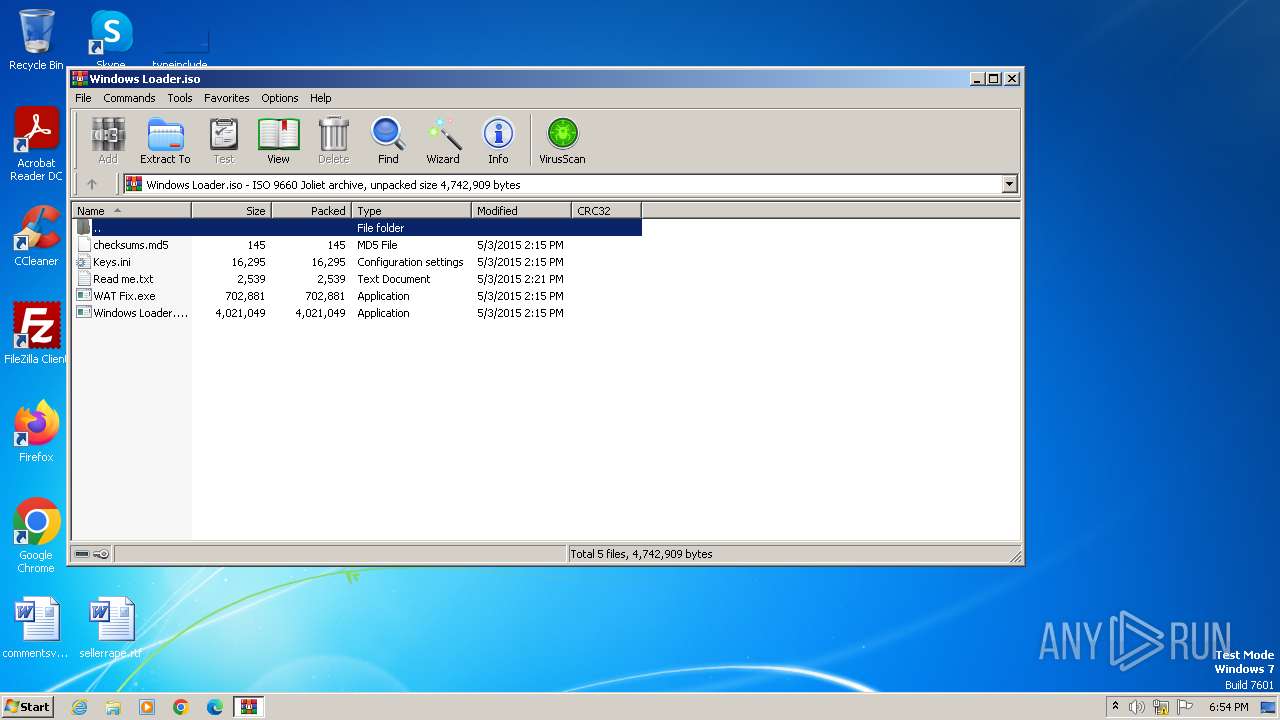
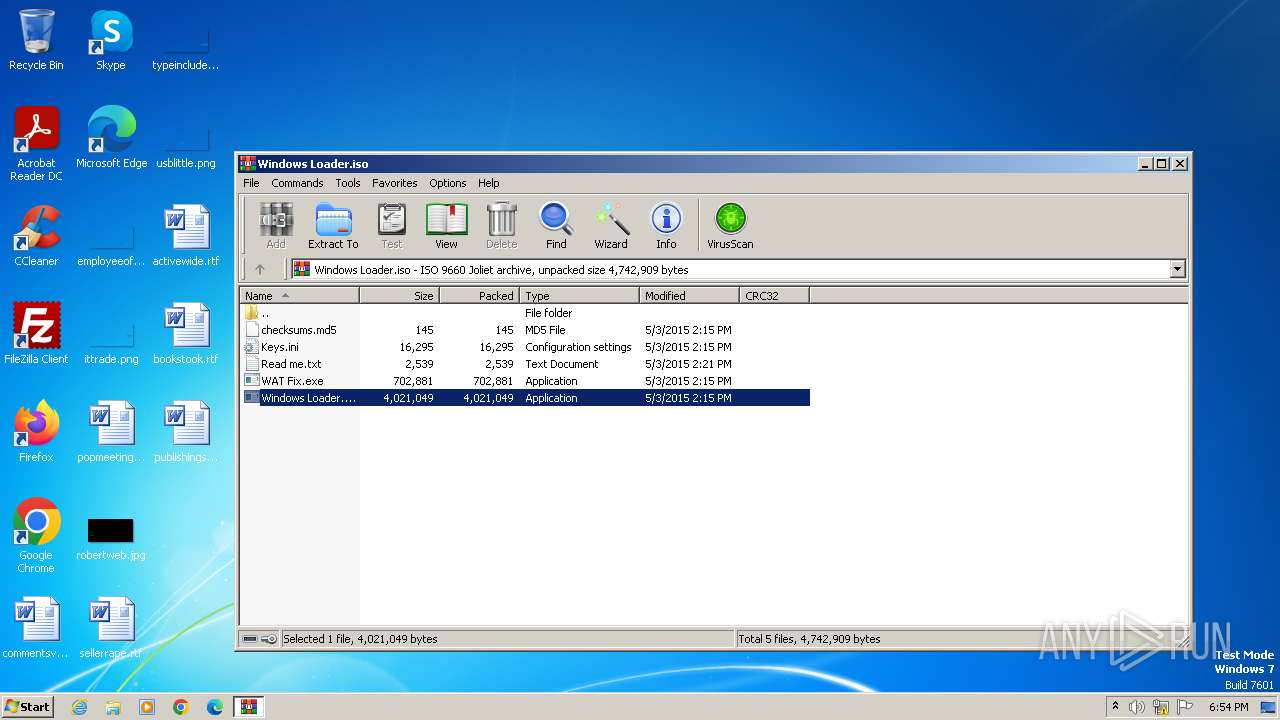
| File name: | Windows Loader.iso |
| Full analysis: | https://app.any.run/tasks/bb575cdf-0d20-4927-a9d5-fc7742de665c |
| Verdict: | Malicious activity |
| Analysis date: | November 09, 2023, 18:53:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-iso9660-image |
| File info: | ISO 9660 CD-ROM filesystem data '20160312_1540' |
| MD5: | 5FF25C64153C4AA535B040C4CB291964 |
| SHA1: | 9B5A3FD13458C98332E89A4442CD0088A19F308A |
| SHA256: | A823806E80EC2AA3DB37150EE17AD02D57995570640EB108CA19057967B70BE0 |
| SSDEEP: | 98304:M6bbMU95DKW3xsUVaGHPZoxTEAURJGtXKnNBk0SFbLHGUUl2bnuC9KtZrswbm:V |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 2060)
- cmd.exe (PID: 1752)
- net.exe (PID: 1376)
- net.exe (PID: 2368)
- net.exe (PID: 2300)
- net.exe (PID: 2136)
- cmd.exe (PID: 3800)
- cmd.exe (PID: 2312)
Opens a text file (SCRIPT)
- cscript.exe (PID: 1892)
Accesses environment variables (SCRIPT)
- cscript.exe (PID: 1892)
Checks whether a specified folder exists (SCRIPT)
- cscript.exe (PID: 1892)
SUSPICIOUS
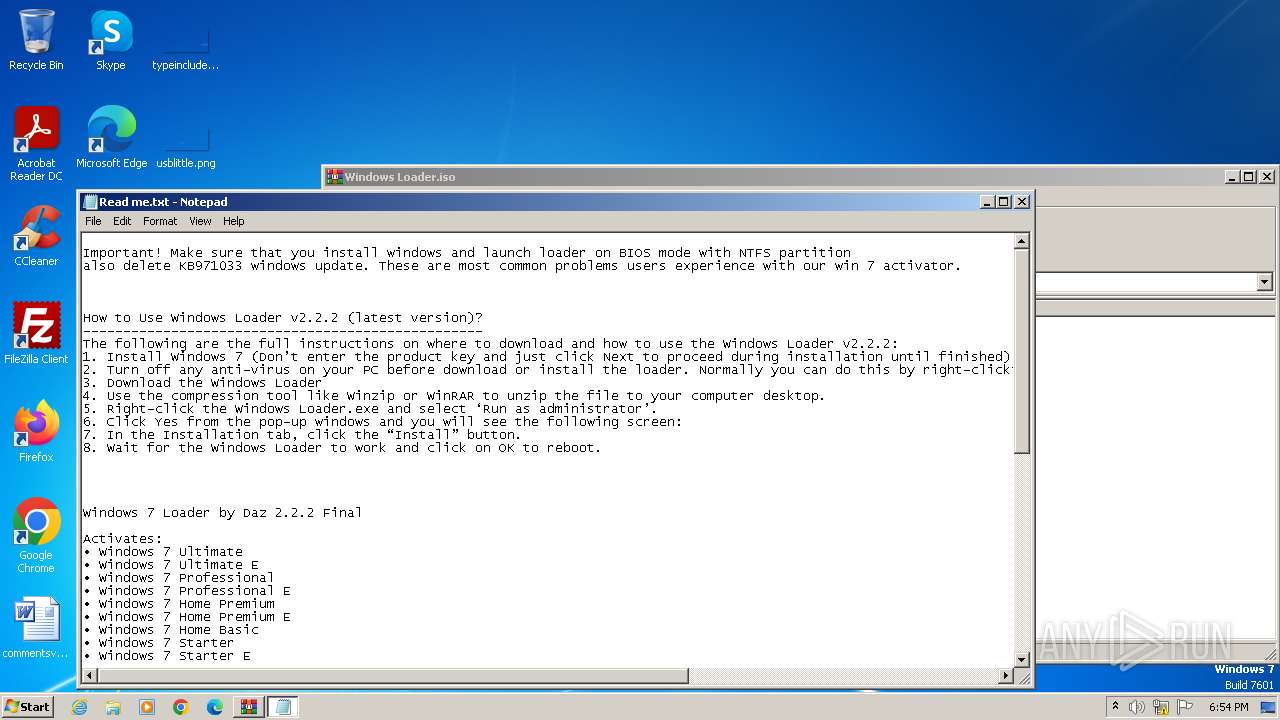
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3428)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 4084)
Reads the BIOS version
- Windows Loader.exe (PID: 3424)
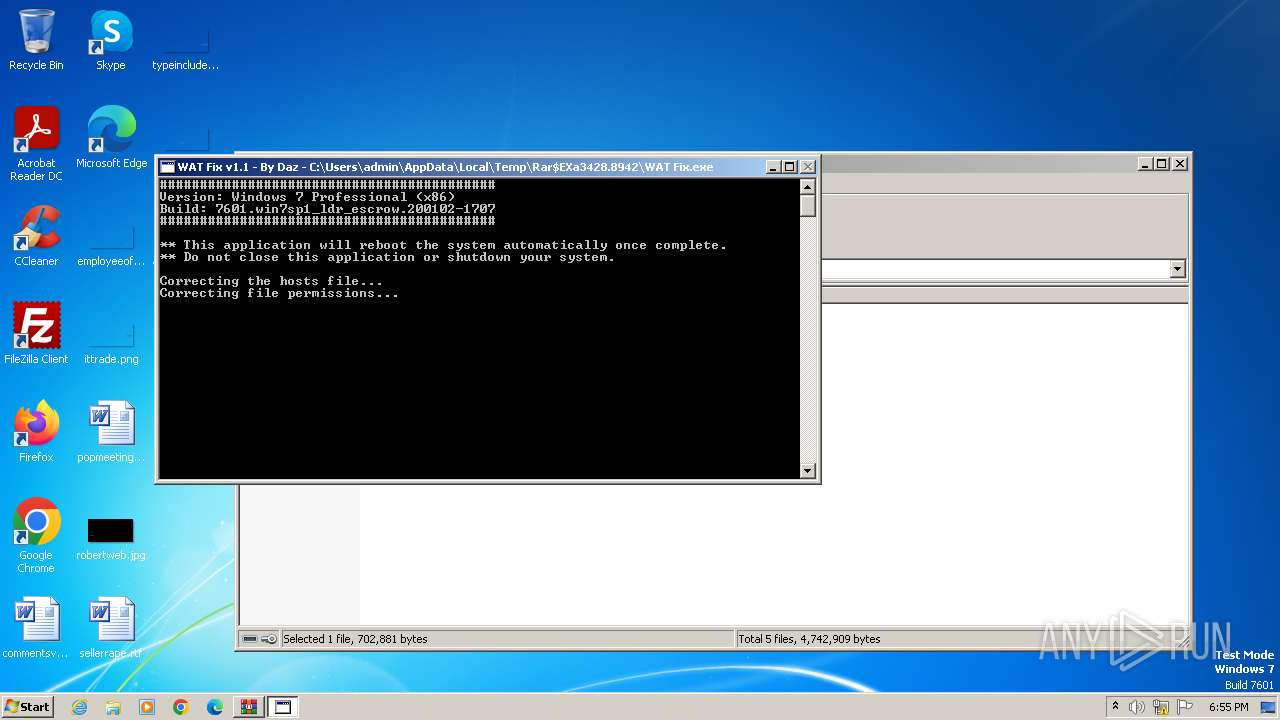
Starts CMD.EXE for commands execution
- WAT Fix.exe (PID: 4012)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3684)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4076)
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 3028)
The process executes VB scripts
- cmd.exe (PID: 528)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 1892)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 1892)
Starts SC.EXE for service management
- cmd.exe (PID: 3020)
- cmd.exe (PID: 756)
- cmd.exe (PID: 1232)
- cmd.exe (PID: 1944)
- cmd.exe (PID: 3804)
- cmd.exe (PID: 2084)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- cscript.exe (PID: 1892)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 1892)
Checks whether a specific file exists (SCRIPT)
- cscript.exe (PID: 1892)
Reads data from a file (SCRIPT)
- cscript.exe (PID: 1892)
Changes charset (SCRIPT)
- cscript.exe (PID: 1892)
Accesses system date via WMI (SCRIPT)
- cscript.exe (PID: 1892)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 1892)
Executes WMI query (SCRIPT)
- cscript.exe (PID: 1892)
INFO
Reads Environment values
- Windows Loader.exe (PID: 3424)
- WAT Fix.exe (PID: 4012)
Checks supported languages
- WAT Fix.exe (PID: 4012)
- Windows Loader.exe (PID: 3424)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3428)
Reads the computer name
- WAT Fix.exe (PID: 4012)
- Windows Loader.exe (PID: 3424)
Reads product name
- WAT Fix.exe (PID: 4012)
- Windows Loader.exe (PID: 3424)
Reads security settings of Internet Explorer
- cscript.exe (PID: 1892)
Reads the machine GUID from the registry
- Windows Loader.exe (PID: 3424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .iso | | | ISO 9660 CD image (27.6) |
|---|---|---|
| .atn | | | Photoshop Action (27.1) |
| .gmc | | | Game Music Creator Music (6.1) |
EXIF
ISO
| VolumeName: | 20160312_1540 |
|---|---|
| VolumeBlockCount: | 2345 |
| VolumeBlockSize: | 2048 |
| RootDirectoryCreateDate: | 2016:03:12 15:40:47+00:00 |
| VolumeSetName: | 20160312_1540 |
| Publisher: | MagicISO v5.2 COPYRIGHT (C) 2001-2006 MagicISO, Inc. |
| DataPreparer: | MagicISO v5.2 COPYRIGHT (C) 2001-2006 MagicISO, Inc. |
| VolumeCreateDate: | 20160312154431 |
| VolumeModifyDate: | 20160312154431 |
Composite
| VolumeSize: | 4.6 MiB |
|---|
Total processes
86
Monitored processes
44
Malicious processes
5
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 528 | cmd.exe /A /C "cscript.exe //nologo %SystemRoot%\system32\slmgr.vbs -rilc 2>NUL>NUL" | C:\Windows\System32\cmd.exe | — | WAT Fix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 588 | sc stop uodin64 | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | cmd.exe /A /C "ren %SystemRoot%\system32\slmgr.vbs.removewat slmgr.vbs 2>NUL>NUL" | C:\Windows\System32\cmd.exe | — | WAT Fix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 756 | cmd.exe /A /C "sc config sppuinotify start= demand 2>NUL>NUL" | C:\Windows\System32\cmd.exe | — | WAT Fix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1232 | cmd.exe /A /C "sc delete uodin86 2>NUL>NUL" | C:\Windows\System32\cmd.exe | — | WAT Fix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1060 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1376 | net start sppsvc | C:\Windows\System32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1640 | sc delete uodin86 | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 1060 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1752 | cmd.exe /A /C "net start sppuinotify 2>NUL>NUL" | C:\Windows\System32\cmd.exe | — | WAT Fix.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1760 | C:\Windows\system32\net1 start sppsvc | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1892 | cscript.exe //nologo C:\Windows\system32\slmgr.vbs -rilc | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
2 056
Read events
2 038
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3428) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
4
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3428.7011\Keys.ini | text | |
MD5:3BA4950BCF43B1C7B714A1D93B57EA86 | SHA256:1384C5FD758A1BD8C9372594503E22D71B0877D332886A1B7D50CB86C4A0A13C | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3428.7011\WAT Fix.exe | executable | |
MD5:0A1023D7FD543F6B73AD2A4CA553BBA1 | SHA256:D2BEF451A44457EF4B1DA38982F568E1E75402FBD2FEDC6EAA5F761CD6A5E751 | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3428.7011\Read me.txt | text | |
MD5:D82C50EE472476C01D4CDC5AB3DA4531 | SHA256:559685D98F34E3F7E48DDD1DB091E90497AF9ACDC7A8BE98C717626A505229B8 | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3428.8942\Keys.ini | text | |
MD5:3BA4950BCF43B1C7B714A1D93B57EA86 | SHA256:1384C5FD758A1BD8C9372594503E22D71B0877D332886A1B7D50CB86C4A0A13C | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3428.7011\Windows Loader.exe | executable | |
MD5:323C0FD51071400B51EEDB1BE90A8188 | SHA256:2F2ABA1E074F5F4BAA08B524875461889F8F04D4FFC43972AC212E286022AB94 | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3428.4958\Read me.txt | text | |
MD5:D82C50EE472476C01D4CDC5AB3DA4531 | SHA256:559685D98F34E3F7E48DDD1DB091E90497AF9ACDC7A8BE98C717626A505229B8 | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3428.7011\checksums.md5 | text | |
MD5:CAB45D50BE4C1FC788D29593464B1F35 | SHA256:C083F57AC4D8A5EAF9BC934F08204A691FA9E4FD275F90AAADFD195A4EEF820F | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3428.8942\checksums.md5 | text | |
MD5:CAB45D50BE4C1FC788D29593464B1F35 | SHA256:C083F57AC4D8A5EAF9BC934F08204A691FA9E4FD275F90AAADFD195A4EEF820F | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3428.8942\WAT Fix.exe | executable | |
MD5:0A1023D7FD543F6B73AD2A4CA553BBA1 | SHA256:D2BEF451A44457EF4B1DA38982F568E1E75402FBD2FEDC6EAA5F761CD6A5E751 | |||
| 3428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3428.8942\Windows Loader.exe | executable | |
MD5:323C0FD51071400B51EEDB1BE90A8188 | SHA256:2F2ABA1E074F5F4BAA08B524875461889F8F04D4FFC43972AC212E286022AB94 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
2
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |