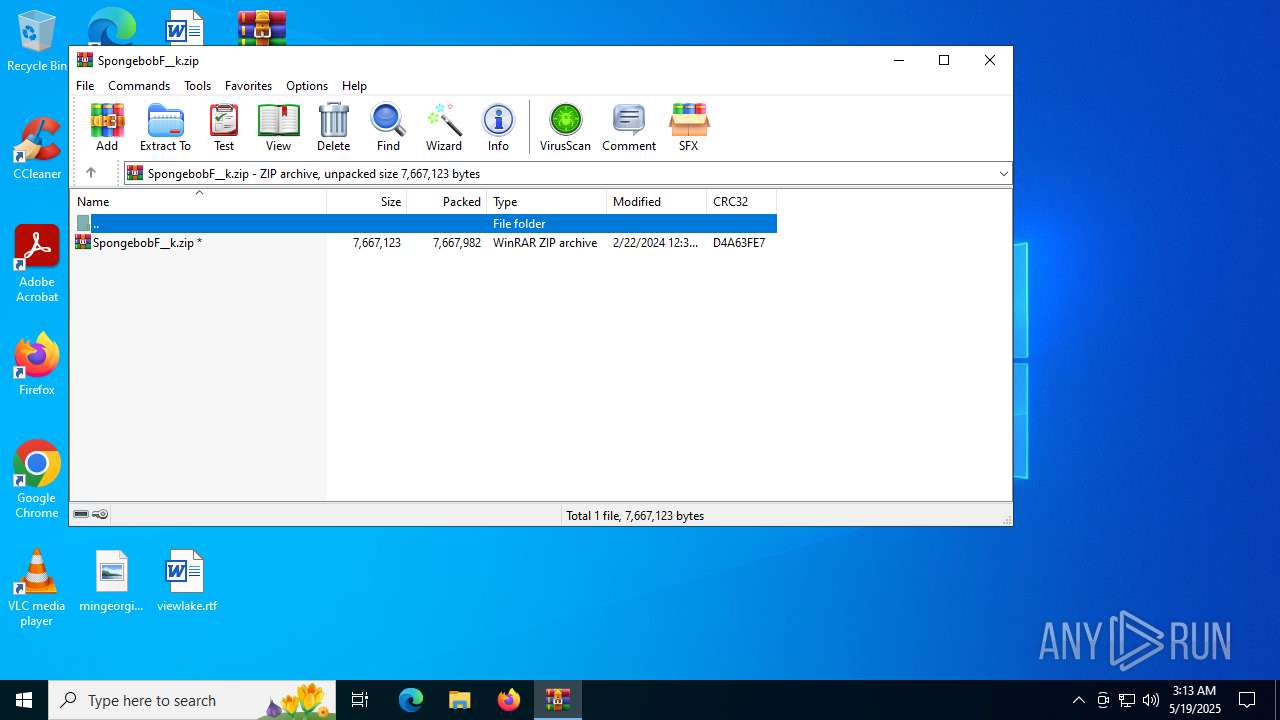
| File name: | SpongebobF__k.zip |
| Full analysis: | https://app.any.run/tasks/3432770e-4ef4-482c-9987-7b276cb202af |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 03:13:27 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | F8291DA1E099DF0FFD0C29B1D524486A |
| SHA1: | D585BC7505C143175AF3DD211528312CCA3B518E |
| SHA256: | A80CCB67B62BE1F2E7A76DC2901EF45B187FD1E50DA23380F3155DDC180A242C |
| SSDEEP: | 98304:oGtXrezJqoEEkXYoowXcMaoH3SndfMcaSup0P6kG/2UdcmNgLKQTZ30S2BIczyOc:jxZmnMocaRakB |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4916)
SUSPICIOUS
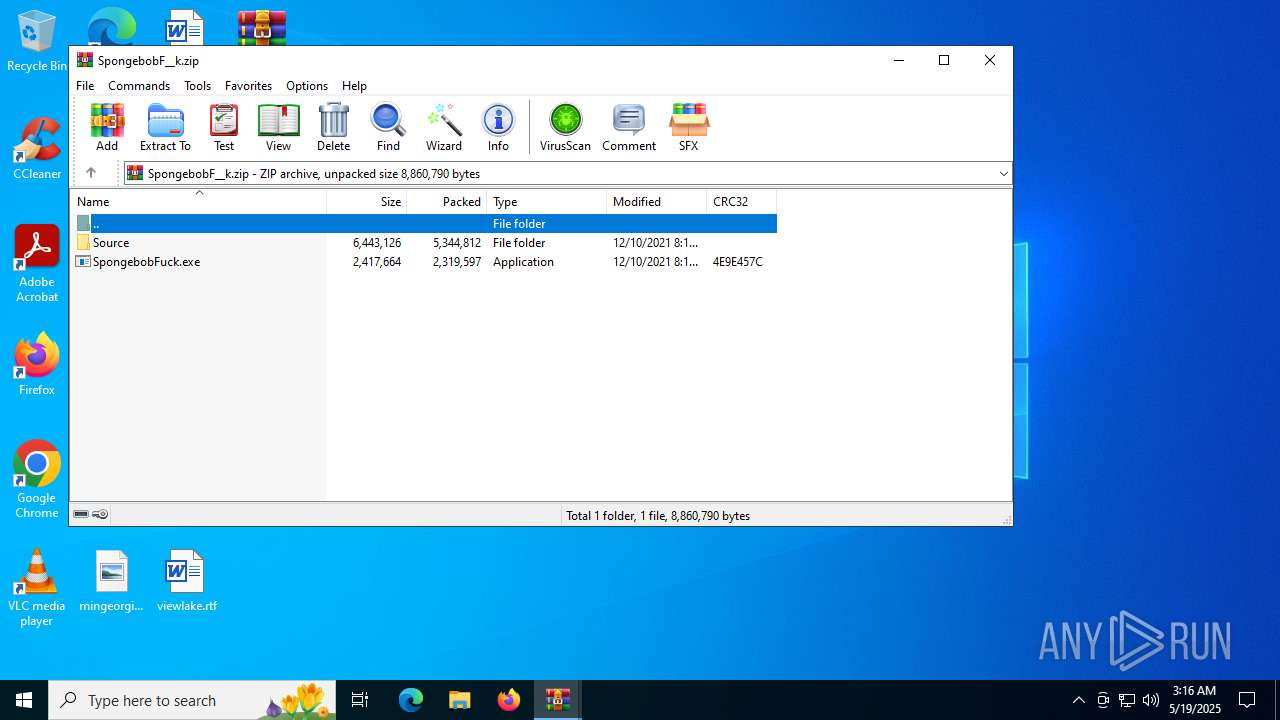
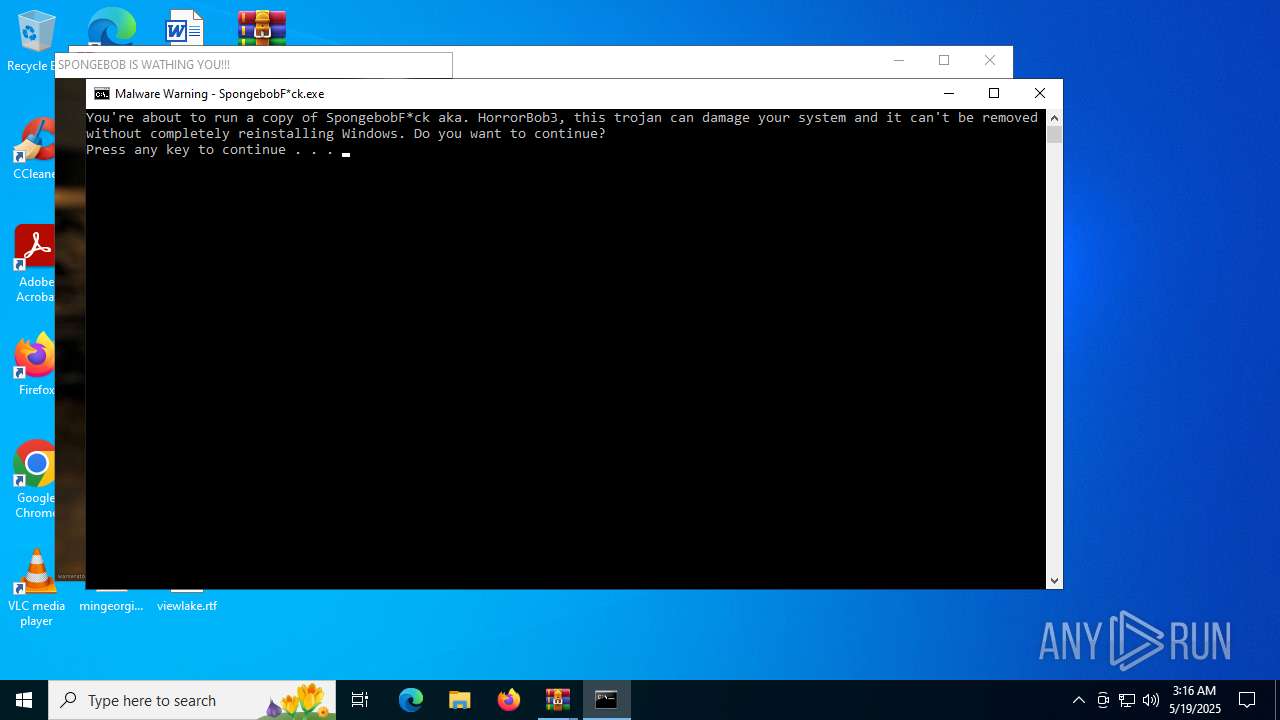
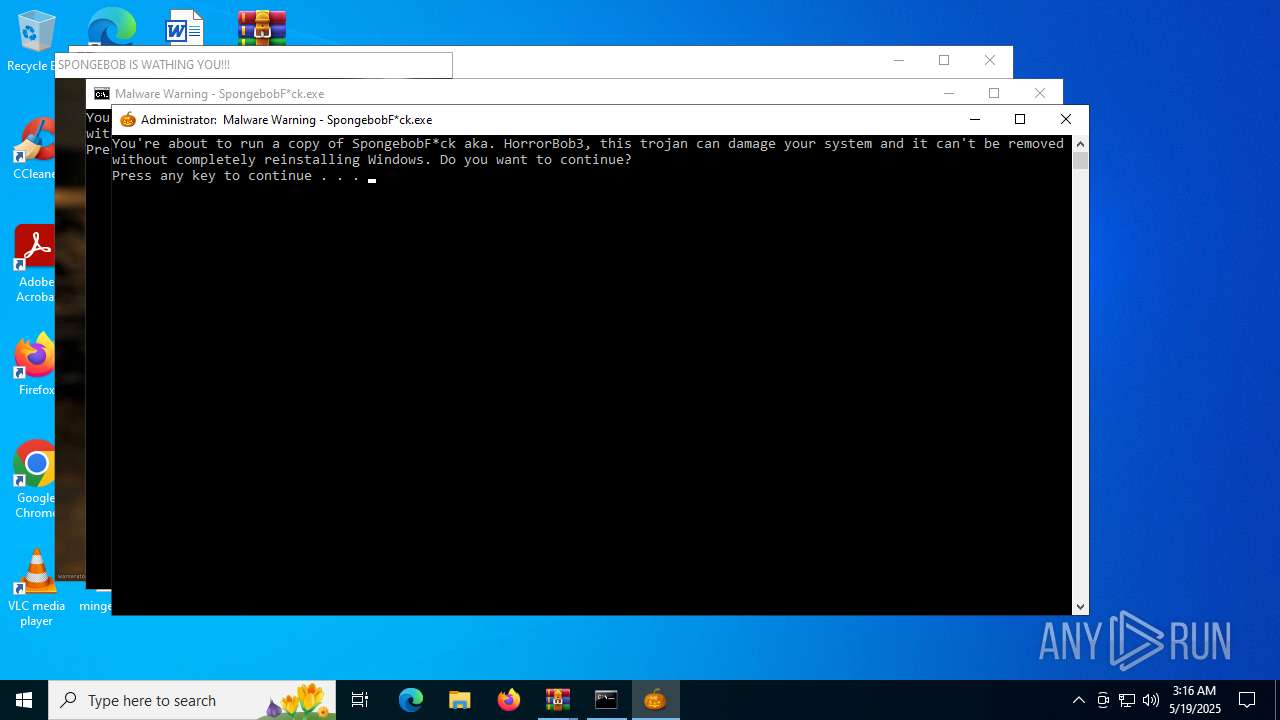
Executable content was dropped or overwritten
- SpongebobFuck.exe (PID: 4816)
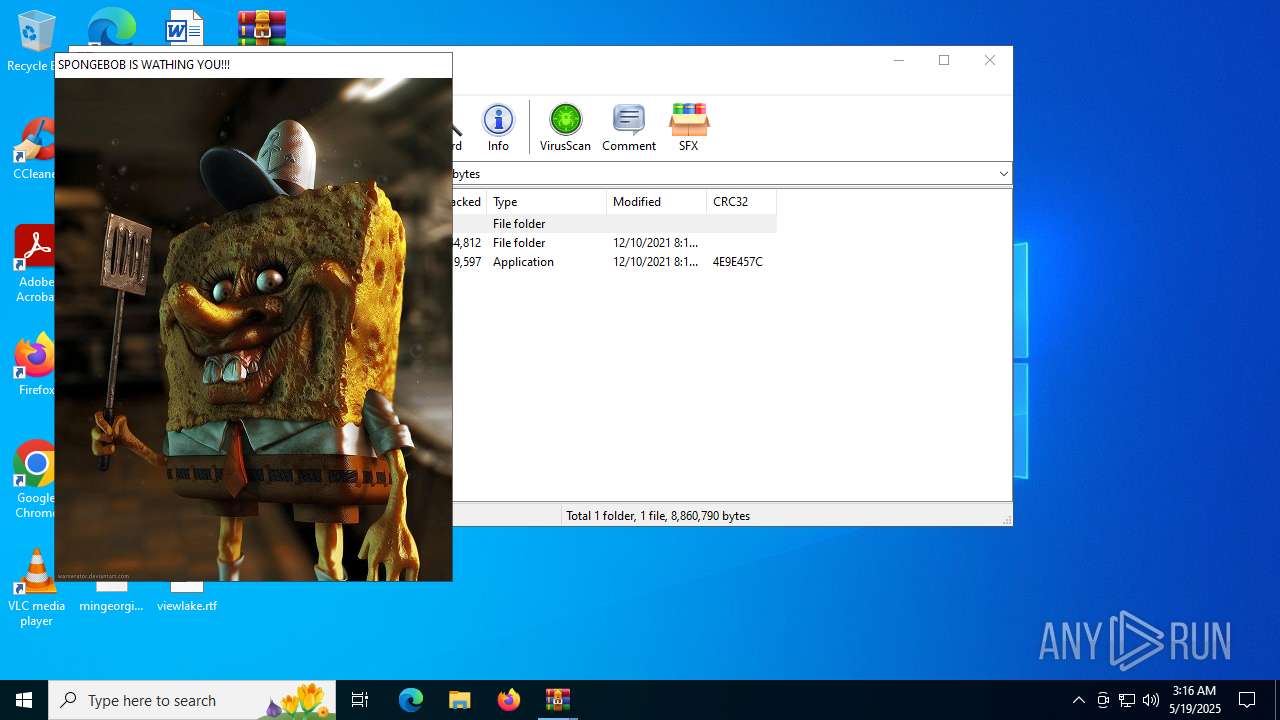
Starts CMD.EXE for commands execution
- SpongebobFuck.exe (PID: 4816)
Executing commands from ".cmd" file
- SpongebobFuck.exe (PID: 4816)
INFO
Checks proxy server information
- slui.exe (PID: 2292)
Reads the software policy settings
- slui.exe (PID: 2292)
Manual execution by a user
- WinRAR.exe (PID: 5244)
- MainWindow.exe (PID: 2356)
- cmd.exe (PID: 6572)
- SpongebobFuck.exe (PID: 6580)
- SpongebobFuck.exe (PID: 4816)
- wscript.exe (PID: 392)
- rundll32.exe (PID: 5464)
- OpenWith.exe (PID: 6640)
- OpenWith.exe (PID: 7020)
- rundll32.exe (PID: 7076)
- OpenWith.exe (PID: 2532)
Checks supported languages
- MainWindow.exe (PID: 2356)
- SpongebobFuck.exe (PID: 4816)
Reads the computer name
- MainWindow.exe (PID: 2356)
Create files in a temporary directory
- SpongebobFuck.exe (PID: 4816)
The sample compiled with english language support
- SpongebobFuck.exe (PID: 4816)
Reads Microsoft Office registry keys
- OpenWith.exe (PID: 6640)
- OpenWith.exe (PID: 2532)
- OpenWith.exe (PID: 7020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:02:22 12:39:14 |
| ZipCRC: | 0xd4a63fe7 |
| ZipCompressedSize: | 7667982 |
| ZipUncompressedSize: | 7667123 |
| ZipFileName: | SpongebobF__k.zip |
Total processes
154
Monitored processes
16
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\WINDOWS\System32\WScript.exe" C:\Users\admin\Desktop\bobspeak.vbs | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2292 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2320 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SpongebobFuck.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2356 | "C:\Users\admin\Desktop\MainWindow.exe" | C:\Users\admin\Desktop\MainWindow.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Version: 1.00 Modules
| |||||||||||||||
| 2532 | "C:\WINDOWS\System32\OpenWith.exe" C:\Users\admin\Desktop\MainWindow.vbp | C:\Windows\System32\OpenWith.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 2147943623 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3624 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\DD43.tmp\SpongebobFuck.cmd"" | C:\Windows\SysWOW64\cmd.exe | — | SpongebobFuck.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4816 | "C:\Users\admin\Desktop\SpongebobFuck.exe" | C:\Users\admin\Desktop\SpongebobFuck.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4916 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\SpongebobF__k.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5244 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\SpongebobF__k.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 5464 | "C:\WINDOWS\System32\rundll32.exe" "C:\Program Files\Windows Photo Viewer\PhotoViewer.dll", ImageView_Fullscreen C:\Users\admin\Desktop\Aha-Soft-Desktop-Halloween-Halloween.ico | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
8 837
Read events
8 610
Write events
227
Delete events
0
Modification events
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SpongebobF__k.zip | |||
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4916) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
2
Suspicious files
1
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4816 | SpongebobFuck.exe | C:\Users\admin\AppData\Local\Temp\DD43.tmp\bg.bmp | image | |
MD5:CE45A70D3CC2941A147C09264FC1CDA5 | SHA256:ECEEDADFDE8506A73650CFA9A936E6A8FFF7FFB664C9602BB14432AA2F8109AC | |||
| 4816 | SpongebobFuck.exe | C:\Users\admin\AppData\Local\Temp\DD43.tmp\mover.exe | executable | |
MD5:C1978E4080D1EC7E2EDF49D6C9710045 | SHA256:C9E2A7905501745C304FFC5A70B290DB40088D9DC10C47A98A953267468284A8 | |||
| 4816 | SpongebobFuck.exe | C:\Users\admin\AppData\Local\Temp\DD43.tmp\MainWindow.exe | executable | |
MD5:03D8B31DB1ED1294334B872F756AD1A1 | SHA256:7E17DCAAFC07877E720B3FC0E666AC69E2DCE8E7458AE9B23902BCF5F8F2A40A | |||
| 4816 | SpongebobFuck.exe | C:\Users\admin\AppData\Local\Temp\DD43.tmp\bobspeak.vbs | text | |
MD5:8884A25E47D799F6BD3D4EC20F05A3B7 | SHA256:5A68437EDD63BD826A1F1557121D4C05114C608FD8A18A0C9C156A60D90BD0C1 | |||
| 392 | wscript.exe | C:\Users\admin\AppData\Roaming\Microsoft\Speech\Files\UserLexicons\SP_4FC21E5A7FB2400B88F9EAFE432B6441.dat | binary | |
MD5:4C0B1E759E0245D9322B21955B4ABC02 | SHA256:DC066BB545ADF03DB8BB6DA0A4D592C16A33E6630AB21C5B69601F7B71F77E3A | |||
| 4816 | SpongebobFuck.exe | C:\Users\admin\AppData\Local\Temp\DD43.tmp\SpongebobFuck.cmd | text | |
MD5:7A918ED93F7FB297E05464EDCCC46756 | SHA256:82FCB47B437DC1BEDB77648755770B7CD9A29342FD2AB972C8BD063968D04604 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
38
DNS requests
23
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6512 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6512 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7156 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5840 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5528 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5528 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2036 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6512 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6512 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2128 | svchost.exe | 95.100.186.9:443 | go.microsoft.com | AKAMAI-AS | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |