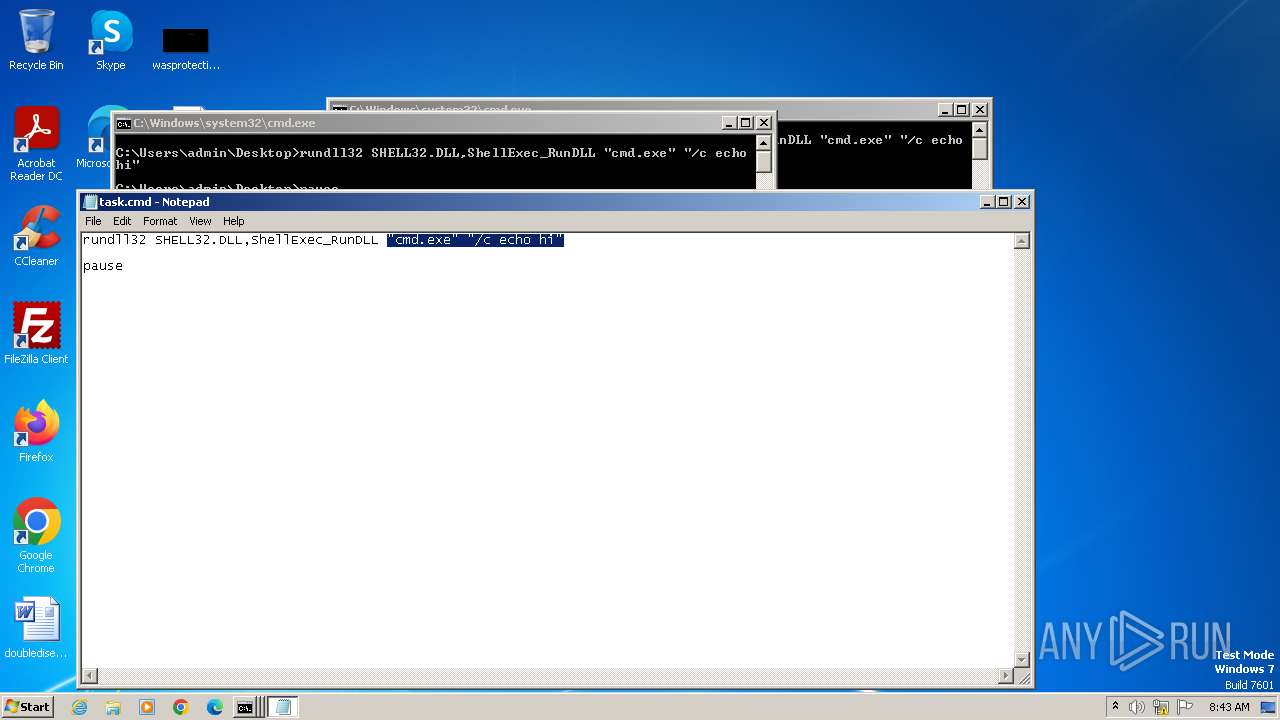
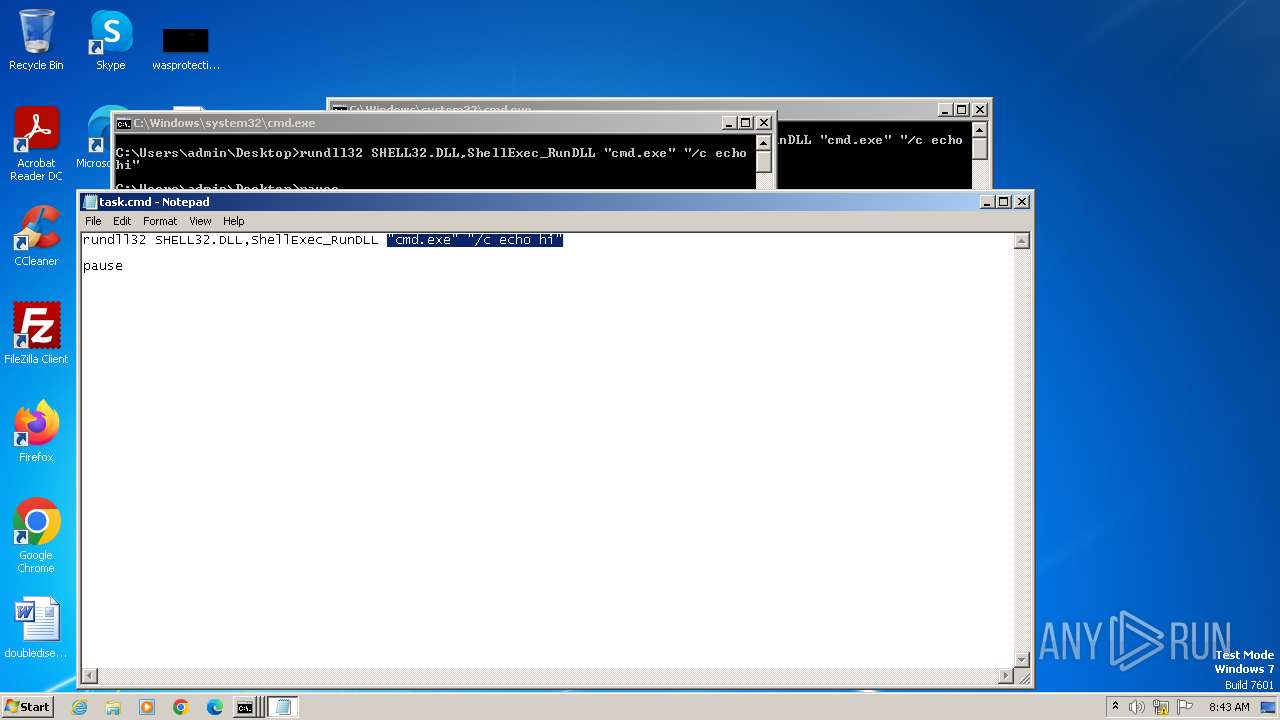
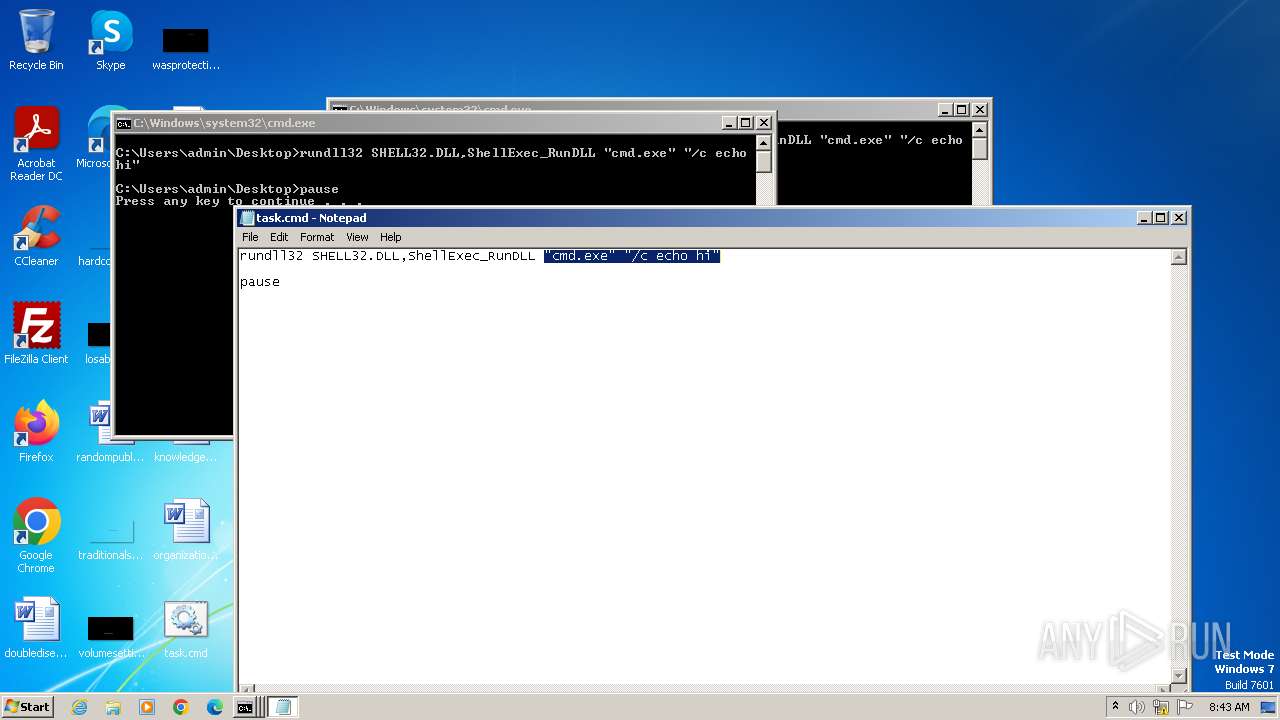
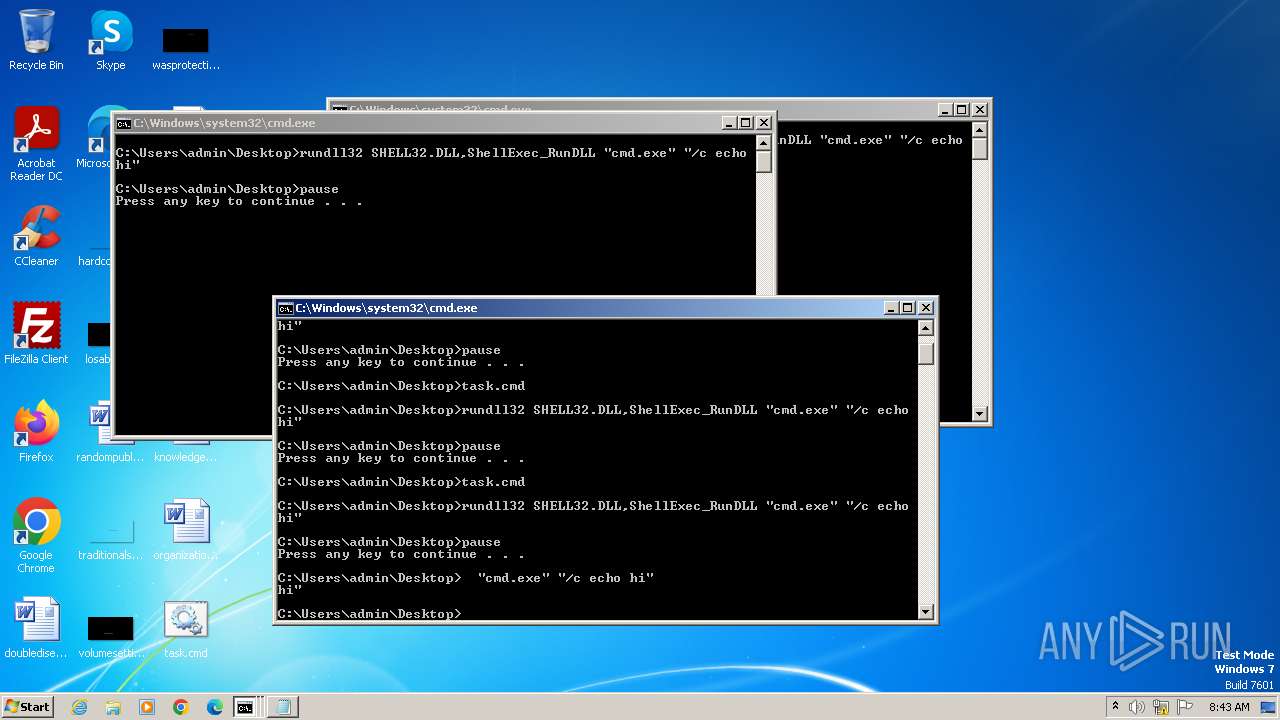
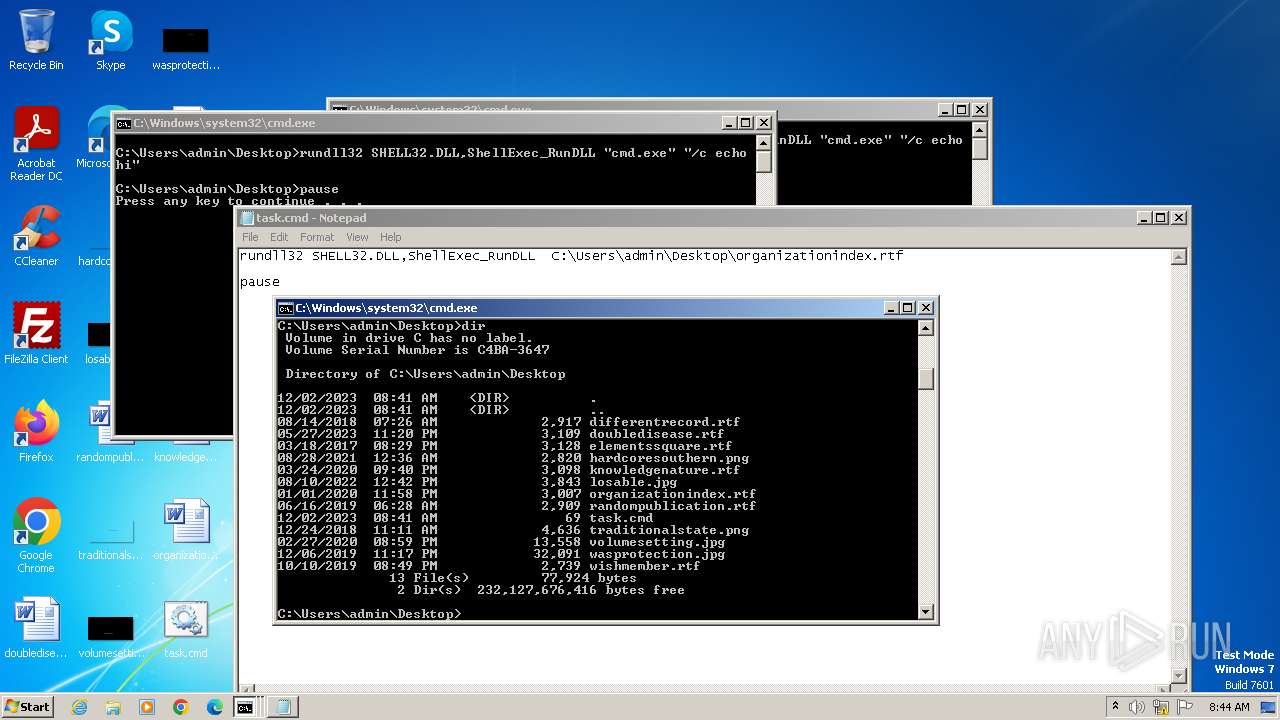
| File name: | task.cmd |
| Full analysis: | https://app.any.run/tasks/9a80f29d-95f8-45b9-9b13-18e9ed02c467 |
| Verdict: | Malicious activity |
| Analysis date: | December 02, 2023, 08:41:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | A9BE872F90C81AF9D9F5B3291D772CD5 |
| SHA1: | C8CA611022F102773B927E98484267681F558575 |
| SHA256: | A989DC40AC19FB47AA63A1FFBB0D4C1BE9CF44DD0414FF97CE03857D6D471423 |
| SSDEEP: | 3:m6FEztOprndKGFxKFeH7X:m6RlIGFM8H7X |
MALICIOUS
No malicious indicators.SUSPICIOUS
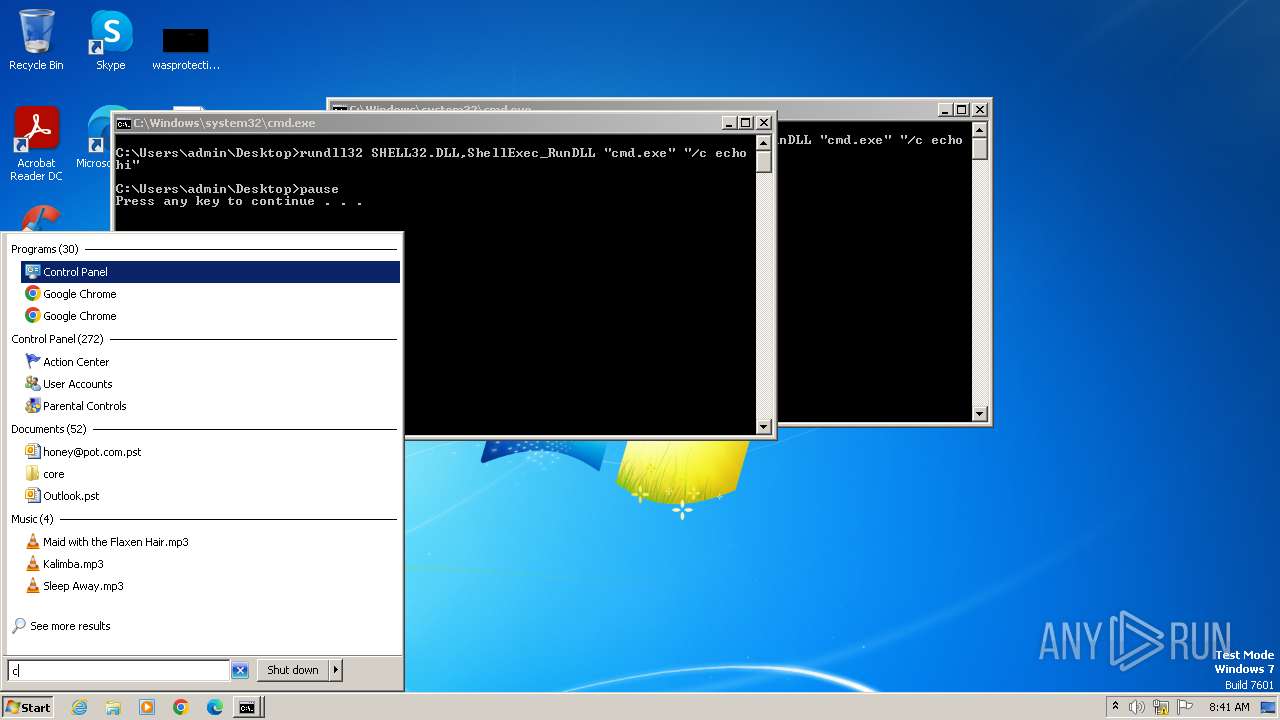
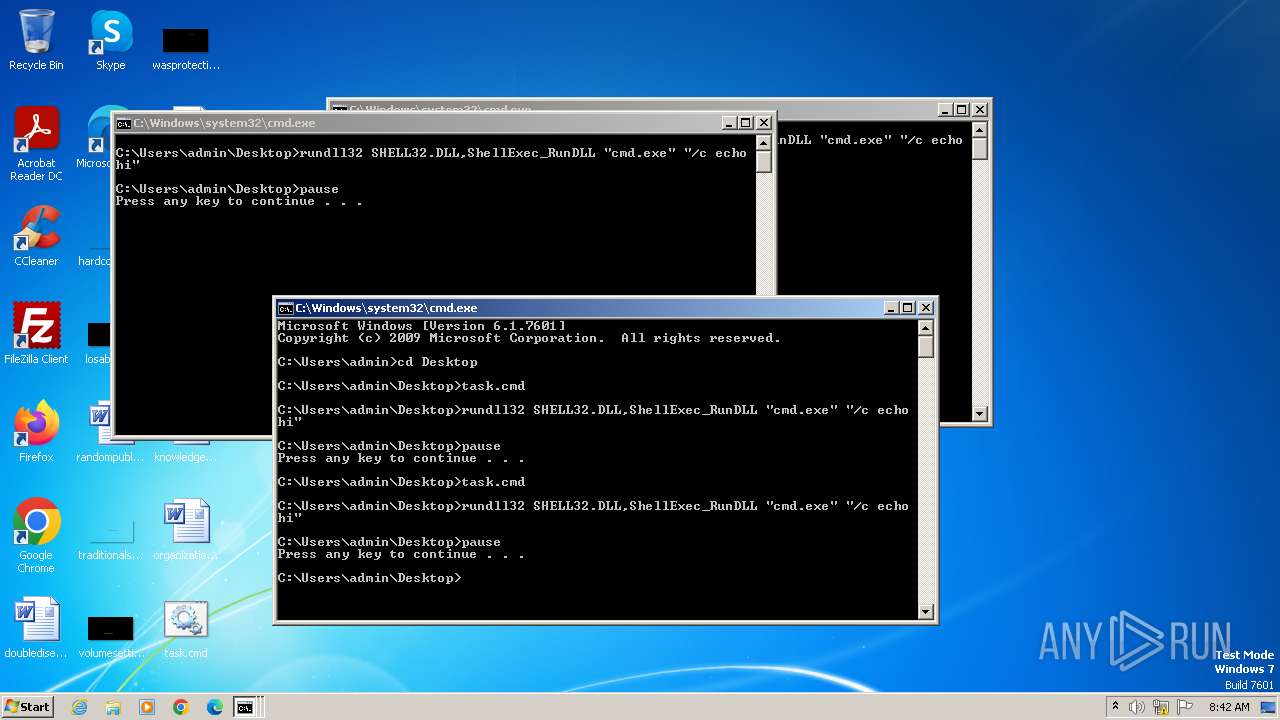
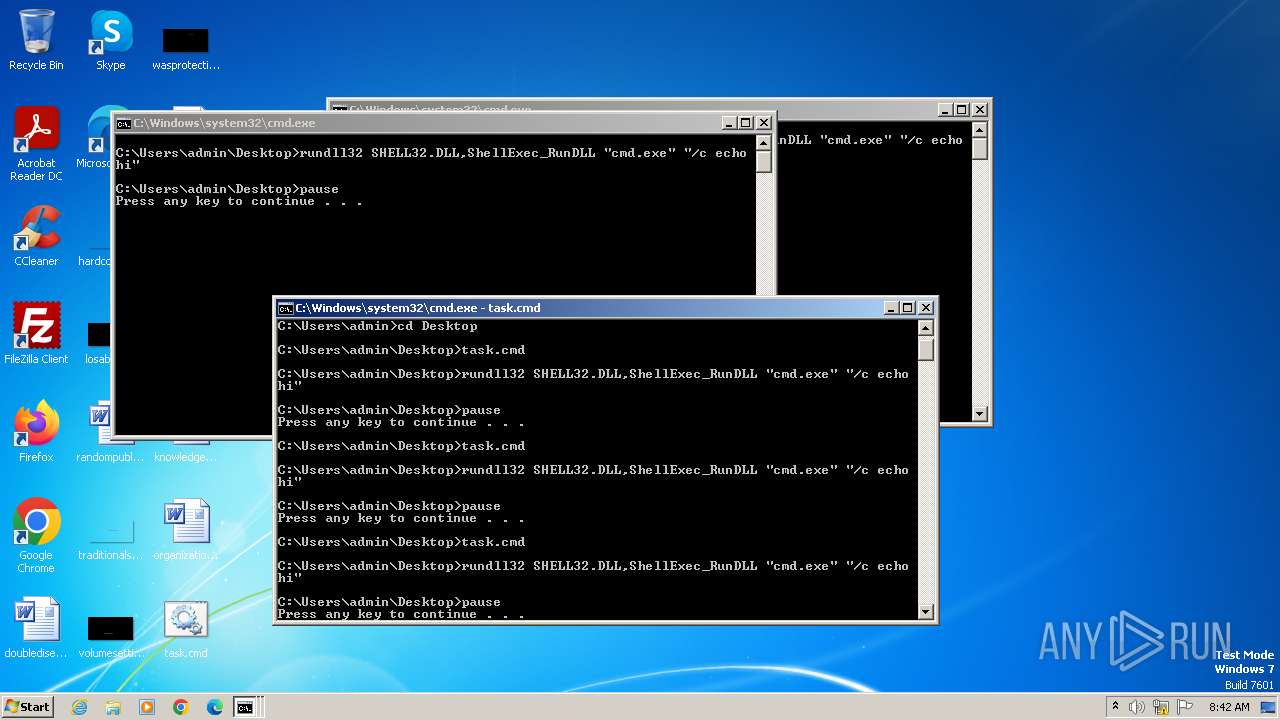
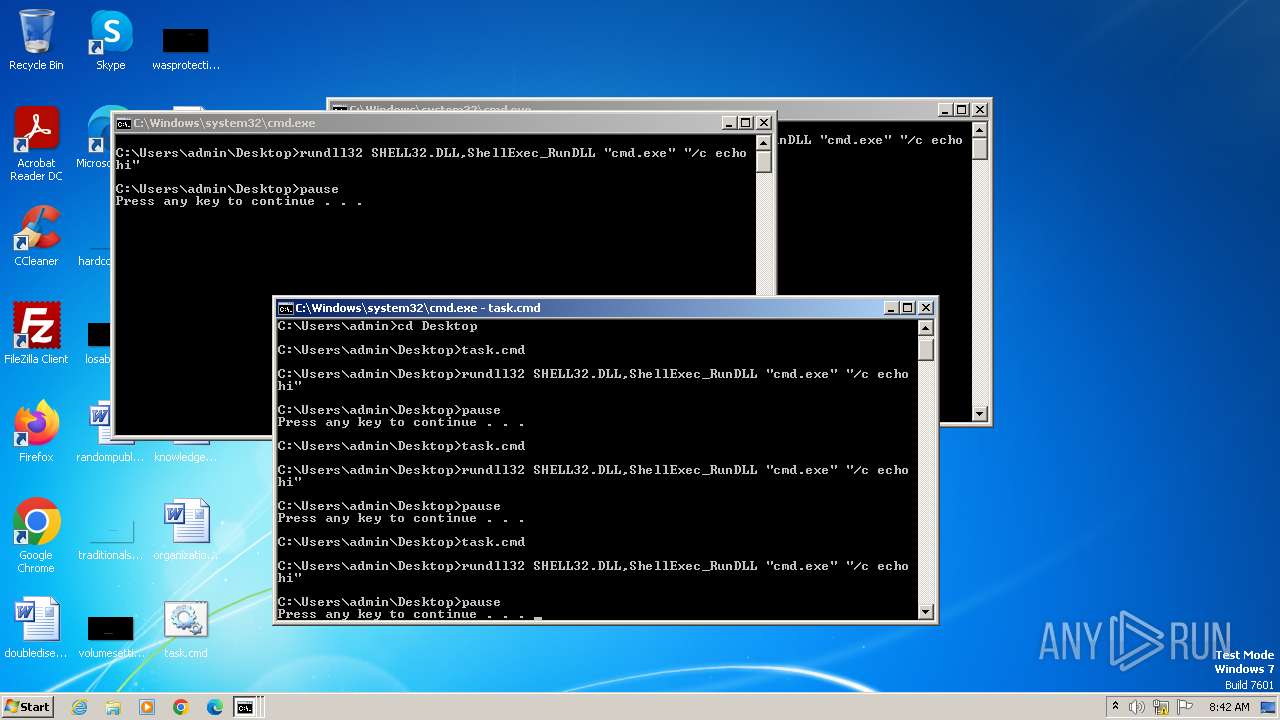
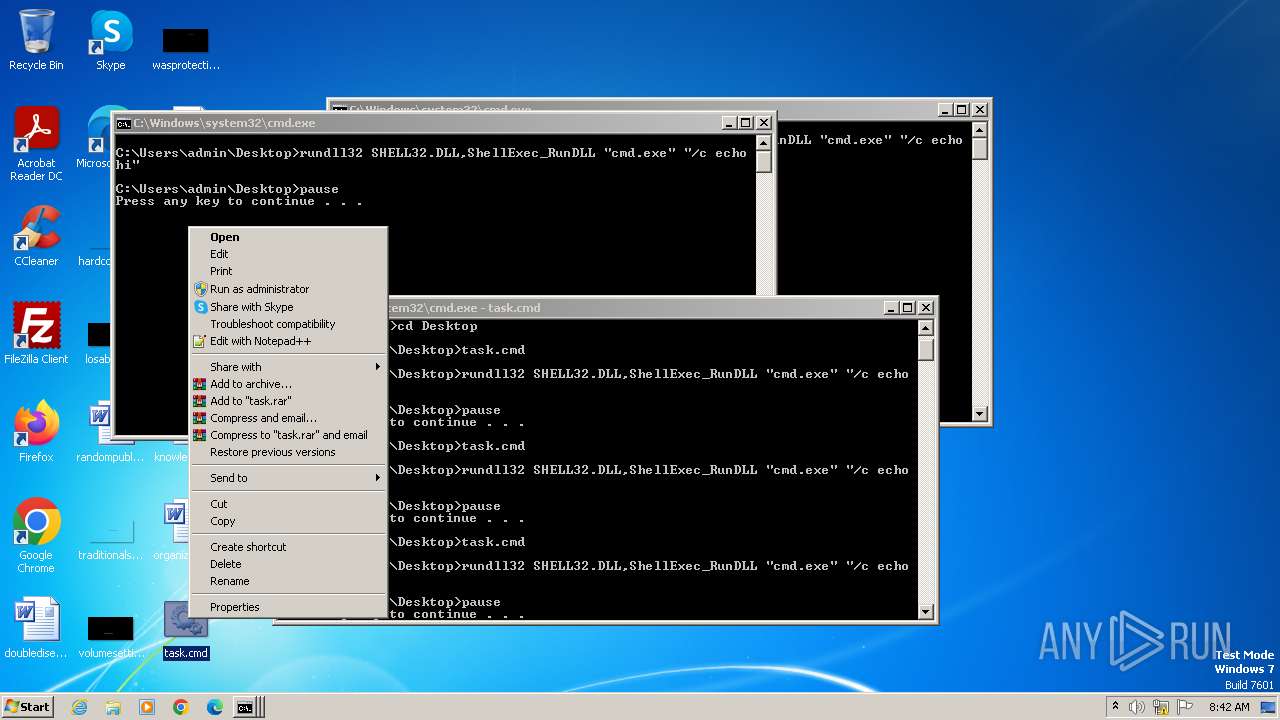
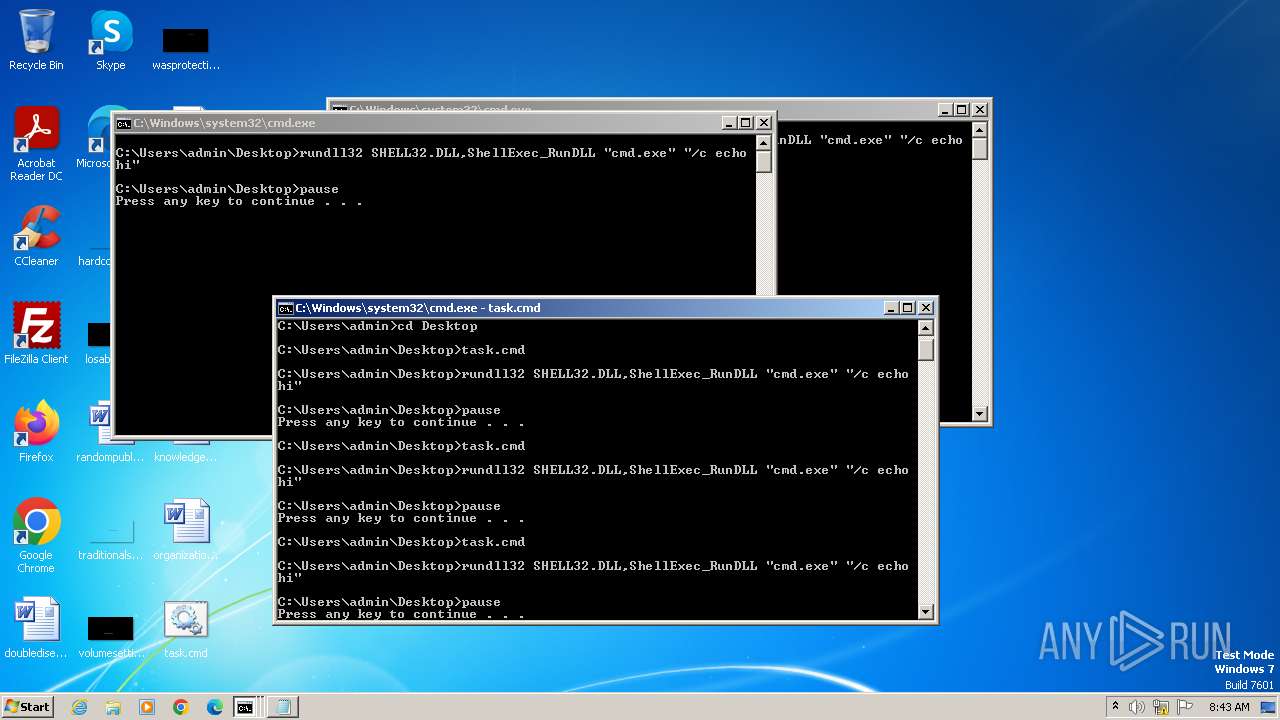
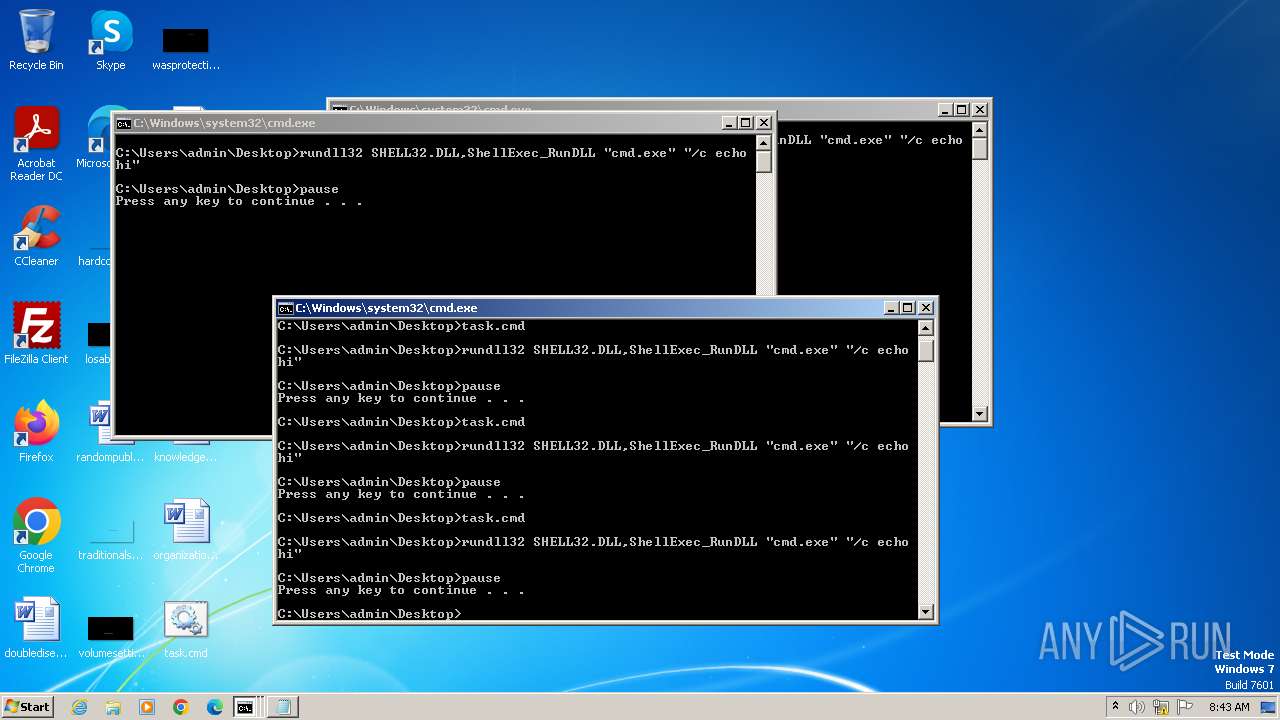
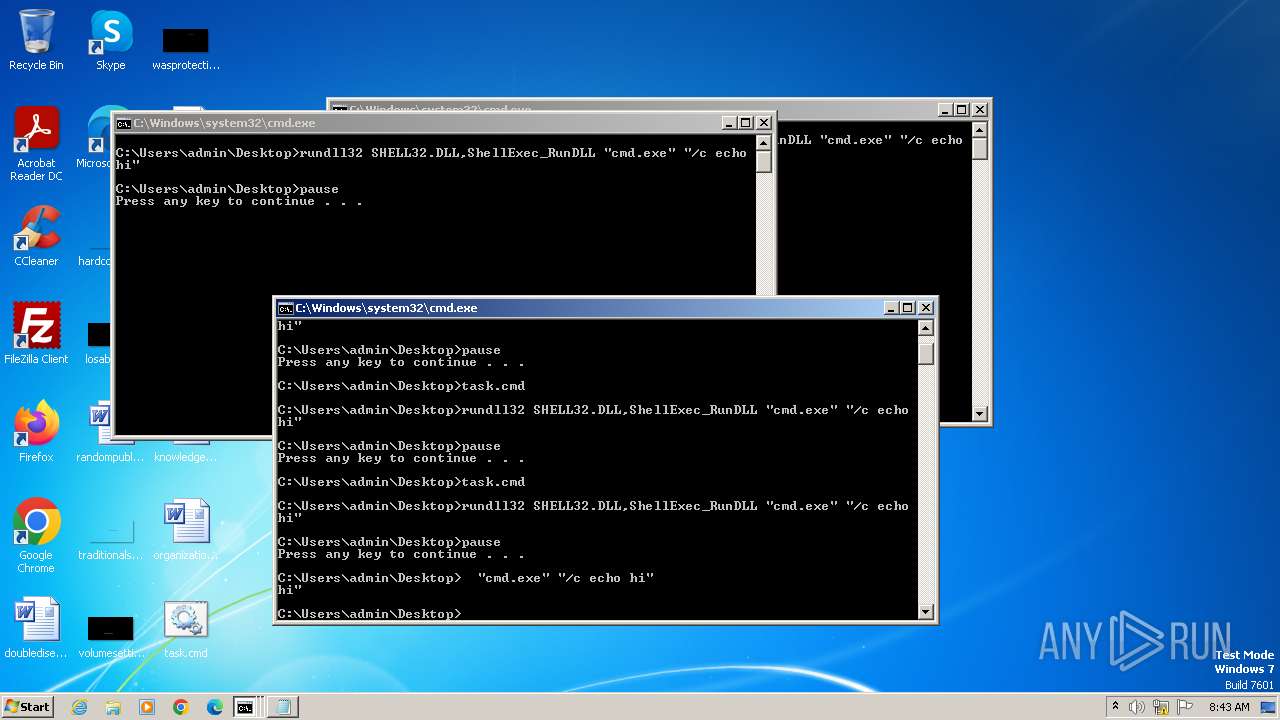
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 564)
- cmd.exe (PID: 1996)
- cmd.exe (PID: 1152)
Starts CMD.EXE for commands execution
- rundll32.exe (PID: 2740)
- rundll32.exe (PID: 2464)
- rundll32.exe (PID: 2532)
- rundll32.exe (PID: 3924)
- rundll32.exe (PID: 2764)
- cmd.exe (PID: 1152)
Reads the Internet Settings
- rundll32.exe (PID: 2740)
- rundll32.exe (PID: 2464)
- rundll32.exe (PID: 2532)
- rundll32.exe (PID: 3924)
- rundll32.exe (PID: 2764)
Process run an executable payload
- rundll32.exe (PID: 2740)
- rundll32.exe (PID: 2464)
- rundll32.exe (PID: 2532)
- rundll32.exe (PID: 3924)
- rundll32.exe (PID: 2764)
Application launched itself
- cmd.exe (PID: 1152)
INFO
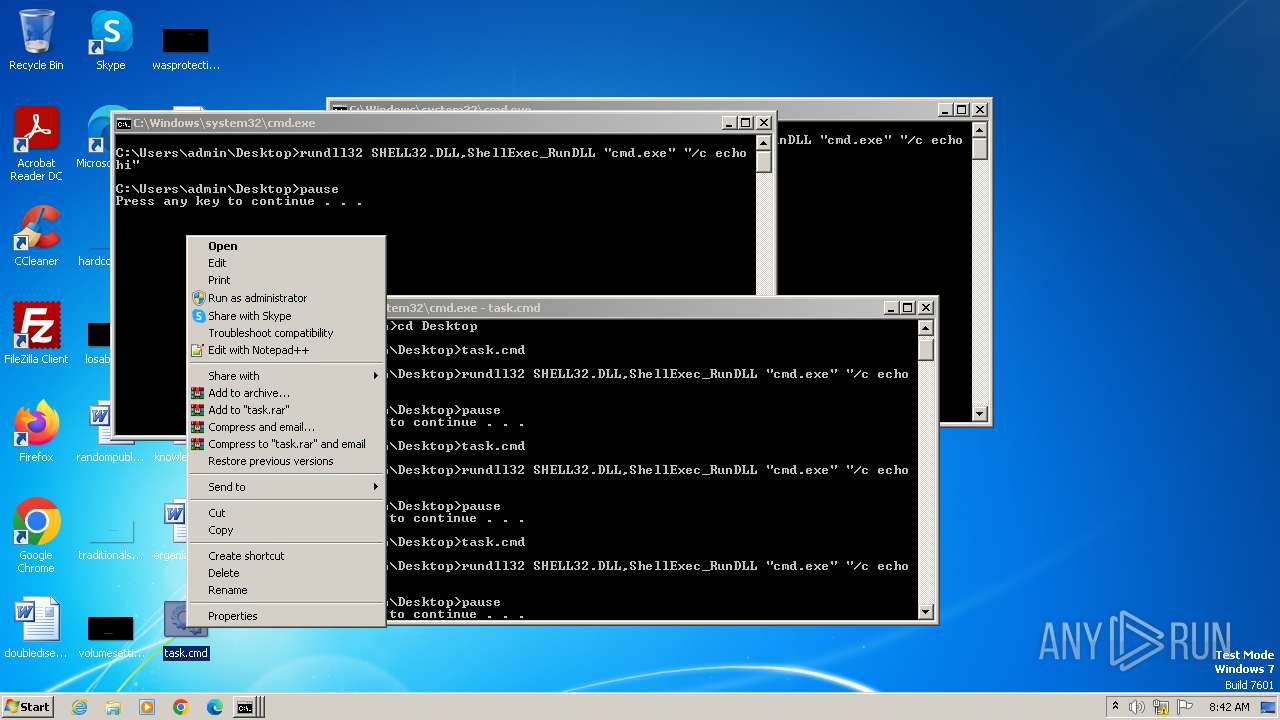
Manual execution by a user
- cmd.exe (PID: 1996)
- cmd.exe (PID: 1152)
- notepad.exe (PID: 2520)
Reads Microsoft Office registry keys
- rundll32.exe (PID: 3156)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
65
Monitored processes
17
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
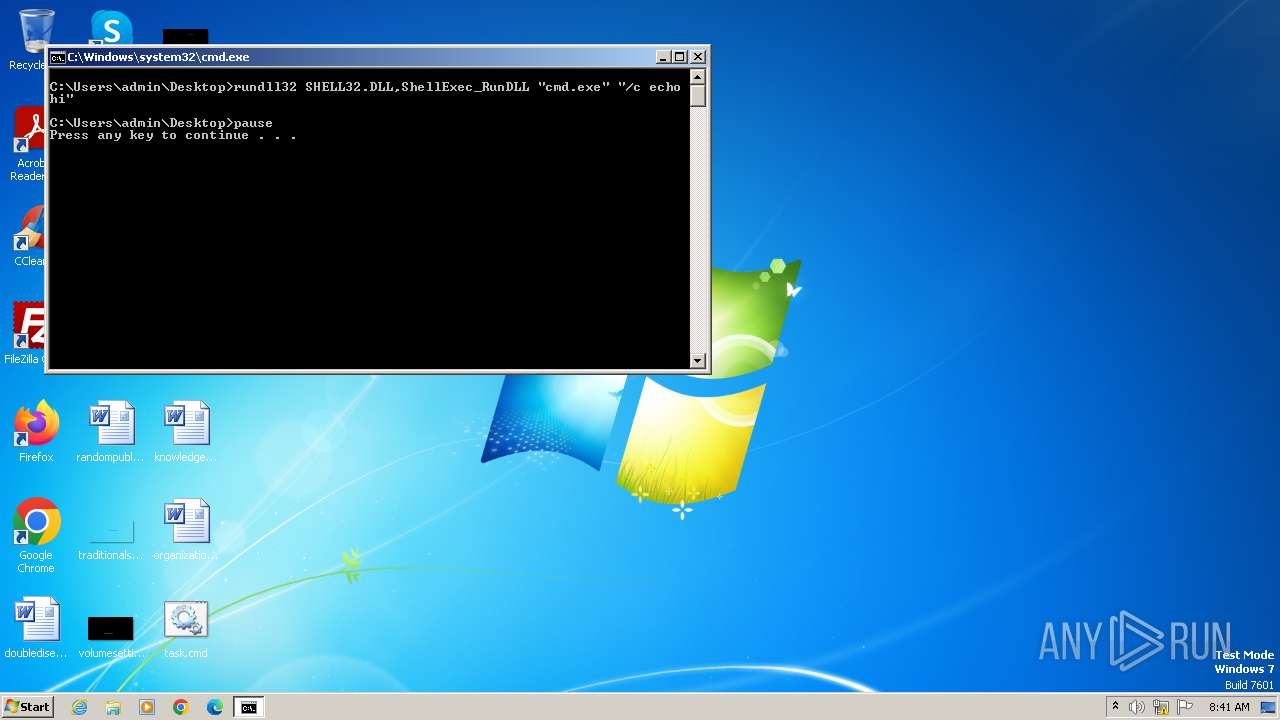
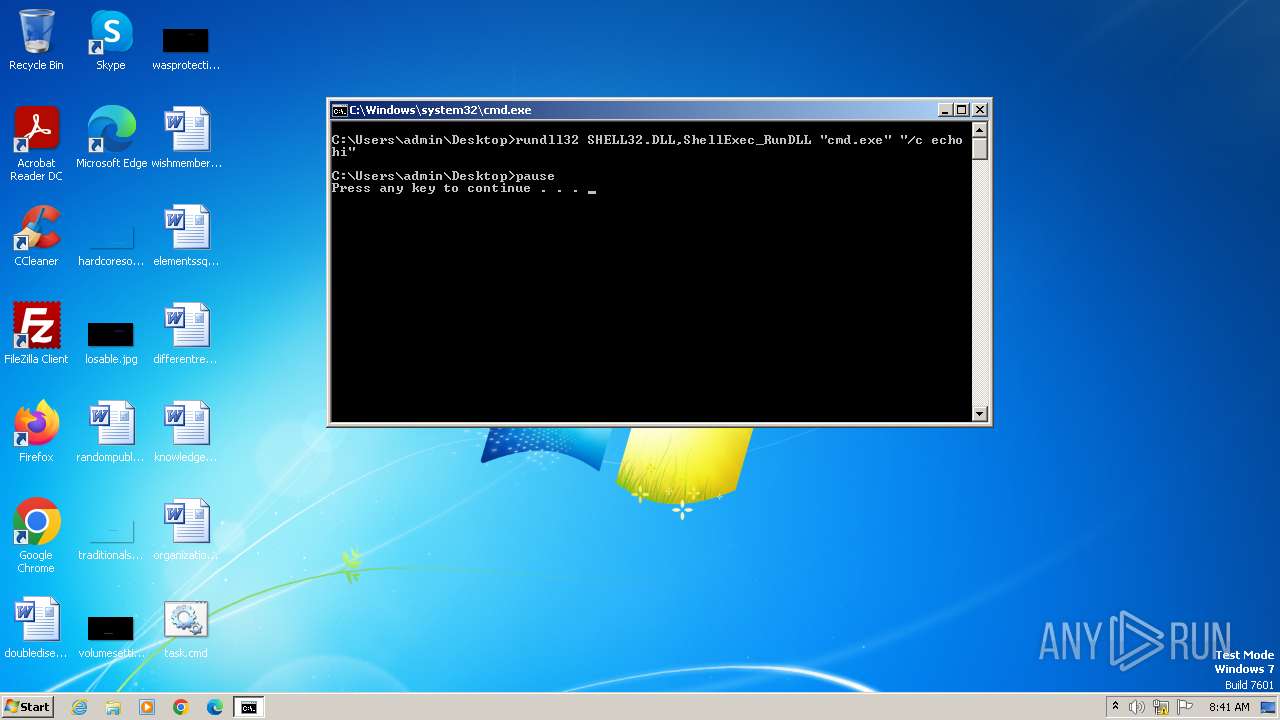
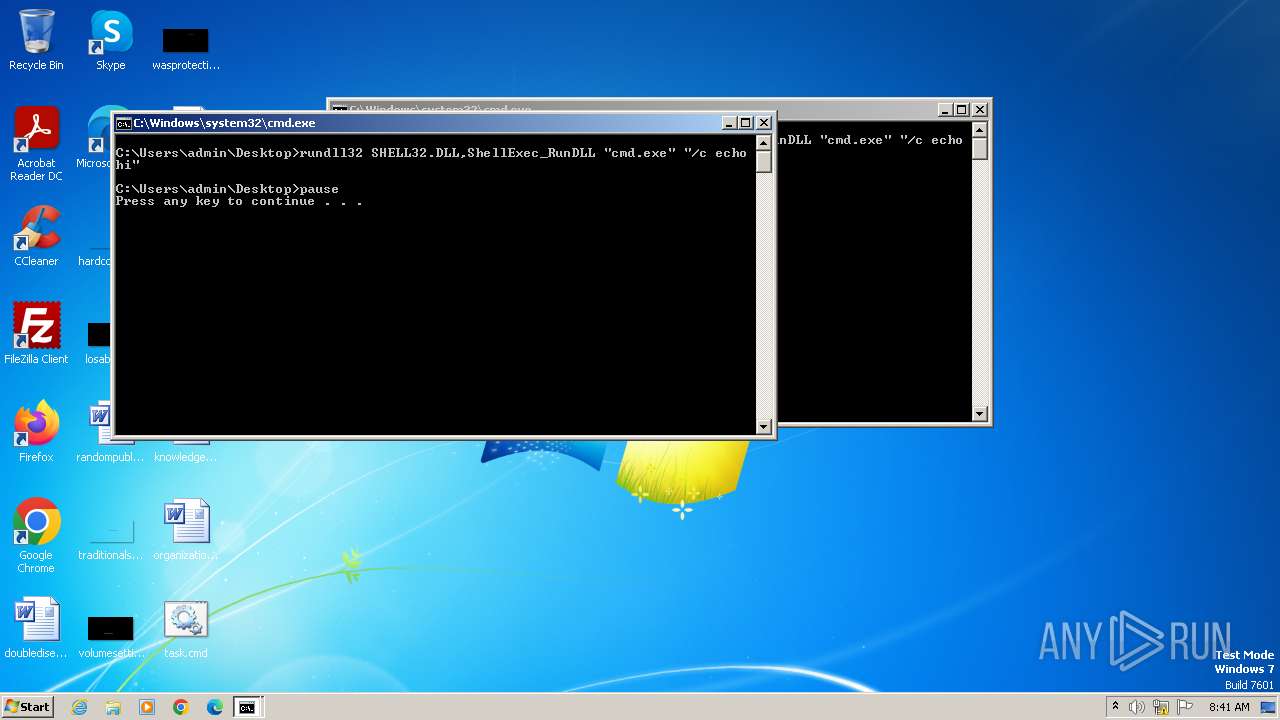
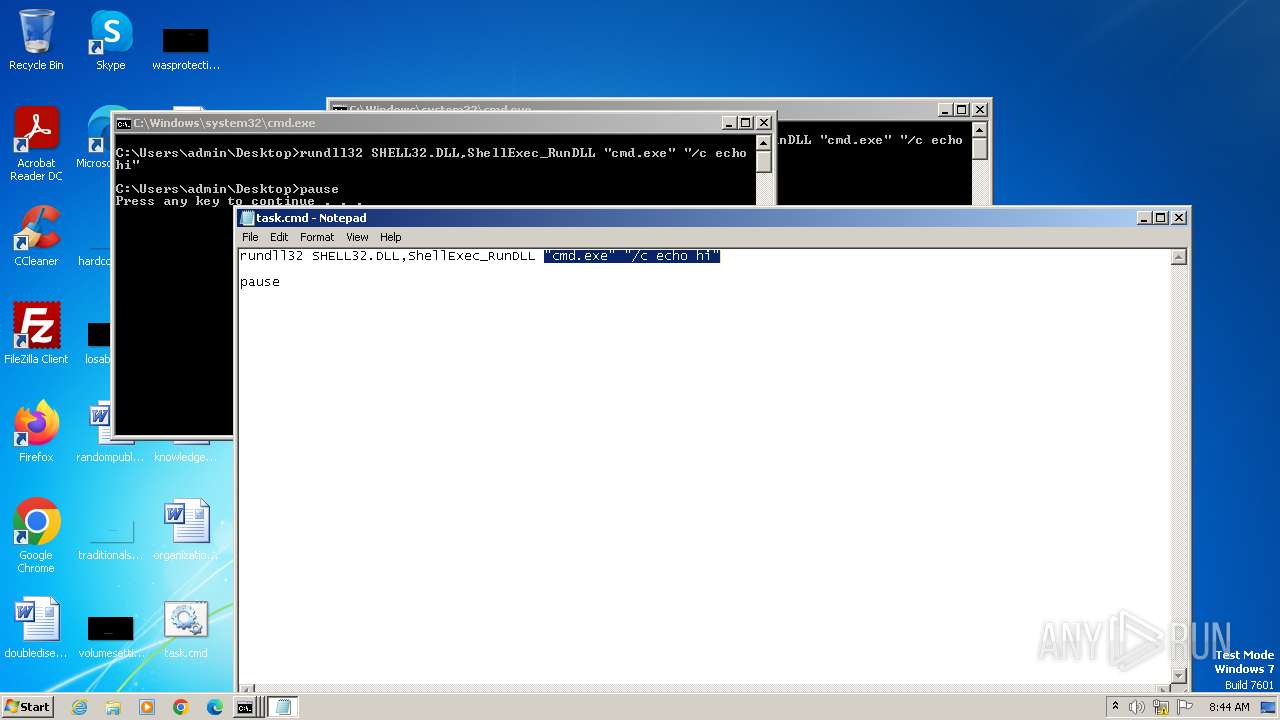
| 564 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\task.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 684 | "C:\Windows\system32\cmd.exe" "/c echo hi" | C:\Windows\System32\cmd.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1152 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1380 | "cmd.exe" "/c echo hi" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1852 | "C:\Windows\system32\cmd.exe" "/c echo hi" | C:\Windows\System32\cmd.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1996 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\Desktop\task.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2464 | rundll32 SHELL32.DLL,ShellExec_RunDLL "cmd.exe" "/c echo hi" | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 3221225547 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2520 | "C:\Windows\System32\NOTEPAD.EXE" C:\Users\admin\Desktop\task.cmd | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2532 | rundll32 SHELL32.DLL,ShellExec_RunDLL "cmd.exe" "/c echo hi" | C:\Windows\System32\rundll32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2668 | "C:\Windows\system32\cmd.exe" "/c echo hi" | C:\Windows\System32\cmd.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
3 503
Read events
3 001
Write events
357
Delete events
145
Modification events
| (PID) Process: | (2740) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2740) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2740) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2740) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2464) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2464) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2464) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2464) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2532) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2532) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
1
Suspicious files
4
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3340 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7380.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3340 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:C541DFE09511A60EE8852F5E53A87D17 | SHA256:1E9F66BFA7FBC74D500CC4B231D0EC45E0A556F8B888D470262FB8E9682A1672 | |||
| 3340 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:62F40420E351CCF4F8A6786B42361B55 | SHA256:8391B3A0A4259EDCBB831E02D952C5D47B5110835F5F861A8C500A9FD7670319 | |||
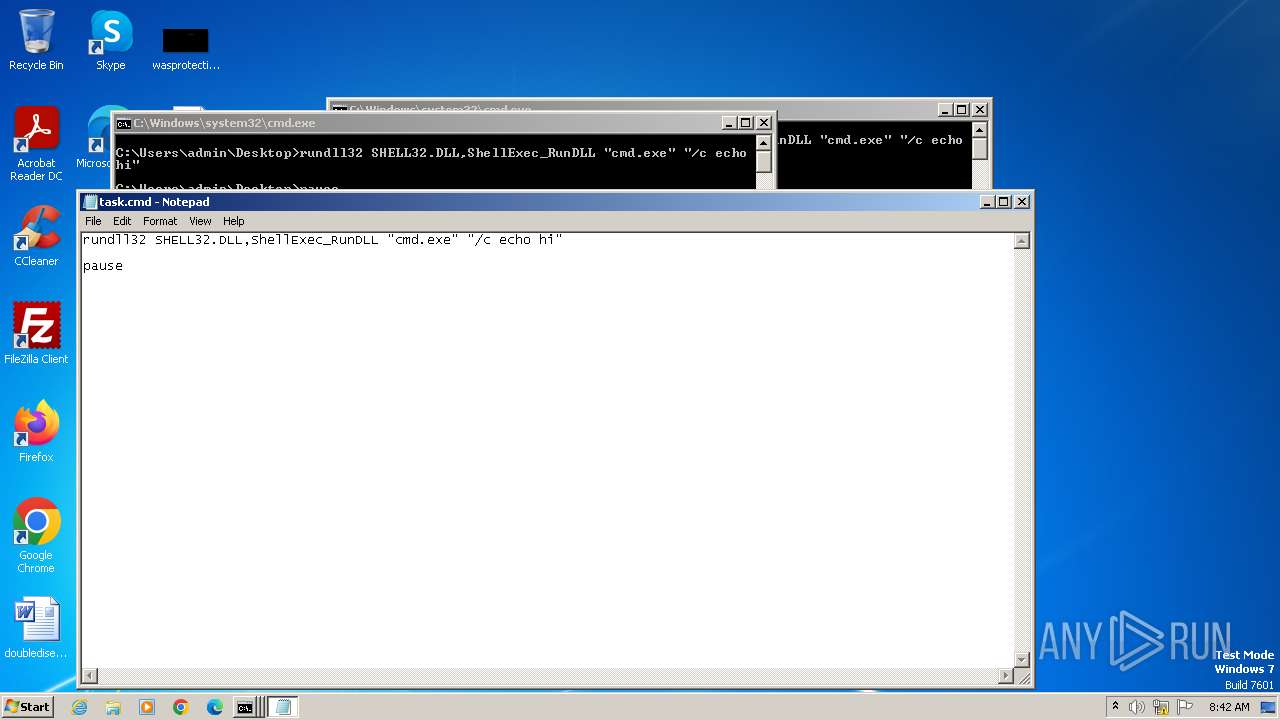
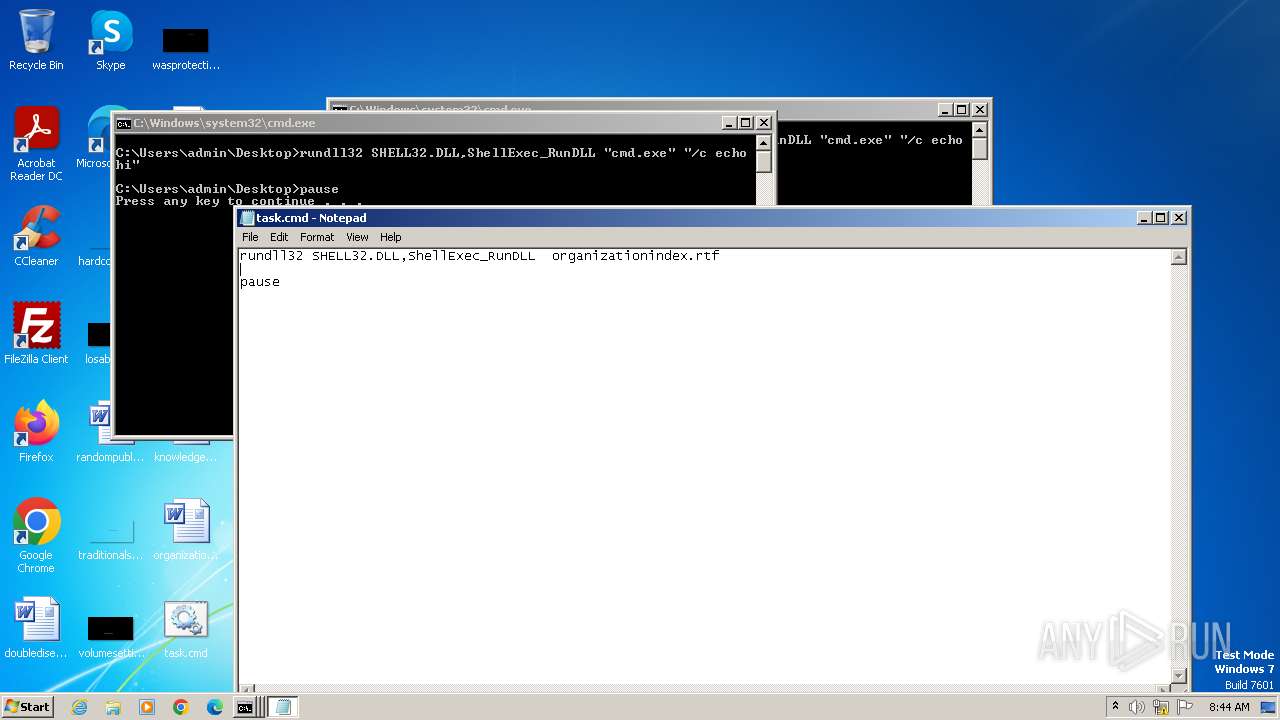
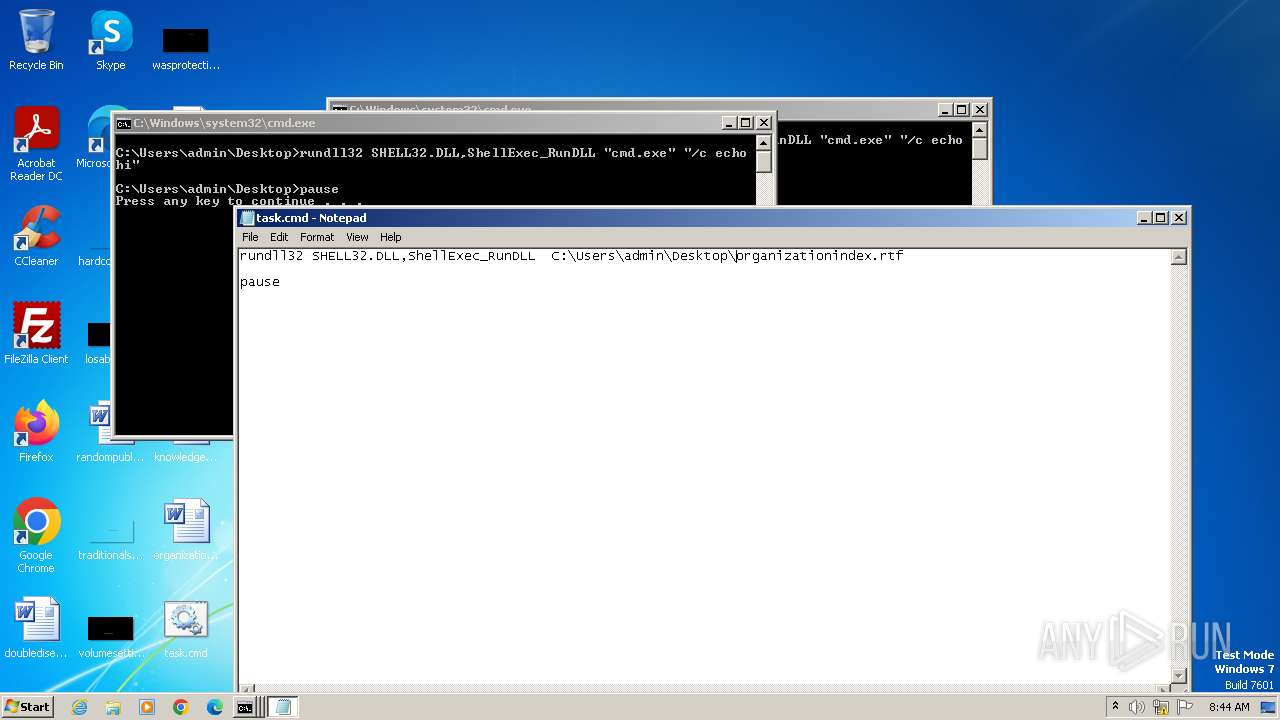
| 2520 | notepad.exe | C:\Users\admin\Desktop\task.cmd | text | |
MD5:97BE0816CC30E376B75BCA50E2A582E9 | SHA256:EA8223FFD06E7138C6B01EF19355FB9BB58BEEACC61A38A8FDC2500A5D0F66C0 | |||
| 3340 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\organizationindex.rtf.LNK | binary | |
MD5:9BB14E718549615D1BB84FCFBD68914C | SHA256:0DF6CB400446D741DE5FFEBD4FB727D4B0156F40507C1F9CBF477EAC3CFC0A96 | |||
| 3340 | WINWORD.EXE | C:\Users\admin\Desktop\~$ganizationindex.rtf | binary | |
MD5:0DDED6187D50D33DCFD5EE8414CD1F07 | SHA256:D640E93CAF447EDB5174FBC7A28031624F938DF515E649A4A0A7E85EBB282B53 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
868 | svchost.exe | 23.35.228.137:80 | — | AKAMAI-AS | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
868 | svchost.exe | 88.221.124.138:80 | armmf.adobe.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
armmf.adobe.com |
| whitelisted |