| URL: | https://invitrofiles.ru/download/9b522eba711f/ |
| Full analysis: | https://app.any.run/tasks/261ce420-6168-4439-b3e6-1e1058f4b086 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2022, 08:10:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B7385DEA36B6CE6F6463CEDDE9B641D5 |
| SHA1: | DDF675CBD1C186102960F85C21F10DB2A1FB8746 |
| SHA256: | A941B6CC32A5B599D67493D45B284BFF70BC5B7753642E1AF70B0366B1A085D6 |
| SSDEEP: | 3:N8OeykLJkcwXXnSUBn:2OUfwHSsn |
MALICIOUS
Loads dropped or rewritten executable
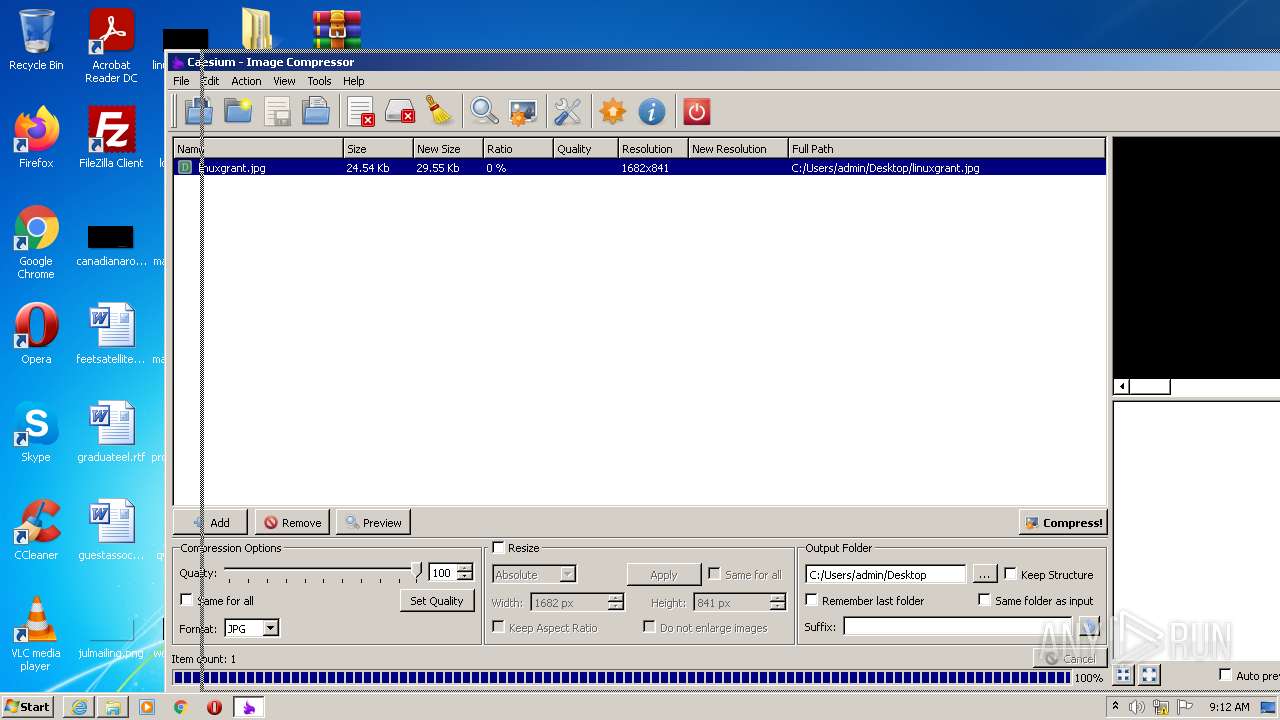
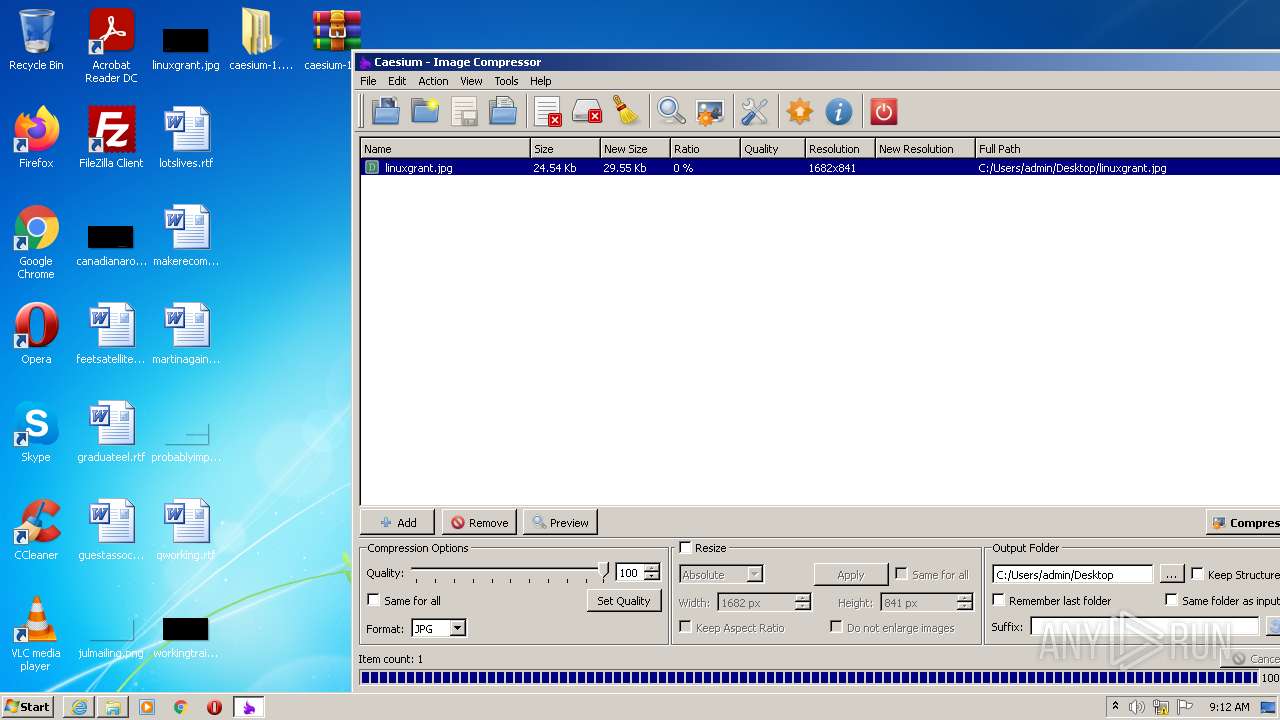
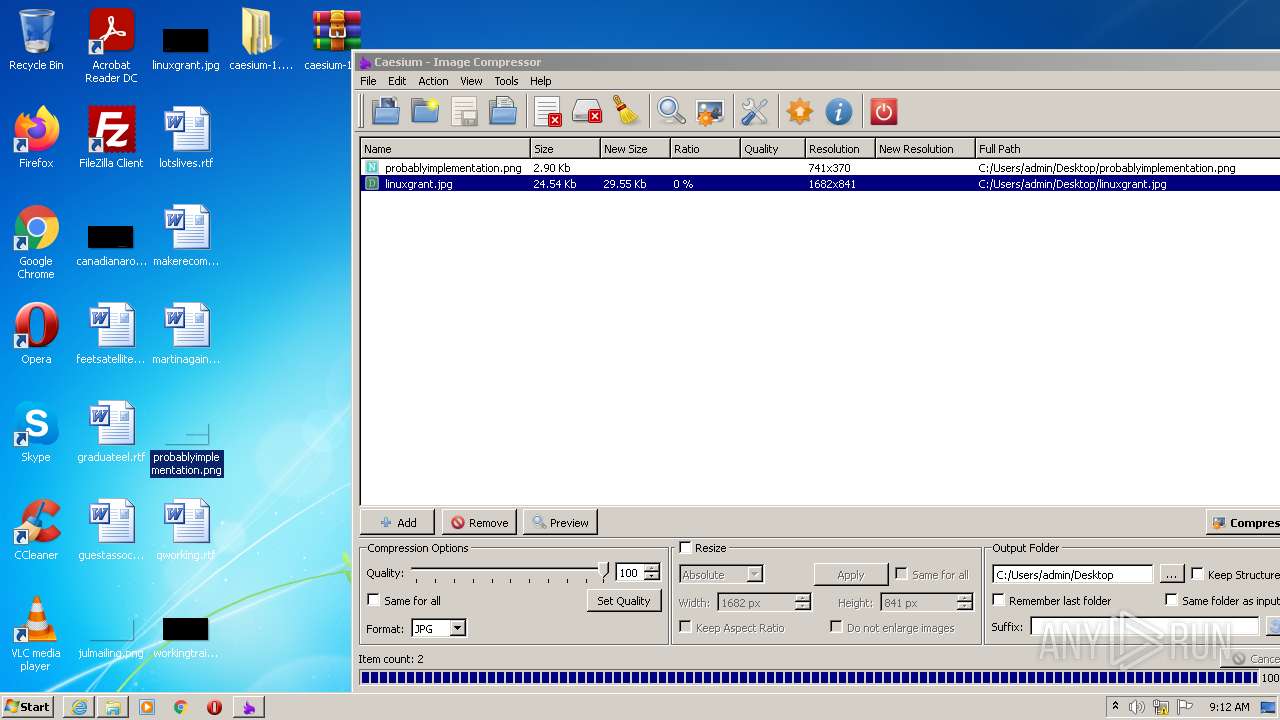
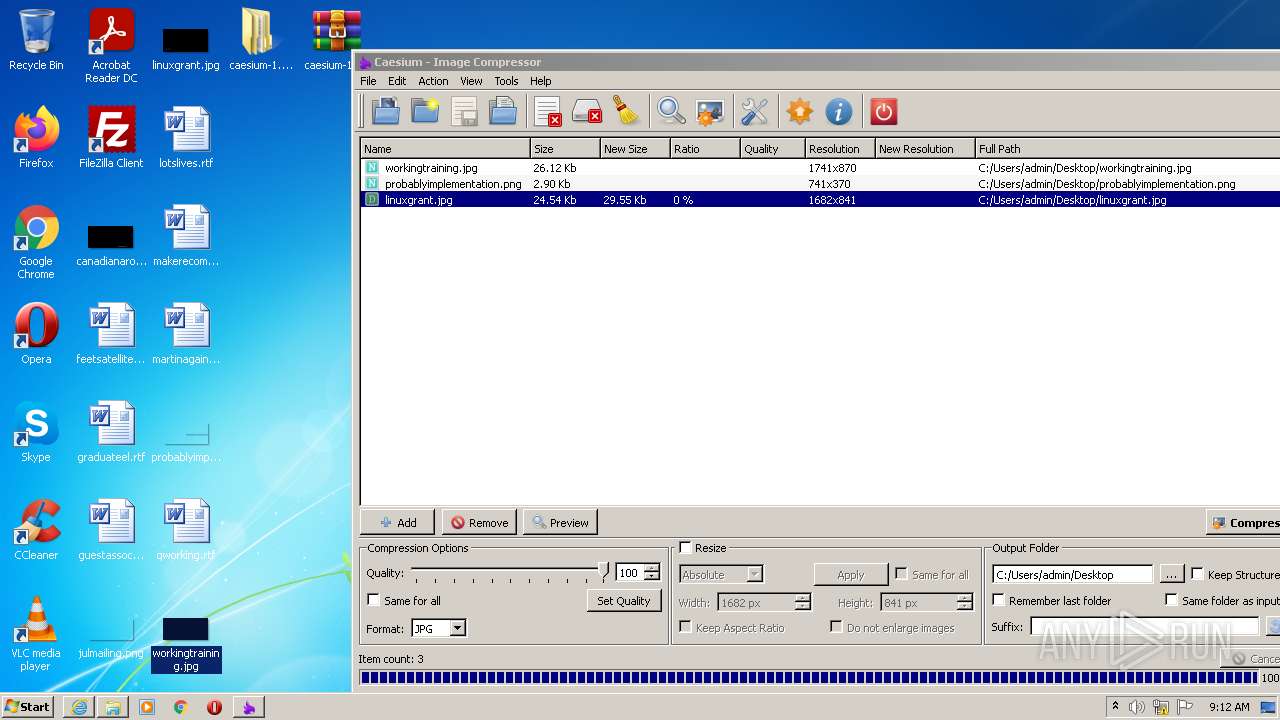
- exif_copy.exe (PID: 2924)
- SearchProtocolHost.exe (PID: 3548)
- Caesium.exe (PID: 4028)
- exif_copy.exe (PID: 1572)
- exif_copy.exe (PID: 1816)
- exif_copy.exe (PID: 1380)
- exif_copy.exe (PID: 3156)
- exif_copy.exe (PID: 2268)
- exif_copy.exe (PID: 2204)
Drops executable file immediately after starts
- WinRAR.exe (PID: 1788)
Application was dropped or rewritten from another process
- Caesium.exe (PID: 4028)
- exif_copy.exe (PID: 1572)
- exif_copy.exe (PID: 2924)
- exif_copy.exe (PID: 1816)
- exif_copy.exe (PID: 1380)
- exif_copy.exe (PID: 2204)
- exif_copy.exe (PID: 3156)
- exif_copy.exe (PID: 2268)
Renames files like Ransomware
- Caesium.exe (PID: 4028)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 888)
Reads the computer name
- WinRAR.exe (PID: 1788)
- Caesium.exe (PID: 4028)
Checks supported languages
- WinRAR.exe (PID: 1788)
- Caesium.exe (PID: 4028)
- exif_copy.exe (PID: 1572)
- exif_copy.exe (PID: 2924)
- exif_copy.exe (PID: 1816)
- exif_copy.exe (PID: 1380)
- exif_copy.exe (PID: 2268)
- exif_copy.exe (PID: 3156)
- exif_copy.exe (PID: 2204)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1788)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1788)
Loads Python modules
- SearchProtocolHost.exe (PID: 3548)
- exif_copy.exe (PID: 1572)
- exif_copy.exe (PID: 2924)
- exif_copy.exe (PID: 1380)
- exif_copy.exe (PID: 2204)
- exif_copy.exe (PID: 3156)
- exif_copy.exe (PID: 1816)
- exif_copy.exe (PID: 2268)
Reads default file associations for system extensions
- Caesium.exe (PID: 4028)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2940)
Checks supported languages
- iexplore.exe (PID: 888)
- iexplore.exe (PID: 2940)
Application launched itself
- iexplore.exe (PID: 2940)
Reads the computer name
- iexplore.exe (PID: 2940)
- iexplore.exe (PID: 888)
Reads settings of System Certificates
- iexplore.exe (PID: 888)
- iexplore.exe (PID: 2940)
Checks Windows Trust Settings
- iexplore.exe (PID: 888)
- iexplore.exe (PID: 2940)
Changes settings of System certificates
- iexplore.exe (PID: 2940)
Reads internet explorer settings
- iexplore.exe (PID: 888)
Creates files in the user directory
- iexplore.exe (PID: 888)
- iexplore.exe (PID: 2940)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2940)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2940)
Manual execution by user
- WinRAR.exe (PID: 1788)
- Caesium.exe (PID: 4028)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
60
Monitored processes
12
Malicious processes
4
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2940 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1380 | tools\exif_copy.exe "C:/Users/admin/Desktop/probablyimplementation.png" "C:/Users/admin/Desktop\probablyimplementation" | C:\Users\admin\Desktop\caesium-1.7.0-port\Caesium Portable\tools\exif_copy.exe | — | Caesium.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1572 | tools\exif_copy.exe "C:/Users/admin/Desktop/linuxgrant.jpg" "C:/Users/admin/Desktop\linuxgrant" | C:\Users\admin\Desktop\caesium-1.7.0-port\Caesium Portable\tools\exif_copy.exe | — | Caesium.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1788 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\caesium-1.7.0-port.zip" C:\Users\admin\Desktop\caesium-1.7.0-port\ | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1816 | tools\exif_copy.exe "C:/Users/admin/Desktop/workingtraining.jpg" "C:/Users/admin/Desktop\workingtraining" | C:\Users\admin\Desktop\caesium-1.7.0-port\Caesium Portable\tools\exif_copy.exe | — | Caesium.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2204 | tools\exif_copy.exe "C:/Users/admin/Desktop/linuxgrant.jpg" "C:/Users/admin/Desktop\linuxgrant" | C:\Users\admin\Desktop\caesium-1.7.0-port\Caesium Portable\tools\exif_copy.exe | — | Caesium.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2268 | tools\exif_copy.exe "C:/Users/admin/Desktop/linuxgrant.jpg" "C:/Users/admin/AppData/Local/Temp/_caesium_/linuxgrant.jpg.cae" | C:\Users\admin\Desktop\caesium-1.7.0-port\Caesium Portable\tools\exif_copy.exe | — | Caesium.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2924 | tools\exif_copy.exe "C:/Users/admin/Desktop/linuxgrant.jpg" "C:/Users/admin/Desktop\linuxgrant" | C:\Users\admin\Desktop\caesium-1.7.0-port\Caesium Portable\tools\exif_copy.exe | — | Caesium.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2940 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://invitrofiles.ru/download/9b522eba711f/" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3156 | tools\exif_copy.exe "C:/Users/admin/Desktop/probablyimplementation.png" "C:/Users/admin/AppData/Local/Temp/_caesium_/probablyimplementation.png.cae" | C:\Users\admin\Desktop\caesium-1.7.0-port\Caesium Portable\tools\exif_copy.exe | — | Caesium.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
Total events
16 791
Read events
16 543
Write events
241
Delete events
7
Modification events
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30955643 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30955643 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2940) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
23
Suspicious files
19
Text files
49
Unknown types
24
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | der | |
MD5:— | SHA256:— | |||
| 888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:— | SHA256:— | |||
| 888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:— | SHA256:— | |||
| 888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\9b522eba711f[1].htm | html | |
MD5:— | SHA256:— | |||
| 888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\upload[1].css | text | |
MD5:— | SHA256:— | |||
| 888 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\FMFKRQIH.txt | text | |
MD5:— | SHA256:— | |||
| 888 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\OAC2BJ7U.txt | text | |
MD5:— | SHA256:— | |||
| 888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\72BA427A91F50409B9EAC87F2B59B951_BBE8A1F6C220CAA841FB9F1F6DC51B5E | binary | |
MD5:— | SHA256:— | |||
| 888 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\common[1].css | text | |
MD5:— | SHA256:— | |||
| 888 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
39
DNS requests
20
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
888 | iexplore.exe | GET | 200 | 23.36.162.83:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTYOkzrrCGQj08njZXbUQQpkoUmuQQUCHbNywf%2FJPbFze27kLzihDdGdfcCEQDkBUeDDgxkUpdvejVJwN1I | NL | der | 1.54 Kb | whitelisted |
888 | iexplore.exe | GET | 200 | 5.45.205.245:80 | http://yandex.ocsp-responder.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBStniMGfahyWUWDEeSLUFbNR9JLAgQUN1zjGeCyjqGoTtLPq9Dc4wtcNU0CEGlTKIPuh018TJJ9M3J8QXw%3D | RU | der | 1.48 Kb | whitelisted |
2940 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
4028 | Caesium.exe | GET | 200 | 204.68.111.100:80 | http://caesium.sourceforge.net/changelog.txt | US | text | 1.95 Kb | malicious |
888 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQh80WaEMqmyEvaHjlisSfVM4p8SAQUF9nWJSdn%2BTHCSUPZMDZEjGypT%2BsCEQCP672dkbDSfheYsuexULqh | US | der | 472 b | whitelisted |
888 | iexplore.exe | GET | 200 | 23.36.162.83:80 | http://subca.ocsp-certum.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBR5iK7tYk9tqQEoeQhZNkKcAol9bgQUjEPEy22YwaechGnr30oNYJY6w%2FsCEQCTkoVAAWVxX5R%2FKI%2FvyZso | NL | der | 1.50 Kb | whitelisted |
2940 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | US | der | 471 b | whitelisted |
4028 | Caesium.exe | GET | 200 | 204.68.111.100:80 | http://caesium.sourceforge.net/current_version.txt | US | text | 3 b | malicious |
888 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | US | der | 727 b | whitelisted |
888 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
888 | iexplore.exe | 91.217.227.152:443 | invitrofiles.ru | Nezavisimaya laboratoriya INVITRO Ltd | RU | unknown |
888 | iexplore.exe | 172.64.155.188:80 | ocsp.comodoca.com | — | US | suspicious |
888 | iexplore.exe | 95.140.236.128:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | GB | malicious |
888 | iexplore.exe | 87.250.251.119:443 | mc.yandex.ru | YANDEX LLC | RU | whitelisted |
2940 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
888 | iexplore.exe | 5.45.205.245:80 | yandex.ocsp-responder.com | YANDEX LLC | RU | whitelisted |
2940 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
888 | iexplore.exe | 23.36.162.83:80 | subca.ocsp-certum.com | CW Vodafone Group PLC | NL | suspicious |
2940 | iexplore.exe | 91.217.227.152:443 | invitrofiles.ru | Nezavisimaya laboratoriya INVITRO Ltd | RU | unknown |
2940 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
invitrofiles.ru |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
mc.yandex.ru |
| whitelisted |
subca.ocsp-certum.com |
| whitelisted |
yandex.ocsp-responder.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4028 | Caesium.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
4028 | Caesium.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
4028 | Caesium.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3 ETPRO signatures available at the full report
Process | Message |
|---|---|
Caesium.exe | QPixmap::scaled: Pixmap is a null pixmap
|
Caesium.exe | selectNameFilter: Invalid parameter 'Directories' not found in 'All Files (*)'.
|
Caesium.exe | QPixmap::scaled: Pixmap is a null pixmap
|
Caesium.exe | QObject::connect: Cannot queue arguments of type 'QVector<int>'
(Make sure 'QVector<int>' is registered using qRegisterMetaType().)
|
Caesium.exe | QObject::connect: Cannot queue arguments of type 'QVector<int>'
(Make sure 'QVector<int>' is registered using qRegisterMetaType().)
|
Caesium.exe | QObject::connect: Cannot queue arguments of type 'QVector<int>'
(Make sure 'QVector<int>' is registered using qRegisterMetaType().)
|
Caesium.exe | QObject::connect: Cannot queue arguments of type 'QVector<int>'
(Make sure 'QVector<int>' is registered using qRegisterMetaType().)
|
Caesium.exe | QObject: Cannot create children for a parent that is in a different thread.
(Parent is Caesium(0x22fdfc), parent's thread is QThread(0x548f90), current thread is QThread(0x4021c70)
|
Caesium.exe | QPixmap::scaled: Pixmap is a null pixmap
|
Caesium.exe | QPixmap::scaled: Pixmap is a null pixmap
|