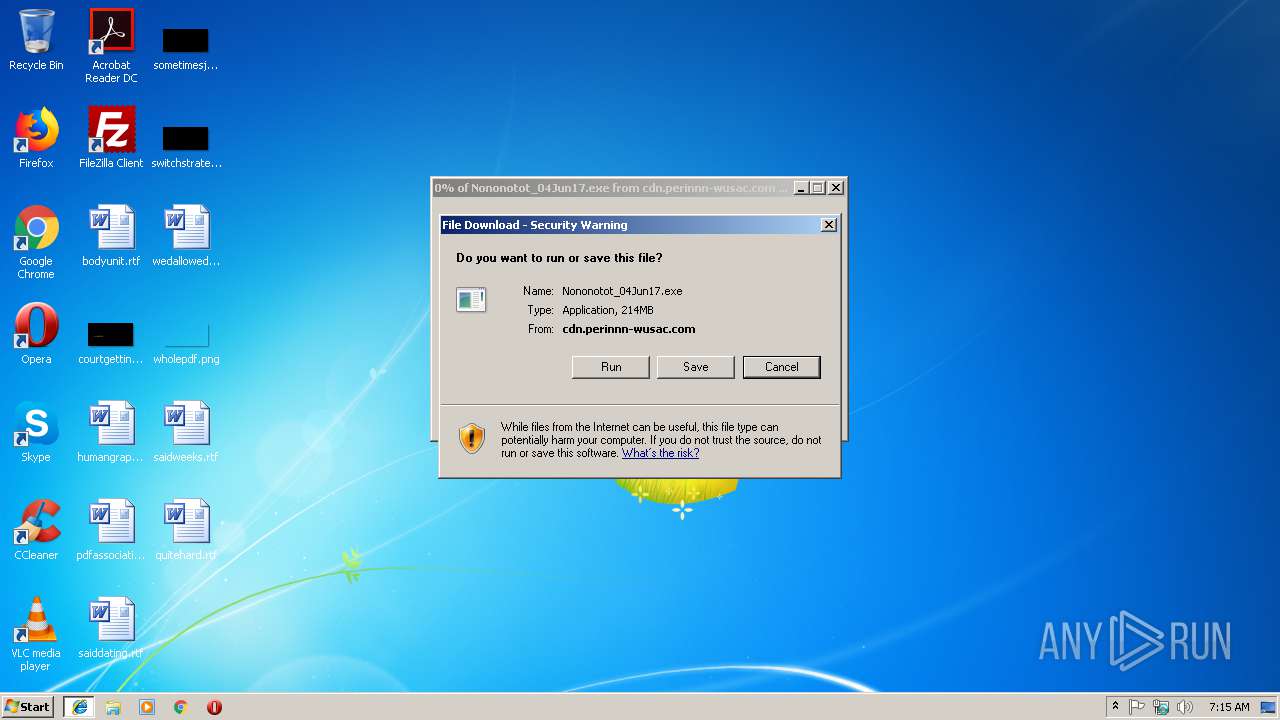
| URL: | http://cdn.perinnn-wusac.com/ofr/Nononotot/Nononotot_04Jun17.exe |
| Full analysis: | https://app.any.run/tasks/aa1584c4-c443-4b1e-ad63-847888524bbe |
| Verdict: | Malicious activity |
| Analysis date: | February 07, 2019, 07:15:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A70F0A3756945FDE73A7B037ED22E367 |
| SHA1: | 45DA1476A699715005E4562D6DFDCB62C93770E8 |
| SHA256: | A940C0C5DA82D9268080201846A243A5BEDFB9AEADF06CAC9232EF57768B73FB |
| SSDEEP: | 3:N1KdBLWXervOPzRKRzRKTLUSLAdA:CXQa2bRKRzRKTgSLAC |
MALICIOUS
Loads dropped or rewritten executable
- Nononotot_04Jun17[1].exe (PID: 3160)
- explorer.exe (PID: 284)
- coInst.exe (PID: 4056)
- SearchProtocolHost.exe (PID: 968)
- coInst.exe (PID: 2988)
- EFAInst.exe (PID: 2640)
- SymIMIns.exe (PID: 2480)
- RuleUp.exe (PID: 3532)
- SymVTCatalogDB.exe (PID: 2148)
- tuIH.exe (PID: 3300)
- InstCA.exe (PID: 3704)
- NS.exe (PID: 584)
- SRTSP_CA.exe (PID: 3636)
- symerr.exe (PID: 3884)
- cltLMH.exe (PID: 2804)
- cltLMH.exe (PID: 3376)
- NS.exe (PID: 2484)
- uiStub.exe (PID: 1904)
- uiStub.exe (PID: 3448)
- cltLMH.exe (PID: 2412)
- WSCStub.exe (PID: 2100)
- WSCStub.exe (PID: 3960)
- WSCStub.exe (PID: 3292)
- WSCStub.exe (PID: 2428)
Changes the autorun value in the registry
- Nononotot_04Jun17[1].exe (PID: 3160)
Application was dropped or rewritten from another process
- EFAInst.exe (PID: 2640)
- Sevinst.exe (PID: 3416)
- InstCA.exe (PID: 3704)
- NS.exe (PID: 584)
- cltLMH.exe (PID: 2804)
- cltLMH.exe (PID: 3376)
- NS.exe (PID: 2484)
- symerr.exe (PID: 3884)
- coInst.exe (PID: 2988)
- coInst.exe (PID: 4056)
- SRTSP_CA.exe (PID: 3636)
- SymIMIns.exe (PID: 2480)
- uiStub.exe (PID: 3448)
- tuIH.exe (PID: 3300)
- WSCStub.exe (PID: 2100)
- RuleUp.exe (PID: 3532)
- uiStub.exe (PID: 1904)
- SymVTCatalogDB.exe (PID: 2148)
- cltLMH.exe (PID: 2412)
- WSCStub.exe (PID: 3960)
- WSCStub.exe (PID: 3292)
- WSCStub.exe (PID: 2428)
Loads the Task Scheduler COM API
- tuIH.exe (PID: 3300)
- symerr.exe (PID: 3884)
- InstCA.exe (PID: 3704)
- NS.exe (PID: 584)
SUSPICIOUS
Starts Internet Explorer
- explorer.exe (PID: 284)
Application launched itself
- Nononotot_04Jun17[1].exe (PID: 1684)
- NS.exe (PID: 584)
Creates a software uninstall entry
- Nononotot_04Jun17[1].exe (PID: 3160)
- Sevinst.exe (PID: 3416)
Creates or modifies windows services
- Nononotot_04Jun17[1].exe (PID: 3160)
Creates COM task schedule object
- Nononotot_04Jun17[1].exe (PID: 3160)
Writes to a desktop.ini file (may be used to cloak folders)
- Nononotot_04Jun17[1].exe (PID: 3160)
Creates files in the Windows directory
- Nononotot_04Jun17[1].exe (PID: 3160)
- Sevinst.exe (PID: 3416)
Creates files in the driver directory
- Nononotot_04Jun17[1].exe (PID: 3160)
- Sevinst.exe (PID: 3416)
Executable content was dropped or overwritten
- Sevinst.exe (PID: 3416)
- Nononotot_04Jun17[1].exe (PID: 3160)
Creates files in the program directory
- EFAInst.exe (PID: 2640)
- Sevinst.exe (PID: 3416)
- RuleUp.exe (PID: 3532)
- SymIMIns.exe (PID: 2480)
- tuIH.exe (PID: 3300)
- InstCA.exe (PID: 3704)
- NS.exe (PID: 2484)
- cltLMH.exe (PID: 2804)
- Nononotot_04Jun17[1].exe (PID: 3160)
- NS.exe (PID: 584)
Low-level read access rights to disk partition
- cltLMH.exe (PID: 3376)
Creates files in the user directory
- NS.exe (PID: 2484)
Starts CMD.EXE for commands execution
- NS.exe (PID: 584)
INFO
Application launched itself
- iexplore.exe (PID: 2964)
Changes internet zones settings
- iexplore.exe (PID: 2964)
Reads Internet Cache Settings
- iexplore.exe (PID: 3236)
Reads Microsoft Office registry keys
- NS.exe (PID: 2484)
Reads settings of System Certificates
- explorer.exe (PID: 284)
- NS.exe (PID: 584)
Dropped object may contain Bitcoin addresses
- Nononotot_04Jun17[1].exe (PID: 3160)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
64
Monitored processes
29
Malicious processes
25
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 584 | "C:\Program Files\Norton Security\Engine\22.9.1.12\NS.exe" /s "NS" /m "C:\Program Files\Norton Security\Engine\22.9.1.12\diMaster.dll" /prefetch:1 | C:\Program Files\Norton Security\Engine\22.9.1.12\NS.exe | services.exe | ||||||||||||
User: SYSTEM Company: Symantec Corporation Integrity Level: SYSTEM Description: Norton Security Exit code: 0 Version: 14.1.0.65 Modules
| |||||||||||||||
| 968 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1684 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\Nononotot_04Jun17[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\Nononotot_04Jun17[1].exe | — | iexplore.exe | |||||||||||
User: admin Company: Symantec Corporation Integrity Level: MEDIUM Description: Norton Security Exit code: 0 Version: 22.9.1.12 Modules
| |||||||||||||||
| 1904 | "C:\Program Files\Norton Security\Engine\22.9.1.12\uiStub.exe" | C:\Program Files\Norton Security\Engine\22.9.1.12\uiStub.exe | — | explorer.exe | |||||||||||
User: admin Company: Symantec Corporation Integrity Level: MEDIUM Description: Norton Protection Center UI Stub Exit code: 0 Version: 22.9.1.12 Modules
| |||||||||||||||
| 2100 | "C:\Program Files\Norton Security\Engine\22.9.1.12\WSCStub.exe" | C:\Program Files\Norton Security\Engine\22.9.1.12\WSCStub.exe | — | NS.exe | |||||||||||
User: SYSTEM Company: Symantec Corporation Integrity Level: SYSTEM Description: WSCStub Exit code: 0 Version: 22.9.1.12 Modules
| |||||||||||||||
| 2148 | "C:\Program Files\Norton Security\Engine\22.9.1.12\SymVTCatalogDB.exe" /d | C:\Program Files\Norton Security\Engine\22.9.1.12\SymVTCatalogDB.exe | — | Nononotot_04Jun17[1].exe | |||||||||||
User: admin Integrity Level: HIGH Description: SymVT Catalog Database Application Exit code: 0 Version: 8.0.0.30 Modules
| |||||||||||||||
| 2412 | scan:b-f+ onlinedefs:0 boot:"*"- file:"%SYSTEMDRIVE%\*"+"%TEMP%"-"%TMP%"- container:"*"+"dxsndb"- containerdepth:8 dataexchange:"%APPDATA%\cltLMH.dxsndb" | C:\PROGRAM FILES\NORTON SECURITY\ENGINE\22.9.1.12\cltLMH.exe | NS.exe | ||||||||||||
User: SYSTEM Company: Symantec Corporation Integrity Level: SYSTEM Description: Symantec Shared Component Exit code: 2147776550 Version: 15.9.1.7 Modules
| |||||||||||||||
| 2428 | "C:\Program Files\Norton Security\Engine\22.9.1.12\WSCStub.exe" | C:\Program Files\Norton Security\Engine\22.9.1.12\WSCStub.exe | — | NS.exe | |||||||||||
User: SYSTEM Company: Symantec Corporation Integrity Level: SYSTEM Description: WSCStub Exit code: 0 Version: 22.9.1.12 Modules
| |||||||||||||||
| 2480 | "C:\Program Files\Norton Security\Engine\22.9.1.12\SymIMIns.exe" /install | C:\Program Files\Norton Security\Engine\22.9.1.12\SymIMIns.exe | Nononotot_04Jun17[1].exe | ||||||||||||
User: admin Company: Symantec Corporation Integrity Level: HIGH Description: SymIM Install Custom Action Executable Exit code: 0 Version: 16.0.0.209 Modules
| |||||||||||||||
Total events
9 656
Read events
7 397
Write events
2 167
Delete events
92
Modification events
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {2D66CD1B-2AA8-11E9-AA93-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2964) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30702000400070007000F002B008C00 | |||
Executable files
1 686
Suspicious files
419
Text files
482
Unknown types
66
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF8CBDC47140B9BA17.TMP | — | |
MD5:— | SHA256:— | |||
| 3236 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\Nononotot_04Jun17[1].exe | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\R9ZEWH8D\Nononotot_04Jun17[1].exe | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF7CFCF53F91FBE4D8.TMP | — | |
MD5:— | SHA256:— | |||
| 2964 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\RecoveryStore.{2D66CD1B-2AA8-11E9-AA93-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
| 3236 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019020720190208\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3160 | Nononotot_04Jun17[1].exe | C:\Program Files\NortonInstaller\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\NS\562C4DD5\22.9.1.12\InstStub.exe | executable | |
MD5:— | SHA256:— | |||
| 3160 | Nononotot_04Jun17[1].exe | C:\Program Files\NortonInstaller\{0C55C096-0F1D-4F28-AAA2-85EF591126E7}\NS\562C4DD5\22.9.1.12\01\01\InsMUI.loc | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3236 | iexplore.exe | GET | — | 199.201.110.78:80 | http://cdn.perinnn-wusac.com/ofr/Nononotot/Nononotot_04Jun17.exe | US | — | — | malicious |
2964 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2964 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3236 | iexplore.exe | 199.201.110.78:80 | cdn.perinnn-wusac.com | Namecheap, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
cdn.perinnn-wusac.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3236 | iexplore.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
Process | Message |
|---|---|
EFAInst.exe | 2019-02-07-07-17-13-687 : EFASIInst : 0x0A50 : 0x0A54 : Information : --> Starting wWinMain...
|
EFAInst.exe | 2019-02-07-07-17-13-687 : EFASIInst : 0x0A50 : 0x0A54 : Information : Command line arguments: /legacydelsysvolinfo
|
EFAInst.exe | 2019-02-07-07-17-13-687 : EFASIInst : 0x0A50 : 0x0A54 : Information : --> Starting Main...
|
EFAInst.exe | 2019-02-07-07-17-14-765 : EFASIInst : 0x0A50 : 0x0A54 : Information : SymEFA 4.x style uninstall started.
|
EFAInst.exe | 2019-02-07-07-17-14-765 : EFASIInst : 0x0A50 : 0x0A54 : Information : Removing data from System Volume Information folders.
|
EFAInst.exe | 2019-02-07-07-17-14-765 : EFASIInst : 0x0A50 : 0x0A54 : Information : Getting DelSysVol actions...
|
EFAInst.exe | 2019-02-07-07-17-14-765 : EFASIInst : 0x0A50 : 0x0A54 : Information : <-- SymEFA::GetDelSysVolInfoActions ended
|
EFAInst.exe | 2019-02-07-07-17-14-765 : EFASIInst : 0x0A50 : 0x0A54 : Information : <-- SymEFA::GetDelSysVolInfoActions ended
|
EFAInst.exe | 2019-02-07-07-17-14-765 : EFASIInst : 0x0A50 : 0x0A54 : Information : Acquiring privileges...
|
EFAInst.exe | 2019-02-07-07-17-14-765 : EFASIInst : 0x0A50 : 0x0A54 : Information : CEfaDataAction: Action will be permanently uninstalled
|