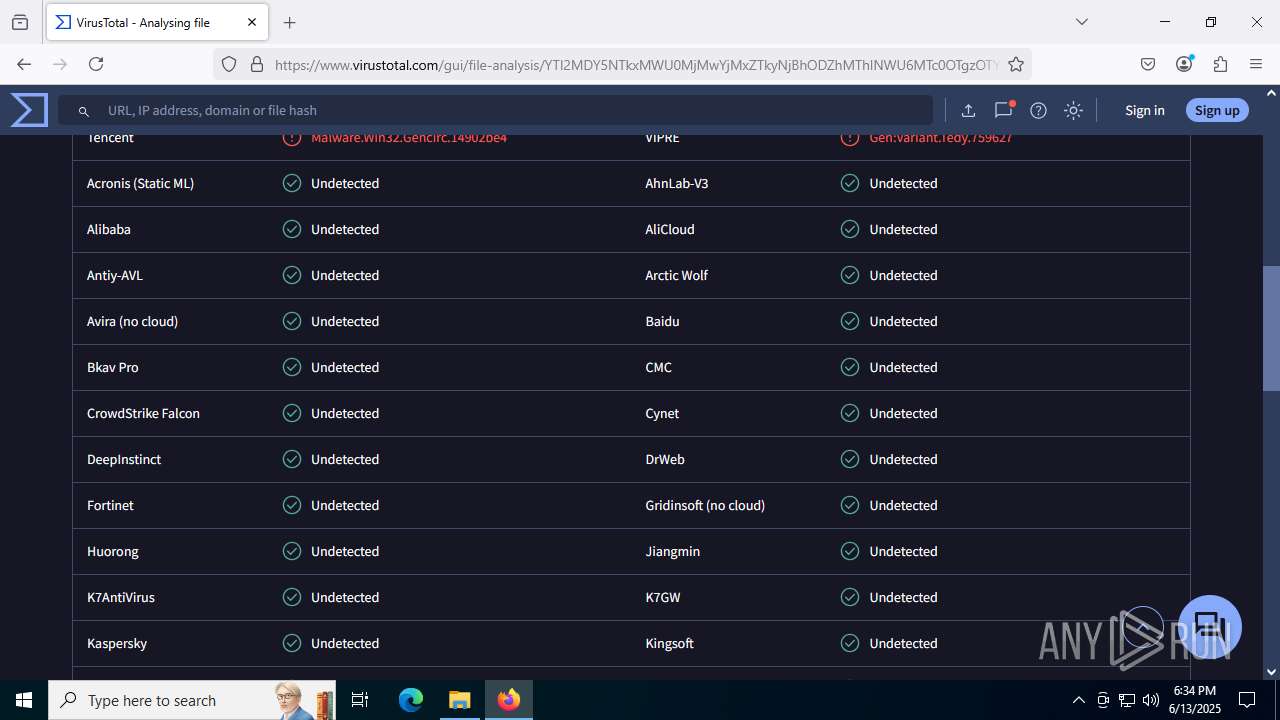
MALICIOUS
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 5612)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 5612)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 5612)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 5612)
Deletes a file (SCRIPT)
- wscript.exe (PID: 5612)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 5612)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 5612)
Runs shell command (SCRIPT)
- wscript.exe (PID: 5612)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 5612)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 5612)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 5612)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 5612)
Creates a Folder object (SCRIPT)
- wscript.exe (PID: 5612)
Executable content was dropped or overwritten
- wscript.exe (PID: 5612)
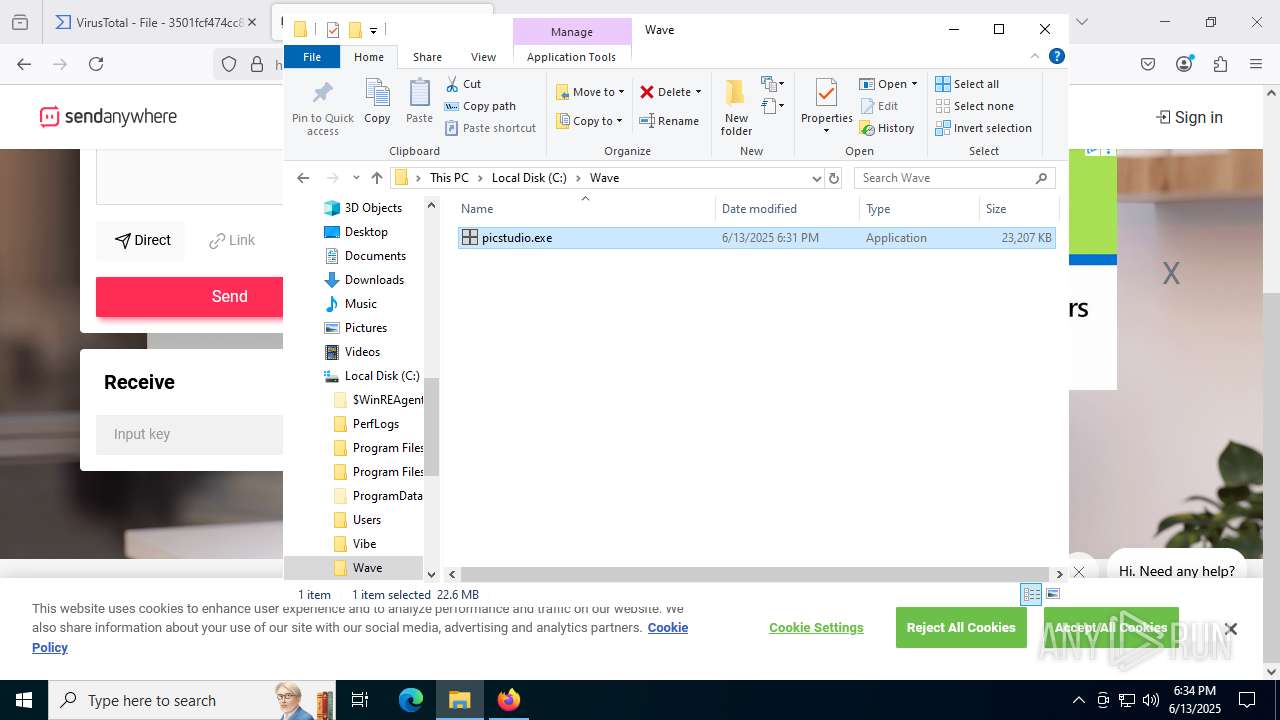
- fontdesign.exe (PID: 7680)
Likely accesses (executes) a file from the Public directory
- fontdesign.exe (PID: 7680)
Reads security settings of Internet Explorer
- fontdesign.exe (PID: 7680)
There is functionality for taking screenshot (YARA)
- notesimple.exe (PID: 5476)
- picstudio.exe (PID: 3800)
Connects to the server without a host name
- picstudio.exe (PID: 3800)
INFO
Manual execution by a user
- wscript.exe (PID: 5612)
- firefox.exe (PID: 5500)
Checks proxy server information
- wscript.exe (PID: 5612)
- fontdesign.exe (PID: 7680)
The sample compiled with english language support
- wscript.exe (PID: 5612)
- fontdesign.exe (PID: 7680)
- firefox.exe (PID: 8140)
Application launched itself
- msedge.exe (PID: 6680)
- msedge.exe (PID: 640)
- firefox.exe (PID: 8140)
- firefox.exe (PID: 5500)
Checks supported languages
- fontdesign.exe (PID: 7680)
- identity_helper.exe (PID: 7980)
- notesimple.exe (PID: 5476)
- picstudio.exe (PID: 3800)
Reads the computer name
- fontdesign.exe (PID: 7680)
- identity_helper.exe (PID: 7980)
- notesimple.exe (PID: 5476)
- picstudio.exe (PID: 3800)
Reads Environment values
- identity_helper.exe (PID: 7980)
- picstudio.exe (PID: 3800)
- notesimple.exe (PID: 5476)
Compiled with Borland Delphi (YARA)
- fontdesign.exe (PID: 7680)
- notesimple.exe (PID: 5476)
- slui.exe (PID: 7584)
- picstudio.exe (PID: 3800)
Reads the software policy settings
- fontdesign.exe (PID: 7680)
Creates files or folders in the user directory
- fontdesign.exe (PID: 7680)
Reads the machine GUID from the registry
- fontdesign.exe (PID: 7680)
Process checks computer location settings
- fontdesign.exe (PID: 7680)
Executable content was dropped or overwritten
- firefox.exe (PID: 8140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:13 19:27:48 |
| ZipCRC: | 0x2f300cfb |
| ZipCompressedSize: | 857127 |
| ZipUncompressedSize: | 2801638 |
| ZipFileName: | guiaIRS_jyh.vbs |
Total processes
229
Monitored processes
80
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4828,i,1515331132517355392,10399560383034486175,262144 --variations-seed-version --mojo-platform-channel-handle=4864 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 640 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=2220,i,1515331132517355392,10399560383034486175,262144 --variations-seed-version --mojo-platform-channel-handle=2516 /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1192 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 4216 -prefsLen 44877 -prefMapHandle 4220 -prefMapSize 272997 -jsInitHandle 4240 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 4248 -initialChannelId {33b0c6fa-b1d6-4a07-8778-bea336b7d4cc} -parentPid 8140 -crashReporter "\\.\pipe\gecko-crash-server-pipe.8140" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 5 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5356 -prefsLen 39348 -prefMapHandle 4212 -prefMapSize 272997 -jsInitHandle 6088 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 2800 -initialChannelId {8131a5c4-49ad-4328-b90e-9f7e8f322b31} -parentPid 8140 -crashReporter "\\.\pipe\gecko-crash-server-pipe.8140" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 18 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 1580 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -isForBrowser -prefsHandle 5768 -prefsLen 39149 -prefMapHandle 5624 -prefMapSize 272997 -jsInitHandle 5792 -jsInitLen 247456 -parentBuildID 20250227124745 -ipcHandle 5712 -initialChannelId {c0379483-70da-46f7-83b9-f401c8b336b5} -parentPid 8140 -crashReporter "\\.\pipe\gecko-crash-server-pipe.8140" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 11 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 136.0 Modules
| |||||||||||||||
| 1688 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=4140,i,17427158412948986814,18024733680197576370,262144 --variations-seed-version --mojo-platform-channel-handle=4988 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1816 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc -parentBuildID 20250227124745 -prefsHandle 2200 -prefsLen 36520 -prefMapHandle 2204 -prefMapSize 272997 -ipcHandle 2212 -initialChannelId {e60c2df7-e5ef-40ff-9afa-0bf5bd0905e2} -parentPid 8140 -crashReporter "\\.\pipe\gecko-crash-server-pipe.8140" -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - 2 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 136.0 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\guiaIRS_jyh.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2228 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --disable-quic --message-loop-type-ui --string-annotations --always-read-main-dll --field-trial-handle=5236,i,17427158412948986814,18024733680197576370,262144 --variations-seed-version --mojo-platform-channel-handle=6044 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
58 101
Read events
57 902
Write events
180
Delete events
19
Modification events
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\guiaIRS_jyh.zip | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2044) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
20
Suspicious files
896
Text files
144
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6680 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF179356.TMP | — | |
MD5:— | SHA256:— | |||
| 6680 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF179356.TMP | — | |
MD5:— | SHA256:— | |||
| 6680 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF179356.TMP | — | |
MD5:— | SHA256:— | |||
| 6680 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6680 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6680 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6680 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF179366.TMP | — | |
MD5:— | SHA256:— | |||
| 6680 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5612 | wscript.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:D7787C6D770AFA8EC557E20095B11BA0 | SHA256:AB52D3E3279C149AF90E34502EAAA2391E78A6416111610B879C3211F51CC9A5 | |||
| 2044 | WinRAR.exe | C:\Users\admin\Desktop\guiaIRS_jyh.vbs | binary | |
MD5:7D4FE9E48A234FF5E122157465646E1E | SHA256:20ECEB9BA687C9701EBFC89ABB5C81770CF295FE1961C859180E6F0FDA753BC7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
118
TCP/UDP connections
335
DNS requests
447
Threats
44
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3800 | picstudio.exe | PUT | 200 | 94.241.141.101:80 | http://94.241.141.101/dm4/publi.php | unknown | — | — | unknown |
2940 | svchost.exe | GET | 200 | 2.23.197.184:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
8128 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750173188&P2=404&P3=2&P4=gyiu7B8sfkOC0r51hkJcnEWr6j9wAYwoc1QNR9NaEn6S4pJEUdJUwYAWs76PT3AsBNt0ioguLbnyvRYvm3gjsA%3d%3d | unknown | — | — | whitelisted |
8128 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750173188&P2=404&P3=2&P4=gyiu7B8sfkOC0r51hkJcnEWr6j9wAYwoc1QNR9NaEn6S4pJEUdJUwYAWs76PT3AsBNt0ioguLbnyvRYvm3gjsA%3d%3d | unknown | — | — | whitelisted |
8128 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1750173188&P2=404&P3=2&P4=gyiu7B8sfkOC0r51hkJcnEWr6j9wAYwoc1QNR9NaEn6S4pJEUdJUwYAWs76PT3AsBNt0ioguLbnyvRYvm3gjsA%3d%3d | unknown | — | — | whitelisted |
4168 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.241.12:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5612 | wscript.exe | GET | 200 | 18.66.145.213:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1512 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4168 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4168 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 2.16.241.12:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
maliguetecomunicarcomfoco.s3.eu-north-1.amazonaws.com |
| shared |
ocsp.rootca1.amazontrust.com |
| whitelisted |
ocsp.r2m01.amazontrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3644 | msedge.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (is .gd) |
3644 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (is .gd) |
3644 | msedge.exe | Misc activity | INFO [ANY.RUN] Possible short link service (is .gd) |
3644 | msedge.exe | Misc activity | ET INFO URL Shortener Service Domain in DNS Lookup (is .gd) |
3644 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] BootstrapCDN (maxcdn .bootstrapcdn .com) |
3644 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] BootstrapCDN (maxcdn .bootstrapcdn .com) |
3644 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
3644 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
3644 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |
3644 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |