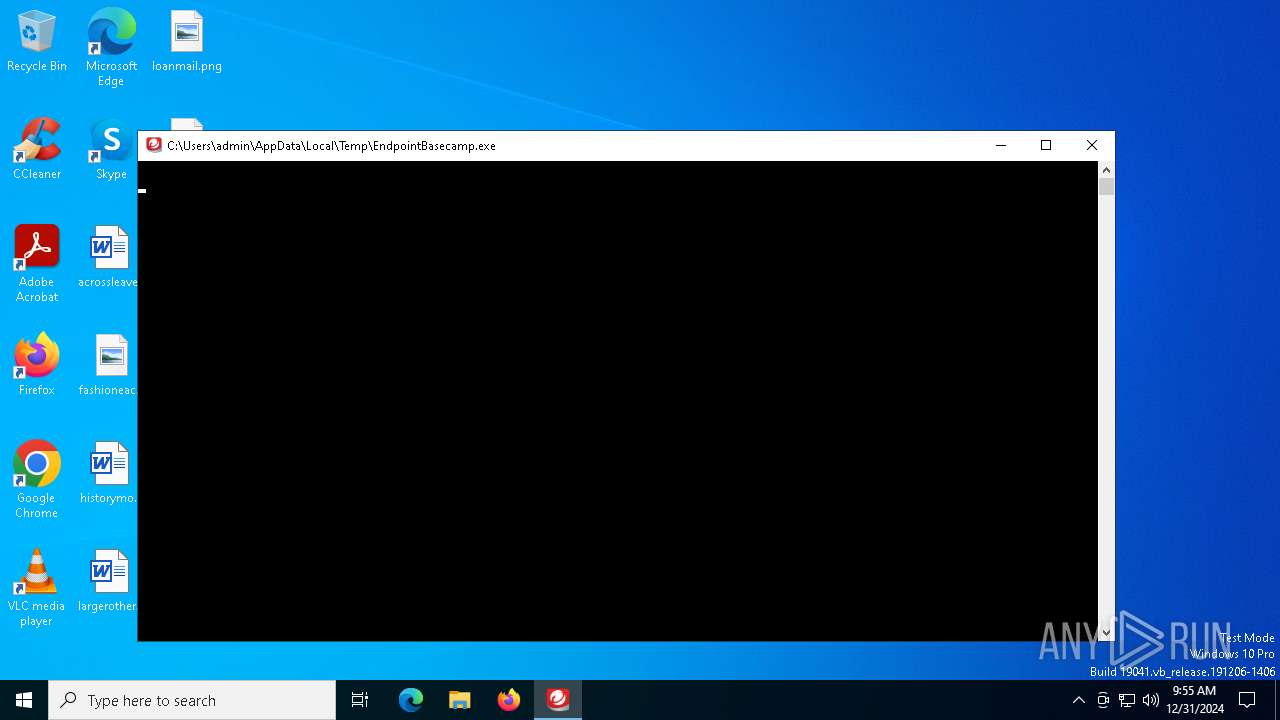
| File name: | EndpointBasecamp.exe |
| Full analysis: | https://app.any.run/tasks/69f72b21-4f38-4a2a-a1fa-0c37801b9618 |
| Verdict: | Malicious activity |
| Analysis date: | December 31, 2024, 09:55:40 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (console) Intel 80386, for MS Windows, 5 sections |
| MD5: | 76F41CBA65CF625DF1BCCE3F8AB5ED96 |
| SHA1: | BBD65C9DC67D164EAEEE1AB7C80B58323710F434 |
| SHA256: | A949D4AC7F1B4EEF9FC5F2E45CBBEC29D253BD2B189B1A9E41C4B13781D8C2D7 |
| SSDEEP: | 98304:1WRgsH2EMRFSpbBEYNEUEBYGgpvq9YsV4tdhQwaZ9n83TxmQNyw+Eiqb58:k8 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- EndpointBasecamp.exe (PID: 6288)
- EndpointBasecamp.exe (PID: 6404)
- VOMSvcWebInstaller.exe (PID: 6852)
- TelemetryAgentServiceWebInstaller.exe (PID: 7148)
- VOneModuleInstaller.exe (PID: 3172)
- WSCommunicator.exe (PID: 6948)
The process verifies whether the antivirus software is installed
- EndpointBasecamp.exe (PID: 6288)
- conhost.exe (PID: 6860)
- EndpointBasecamp.exe (PID: 6404)
- VOMSvcWebInstaller.exe (PID: 6852)
- EndpointBasecamp.exe (PID: 6928)
- TelemetryAgentServiceWebInstaller.exe (PID: 7148)
- conhost.exe (PID: 7160)
- EndpointBasecamp.exe (PID: 5588)
- EndpointBasecamp.exe (PID: 7048)
- EndpointBasecamp.exe (PID: 5036)
- VOneModuleInstaller.exe (PID: 3172)
- conhost.exe (PID: 7008)
- WSCommunicator.exe (PID: 6948)
- WSCommunicator.exe (PID: 6980)
- EndpointBasecamp.exe (PID: 6936)
- EndpointBasecampDebugger.exe (PID: 2612)
- conhost.exe (PID: 4400)
Executes as Windows Service
- EndpointBasecamp.exe (PID: 6404)
- WSCommunicator.exe (PID: 6980)
Checks Windows Trust Settings
- EndpointBasecamp.exe (PID: 6404)
- VOMSvcWebInstaller.exe (PID: 6852)
- EndpointBasecamp.exe (PID: 6928)
- EndpointBasecamp.exe (PID: 7048)
- EndpointBasecamp.exe (PID: 5588)
- TelemetryAgentServiceWebInstaller.exe (PID: 7148)
- VOneModuleInstaller.exe (PID: 3172)
- EndpointBasecamp.exe (PID: 5036)
- EndpointBasecamp.exe (PID: 6936)
- WSCommunicator.exe (PID: 6948)
- WSCommunicator.exe (PID: 6980)
- EndpointBasecampDebugger.exe (PID: 2612)
Drops a system driver (possible attempt to evade defenses)
- VOMSvcWebInstaller.exe (PID: 6852)
Application launched itself
- EndpointBasecamp.exe (PID: 6404)
The process checks if it is being run in the virtual environment
- EndpointBasecamp.exe (PID: 7048)
INFO
The sample compiled with english language support
- EndpointBasecamp.exe (PID: 6288)
- EndpointBasecamp.exe (PID: 6404)
- VOMSvcWebInstaller.exe (PID: 6852)
- TelemetryAgentServiceWebInstaller.exe (PID: 7148)
- WSCommunicator.exe (PID: 6948)
- VOneModuleInstaller.exe (PID: 3172)
Checks supported languages
- EndpointBasecamp.exe (PID: 6288)
- EndpointBasecamp.exe (PID: 6404)
- VOMSvcWebInstaller.exe (PID: 6852)
- EndpointBasecamp.exe (PID: 6928)
- EndpointBasecamp.exe (PID: 7048)
- EndpointBasecamp.exe (PID: 5588)
- VOneModuleInstaller.exe (PID: 3172)
- EndpointBasecamp.exe (PID: 5036)
- WSCommunicator.exe (PID: 6948)
- EndpointBasecamp.exe (PID: 6936)
- WSCommunicator.exe (PID: 6980)
- EndpointBasecampDebugger.exe (PID: 2612)
Creates files in the program directory
- EndpointBasecamp.exe (PID: 6288)
- VOMSvcWebInstaller.exe (PID: 6852)
- EndpointBasecamp.exe (PID: 7048)
- TelemetryAgentServiceWebInstaller.exe (PID: 7148)
- VOneModuleInstaller.exe (PID: 3172)
- WSCommunicator.exe (PID: 6948)
Reads the machine GUID from the registry
- EndpointBasecamp.exe (PID: 6288)
- EndpointBasecamp.exe (PID: 6404)
- VOMSvcWebInstaller.exe (PID: 6852)
- EndpointBasecamp.exe (PID: 6928)
- EndpointBasecamp.exe (PID: 7048)
- EndpointBasecamp.exe (PID: 5588)
- TelemetryAgentServiceWebInstaller.exe (PID: 7148)
- VOneModuleInstaller.exe (PID: 3172)
- EndpointBasecamp.exe (PID: 5036)
- WSCommunicator.exe (PID: 6948)
- EndpointBasecamp.exe (PID: 6936)
- EndpointBasecampDebugger.exe (PID: 2612)
- WSCommunicator.exe (PID: 6980)
Reads the software policy settings
- EndpointBasecamp.exe (PID: 6404)
- VOMSvcWebInstaller.exe (PID: 6852)
- EndpointBasecamp.exe (PID: 7048)
- EndpointBasecamp.exe (PID: 5588)
- VOneModuleInstaller.exe (PID: 3172)
- WSCommunicator.exe (PID: 6948)
- WSCommunicator.exe (PID: 6980)
- EndpointBasecampDebugger.exe (PID: 2612)
Reads the computer name
- VOMSvcWebInstaller.exe (PID: 6852)
- VOneModuleInstaller.exe (PID: 3172)
- WSCommunicator.exe (PID: 6948)
- EndpointBasecampDebugger.exe (PID: 2612)
Manual execution by a user
- Taskmgr.exe (PID: 6584)
- Taskmgr.exe (PID: 4300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:12:03 01:58:33+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.29 |
| CodeSize: | 3428352 |
| InitializedDataSize: | 1078784 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2b2f82 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.1.0.5015 |
| ProductVersionNumber: | 1.1.0.5015 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build, Special build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Trend Micro Endpoint Basecamp |
| FileVersion: | 1.1.0.5015 |
| ProductVersion: | 1.1 |
| ProductName: | Trend Micro Endpoint Basecamp |
| CompanyName: | Trend Micro Inc. |
| LegalCopyright: | Copyright (C) 2024 Trend Micro Incorporated. All rights reserved. |
| LegalTrademarks: | Copyright (C) Trend Micro Inc. |
| OriginalFileName: | EndpointBasecamp.exe |
Total processes
155
Monitored processes
26
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2612 | "C:\WINDOWS\temp\jc83SCfmOdp\ICL0ggMTfPN\EndpointBasecampDebugger.exe" /device_id 15c350c7-e9e2-47e2-99f3-ba477c551094 /collect_file "C:\Program Files (x86)\Trend Micro\Endpoint Basecamp\log\EndpointBasecamp.log" "XBC client" /collect_file "C:\windows\Temp\apo_preassess.log" "ES precheck" /collect_file "C:\windows\Temp\edr_indicator.log" "ES indicator" /collect_file "C:\Windows\Temp\ESE_Debug" "ES client" /collect_file "C:\windows\Temp\Cloud Endpoint" "MGCP client" /collect_file "C:\windows\Temp\TMER_Installer.log" "ER_Installer" | C:\Windows\Temp\jc83SCfmOdp\ICL0ggMTfPN\EndpointBasecampDebugger.exe | EndpointBasecamp.exe | ||||||||||||
User: SYSTEM Company: Trend Micro Inc. Integrity Level: SYSTEM Description: Trend Micro Endpoint Basecamp Debugger Exit code: 0 Version: 1.1.0.4643 Modules
| |||||||||||||||
| 3172 | C:\Windows\Temp\ROPQFoGt9mZ\nz8atYgpfnw\VOneModuleInstaller.exe --setup --dest="vom" --moduleId="ceta" --moduleDir="Ceta" --moduleDll="Ceta.dll" --pkg="C:\Windows\Temp\ROPQFoGt9mZ\nz8atYgpfnw\Telemetry Agent" | C:\Windows\Temp\ROPQFoGt9mZ\nz8atYgpfnw\VOneModuleInstaller.exe | TelemetryAgentServiceWebInstaller.exe | ||||||||||||
User: SYSTEM Company: Trend Micro Inc. Integrity Level: SYSTEM Description: Trend Micro Vision One Management Service Web Installer Exit code: 0 Version: 1.2.0.565 Modules
| |||||||||||||||
| 4144 | "C:\Users\admin\AppData\Local\Temp\EndpointBasecamp.exe" | C:\Users\admin\AppData\Local\Temp\EndpointBasecamp.exe | — | explorer.exe | |||||||||||
User: admin Company: Trend Micro Inc. Integrity Level: MEDIUM Description: Trend Micro Endpoint Basecamp Exit code: 3221226540 Version: 1.1.0.5015 Modules
| |||||||||||||||
| 4300 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4400 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | EndpointBasecampDebugger.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4604 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | EndpointBasecamp.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5036 | "C:\Program Files (x86)\Trend Micro\Endpoint Basecamp\EndpointBasecamp.exe" /xbc_auth_sdk dQEPfUpO4tG8E39pgit1 | C:\Program Files (x86)\Trend Micro\Endpoint Basecamp\EndpointBasecamp.exe | — | VOneModuleInstaller.exe | |||||||||||
User: SYSTEM Company: Trend Micro Inc. Integrity Level: SYSTEM Description: Trend Micro Endpoint Basecamp Exit code: 0 Version: 1.1.0.5015 Modules
| |||||||||||||||
| 5588 | "C:\Program Files (x86)\Trend Micro\Endpoint Basecamp\EndpointBasecamp.exe" /xbc_auth_sdk 75JNO0BPXPnYXhR20k6L | C:\Program Files (x86)\Trend Micro\Endpoint Basecamp\EndpointBasecamp.exe | — | TelemetryAgentServiceWebInstaller.exe | |||||||||||
User: SYSTEM Company: Trend Micro Inc. Integrity Level: SYSTEM Description: Trend Micro Endpoint Basecamp Exit code: 0 Version: 1.1.0.5015 Modules
| |||||||||||||||
| 6288 | "C:\Users\admin\AppData\Local\Temp\EndpointBasecamp.exe" | C:\Users\admin\AppData\Local\Temp\EndpointBasecamp.exe | explorer.exe | ||||||||||||
User: admin Company: Trend Micro Inc. Integrity Level: HIGH Description: Trend Micro Endpoint Basecamp Exit code: 0 Version: 1.1.0.5015 Modules
| |||||||||||||||
| 6316 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | EndpointBasecamp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
73 673
Read events
73 568
Write events
96
Delete events
9
Modification events
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\TMSecurityService |
| Operation: | write | Name: | runtime_stage |
Value: 0 | |||
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\TMSecurityService |
| Operation: | write | Name: | device_id |
Value: 15c350c7-e9e2-47e2-99f3-ba477c551094 | |||
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\TMSecurityService |
| Operation: | write | Name: | proxy_server |
Value: | |||
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\TMSecurityService |
| Operation: | write | Name: | proxy_bypass |
Value: | |||
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\TMSecurityService |
| Operation: | write | Name: | proxy_source |
Value: 6 | |||
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\TMSecurityService |
| Operation: | write | Name: | runtime_proxy_source |
Value: 0 | |||
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\TMSecurityService |
| Operation: | write | Name: | sg_proxy_source |
Value: 0 | |||
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\SecurityKeys |
| Operation: | write | Name: | proxy_username |
Value: FepjXg== | |||
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\SecurityKeys |
| Operation: | write | Name: | proxy_password |
Value: MornBg== | |||
| (PID) Process: | (6288) EndpointBasecamp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\TrendMicro\TMSecurityService |
| Operation: | write | Name: | gcs_server |
Value: | |||
Executable files
35
Suspicious files
26
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6852 | VOMSvcWebInstaller.exe | C:\Windows\Temp\1DLCvwqR6ZX\dMWyKNURVLt\vom\modules\CeBridgeProxyModule\CeBridgeProxyModule.dll | executable | |
MD5:C14F3D5062472FC0578443B282FC0B06 | SHA256:590D8D707165C0C55E108B3155CAD4B32452E2F8710210D3DBFD63BEEB9BA72C | |||
| 6404 | EndpointBasecamp.exe | C:\Windows\Temp\1DLCvwqR6ZX\dMWyKNURVLt\VOMSvcWebInstaller.exe | executable | |
MD5:CA39FE0B2BEFB2CEBA0D13AF4540979F | SHA256:E671D985F6160CED8C424A95B4C9E03EE8721FA1920AC2C0993EAAB6BED2CF6D | |||
| 6288 | EndpointBasecamp.exe | C:\Program Files (x86)\Trend Micro\Endpoint Basecamp\EndpointBasecamp.exe | executable | |
MD5:76F41CBA65CF625DF1BCCE3F8AB5ED96 | SHA256:A949D4AC7F1B4EEF9FC5F2E45CBBEC29D253BD2B189B1A9E41C4B13781D8C2D7 | |||
| 6404 | EndpointBasecamp.exe | C:\Windows\Temp\1DLCvwqR6ZX\USeTe17anpe.zip | compressed | |
MD5:079F6C0FE340209BD19A3DCD89ACCC5E | SHA256:73D4F99B226C3D7FDF92E016AED5631EFA7AD2B0B8BFDE27E150F1F1F8927E07 | |||
| 6852 | VOMSvcWebInstaller.exe | C:\Windows\Temp\1DLCvwqR6ZX\dMWyKNURVLt\vom\PackageCheck.cat | cat | |
MD5:23CAD2C04314E773E3E96E6998BAB7C1 | SHA256:366B5F5EE010ED5A9835B7C1439EDCC6B75BA0D9DFCA71C400964D013E7F5C58 | |||
| 6852 | VOMSvcWebInstaller.exe | C:\Windows\Temp\1DLCvwqR6ZX\dMWyKNURVLt\vom\VOM.dll | executable | |
MD5:59CC56B78F03195727337C74FEF33ACB | SHA256:D8BB0AB62179081FD5604D35EA82021097F4D31CCDA6823852611D1FEB92B1F1 | |||
| 6852 | VOMSvcWebInstaller.exe | C:\Windows\Temp\1DLCvwqR6ZX\dMWyKNURVLt\VOMSvc.zip | compressed | |
MD5:CEEE8EDB378A89C227C0A4CD9395C91D | SHA256:E46B37C6174C8C375EDDC959E3C383099B4159ECF6B04F231BCD0434C51293A4 | |||
| 6288 | EndpointBasecamp.exe | C:\Program Files (x86)\Trend Micro\Endpoint Basecamp\log\EndpointBasecamp.log | text | |
MD5:EB18F3FC57081ED9968135FE31B7A338 | SHA256:0A9E6582C3DFC65BA096EDEA05294F2C4A8412A132B5A1747C2E4D2D40BE6119 | |||
| 6852 | VOMSvcWebInstaller.exe | C:\Windows\Temp\1DLCvwqR6ZX\dMWyKNURVLt\vom\VOMSvc.cfg | binary | |
MD5:CD32DDF03CAFFD9F0C6419226ADB76B0 | SHA256:0B6E0BD297CCCE7577BAC8ED1D90F390E14C0ECF063BD312276A2C6B07472258 | |||
| 6852 | VOMSvcWebInstaller.exe | C:\Windows\Temp\1DLCvwqR6ZX\dMWyKNURVLt\vom\dllXbcSdk.dll | executable | |
MD5:6F4F857F82598671CF40469E01ADB2D5 | SHA256:E33317340FF28D16DD6B6582E42ABBA84B9768CB745DF8039D543F2318A623A5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
60
DNS requests
25
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.32.238.107:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m02.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRmbQtwnInkvkvr7BNFR%2BS2lTYPjAQUwDFSzVpQw4J8dHHOy%2Bmc%2BXrrguICEAq4j16W4SPpkH6HDeODfNA%3D | unknown | — | — | whitelisted |
5576 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5576 | SIHClient.exe | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.38.73.129:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
760 | lsass.exe | GET | 200 | 18.245.38.41:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkpLy9ROx7U76vGUhC06D6E%3D | unknown | — | — | unknown |
6216 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2356 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.32.238.107:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.38.73.129:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.19.80.27:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
6288 | EndpointBasecamp.exe | 18.185.221.143:443 | api-eu1.xbc.trendmicro.com | AMAZON-02 | DE | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
api-eu1.xbc.trendmicro.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
release-us1.mgcp.trendmicro.com |
| whitelisted |