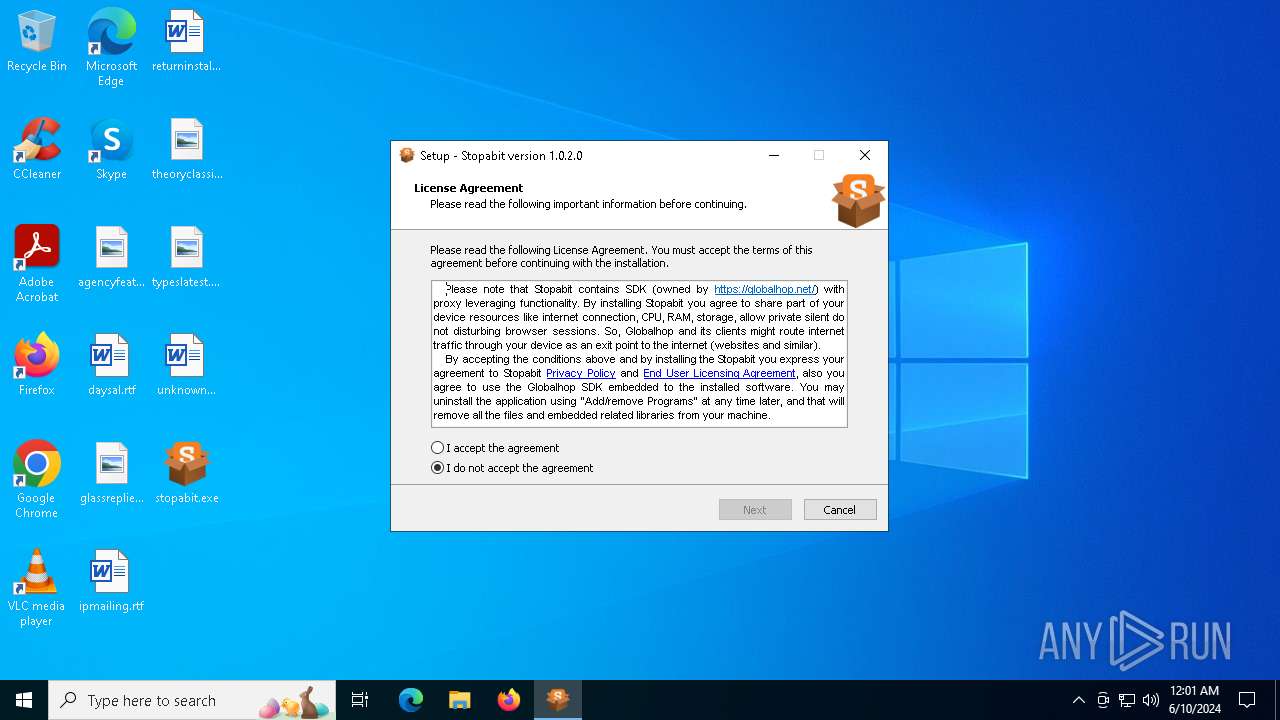
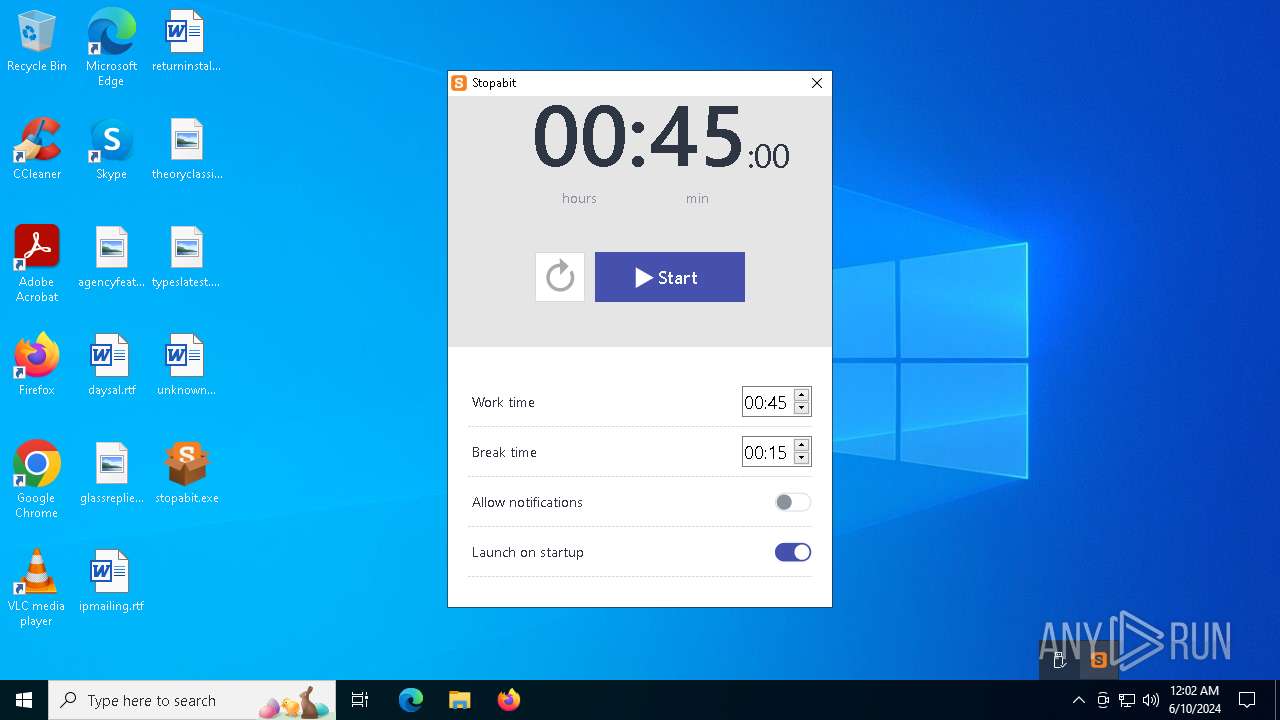
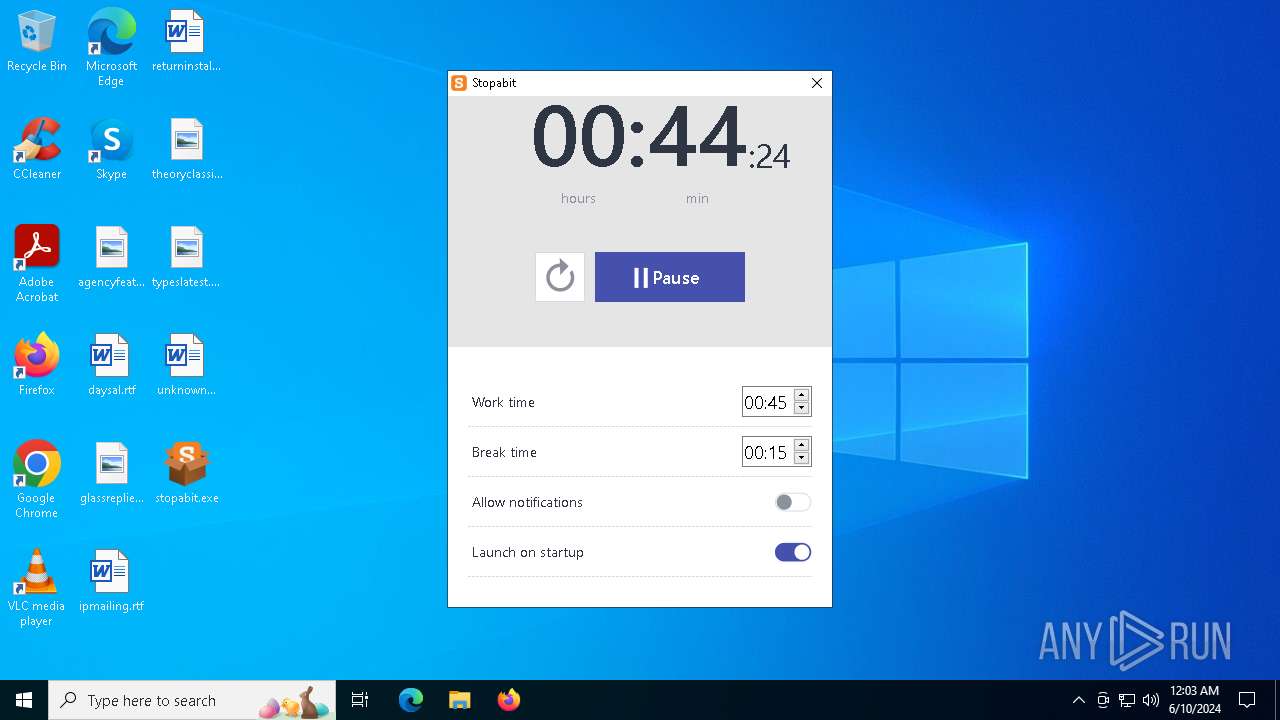
| File name: | stopabit.exe |
| Full analysis: | https://app.any.run/tasks/6225454a-f91a-43aa-b42c-07d3c91e1b06 |
| Verdict: | Malicious activity |
| Analysis date: | June 10, 2024, 00:01:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 69BF068D2015B017D1B013BCE883D26D |
| SHA1: | F9DFA607AB08D456F01D5322B601670CE61D0AE7 |
| SHA256: | A832013E3DC290A2B569EE22E8F0F57DCCA23C8309F45D998A9CA85835A92E13 |
| SSDEEP: | 98304:++cD4dnE+zcnya86xPRydBCMPgU8LECBADmnR+y4wG3ZlNtlmb8P2lUsb5a6yHRZ:geYcYY |
MALICIOUS
Drops the executable file immediately after the start
- stopabit.exe (PID: 6432)
- stopabit.tmp (PID: 6460)
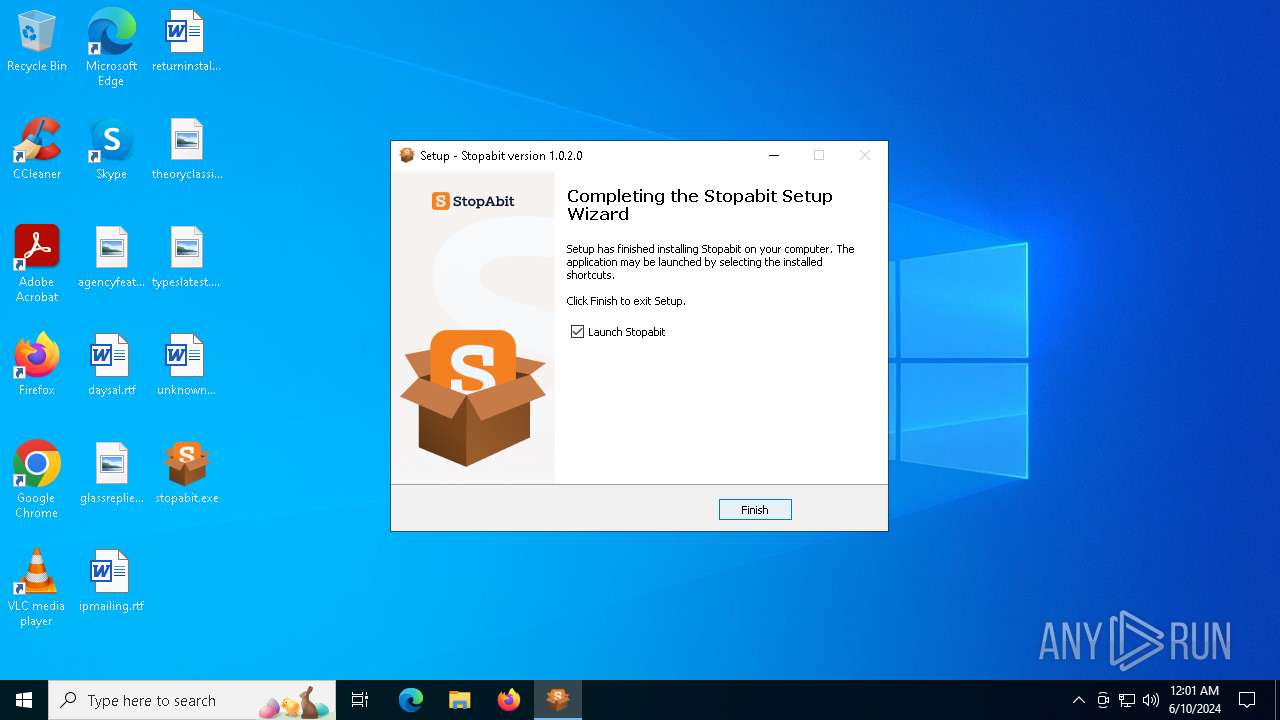
Changes the autorun value in the registry
- Stopabit.exe (PID: 6784)
SUSPICIOUS
Executable content was dropped or overwritten
- stopabit.exe (PID: 6432)
- stopabit.tmp (PID: 6460)
Reads the Windows owner or organization settings
- stopabit.tmp (PID: 6460)
Process drops legitimate windows executable
- stopabit.tmp (PID: 6460)
Reads security settings of Internet Explorer
- Stopabit.exe (PID: 6784)
Checks Windows Trust Settings
- Stopabit.exe (PID: 6784)
Reads Microsoft Outlook installation path
- Stopabit.exe (PID: 6784)
Reads Internet Explorer settings
- Stopabit.exe (PID: 6784)
INFO
Checks supported languages
- stopabit.tmp (PID: 6460)
- stopabit.exe (PID: 6432)
- Stopabit.exe (PID: 6784)
Reads the machine GUID from the registry
- stopabit.tmp (PID: 6460)
- Stopabit.exe (PID: 6784)
Reads the computer name
- stopabit.tmp (PID: 6460)
- Stopabit.exe (PID: 6784)
Create files in a temporary directory
- stopabit.exe (PID: 6432)
- stopabit.tmp (PID: 6460)
Reads the software policy settings
- stopabit.tmp (PID: 6460)
- Stopabit.exe (PID: 6784)
Creates files or folders in the user directory
- stopabit.tmp (PID: 6460)
- Stopabit.exe (PID: 6784)
Creates a software uninstall entry
- stopabit.tmp (PID: 6460)
Checks proxy server information
- Stopabit.exe (PID: 6784)
Reads the time zone
- Stopabit.exe (PID: 6784)
Reads Environment values
- Stopabit.exe (PID: 6784)
Process checks Internet Explorer phishing filters
- Stopabit.exe (PID: 6784)
Disables trace logs
- Stopabit.exe (PID: 6784)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (65.1) |
|---|---|---|
| .exe | | | Win32 EXE PECompact compressed (generic) (24.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.9) |
| .exe | | | Win32 Executable (generic) (2.6) |
| .exe | | | Win16/32 Executable Delphi generic (1.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:04:14 16:10:23+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 74240 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.2.0 |
| ProductVersionNumber: | 1.0.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Stopabit |
| FileDescription: | Stopabit Setup |
| FileVersion: | 1.0.2.0 |
| LegalCopyright: | Copyright © 2023 Stopabit |
| OriginalFileName: | |
| ProductName: | Stopabit |
| ProductVersion: | 1.0.2.0 |
Total processes
125
Monitored processes
3
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6432 | "C:\Users\admin\Desktop\stopabit.exe" | C:\Users\admin\Desktop\stopabit.exe | explorer.exe | ||||||||||||
User: admin Company: Stopabit Integrity Level: MEDIUM Description: Stopabit Setup Exit code: 0 Version: 1.0.2.0 Modules
| |||||||||||||||
| 6460 | "C:\Users\admin\AppData\Local\Temp\is-54BE2.tmp\stopabit.tmp" /SL5="$401DE,2969674,817152,C:\Users\admin\Desktop\stopabit.exe" | C:\Users\admin\AppData\Local\Temp\is-54BE2.tmp\stopabit.tmp | stopabit.exe | ||||||||||||
User: admin Company: Stopabit Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6784 | "C:\Users\admin\AppData\Local\Programs\Stopabit\Stopabit.exe" | C:\Users\admin\AppData\Local\Programs\Stopabit\Stopabit.exe | stopabit.tmp | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Stopabit Version: 1.0.2.0 Modules
| |||||||||||||||
Total events
13 603
Read events
13 544
Write events
53
Delete events
6
Modification events
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 3C190000714A2F5BC9BADA01 | |||
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: E09EBD3A45BED7EA6DC54C33CDD7D097F608E394A20C69562D9F0C9AD3C734C1 | |||
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\Programs\Stopabit\Stopabit.exe | |||
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 9F8CEC090D08AF9053AAE015055E5D05FC1011422AD039F3FCB60F8C79D3870D | |||
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\SlowJobber |
| Operation: | write | Name: | version |
Value: 1.0.2.0 | |||
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FD04524F-249D-425E-81DF-1A30526751D1}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.2.1 | |||
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FD04524F-249D-425E-81DF-1A30526751D1}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Users\admin\AppData\Local\Programs\Stopabit | |||
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FD04524F-249D-425E-81DF-1A30526751D1}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Users\admin\AppData\Local\Programs\Stopabit\ | |||
| (PID) Process: | (6460) stopabit.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{FD04524F-249D-425E-81DF-1A30526751D1}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Stopabit | |||
Executable files
20
Suspicious files
12
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6432 | stopabit.exe | C:\Users\admin\AppData\Local\Temp\is-54BE2.tmp\stopabit.tmp | executable | |
MD5:7E78166168795D7DA0AB9C918D37EE7F | SHA256:5A8C2ECFBECEEBF667BAF05BA01A565D8C345A9D1A88483EC5533738AE7D7077 | |||
| 6460 | stopabit.tmp | C:\Users\admin\AppData\Local\Programs\Stopabit\is-K24DP.tmp | executable | |
MD5:F64290A69768377482BD437268A866DA | SHA256:2BD09113F2FA48A80837453B3721CDE04604D4874F90A8C941DE3EB5102A1754 | |||
| 6460 | stopabit.tmp | C:\Users\admin\AppData\Local\Programs\Stopabit\is-9CLVC.tmp | executable | |
MD5:304E0F414C764D7A5C2647D721646E13 | SHA256:86CB999EF8B3D20CB81B69FF03580CC6F3D2CA6CC699AB0810FAB8CAC0E7397E | |||
| 6460 | stopabit.tmp | C:\Users\admin\AppData\Local\Programs\Stopabit\unins000.exe | executable | |
MD5:7E78166168795D7DA0AB9C918D37EE7F | SHA256:5A8C2ECFBECEEBF667BAF05BA01A565D8C345A9D1A88483EC5533738AE7D7077 | |||
| 6460 | stopabit.tmp | C:\Users\admin\AppData\Local\Programs\Stopabit\is-EK5BQ.tmp | xml | |
MD5:3E8F51C2B6FD8149C32819EADEC0CA72 | SHA256:0E7ACBB755E5161D596D65BC357EC09EE0F82017D15F65504E4EEC47DAC927BD | |||
| 6460 | stopabit.tmp | C:\Users\admin\AppData\Local\Programs\Stopabit\sdk.dll | executable | |
MD5:F64290A69768377482BD437268A866DA | SHA256:2BD09113F2FA48A80837453B3721CDE04604D4874F90A8C941DE3EB5102A1754 | |||
| 6460 | stopabit.tmp | C:\Users\admin\AppData\Local\Programs\Stopabit\is-AB93Q.tmp | executable | |
MD5:83222120C8095B8623FE827FB70FAF6B | SHA256:EFF79DE319CA8941A2E62FB573230D82B79B80958E5A26AB1A4E87193EB13503 | |||
| 6460 | stopabit.tmp | C:\Users\admin\AppData\Local\Programs\Stopabit\is-5LFFK.tmp | executable | |
MD5:3B17CBEEC5F03DDD8672CCDBB0856016 | SHA256:C915CE8A186483689CB51D74E0D9BC9D081F6F79F16D1953F250058EC61C4577 | |||
| 6460 | stopabit.tmp | C:\Users\admin\AppData\Local\Programs\Stopabit\Stopabit.exe.config | xml | |
MD5:3E8F51C2B6FD8149C32819EADEC0CA72 | SHA256:0E7ACBB755E5161D596D65BC357EC09EE0F82017D15F65504E4EEC47DAC927BD | |||
| 6460 | stopabit.tmp | C:\Users\admin\AppData\Local\Programs\Stopabit\AsyncBridge.Net35.dll | executable | |
MD5:35CBDBE6987B9951D3467DDA2F318F3C | SHA256:E4915F18FD6713EE84F27A06ED1F6F555CDBEBE1522792CF4B4961664550CF83 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
61
DNS requests
35
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4264 | svchost.exe | GET | 200 | 104.103.72.96:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 104.103.72.96:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
5140 | MoUsoCoreWorker.exe | GET | 200 | 2.17.0.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
4540 | RUXIMICS.exe | GET | 200 | 2.17.0.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6784 | Stopabit.exe | GET | 200 | 2.23.154.57:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | unknown |
6784 | Stopabit.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRd0JozUYXMqqW4y4zJTrLcMCRSkAQUgTKSQSsozUbIxKLGKjkS7EipPxQCEQC67%2BPv6JBMH8tNHthn3EeN | unknown | — | — | unknown |
6784 | Stopabit.exe | GET | 200 | 2.23.154.57:80 | http://crl.microsoft.com/pki/crl/products/CodeSigPCA.crl | unknown | — | — | unknown |
6784 | Stopabit.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEDPXCKiRQFMZ4qW70zm5rW4%3D | unknown | — | — | unknown |
— | — | POST | 204 | 95.101.23.43:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | unknown |
— | — | GET | 200 | 104.21.82.170:443 | https://stats.stopabit.com/i?app_key=89531f58dcc968643c19188f5fc3b7250f3b2236&device_id=ad1f12af3f363c28b3512ce4355f42c2&events=%5B%7B%22key%22%3A%22PreInstall%22%2C%22count%22%3A1%2C%22segmentation%22%3A%7B%22version%22%3A%221.0.2.0%22%2C%22dotNet%22%3A%22True%22%7D%7D%5D | unknown | binary | 20 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 239.255.255.250:1900 | — | — | — | unknown |
4264 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4540 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4264 | svchost.exe | 104.103.72.96:80 | crl.microsoft.com | Akamai International B.V. | AT | unknown |
5140 | MoUsoCoreWorker.exe | 104.103.72.96:80 | crl.microsoft.com | Akamai International B.V. | AT | unknown |
4540 | RUXIMICS.exe | 104.103.72.96:80 | crl.microsoft.com | Akamai International B.V. | AT | unknown |
5140 | MoUsoCoreWorker.exe | 2.17.0.227:80 | www.microsoft.com | AKAMAI-AS | DK | unknown |
4264 | svchost.exe | 2.17.0.227:80 | www.microsoft.com | AKAMAI-AS | DK | unknown |
6460 | stopabit.tmp | 172.67.159.214:443 | stats.stopabit.com | CLOUDFLARENET | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
stats.stopabit.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
track.stopabit.com |
| unknown |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
zenreminder.org |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Generic Protocol Command Decode | SURICATA HTTP Request abnormal Content-Encoding header |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request abnormal Content-Encoding header |