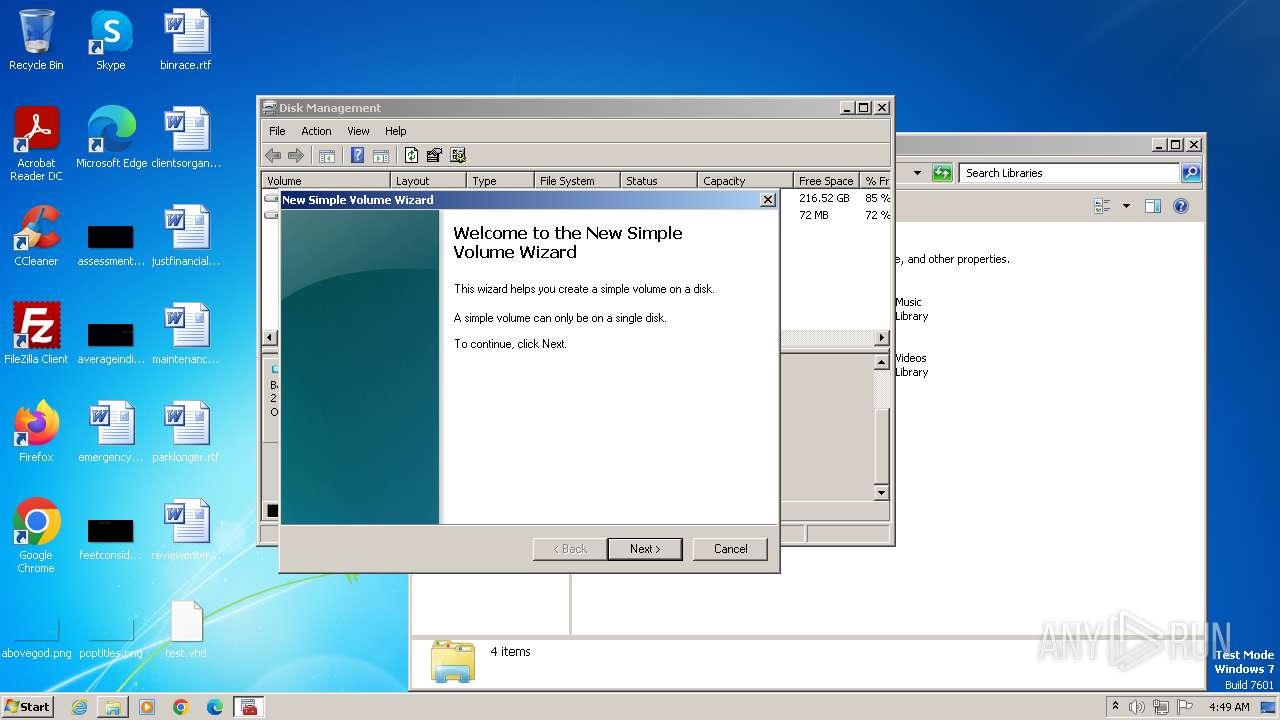
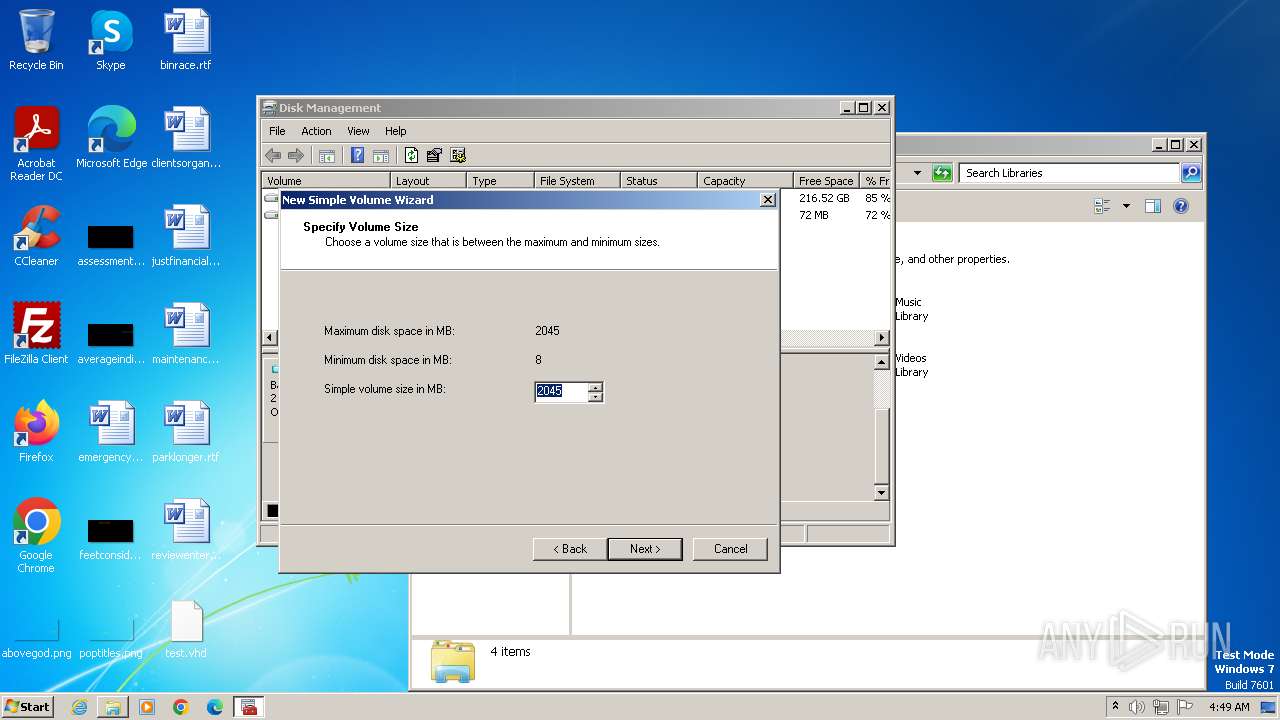
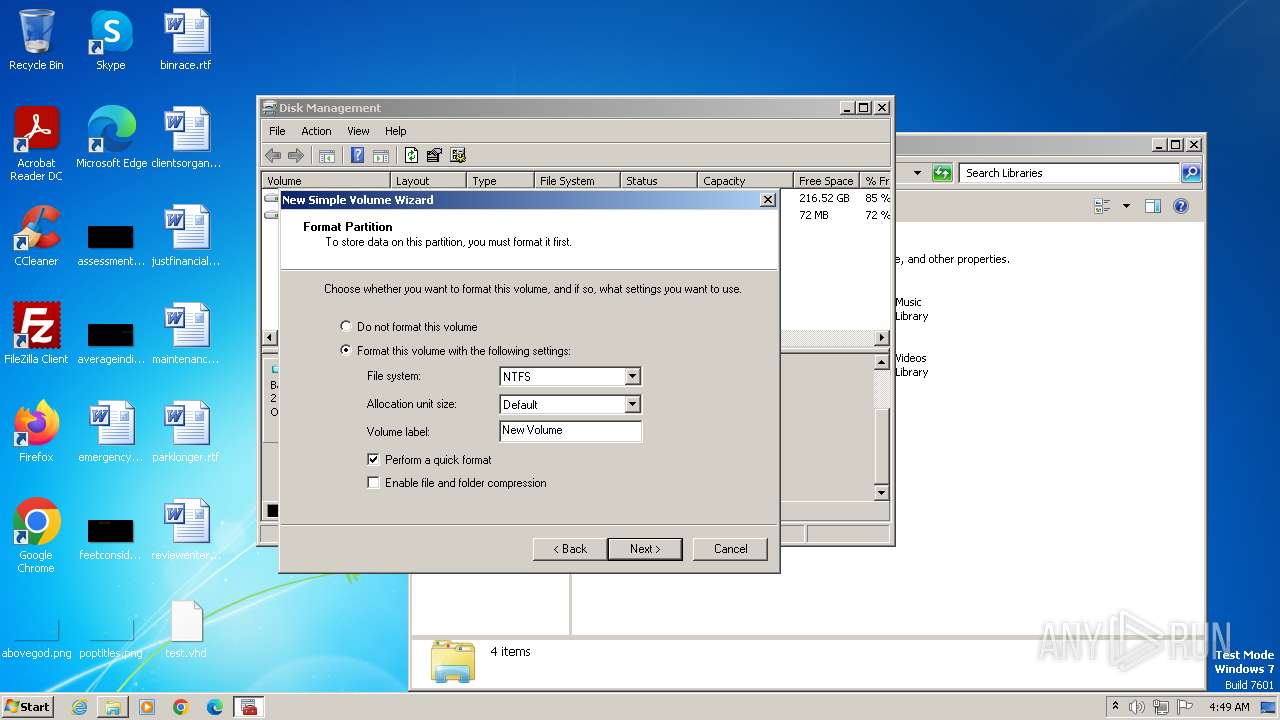
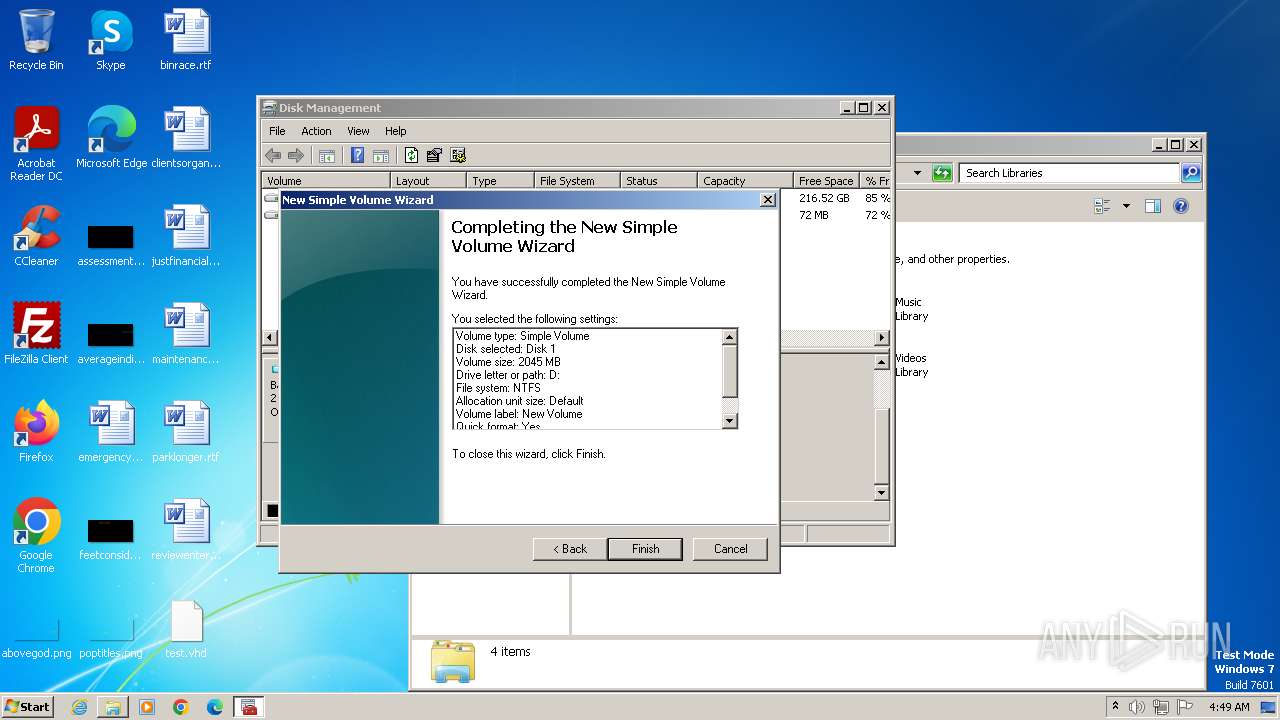
| File name: | U.exe |
| Full analysis: | https://app.any.run/tasks/fa0a3b4d-4836-4e20-aed1-5a11fb5b357f |
| Verdict: | Malicious activity |
| Analysis date: | October 06, 2023, 03:47:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 7E95F8B5DFF13C6E11F24133306A59F3 |
| SHA1: | C2B4E26C24E75CB840C214BD673727B94D5811BA |
| SHA256: | A94B300E638E57F55FAB5F61EAA389B7F0CEDCF5C80BCF516C3B49F5E8B41C5C |
| SSDEEP: | 1536:EBrE3lCdHup+pADgJ/Ffc+p9c3EyzsWjcdVJjwnW4r:A8lXp+lZc+pLy8LjwW4r |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- vds.exe (PID: 2404)
Reads the Internet Settings
- mmc.exe (PID: 2372)
- rundll32.exe (PID: 2332)
Checks Windows Trust Settings
- drvinst.exe (PID: 1232)
- drvinst.exe (PID: 592)
- drvinst.exe (PID: 3248)
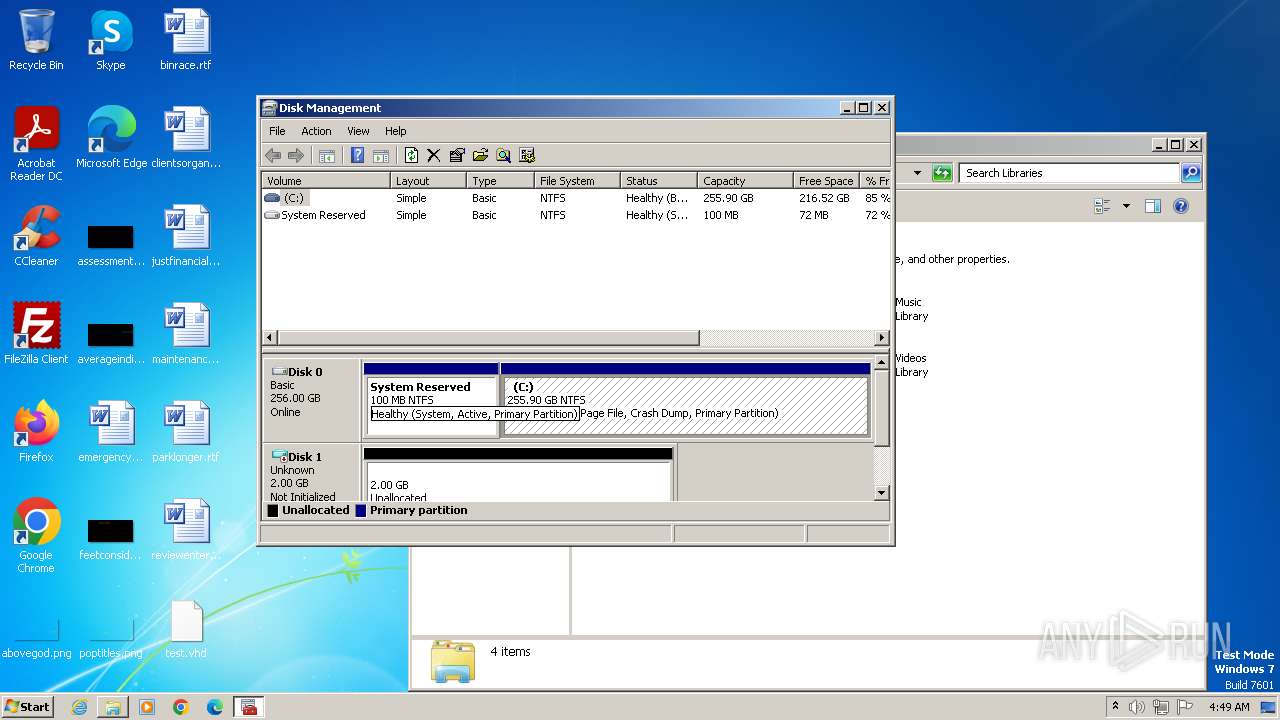
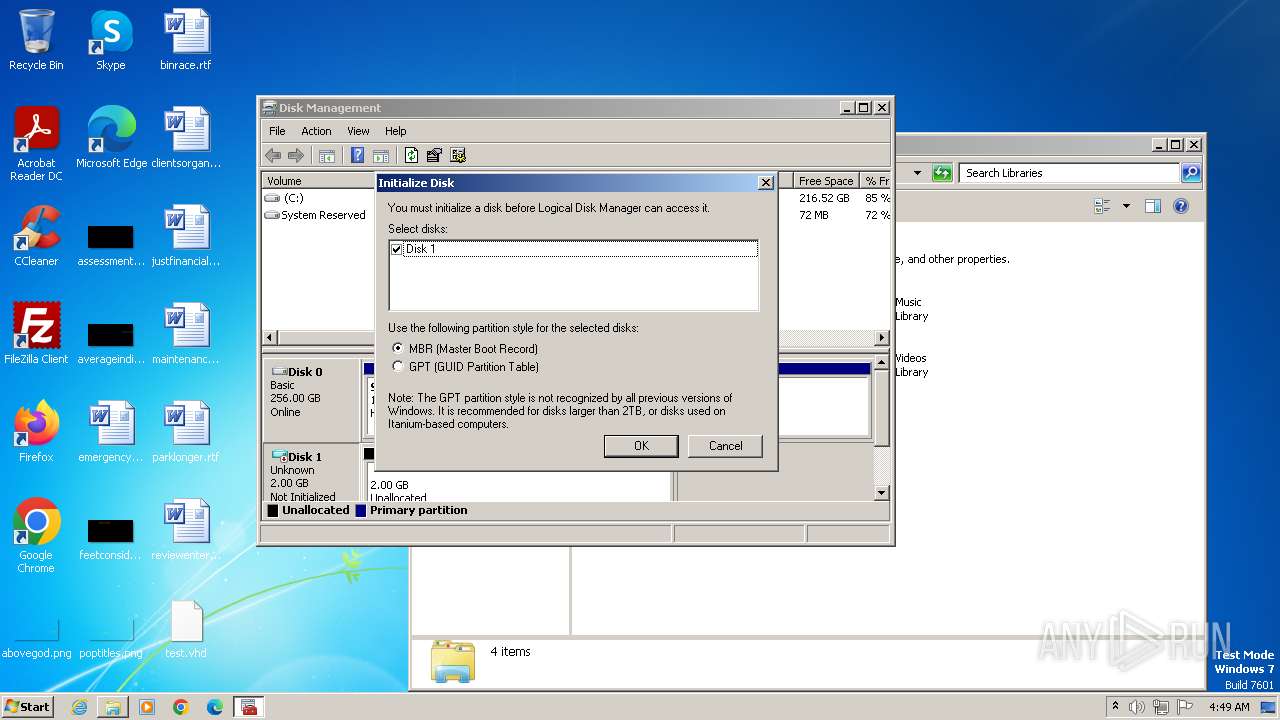
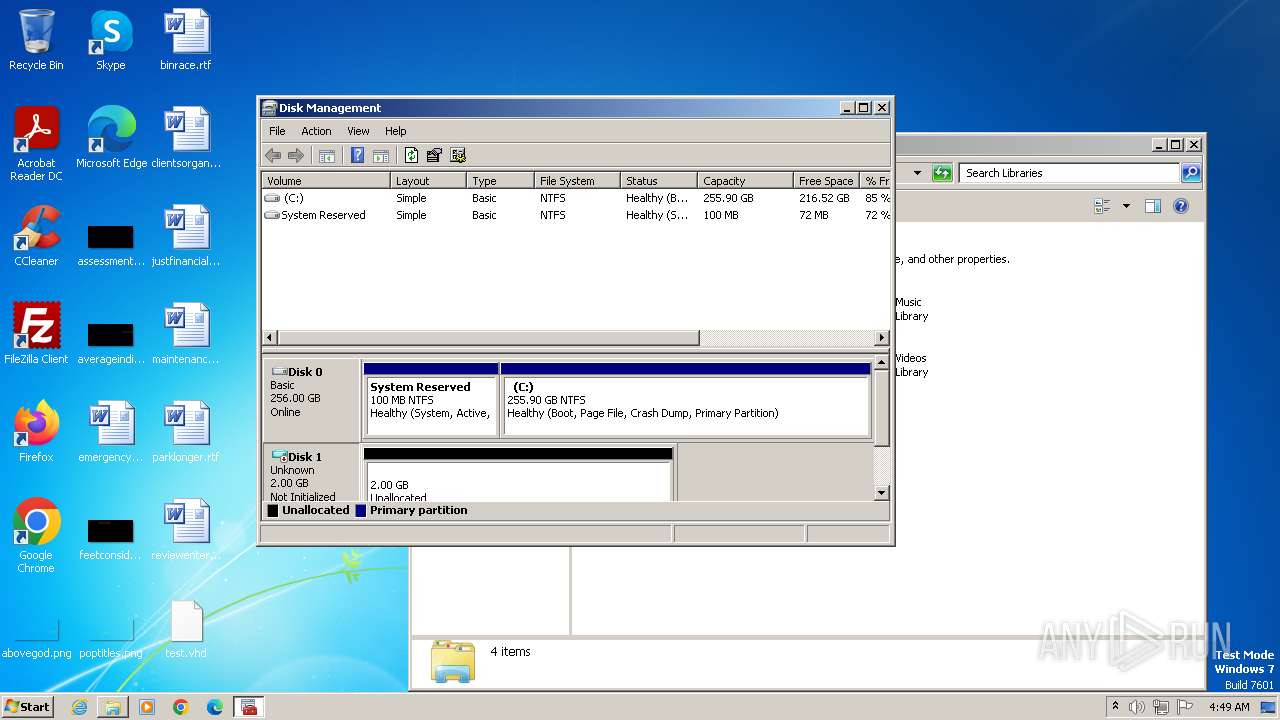
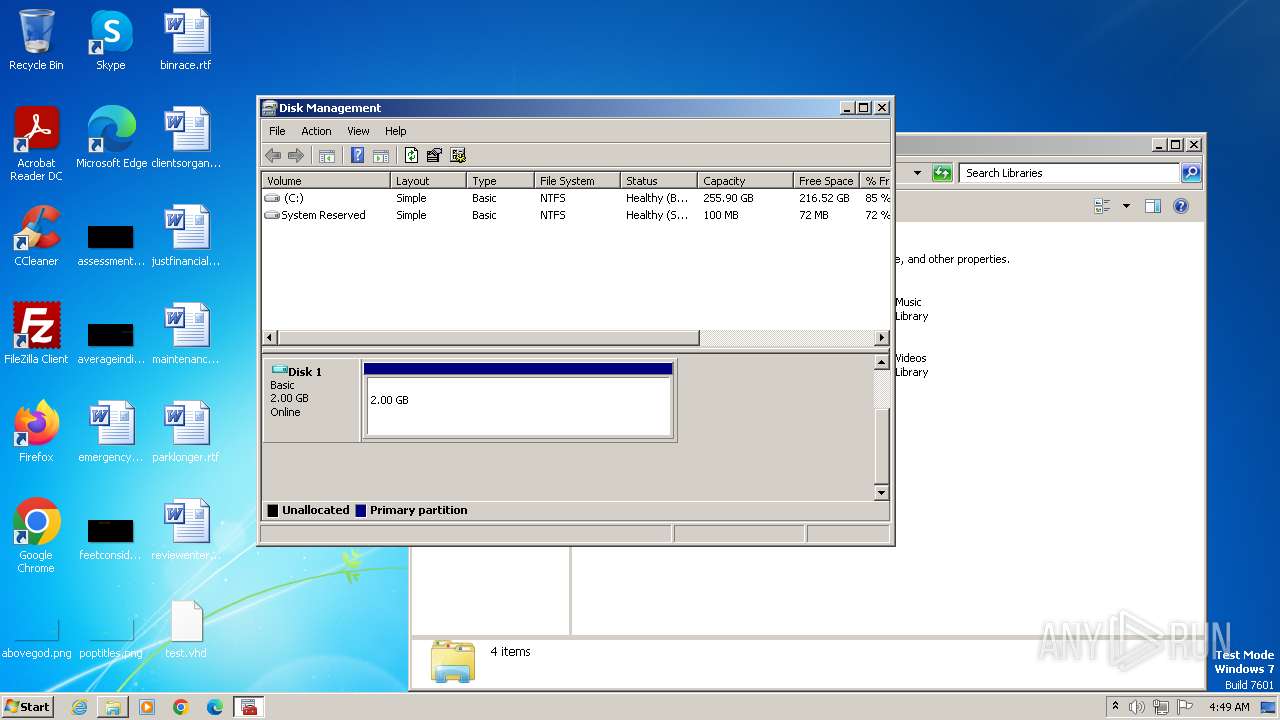
Image mount is detect
- drvinst.exe (PID: 592)
INFO
Checks supported languages
- U.exe (PID: 2484)
- wmpnscfg.exe (PID: 2852)
- drvinst.exe (PID: 1232)
- drvinst.exe (PID: 592)
- drvinst.exe (PID: 3248)
- U.exe (PID: 2884)
Reads the computer name
- wmpnscfg.exe (PID: 2852)
- drvinst.exe (PID: 1232)
- drvinst.exe (PID: 592)
- drvinst.exe (PID: 3248)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2852)
- drvinst.exe (PID: 1232)
- drvinst.exe (PID: 592)
- drvinst.exe (PID: 3248)
Manual execution by a user
- mmc.exe (PID: 3360)
- wmpnscfg.exe (PID: 2852)
- explorer.exe (PID: 3988)
- mmc.exe (PID: 2372)
- U.exe (PID: 2884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:01:28 05:06:10+01:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 11 |
| CodeSize: | 41984 |
| InitializedDataSize: | 55808 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2993 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
60
Monitored processes
13
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 592 | DrvInst.exe "1" "200" "SCSI\Disk&Ven_Msft&Prod_Virtual_Disk\2&1f4adffe&0&000001" "" "" "69911eaf3" "00000000" "00000618" "000005E4" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | DrvInst.exe "1" "200" "{8e7bd593-6e6c-4c52-86a6-77175494dd8e}\MsVhdHba\1&3030e83&0&01" "" "" "66583b687" "00000000" "000005E0" "000005E8" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1928 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2332 | rundll32.exe C:\Windows\system32\newdev.dll,pDiDeviceInstallNotification \\.\pipe\PNP_Device_Install_Pipe_1.{6abebe58-8d4a-4ac9-898c-142170ba7758} "(null)" | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
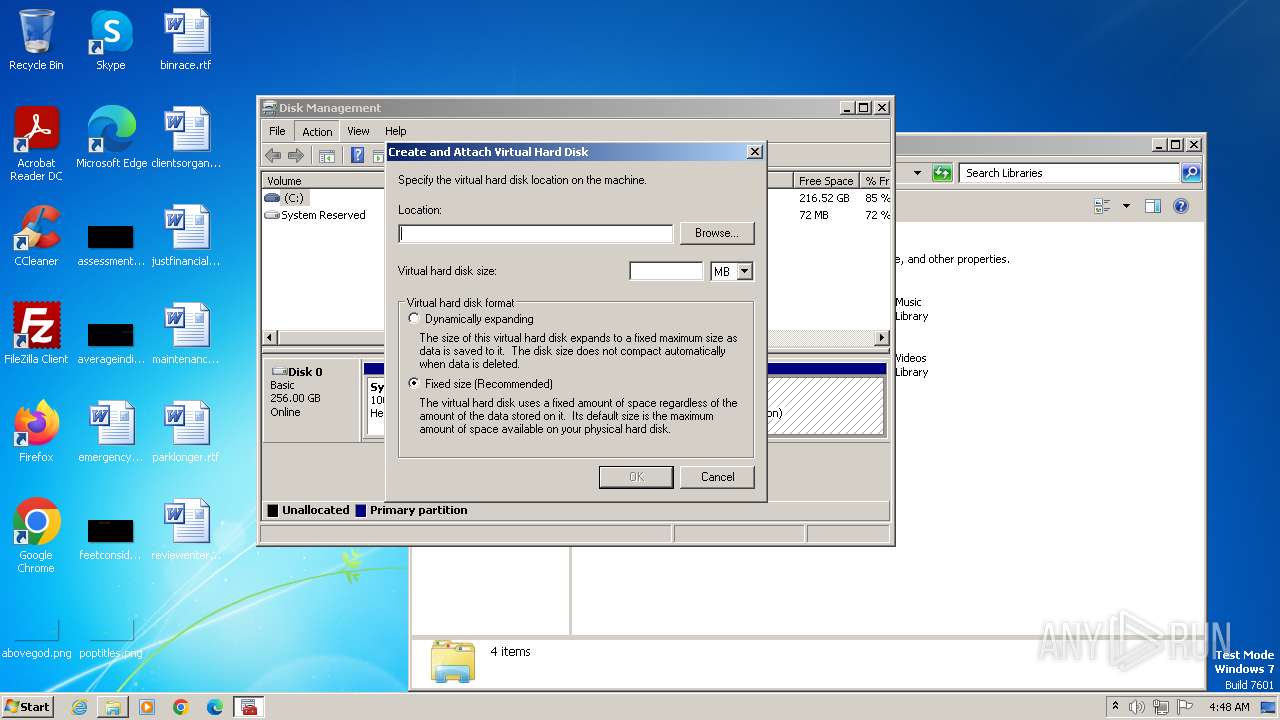
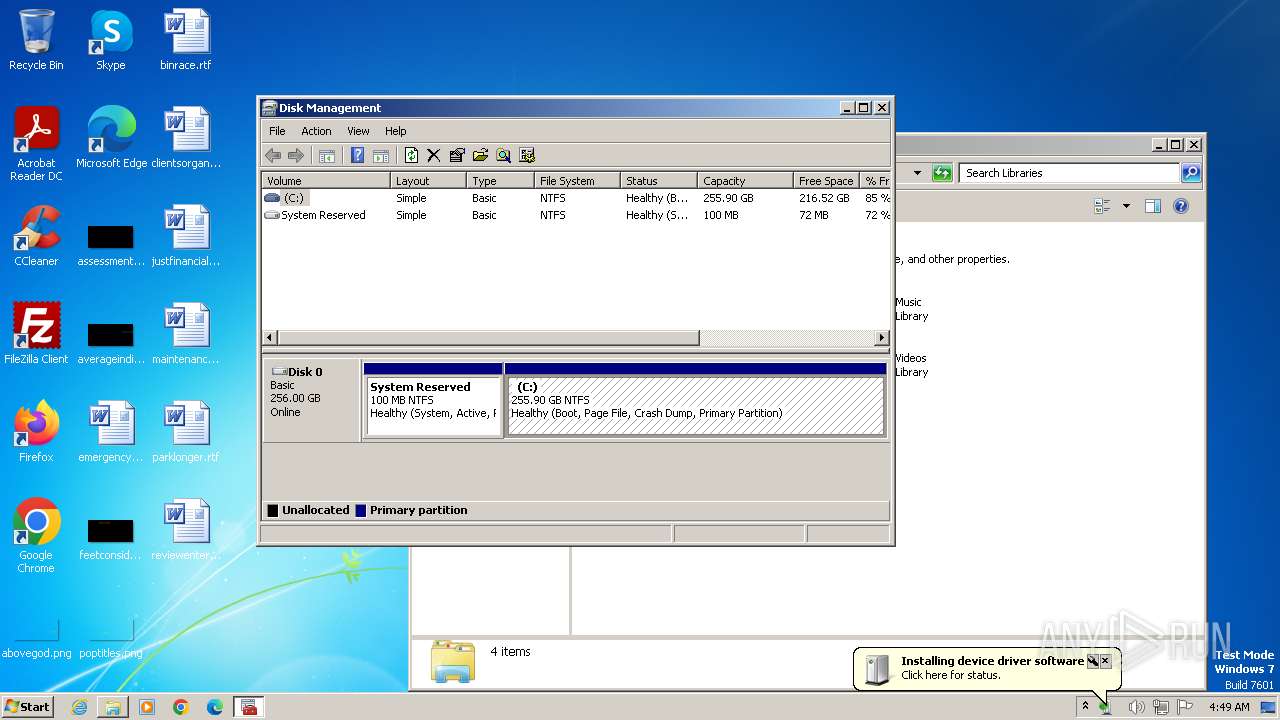
| 2372 | "C:\Windows\system32\mmc.exe" C:\Windows\system32\diskmgmt.msc | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2404 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2484 | "C:\Users\admin\AppData\Local\Temp\U.exe" | C:\Users\admin\AppData\Local\Temp\U.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2488 | "C:\Windows\System32\dinotify.exe" pnpui.dll,SimplifiedDINotification | C:\Windows\System32\dinotify.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Device Installation Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2852 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | "C:\Users\admin\AppData\Local\Temp\U.exe" | C:\Users\admin\AppData\Local\Temp\U.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
10 697
Read events
10 597
Write events
92
Delete events
8
Modification events
| (PID) Process: | (2852) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{1CFDEB62-E7B5-4745-BF1B-33377B1DE92D}\{6B87D382-2823-481A-B3A0-BA011C4A7647} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2852) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{1CFDEB62-E7B5-4745-BF1B-33377B1DE92D} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2852) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{84BCD53B-BE9B-4F7D-991E-086722F1A76C} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2372) mmc.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (2372) mmc.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000000000000700000006000000010000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (2372) mmc.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2372) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | delete value | Name: | 0 |
Value: 6D006D0063002E0065007800650000000000 | |||
| (PID) Process: | (2372) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\LastVisitedPidlMRU |
| Operation: | write | Name: | MRUListEx |
Value: 020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (2372) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\OpenSavePidlMRU\* |
| Operation: | write | Name: | MRUListEx |
Value: 0A00000009000000080000000700000006000000050000000400000003000000020000000100000000000000FFFFFFFF | |||
| (PID) Process: | (2372) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\ComDlg32\CIDSizeMRU |
| Operation: | delete value | Name: | 0 |
Value: 6D006D0063002E006500780065000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000FE000000EB000000AB020000C80100000101000001010000AD02000027020000BE000000400000003E03000020020000000000000000000000000000000000000100000000000000 | |||
Executable files
0
Suspicious files
5
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1232 | drvinst.exe | C:\Windows\INF\vhdmp.PNF | binary | |
MD5:66E0E007E577508A40AB638991F60BAC | SHA256:2F88E6AF11804AB70995E6E2E131D35B127A77CE5664B46DEADD2D625B806ABE | |||
| 1232 | drvinst.exe | C:\Windows\INF\setupapi.ev3 | binary | |
MD5:3B30EB4945E73367BC49BB44E88725EF | SHA256:D9EF00D6E5363E33F2149950B249C441827BE2FA0097B3268CE4558C9854F371 | |||
| 1232 | drvinst.exe | C:\Windows\INF\setupapi.ev2 | binary | |
MD5:05E5695A48EBE102C320C5316B8055F3 | SHA256:FEAD79C2B8AF15A0DFDE7E52CE19BB4B993612235CFA206F5D3001C45749F035 | |||
| 1232 | drvinst.exe | C:\Windows\System32\DriverStore\FileRepository\vhdmp.inf_x86_neutral_efa659e9a38d5b8c\vhdmp.PNF | binary | |
MD5:C30262B79AC9B3F62E65E740F257EA8B | SHA256:D5BAE40F138499DFDB27DBB9144B10AA3AB9B746A0447B8A87FD0C4B384EDE36 | |||
| 1232 | drvinst.exe | C:\Windows\INF\setupapi.ev1 | binary | |
MD5:B20118E4E8C48AE7BDDCDAE53419AD52 | SHA256:15FCE42186239AA130636A7DBE112A3BC6E3B1D679294D7BD80D496933770C0B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |