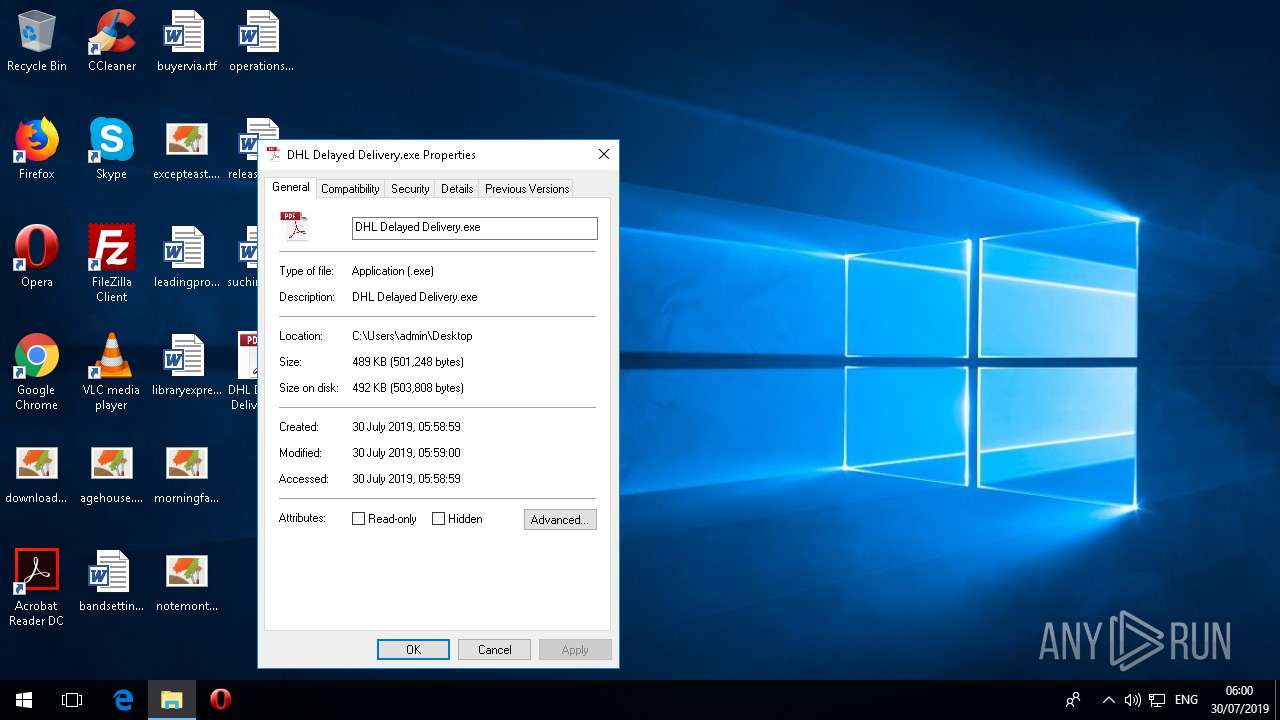
| File name: | DHL Delayed Delivery.exe |
| Full analysis: | https://app.any.run/tasks/c78272de-02db-44a5-8752-47b5d5e6bc06 |
| Verdict: | Suspicious activity |
| Analysis date: | July 30, 2019, 04:58:33 |
| OS: | Windows 10 Professional (build: 16299, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 54A7BB1AA43E5085CA622CEED233DA8C |
| SHA1: | FBA46AFF11653B08A6C7502DA23C53CB09FCF45B |
| SHA256: | A80C3D7574EF8FF681C40F8C0129CC192F339E887D536D1D915019B664E5F687 |
| SSDEEP: | 12288:2VObOcVp2clQjstK6inY/pfB7MKlPuglBmnooRftpJ:wcr2clQlg/T7MKJdmnoo/pJ |
MALICIOUS
Changes the autorun value in the registry
- DHL Delayed Delivery.exe (PID: 916)
SUSPICIOUS
Creates files in the user directory
- DHL Delayed Delivery.exe (PID: 916)
Executable content was dropped or overwritten
- DHL Delayed Delivery.exe (PID: 916)
Creates files in the program directory
- WerFault.exe (PID: 2960)
Reads Environment values
- WerFault.exe (PID: 2960)
INFO
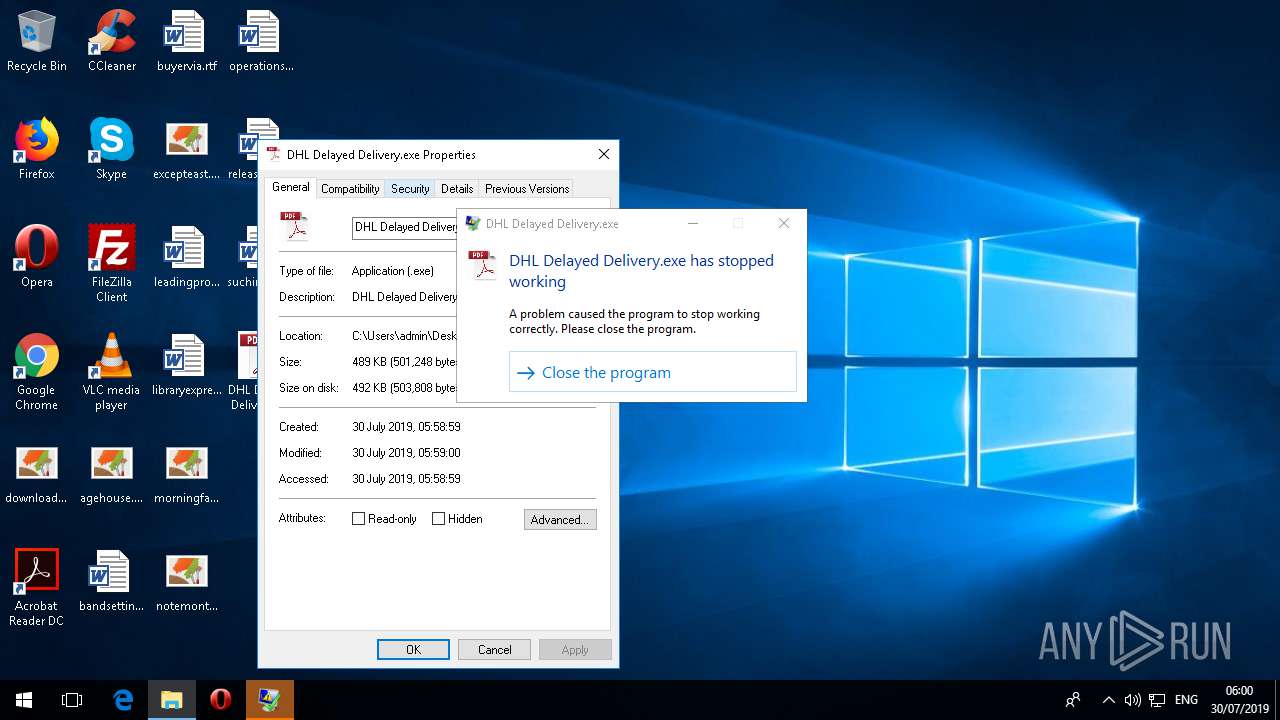
Application was crashed
- DHL Delayed Delivery.exe (PID: 916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2019:06:13 12:29:35+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 210944 |
| InitializedDataSize: | 289792 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x356e6 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 13-Jun-2019 10:29:35 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 13-Jun-2019 10:29:35 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x000336FC | 0x00033800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.1409 |
.rsrc | 0x00036000 | 0x00046930 | 0x00046A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.4807 |
.reloc | 0x0007E000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.10191 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
0 | 1.51664 | 20 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
1 | 7.97419 | 23091 | Latin 1 / Western European | English - United States | RT_ICON |
115 | 7.41361 | 265728 | Latin 1 / Western European | German - Germany | RT_HTML |
Imports
mscoree.dll |
Total processes
49
Monitored processes
2
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 916 | "C:\Users\admin\Desktop\DHL Delayed Delivery.exe" | C:\Users\admin\Desktop\DHL Delayed Delivery.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3762504530 Modules
| |||||||||||||||
| 2960 | C:\WINDOWS\system32\WerFault.exe -u -p 916 -s 9696 | C:\WINDOWS\system32\WerFault.exe | — | DHL Delayed Delivery.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
150
Read events
113
Write events
37
Delete events
0
Modification events
| (PID) Process: | (916) DHL Delayed Delivery.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | startupname |
Value: C:\Users\admin\AppData\Roaming\filename.exe | |||
| (PID) Process: | (2960) WerFault.exe | Key: | \REGISTRY\A\{e134eb41-29ff-3894-5404-473f93150a09}\Root\InventoryApplicationFile |
| Operation: | write | Name: | ProviderSyncId |
Value: {22b1115c-733a-4c56-978f-7579a80bf34b} | |||
| (PID) Process: | (2960) WerFault.exe | Key: | \REGISTRY\A\{e134eb41-29ff-3894-5404-473f93150a09}\Root\InventoryApplicationFile\dhl delayed deli|42b4fa58 |
| Operation: | write | Name: | ProgramId |
Value: 0006c1c5247488840eff3219ef302af9cc530000ffff | |||
| (PID) Process: | (2960) WerFault.exe | Key: | \REGISTRY\A\{e134eb41-29ff-3894-5404-473f93150a09}\Root\InventoryApplicationFile\dhl delayed deli|42b4fa58 |
| Operation: | write | Name: | FileId |
Value: 0000fba46aff11653b08a6c7502da23c53cb09fcf45b | |||
| (PID) Process: | (2960) WerFault.exe | Key: | \REGISTRY\A\{e134eb41-29ff-3894-5404-473f93150a09}\Root\InventoryApplicationFile\dhl delayed deli|42b4fa58 |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\users\admin\desktop\dhl delayed delivery.exe | |||
| (PID) Process: | (2960) WerFault.exe | Key: | \REGISTRY\A\{e134eb41-29ff-3894-5404-473f93150a09}\Root\InventoryApplicationFile\dhl delayed deli|42b4fa58 |
| Operation: | write | Name: | LongPathHash |
Value: dhl delayed deli|42b4fa58 | |||
| (PID) Process: | (2960) WerFault.exe | Key: | \REGISTRY\A\{e134eb41-29ff-3894-5404-473f93150a09}\Root\InventoryApplicationFile\dhl delayed deli|42b4fa58 |
| Operation: | write | Name: | Name |
Value: dhl delayed delivery.exe | |||
| (PID) Process: | (2960) WerFault.exe | Key: | \REGISTRY\A\{e134eb41-29ff-3894-5404-473f93150a09}\Root\InventoryApplicationFile\dhl delayed deli|42b4fa58 |
| Operation: | write | Name: | Publisher |
Value: | |||
| (PID) Process: | (2960) WerFault.exe | Key: | \REGISTRY\A\{e134eb41-29ff-3894-5404-473f93150a09}\Root\InventoryApplicationFile\dhl delayed deli|42b4fa58 |
| Operation: | write | Name: | Version |
Value: | |||
| (PID) Process: | (2960) WerFault.exe | Key: | \REGISTRY\A\{e134eb41-29ff-3894-5404-473f93150a09}\Root\InventoryApplicationFile\dhl delayed deli|42b4fa58 |
| Operation: | write | Name: | BinFileVersion |
Value: | |||
Executable files
1
Suspicious files
0
Text files
1
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2960 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\DHL Delayed Delivery.exe.916.dmp | — | |
MD5:— | SHA256:— | |||
| 2960 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6DE6.tmp.WERInternalMetadata.xml | xml | |
MD5:— | SHA256:— | |||
| 2960 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6B93.tmp.dmp | dmp | |
MD5:— | SHA256:— | |||
| 916 | DHL Delayed Delivery.exe | C:\Users\admin\AppData\Roaming\filename.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
5
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 40.90.23.227:443 | https://login.live.com/RST2.srf | US | xml | 11.2 Kb | whitelisted |
— | — | POST | 200 | 40.90.23.227:443 | https://login.live.com/RST2.srf | US | xml | 9.85 Kb | whitelisted |
1628 | svchost.exe | GET | 200 | 2.21.41.70:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Windows%20Phone%20Production%20PCA%202012.crl | FR | der | 826 b | whitelisted |
1628 | svchost.exe | GET | 200 | 2.21.41.70:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl | FR | der | 564 b | whitelisted |
1628 | svchost.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | der | 824 b | whitelisted |
1628 | svchost.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 550 b | whitelisted |
1628 | svchost.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | der | 781 b | whitelisted |
1628 | svchost.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | der | 555 b | whitelisted |
1628 | svchost.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | der | 555 b | whitelisted |
1628 | svchost.exe | GET | 200 | 2.16.186.74:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | der | 1.11 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.90.23.227:443 | login.live.com | Microsoft Corporation | US | unknown |
1628 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1628 | svchost.exe | 2.21.41.70:80 | www.microsoft.com | GTT Communications Inc. | FR | malicious |
1628 | svchost.exe | 2.16.186.74:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
Threats
Process | Message |
|---|---|
DHL Delayed Delivery.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
DHL Delayed Delivery.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
DHL Delayed Delivery.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
DHL Delayed Delivery.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
DHL Delayed Delivery.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
DHL Delayed Delivery.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|
DHL Delayed Delivery.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1391
|
DHL Delayed Delivery.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\identityauthority.cpp, line 278
|