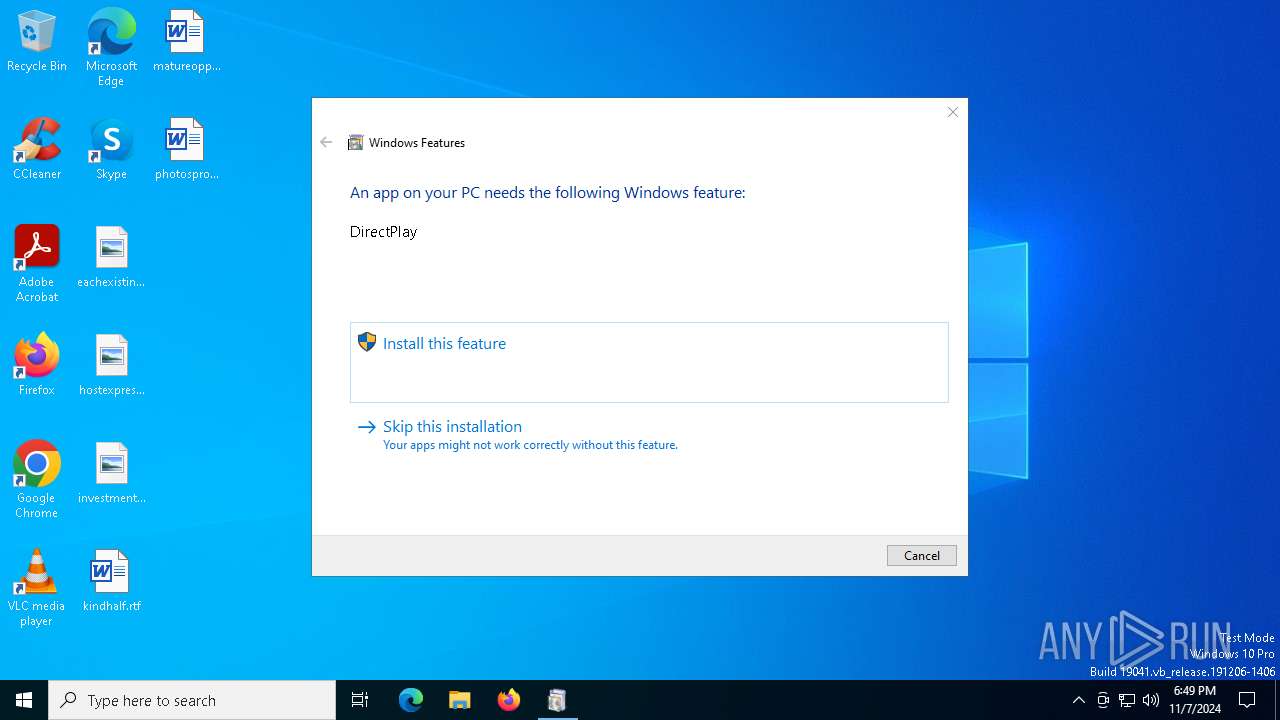
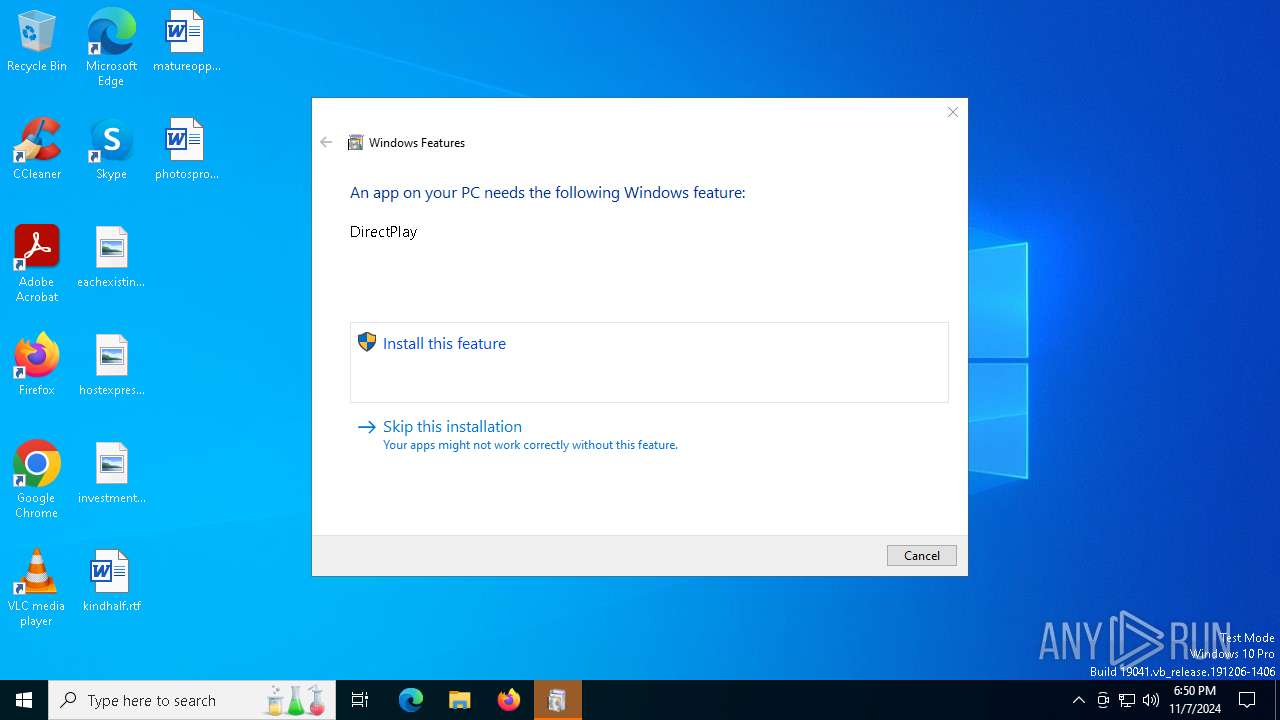
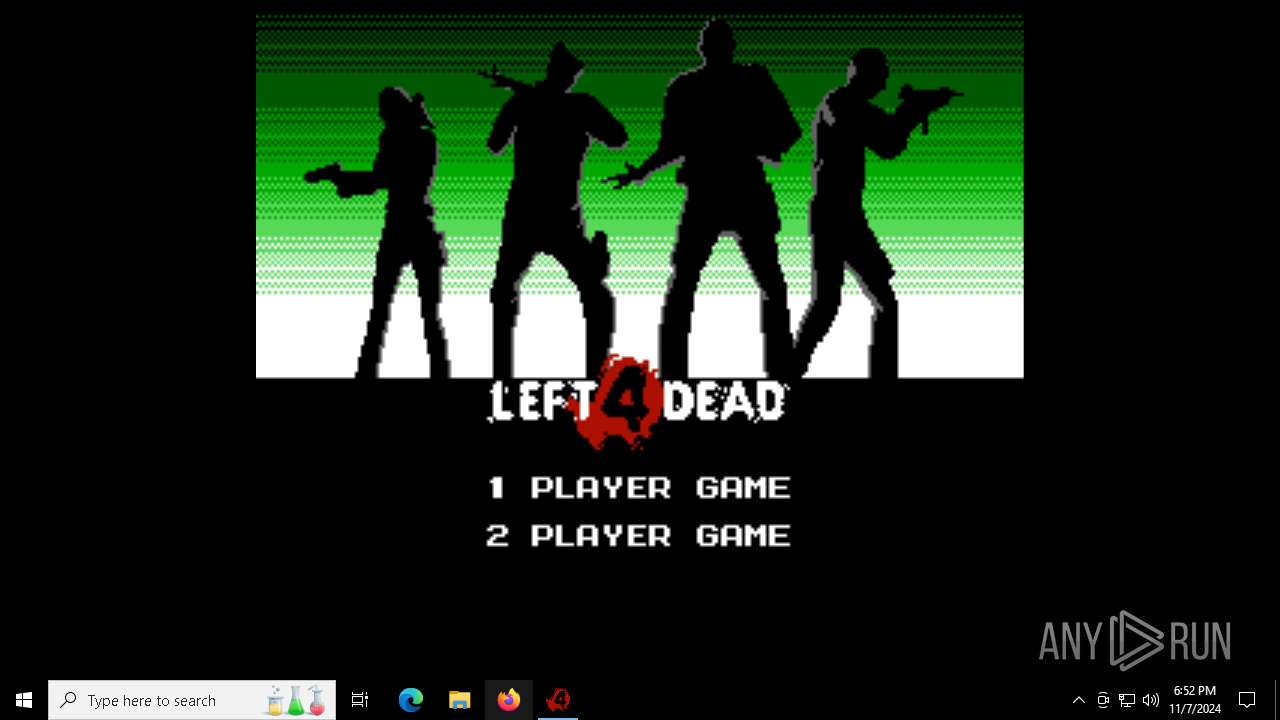
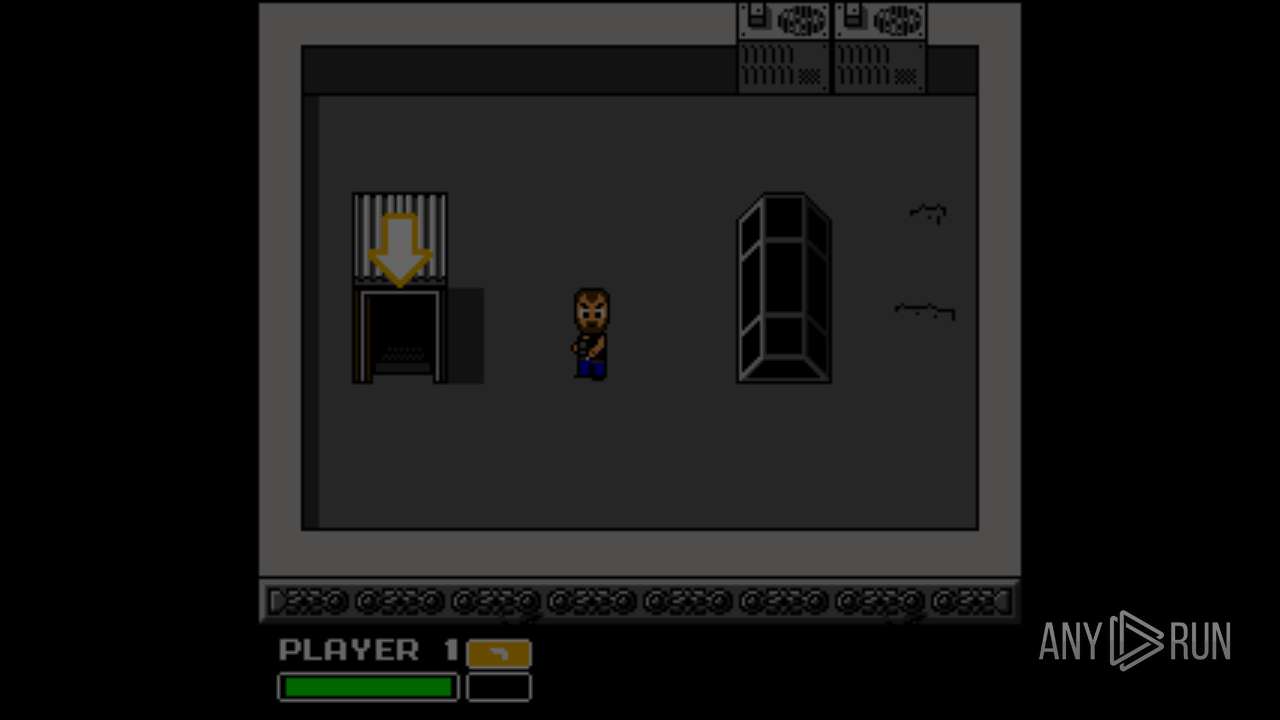
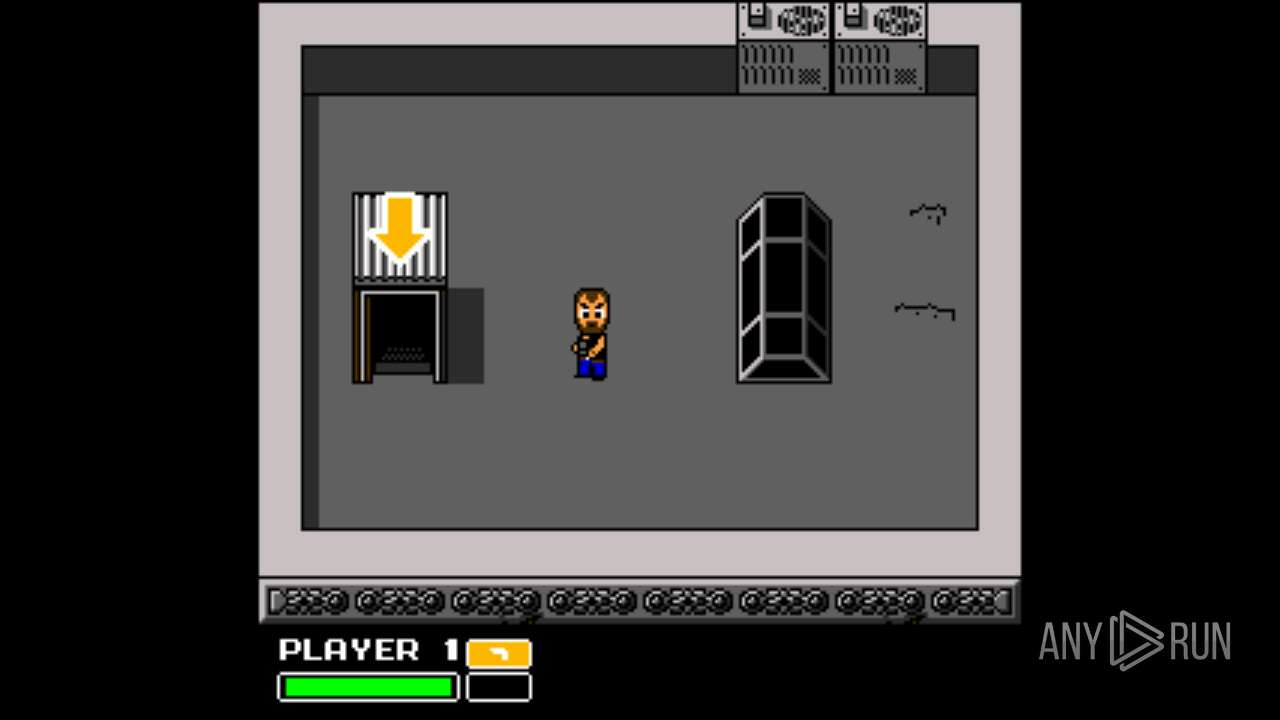
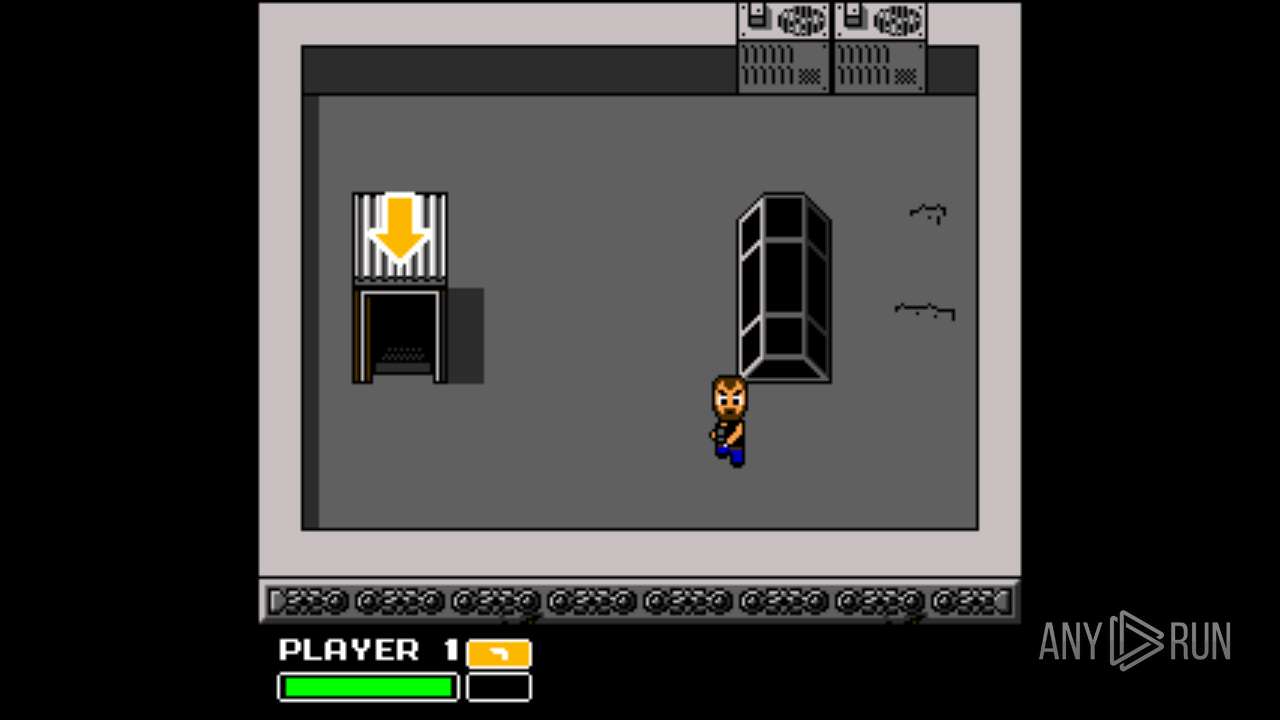
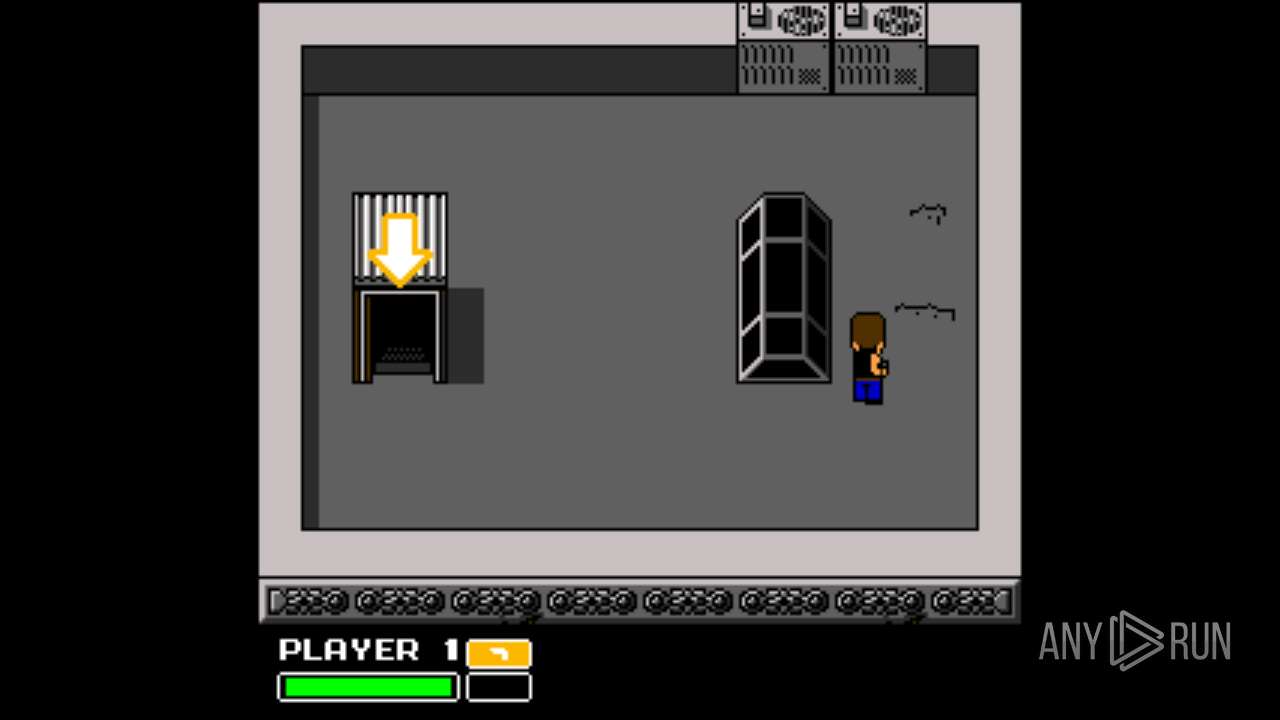
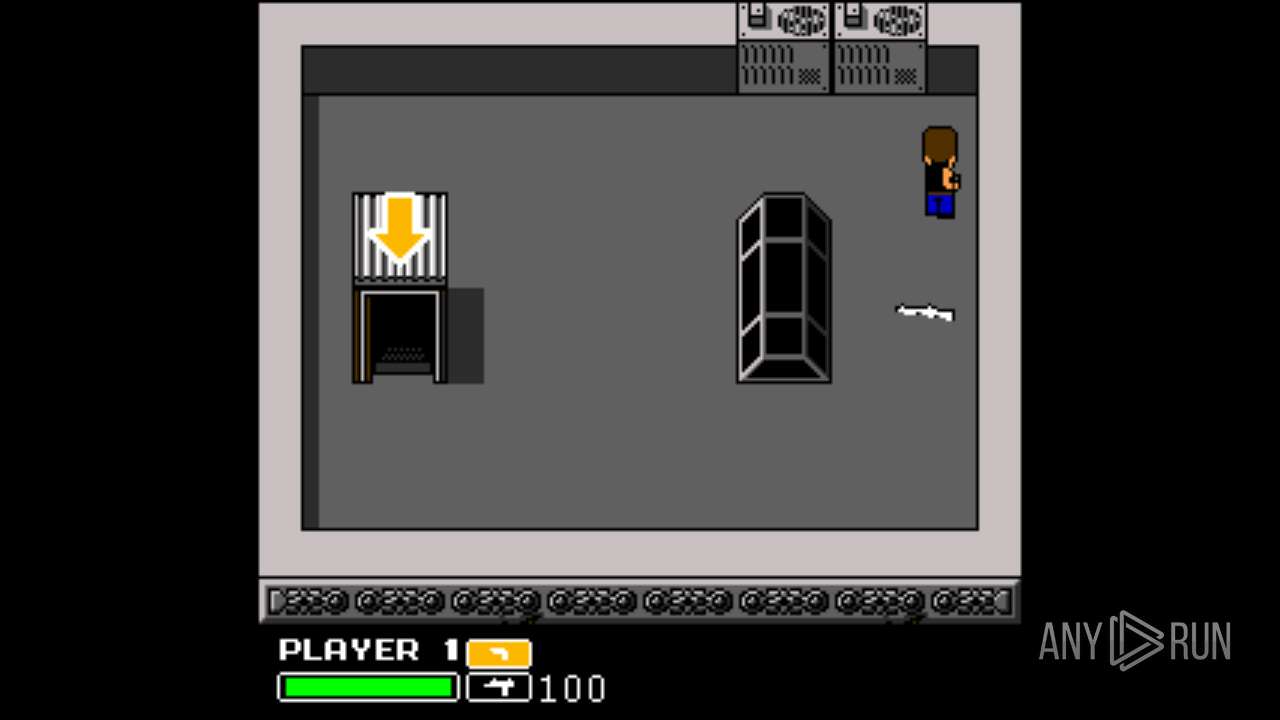
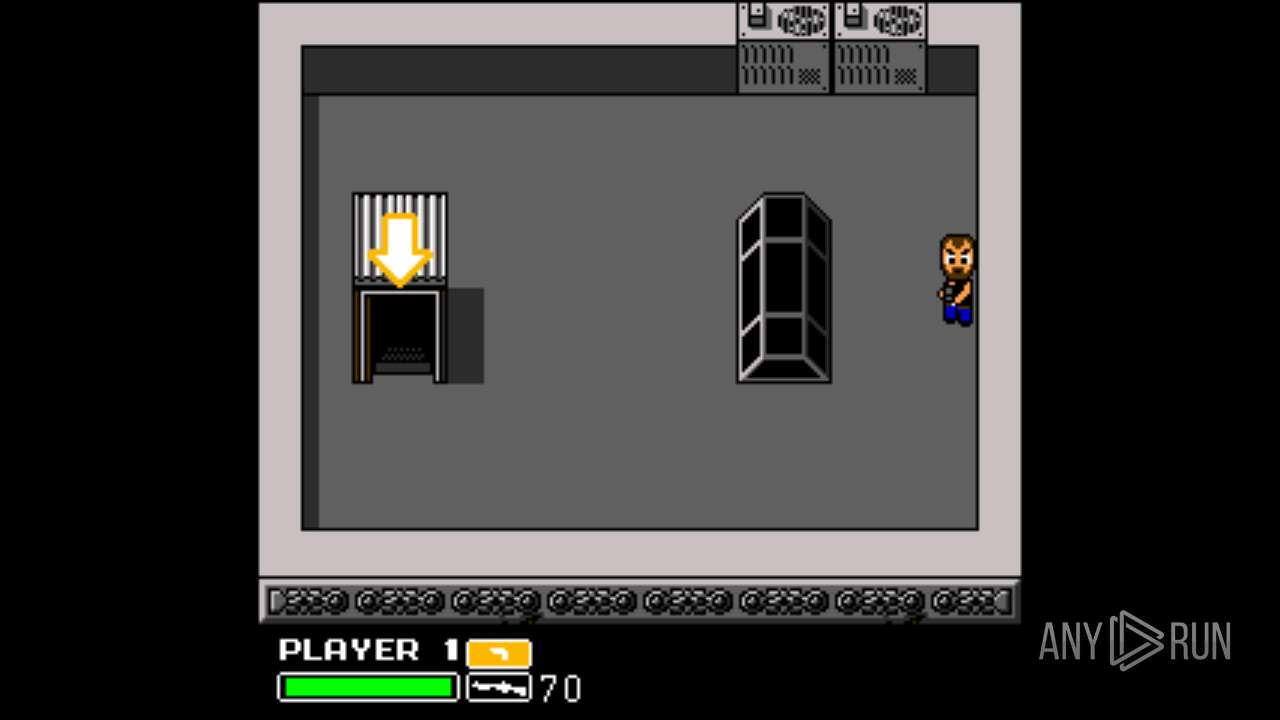
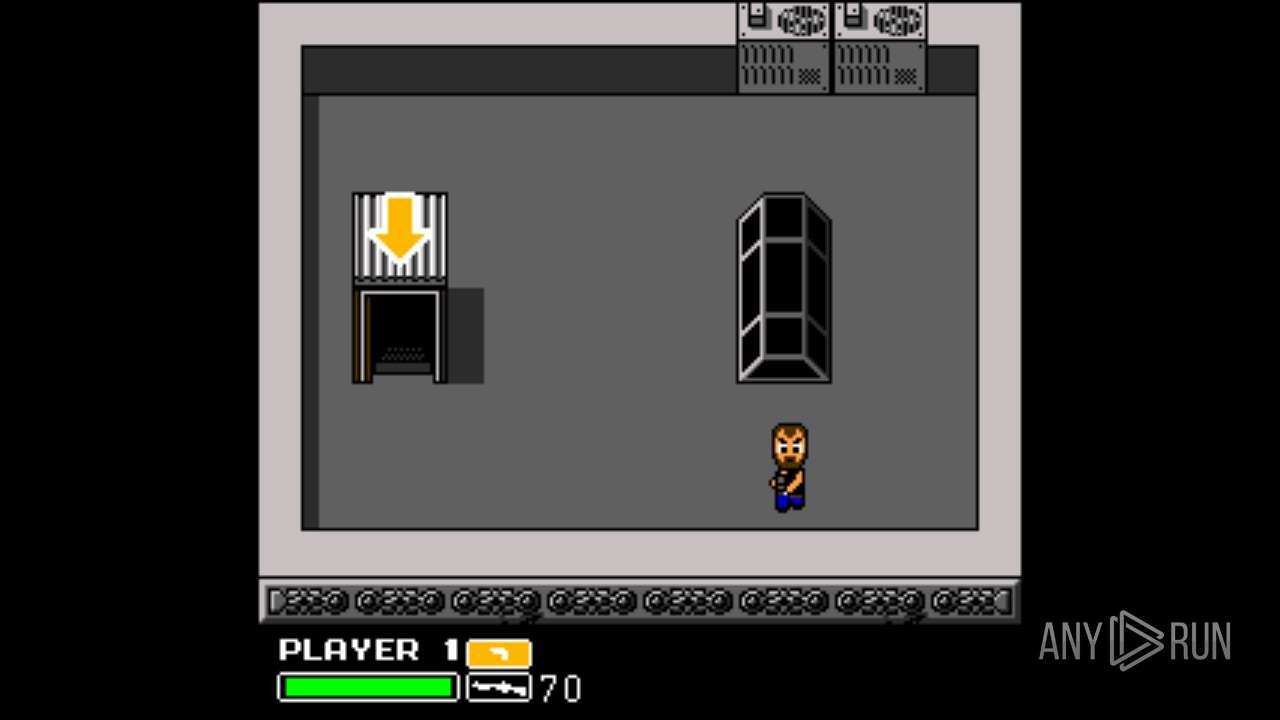
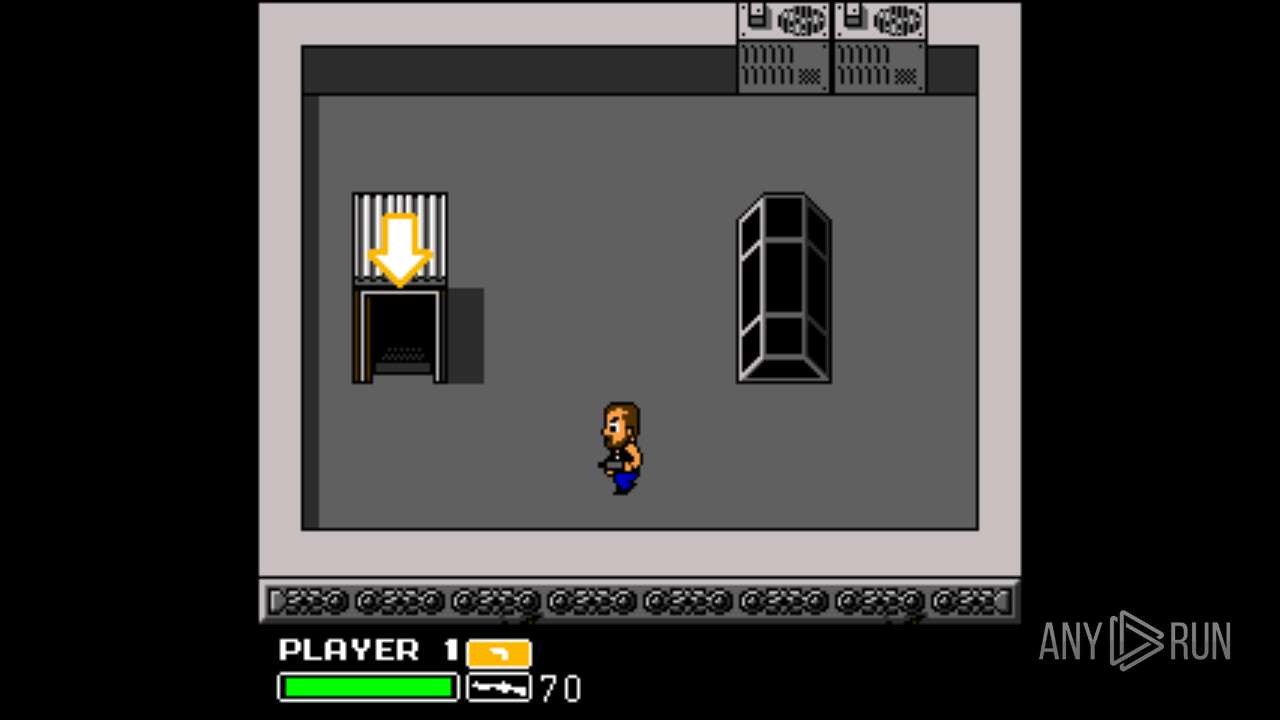
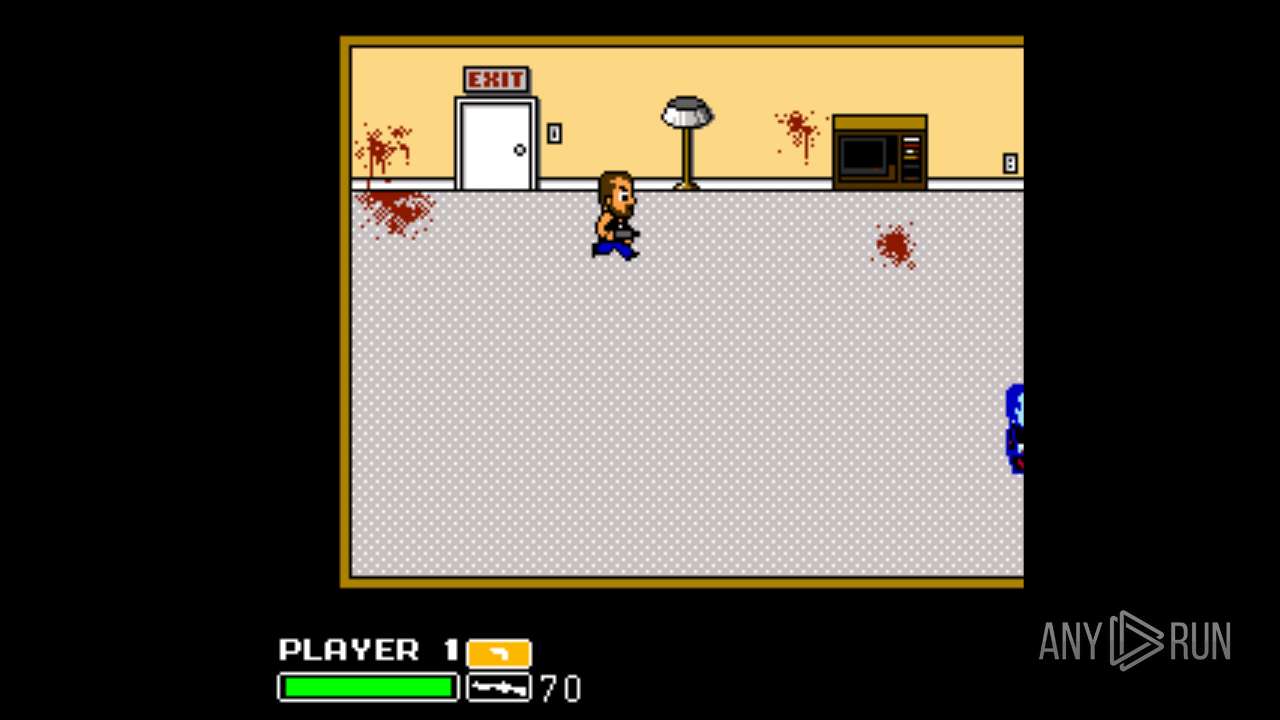
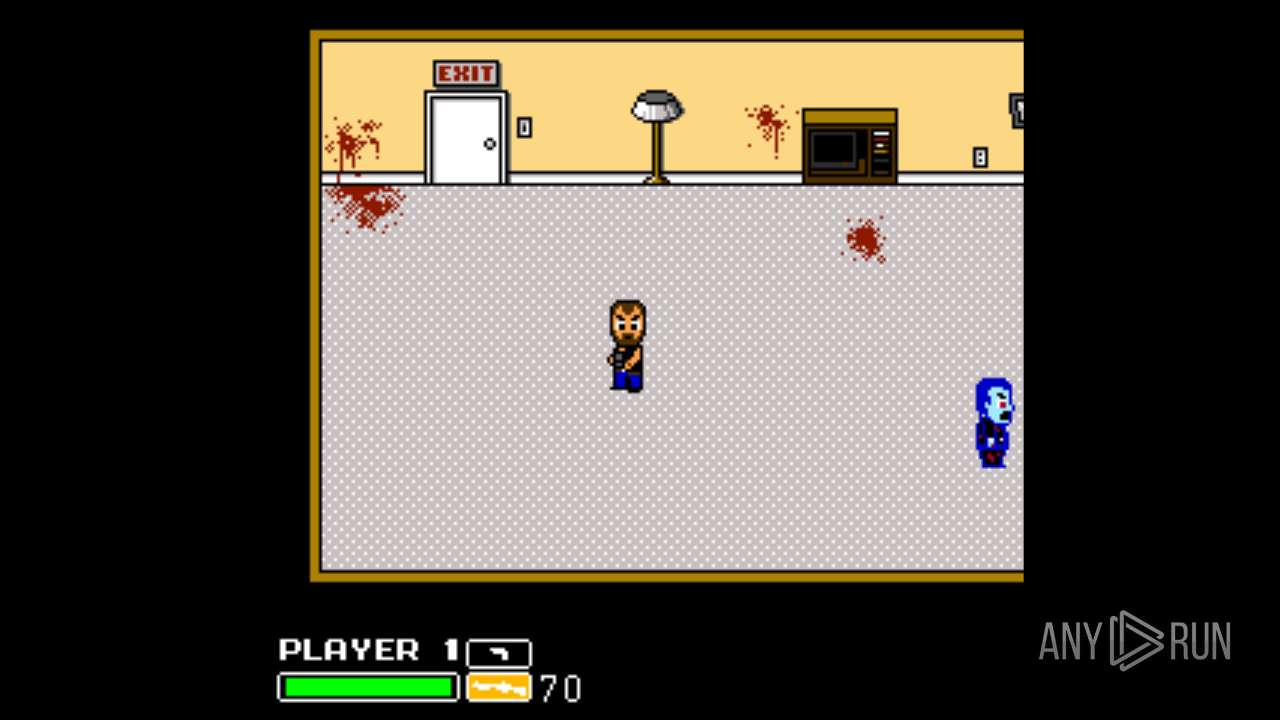
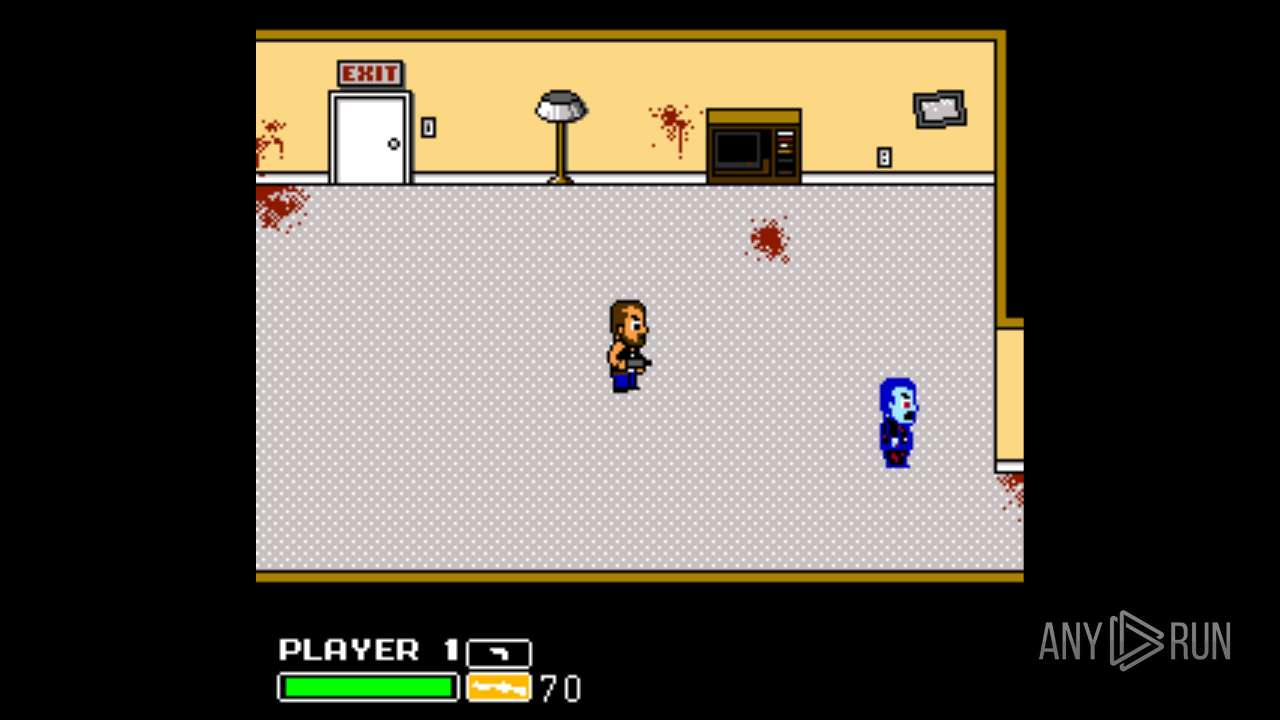
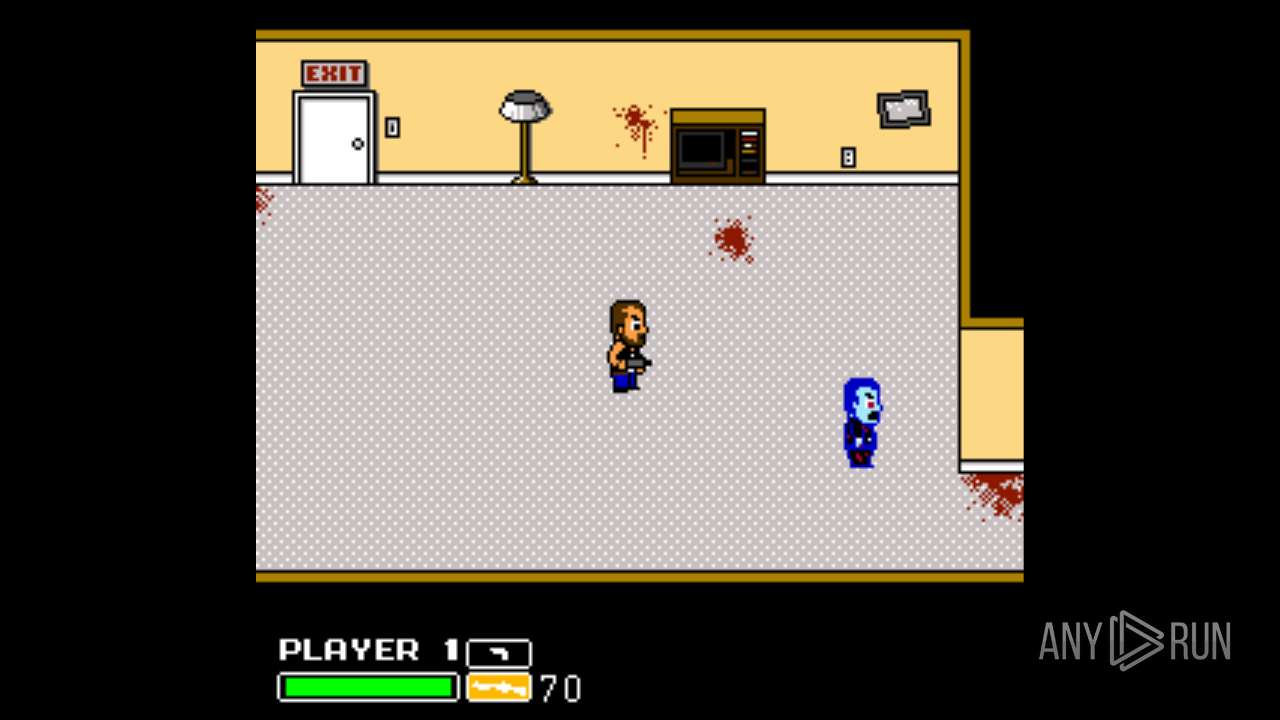
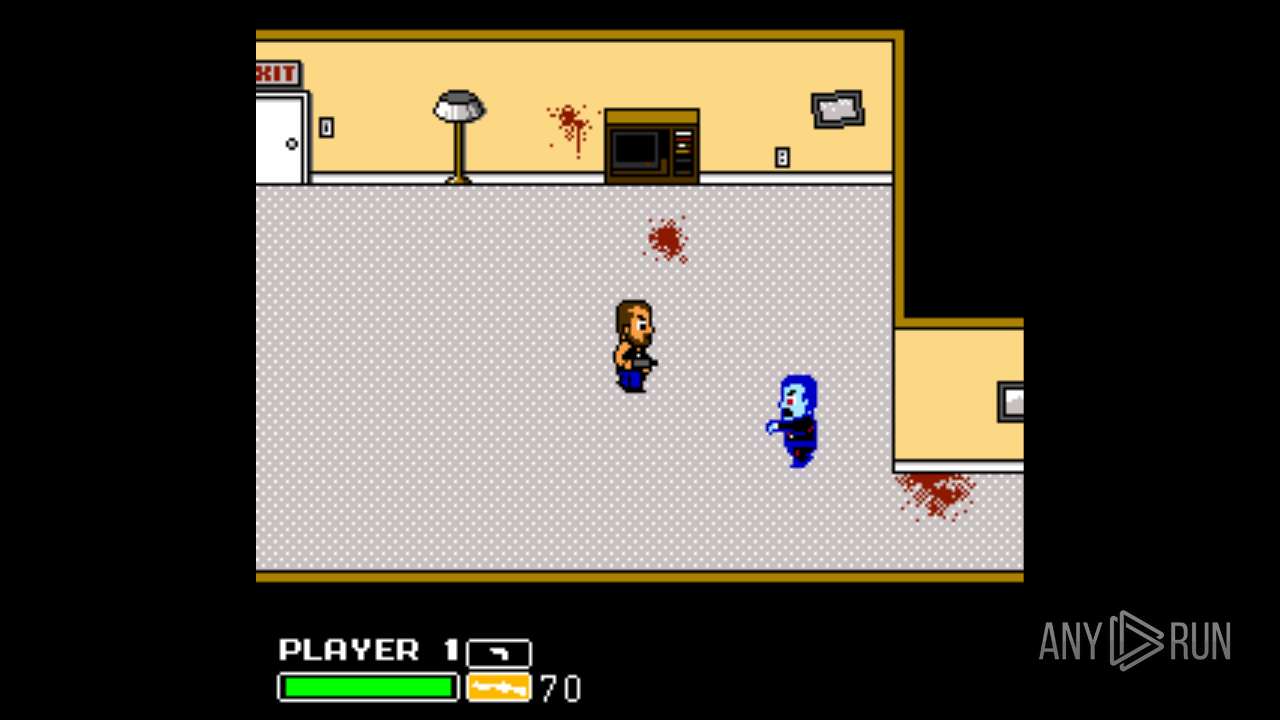
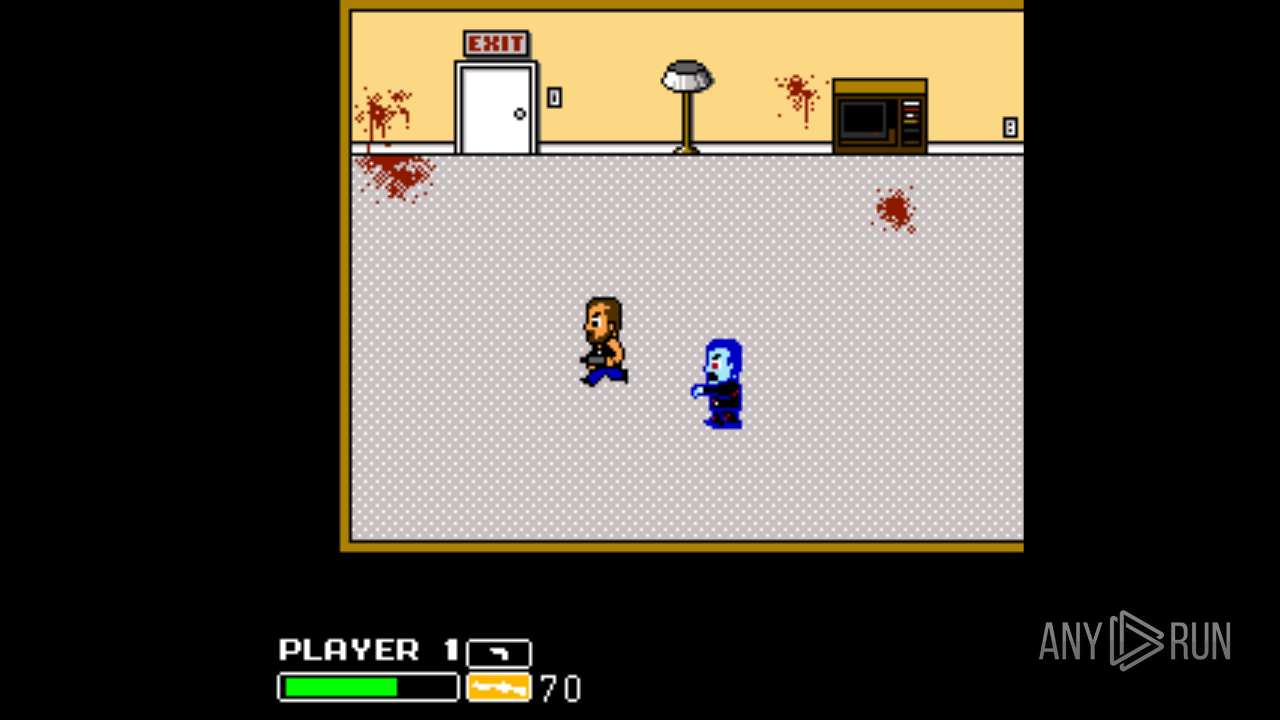
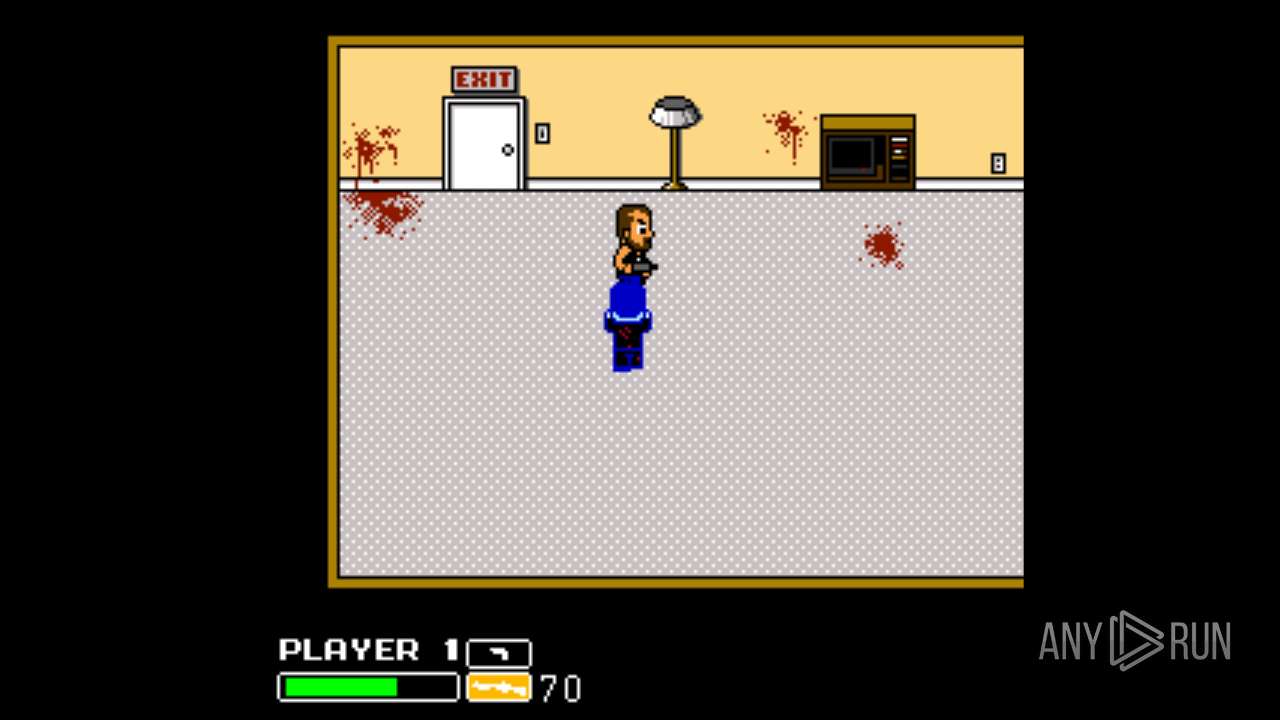
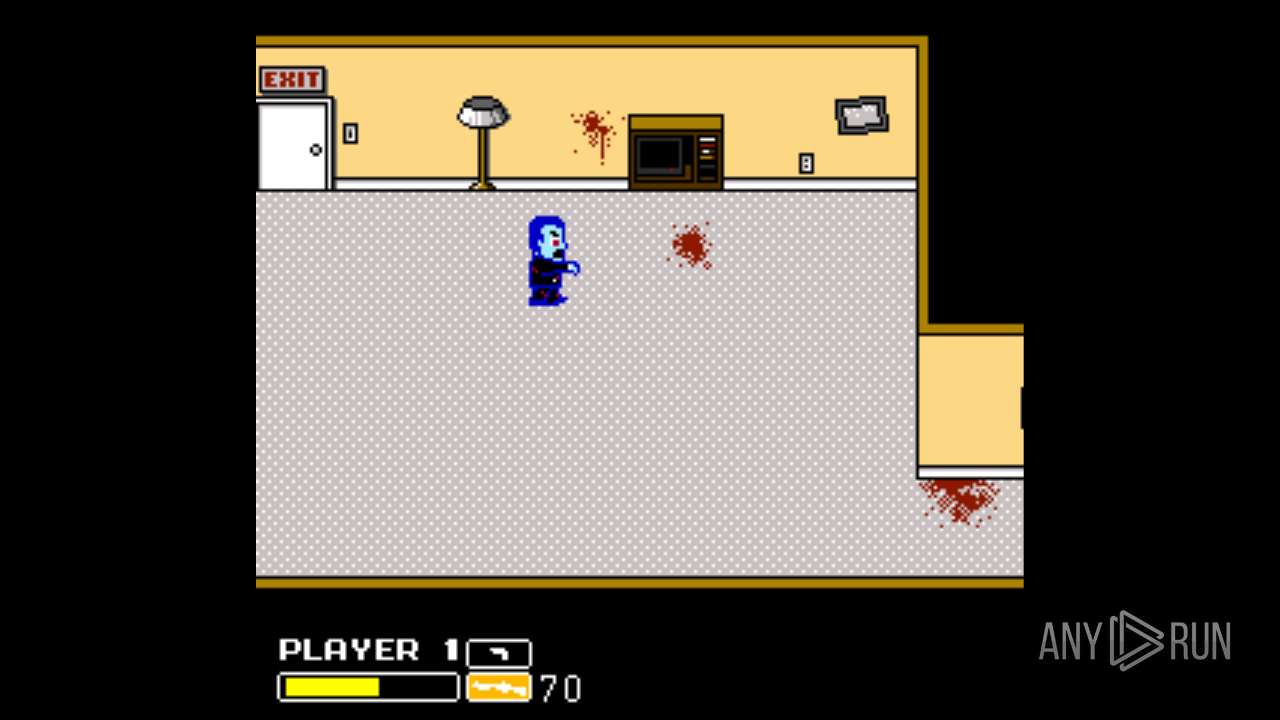
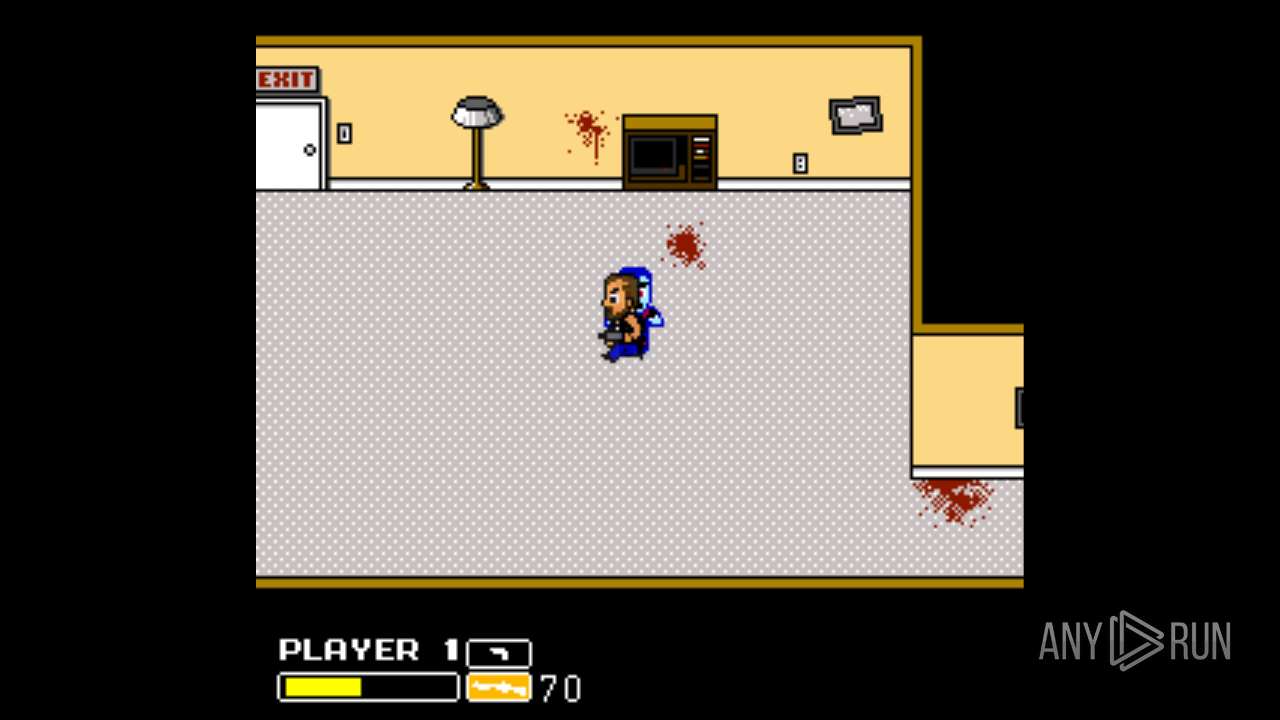
| File name: | Left 4 Dead.exe |
| Full analysis: | https://app.any.run/tasks/a9680b2a-59ce-4181-9d52-9b226eb5e5b6 |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2024, 18:49:46 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 8 sections |
| MD5: | 2A705E7B446AF6560BDA9FAAC2ACB336 |
| SHA1: | AE582EA8038B2B34E8A0F734824DDA5151CD2D55 |
| SHA256: | A962CB4E9E80D228C73E8354958DD0E5BC65CC5972F4496FB7CB27BD0F22455E |
| SSDEEP: | 98304:lXch2QdTER2iiJY0xZ/JriUrbLbronxnGiPrsLHyZaGc2gEOYnWx5vFY9MrCDYsj:8ilnI3oXRegH |
MALICIOUS
No malicious indicators.SUSPICIOUS
There is functionality for taking screenshot (YARA)
- Left 4 Dead.exe (PID: 6680)
Executes as Windows Service
- VSSVC.exe (PID: 4812)
Process drops legitimate windows executable
- TiWorker.exe (PID: 5920)
Executable content was dropped or overwritten
- TiWorker.exe (PID: 5920)
- Left 4 Dead.exe (PID: 6680)
INFO
Manages system restore points
- SrTasks.exe (PID: 7040)
Checks supported languages
- Left 4 Dead.exe (PID: 6680)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Borland Delphi 7 (54.2) |
|---|---|---|
| .exe | | | Win32 Executable Borland Delphi 5 (36.8) |
| .exe | | | InstallShield setup (3.5) |
| .exe | | | Win32 EXE PECompact compressed (generic) (3.3) |
| .exe | | | Win32 Executable Delphi generic (1.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1586176 |
| InitializedDataSize: | 380416 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1841a4 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.1.3 |
| ProductVersionNumber: | 1.0.1.3 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Eric Ruth Games |
| FileDescription: | - |
| FileVersion: | 1.0.1.3 |
| InternalName: | - |
| LegalCopyright: | Valve Software 2008 |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Pixel Force: Left 4 Dead |
| ProductVersion: | 1.0.1.3 |
| Comments: | - |
Total processes
144
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1552 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | Left 4 Dead.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 4348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 4812 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5920 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Exit code: 0 Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6680 | "C:\Users\admin\AppData\Local\Temp\Left 4 Dead.exe" | C:\Users\admin\AppData\Local\Temp\Left 4 Dead.exe | explorer.exe | ||||||||||||
User: admin Company: Eric Ruth Games Integrity Level: MEDIUM Version: 1.0.1.3 Modules
| |||||||||||||||
| 7040 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | TiWorker.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
Total events
3 833
Read events
3 770
Write events
49
Delete events
14
Modification events
| (PID) Process: | (6680) Left 4 Dead.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Left 4 Dead.exe | |||
| (PID) Process: | (5920) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31142213 | |||
| (PID) Process: | (5920) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
| (PID) Process: | (5920) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS\ServicingStackVersions |
| Operation: | write | Name: | 10.0.19041.3989 (WinBuild.160101.0800) |
Value: 2024/11/7:18:50:28.679 10.0.19041.3989 (WinBuild.160101.0800) | |||
| (PID) Process: | (5920) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PendingRequired |
Value: | |||
| (PID) Process: | (5920) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PendingXmlIdentifier |
Value: | |||
| (PID) Process: | (5920) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PoqexecFailure |
Value: | |||
| (PID) Process: | (5920) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | ExecutionState |
Value: | |||
| (PID) Process: | (5920) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | RepairTransactionPended |
Value: | |||
| (PID) Process: | (5920) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | DoqTime |
Value: 0 | |||
Executable files
43
Suspicious files
35
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5920 | TiWorker.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
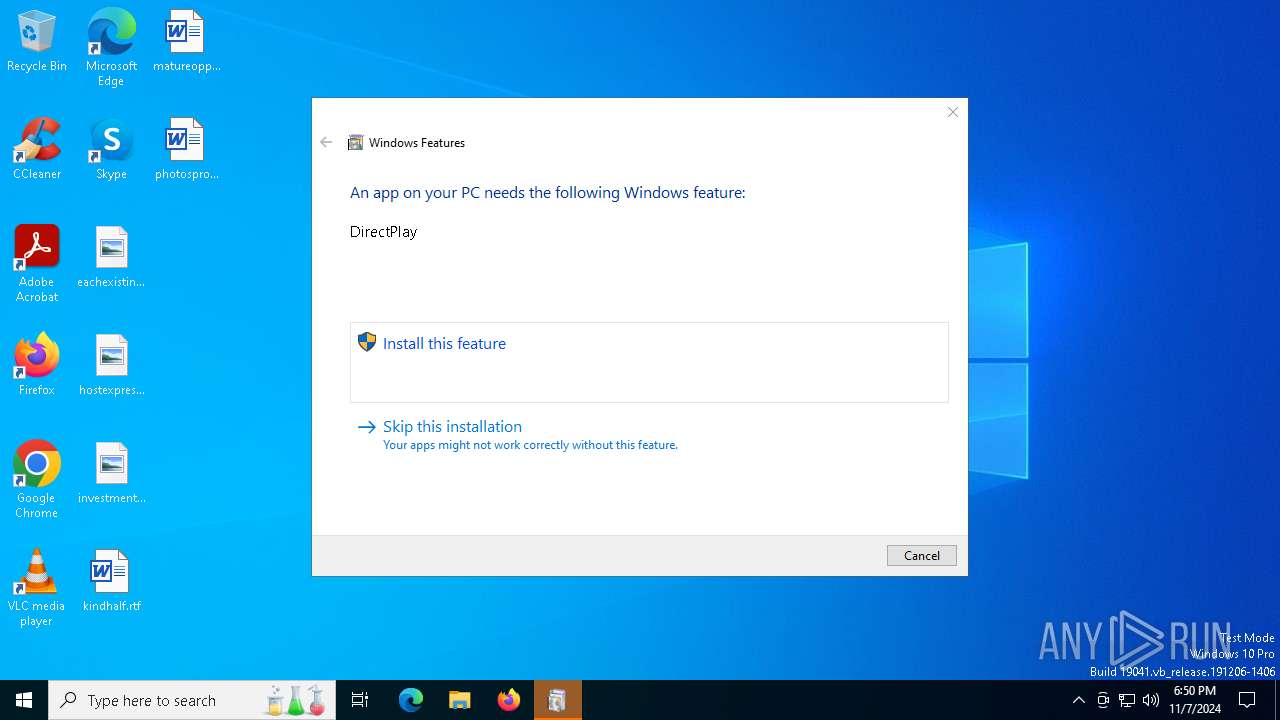
| 5920 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\31828a064631db01110000002017141a\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dpmodemx.dll | executable | |
MD5:CDE67309989D9E0944501F71A690DA95 | SHA256:4482FDFA30C60A6FF68DAB91B3DD340A16990A7BCE04A4D11481B09BB6BD796E | |||
| 5920 | TiWorker.exe | C:\Windows\WinSxS\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dpmodemx.dll | executable | |
MD5:CDE67309989D9E0944501F71A690DA95 | SHA256:4482FDFA30C60A6FF68DAB91B3DD340A16990A7BCE04A4D11481B09BB6BD796E | |||
| 5920 | TiWorker.exe | C:\Windows\WinSxS\Temp\PendingDeletes\22d298064631db01150000002017141a.dpwsockx.dll | binary | |
MD5:88B0B31201F3C9EC0DCEF1BEDAD05185 | SHA256:7E59374D1E693E01C928C40E2F2A5BF608203A3A429672DD1127950307884F08 | |||
| 5920 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\31828a064631db01110000002017141a\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dplaysvr.exe | executable | |
MD5:F825C2679BB5177E015FD3F0133B7788 | SHA256:EBC69C1285014C40D286ABFAC9CB3CE18B99B422AA9A30B56313C9CA7E1E8804 | |||
| 5920 | TiWorker.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:B65D56867B37CF3312651554B6202D32 | SHA256:C4FC49745961651F210E2ED4254C68EF11FF9355623E0C3C2E80D88ADFD68E16 | |||
| 5920 | TiWorker.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{a24899af-b58f-427f-b61e-84e69a4c6e98}_OnDiskSnapshotProp | binary | |
MD5:B65D56867B37CF3312651554B6202D32 | SHA256:C4FC49745961651F210E2ED4254C68EF11FF9355623E0C3C2E80D88ADFD68E16 | |||
| 5920 | TiWorker.exe | C:\Windows\servicing\Sessions\31142213_3904226853.xml | xml | |
MD5:36E65A5835D19CF49792B7C6562335FD | SHA256:EE896B2B0A1FCA20005D828F18700A641EA70E84EF712231A369A312549E24C3 | |||
| 5920 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:0857CEF33AB99FF3FDCF94BEEFD2B923 | SHA256:C2A051264A24AE9933ACA5474D99462C7AE6BBEF560D1376A6792765B31AA181 | |||
| 5920 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\31828a064631db01110000002017141a\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dplayx.dll | executable | |
MD5:27D86453433108C3E1DF2EC84F8B3758 | SHA256:32C9CA064999D8A87CAB3EE4AA2D9566278D254326A7EFAED8D33E6A44170759 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
43
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 173.223.117.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2224 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2224 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7060 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
5488 | MoUsoCoreWorker.exe | 173.223.117.131:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4360 | SearchApp.exe | 2.16.204.144:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |