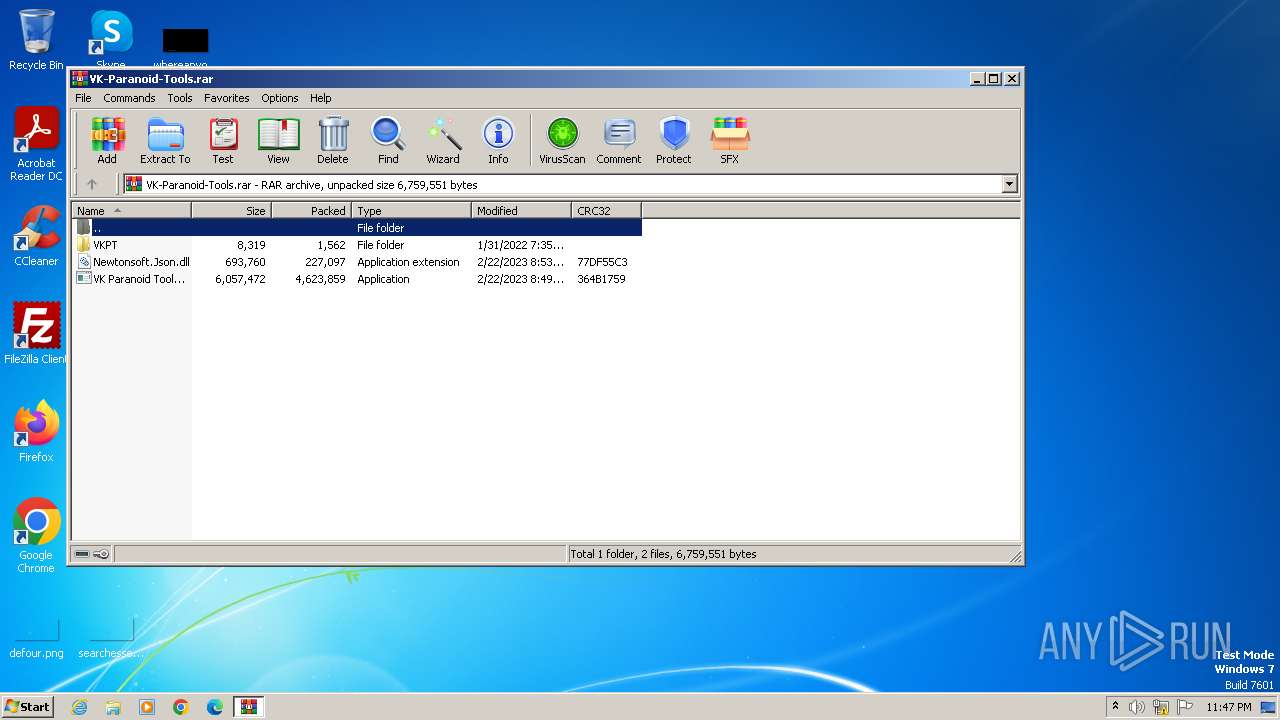
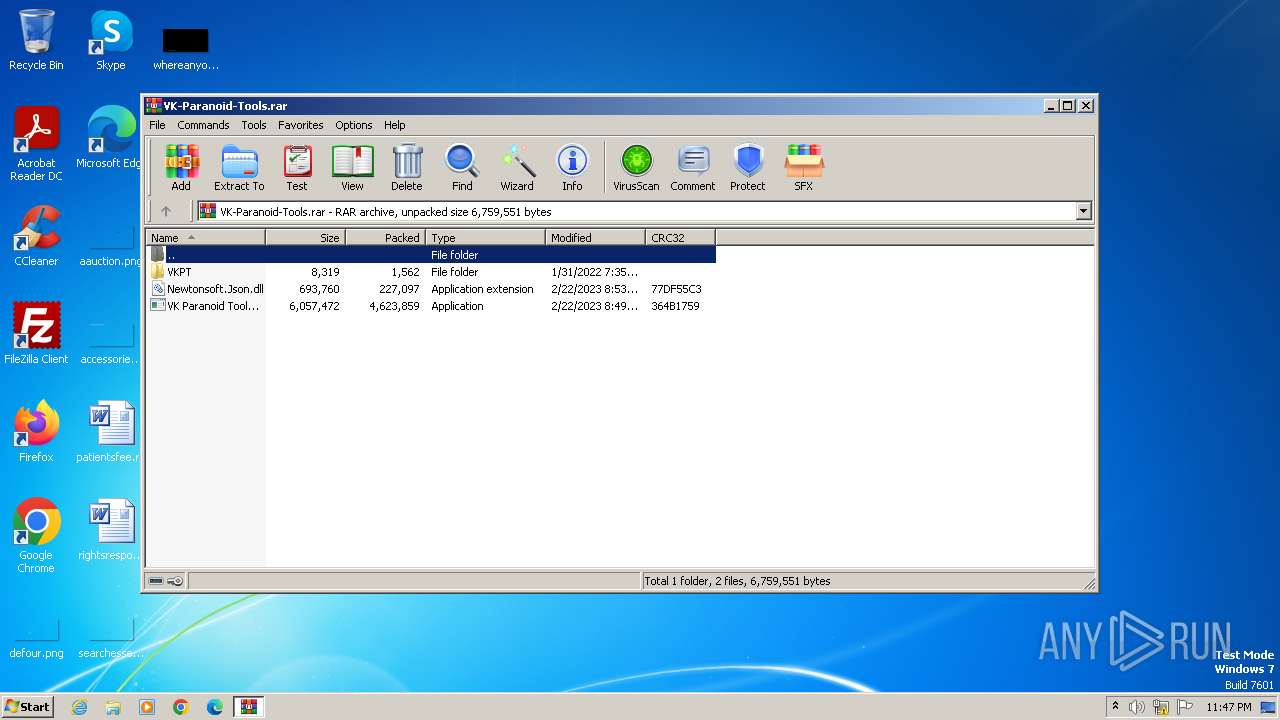
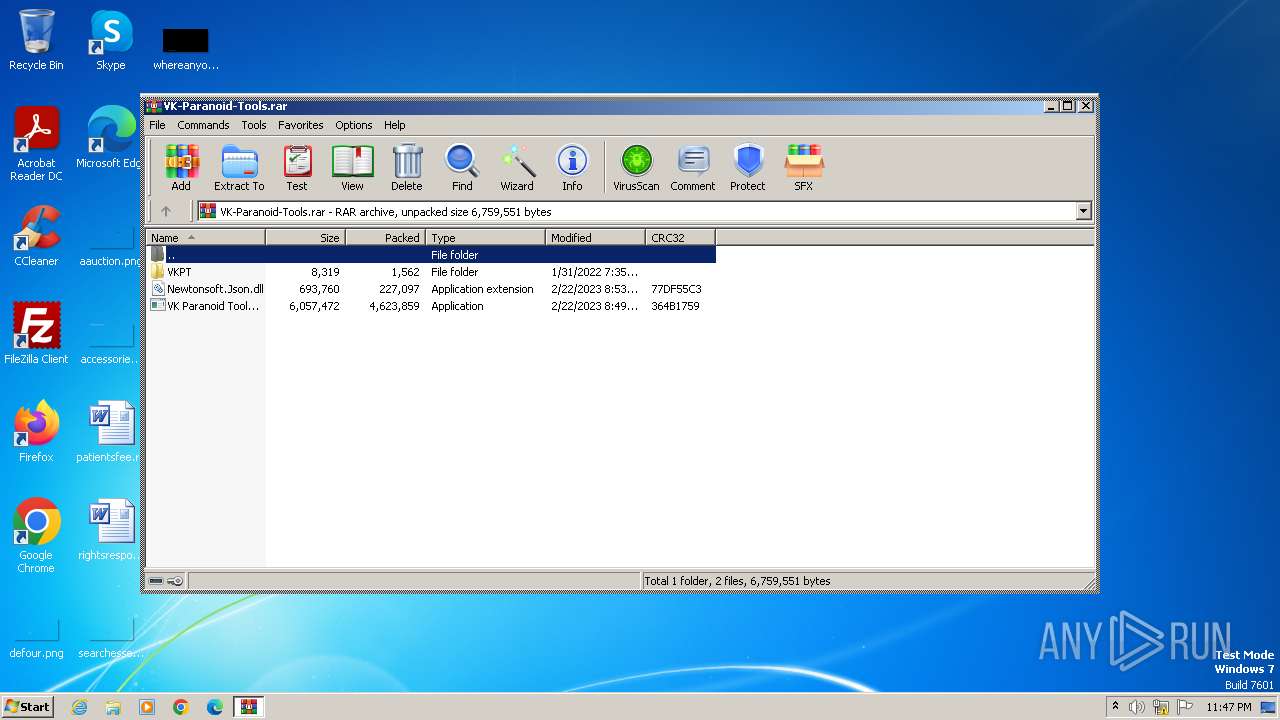
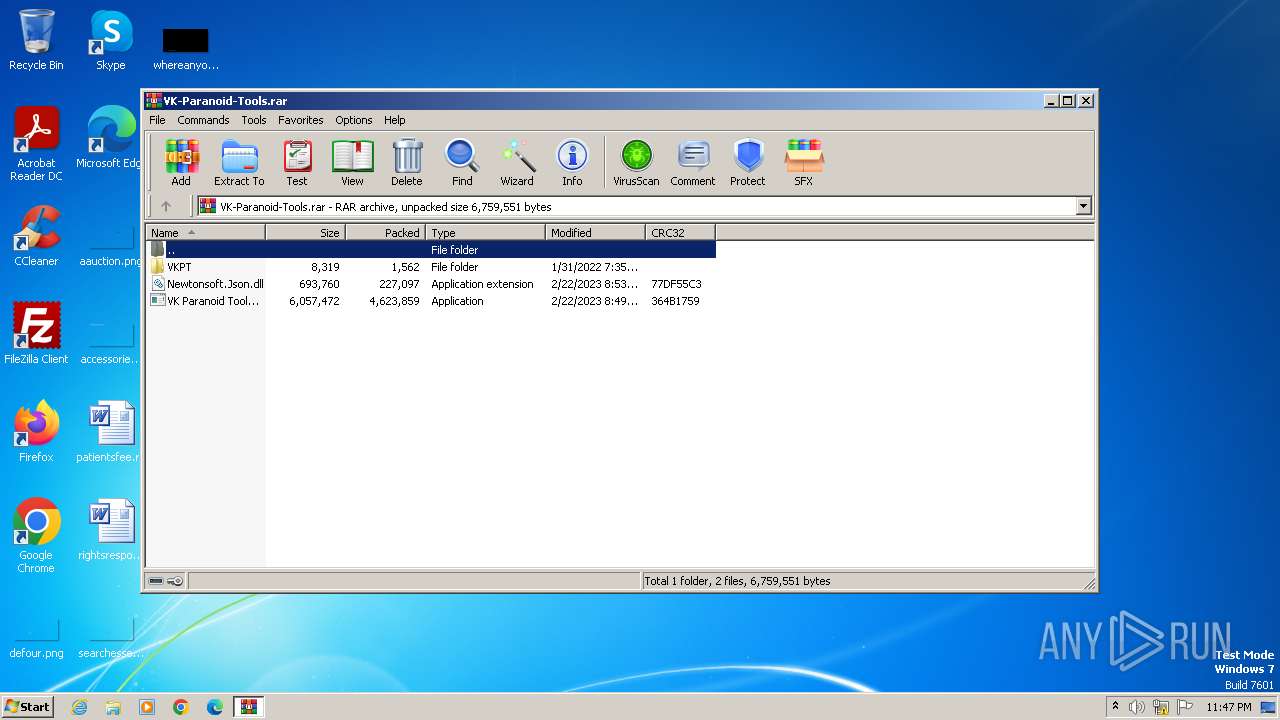
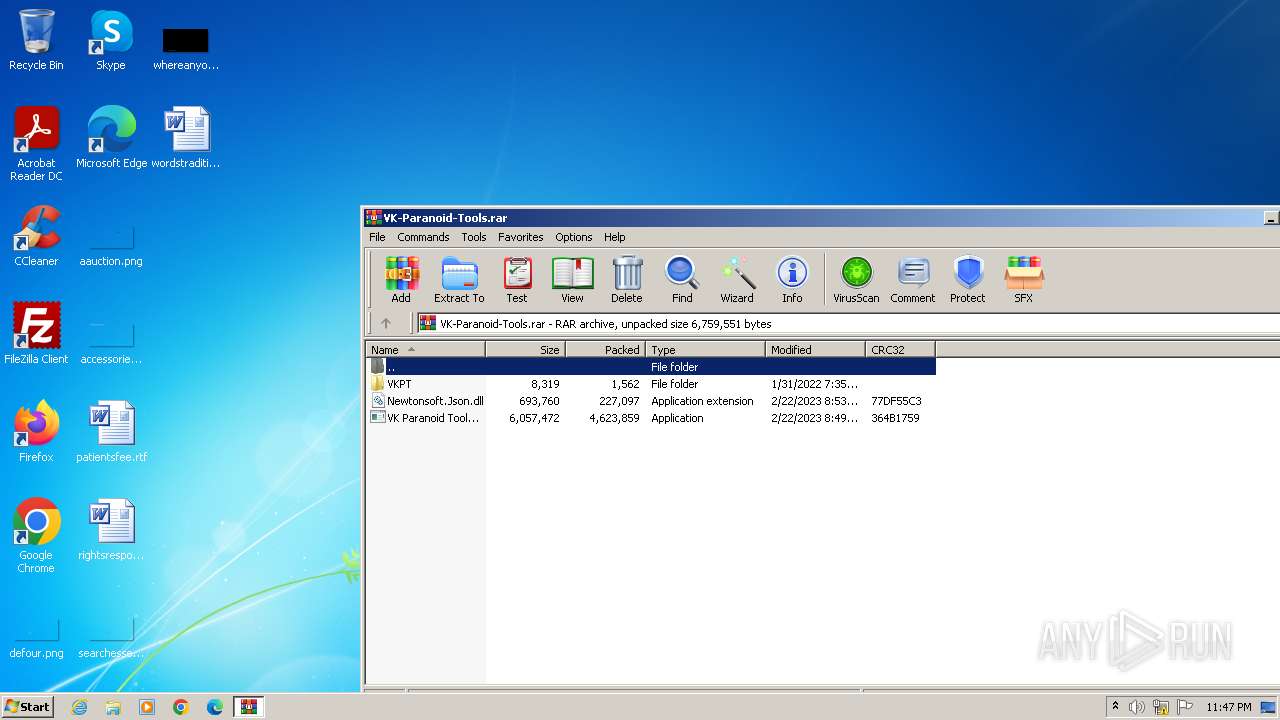
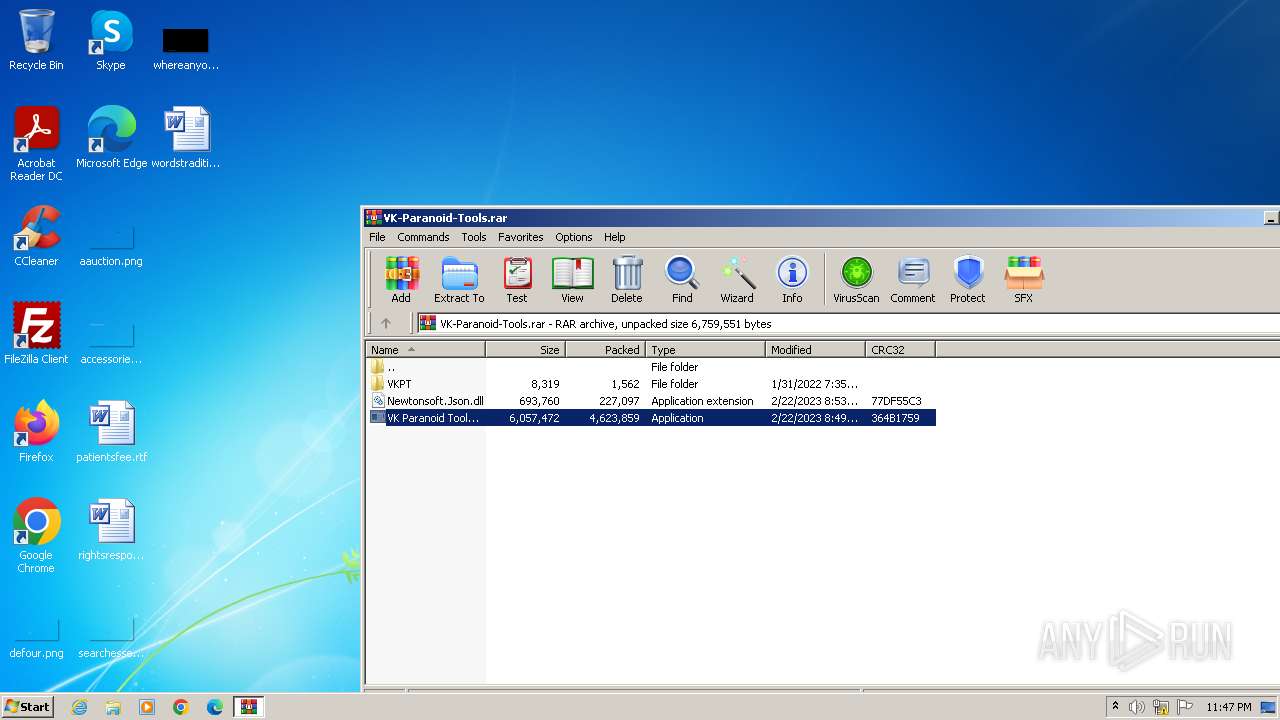
| File name: | VK-Paranoid-Tools.rar |
| Full analysis: | https://app.any.run/tasks/76349695-96ee-47e3-9ee2-98bdaab7bd47 |
| Verdict: | Malicious activity |
| Analysis date: | June 10, 2024, 22:46:58 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 7E80D708585823336B4351233C5E7D34 |
| SHA1: | F7CBA9AFCD954F9CF3D49010CFE2E0385A8189F7 |
| SHA256: | A86121D9B19C769ACDCB4B86BB983D51926553DE82F1D1D0AC62982C31E99A1D |
| SSDEEP: | 98304:V1DE5uB8n50DOwNbM1v1yX5ZyDhA/REPWlkweqcahJFlaGpo3p9NAZoIpiK2pdir:0Pum5b2I2Zz |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3984)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3984)
- VK Paranoid Tools.exe (PID: 4060)
Reads the Internet Settings
- VK Paranoid Tools.exe (PID: 4060)
Reads settings of System Certificates
- VK Paranoid Tools.exe (PID: 4060)
Reads Microsoft Outlook installation path
- VK Paranoid Tools.exe (PID: 4060)
Checks Windows Trust Settings
- VK Paranoid Tools.exe (PID: 4060)
Reads Internet Explorer settings
- VK Paranoid Tools.exe (PID: 4060)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3984)
Checks supported languages
- VK Paranoid Tools.exe (PID: 4060)
- wmpnscfg.exe (PID: 1620)
Reads the computer name
- VK Paranoid Tools.exe (PID: 4060)
- wmpnscfg.exe (PID: 1620)
Reads Environment values
- VK Paranoid Tools.exe (PID: 4060)
Reads the machine GUID from the registry
- VK Paranoid Tools.exe (PID: 4060)
Disables trace logs
- VK Paranoid Tools.exe (PID: 4060)
Checks proxy server information
- VK Paranoid Tools.exe (PID: 4060)
Reads the software policy settings
- VK Paranoid Tools.exe (PID: 4060)
Creates files or folders in the user directory
- VK Paranoid Tools.exe (PID: 4060)
Manual execution by a user
- wmpnscfg.exe (PID: 1620)
Process checks whether UAC notifications are on
- VK Paranoid Tools.exe (PID: 4060)
Application launched itself
- iexplore.exe (PID: 1704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
40
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1620 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1944 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1704 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3984 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\VK-Paranoid-Tools.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4060 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.46275\VK Paranoid Tools.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.46275\VK Paranoid Tools.exe | WinRAR.exe | ||||||||||||
User: admin Company: VKPT Software Integrity Level: MEDIUM Description: VK Paranoid Tools Version: 2.0.0.8 Modules
| |||||||||||||||
Total events
25 356
Read events
25 125
Write events
182
Delete events
49
Modification events
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\VK-Paranoid-Tools.rar | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3984) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
4
Suspicious files
16
Text files
41
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\VK-Paranoid-Tools\VK Paranoid Tools.exe | executable | |
MD5:0BA1D5D2E90FDF7CD4DD64372C11B382 | SHA256:ADB0B5734D84190C349ADA88EC2CC79DAFF8DB164ED06271B811BAAF0BFEFE33 | |||
| 4060 | VK Paranoid Tools.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\1WY87JBL.txt | text | |
MD5:5098F7C6D8693E1A34B5C0BD5E8B034F | SHA256:8D7892BBFDF018722B349EF5026E9E55E2A65F5B6EA798AD360724D077055B0F | |||
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.46275\VKPT\Settings.pts | pi2 | |
MD5:BF4D202D5A850A732B4E9A080A77E4F1 | SHA256:C3E567BA6523487EDFD5FB02839DCC848C877EE937141B2629057375C05DA766 | |||
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.46275\VK Paranoid Tools.exe | executable | |
MD5:0BA1D5D2E90FDF7CD4DD64372C11B382 | SHA256:ADB0B5734D84190C349ADA88EC2CC79DAFF8DB164ED06271B811BAAF0BFEFE33 | |||
| 4060 | VK Paranoid Tools.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\base.ec2ae8ae[1].css | text | |
MD5:F2C0C93220E42476FAFFF67AB2C11169 | SHA256:C45807DF5BC4B33DDE32D6D021EFABED8070EB36790508DFAD15D097AE60BF3F | |||
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\VK-Paranoid-Tools\VKPT\Settings.pts | pi2 | |
MD5:BF4D202D5A850A732B4E9A080A77E4F1 | SHA256:C3E567BA6523487EDFD5FB02839DCC848C877EE937141B2629057375C05DA766 | |||
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\VK-Paranoid-Tools\Newtonsoft.Json.dll | executable | |
MD5:8F2EF6D6DECCED70370270DAFA84AADD | SHA256:517E2BACE9ADBDB906A5B28C76E6C07CF28A5BF70FE35D34DB78E8F9530848B3 | |||
| 4060 | VK Paranoid Tools.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\common.a532912c[1].css | text | |
MD5:CAC7B9323F7E897D375F281429D18CA6 | SHA256:926E95CC28AE328D53902433D031DFB14A3349BCB54FEFB2EF050133E91126F9 | |||
| 3984 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3984.46275\Newtonsoft.Json.dll | executable | |
MD5:8F2EF6D6DECCED70370270DAFA84AADD | SHA256:517E2BACE9ADBDB906A5B28C76E6C07CF28A5BF70FE35D34DB78E8F9530848B3 | |||
| 4060 | VK Paranoid Tools.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\66F835E41EC6A985EB9271E4A70169D7_CF44E3C99F7F4AC558EEB35244F7E046 | der | |
MD5:4129A2FD6F7CA8AE12CC8F4C55754D75 | SHA256:E58D81FF4D05598130D0DD3FC645BE0600F49ED5B86DAF9AFFA7BA457DFD89CC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
34
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4060 | VK Paranoid Tools.exe | POST | 200 | 172.67.165.160:80 | http://vkpt.info/core/204/two.php | unknown | — | — | unknown |
4060 | VK Paranoid Tools.exe | POST | 200 | 172.67.165.160:80 | http://vkpt.info/core/204/twelve.php | unknown | — | — | unknown |
4060 | VK Paranoid Tools.exe | POST | 200 | 172.67.165.160:80 | http://vkpt.info/core/204/six.php | unknown | — | — | unknown |
4060 | VK Paranoid Tools.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr5/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQiD0S5cIHyfrLTJ1fvAkJWflH%2B2QQUPeYpSJvqB8ohREom3m7e0oPQn1kCDQHuXyKVQkkF%2BQGRqNw%3D | unknown | — | — | unknown |
4060 | VK Paranoid Tools.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gseccovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSTMjK03nNiYoQYvu4Izyfn9OJNdAQUWHuOdSr%2BYYCqkEABrtboB0ZuP0gCDHmsXXQgoaZQ4a3ukw%3D%3D | unknown | — | — | unknown |
1944 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCDQHuXyId%2FGI71DM6hVc%3D | unknown | — | — | unknown |
1944 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gseccovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBSTMjK03nNiYoQYvu4Izyfn9OJNdAQUWHuOdSr%2BYYCqkEABrtboB0ZuP0gCDB8VCpIoQMc6D1nxwA%3D%3D | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 23.33.27.106:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?59797f4bc62666b4 | unknown | — | — | unknown |
1704 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
1944 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp.globalsign.com/gsrsaovsslca2018/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBRrcGT%2BanRD3C1tW3nsrKeuXC7DPwQU%2BO9%2F8s14Z6jeb48kjYjxhwMCs%2BsCDFMnLpLoNNSL80QG5w%3D%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4060 | VK Paranoid Tools.exe | 172.67.165.160:80 | vkpt.info | CLOUDFLARENET | US | unknown |
4060 | VK Paranoid Tools.exe | 95.213.56.1:443 | oauth.vk.com | VKontakte Ltd | RU | unknown |
4060 | VK Paranoid Tools.exe | 23.33.27.107:80 | ctldl.windowsupdate.com | Akamai International B.V. | FR | unknown |
4060 | VK Paranoid Tools.exe | 104.18.20.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | shared |
4060 | VK Paranoid Tools.exe | 87.240.129.133:443 | vk.com | VKontakte Ltd | RU | unknown |
1944 | iexplore.exe | 87.240.129.133:443 | vk.com | VKontakte Ltd | RU | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
vkpt.info |
| malicious |
oauth.vk.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
vk.com |
| whitelisted |
m.vk.com |
| whitelisted |
st6-21.vk.com |
| unknown |
sun6-22.userapi.com |
| unknown |
sun6-21.userapi.com |
| whitelisted |