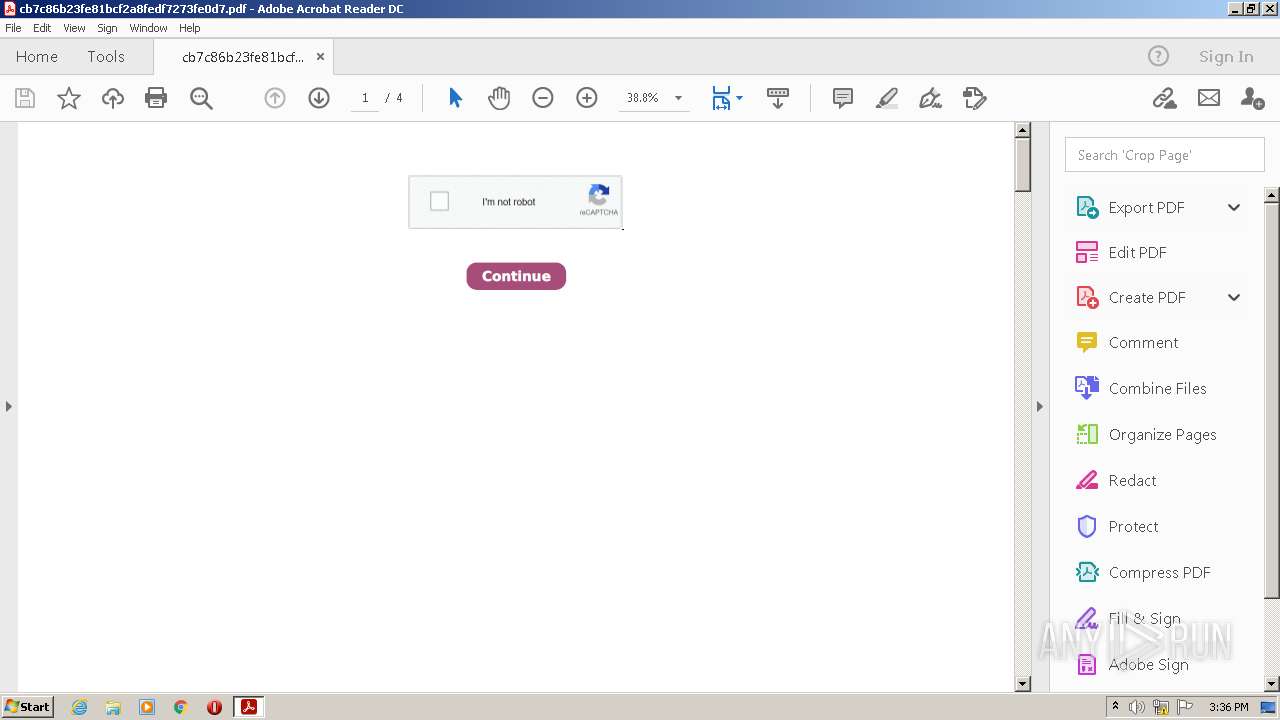
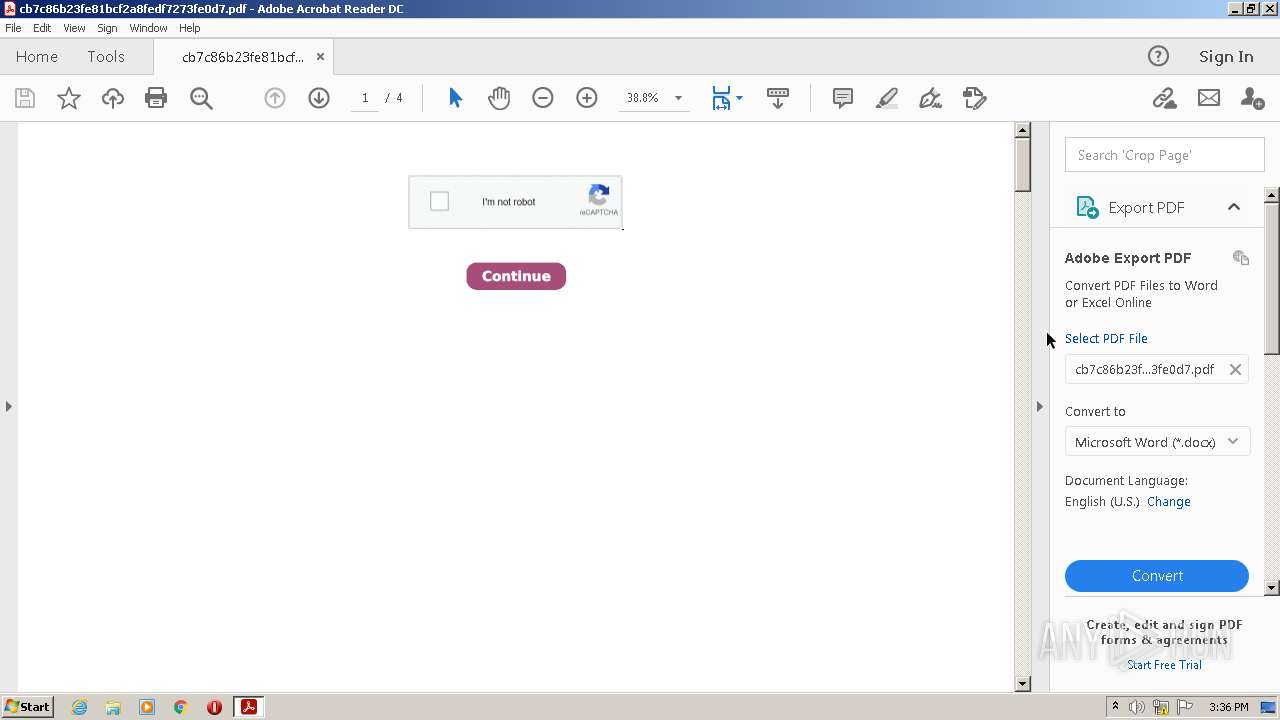
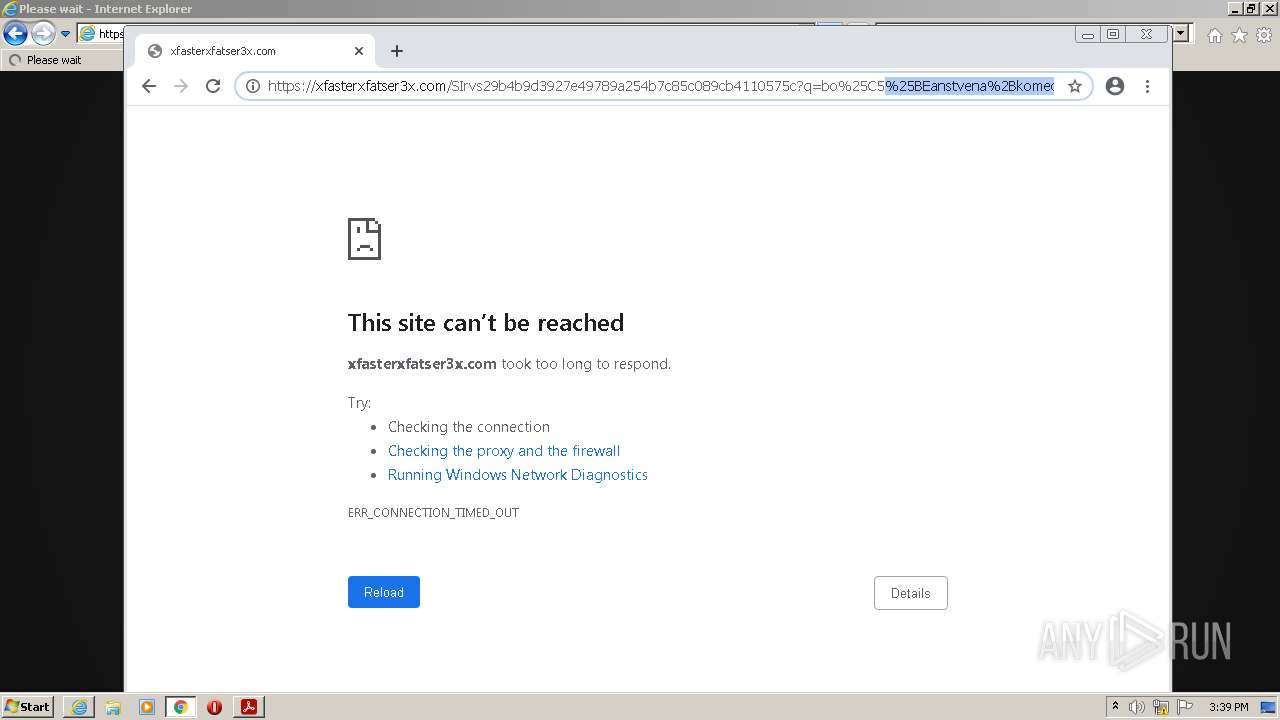
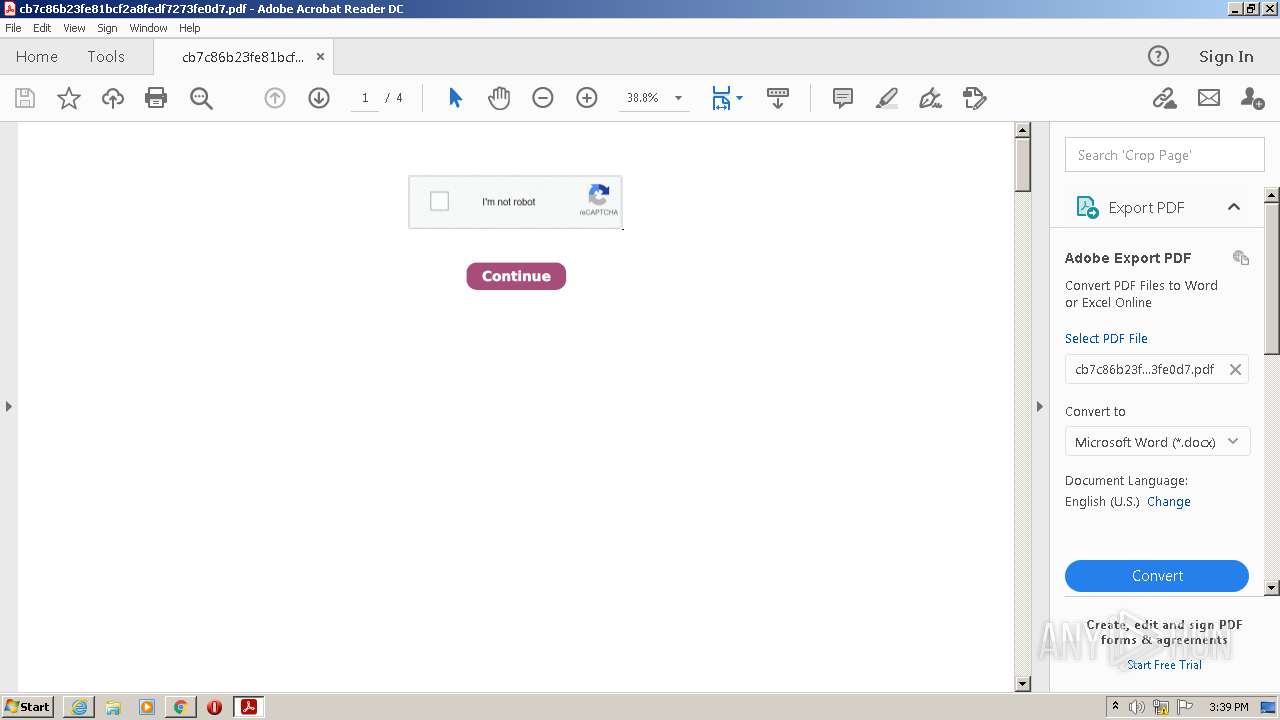
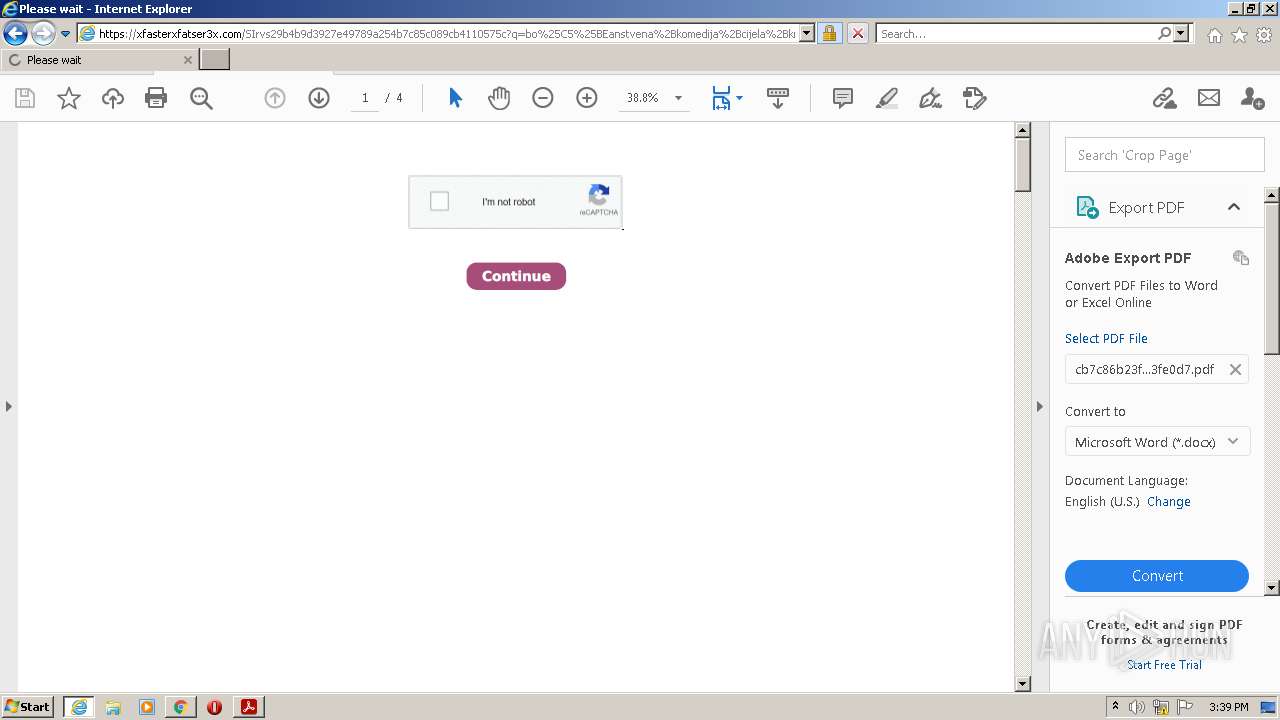
| File name: | cb7c86b23fe81bcf2a8fedf7273fe0d7.pdf |
| Full analysis: | https://app.any.run/tasks/0a0b8513-3fcf-4daa-a138-7df493a807bd |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 15:36:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.4 |
| MD5: | CB7C86B23FE81BCF2A8FEDF7273FE0D7 |
| SHA1: | C4C22A81B42F1657A8158AC8F98008056511A11C |
| SHA256: | A82E9297DA902F3E4C68758BD5EEC73E965CD88DB7CB34B1C6AB5C1E84DBD8F6 |
| SSDEEP: | 3072:9KCC+9PJfbL9MSStadBsq2aZ1SDuR6diwz/n0:97C+9Pl9jBbrxZUldzc |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- AcroRd32.exe (PID: 1324)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3304)
Reads the computer name
- AdobeARM.exe (PID: 3792)
Checks supported languages
- AdobeARM.exe (PID: 3792)
- Reader_sl.exe (PID: 3824)
INFO
Reads the computer name
- AcroRd32.exe (PID: 1324)
- AcroRd32.exe (PID: 272)
- RdrCEF.exe (PID: 2180)
- iexplore.exe (PID: 3152)
- iexplore.exe (PID: 3304)
- chrome.exe (PID: 3192)
- chrome.exe (PID: 2132)
- chrome.exe (PID: 436)
- chrome.exe (PID: 3428)
- chrome.exe (PID: 1564)
- chrome.exe (PID: 1236)
- chrome.exe (PID: 848)
Application launched itself
- AcroRd32.exe (PID: 1324)
- RdrCEF.exe (PID: 2180)
- iexplore.exe (PID: 3152)
- chrome.exe (PID: 3192)
Searches for installed software
- AcroRd32.exe (PID: 1324)
- AcroRd32.exe (PID: 272)
Checks supported languages
- AcroRd32.exe (PID: 272)
- AcroRd32.exe (PID: 1324)
- RdrCEF.exe (PID: 2180)
- RdrCEF.exe (PID: 3552)
- RdrCEF.exe (PID: 1872)
- RdrCEF.exe (PID: 3228)
- RdrCEF.exe (PID: 1936)
- RdrCEF.exe (PID: 3652)
- RdrCEF.exe (PID: 4024)
- iexplore.exe (PID: 3152)
- RdrCEF.exe (PID: 4084)
- iexplore.exe (PID: 3304)
- chrome.exe (PID: 3192)
- chrome.exe (PID: 1400)
- chrome.exe (PID: 3428)
- chrome.exe (PID: 2516)
- chrome.exe (PID: 2824)
- chrome.exe (PID: 3444)
- chrome.exe (PID: 2132)
- chrome.exe (PID: 436)
- chrome.exe (PID: 3628)
- chrome.exe (PID: 3120)
- chrome.exe (PID: 1024)
- chrome.exe (PID: 576)
- chrome.exe (PID: 1564)
- chrome.exe (PID: 1236)
- chrome.exe (PID: 848)
- chrome.exe (PID: 2416)
- chrome.exe (PID: 2412)
Reads CPU info
- AcroRd32.exe (PID: 272)
Reads the hosts file
- RdrCEF.exe (PID: 2180)
- chrome.exe (PID: 3192)
- chrome.exe (PID: 436)
Checks Windows Trust Settings
- AcroRd32.exe (PID: 1324)
- iexplore.exe (PID: 3304)
- iexplore.exe (PID: 3152)
Reads settings of System Certificates
- AcroRd32.exe (PID: 1324)
- RdrCEF.exe (PID: 2180)
- iexplore.exe (PID: 3304)
- iexplore.exe (PID: 3152)
Changes internet zones settings
- iexplore.exe (PID: 3152)
Reads internet explorer settings
- iexplore.exe (PID: 3304)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3152)
Creates files in the user directory
- iexplore.exe (PID: 3304)
- iexplore.exe (PID: 3152)
Changes settings of System certificates
- iexplore.exe (PID: 3152)
Manual execution by user
- chrome.exe (PID: 3192)
Reads the date of Windows installation
- chrome.exe (PID: 848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
XMP
| Marked: | |
|---|---|
| InstanceID: | 36cda9d6-2384-4d85-b73f-c225e147cbc8 |
| DocumentID: | eec9757d-ee0b-451f-91a9-0608dfbe2cca |
| CreatorTool: | Inkscape |
| CreateDate: | 2020:02:13 09:55:03 |
| Producer: | Inkscape |
| Title: | Božanstvena komedija cijela knjiga pdf |
| Subject: | Božanstvena komedija cijela knjiga pdf. https://dereta.rs/a.aspx?autor_uid=2791ab40-d633-4f85-bd81-da90e858f04d Thank you for interestin |
| Description: | Božanstvena komedija cijela knjiga pdf. https://dereta.rs/a.aspx?autor_uid=2791ab40-d633-4f85-bd81-da90e858f04d Thank you for interestin |
| Creator: | Sotacebu Silefa |
| Format: | application/pdf |
| XMPToolkit: | Inkscape |
| PageCount: | 4 |
|---|---|
| Subject: | Božanstvena komedija cijela knjiga pdf. https://dereta.rs/a.aspx?autor_uid=2791ab40-d633-4f85-bd81-da90e858f04d Thank you for interestin |
| Author: | Sotacebu Silefa |
| CreateDate: | 2020:02:13 09:55:03 |
| Producer: | Inkscape |
| Creator: | Inkscape |
| Title: | Božanstvena komedija cijela knjiga pdf |
| Linearized: | No |
| PDFVersion: | 1.4 |
Total processes
70
Monitored processes
31
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\Downloads\cb7c86b23fe81bcf2a8fedf7273fe0d7.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 436 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --field-trial-handle=1064,14453187563987345992,15760423622575056817,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=network --mojo-platform-channel-handle=1332 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 576 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,14453187563987345992,15760423622575056817,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=11 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2728 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 848 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1064,14453187563987345992,15760423622575056817,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=964 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1024 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,14453187563987345992,15760423622575056817,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3052 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1064,14453187563987345992,15760423622575056817,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1784 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1324 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\Downloads\cb7c86b23fe81bcf2a8fedf7273fe0d7.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | Explorer.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1400 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1064,14453187563987345992,15760423622575056817,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2276 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1564 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1064,14453187563987345992,15760423622575056817,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2012 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1872 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1068,2030437550257746432,6767444340347465527,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=10718516799608961599 --mojo-platform-channel-handle=1384 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
34 151
Read events
33 834
Write events
308
Delete events
9
Modification events
| (PID) Process: | (272) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (272) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | iNumReaderLaunches |
Value: 2 | |||
| (PID) Process: | (272) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FTEDialog |
| Operation: | write | Name: | bShowUpdateFTE |
Value: 1 | |||
| (PID) Process: | (272) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\HomeWelcome |
| Operation: | write | Name: | bIsAcrobatUpdated |
Value: 1 | |||
| (PID) Process: | (272) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\HomeWelcomeFirstMileReader |
| Operation: | write | Name: | iCardCountShown |
Value: 2 | |||
| (PID) Process: | (272) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\FTEDialog |
| Operation: | delete value | Name: | iLastCardShown |
Value: 0 | |||
| (PID) Process: | (1324) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (272) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement |
| Operation: | write | Name: | bNormalExit |
Value: 0 | |||
| (PID) Process: | (272) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement\cWindowsCurrent\cWin0\cTab0\cPathInfo |
| Operation: | write | Name: | sDI |
Value: 2F432F55736572732F61646D696E2F446F776E6C6F6164732F63623763383662323366653831626366326138666564663732373366653064372E70646600 | |||
| (PID) Process: | (272) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\SessionManagement\cWindowsCurrent\cWin0\cTab0\cPathInfo |
| Operation: | write | Name: | tDIText |
Value: /C/Users/admin/Downloads/cb7c86b23fe81bcf2a8fedf7273fe0d7.pdf | |||
Executable files
0
Suspicious files
187
Text files
118
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\bba29d2e6197e2f4_0 | binary | |
MD5:— | SHA256:— | |||
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\983b7a3da8f39a46_0 | binary | |
MD5:— | SHA256:— | |||
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\560e9c8bff5008d8_0 | binary | |
MD5:— | SHA256:— | |||
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\8e417e79df3bf0e9_0 | binary | |
MD5:— | SHA256:— | |||
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\86b8040b7132b608_0 | binary | |
MD5:— | SHA256:— | |||
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\2a426f11fd8ebe18_0 | binary | |
MD5:— | SHA256:— | |||
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:— | SHA256:— | |||
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:— | SHA256:— | |||
| 2180 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\92c56fa2a6c4d5ba_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
104
DNS requests
46
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3304 | iexplore.exe | GET | — | 104.18.30.182:80 | http://zerossl.ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQILj%2F5BYz%2BinwYvRPv3x0WYHB6awQUyNl4aKLZGWjVPXLeXwo%2B3LWGhqYCEFGCcTV1KvZbb65X7xpUvO0%3D | US | — | — | whitelisted |
1324 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3304 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://crl.pki.goog/gsr1/gsr1.crl | US | der | 1.61 Kb | whitelisted |
3304 | iexplore.exe | GET | 200 | 95.101.89.24:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgPDQL6WtCglZS7LxVQ%2BkgHmMA%3D%3D | unknown | der | 503 b | shared |
3304 | iexplore.exe | GET | 200 | 104.18.30.182:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEGxVq9vQB5LHnQcM2BGe1r8%3D | US | der | 727 b | whitelisted |
3152 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
3304 | iexplore.exe | GET | 200 | 95.101.89.24:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgT65Iw39%2B%2FldDj7B97CRBMjGg%3D%3D | unknown | der | 503 b | shared |
3152 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
3304 | iexplore.exe | GET | 200 | 142.250.184.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQC04WHG3wyS9QoAAAABK3x8 | US | der | 472 b | whitelisted |
3304 | iexplore.exe | GET | 200 | 178.79.242.128:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8380fd539fc7a7f7 | DE | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2180 | RdrCEF.exe | 2.20.156.175:443 | geo2.adobe.com | Akamai International B.V. | — | whitelisted |
— | — | 104.79.88.64:443 | armmf.adobe.com | Time Warner Cable Internet LLC | US | suspicious |
1324 | AcroRd32.exe | 92.123.225.49:443 | acroipm2.adobe.com | Akamai International B.V. | — | suspicious |
2180 | RdrCEF.exe | 104.79.88.64:443 | armmf.adobe.com | Time Warner Cable Internet LLC | US | suspicious |
2180 | RdrCEF.exe | 107.22.247.231:443 | p13n.adobe.io | Amazon.com, Inc. | US | suspicious |
3304 | iexplore.exe | 142.250.184.195:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
1324 | AcroRd32.exe | 178.79.242.128:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | DE | malicious |
3304 | iexplore.exe | 178.79.242.128:80 | ctldl.windowsupdate.com | Limelight Networks, Inc. | DE | malicious |
1324 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3152 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
geo2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
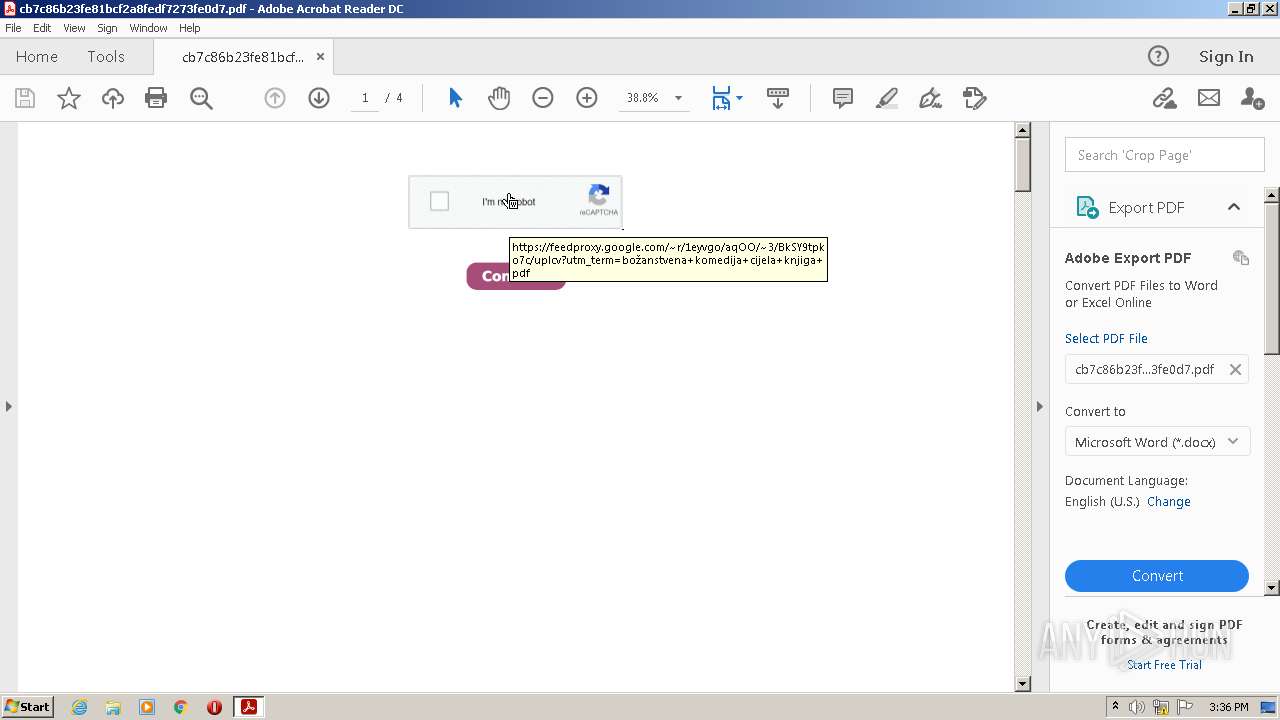
feedproxy.google.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3304 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3304 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3304 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed ZeroSSL SSL/TLS Certificate |
3304 | iexplore.exe | Potentially Bad Traffic | ET INFO Observed ZeroSSL SSL/TLS Certificate |