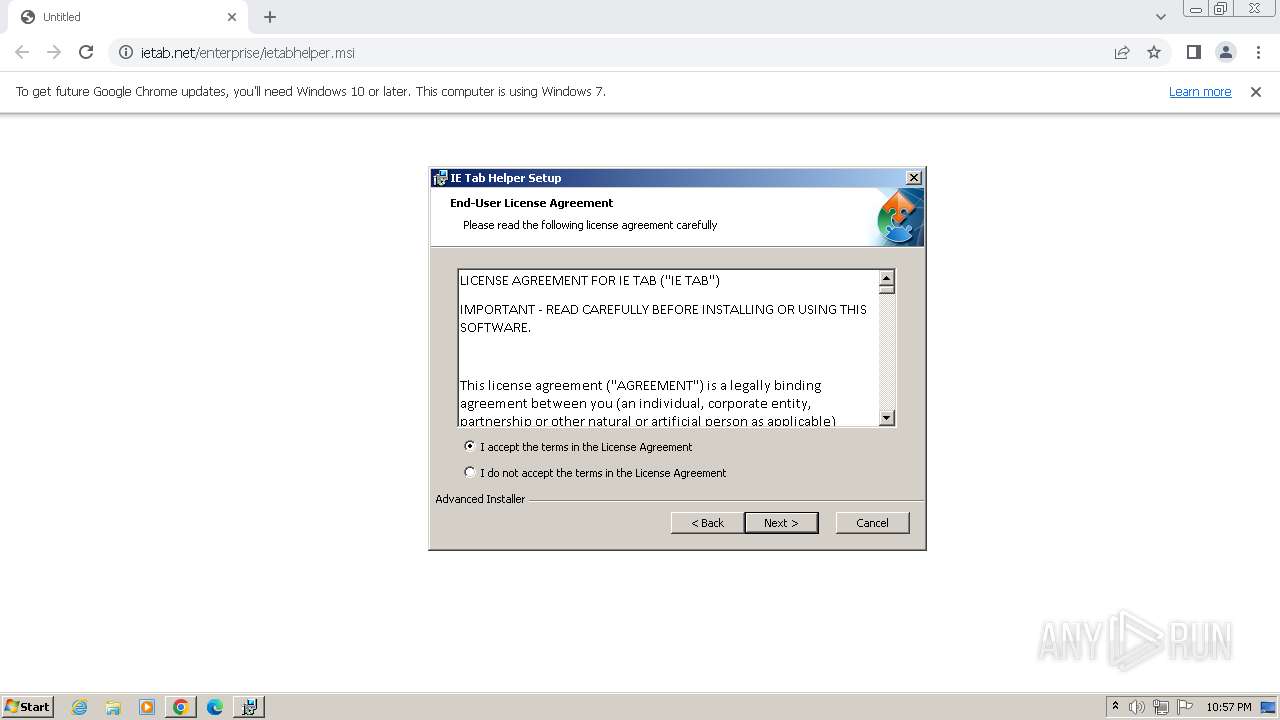
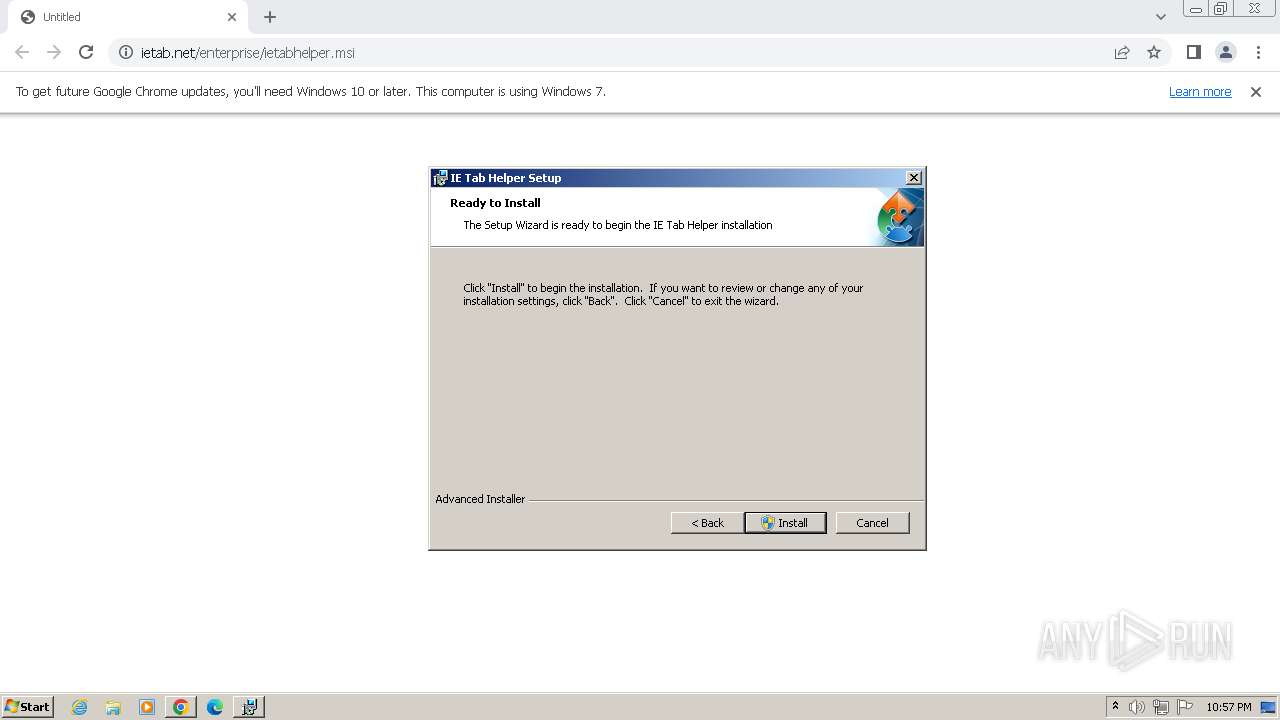
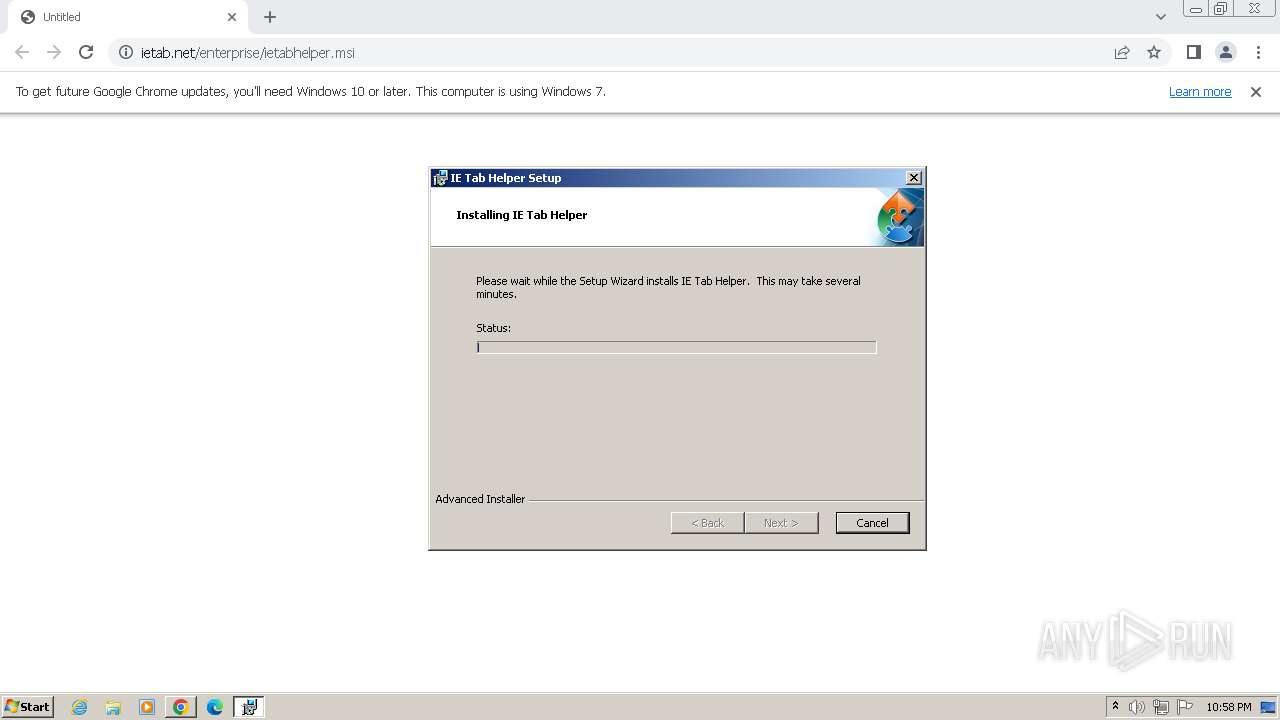
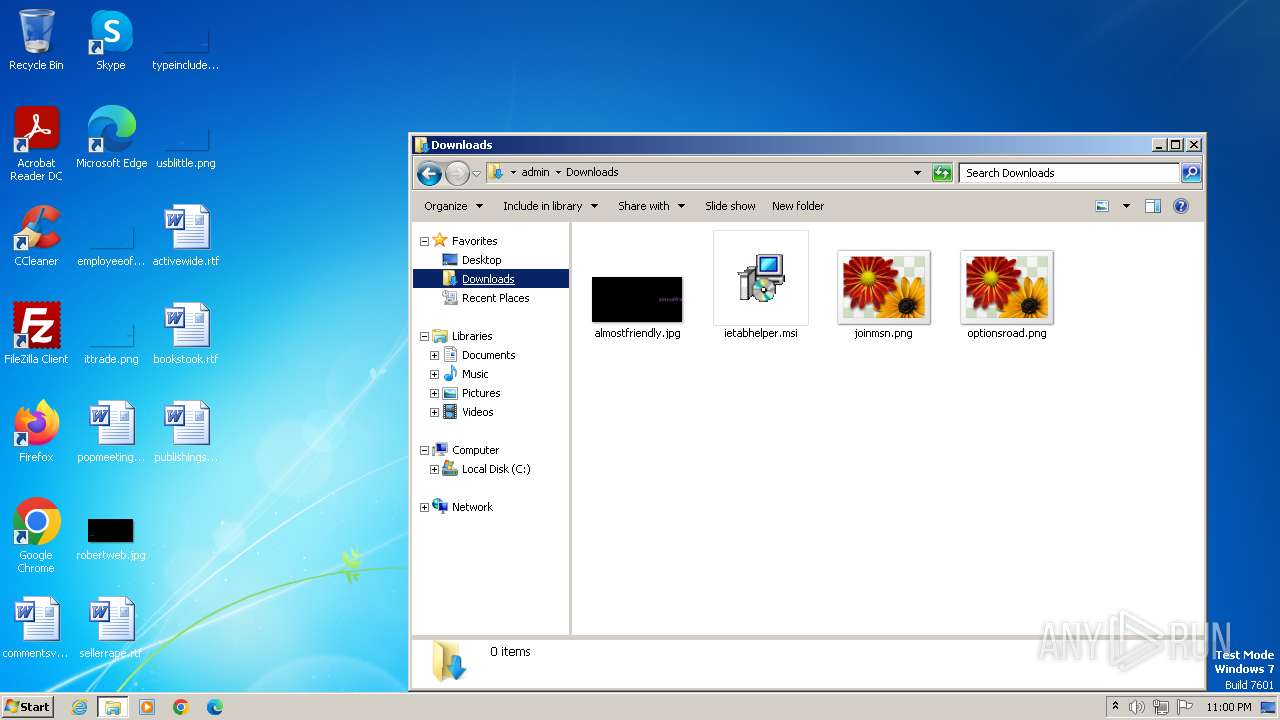
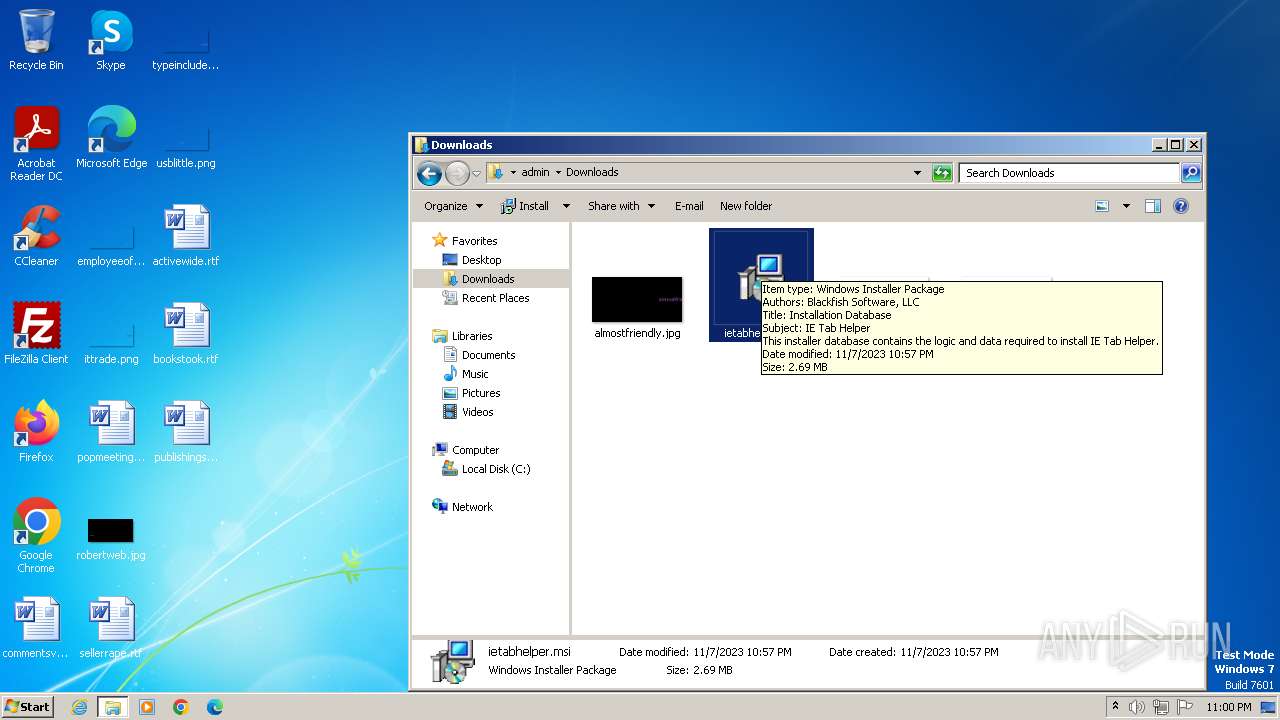
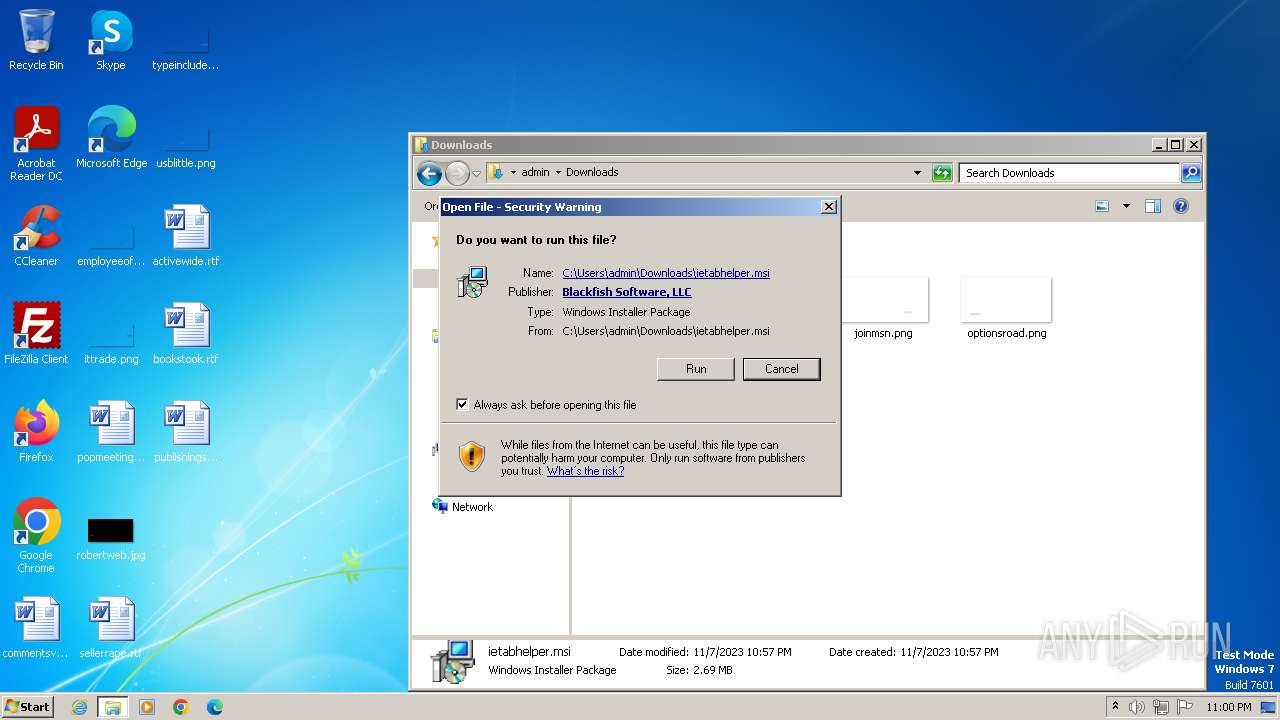
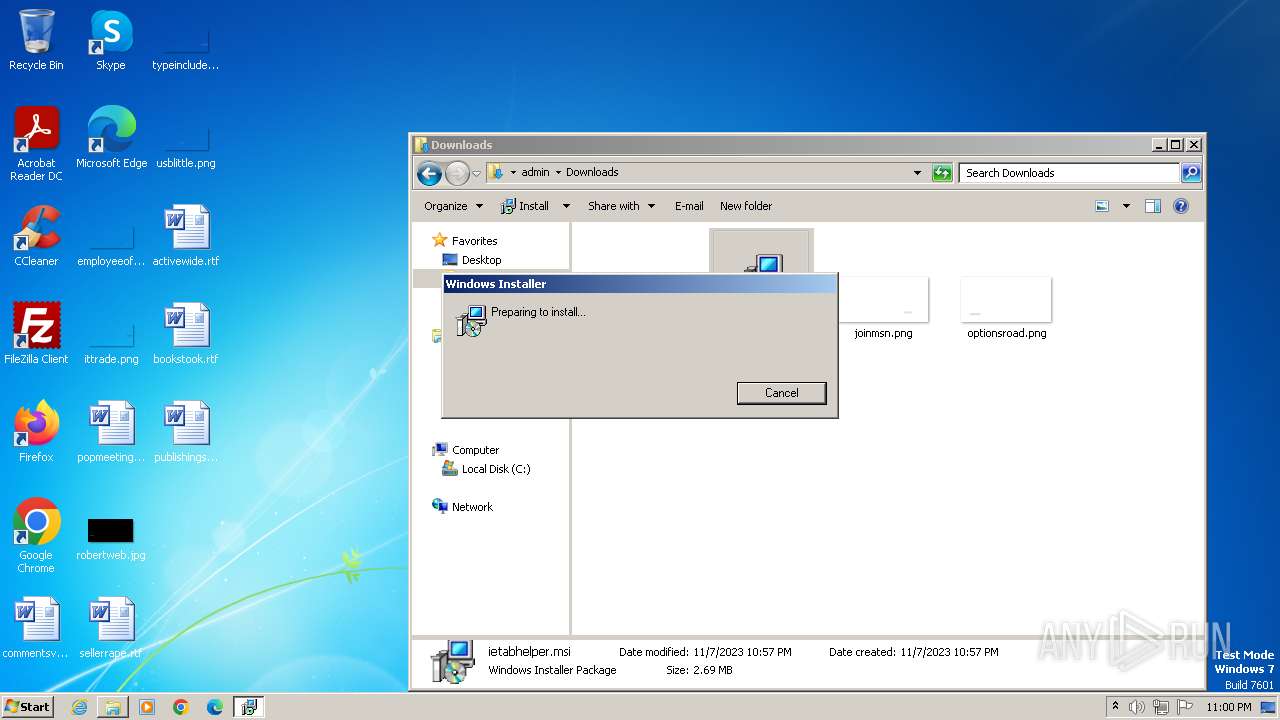
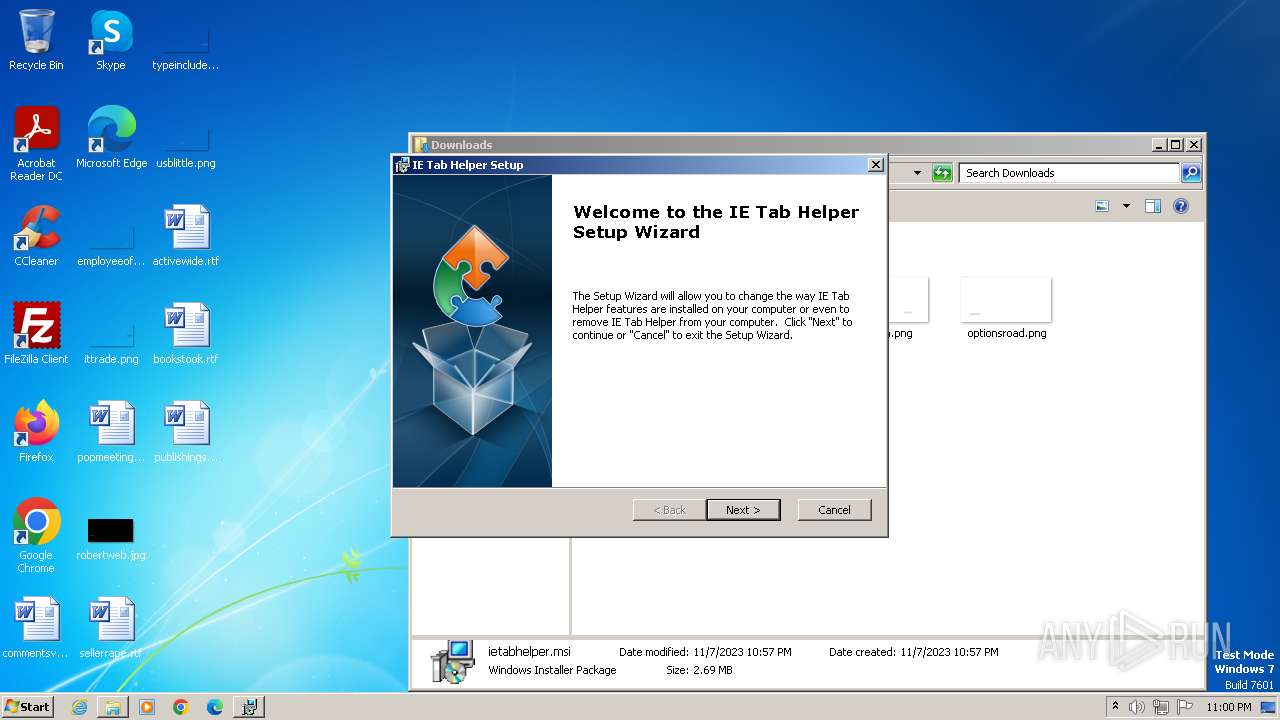
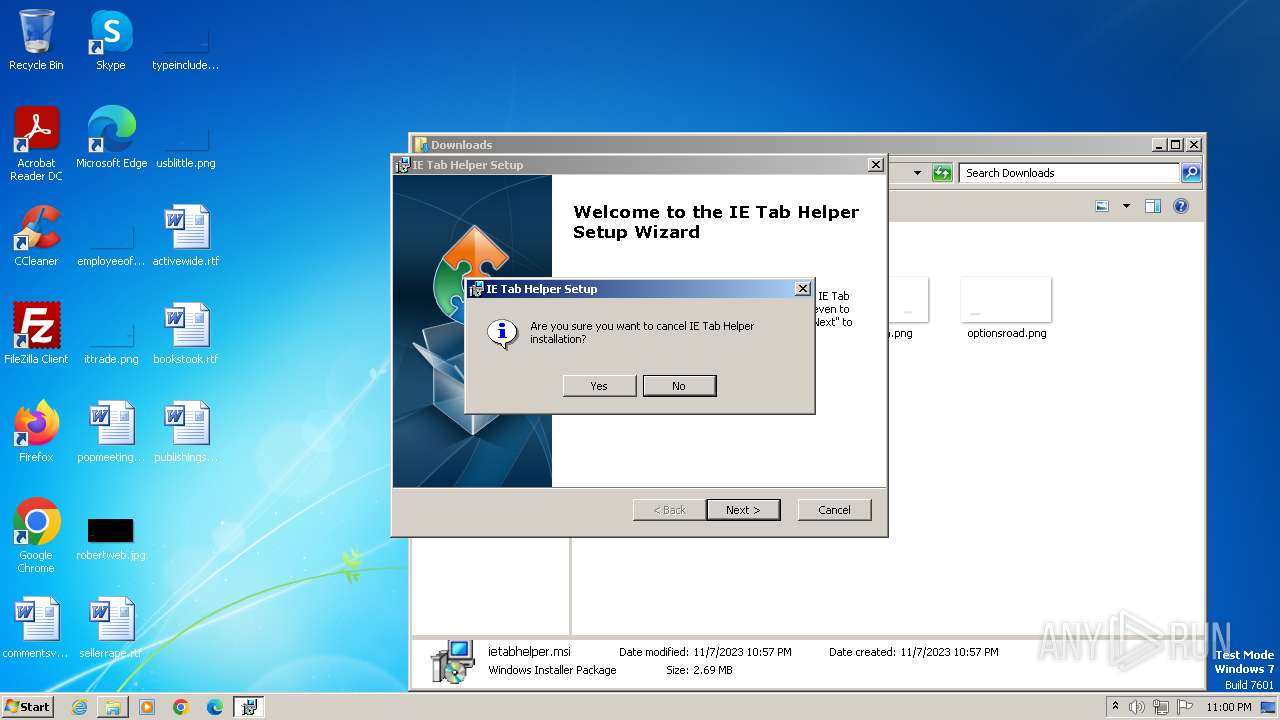
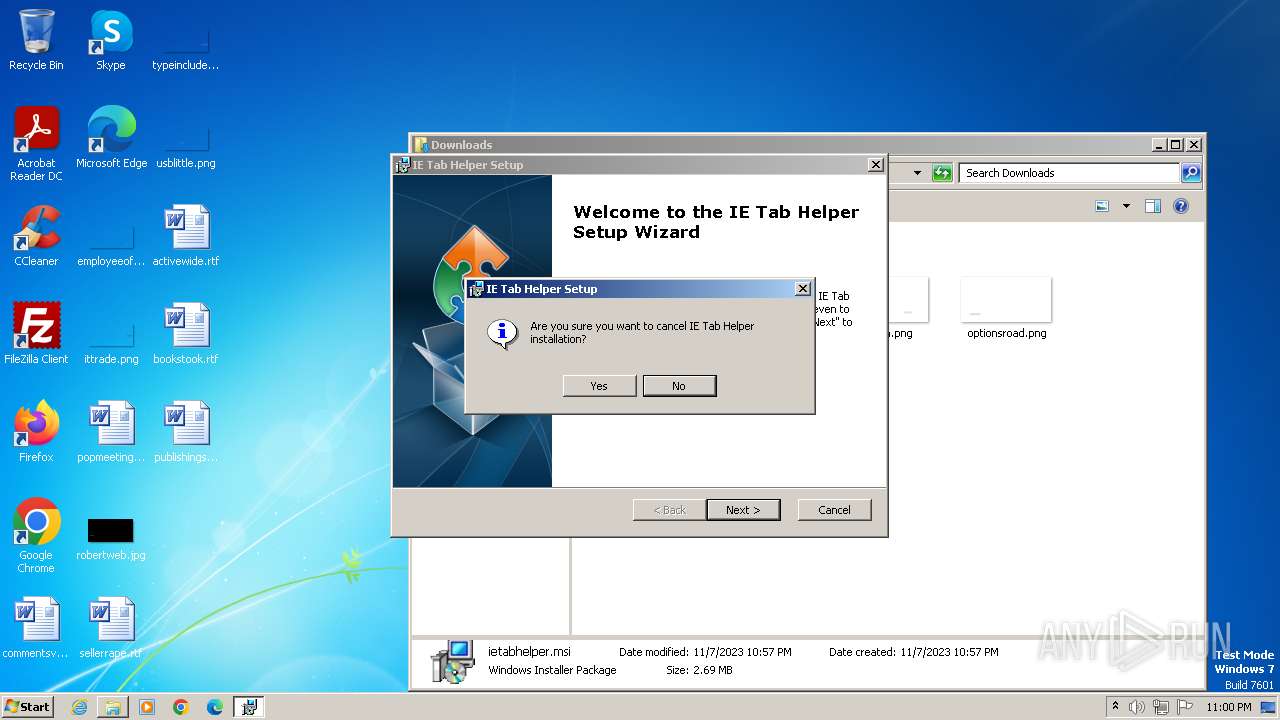
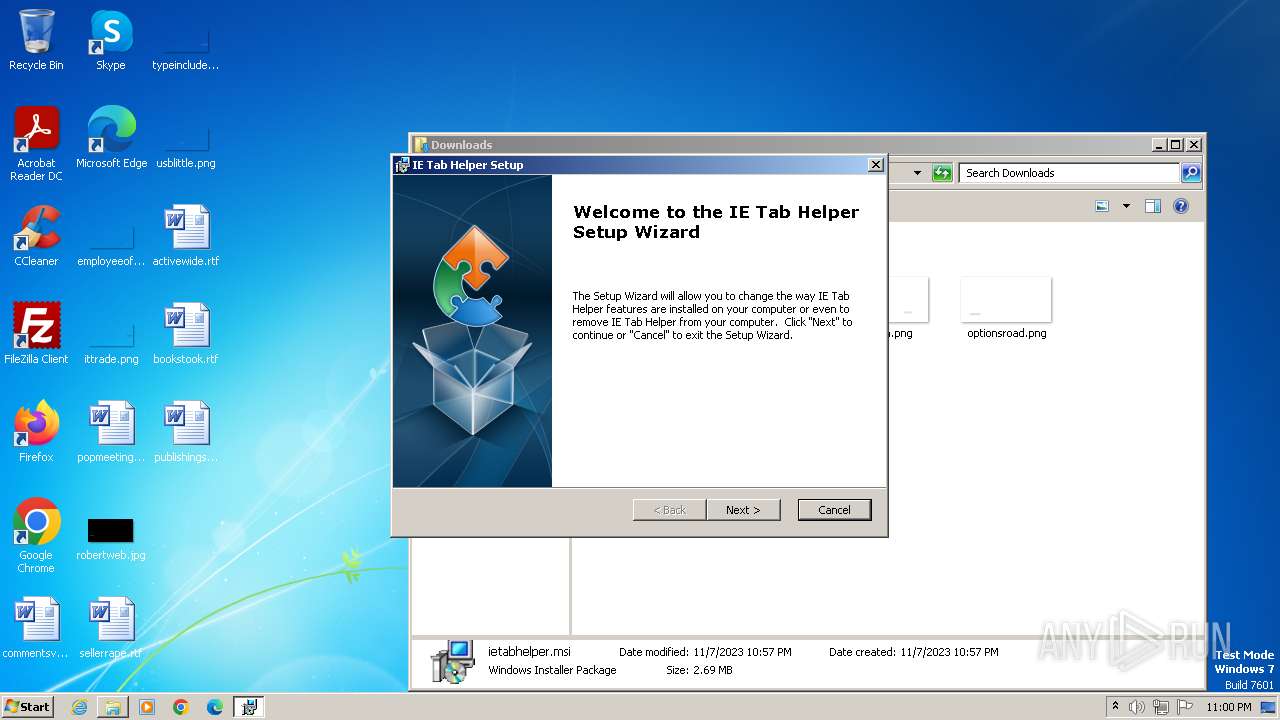
| URL: | http://www.ietab.net/enterprise/ietabhelper.msi |
| Full analysis: | https://app.any.run/tasks/f1d1330f-7e11-4ac3-aa69-1c84037626ed |
| Verdict: | Malicious activity |
| Analysis date: | November 07, 2023, 22:57:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | F24C591995E1D58BEBD737BC92A0A6FF5F632787 |
| SHA256: | A886639B8CEB9A1886A5E4EE339066F2420684B3A60085BCDE334AE0DA85A95E |
| SSDEEP: | 3:N1KJS4uLo4uWAX0EaqXLY:Cc4EWWU0EasLY |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 1924)
- msiexec.exe (PID: 1860)
- msiexec.exe (PID: 3820)
- ietabhelper.exe (PID: 1604)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 1924)
- msiexec.exe (PID: 3820)
Checks Windows Trust Settings
- msiexec.exe (PID: 1860)
Executes as Windows Service
- VSSVC.exe (PID: 2396)
Creates FileSystem object to access computer's file system (SCRIPT)
- msiexec.exe (PID: 900)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 2984)
Uses REG/REGEDIT.EXE to modify registry
- MSI174C.tmp (PID: 4036)
Executing commands from a ".bat" file
- msiexec.exe (PID: 2984)
Reads the Internet Settings
- wmplayer.exe (PID: 3816)
- setup_wm.exe (PID: 1828)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 2376)
- wmplayer.exe (PID: 3816)
- msiexec.exe (PID: 4080)
- ietabhelper.exe (PID: 1604)
- ietabhelper.exe (PID: 2612)
Checks supported languages
- wmpnscfg.exe (PID: 2376)
- msiexec.exe (PID: 1860)
- msiexec.exe (PID: 1924)
- msiexec.exe (PID: 900)
- MSI174C.tmp (PID: 4036)
- msiexec.exe (PID: 2984)
- MSI17E9.tmp (PID: 2196)
- MsiZap.exe (PID: 600)
- MsiZap.exe (PID: 2092)
- MSI19CE.tmp (PID: 1032)
- setup_wm.exe (PID: 1828)
- wmplayer.exe (PID: 3816)
- ietabhelper.exe (PID: 1604)
- ietabhelper.exe (PID: 2612)
- msiexec.exe (PID: 3820)
Drops the executable file immediately after the start
- msiexec.exe (PID: 1508)
- msiexec.exe (PID: 4080)
The process uses the downloaded file
- chrome.exe (PID: 3460)
- chrome.exe (PID: 3672)
- chrome.exe (PID: 2184)
- chrome.exe (PID: 2028)
- chrome.exe (PID: 2740)
Reads the computer name
- wmpnscfg.exe (PID: 2376)
- msiexec.exe (PID: 1860)
- msiexec.exe (PID: 1924)
- msiexec.exe (PID: 900)
- MsiZap.exe (PID: 600)
- MSI174C.tmp (PID: 4036)
- MSI17E9.tmp (PID: 2196)
- msiexec.exe (PID: 2984)
- MsiZap.exe (PID: 2092)
- MSI19CE.tmp (PID: 1032)
- wmplayer.exe (PID: 3816)
- setup_wm.exe (PID: 1828)
- msiexec.exe (PID: 3820)
Application launched itself
- chrome.exe (PID: 3460)
- msiexec.exe (PID: 1860)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 2376)
- msiexec.exe (PID: 1860)
- msiexec.exe (PID: 1924)
- msiexec.exe (PID: 900)
- msiexec.exe (PID: 2984)
- setup_wm.exe (PID: 1828)
- msiexec.exe (PID: 3820)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 1508)
Create files in a temporary directory
- msiexec.exe (PID: 1924)
- msiexec.exe (PID: 900)
- msiexec.exe (PID: 1860)
- msiexec.exe (PID: 2984)
- setup_wm.exe (PID: 1828)
- msiexec.exe (PID: 3820)
Reads Environment values
- msiexec.exe (PID: 900)
- msiexec.exe (PID: 2984)
- setup_wm.exe (PID: 1828)
Starts application with an unusual extension
- msiexec.exe (PID: 1860)
Process checks computer location settings
- setup_wm.exe (PID: 1828)
Checks proxy server information
- setup_wm.exe (PID: 1828)
Creates files or folders in the user directory
- ietabhelper.exe (PID: 1604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
89
Monitored processes
39
Malicious processes
3
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 600 | "C:\Users\admin\AppData\Local\Temp\MsiZap.exe" T! {06FE7581-2E5E-4B24-9350-535C650F18D0} | C:\Users\admin\AppData\Local\Temp\MsiZap.exe | MSI17E9.tmp | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® Installer Data Zapper Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | C:\Windows\system32\MsiExec.exe -Embedding 522459270F85F4C05E95A7A72432D7C2 | C:\Windows\System32\msiexec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1032 | "C:\Windows\Installer\MSI19CE.tmp" /HideWindow "C:\Users\admin\AppData\Local\Temp\MsiZap.exe" T! {6B7F960F-CD0C-4F9A-8673-033236237312} | C:\Windows\Installer\MSI19CE.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: File that launches another file Exit code: 0 Version: 11.5.1.0 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4072 --field-trial-handle=1128,i,17004686984975388090,14030257433144157398,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
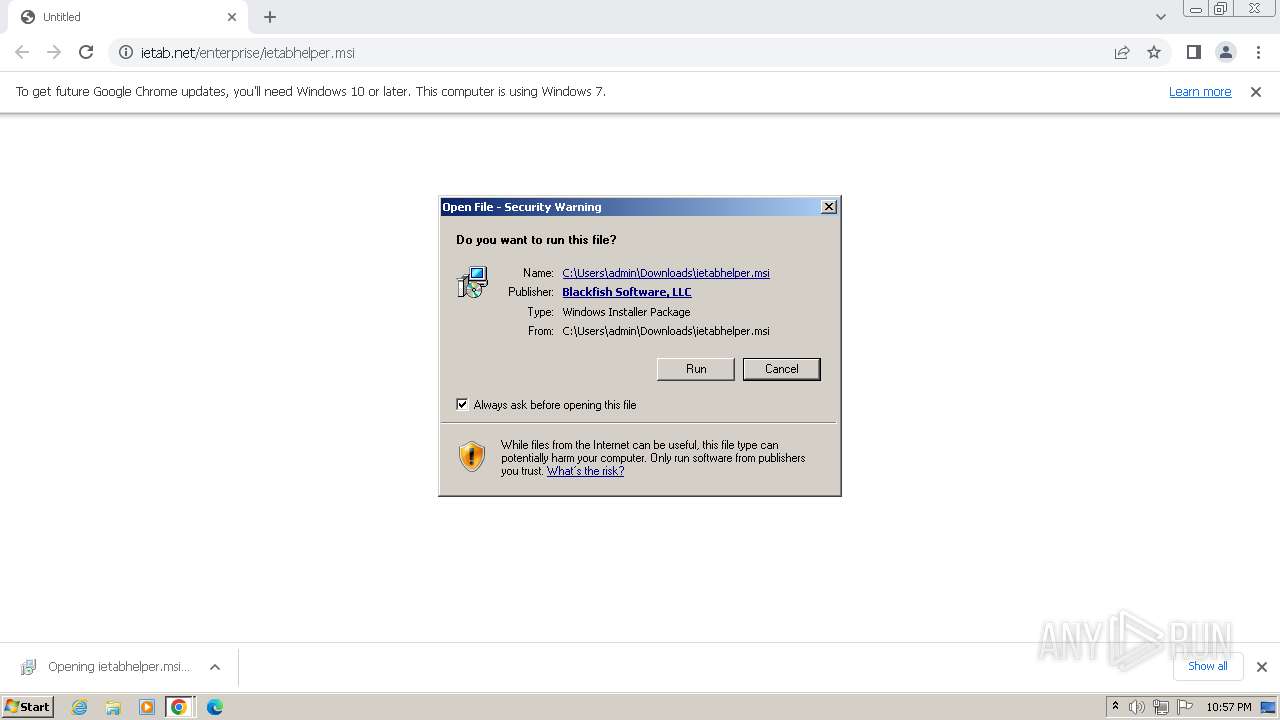
| 1508 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Downloads\ietabhelper.msi" | C:\Windows\System32\msiexec.exe | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1604 | "C:\Program Files\Blackfish Software, LLC\IE Tab Helper\16.10.16.1\ietabhelper.exe" | C:\Program Files\Blackfish Software, LLC\IE Tab Helper\16.10.16.1\ietabhelper.exe | — | explorer.exe | |||||||||||
User: admin Company: Blackfish Software Integrity Level: MEDIUM Description: IE Tab Helper application Exit code: 0 Version: 16.10.16.1 Modules
| |||||||||||||||
| 1828 | "C:\Program Files\Windows Media Player\setup_wm.exe" /RunOnce:"C:\Program Files\Windows Media Player\wmplayer.exe" /prefetch:1 | C:\Program Files\Windows Media Player\setup_wm.exe | wmplayer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Windows Media Configuration Utility Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1860 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1924 | C:\Windows\system32\MsiExec.exe -Embedding 43C92486D98E6E86895333B2E1BBDDDC C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3844 --field-trial-handle=1128,i,17004686984975388090,14030257433144157398,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
17 928
Read events
17 724
Write events
181
Delete events
23
Modification events
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (3460) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
31
Suspicious files
102
Text files
39
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF166eeb.TMP | — | |
MD5:— | SHA256:— | |||
| 3460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old~RF166eeb.TMP | text | |
MD5:D5C9ECBD2DCA29D89266782824D7AF99 | SHA256:D22D1243ACC064A30823180D0E583C853E9395367C78C2AD9DE59A463904F702 | |||
| 3460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:513218482935B0D388C0A990D868387A | SHA256:8E39CBAAF4AACC3A01AFA74EA8C30FB24FE69A22B8B30728AFB1614FD68809D9 | |||
| 3460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF166f1a.TMP | text | |
MD5:CDCC923CEC2CD9228330551E6946A9C2 | SHA256:592F4750166BE662AA88728F9969537163FEC5C3E95E81537C8C6917F8D0929E | |||
| 3460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old~RF167350.TMP | — | |
MD5:— | SHA256:— | |||
| 3460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3460 | chrome.exe | C:\Users\admin\Downloads\Unconfirmed 875598.crdownload | — | |
MD5:— | SHA256:— | |||
| 3460 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:E91E138A25FD7E5BCA5E60111F39C91A | SHA256:B1F7E3537A31A4B847F862858E5D2581993CC9372F19ABF19EA2A9185FE42A4F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
22
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | — | — | unknown |
1828 | setup_wm.exe | GET | 302 | 2.21.20.154:80 | http://redir.metaservices.microsoft.com/redir/allservices/?sv=5&version=12.0.7601.17514&locale=409&userlocale=409&geoid=f4&parch=x86&arch=x86 | unknown | — | — | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 6.04 Kb | unknown |
1828 | setup_wm.exe | GET | 200 | 23.216.77.37:80 | http://onlinestores.metaservices.microsoft.com/serviceswitching/AllServices.aspx?sv=5&version=12.0.7601.17514&locale=409&userlocale=409&geoid=f4&parch=x86&arch=x86 | unknown | xml | 546 b | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 9.87 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 44.6 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 1.17 Mb | unknown |
3408 | chrome.exe | GET | 301 | 54.174.17.107:80 | http://www.ietab.net/enterprise/ietabhelper.msi | unknown | html | 336 b | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 10.1 Kb | unknown |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k4ldha5kevpu7qn7k4s3mznvgu_4.10.2710.0/oimompecagnajdejgnnjijobebaeigek_4.10.2710.0_win32_ad2kbvs6jks3au5dsxn7cqflsiiq.crx3 | unknown | binary | 1.45 Mb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3460 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3408 | chrome.exe | 142.250.186.141:443 | accounts.google.com | GOOGLE | US | whitelisted |
3408 | chrome.exe | 54.174.17.107:80 | www.ietab.net | AMAZON-AES | US | unknown |
3408 | chrome.exe | 54.174.17.107:443 | www.ietab.net | AMAZON-AES | US | unknown |
3460 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
3408 | chrome.exe | 216.58.206.46:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
www.ietab.net |
| whitelisted |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
optimizationguide-pa.googleapis.com |
| whitelisted |
www.googleapis.com |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgedl.me.gvt1.com |
| whitelisted |
clients1.google.com |
| whitelisted |
redir.metaservices.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
msiexec.exe | # 2023-11-07 @22:58:06 [PID=900|Thread=3364] | OnAiRemoveFileImmediate start.
|
msiexec.exe | # 2023-11-07 @22:58:06 [PID=900|Thread=3364] | SELECT Join Query: [SELECT * FROM `RemoveFile`, `AI_RemoveFile` WHERE `RemoveFile`.`FileKey` = `AI_RemoveFile`.`RemoveFile`].
|
msiexec.exe | # 2023-11-07 @22:58:06 [PID=900|Thread=3364] | Deffered with rollback scheduled.
|
msiexec.exe | # 2023-11-07 @22:58:06 [PID=900|Thread=3364] | MsiTableReader::ExecuteQuery [DELETE FROM `RemoveFile` WHERE `RemoveFile`.`FileKey`='__2']...
|
msiexec.exe | # 2023-11-07 @22:58:06 [PID=900|Thread=3364] | Build JOINed tables CustomActionData string...
|
msiexec.exe | # 2023-11-07 @22:58:06 [PID=900|Thread=3364] | MsiTableReader::ExecuteQuery [SELECT * FROM `RemoveFile`, `AI_RemoveFile` WHERE `RemoveFile`.`FileKey` = `AI_RemoveFile`.`RemoveFile`]...
|
msiexec.exe | # 2023-11-07 @22:58:06 [PID=900|Thread=3364] | MsiTableReader: Getting the active MSI database for this installation session...
|
msiexec.exe | # 2023-11-07 @22:58:06 [PID=900|Thread=3364] | OnAiRemoveFileImmediate end.
|
msiexec.exe | # 2023-11-07 @22:58:06 [PID=2984|Thread=2676] | OnAiRemoveFiles start.
|
msiexec.exe | # 2023-11-07 @22:58:07 [PID=2984|Thread=2676] | OnAiRemoveFiles end.
|