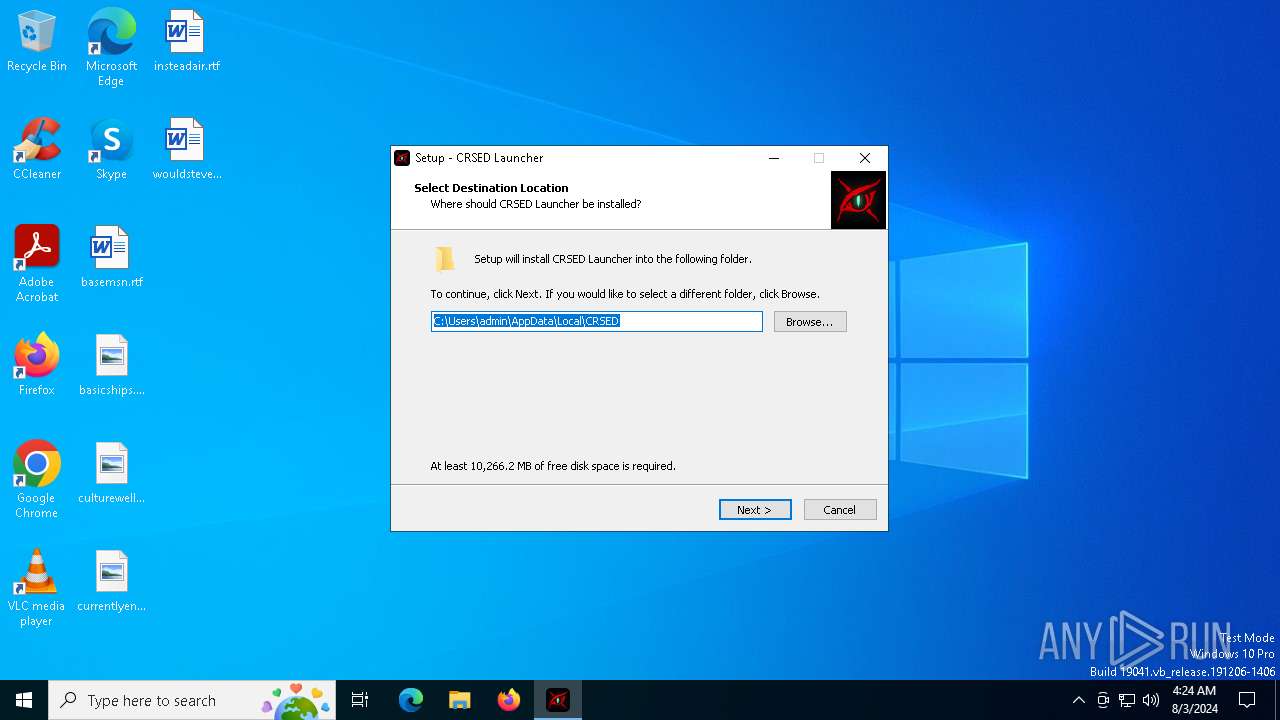
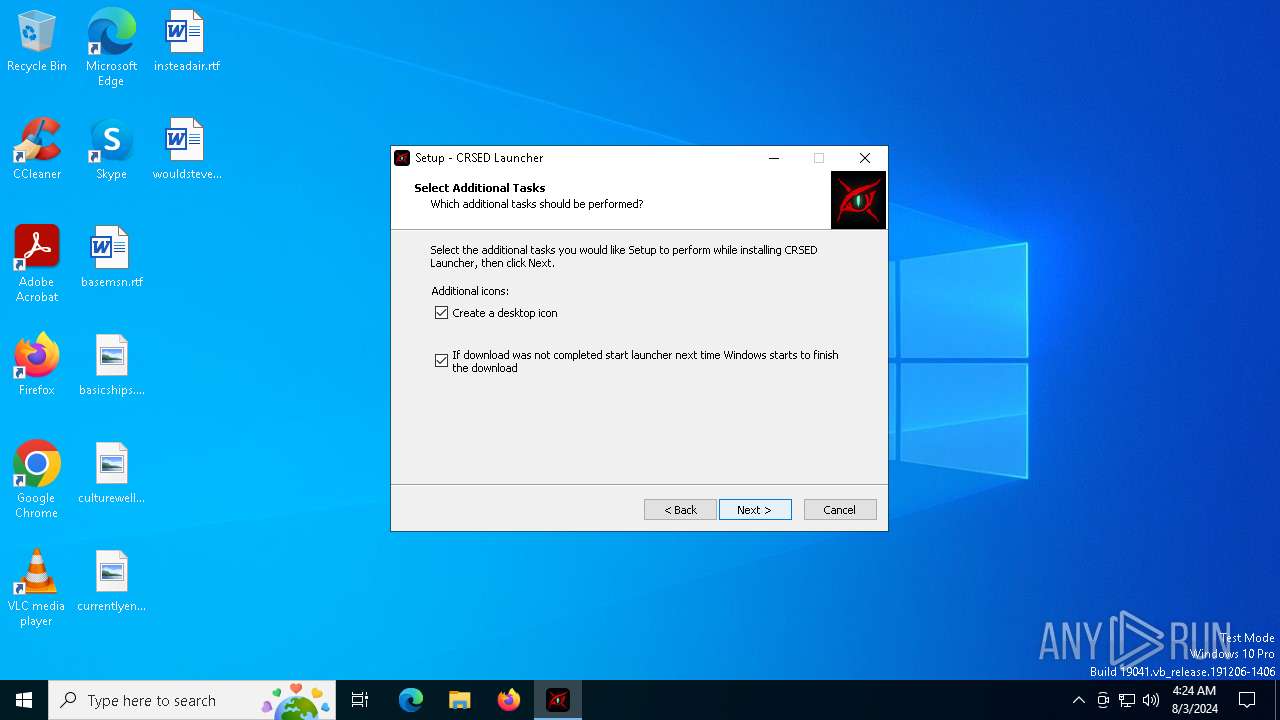
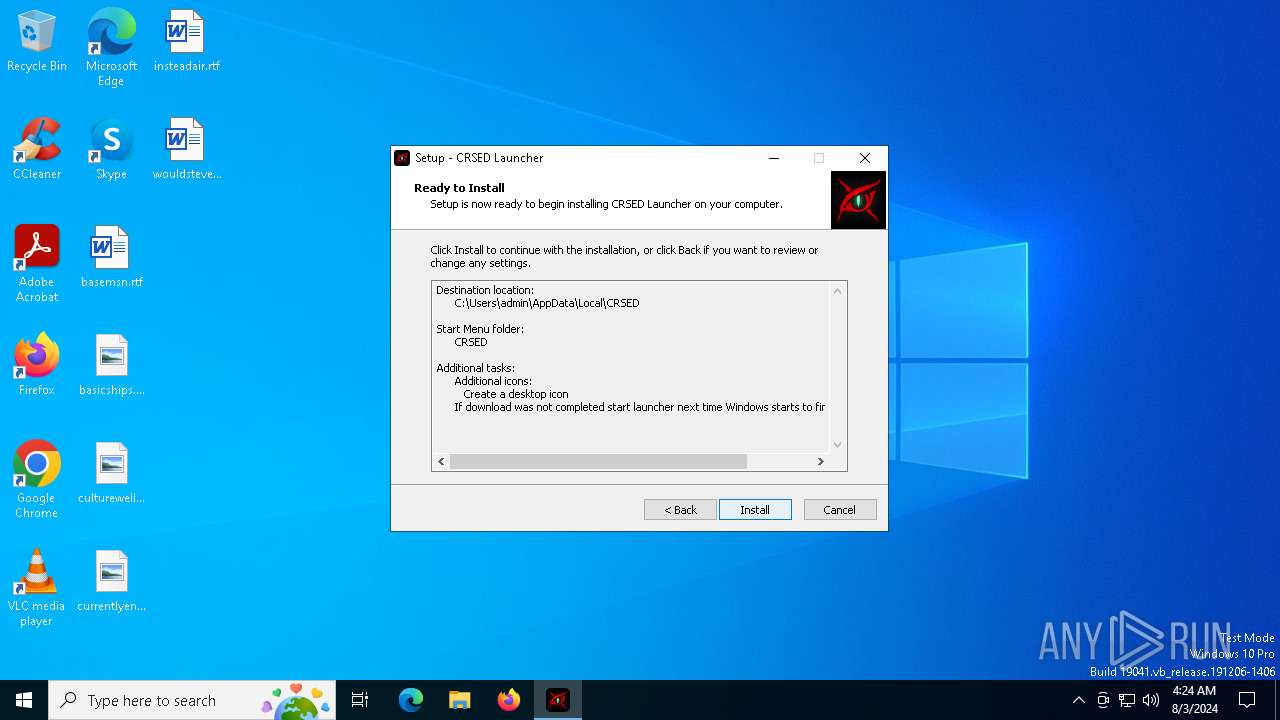
| File name: | cr_launcher_1.0.3.139-an3bou6y2.exe |
| Full analysis: | https://app.any.run/tasks/8579438c-b749-4e9b-aaa2-db9386bdcc49 |
| Verdict: | Malicious activity |
| Analysis date: | August 03, 2024, 04:24:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 1A35B02AE4CF92848D3B69E76A59D0CB |
| SHA1: | EF2F5B09EAF78FD6C09FD2E203461EE00DCB4ADE |
| SHA256: | A9412D2B1FF2A07936C2EB903331C19590B8412994B69AB539CF1BB132574B80 |
| SSDEEP: | 98304:Dg6mNuZNNGNNNNNN/dAGpNRy7jIyGMSgH13AiHtPNZ5xRpdsuOIYKvSzAyv9Atdl:3WqWCxLhnkPN0 |
MALICIOUS
Drops the executable file immediately after the start
- cr_launcher_1.0.3.139-an3bou6y2.exe (PID: 6728)
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
- launcher.exe (PID: 7128)
Changes the autorun value in the registry
- gjagent.exe (PID: 6396)
SUSPICIOUS
Reads the Windows owner or organization settings
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
Executable content was dropped or overwritten
- cr_launcher_1.0.3.139-an3bou6y2.exe (PID: 6728)
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
- launcher.exe (PID: 7128)
Process drops legitimate windows executable
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
Creates file in the systems drive root
- launcher.exe (PID: 7128)
- gaijin_downloader.exe (PID: 1860)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
Reads security settings of Internet Explorer
- launcher.exe (PID: 7128)
Reads the date of Windows installation
- launcher.exe (PID: 7128)
There is functionality for sendig ICMP (YARA)
- launcher.exe (PID: 7128)
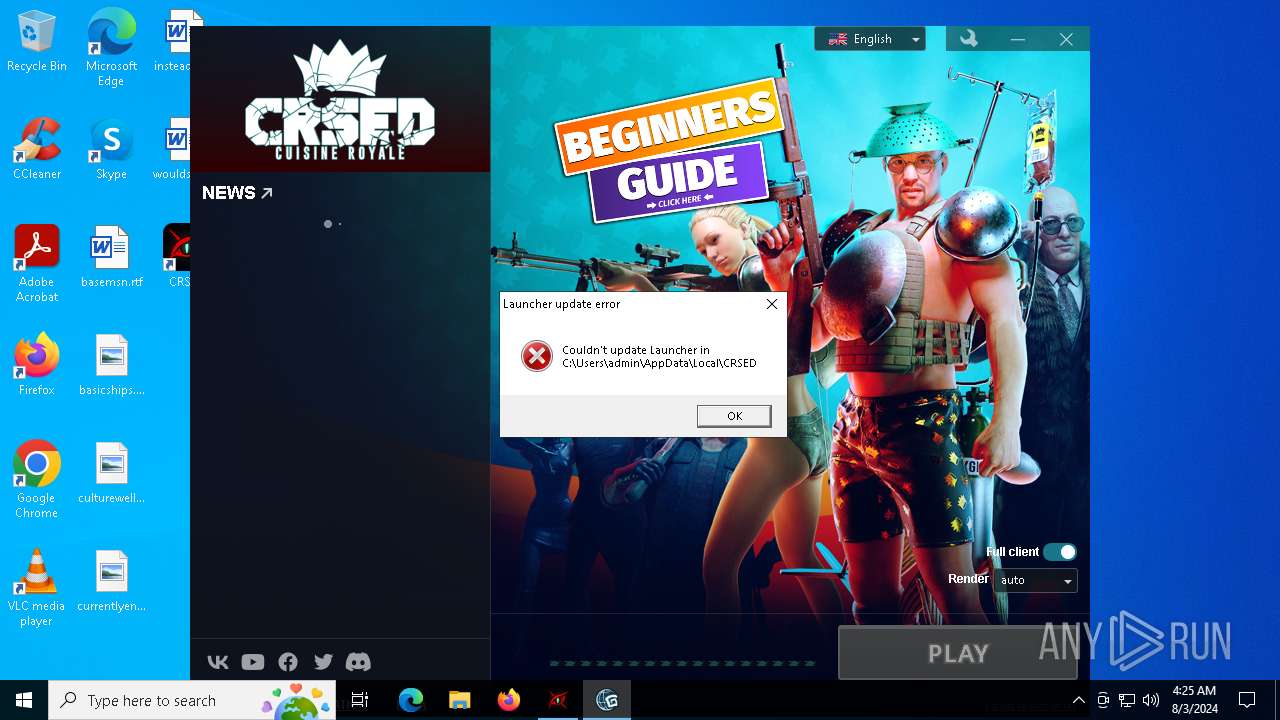
Executes application which crashes
- gaijin_downloader.exe (PID: 1860)
INFO
Create files in a temporary directory
- cr_launcher_1.0.3.139-an3bou6y2.exe (PID: 6728)
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
Checks supported languages
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
- cr_launcher_1.0.3.139-an3bou6y2.exe (PID: 6728)
- launcher.exe (PID: 7128)
- gaijin_downloader.exe (PID: 1860)
- gjagent.exe (PID: 6396)
Reads the computer name
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
- launcher.exe (PID: 7128)
- gaijin_downloader.exe (PID: 1860)
- gjagent.exe (PID: 6396)
Creates a software uninstall entry
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
Creates files or folders in the user directory
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
- launcher.exe (PID: 7128)
- gaijin_downloader.exe (PID: 1860)
- gjagent.exe (PID: 6396)
- WerFault.exe (PID: 2876)
Reads the machine GUID from the registry
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
- launcher.exe (PID: 7128)
- gaijin_downloader.exe (PID: 1860)
- gjagent.exe (PID: 6396)
Reads the software policy settings
- cr_launcher_1.0.3.139-an3bou6y2.tmp (PID: 6756)
- WerFault.exe (PID: 2876)
Creates files in the program directory
- launcher.exe (PID: 7128)
Process checks computer location settings
- launcher.exe (PID: 7128)
Checks proxy server information
- WerFault.exe (PID: 2876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (57.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (18.2) |
| .exe | | | Win16/32 Executable Delphi generic (8.3) |
| .exe | | | Generic Win/DOS Executable (8) |
| .exe | | | DOS Executable Generic (8) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:06 14:39:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 66560 |
| InitializedDataSize: | 249344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x117dc |
| OSVersion: | 5 |
| ImageVersion: | 6 |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Gaijin Network |
| FileDescription: | CRSED Launcher Setup |
| FileVersion: | |
| LegalCopyright: | 2014-2023 Gaijin Games KFT |
| ProductName: | CRSED Launcher |
| ProductVersion: |
Total processes
173
Monitored processes
54
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1044 | "C:\WINDOWS\system32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\Gaijin\Program Files (x86)\NetAgent\gjagent.exe" "Gaijin.Net Updater" ENABLE ALL | C:\Windows\SysWOW64\netsh.exe | — | cr_launcher_1.0.3.139-an3bou6y2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1860 | "C:\WINDOWS\system32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\CRSED\AFR-FriendlyD3D.exe" "CRSED Game Client for CrossFire\SLI" ENABLE ALL | C:\Windows\SysWOW64\netsh.exe | — | cr_launcher_1.0.3.139-an3bou6y2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1860 | "C:\Users\admin\AppData\Local\CRSED\gaijin_downloader.exe" -appid CuisineRoyaleLauncherZip -localversion 1.0.3.139 -execpath launcher.exe -notify_user_about_failure -conditional_gui_app_restart | C:\Users\admin\AppData\Local\CRSED\gaijin_downloader.exe | launcher.exe | ||||||||||||
User: admin Company: Gaijin Integrity Level: MEDIUM Description: Gaijin Downloader Exit code: 3221225477 Modules
| |||||||||||||||
| 2212 | "C:\WINDOWS\system32\netsh.exe" firewall add allowedprogram "C:\Users\admin\AppData\Local\CRSED\ForceSingleGPU.exe" "CRSED Game Client for disabled CrossFire\SLI" ENABLE ALL | C:\Windows\SysWOW64\netsh.exe | — | cr_launcher_1.0.3.139-an3bou6y2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2248 | "C:\WINDOWS\system32\netsh" firewall add portopening protocol = UDP port = 3478-3480 name = "CRSED" | C:\Windows\SysWOW64\netsh.exe | — | cr_launcher_1.0.3.139-an3bou6y2.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2636 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
39 020
Read events
38 975
Write events
39
Delete events
6
Modification events
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 641A00008DD0B9045DE5DA01 | |||
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 76195F6FB2219EE1882430AFE862C4EA6E27422263D4B58C9DB50ECB3346747F | |||
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\CRSED\launcher.exe | |||
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 8294731517125AC47A81E81CFAC3661514EC9FB87930B59CAD35C84F3385182B | |||
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\CuisineRoyale |
| Operation: | write | Name: | StartupWithWindows |
Value: Yes | |||
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\CuisineRoyale |
| Operation: | write | Name: | InstallDir |
Value: C:\Users\admin\AppData\Local\CRSED | |||
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\CuisineRoyale |
| Operation: | write | Name: | InstallPath |
Value: C:\Users\admin\AppData\Local\CRSED | |||
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\CuisineRoyale |
| Operation: | write | Name: | Dir |
Value: C:\Users\admin\AppData\Local\CRSED | |||
| (PID) Process: | (6756) cr_launcher_1.0.3.139-an3bou6y2.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Gaijin\CuisineRoyale |
| Operation: | write | Name: | Path |
Value: C:\Users\admin\AppData\Local\CRSED\launcher.exe | |||
Executable files
18
Suspicious files
10
Text files
12
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | C:\Users\admin\AppData\Local\CRSED\is-OMMQ8.tmp | executable | |
MD5:07218CCD6173A247B7EE6A93EF6021BE | SHA256:7F4DF5A2DDEFFBC6037F9C4123D426462B3B3F3B2E202343A97EE23EC0E2F78B | |||
| 6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | C:\Users\admin\AppData\Local\Temp\is-VSBUI.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | C:\Users\admin\AppData\Local\CRSED\sciter.dll | executable | |
MD5:58115B095C523466950E2F745B70B867 | SHA256:41CF304562A6240AF02157B17800C0EC01154626258A809D665AADD59E7276CA | |||
| 6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | C:\Users\admin\AppData\Local\CRSED\is-7SH89.tmp | executable | |
MD5:ADC796431F36632ED86663E8BCAFDDB8 | SHA256:699783D9218C730A4334532DD0ADC6FA9D6E22395E96274B20CDB32EFEA6EDBA | |||
| 6728 | cr_launcher_1.0.3.139-an3bou6y2.exe | C:\Users\admin\AppData\Local\Temp\is-IT3DL.tmp\cr_launcher_1.0.3.139-an3bou6y2.tmp | executable | |
MD5:07218CCD6173A247B7EE6A93EF6021BE | SHA256:7F4DF5A2DDEFFBC6037F9C4123D426462B3B3F3B2E202343A97EE23EC0E2F78B | |||
| 6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | C:\Users\admin\AppData\Local\CRSED\gjagent.exe | executable | |
MD5:65F9CBA4FB02014A13685D8358CB0E67 | SHA256:2ED5BFDA0B759B4CD795514C0F1FFBDBD0DF40A82EA4FD50044BDFD8AD25CE37 | |||
| 6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | C:\Users\admin\AppData\Local\CRSED\launcherr.dat | compressed | |
MD5:D4ACE8CD21448E463A1A9867A04C1090 | SHA256:7F657D2DA1B0DD686E6D54776B03EF98A123C0A1F7F3BC03B69400D8D141DC16 | |||
| 6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | C:\Users\admin\AppData\Local\CRSED\is-19I43.tmp | text | |
MD5:1E32496378E8FEE43CB01B0689963A67 | SHA256:5B47AEE36F594B7737E00990C9922A87252729B74CC2F1A83C0FCEED9816BDB9 | |||
| 6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | C:\Users\admin\AppData\Local\CRSED\gaijin_downloader.exe | executable | |
MD5:ADC796431F36632ED86663E8BCAFDDB8 | SHA256:699783D9218C730A4334532DD0ADC6FA9D6E22395E96274B20CDB32EFEA6EDBA | |||
| 6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | C:\Users\admin\AppData\Local\CRSED\ca-bundle.crt | text | |
MD5:1E32496378E8FEE43CB01B0689963A67 | SHA256:5B47AEE36F594B7737E00990C9922A87252729B74CC2F1A83C0FCEED9816BDB9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
35
DNS requests
12
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4080 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3268 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4080 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6756 | cr_launcher_1.0.3.139-an3bou6y2.tmp | 188.42.61.240:443 | launcher-bq.gaijin.net | SERVERS-COM | LU | unknown |
1860 | gaijin_downloader.exe | 54.171.18.57:443 | yupmaster.gaijinent.com | AMAZON-02 | IE | unknown |
7128 | launcher.exe | 89.149.224.35:20011 | client-stats.gaijin.net | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
launcher-bq.gaijin.net |
| whitelisted |
client-stats.gaijin.net |
| whitelisted |
client-stats.warthunder.com |
| whitelisted |
yupmaster.gaijinent.com |
| whitelisted |
seeder.gaijin.lan |
| unknown |
crsed.net |
| unknown |
watson.events.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
Process | Message |
|---|---|
launcher.exe | Log path C:\Users\admin\AppData\Local\CRSED\.launcher_log\2024_08_03_04_25_00_7128.txt |
launcher.exe | |
launcher.exe | BUILD TIMESTAMP: Jul 4 2024 12:38:24
|
launcher.exe | 0.31 [D] TIMER freq: ticks/usec=3 ticks/msec=3579
|
launcher.exe | 0.33 [D] Creating thread "Watchdog thread"...
|
launcher.exe | 0.33 [D] Registered message 0xC1A5
|
launcher.exe | ---$01 (null) ---
0.33 [D] $01 Thread "Watchdog thread" started
|
launcher.exe | 0.34 [D] Mounting C:\Users\admin\AppData\Local\CRSED\launcherr.dat...
|
launcher.exe | 0.34 [D] launcherr.dat sign match
|
launcher.exe | 0.34 [D] Mounted blk.nut
|