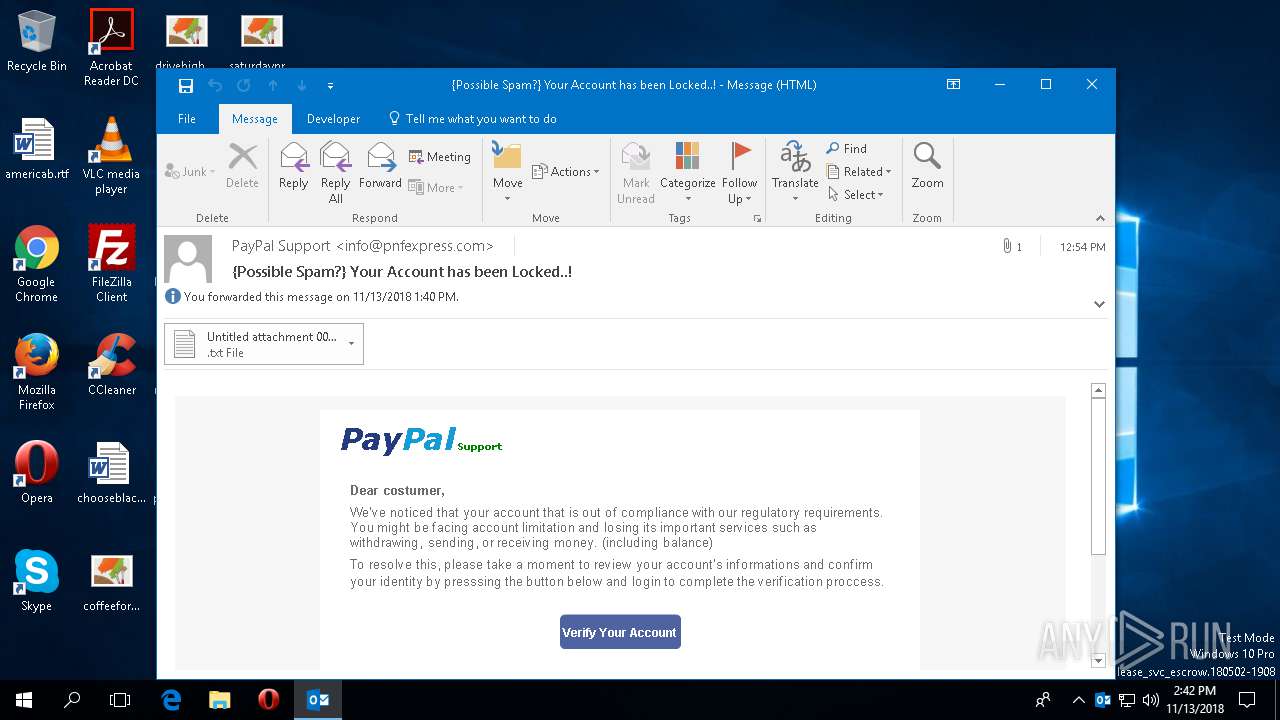
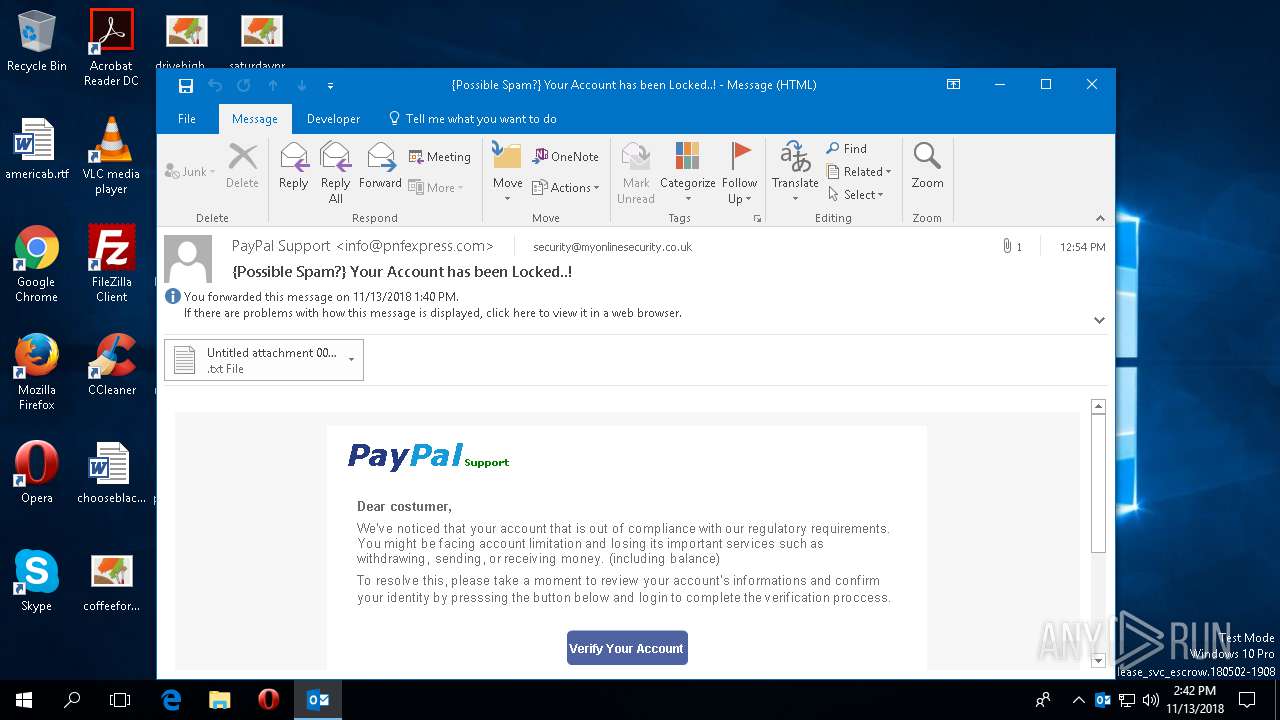
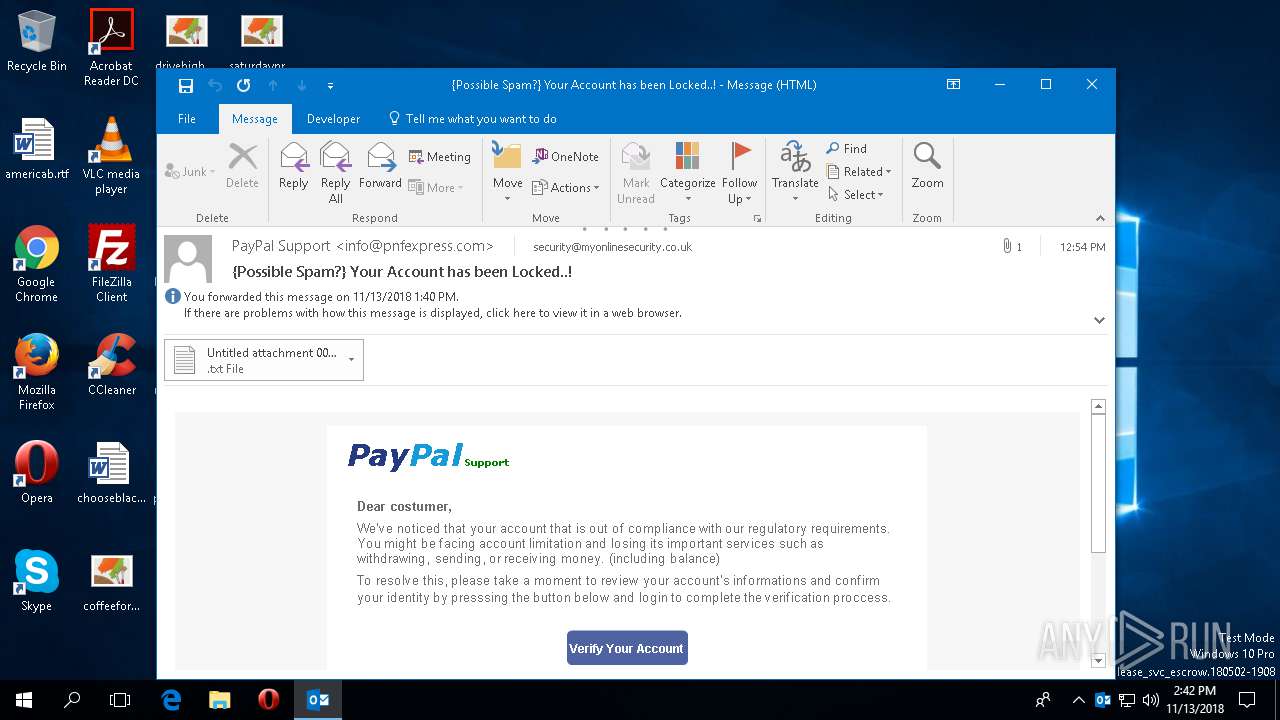
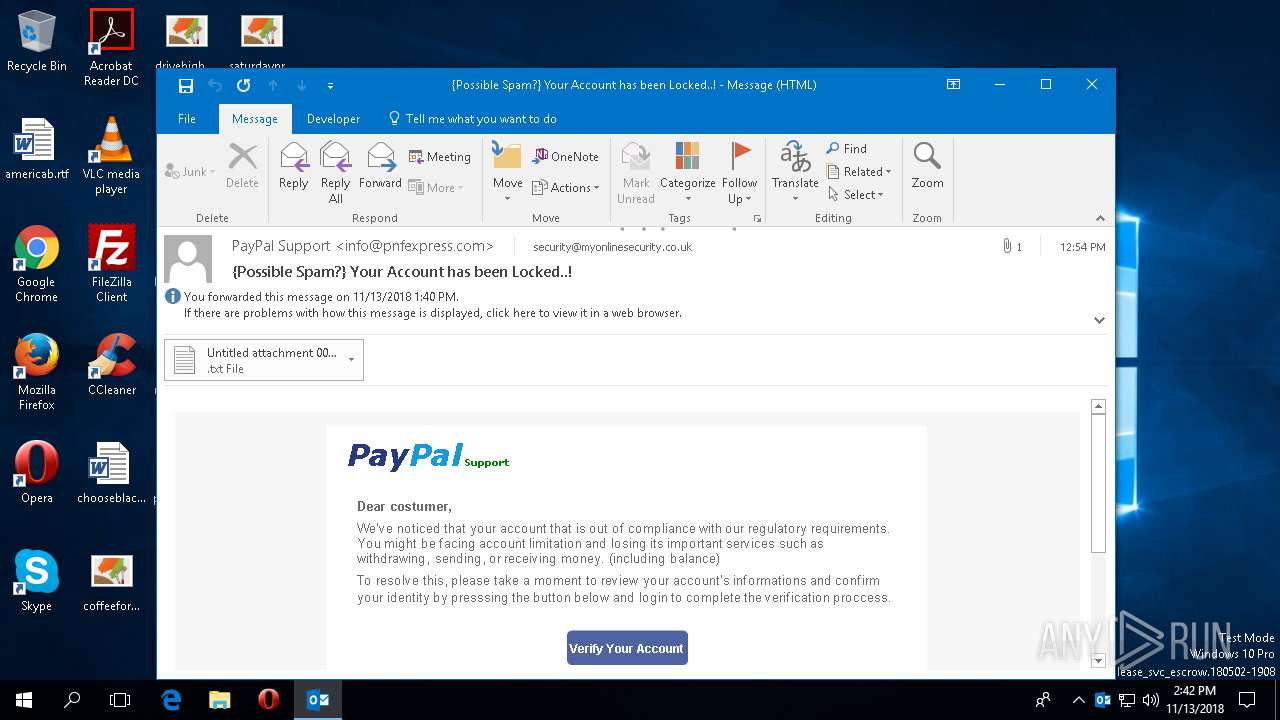
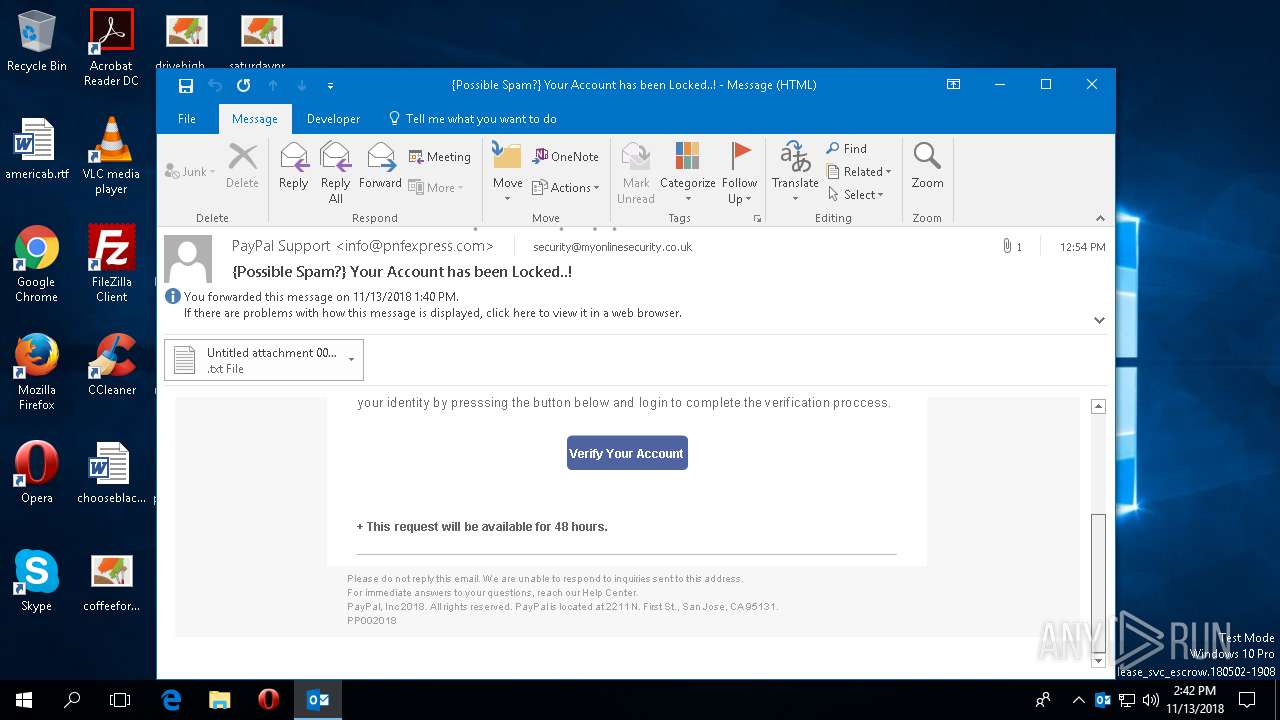
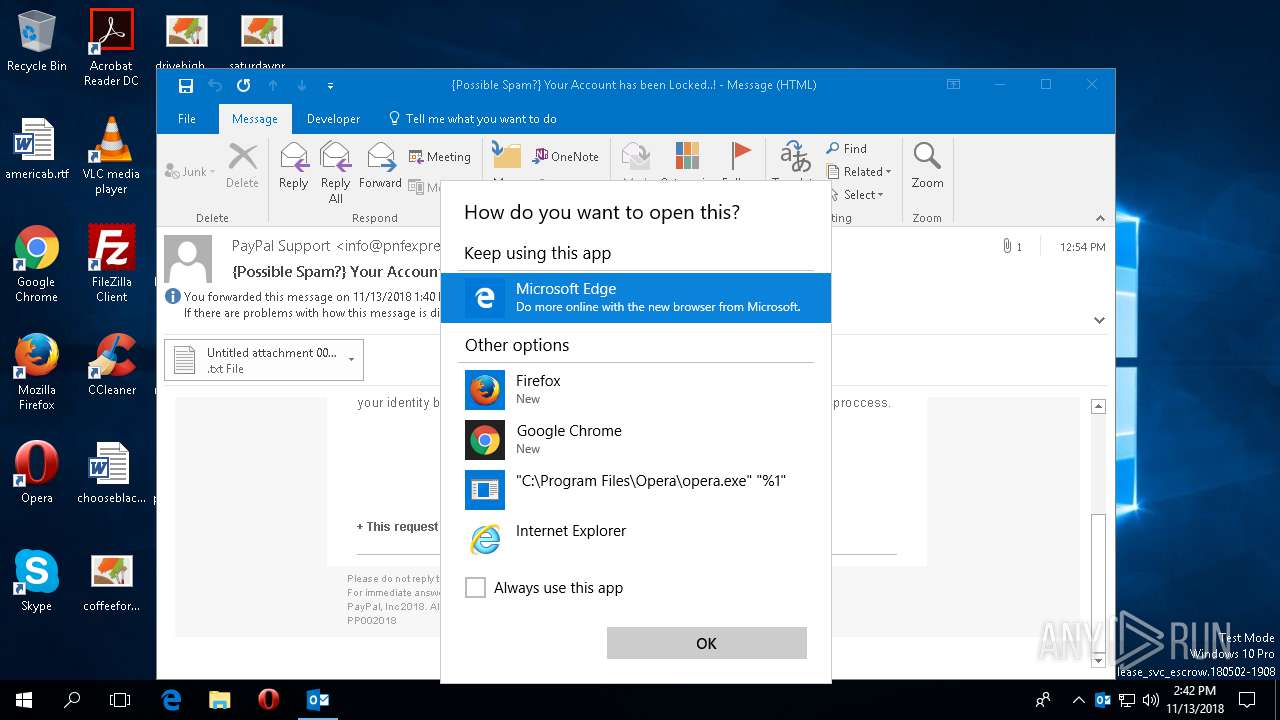
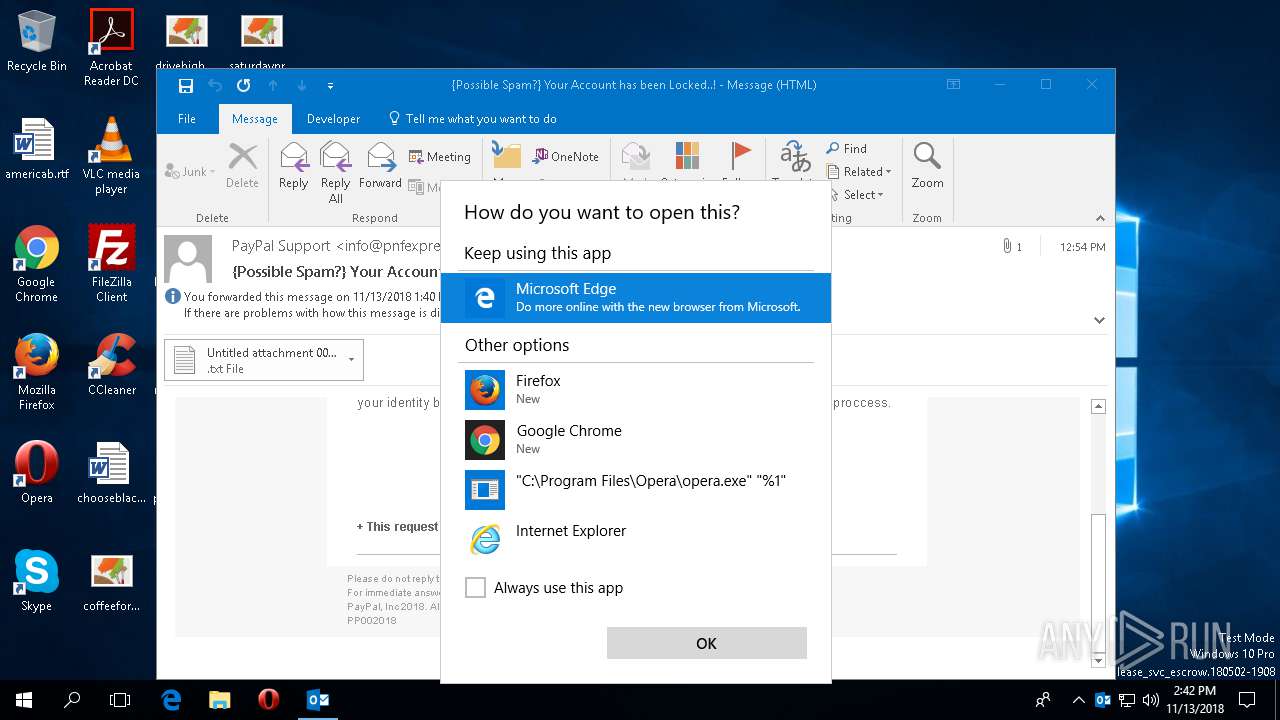
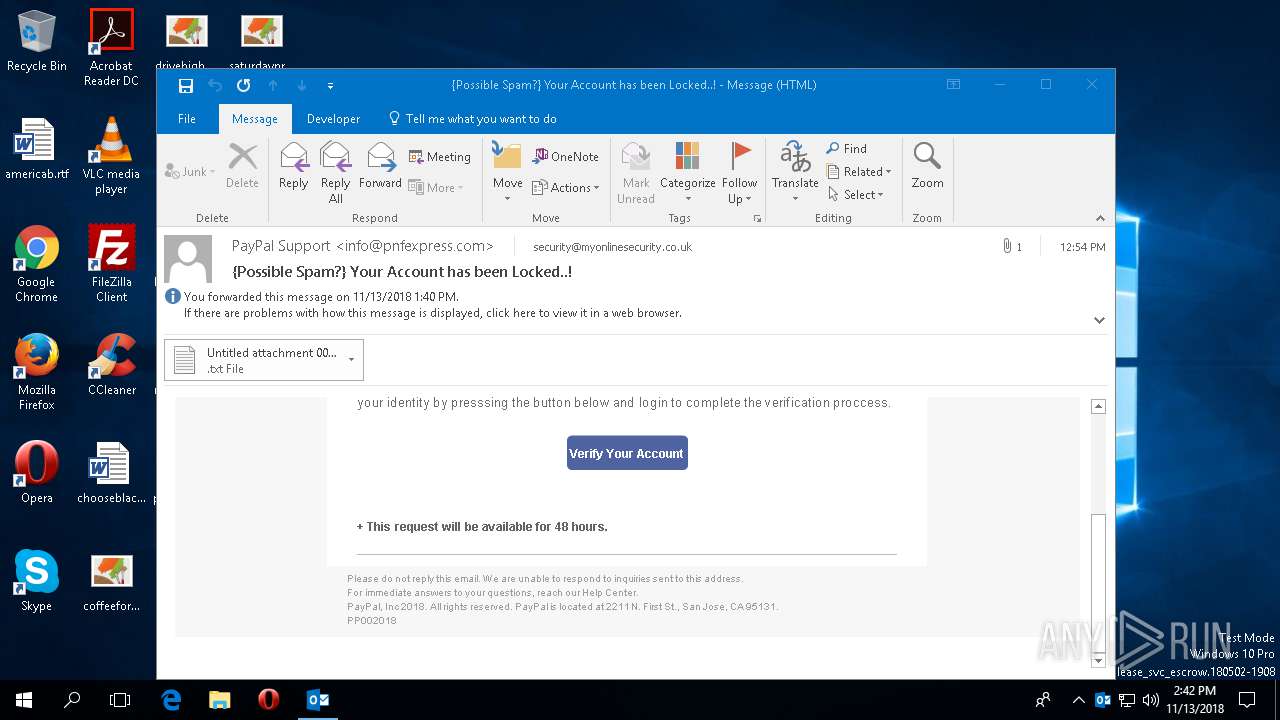
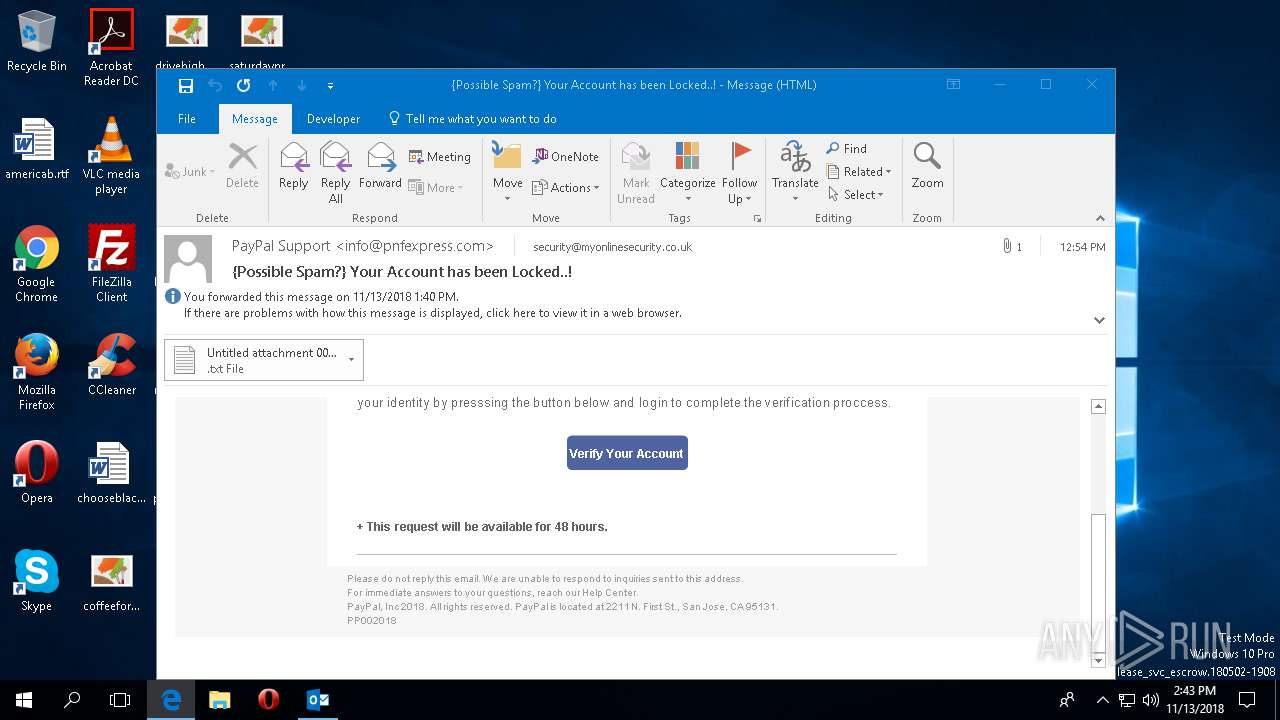
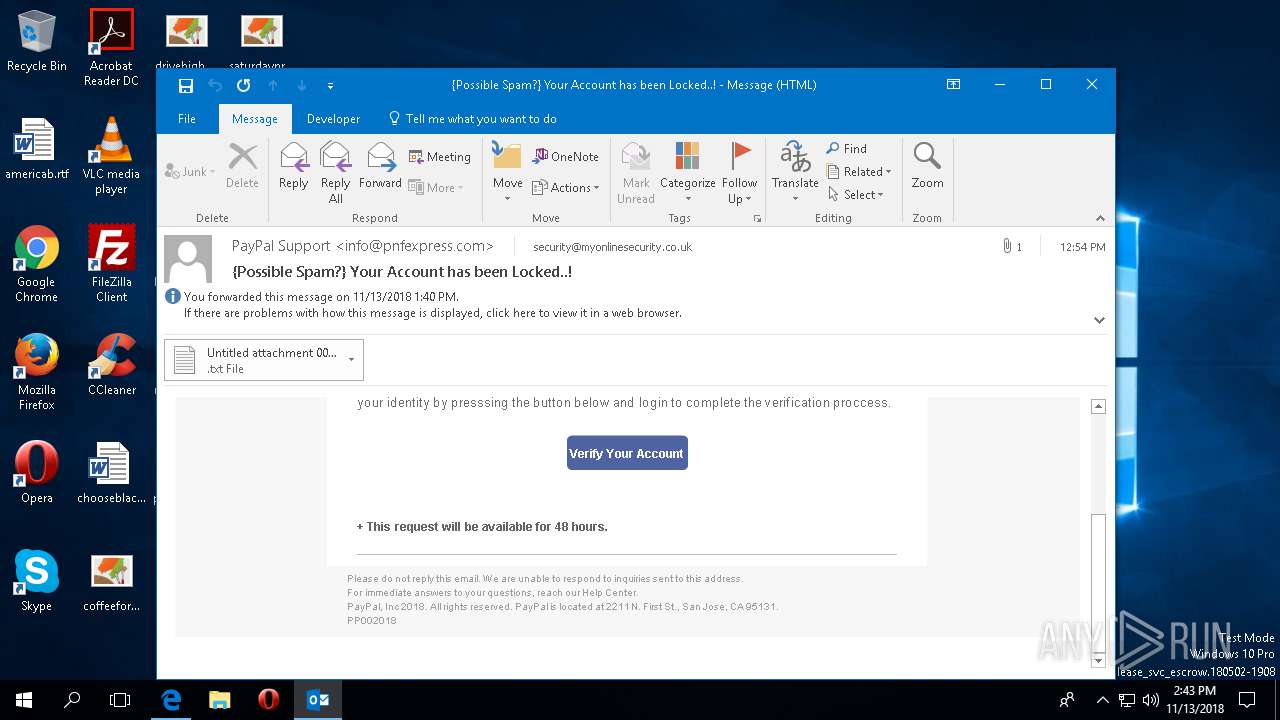
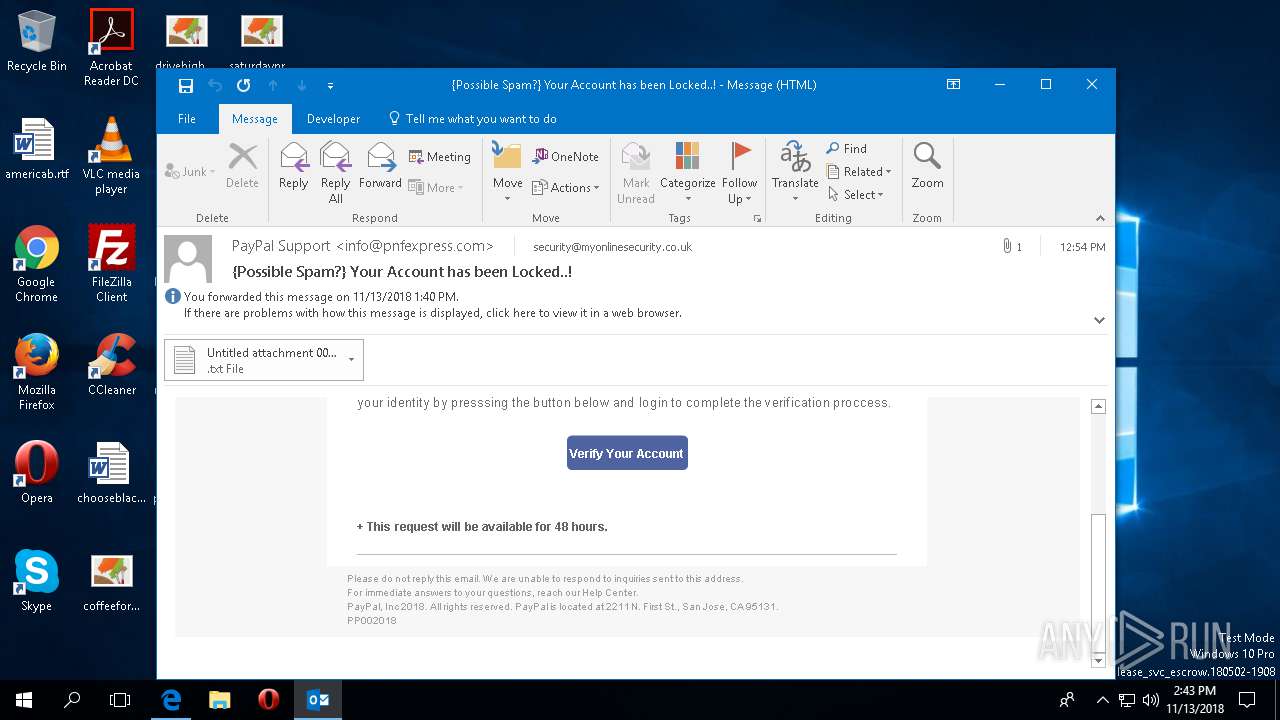
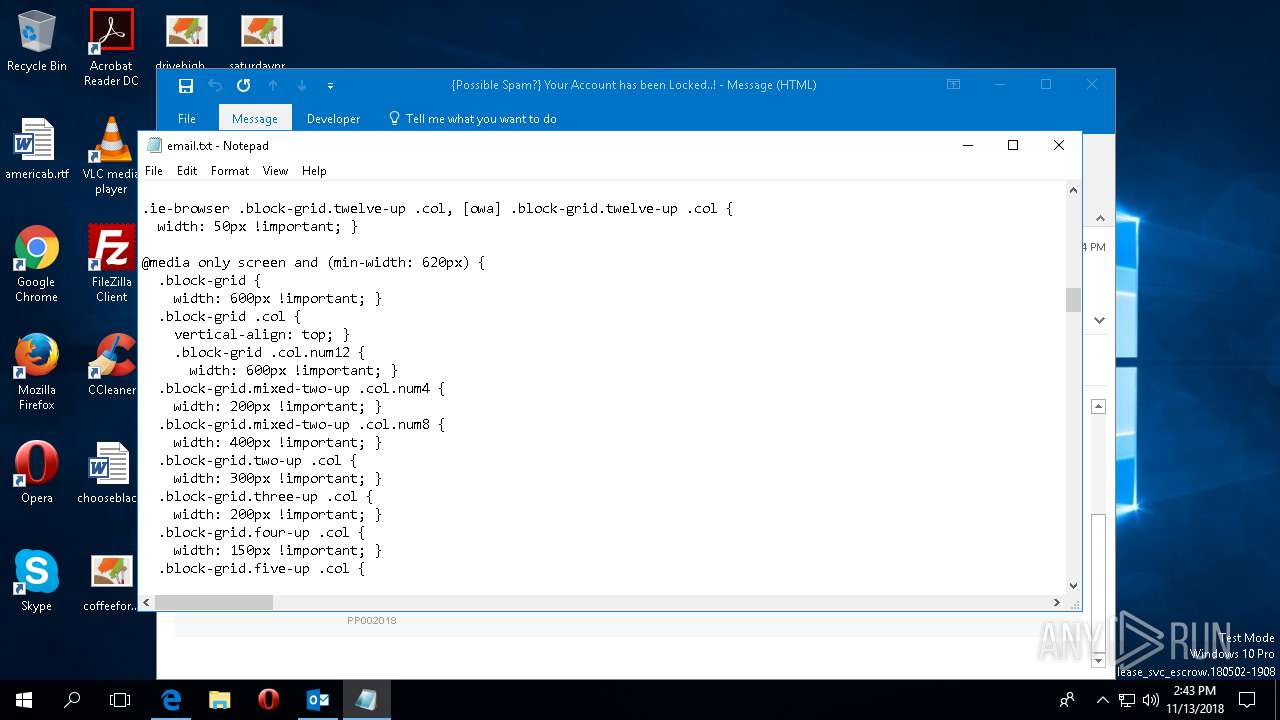
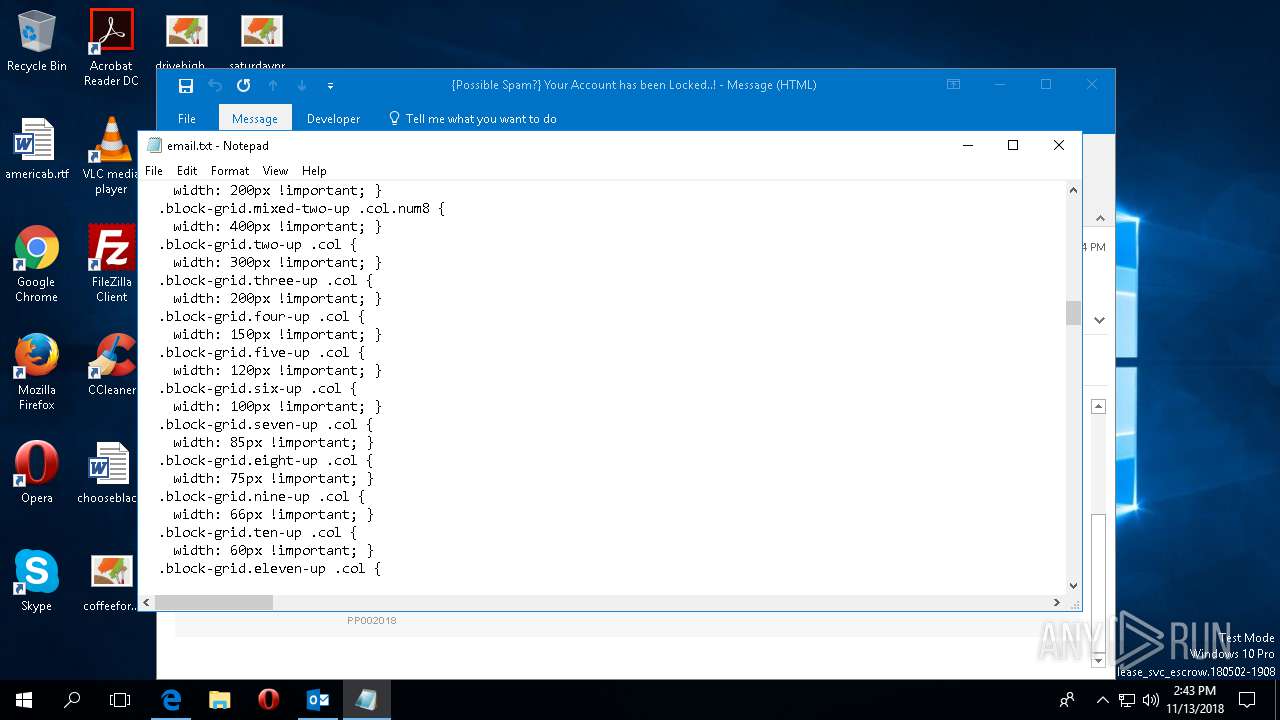
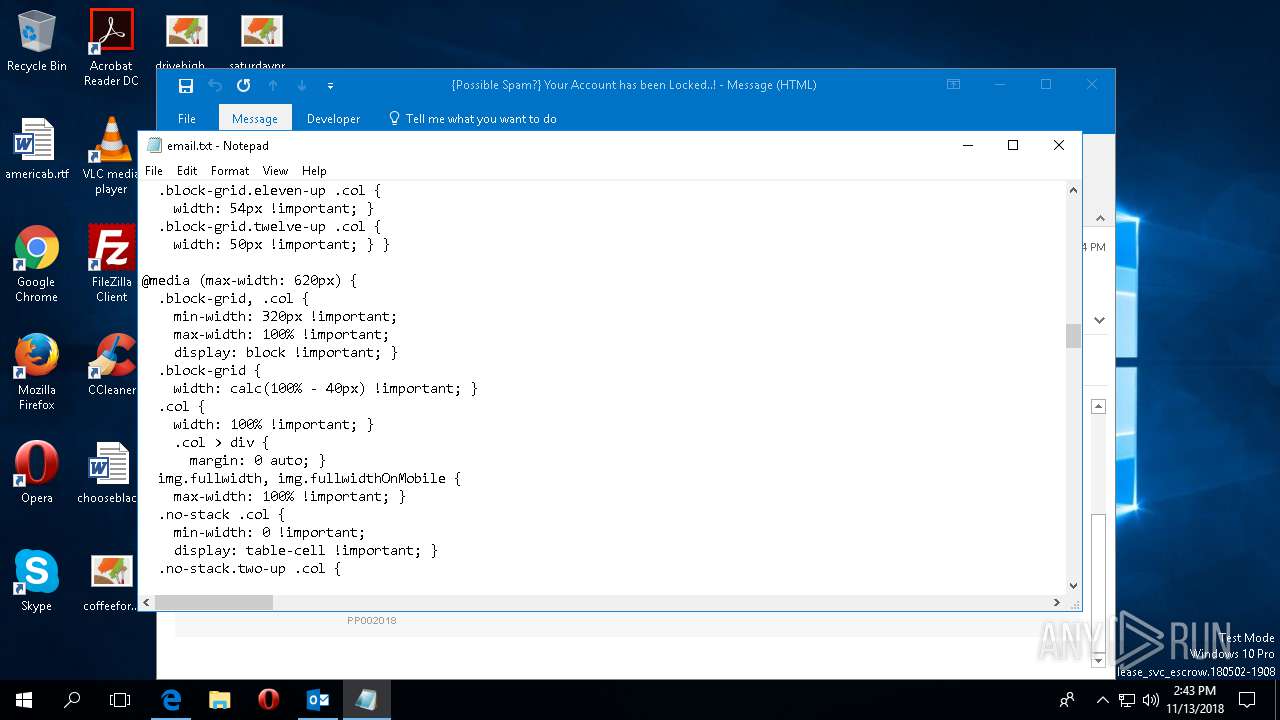
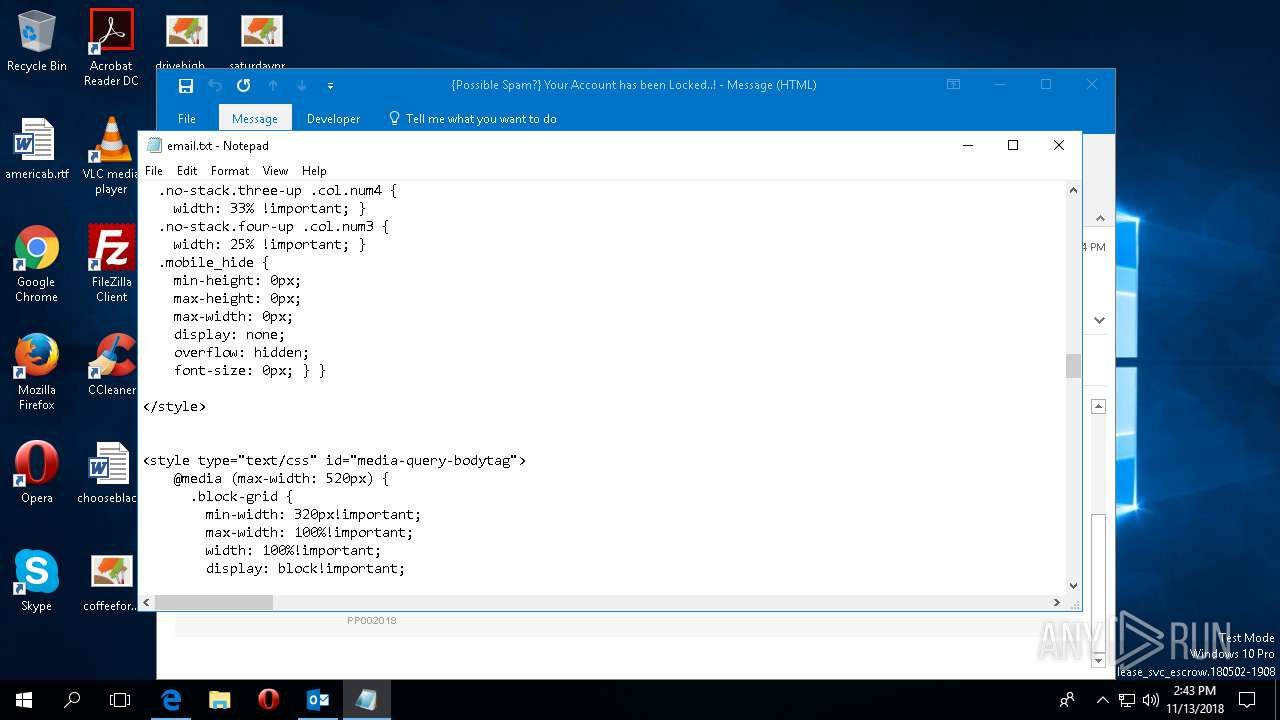
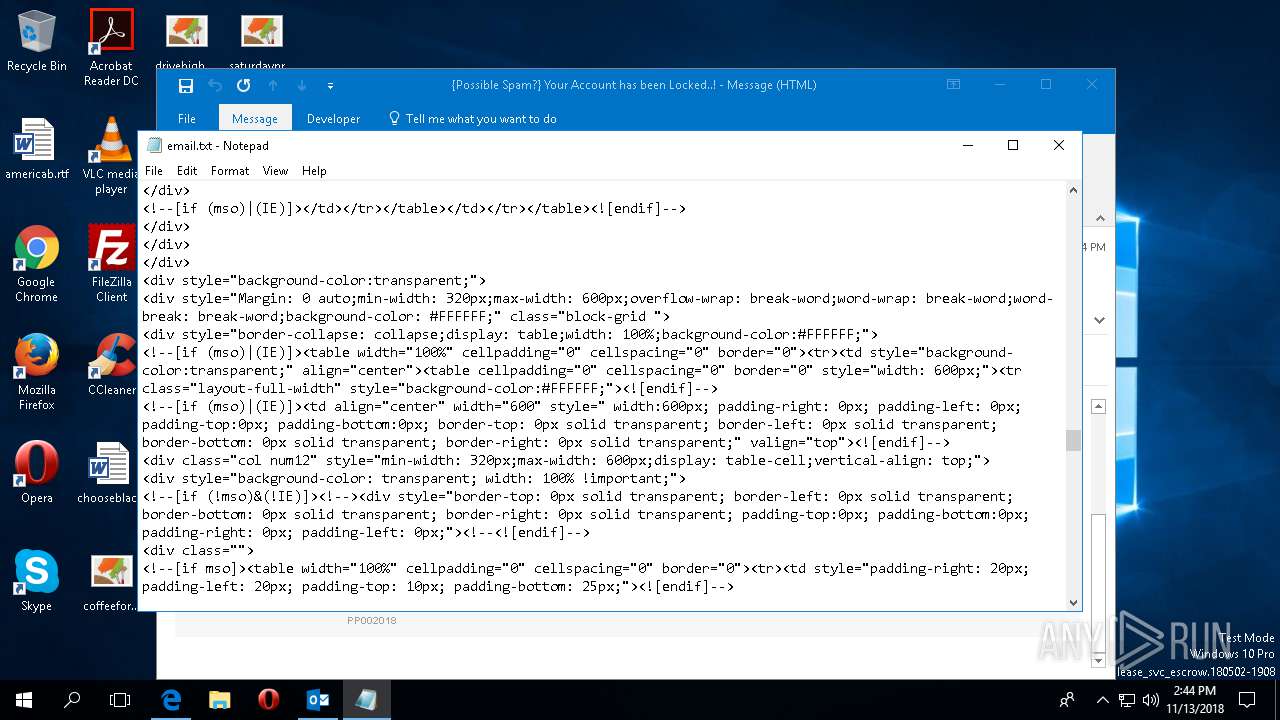
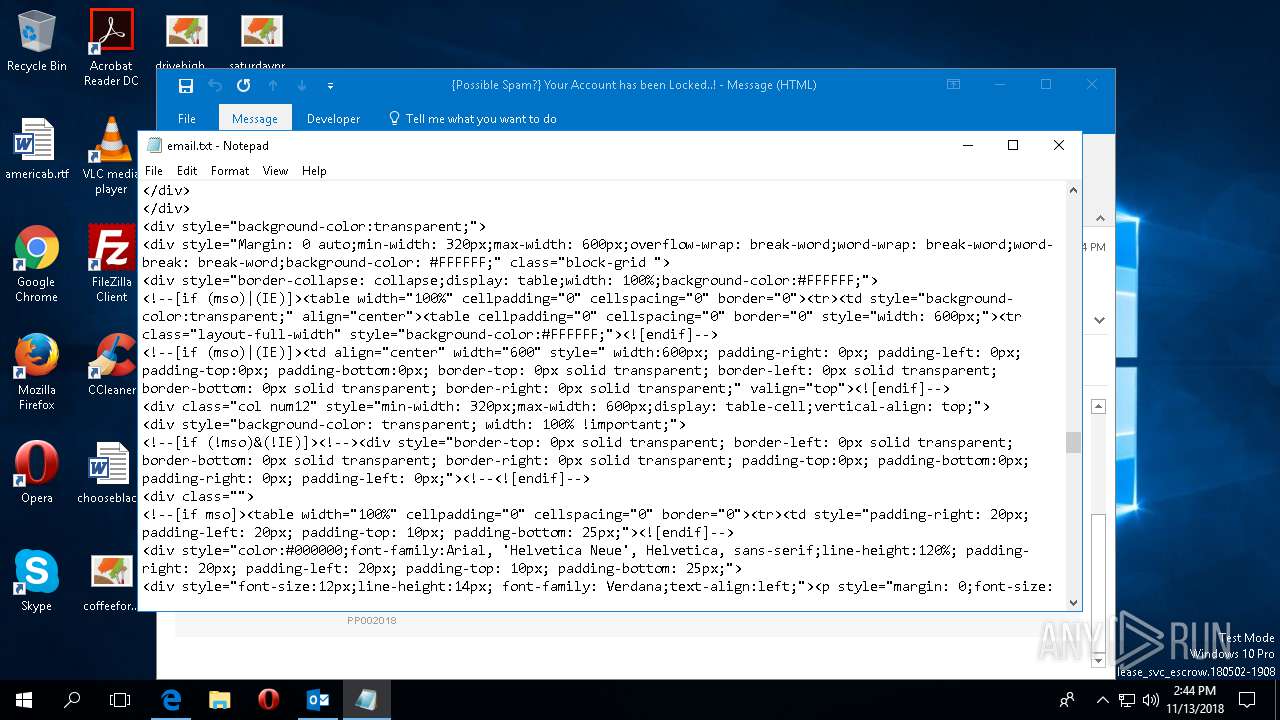
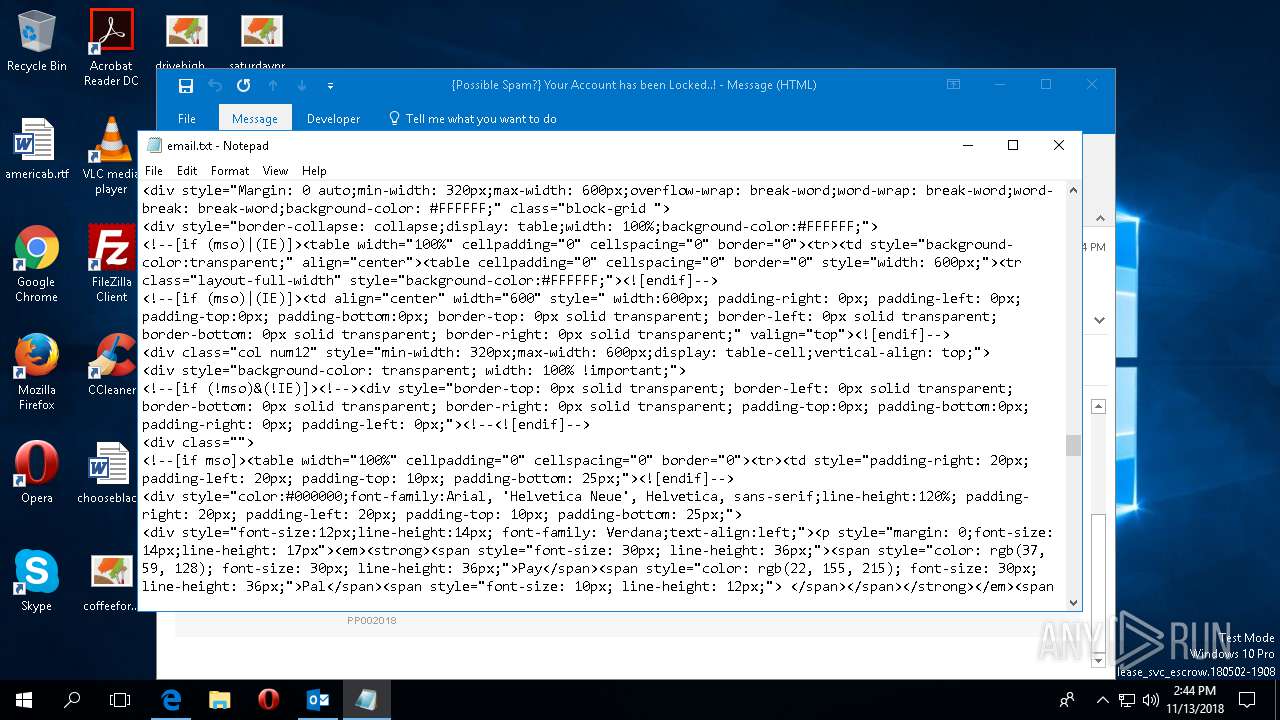
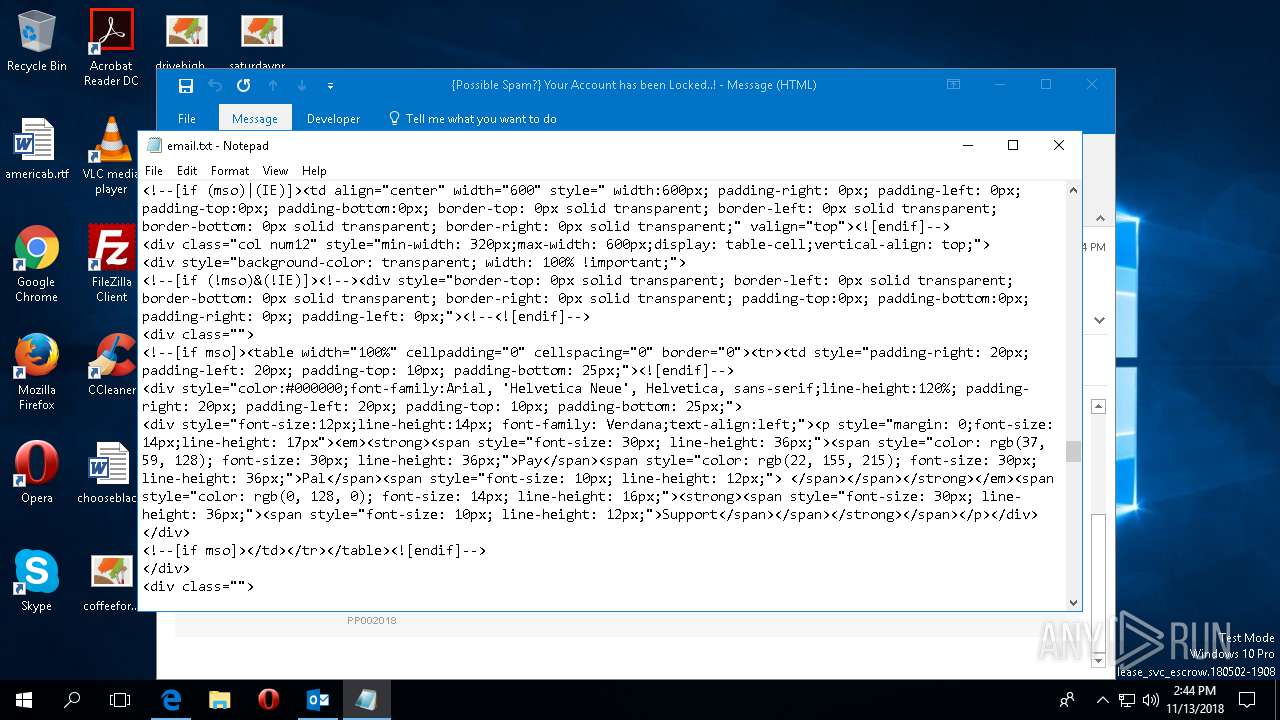
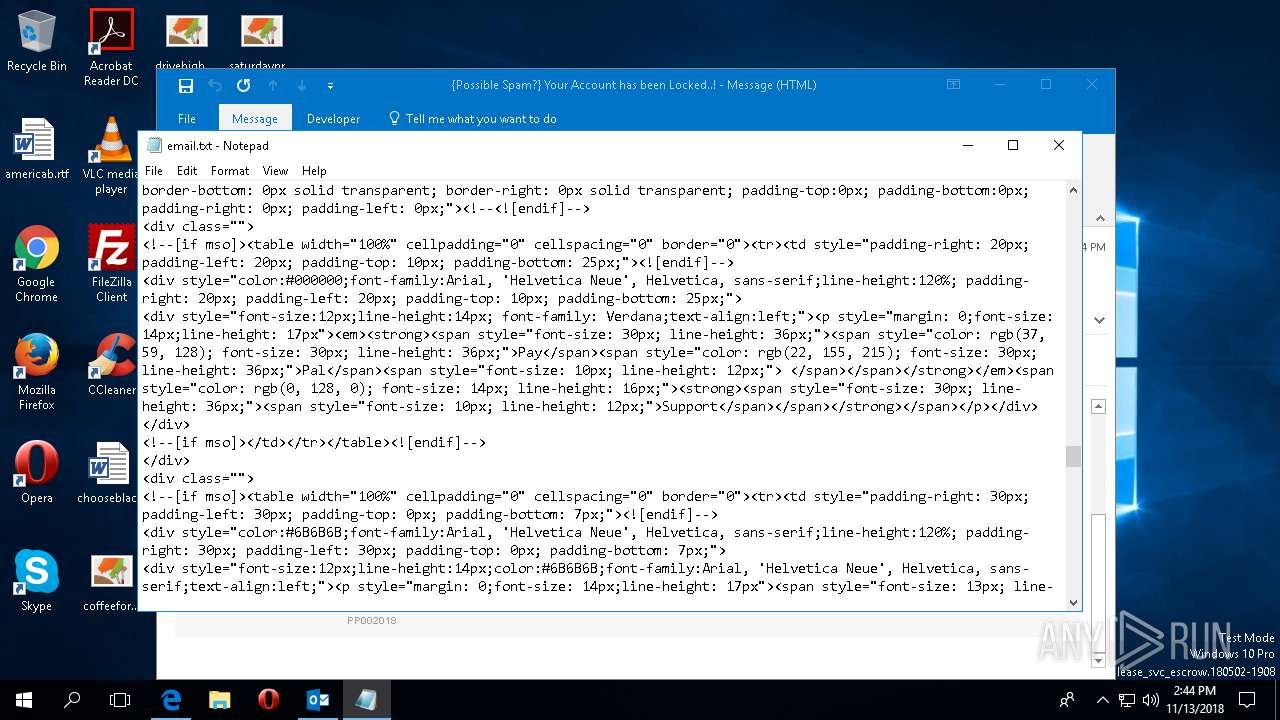
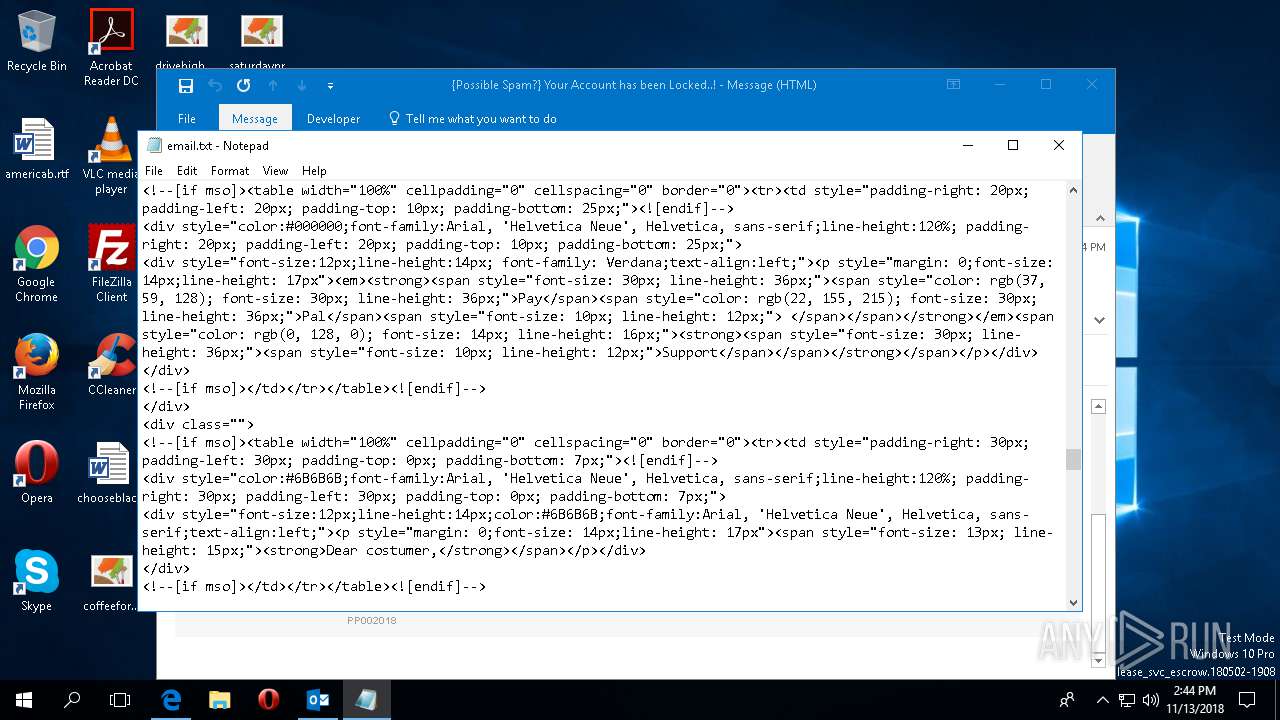
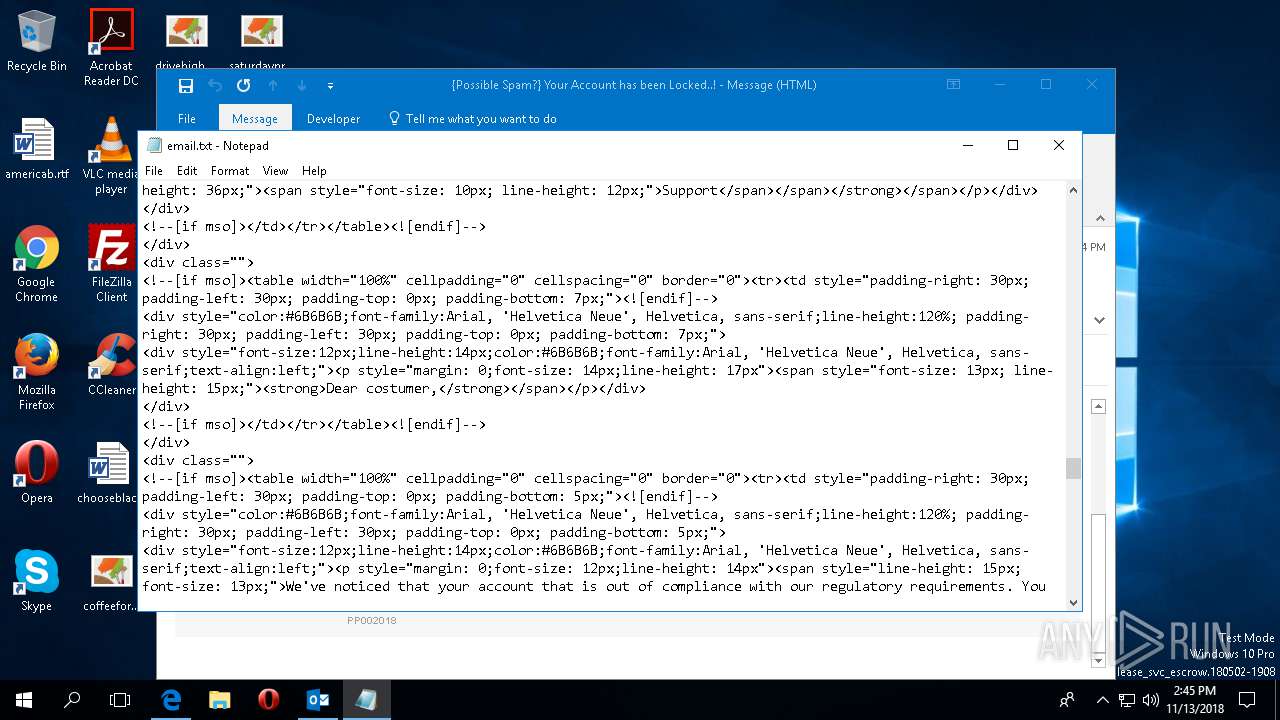
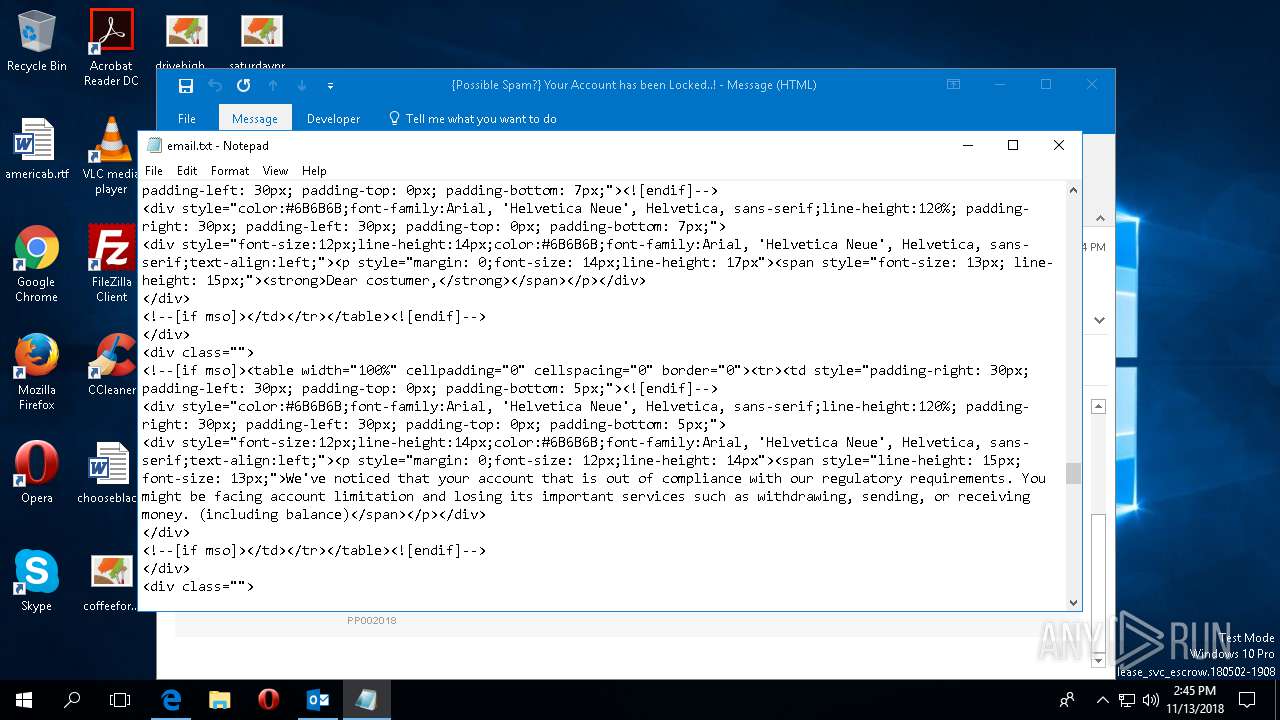
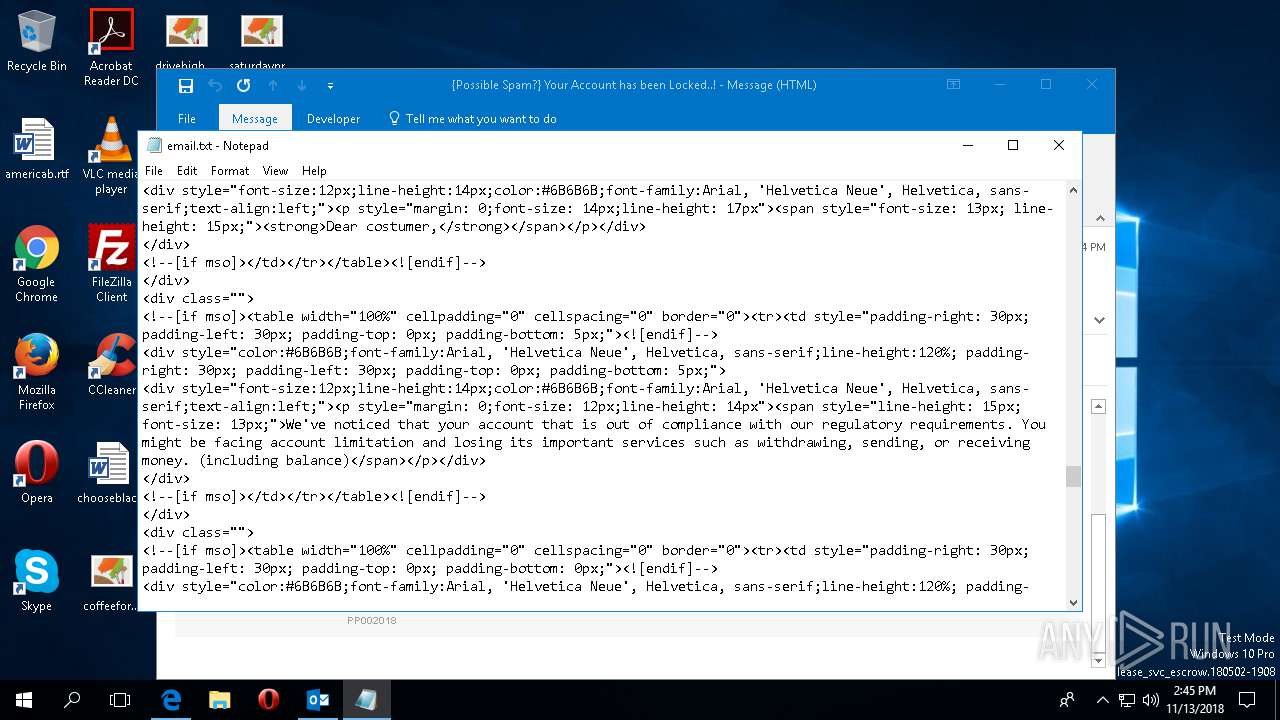
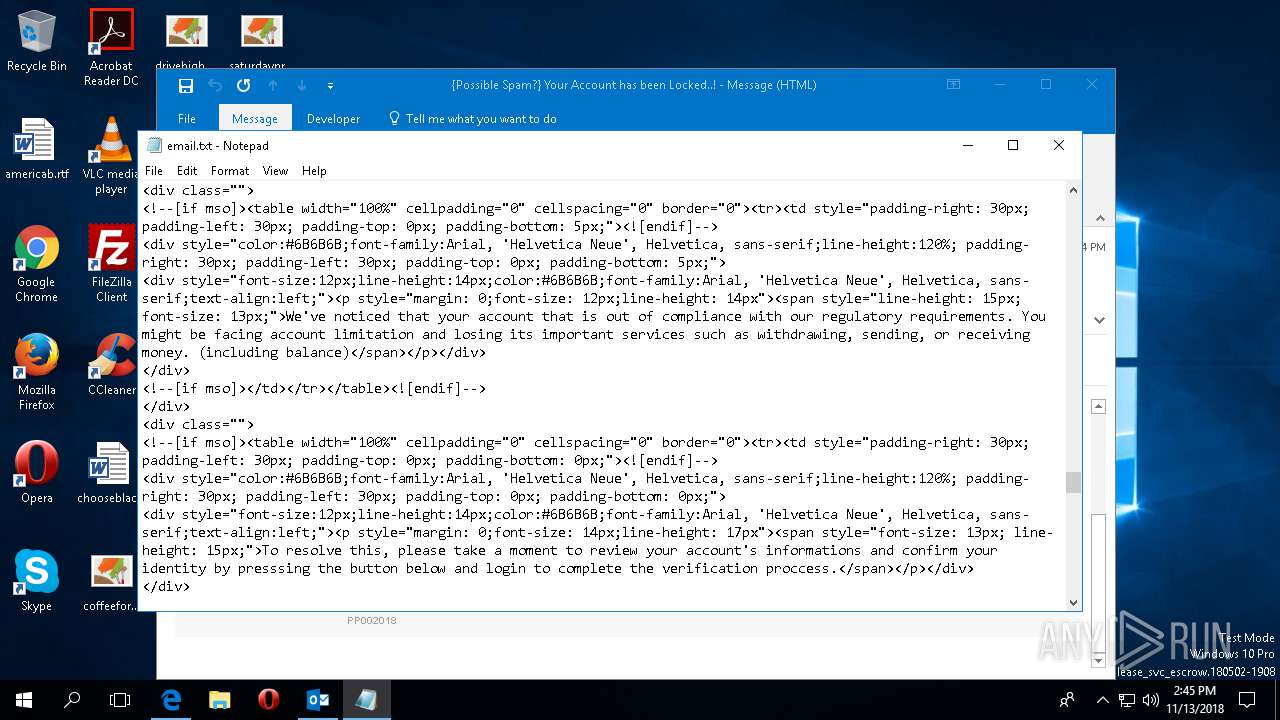
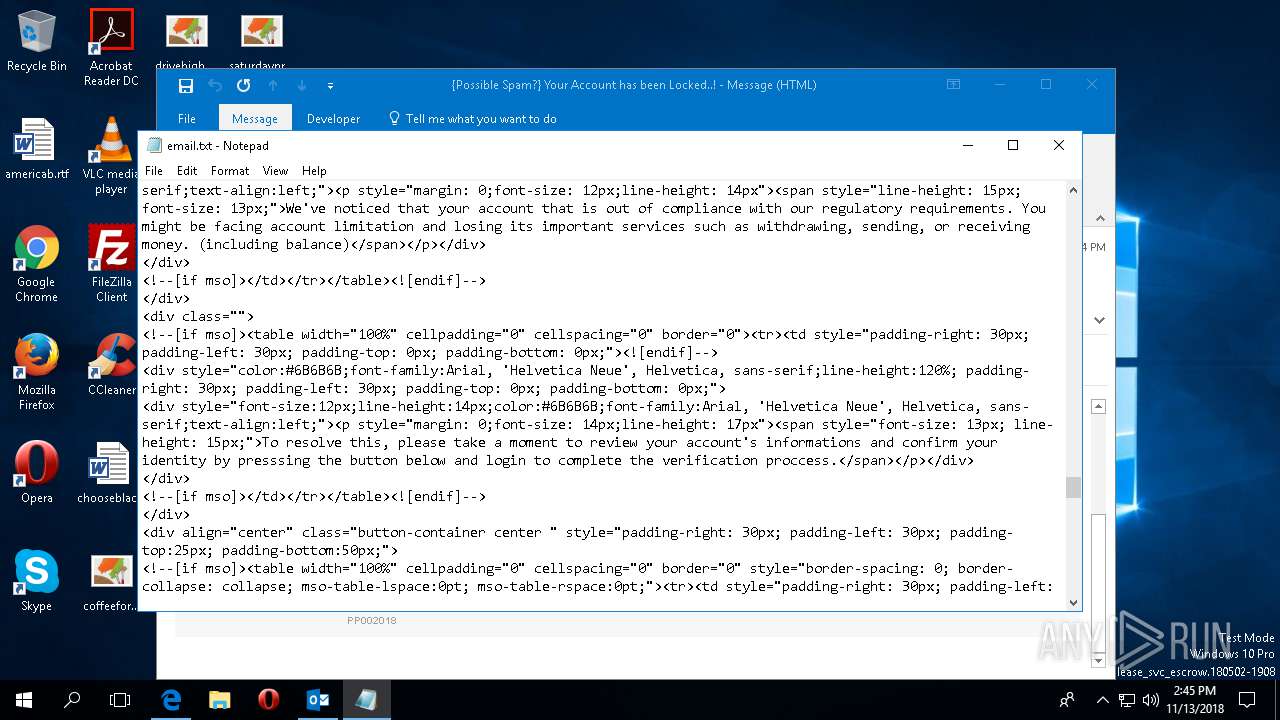
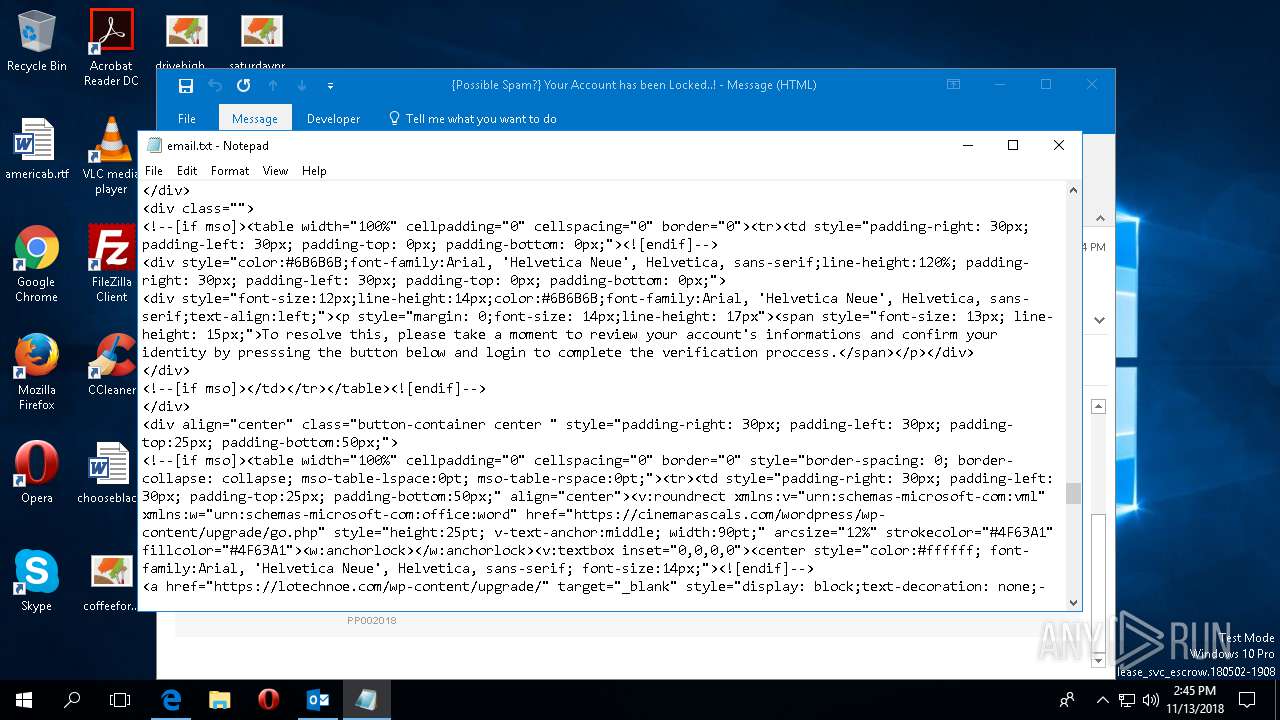
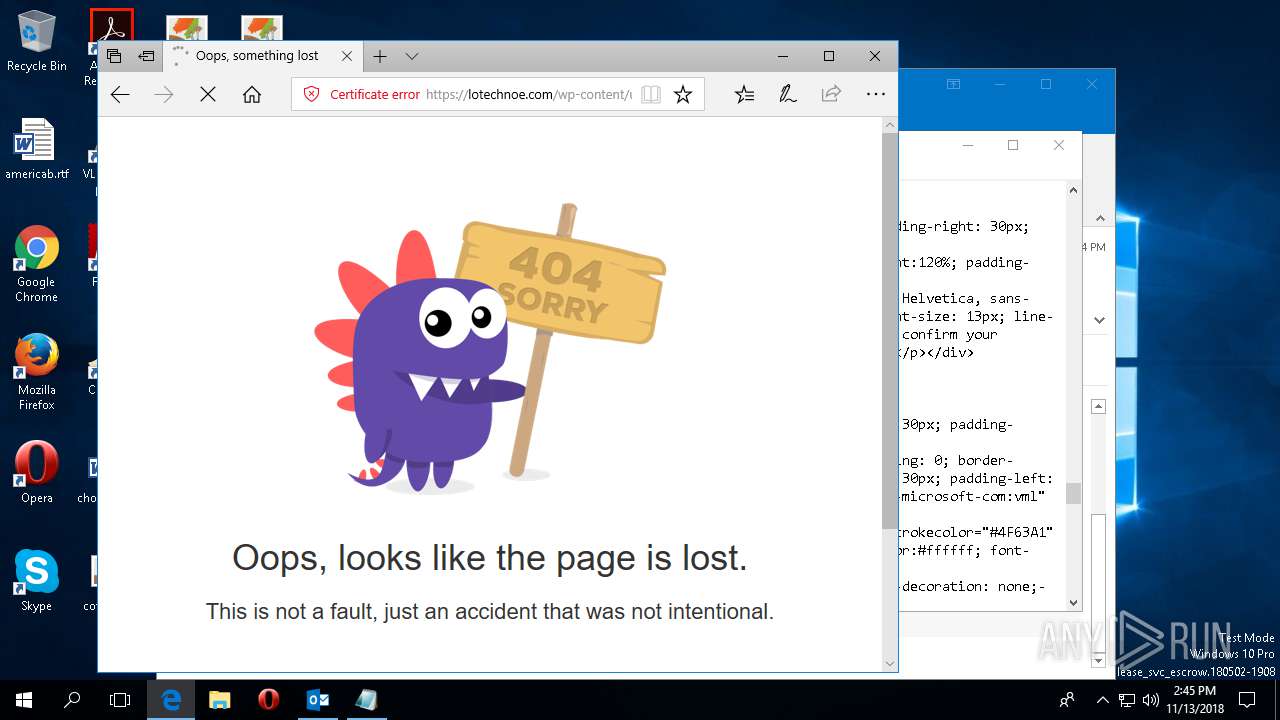
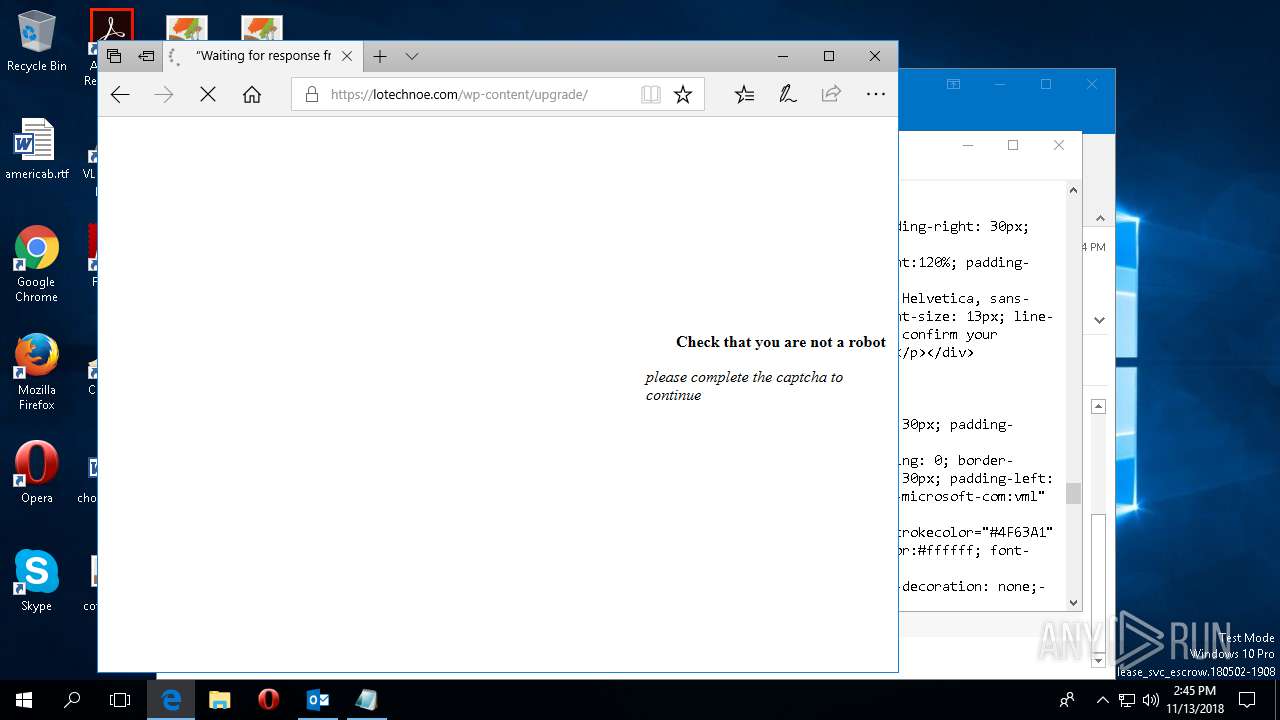
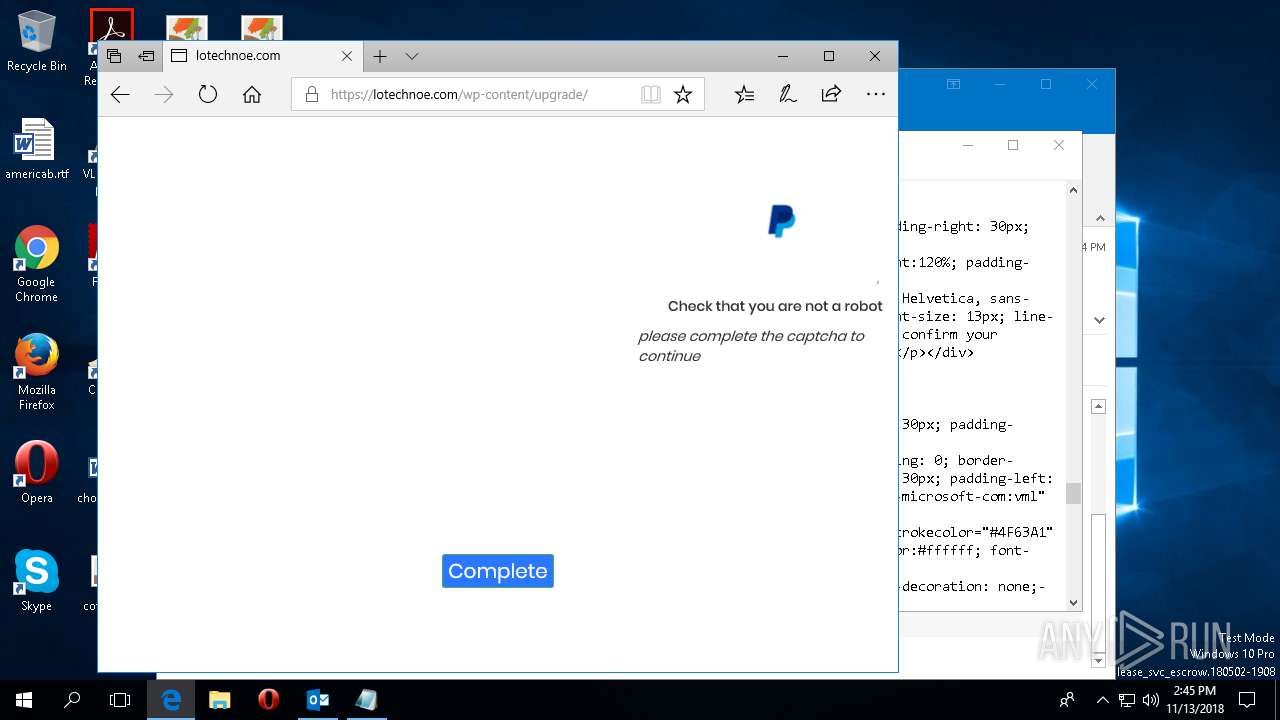
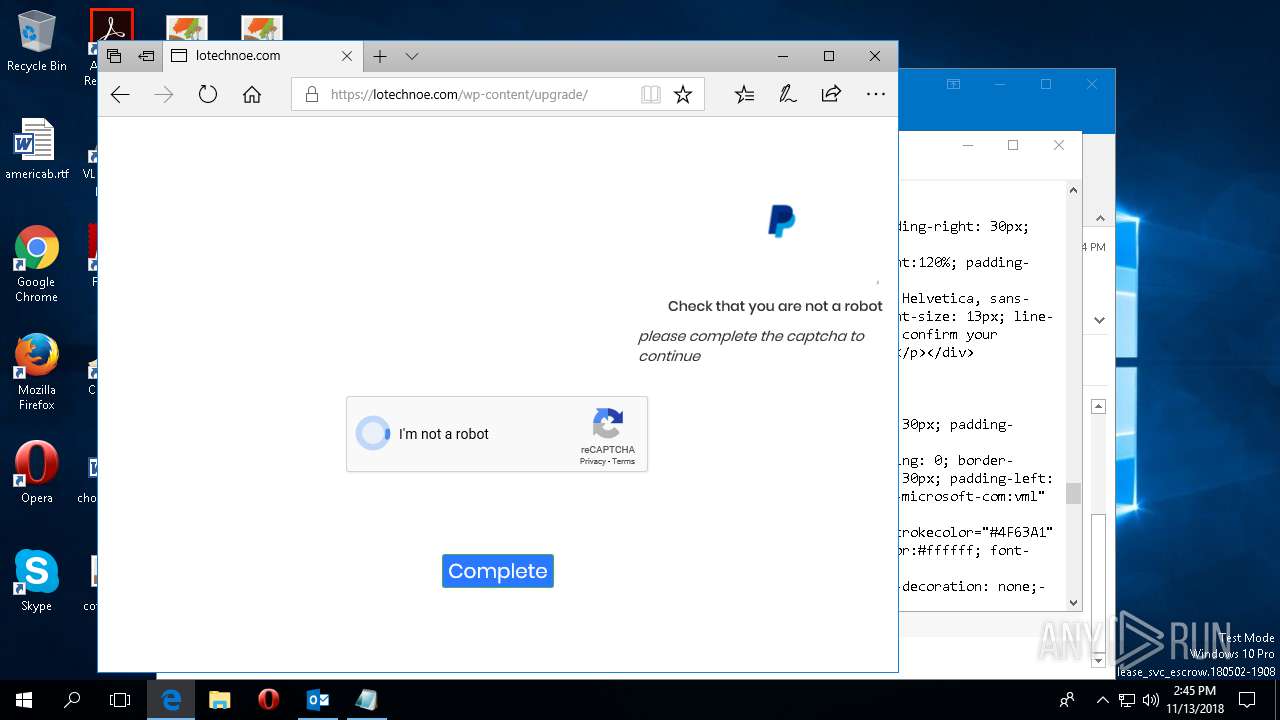
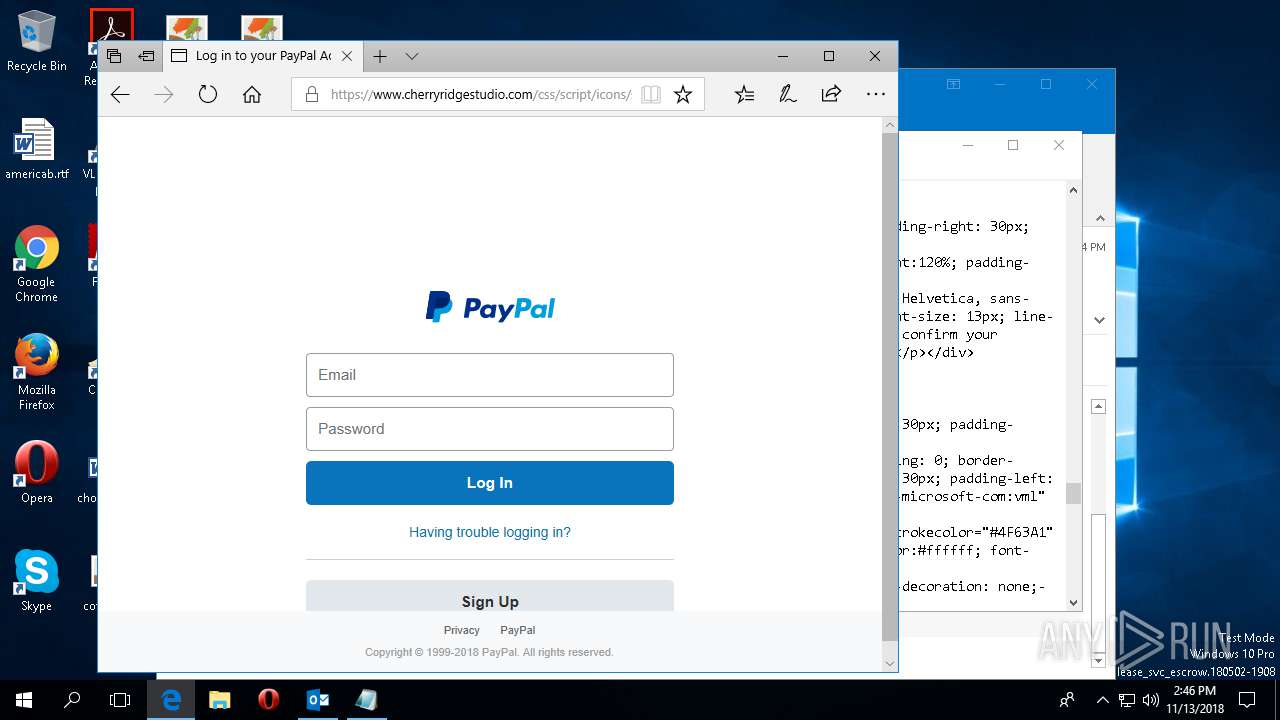
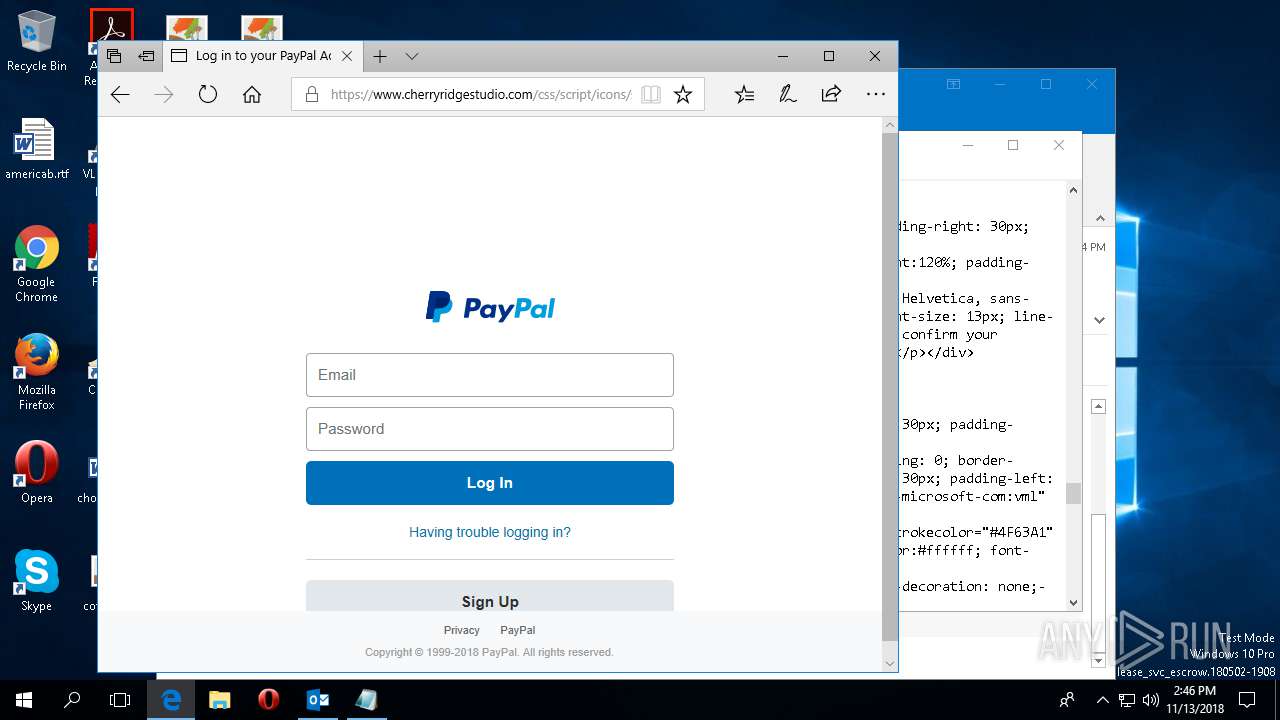
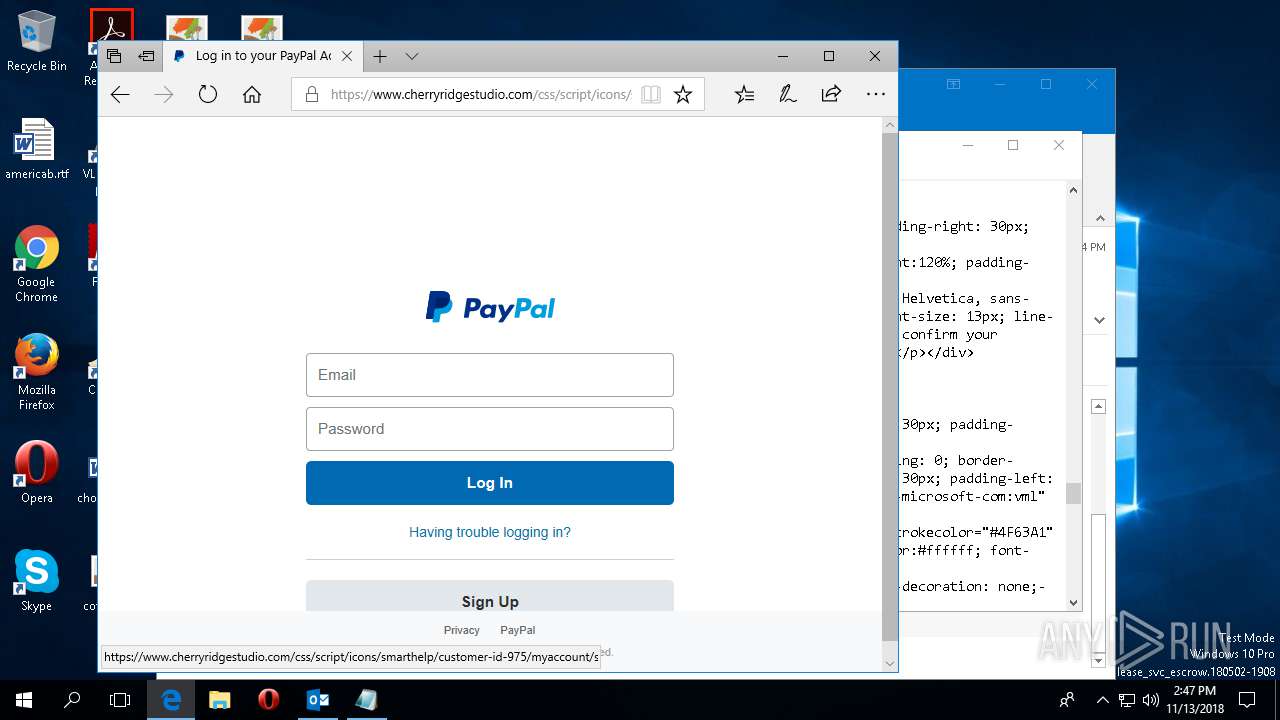
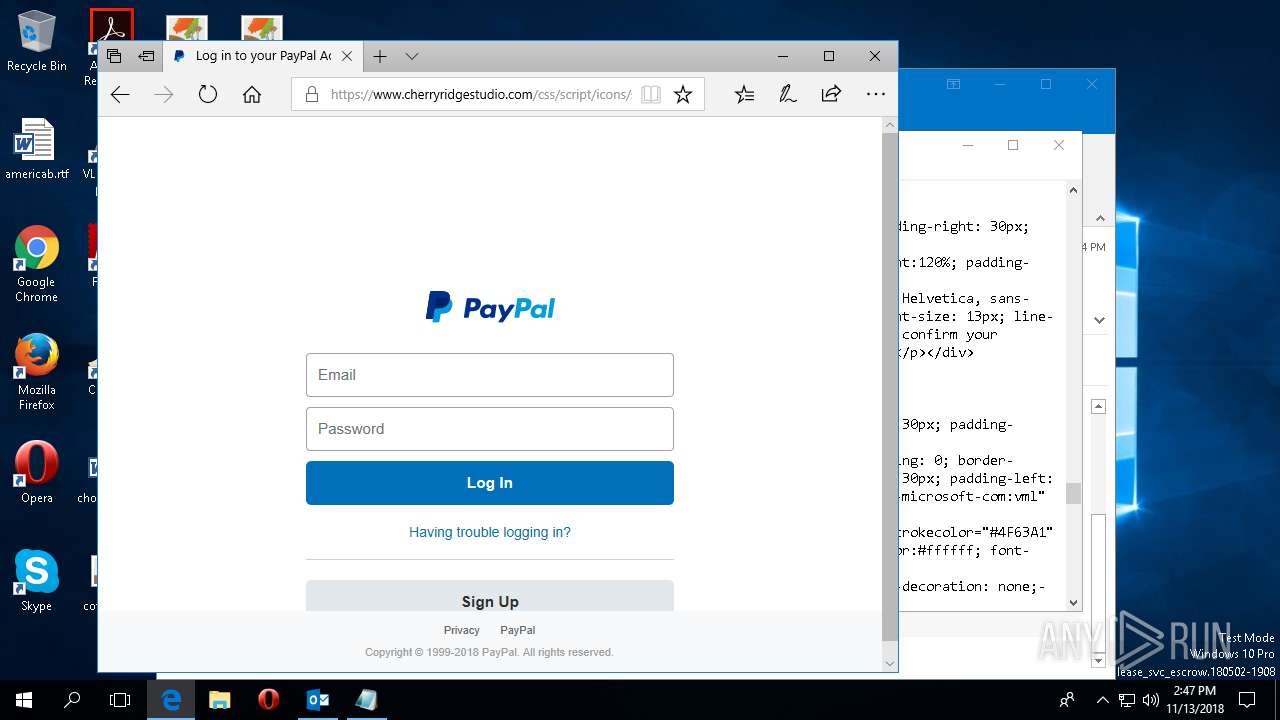
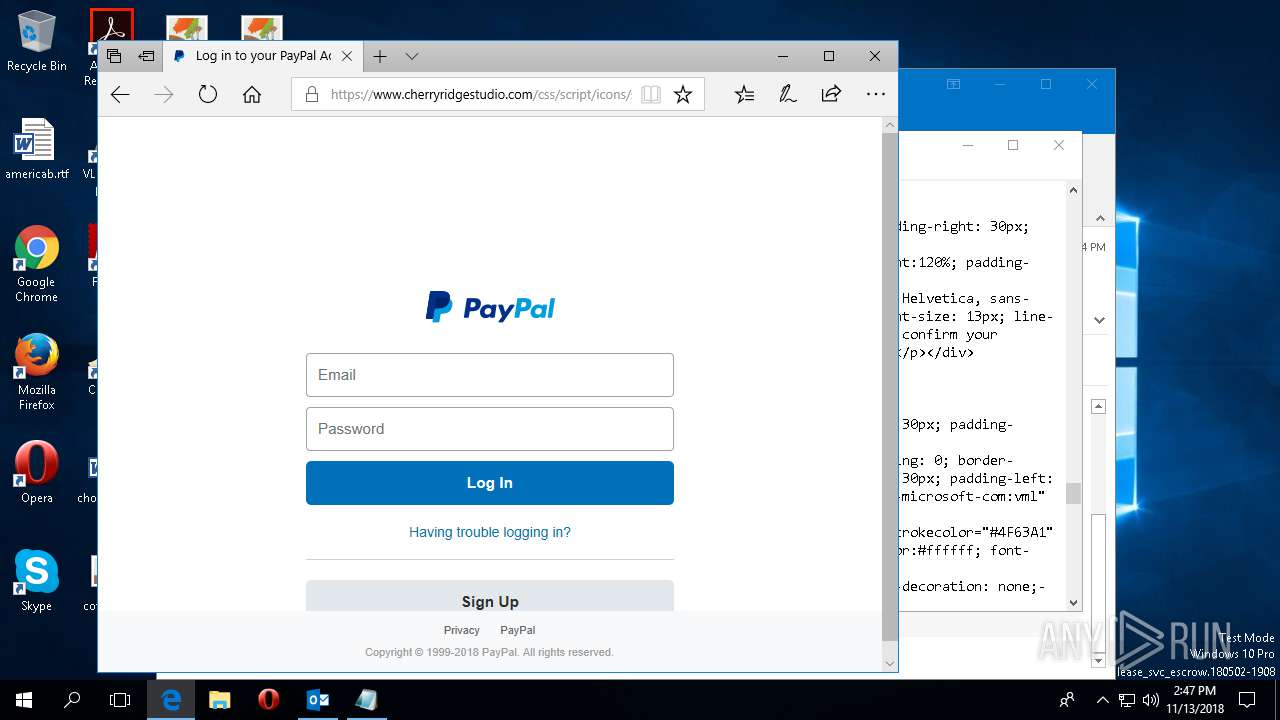
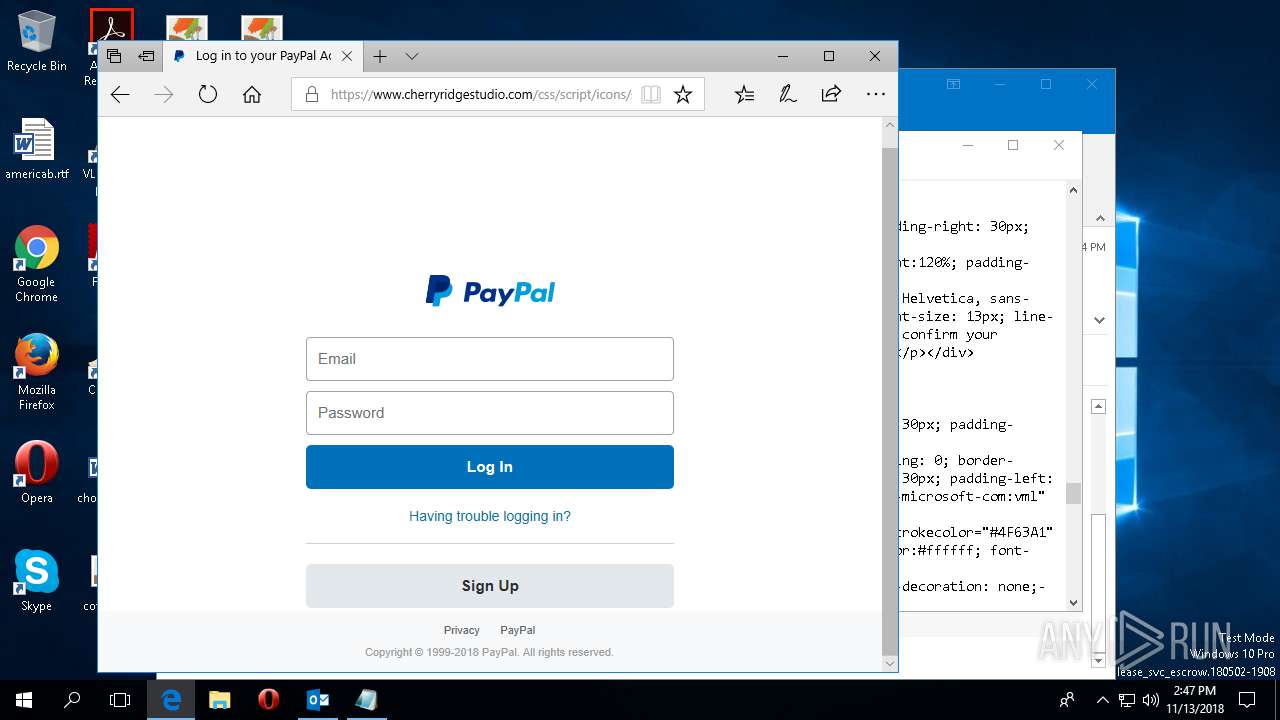
| File name: | {Possible Spam } Your Account has been Locked !.msg |
| Full analysis: | https://app.any.run/tasks/0df078ff-9d3b-47c6-a400-204bcc03ce75 |
| Verdict: | Malicious activity |
| Analysis date: | November 13, 2018, 14:41:32 |
| OS: | Windows 10 Professional (build: 16299, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | 1CF4AE510E0DF211AF18098B26B3A6B8 |
| SHA1: | A901771E96AFF1C903BB33B1E93B3989EB18420C |
| SHA256: | A966F55A323A5B681A45CE2DB875F9B1491912C18F7EEFCCA24CAA3BDD0B3A0F |
| SSDEEP: | 192:KMsVXA2ugJBp9DGl2CMKF3apagM575iQMAFmdC53llU9AAgnPc6BaJzbuAiW:uXAPgJFKRrNgG+cmw53llB0saJzCAi |
MALICIOUS
Scans artifacts that could help determine the target
- OUTLOOK.EXE (PID: 5660)
SUSPICIOUS
Reads the machine GUID from the registry
- OUTLOOK.EXE (PID: 5660)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 5660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
89
Monitored processes
1
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5660 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /f "C:\Users\admin\Desktop\{Possible Spam } Your Account has been Locked !.msg" | C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.6741.2048 Modules
| |||||||||||||||
Total events
1 303
Read events
1 179
Write events
101
Delete events
23
Modification events
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | >x; |
Value: 3E783B001C16000001000000000000006E92DD0A5F7BD40100000000 | |||
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | nx; |
Value: 6E783B001C16000000000440010000008EF3DF0A5F7BD4013A000000E837EE351C5D4442ACD9C235A90305A88EF3DF0A5F7BD40100000000000010000008551A00000000030000000000000002000000000000000000 | |||
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | nx; |
Value: 6E783B001C16000000000440010000008EF3DF0A5F7BD4013C000000E837EE351C5D4442ACD9C235A90305A88EF3DF0A5F7BD40100000000000010000008551A000000000300000007000000040000000000000000000000 | |||
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{02CAC15F-D4BE-400E-9127-D54982AA4AE9} |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{02FD33DF-F746-4A10-93A0-2BC6273BC8E4} |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{11ADBD74-7DF2-4E8E-802B-B3BCBFD04A78} |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{13967EE5-6B23-4BCD-A496-1D788449A8CF} |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (5660) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\outlook.exe\ETWMonitor\{287BF315-5A11-4B2F-B069-B761ADE25A49} |
| Operation: | delete key | Name: | |
Value: | |||
Executable files
0
Suspicious files
3
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5660 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\FORMS\FRMDATA64.DAT | binary | |
MD5:— | SHA256:— | |||
| 5660 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_88614FFAD35D353421B8A7E1FE18FCE4 | der | |
MD5:— | SHA256:— | |||
| 5660 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_88614FFAD35D353421B8A7E1FE18FCE4 | binary | |
MD5:— | SHA256:— | |||
| 5660 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\RoamCache\Stream_ContactPrefs_2_62B28CB4673EF440B91BC3A9A4483685.dat | xml | |
MD5:8BD87194AD4E92165AD51FEB25271160 | SHA256:6C1B1E6B7A1F5A9499A3F7C66939B933D89EFD7BFF818255F57CD182C7474650 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
45
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?6dba2e9b16f570c0 | US | — | — | whitelisted |
— | — | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?986b7c10856ac7b0 | US | — | — | whitelisted |
5660 | OUTLOOK.EXE | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAi4elAbvpzaLRZNPjlRv1U%3D | US | der | 471 b | shared |
— | — | GET | 200 | 104.107.210.17:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D | NL | der | 727 b | whitelisted |
— | — | GET | 200 | 216.58.215.238:80 | http://ocsp.pki.goog/GTSGIAG3/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCCCKTKO%2FebDAr | US | der | 463 b | whitelisted |
— | — | GET | 200 | 2.16.186.32:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR8sWZUnKvbRO5iJhat9GV793rVlAQUrb2YejS0Jvf6xCZU7wO94CTLVBoCECdm7lbrSfOOq9dwovyE3iI%3D | unknown | der | 471 b | whitelisted |
— | — | GET | 200 | 104.107.210.17:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR64T7ooMQqLLQoy%2BemBUYZQOKh6QQUkK9qOpRaC9iQ6hJWc99DtDoo2ucCEQCzNUBL%2B7kbceldihRHAMaa | NL | der | 472 b | whitelisted |
— | — | GET | 200 | 104.107.210.17:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR64T7ooMQqLLQoy%2BemBUYZQOKh6QQUkK9qOpRaC9iQ6hJWc99DtDoo2ucCEBQZr8DeSFN%2FkpmVCws6msc%3D | NL | der | 471 b | whitelisted |
— | — | GET | 200 | 216.58.215.238:80 | http://ocsp.pki.goog/GTSGIAG3/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCCFTsmsx2%2BJSa | US | der | 463 b | whitelisted |
— | — | GET | 200 | 2.16.186.8:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D | unknown | der | 727 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 13.107.5.88:443 | ocos-office365-s2s.msedge.net | Microsoft Corporation | US | whitelisted |
— | — | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 52.109.8.20:443 | nexusrules.officeapps.live.com | Microsoft Corporation | US | whitelisted |
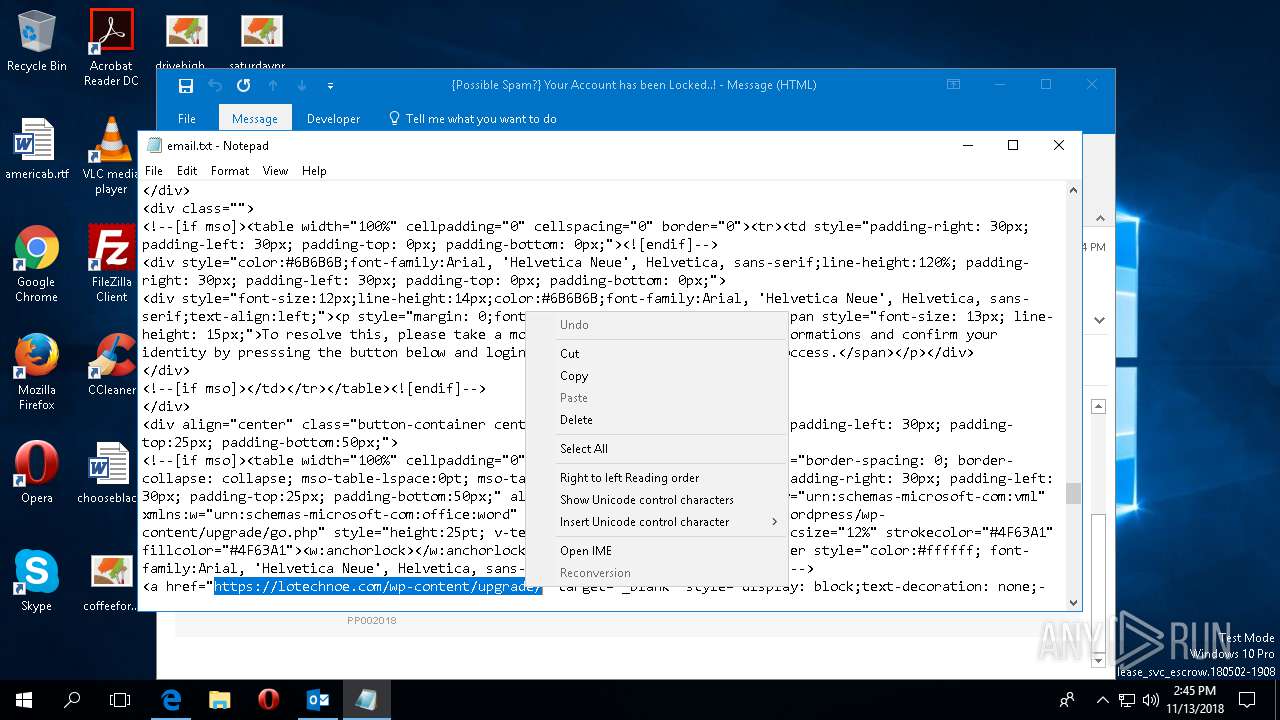
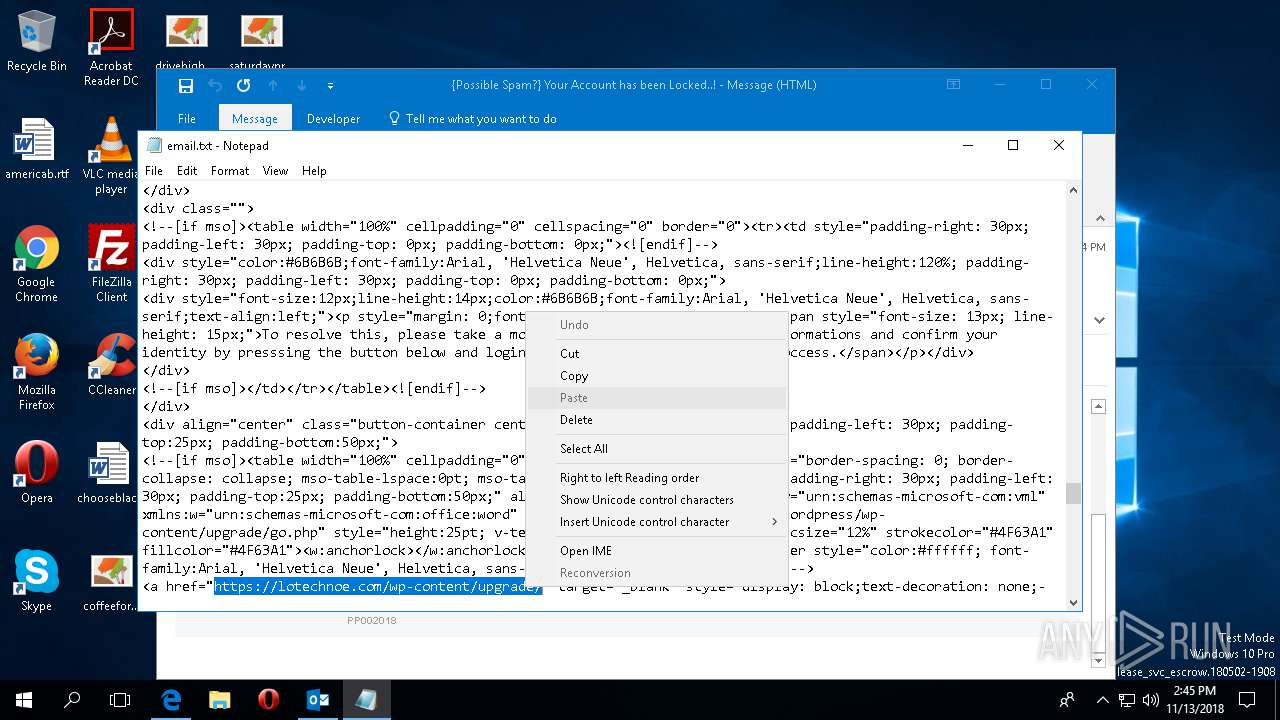
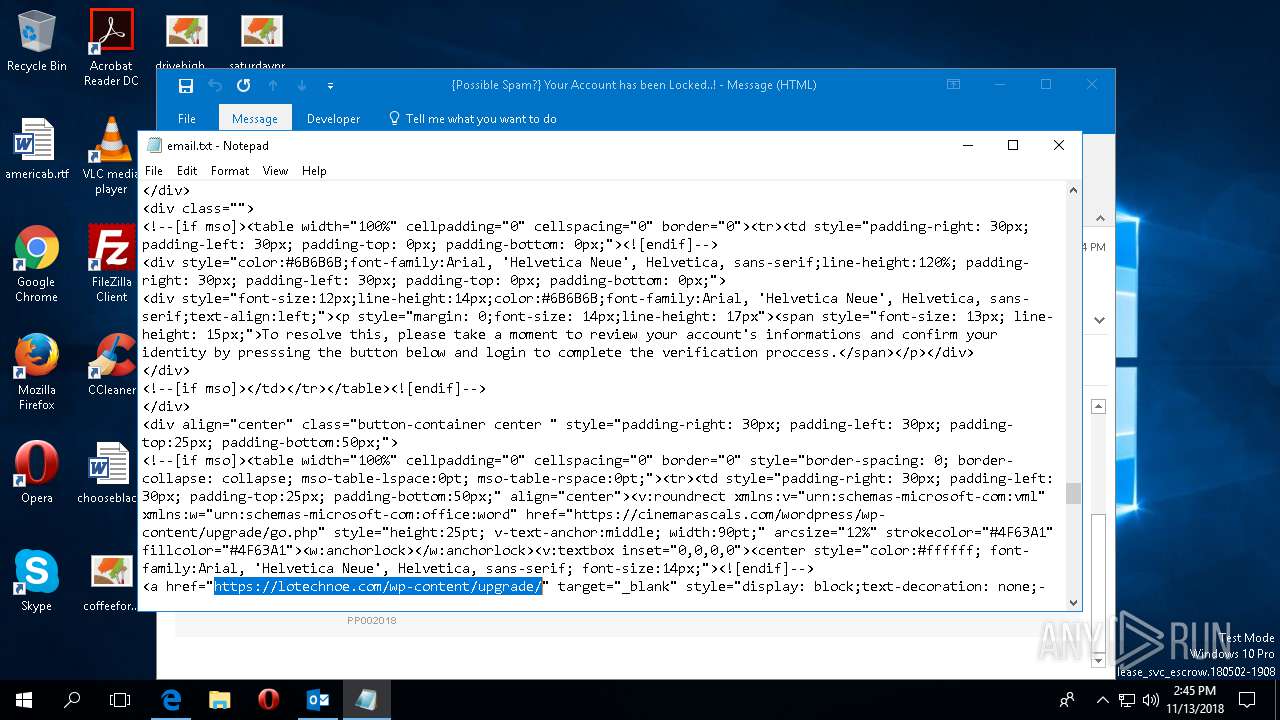
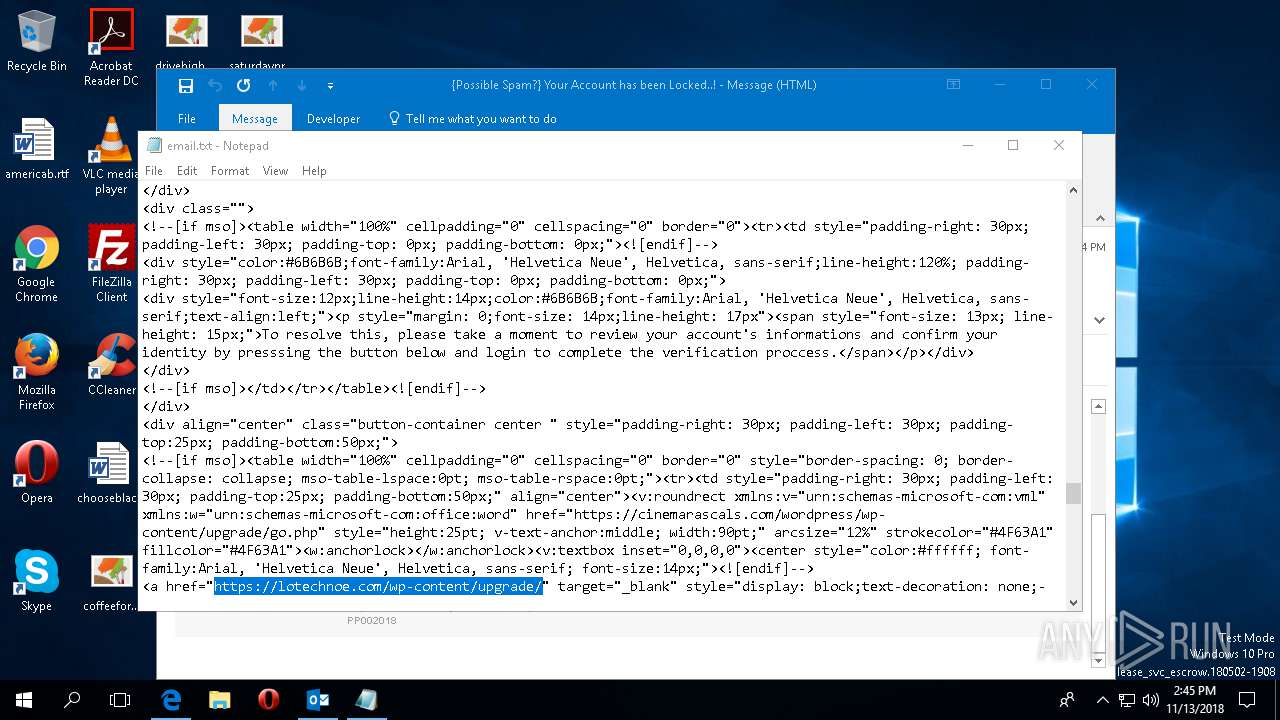
— | — | 185.224.137.23:443 | cinemarascals.com | — | — | malicious |
— | — | 2.16.186.32:80 | ocsp.usertrust.com | Akamai International B.V. | — | whitelisted |
— | — | 104.107.210.17:80 | ocsp.comodoca.com | Akamai International B.V. | NL | whitelisted |
— | — | 209.197.3.15:443 | maxcdn.bootstrapcdn.com | Highwinds Network Group, Inc. | US | whitelisted |
— | — | 216.58.215.234:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
— | — | 216.58.215.238:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
— | — | 216.58.215.227:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocos-office365-s2s.msedge.net |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
cinemarascals.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
maxcdn.bootstrapcdn.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |