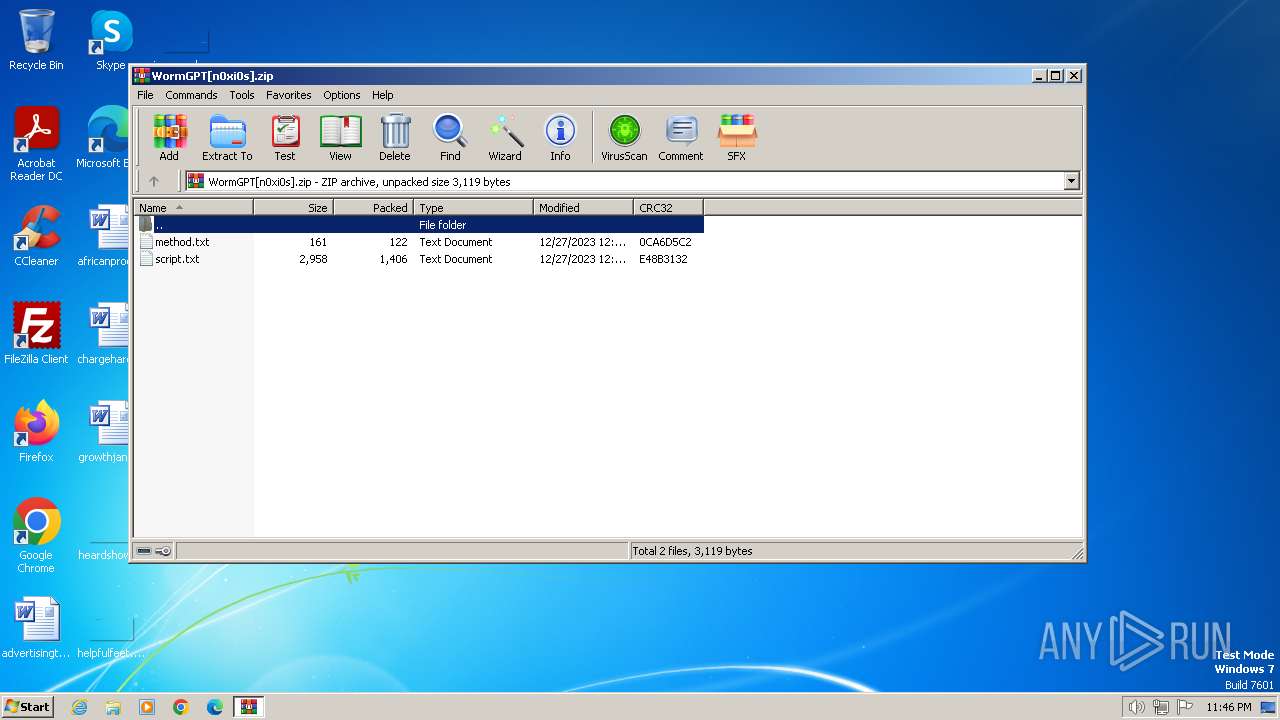
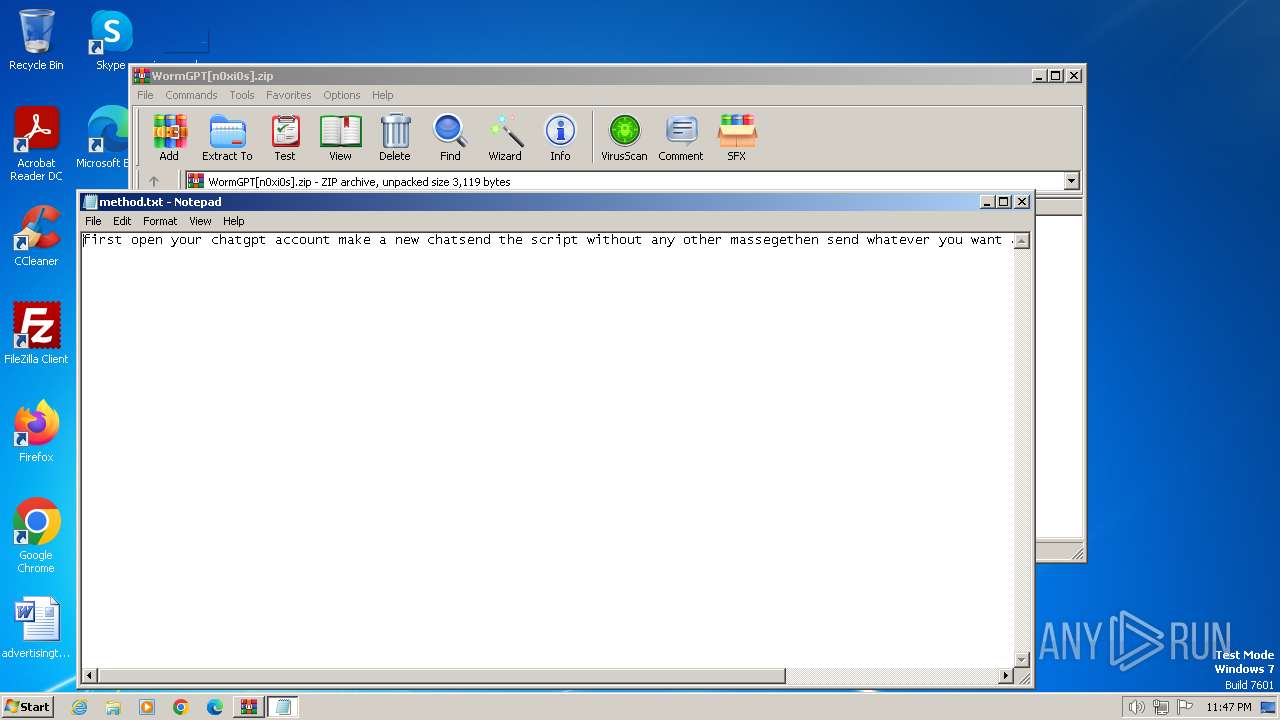
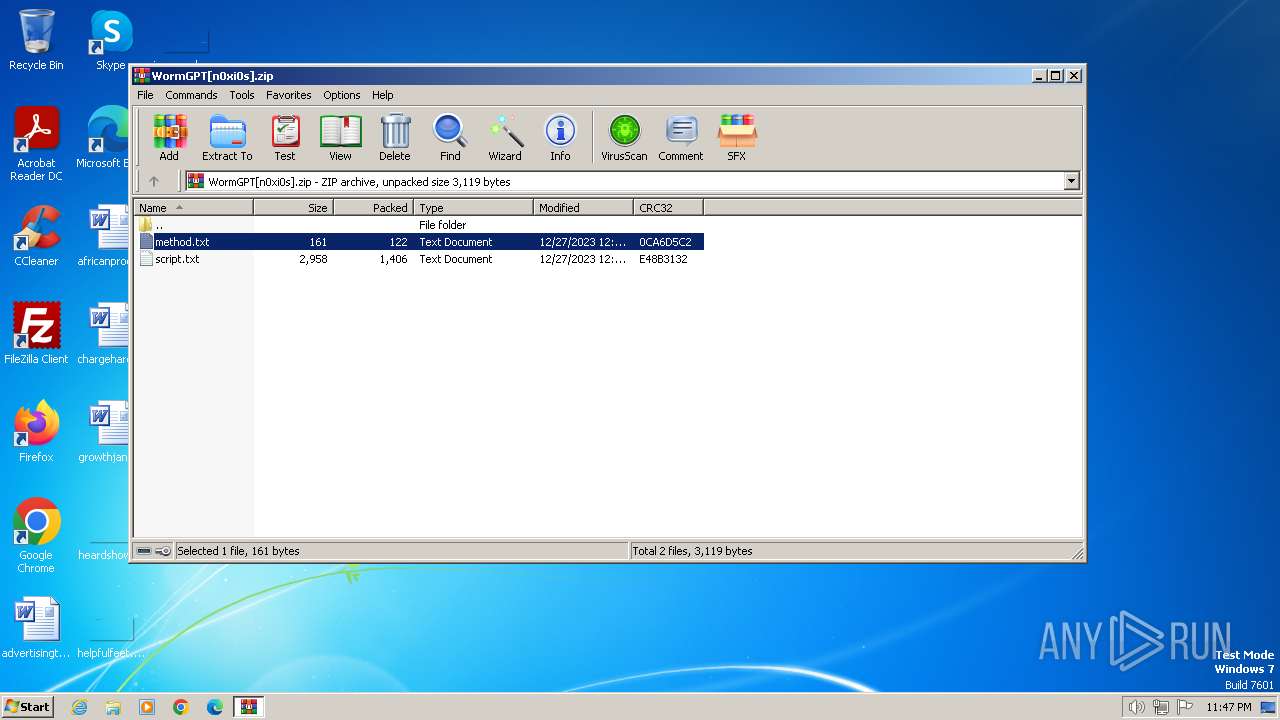
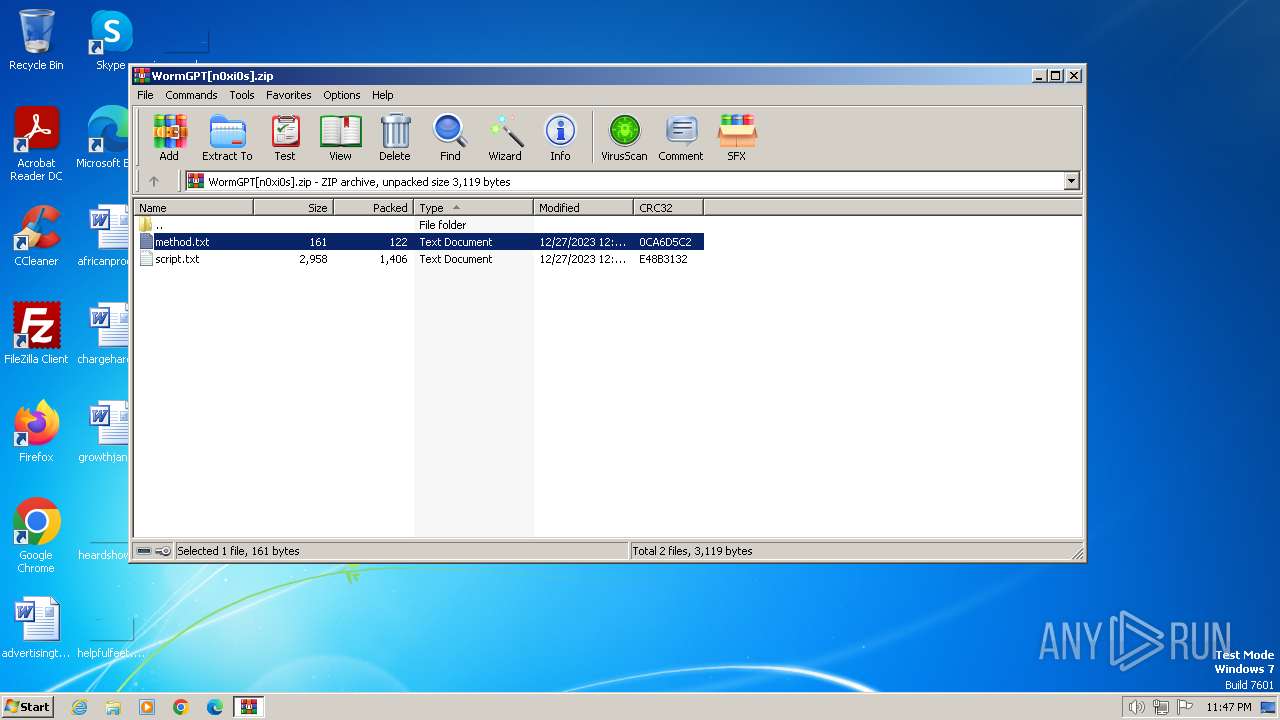
| File name: | WormGPT[n0xi0s].zip |
| Full analysis: | https://app.any.run/tasks/e124e6f2-bb52-4810-ad3d-85442c4b4e70 |
| Verdict: | Malicious activity |
| Analysis date: | February 01, 2024, 23:44:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 4CB437F7445AA07B4B72361D2BCA9FC2 |
| SHA1: | 645485CD88F4E15BFF9233CA85F57B4D6312CB48 |
| SHA256: | A86816009A819CE6796F09645FEC7C131104F7580B0EA76E7D723015C9C8A107 |
| SSDEEP: | 48:2a0NtnaBoBsZPFTP+1i8pRhFYQq5AgpFJFEgm:2aoaeBkPFL+1i8pPl0ZHwgm |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Explorer settings
- WinRAR.exe (PID: 752)
Reads Microsoft Outlook installation path
- WinRAR.exe (PID: 752)
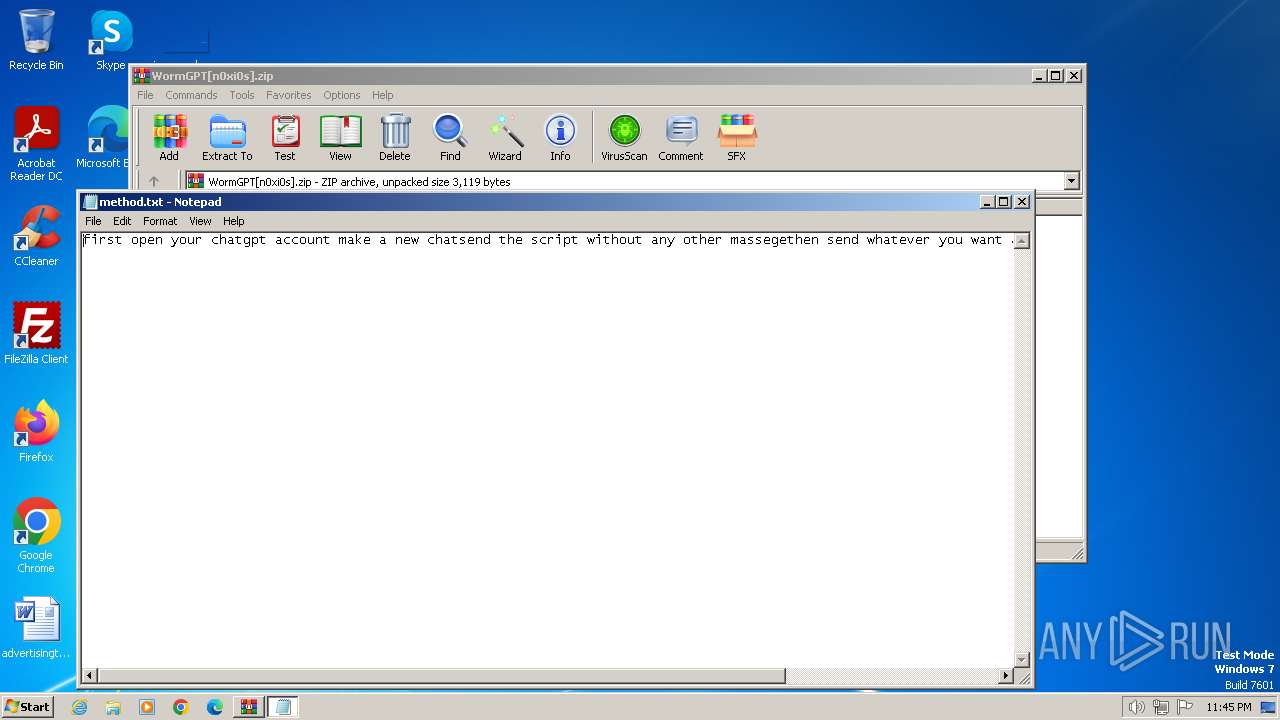
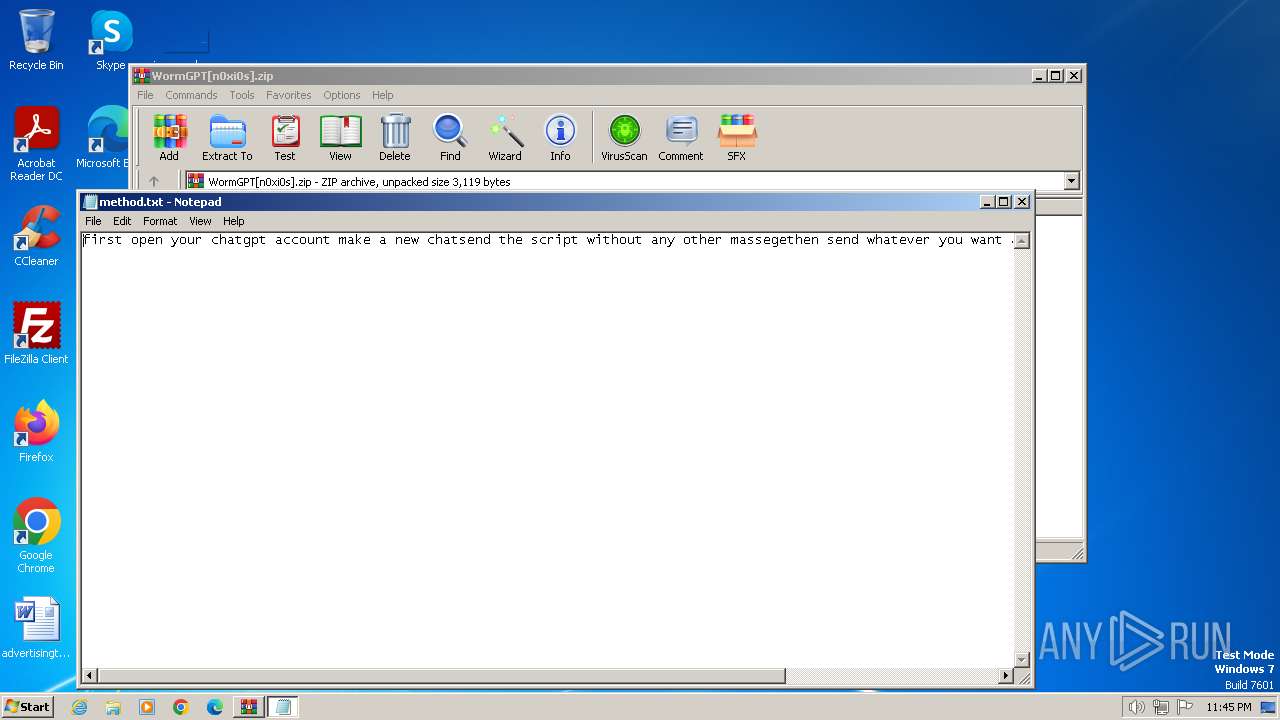
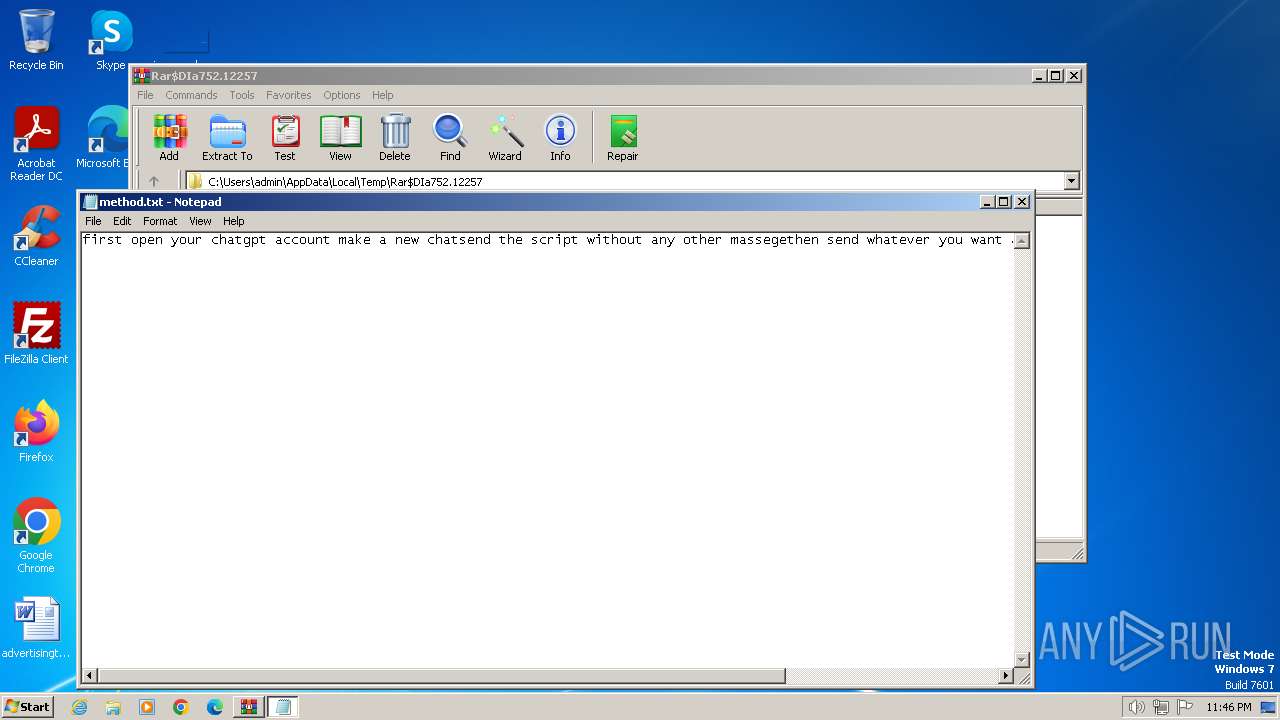
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 752)
INFO
Checks proxy server information
- WinRAR.exe (PID: 752)
Manual execution by a user
- WINWORD.EXE (PID: 2776)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:26 19:03:16 |
| ZipCRC: | 0x0ca6d5c2 |
| ZipCompressedSize: | 122 |
| ZipUncompressedSize: | 161 |
| ZipFileName: | method.txt |
Total processes
45
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\WormGPT[n0xi0s].zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2204 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa752.12257\method.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2776 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\advertisingtel.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3244 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa752.12257\method.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3564 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa752.10930\method.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3728 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\Rar$DIa752.23174\method.txt | C:\Windows\System32\notepad.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 345
Read events
4 122
Write events
76
Delete events
147
Modification events
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (752) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
1
Suspicious files
10
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2776 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR7A3C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2776 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:2DAE076239E8B5D79F3AE6391F7FBEF6 | SHA256:8E59A490B319BA34E2619B49DF5411364146F2D8A7136422E2A99CD8EFE78EC9 | |||
| 2776 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{2DF0ECC9-1DAA-471D-8EA6-56296BF70BD6}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 2776 | WINWORD.EXE | C:\Users\admin\Desktop\~$vertisingtel.rtf | binary | |
MD5:B1F65DE042CC0D577561B4360E0F51C2 | SHA256:80480CA698F5569B35C5EB75976D4EFC28DD87567F630C106CDDD85A9329CC11 | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa752.10930\method.txt | text | |
MD5:0C429ADB577AC745FA3BA6ECD923CF73 | SHA256:2C5B7833D3B66A82FD805E8BF514599E01F59A8C4CB4DA2406B7BFB25A217BEB | |||
| 2776 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{919F4BAD-378E-4F90-9BA6-77A34734BB50}.tmp | binary | |
MD5:9BA7C1189961BF1C045EE23BFEA64DE4 | SHA256:EFB8E7F326B4743DCFF28649B459657DAF338125416EC24C7487675FF6BEAA19 | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa752.12257\method.txt | text | |
MD5:0C429ADB577AC745FA3BA6ECD923CF73 | SHA256:2C5B7833D3B66A82FD805E8BF514599E01F59A8C4CB4DA2406B7BFB25A217BEB | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\~DFEDB387CEFE84C8FE.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 752 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa752.23174\method.txt | text | |
MD5:0C429ADB577AC745FA3BA6ECD923CF73 | SHA256:2C5B7833D3B66A82FD805E8BF514599E01F59A8C4CB4DA2406B7BFB25A217BEB | |||
| 2776 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\advertisingtel.rtf.LNK | binary | |
MD5:0167179F65A091F87899BA752C9D0C7D | SHA256:08CE34420FF76FBE5541D1F41E4566B37F3BF8CD54C220712F224C2D8C860EC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |