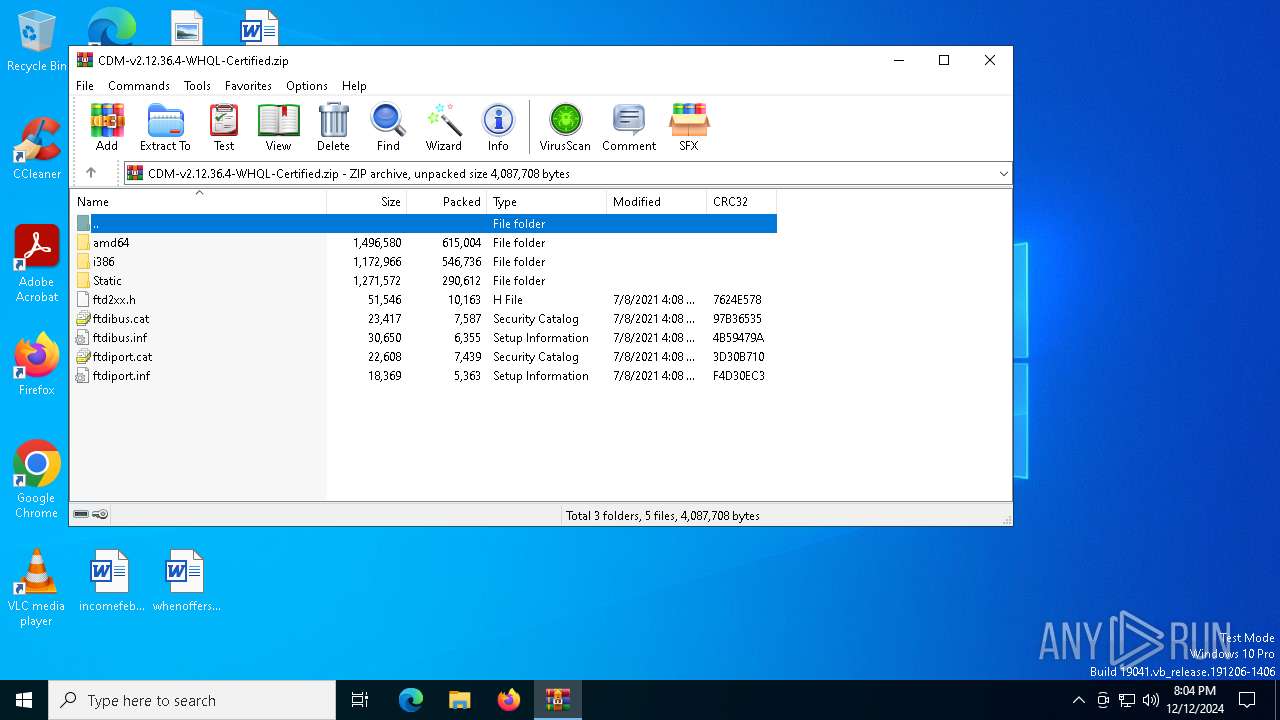
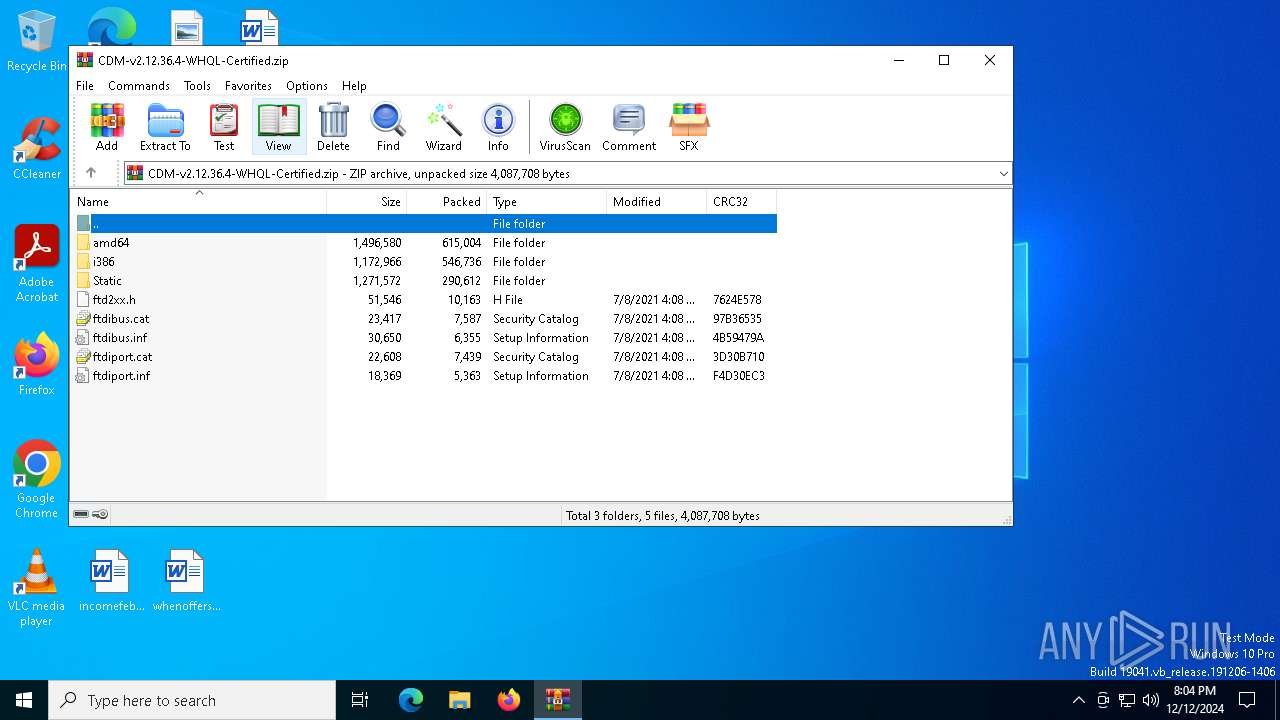
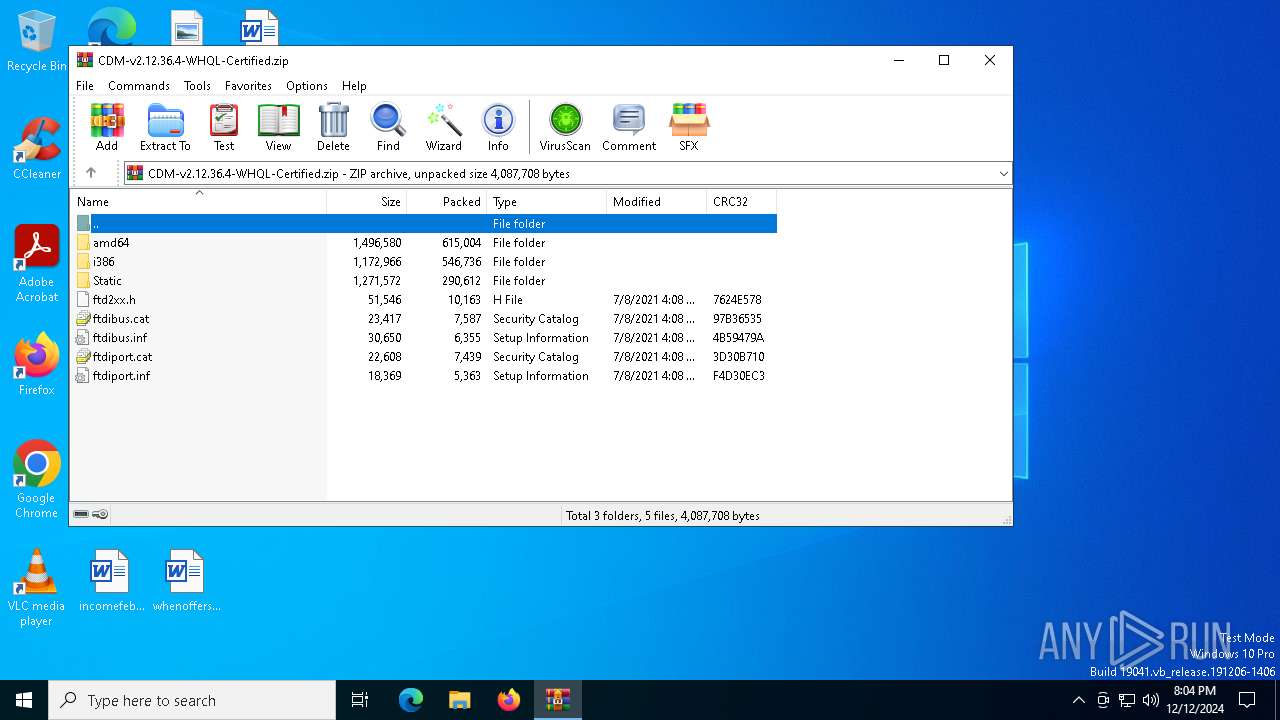
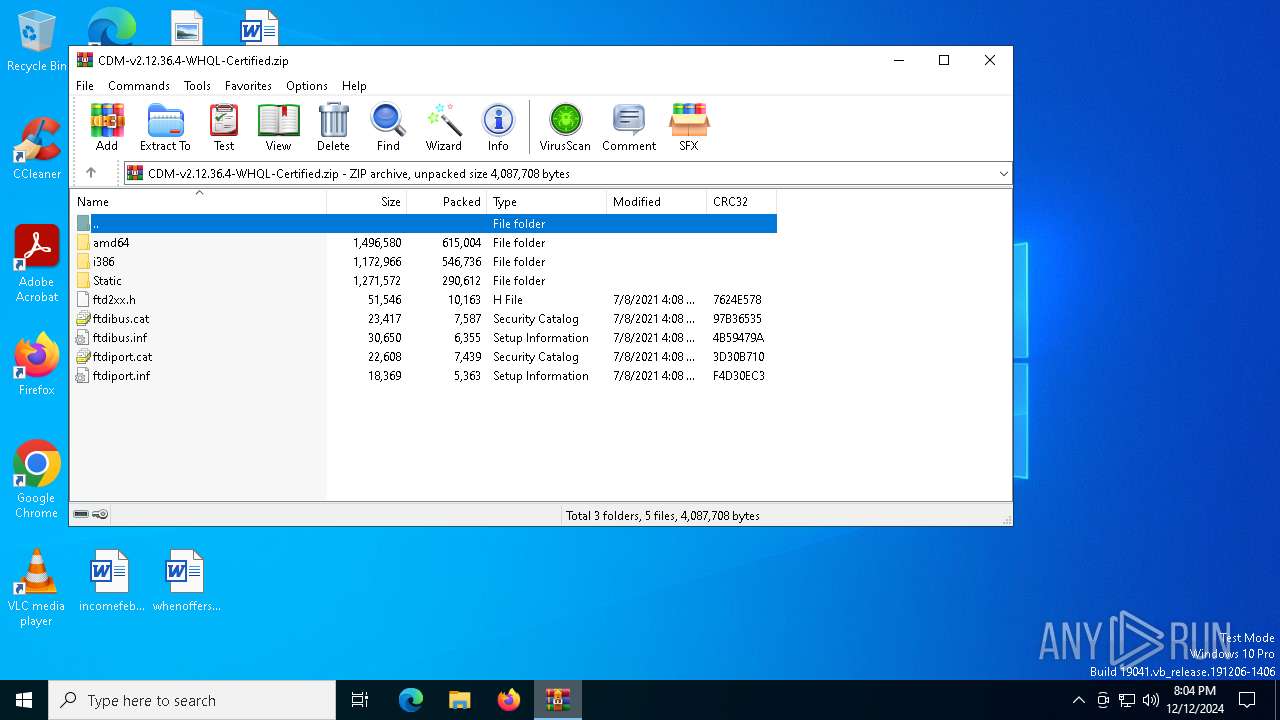
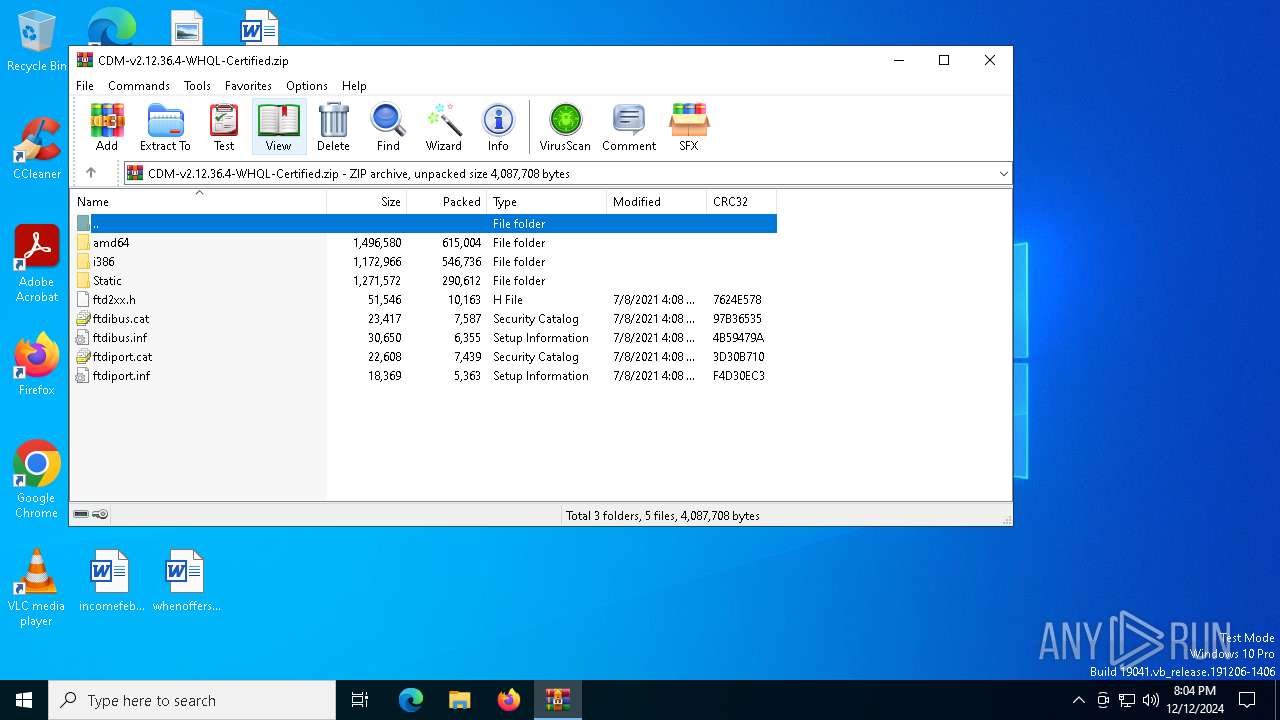
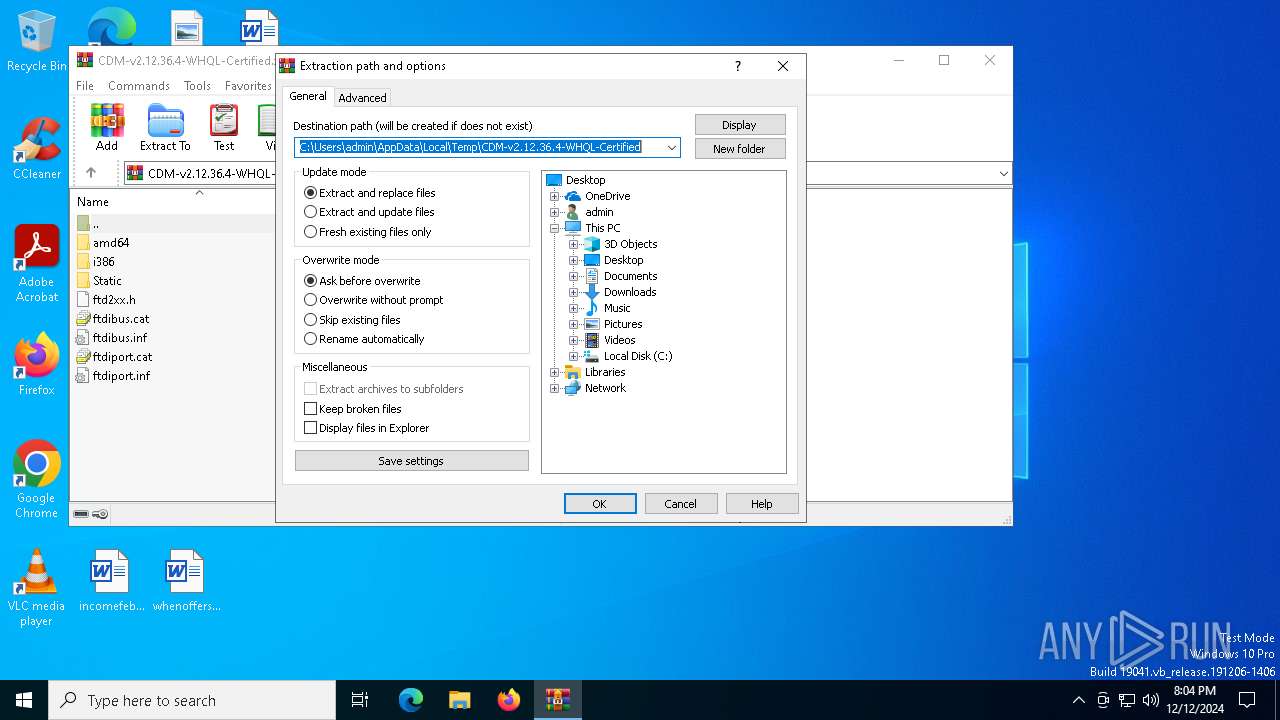
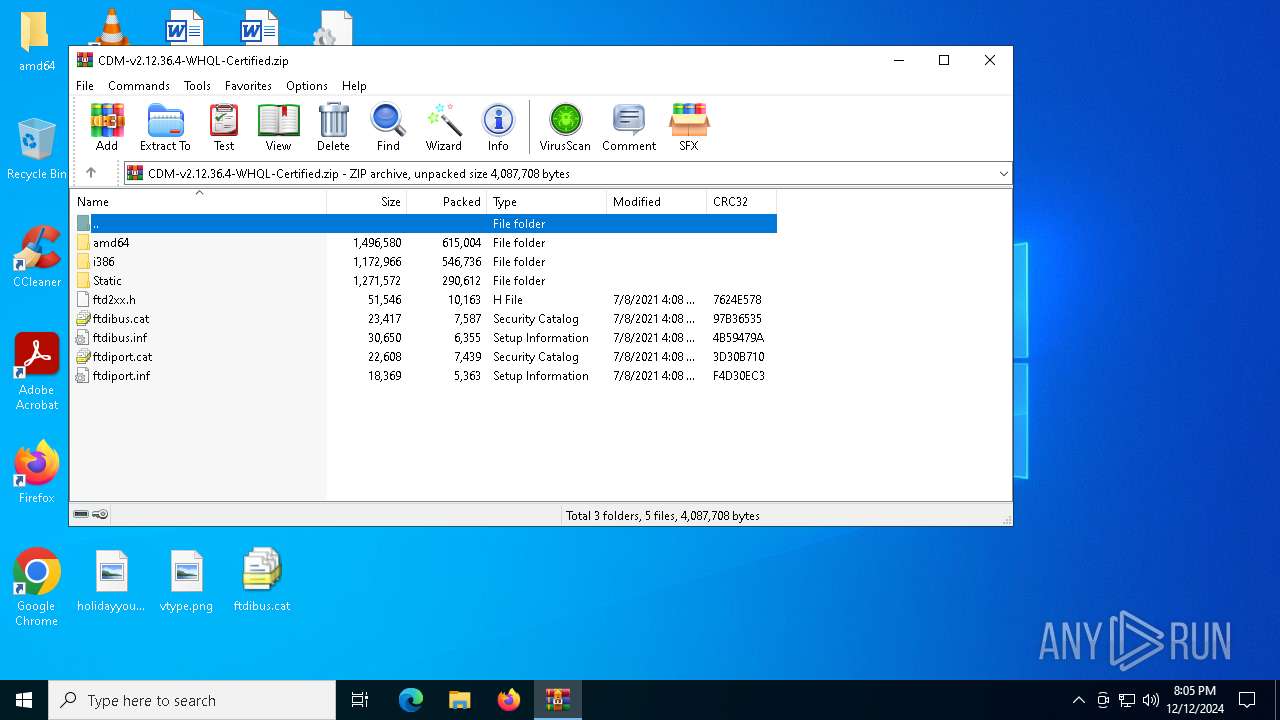
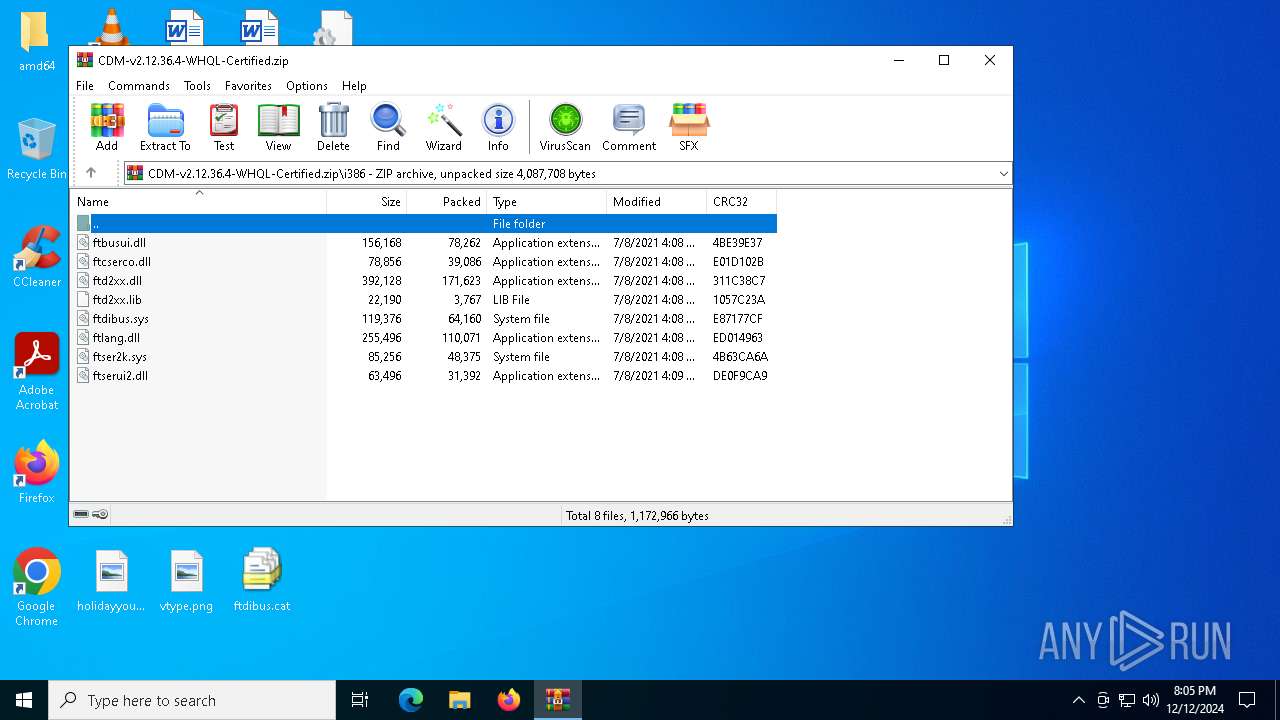
| File name: | CDM-v2.12.36.4-WHQL-Certified.zip |
| Full analysis: | https://app.any.run/tasks/635b02ad-c3b9-4ff0-b98c-002e44fbf56b |
| Verdict: | Malicious activity |
| Analysis date: | December 12, 2024, 20:04:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 6004A4F36FE7BEB06DC86245C4EC3D1B |
| SHA1: | 232237DA18D6615EC79435DB32DF00E9AEB70742 |
| SHA256: | A8654CAA76151E92161E2767294337039189AC3BAB3A794DBAC791CD1901172B |
| SSDEEP: | 24576:sYcAdu8I7q7tMSi5dWZ1bLUVVzkka9J4K/lKB/vH/xHtmss8RpO5p6DXSS+B0acf:sYNuL7q5Mj5dWZdLUVKv9rY/vuvslSSb |
MALICIOUS
No malicious indicators.SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6520)
- InfDefaultInstall.exe (PID: 3620)
- drvinst.exe (PID: 3420)
Executable content was dropped or overwritten
- InfDefaultInstall.exe (PID: 3620)
- drvinst.exe (PID: 3420)
Creates files in the driver directory
- drvinst.exe (PID: 3420)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6520)
- drvinst.exe (PID: 3420)
- InfDefaultInstall.exe (PID: 3620)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6520)
The process uses the downloaded file
- WinRAR.exe (PID: 6520)
Manual execution by a user
- InfDefaultInstall.exe (PID: 3620)
- InfDefaultInstall.exe (PID: 3140)
Create files in a temporary directory
- InfDefaultInstall.exe (PID: 3620)
Reads the software policy settings
- drvinst.exe (PID: 3420)
Reads the machine GUID from the registry
- drvinst.exe (PID: 3420)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:07:08 16:08:34 |
| ZipCRC: | 0x8b6eac4f |
| ZipCompressedSize: | 80887 |
| ZipUncompressedSize: | 168456 |
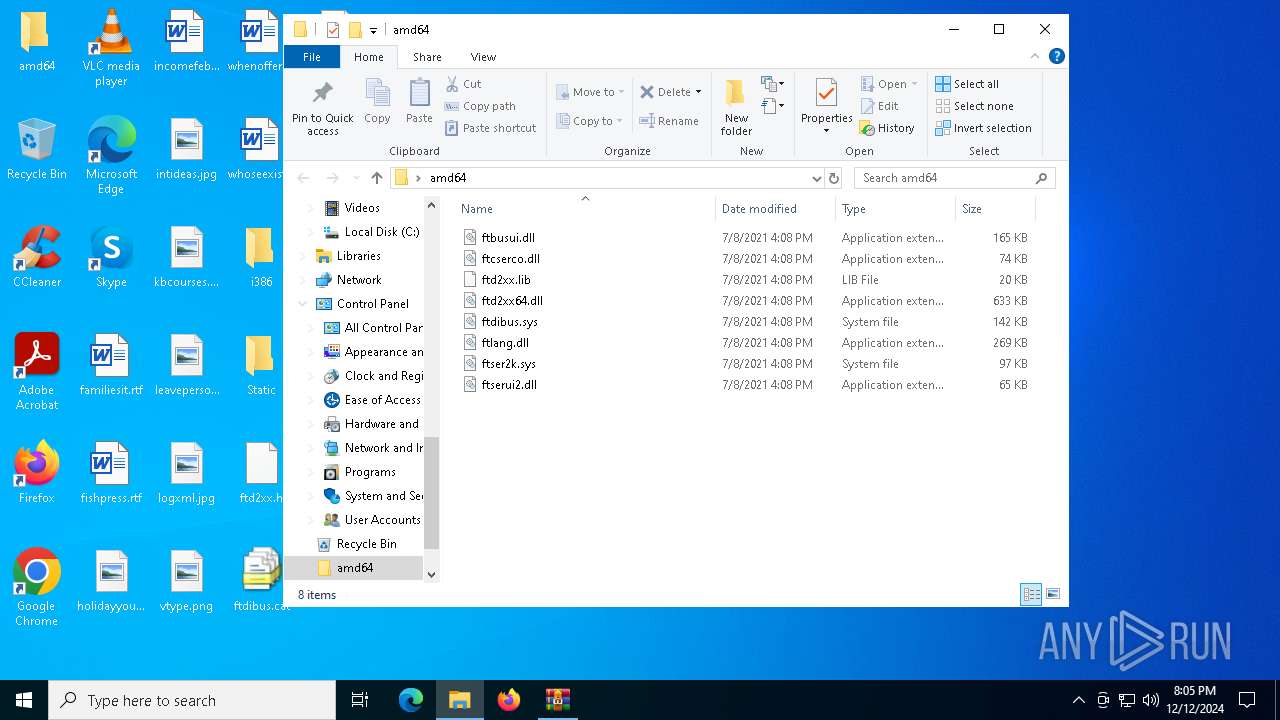
| ZipFileName: | amd64/ftbusui.dll |
Total processes
134
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3140 | "C:\WINDOWS\System32\InfDefaultInstall.exe" "C:\Users\admin\Desktop\ftdibus.inf" | C:\Windows\System32\InfDefaultInstall.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: INF Default Install Exit code: 3221226540 Version: 5.2.3668.0 Modules
| |||||||||||||||
| 3420 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{abbb5e23-e6b8-2a48-9927-c6d68e0be8f9}\ftdibus.inf" "9" "44db9b62f" "0000000000000174" "WinSta0\Default" "00000000000001E0" "208" "C:\Users\admin\Desktop" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3620 | "C:\WINDOWS\System32\InfDefaultInstall.exe" "C:\Users\admin\Desktop\ftdibus.inf" | C:\Windows\System32\InfDefaultInstall.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: INF Default Install Exit code: 0 Version: 5.2.3668.0 Modules
| |||||||||||||||
| 6056 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6520 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
6 288
Read events
6 247
Write events
16
Delete events
25
Modification events
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified.zip | |||
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6520) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
Executable files
49
Suspicious files
14
Text files
12
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\amd64\ftbusui.dll | executable | |
MD5:D79A5E34F684B547FA2F963DFCC15A21 | SHA256:4BBC0B301A7C5A6B1B73878CE3AEEB191F5FCEAC05835372142206D79AC81559 | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\amd64\ftd2xx64.dll | executable | |
MD5:BEFBC1A8F6C2B8E143DDD97CCB6561B5 | SHA256:774AF8B12C85D03562742ACDF222AF5E0432167BF107BA4B260757E4A5E36866 | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\ftdibus.cat | cat | |
MD5:B392C785B9C2AA31187D1BD0A4F5EBA5 | SHA256:B286055896DEA79D4521368293DEEE801930F3FB503CC3076AC97716B338B0F7 | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\ftd2xx.h | text | |
MD5:08FBBF757A92B079CA66FF62D99A6C82 | SHA256:EE0C6358BA2F13015EC7B07AEA16BF3ADA33508851CC494FC256A8B28AF31147 | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\amd64\ftser2k.sys | executable | |
MD5:B66678FF4E347E22146609B3D5B7B2C4 | SHA256:7A303AA880CC746D13F71E565874FB7C174747372CCF358B928A72219D2A50DD | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\amd64\ftdibus.sys | executable | |
MD5:AB7418C8DFBBB97BEFB4F0ADED3D4663 | SHA256:3BD5BB7E646E67469EC25A37CAA5131CF992759703B0FC170DF7AF265B9F8E74 | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\i386\ftd2xx.lib | obj | |
MD5:0BEC36AA3B1CF8C98D9B4F4A2D433FAE | SHA256:3E9C6D57C4B3563E04B20BE5ADC419A0854D3A2ABAD93A39F49B973B52475314 | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\ftdiport.cat | cat | |
MD5:60238C00694F838EED4757D1CE167D8B | SHA256:113A35E6161F3AE8BB9D0E0F31913872C4B32FD6211ECE27DDDEB238F601EB59 | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\ftdiport.inf | text | |
MD5:B16B75B545A296EFC49805C94DFD334C | SHA256:00627112CF622CC6FB99A6B5DE24FCC61B6D0A211A6BD1E90B985BCF9950F6D9 | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\CDM-v2.12.36.4-WHQL-Certified\i386\ftd2xx.dll | executable | |
MD5:6FFEB45E0137622EBBBA8361107D304E | SHA256:60BB0D6348B1EB0127401AA902F34C963D9196D2778C66F4008A6CF0C6F098A5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
32
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
6748 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4136 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4136 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.5:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |