| File name: | bat2exe.exe |
| Full analysis: | https://app.any.run/tasks/556183b4-a9b0-457d-831e-00aa684c6588 |
| Verdict: | Malicious activity |
| Analysis date: | April 20, 2021, 09:23:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 7A56C8B9FFDD23E6F7A2D0EE422E0EB7 |
| SHA1: | ADA737E537318F5FB900865B6ECD5DE9B8AE58F6 |
| SHA256: | A80C25D09BFC8BC4AFFB8E394A7254574B7E7E39404404775382F005E6A067C6 |
| SSDEEP: | 24576:MddFMz0EHPf4R9urwd1Hj+2mZ1j6wF320ujMw91SnA4eOm4Bd7x:Mdd6z0sau41D+xr3O4wiA424Bj |
MALICIOUS
Drops executable file immediately after starts
- bat2exe.exe (PID: 2588)
SUSPICIOUS
Checks supported languages
- bat2exe.exe (PID: 2588)
- cmd.exe (PID: 3652)
- mode.com (PID: 3172)
- cmd.exe (PID: 3316)
- cscript.exe (PID: 2704)
- cmd.exe (PID: 1744)
- cscript.exe (PID: 2152)
Reads the computer name
- bat2exe.exe (PID: 2588)
- cscript.exe (PID: 2704)
- cscript.exe (PID: 2152)
Starts CMD.EXE for commands execution
- bat2exe.exe (PID: 2588)
- cmd.exe (PID: 3652)
Drops a file with a compile date too recent
- bat2exe.exe (PID: 2588)
Drops a file with too old compile date
- bat2exe.exe (PID: 2588)
Drops a file that was compiled in debug mode
- bat2exe.exe (PID: 2588)
Executable content was dropped or overwritten
- bat2exe.exe (PID: 2588)
Application launched itself
- cmd.exe (PID: 3652)
Executes scripts
- cmd.exe (PID: 3316)
- cmd.exe (PID: 1744)
INFO
Checks Windows Trust Settings
- cscript.exe (PID: 2152)
- cscript.exe (PID: 2704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| ProductVersion: | 2 |
|---|---|
| ProductName: | BAT2EXE |
| OriginalFileName: | bat2exe.exe |
| LegalCopyright: | Islam Adel |
| InternalName: | bat2exe.exe |
| FileVersion: | 2 |
| FileDescription: | Created by BAT2EXE.net |
| CompanyName: | Islam Adel |
| CharacterSet: | Unicode |
| LanguageCode: | English (U.S.) |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 2.0.0.0 |
| FileVersionNumber: | 2.0.0.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x1373c |
| UninitializedDataSize: | - |
| InitializedDataSize: | 36352 |
| CodeSize: | 82944 |
| LinkerVersion: | 6 |
| PEType: | PE32 |
| TimeStamp: | 2010:11:18 17:27:32+01:00 |
| MachineType: | Intel 386 or later, and compatibles |
Total processes
40
Monitored processes
7
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
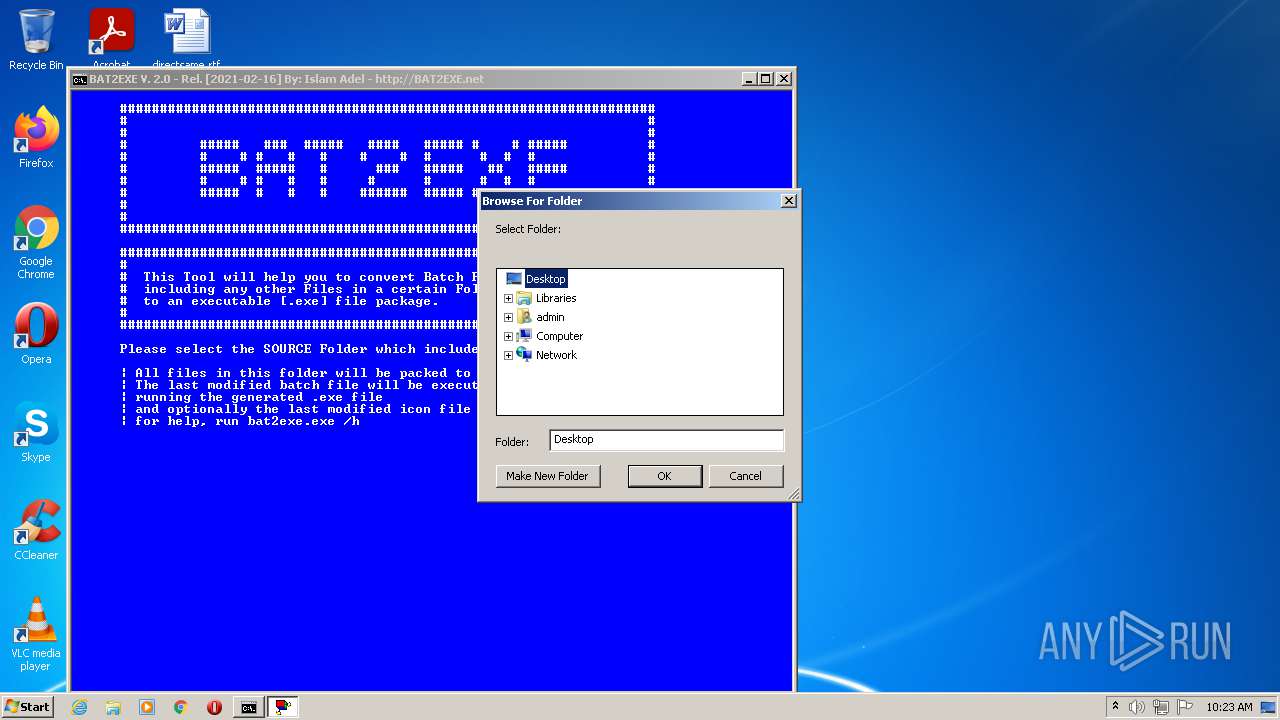
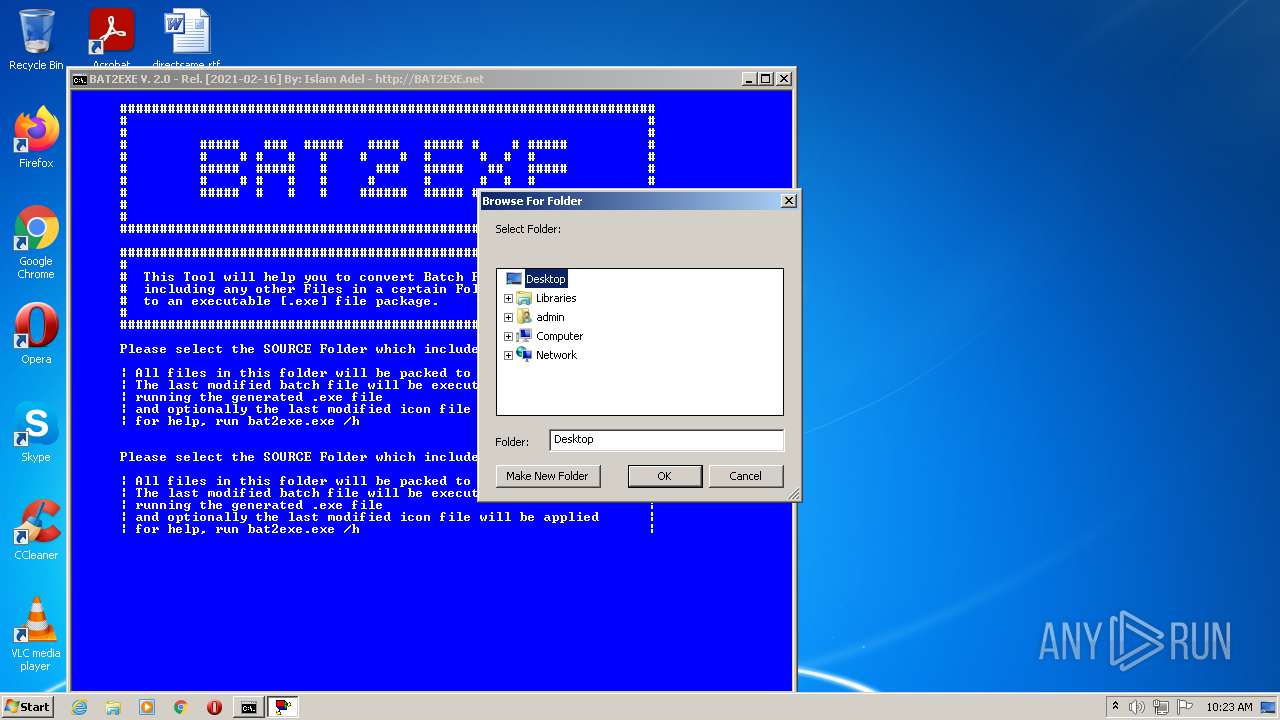
| 1744 | C:\Windows\system32\cmd.exe /c cscript //nologo bin\browse.vbs | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2152 | cscript //nologo bin\browse.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft � Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2588 | "C:\Users\admin\AppData\Local\Temp\bat2exe.exe" | C:\Users\admin\AppData\Local\Temp\bat2exe.exe | Explorer.EXE | ||||||||||||
User: admin Company: Islam Adel Integrity Level: MEDIUM Description: Created by BAT2EXE.net Exit code: 0 Version: 2.0 Modules
| |||||||||||||||
| 2704 | cscript //nologo bin\browse.vbs | C:\Windows\system32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft � Console Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3172 | MODE 90,50 | C:\Windows\system32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3316 | C:\Windows\system32\cmd.exe /c cscript //nologo bin\browse.vbs | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3652 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\7zS9155.tmp\bat2exe.cmd" " | C:\Windows\system32\cmd.exe | — | bat2exe.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 368
Read events
1 355
Write events
13
Delete events
0
Modification events
| (PID) Process: | (2588) bat2exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2588) bat2exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2588) bat2exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2588) bat2exe.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2704) cscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2704) cscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (2704) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (2704) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
| (PID) Process: | (2152) cscript.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
5
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2588 | bat2exe.exe | C:\Users\admin\AppData\Local\Temp\7zS9155.tmp\bin\7z.exe | executable | |
MD5:F17D0D9999EC81F734AF19D721C8DA96 | SHA256:EB021240D46F6C12E53FCF92F095EE87AAE055A82AE0D986318E8F8B57E463CB | |||
| 2588 | bat2exe.exe | C:\Users\admin\AppData\Local\Temp\7zS9155.tmp\bin\choice.exe | executable | |
MD5:E8F8B1058775103AC8BA6381345A4A57 | SHA256:4A1B84960EBB5E98F945A1935952633CD805A86B199D2DBCD140D75033636EC7 | |||
| 2588 | bat2exe.exe | C:\Users\admin\AppData\Local\Temp\7zS9155.tmp\bin\7z.dll | executable | |
MD5:23A37370F275AA63255DFCC703951C37 | SHA256:15B10608AFFD4442D0E2DDB9B2FEA847CD15D5405928D78AB73D81DAE66DB9E4 | |||
| 2588 | bat2exe.exe | C:\Users\admin\AppData\Local\Temp\7zS9155.tmp\bin\rcedit-x64.exe | executable | |
MD5:C1501B8075A6495634F6FA41C59F98DE | SHA256:02E8E8C5D430D8B768980F517B62D7792D690982B9BA0F7E04163CBC1A6E7915 | |||
| 2588 | bat2exe.exe | C:\Users\admin\AppData\Local\Temp\7zS9155.tmp\bin\browse.vbs | text | |
MD5:8580D8CAB38506F200F4D935EDCC19BE | SHA256:CBAF396FF11D723E0FFF497C6B7AFEDABE6975BCB32B7512058732911111AB15 | |||
| 2588 | bat2exe.exe | C:\Users\admin\AppData\Local\Temp\7zS9155.tmp\bin\7zSD.sfx | executable | |
MD5:9E1DDC27083E1FFA5F7CA058860CF131 | SHA256:5EF5C39D7EC09DB365F24984AFAA80D1863F5056E20BB13E9B97A8D2775ACEE3 | |||
| 2588 | bat2exe.exe | C:\Users\admin\AppData\Local\Temp\7zS9155.tmp\bat2exe.cmd | text | |
MD5:DE17828363C64B86228226D8DD6B125C | SHA256:3D86572D4A0F14634DFB2B1EC7CAED5A55D053C25B32D840BC2DE0130CDBC3C7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report