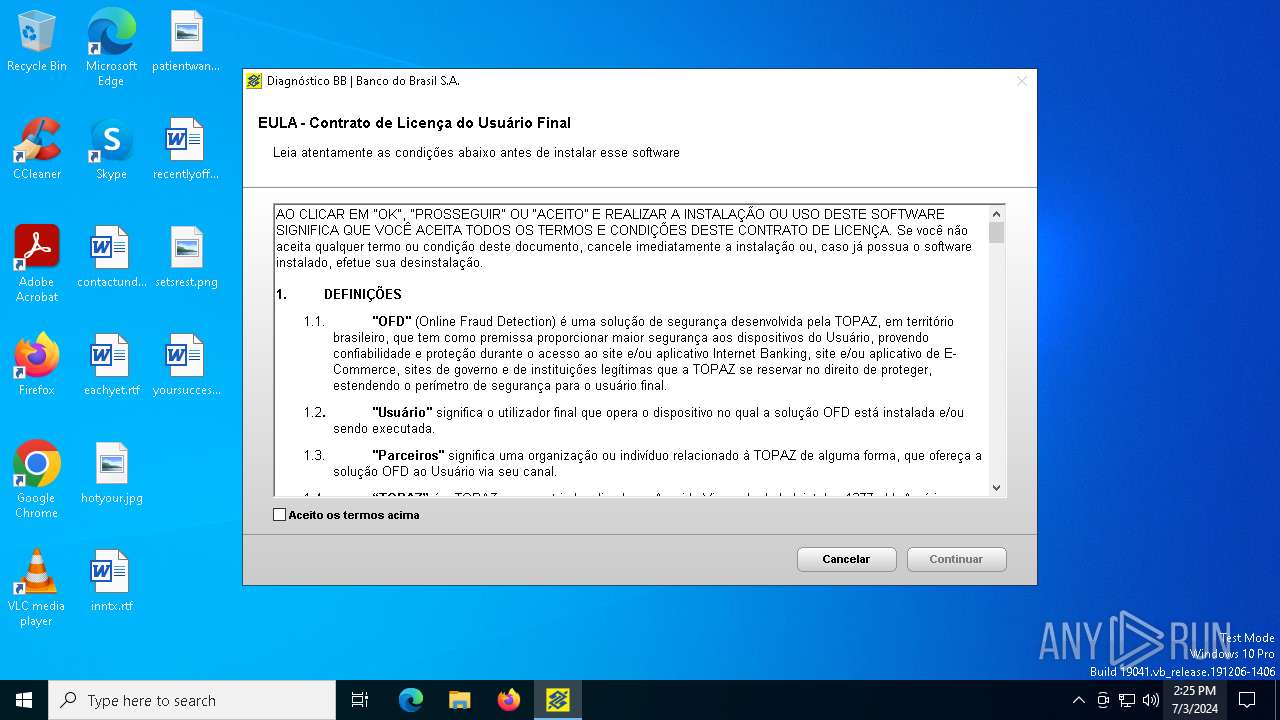
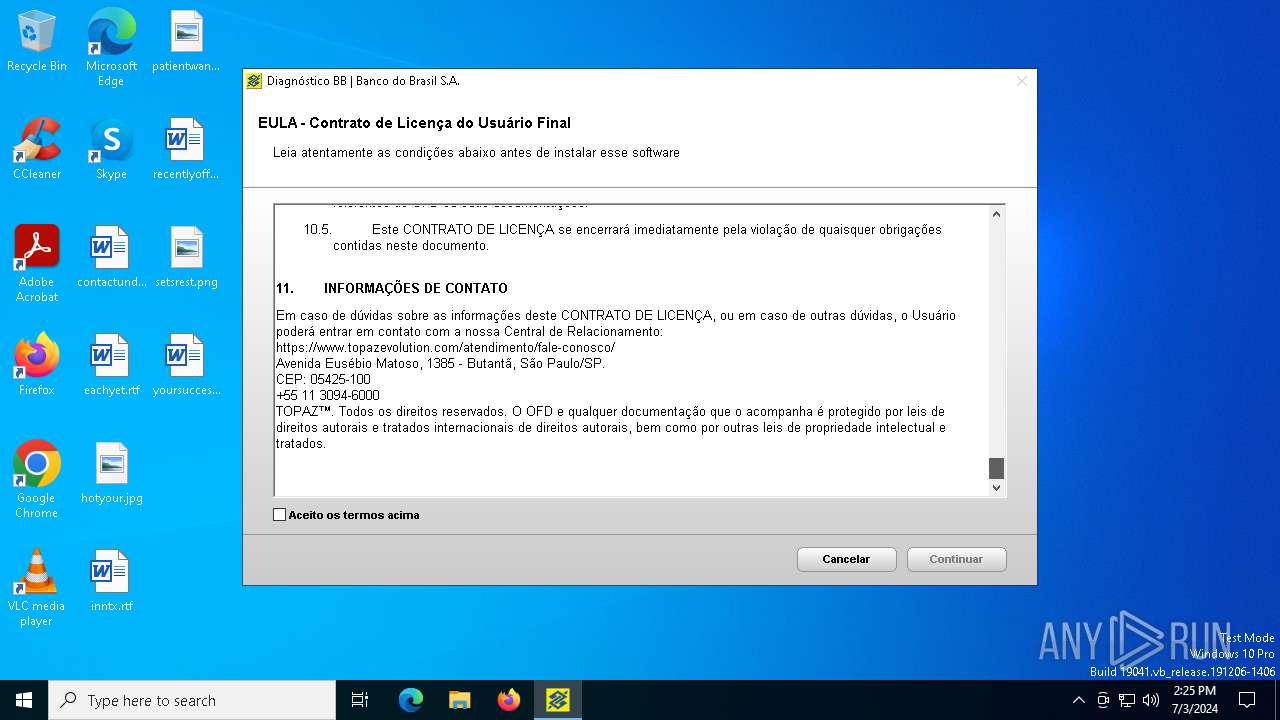
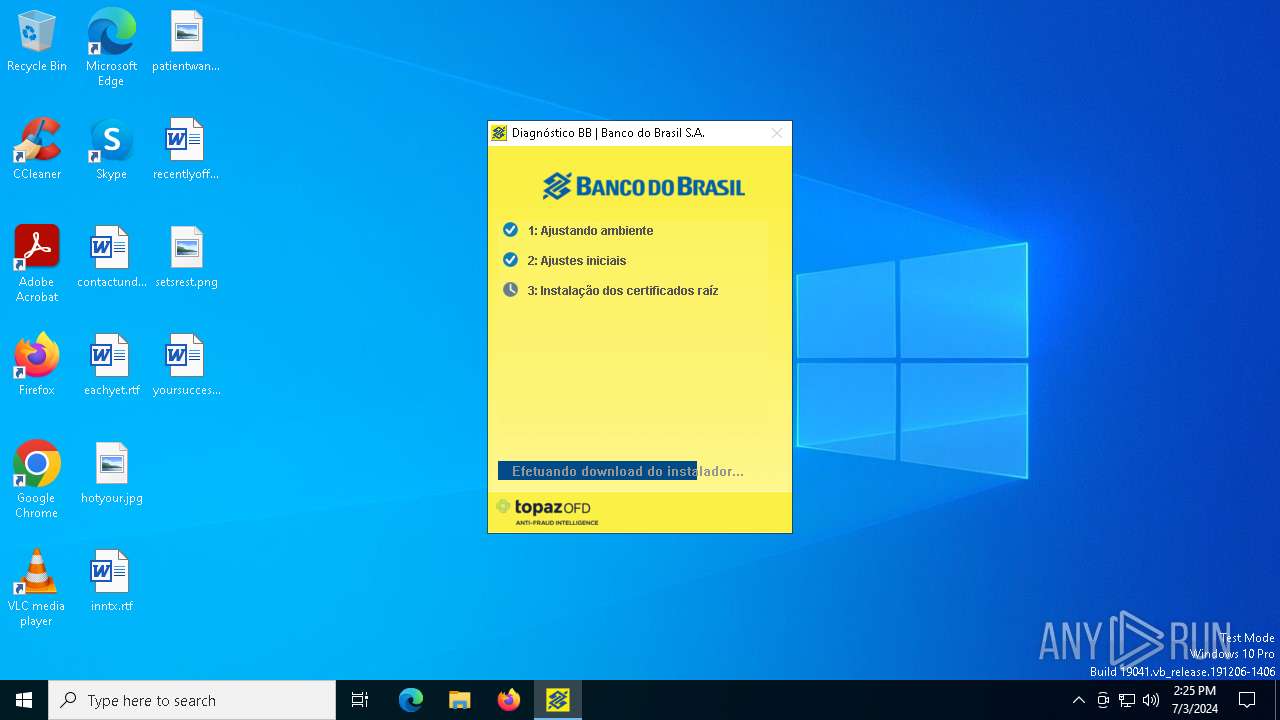
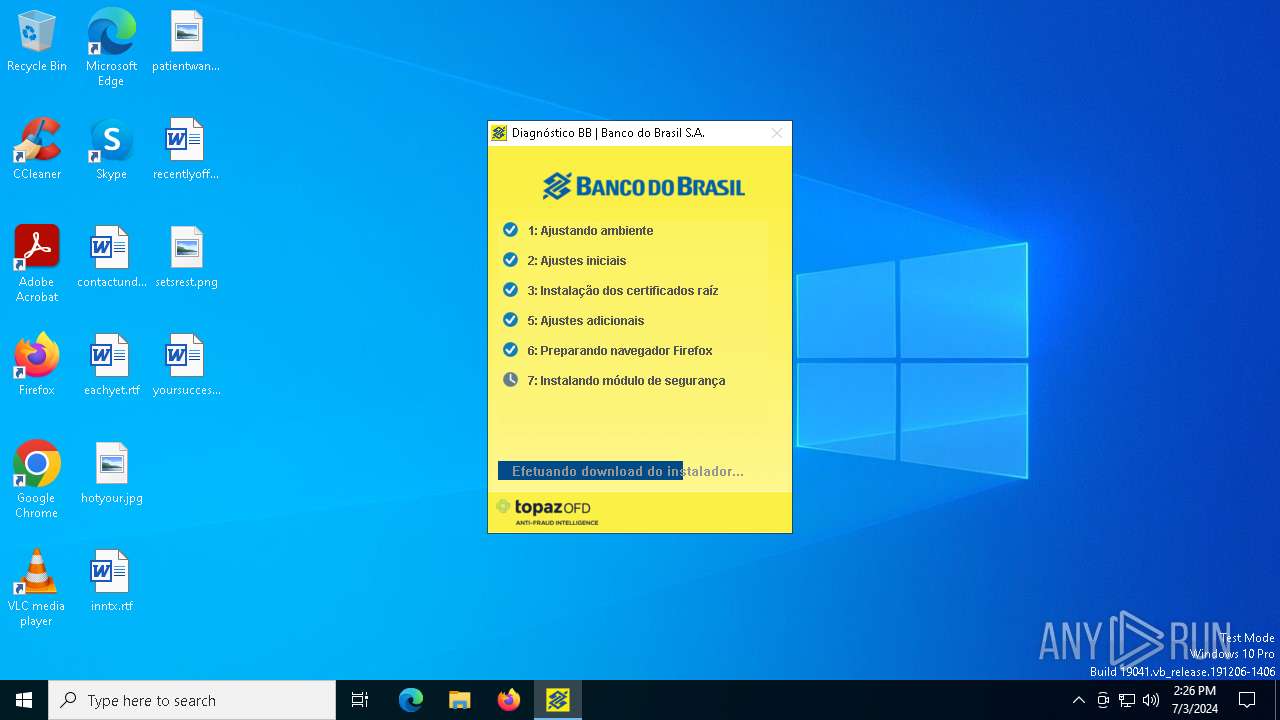
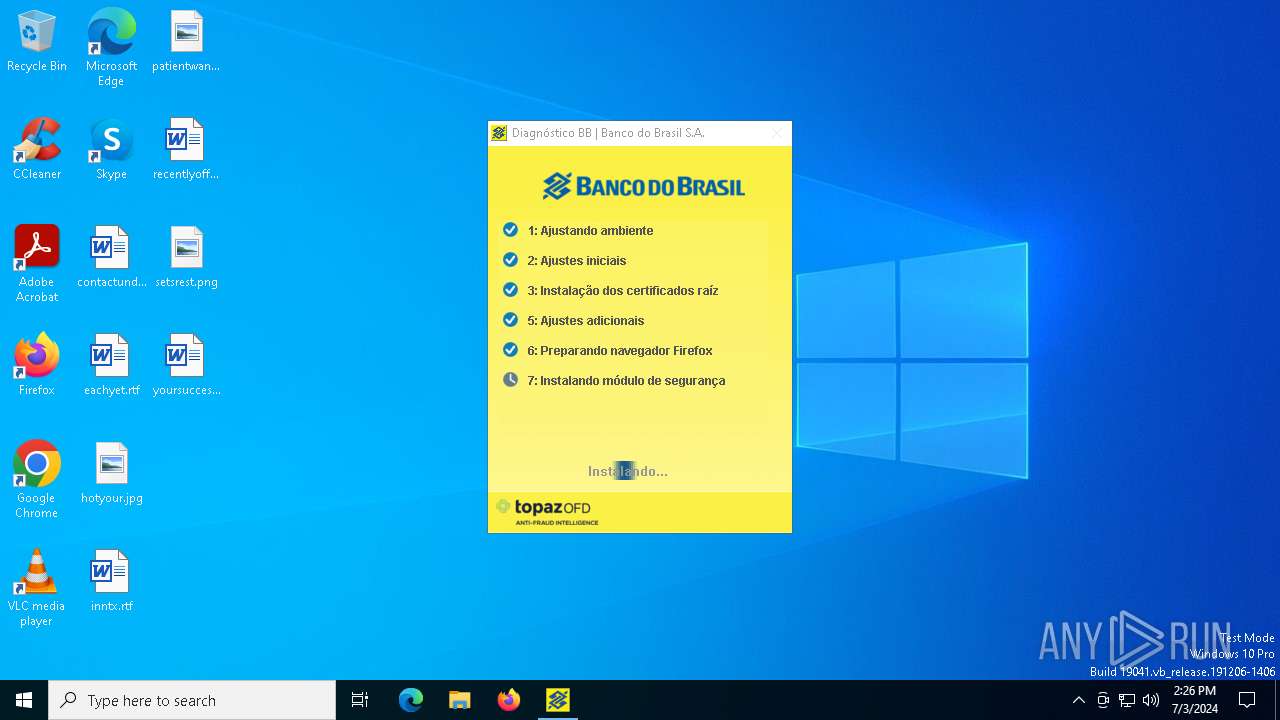
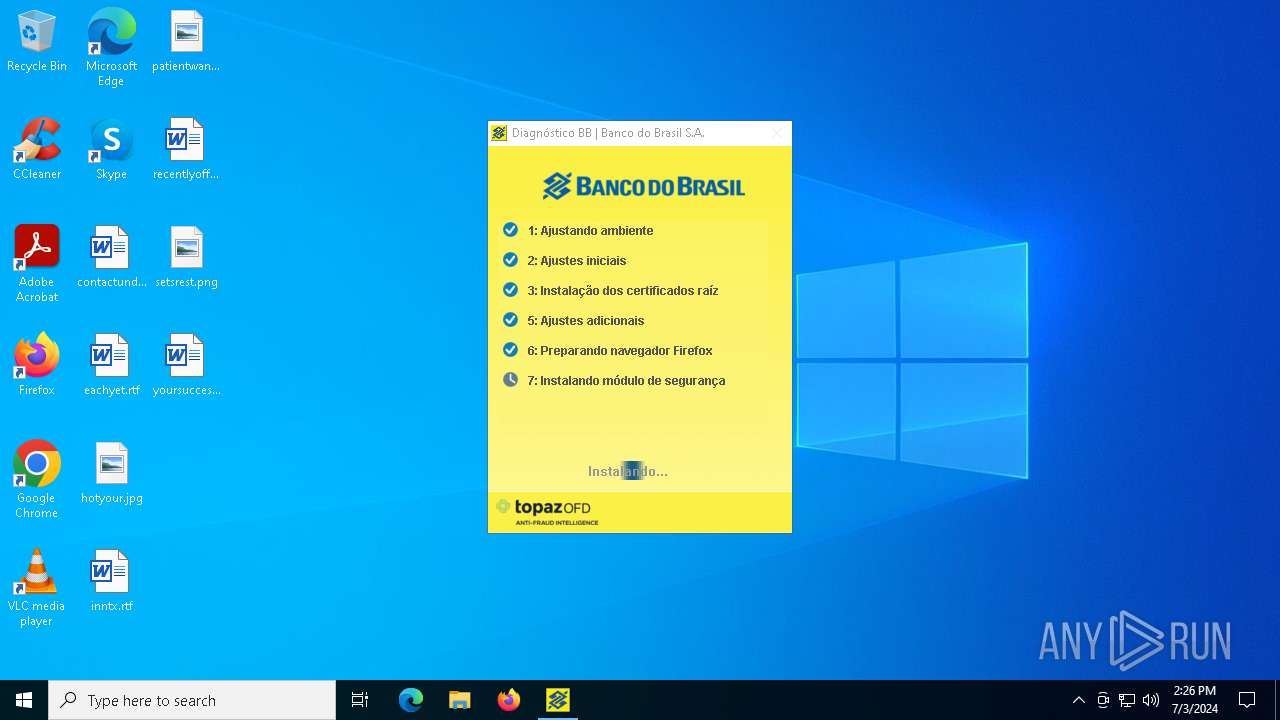
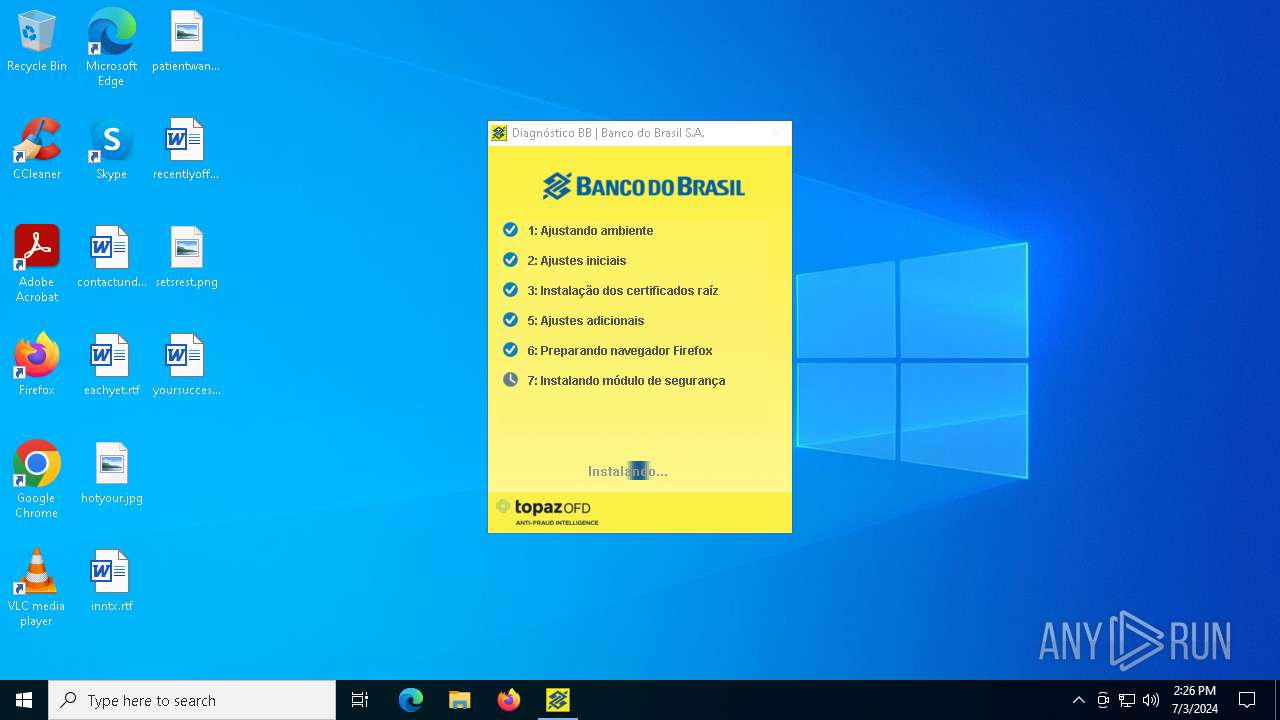
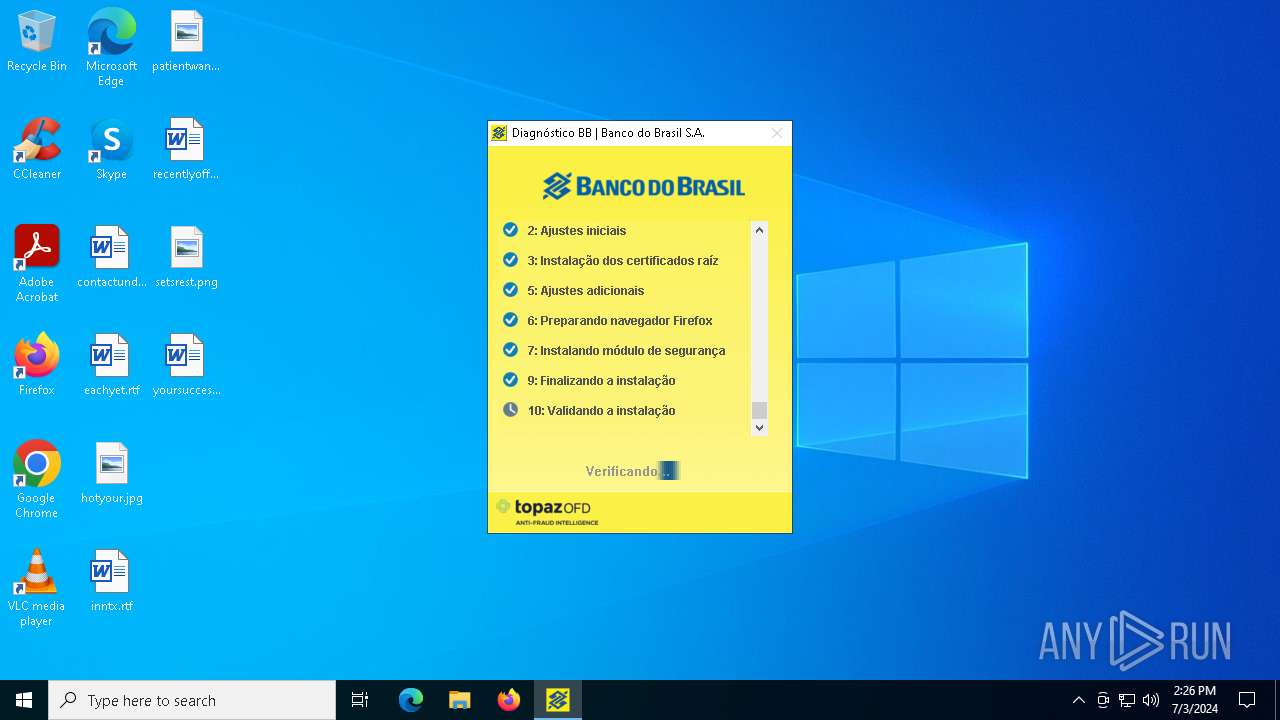
| download: | /bb/downloads/diagnostico/DiagnosticoBB.exe |
| Full analysis: | https://app.any.run/tasks/daa371e8-2ce0-42ef-a224-96d19cd9ecc7 |
| Verdict: | Malicious activity |
| Analysis date: | July 03, 2024, 14:25:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 005ADEE03FD375FA299D1ED14D8AC1E6 |
| SHA1: | B40CFD1E193E50242513CC8067B41451ED939D35 |
| SHA256: | A7FA1179F0611F276BE02C4A8F471DCD757D34B380295F0D6E6F6188EECEEDDF |
| SSDEEP: | 98304:Xnvh2ogQZ56KiOY9Xf0jF5U2lBAODPTx2qyrfFpa6XcVSWx+WyawH2ufUmhcYG1r:5YKR1lH4w |
MALICIOUS
Steals credentials from Web Browsers
- DiagnosticoBB.exe (PID: 6784)
- wsffcmgr64.exe (PID: 5132)
- wsffcmgr64.exe (PID: 4104)
- wsffcmgr64.exe (PID: 2108)
Actions looks like stealing of personal data
- DiagnosticoBB.exe (PID: 6784)
- wsffcmgr64.exe (PID: 5132)
- wsffcmgr64.exe (PID: 4104)
- wsffcmgr64.exe (PID: 2108)
Drops the executable file immediately after the start
- warsaw_setup64.exe (PID: 7012)
- DiagnosticoBB.exe (PID: 6784)
- core.exe (PID: 5608)
- warsaw_setup64.tmp (PID: 1708)
- drvinst.exe (PID: 480)
Deletes shadow copies
- cmd.exe (PID: 3808)
- cmd.exe (PID: 3780)
- cmd.exe (PID: 1272)
Creates a writable file in the system directory
- warsaw_setup64.tmp (PID: 1708)
- core.exe (PID: 5608)
- drvinst.exe (PID: 480)
SUSPICIOUS
Reads security settings of Internet Explorer
- DiagnosticoBB.exe (PID: 6784)
- core.exe (PID: 6712)
Application launched itself
- DiagnosticoBB.exe (PID: 6784)
- cmd.exe (PID: 3692)
- core.exe (PID: 5608)
Reads the date of Windows installation
- DiagnosticoBB.exe (PID: 6784)
- core.exe (PID: 5608)
Executes as Windows Service
- DiagnosticoBB.exe (PID: 1228)
- core.exe (PID: 5608)
Checks Windows Trust Settings
- DiagnosticoBB.exe (PID: 6784)
- DiagnosticoBB.exe (PID: 1228)
- core.exe (PID: 6712)
- core.exe (PID: 5608)
- wsffcmgr64.exe (PID: 5132)
- wsffcmgr64.exe (PID: 4104)
- drvinst.exe (PID: 480)
- wsffcmgr64.exe (PID: 2108)
Executable content was dropped or overwritten
- warsaw_setup64.exe (PID: 7012)
- warsaw_setup64.tmp (PID: 1708)
- DiagnosticoBB.exe (PID: 6784)
- core.exe (PID: 5608)
- drvinst.exe (PID: 480)
There is functionality for hijacking network configuration (YARA)
- DiagnosticoBB.exe (PID: 6784)
- DiagnosticoBB.exe (PID: 1228)
Reads the Windows owner or organization settings
- warsaw_setup64.tmp (PID: 1708)
Uses WMIC.EXE to obtain data on processes
- cmd.exe (PID: 3808)
- cmd.exe (PID: 1272)
- cmd.exe (PID: 3780)
Starts CMD.EXE for commands execution
- warsaw_setup64.tmp (PID: 1708)
- cmd.exe (PID: 3692)
- core.exe (PID: 5608)
Detected use of alternative data streams (AltDS)
- warsaw_setup64.tmp (PID: 1708)
- core.exe (PID: 5608)
The process drops C-runtime libraries
- warsaw_setup64.tmp (PID: 1708)
- core.exe (PID: 5608)
Drops a system driver (possible attempt to evade defenses)
- warsaw_setup64.tmp (PID: 1708)
- drvinst.exe (PID: 480)
Creates files in the driver directory
- warsaw_setup64.tmp (PID: 1708)
- core.exe (PID: 5608)
- drvinst.exe (PID: 480)
Process drops legitimate windows executable
- warsaw_setup64.tmp (PID: 1708)
- core.exe (PID: 5608)
Starts SC.EXE for service management
- warsaw_setup64.tmp (PID: 1708)
Creates or modifies Windows services
- core.exe (PID: 5608)
Creates a software uninstall entry
- warsaw_setup64.tmp (PID: 1708)
- core.exe (PID: 5608)
Reads the BIOS version
- core.exe (PID: 5608)
Executing commands from a ".bat" file
- warsaw_setup64.tmp (PID: 1708)
Get information on the list of running processes
- cmd.exe (PID: 3692)
- cmd.exe (PID: 3832)
Adds/modifies Windows certificates
- core.exe (PID: 5608)
- wsffcmgr64.exe (PID: 5132)
Loads DLL from Mozilla Firefox
- wsffcmgr64.exe (PID: 5132)
- wsffcmgr64.exe (PID: 4104)
- wsffcmgr64.exe (PID: 2108)
Creates/Modifies COM task schedule object
- core.exe (PID: 5608)
Searches for installed software
- core.exe (PID: 5608)
Found regular expressions for crypto-addresses (YARA)
- core.exe (PID: 5608)
INFO
Checks supported languages
- DiagnosticoBB.exe (PID: 6784)
- DiagnosticoBB.exe (PID: 3968)
- DiagnosticoBB.exe (PID: 1228)
- warsaw_setup64.tmp (PID: 1708)
- get_version.exe (PID: 6268)
- get_version.exe (PID: 7000)
- wstlcup.exe (PID: 2356)
- corefixer.exe (PID: 4832)
- core.exe (PID: 6436)
- core.exe (PID: 5608)
- core.exe (PID: 6712)
- warsaw_setup64.exe (PID: 7012)
- wsffcmgr64.exe (PID: 5132)
- drvinst.exe (PID: 480)
- wsffcmgr64.exe (PID: 2108)
- wsffcmgr64.exe (PID: 4104)
Reads the machine GUID from the registry
- DiagnosticoBB.exe (PID: 6784)
- DiagnosticoBB.exe (PID: 1228)
- DiagnosticoBB.exe (PID: 3968)
- get_version.exe (PID: 7000)
- get_version.exe (PID: 6268)
- core.exe (PID: 6436)
- core.exe (PID: 5608)
- core.exe (PID: 6712)
- wsffcmgr64.exe (PID: 5132)
- wsffcmgr64.exe (PID: 4104)
- wsffcmgr64.exe (PID: 2108)
- drvinst.exe (PID: 480)
Checks proxy server information
- DiagnosticoBB.exe (PID: 6784)
- core.exe (PID: 6712)
- slui.exe (PID: 6560)
Reads the computer name
- DiagnosticoBB.exe (PID: 6784)
- DiagnosticoBB.exe (PID: 3968)
- DiagnosticoBB.exe (PID: 1228)
- warsaw_setup64.exe (PID: 7012)
- warsaw_setup64.tmp (PID: 1708)
- corefixer.exe (PID: 4832)
- core.exe (PID: 6436)
- core.exe (PID: 5608)
- core.exe (PID: 6712)
- wsffcmgr64.exe (PID: 5132)
- wsffcmgr64.exe (PID: 4104)
- wsffcmgr64.exe (PID: 2108)
- drvinst.exe (PID: 480)
Creates files in the program directory
- DiagnosticoBB.exe (PID: 6784)
- DiagnosticoBB.exe (PID: 1228)
- warsaw_setup64.tmp (PID: 1708)
- core.exe (PID: 5608)
Process checks computer location settings
- DiagnosticoBB.exe (PID: 6784)
Create files in a temporary directory
- DiagnosticoBB.exe (PID: 6784)
Process checks whether UAC notifications are on
- DiagnosticoBB.exe (PID: 6784)
- core.exe (PID: 5608)
Reads the software policy settings
- DiagnosticoBB.exe (PID: 1228)
- DiagnosticoBB.exe (PID: 6784)
- core.exe (PID: 6712)
- core.exe (PID: 5608)
- wsffcmgr64.exe (PID: 5132)
- drvinst.exe (PID: 480)
- wsffcmgr64.exe (PID: 2108)
- wsffcmgr64.exe (PID: 4104)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7016)
- WMIC.exe (PID: 1048)
- WMIC.exe (PID: 1668)
Reads Windows Product ID
- core.exe (PID: 5608)
Reads Microsoft Office registry keys
- core.exe (PID: 6712)
Creates files or folders in the user directory
- wsffcmgr64.exe (PID: 5132)
- wsffcmgr64.exe (PID: 4104)
- wsffcmgr64.exe (PID: 2108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:05 19:43:11+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 2484736 |
| InitializedDataSize: | 3746304 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1ce86b |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.13.0.1 |
| ProductVersionNumber: | 2.13.0.1 |
| FileFlagsMask: | 0x001f |
| FileFlags: | Private build |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Unknown (0016) |
| CharacterSet: | Unicode |
| CompanyName: | Banco do Brasil S.A. |
| FileDescription: | Diagnóstico BB |
| FileVersion: | 2,13,0,1 |
| InternalName: | HDA |
| LegalCopyright: | Copyright © 2024, Topaz |
| OriginalFileName: | DiagnosticoBB_CLOUD_PT |
| PrivateBuild: | 2,13,0,1 |
| ProductName: | Diagnóstico BB |
| ProductVersion: | 2,13,0,1 |
Total processes
189
Monitored processes
44
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | DrvInst.exe "4" "9" "C:\WINDOWS\system32\drivers\wsddntf.inf" "9" "4a6586d23" "00000000000001C8" "Service-0x0-3e7$\Default" "00000000000001E8" "208" "C:\WINDOWS\system32\drivers" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1048 | WMIC PROCESS WHERE "ExecutablePath like 'C:\\Program Files\\Topaz OFD\\Warsaw\\%'" DELETE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\Users\admin\AppData\Local\Temp\DiagnosticoBB.exe" service_service | C:\Users\admin\AppData\Local\Temp\DiagnosticoBB.exe | services.exe | ||||||||||||
User: SYSTEM Company: Banco do Brasil S.A. Integrity Level: SYSTEM Description: Diagnóstico BB Version: 2,13,0,1 Modules
| |||||||||||||||
| 1272 | "C:\WINDOWS\system32\cmd.exe" /C WMIC PROCESS WHERE "ExecutablePath like 'C:\\Program Files (x86)\\Topaz OFD\\Warsaw\\%'" DELETE | C:\Windows\System32\cmd.exe | — | warsaw_setup64.tmp | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1292 | find /C "core.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=NetworkAvailable | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1668 | WMIC PROCESS WHERE "ExecutablePath like 'C:\\Program Files (x86)\\Topaz OFD\\Warsaw\\%'" DELETE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1708 | "C:\WINDOWS\TEMP\is-E8B1N.tmp\warsaw_setup64.tmp" /SL5="$802B0,29947655,832512,C:\ProgramData\Temp\warsaw_setup64.exe" /verysilent /sp- /norestart /suppressmsgboxes /restartexitcode=3010 /nocancel /accepteula /log="C:\ProgramData\Temp\wslog.dat" | C:\Windows\Temp\is-E8B1N.tmp\warsaw_setup64.tmp | warsaw_setup64.exe | ||||||||||||
User: SYSTEM Company: Topaz Integrity Level: SYSTEM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Topaz OFD\Warsaw\wsffcmgr64.exe" | C:\Program Files\Topaz OFD\Warsaw\wsffcmgr64.exe | core.exe | ||||||||||||
User: SYSTEM Company: Topaz OFD Integrity Level: SYSTEM Description: Topaz OFD - Protection Module Exit code: 0 Version: 1.1.0.15 Modules
| |||||||||||||||
| 2356 | "C:\Program Files\Topaz OFD\Warsaw\wstlcup.exe" | C:\Program Files\Topaz OFD\Warsaw\wstlcup.exe | — | warsaw_setup64.tmp | |||||||||||
User: SYSTEM Company: Topaz OFD Integrity Level: SYSTEM Description: Topaz OFD - Certificate Updater Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
Total events
61 500
Read events
61 295
Write events
182
Delete events
23
Modification events
| (PID) Process: | (6784) DiagnosticoBB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | AutoHelpDesk |
Value: | |||
| (PID) Process: | (6784) DiagnosticoBB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6784) DiagnosticoBB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6784) DiagnosticoBB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6784) DiagnosticoBB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (1228) DiagnosticoBB.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | SecureProtocols |
Value: 128 | |||
| (PID) Process: | (1228) DiagnosticoBB.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | SecureProtocols |
Value: 640 | |||
| (PID) Process: | (1228) DiagnosticoBB.exe | Key: | HKEY_USERS\.DEFAULT\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | SecureProtocols |
Value: 2688 | |||
| (PID) Process: | (6784) DiagnosticoBB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AutoHelpDesk |
| Operation: | write | Name: | RebootTasks |
Value: PdFrF1VwVqSgMSKFlyg4yA== | |||
| (PID) Process: | (6784) DiagnosticoBB.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\AutoHelpDesk |
| Operation: | write | Name: | RebootTasks |
Value: 8M2vRSzKUyL8BGW6cA6F0npx8iGsqnFNLq6LaEF8Jr0= | |||
Executable files
841
Suspicious files
81
Text files
15
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1708 | warsaw_setup64.tmp | C:\Program Files\Topaz OFD\Warsaw:z2fzaw5z | — | |
MD5:— | SHA256:— | |||
| 6784 | DiagnosticoBB.exe | C:\ProgramData\Temp\_cd\589e49d4745d647094694c4d7b625bc5.wtcf | binary | |
MD5:D474DE575C39B2D39C8583C5C065498A | SHA256:7431E5F4C3C1CE4690774F0B61E05440883BA9A01ED00BA6ABD7806ED3B118CF | |||
| 6784 | DiagnosticoBB.exe | C:\ProgramData\Temp\cert0.cer | der | |
MD5:78F2FCAA601F2FB4EBC937BA532E7549 | SHA256:552F7BDCF1A7AF9E6CE672017F4F12ABF77240C78E761AC203D1D9D20AC89988 | |||
| 6784 | DiagnosticoBB.exe | C:\ProgramData\Temp\_cd\88561e6508a6a0d226eac047f2994a11.wtcf | binary | |
MD5:87CE0B7B2A0E4900E158719B37A89372 | SHA256:3E9099B5015E8F486C00BCEA9D111EE721FABA355A89BCF1DF69561E3DC6325C | |||
| 1228 | DiagnosticoBB.exe | C:\ProgramData\Temp\cert_temp\cert2.cer | binary | |
MD5:D474DE575C39B2D39C8583C5C065498A | SHA256:7431E5F4C3C1CE4690774F0B61E05440883BA9A01ED00BA6ABD7806ED3B118CF | |||
| 6784 | DiagnosticoBB.exe | C:\Users\admin\AppData\Local\Temp\Diagnóstico BB.log | text | |
MD5:69536B7FD0177DC833B3F9E205670743 | SHA256:7C0414461D56F8D5D207B9BB38261957F5368031B8C74EC2C4011D0172BC6128 | |||
| 1708 | warsaw_setup64.tmp | C:\Program Files\Topaz OFD\Warsaw\is-7G5CS.tmp | executable | |
MD5:9B7A4889FECD19D45717AD5158893C4D | SHA256:D5F762228B7D6821AB2C881D67CD82F34A7DC6DB1CC41CE906789565AC9841A5 | |||
| 6784 | DiagnosticoBB.exe | C:\ProgramData\Temp\_cd\85aa84dc0ec3b0c12198cb877272586d.wtcf | executable | |
MD5:C7A3CEABFC70886A9E39FFCCCA62ABDE | SHA256:560FB5516C1DA18A3D2CD32C583F52EA57439F9DAC9A5E3BB9E675F653F53001 | |||
| 1228 | DiagnosticoBB.exe | C:\ProgramData\Temp\cert_temp\cert1.cer | der | |
MD5:87CE0B7B2A0E4900E158719B37A89372 | SHA256:3E9099B5015E8F486C00BCEA9D111EE721FABA355A89BCF1DF69561E3DC6325C | |||
| 1708 | warsaw_setup64.tmp | C:\Program Files\Topaz OFD\Warsaw\unins000.exe | executable | |
MD5:9B7A4889FECD19D45717AD5158893C4D | SHA256:D5F762228B7D6821AB2C881D67CD82F34A7DC6DB1CC41CE906789565AC9841A5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
87
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
6216 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3156 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3972 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
3972 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4656 | SearchApp.exe | 92.123.104.53:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 92.123.104.53:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1968 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6064 | svchost.exe | 20.190.160.20:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1452 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1060 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
dn.gastecnologia.com.br |
| shared |