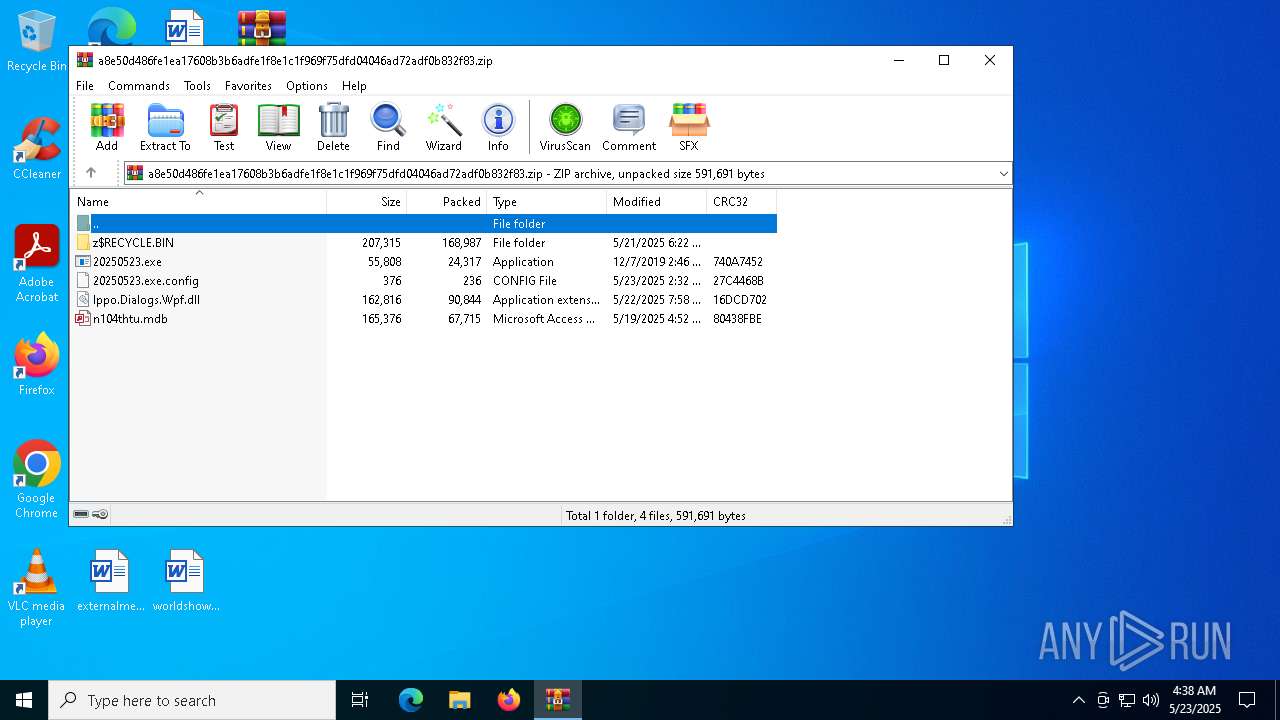
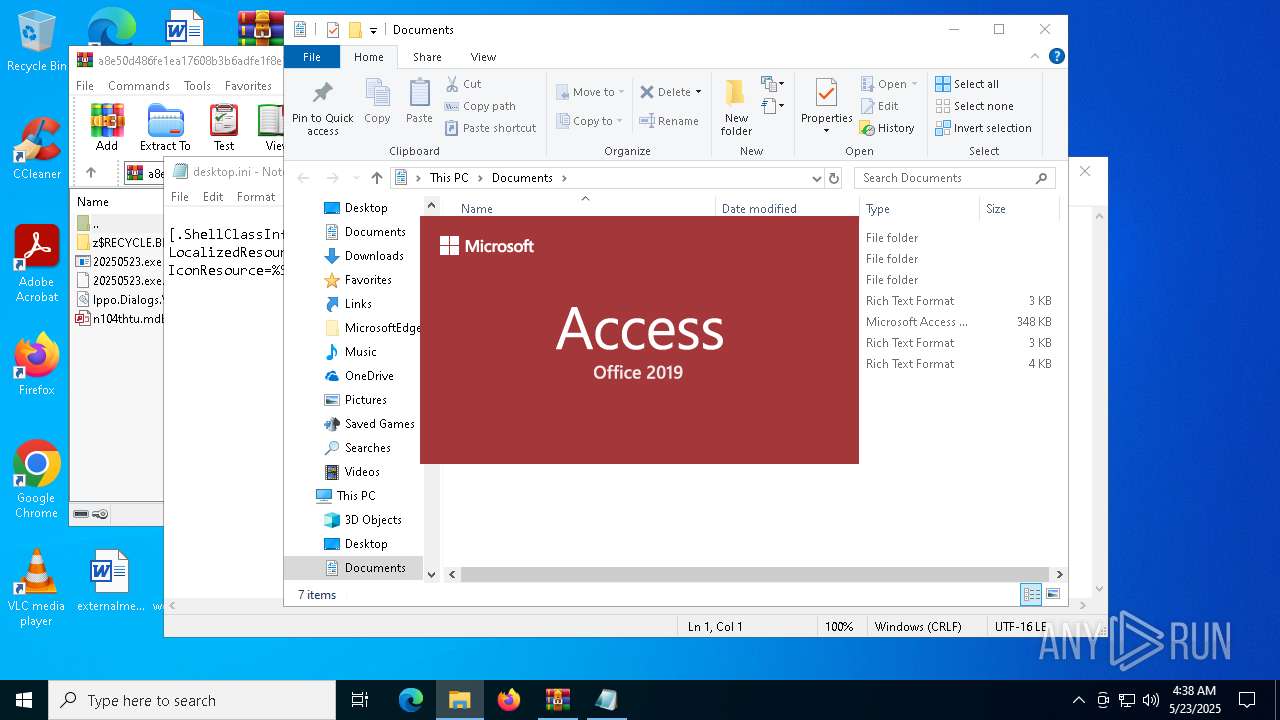
| File name: | a8e50d486fe1ea17608b3b6adfe1f8e1c1f969f75dfd04046ad72adf0b832f83 |
| Full analysis: | https://app.any.run/tasks/7914c93e-285f-44ec-bce9-3ecb74d09738 |
| Verdict: | Malicious activity |
| Analysis date: | May 23, 2025, 04:37:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | A3B7DC10694EB66A7DDB56545E3B5D36 |
| SHA1: | C9BAC0C3705EA2872379AE68E5EDD8460B895810 |
| SHA256: | A8E50D486FE1EA17608B3B6ADFE1F8E1C1F969F75DFD04046AD72ADF0B832F83 |
| SSDEEP: | 12288:zWo5OICqufh23bbkt6LNtnYeYP5C8c8x2:zWWOICquZ23bbk+tYeYP5C8c8x2 |
MALICIOUS
Scans artifacts that could help determine the target
- MSACCESS.EXE (PID: 4944)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 4244)
Starts a Microsoft application from unusual location
- 20250523.exe (PID: 2236)
Executes application which crashes
- 20250523.exe (PID: 2236)
Reads security settings of Internet Explorer
- MSACCESS.EXE (PID: 4944)
Reads the date of Windows installation
- MSACCESS.EXE (PID: 4944)
INFO
Manual execution by a user
- 20250523.exe (PID: 2236)
- MSACCESS.EXE (PID: 4944)
- notepad.exe (PID: 6964)
Checks supported languages
- 20250523.exe (PID: 2236)
- MSACCESS.EXE (PID: 4944)
Reads the computer name
- 20250523.exe (PID: 2236)
- MSACCESS.EXE (PID: 4944)
Creates files or folders in the user directory
- WerFault.exe (PID: 5376)
- MSACCESS.EXE (PID: 4944)
Reads Microsoft Office registry keys
- MSACCESS.EXE (PID: 4944)
Process checks computer location settings
- MSACCESS.EXE (PID: 4944)
Reads security settings of Internet Explorer
- notepad.exe (PID: 6964)
Reads the software policy settings
- MSACCESS.EXE (PID: 4944)
- slui.exe (PID: 668)
Reads the machine GUID from the registry
- MSACCESS.EXE (PID: 4944)
- 20250523.exe (PID: 2236)
Create files in a temporary directory
- MSACCESS.EXE (PID: 4944)
Checks proxy server information
- MSACCESS.EXE (PID: 4944)
- slui.exe (PID: 668)
Reads product name
- MSACCESS.EXE (PID: 4944)
Reads Environment values
- MSACCESS.EXE (PID: 4944)
Reads CPU info
- MSACCESS.EXE (PID: 4944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:05:21 14:22:14 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | z$RECYCLE.BIN/ |
Total processes
132
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 668 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\Users\admin\Desktop\20250523.exe" | C:\Users\admin\Desktop\20250523.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Exit code: 3762504530 Version: 10.0.19041.1 Modules
| |||||||||||||||
| 4244 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\a8e50d486fe1ea17608b3b6adfe1f8e1c1f969f75dfd04046ad72adf0b832f83.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
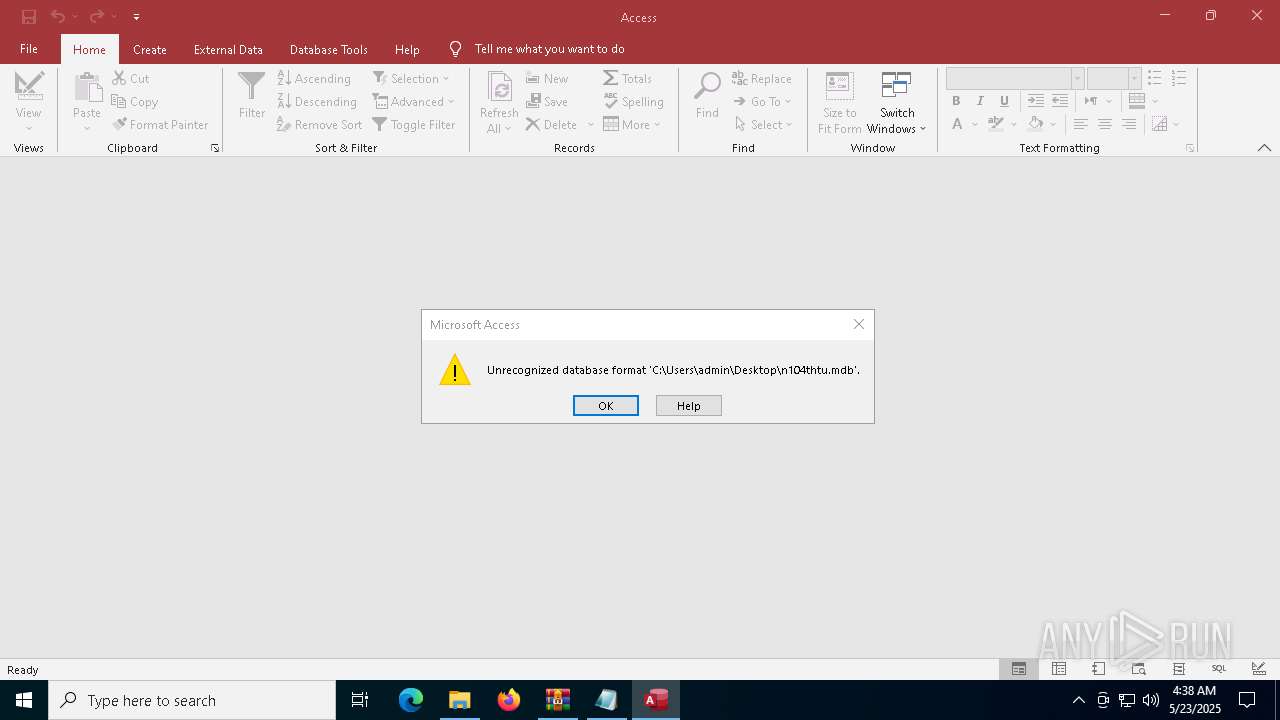
| 4944 | "C:\Program Files\Microsoft Office\Root\Office16\MSACCESS.EXE" /NOSTARTUP C:\Users\admin\Desktop\n104thtu.mdb %2 %3 %4 %5 %6 %7 %8 %9 | C:\Program Files\Microsoft Office\root\Office16\MSACCESS.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Access Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5376 | C:\WINDOWS\system32\WerFault.exe -u -p 2236 -s 1016 | C:\Windows\System32\WerFault.exe | — | 20250523.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6964 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\desktop.ini | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
15 829
Read events
15 420
Write events
368
Delete events
41
Modification events
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\a8e50d486fe1ea17608b3b6adfe1f8e1c1f969f75dfd04046ad72adf0b832f83.zip | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4244) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4944) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 2 |
Value: 01600E000000001000B24E9A3E01000000000000000200000000000000 | |||
| (PID) Process: | (4944) MSACCESS.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\MSACCESS\4944 |
| Operation: | write | Name: | 0 |
Value: 0B0E102E7DC772EAEFDA4D80FFC0D8C2204AC4230046AEDCABD2C7F3F2ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E223733476255664B62784F56664E70753657616837594A2F4D45484154685631664A6E64643072694C4A67493D22CA0DC2190000C91003783634C511D026D2120C6D0073006100630063006500730073002E00650078006500C51620C517808004C91808323231322D44656300 | |||
Executable files
0
Suspicious files
5
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5376 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_20250523.exe_dc5bb4633339c6706e188b23b145e93f63ad05f_0e6867c3_e3023ee7-6af4-46a0-8d85-328e2107341a\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5376 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\20250523.exe.2236.dmp | — | |
MD5:— | SHA256:— | |||
| 5376 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERCDD2.tmp.WERInternalMetadata.xml | xml | |
MD5:FD3B59AFF7F8FDC4D1E1D1569C6485DD | SHA256:59D2654C6E3BE3FB28ABB8087A0DF5B013FEDE7A3BB31625907F9AA1577E21AB | |||
| 4944 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{4B448EE0-CD5A-418A-8DB8-2E66ED56FA28}\{3D3B5679-CCC3-440E-9126-4DA6106344A8}mt01225355.png | image | |
MD5:377B5ECED0E2105A899F7D0D9989EFEB | SHA256:E295597799CFC910B656FED12B6E6B29C32776E0E88DBC2CCB4A1B79C32638C7 | |||
| 4944 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:C0607CD39D500E10F7189E1EC98F3770 | SHA256:8948DBA7D7F3D0BC40024B9572F895BCA24FE04B08107CD17BCED4C778F041B7 | |||
| 4944 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{4B448EE0-CD5A-418A-8DB8-2E66ED56FA28}\{8AD415B8-4287-4B8F-A5C1-95C0E8AE85EC}mt01225342.png | image | |
MD5:D4E07E723C3A2F2EAF3AD5CAAD7BDC44 | SHA256:6A0BCF1FCBCF6945713B7934A7DA6BFA3A10F66E38D00DE97EFE47D31A37BA61 | |||
| 4944 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{4B448EE0-CD5A-418A-8DB8-2E66ED56FA28}\{AB8CA70E-5ABB-4FE4-837A-F75FC5F7C051}mt01225343.png | image | |
MD5:28D825FED592B6B24FD4A632F4AC24F5 | SHA256:895688D88A7B3F5B7372D07584AD0DE540D9032EF13942A417D909EEE9471007 | |||
| 4944 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{4B448EE0-CD5A-418A-8DB8-2E66ED56FA28}\{B2347718-4BB6-4106-84E2-84ADEE588A72}mt01225356.png | image | |
MD5:97CF6C6F39D6708CACB74CCD9404AD38 | SHA256:F18DAEA0DDBB21D473289C85CCADEF59F7CE11B8E99F6C8938285771FD2BDE76 | |||
| 4944 | MSACCESS.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\H1CSF9B568P6IB3ZFO3D.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 4944 | MSACCESS.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\DTS\en-US{4B448EE0-CD5A-418A-8DB8-2E66ED56FA28}\{238BC4D9-DFD3-4CD2-82B2-0335BB1B6181}mt01225345.png | image | |
MD5:EC74A94632262E9A0CFECE0DA4B885E1 | SHA256:5A520C5C7DC6E0A711AB9682FD0AEACF4C61F1BD1049DA001D9825A9CC0EE702 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
46
TCP/UDP connections
61
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 52.109.76.240:443 | https://officeclient.microsoft.com/config16/?syslcid=1033&build=16.0.16026&crev=3 | unknown | xml | 179 Kb | whitelisted |
— | — | GET | 200 | 2.21.20.142:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/mt01225356.png | unknown | image | 4.39 Kb | whitelisted |
— | — | GET | 200 | 2.21.20.151:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/mt10094830.png | unknown | image | 2.44 Kb | whitelisted |
— | — | POST | 200 | 52.182.143.211:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 60 b | whitelisted |
— | — | GET | 200 | 52.123.128.14:443 | https://ecs.office.com/config/v2/Office/access/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=access&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=msaccess.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7b72C77D2E-EFEA-4DDA-80FF-C0D8C2204AC4%7d&LabMachine=false | unknown | binary | 361 Kb | whitelisted |
— | — | POST | 200 | 13.107.6.156:443 | https://roaming.officeapps.live.com/rs/RoamingSoapService.svc | unknown | — | — | whitelisted |
— | — | GET | 200 | 52.111.236.4:443 | https://messaging.engagement.office.com/campaignmetadataaggregator?app=2&platform=10&OFC_CHANNEL=CC&OFC_AUDIENCE=Production&OFC_FLIGHTS=ofsh6c2b1tla1a31%3Bofcrui4yvdulbf31%3Bofhpex3jznepoo31%3Bofaa1msspvo2xw31&ver=16.0.16026.20002&hwid=04111-083-043729AED3&OSVersion=10.0.19045&country=US&locale=en-US&OFC_LICENSECATEGORY=6&OFC_LICENSESKU=Professional2019Retail&ContentType=UserGovernanceRules%3BMessageMetadata | unknown | binary | 47 b | whitelisted |
— | — | POST | 200 | 40.126.32.76:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.160.64:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.160.65:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
4944 | MSACCESS.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4944 | MSACCESS.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4944 | MSACCESS.EXE | 52.109.0.140:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4944 | MSACCESS.EXE | 52.111.236.4:443 | messaging.engagement.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4944 | MSACCESS.EXE | 2.21.239.23:443 | metadata.templates.cdn.office.net | AKAMAI-AS | TR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ecs.office.com |
| whitelisted |
messaging.engagement.office.com |
| whitelisted |
login.live.com |
| whitelisted |
metadata.templates.cdn.office.net |
| whitelisted |
binaries.templates.cdn.office.net |
| whitelisted |