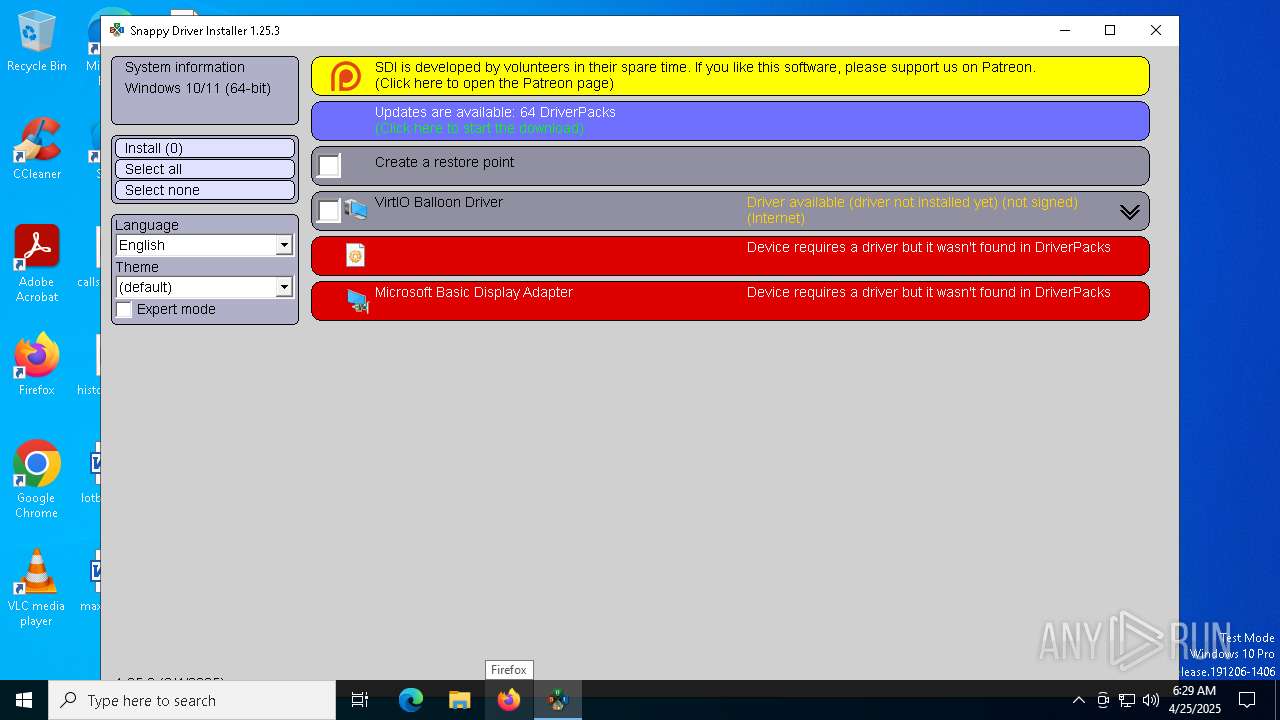
| File name: | SDI_x64_R2503.exe |
| Full analysis: | https://app.any.run/tasks/8c1fca1c-9f49-42bc-bb7e-62dab5baa7e8 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2025, 06:28:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64 (stripped to external PDB), for MS Windows, 10 sections |
| MD5: | 9EFE93E16003613E45640BBCFB661D9A |
| SHA1: | E64BF7DF324BD5B2773F166A37C96B9C107D8705 |
| SHA256: | A7F9959E42293A5A1056F03800C25C28B86D78CA196F6E9F9A24244AA5C444E9 |
| SSDEEP: | 98304:pJaF7p0B80o4rBpp7Ef9CKY+DGPfJWoDNE0nk+dtSDk8qmoHfj4SMkUMrbQC4UMa:/ |
MALICIOUS
BITTORRENT has been detected (SURICATA)
- SDI_x64_R2503.exe (PID: 7572)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- SDI_x64_R2503.exe (PID: 7572)
Potential Corporate Privacy Violation
- SDI_x64_R2503.exe (PID: 7572)
Reads the date of Windows installation
- SDI_x64_R2503.exe (PID: 7572)
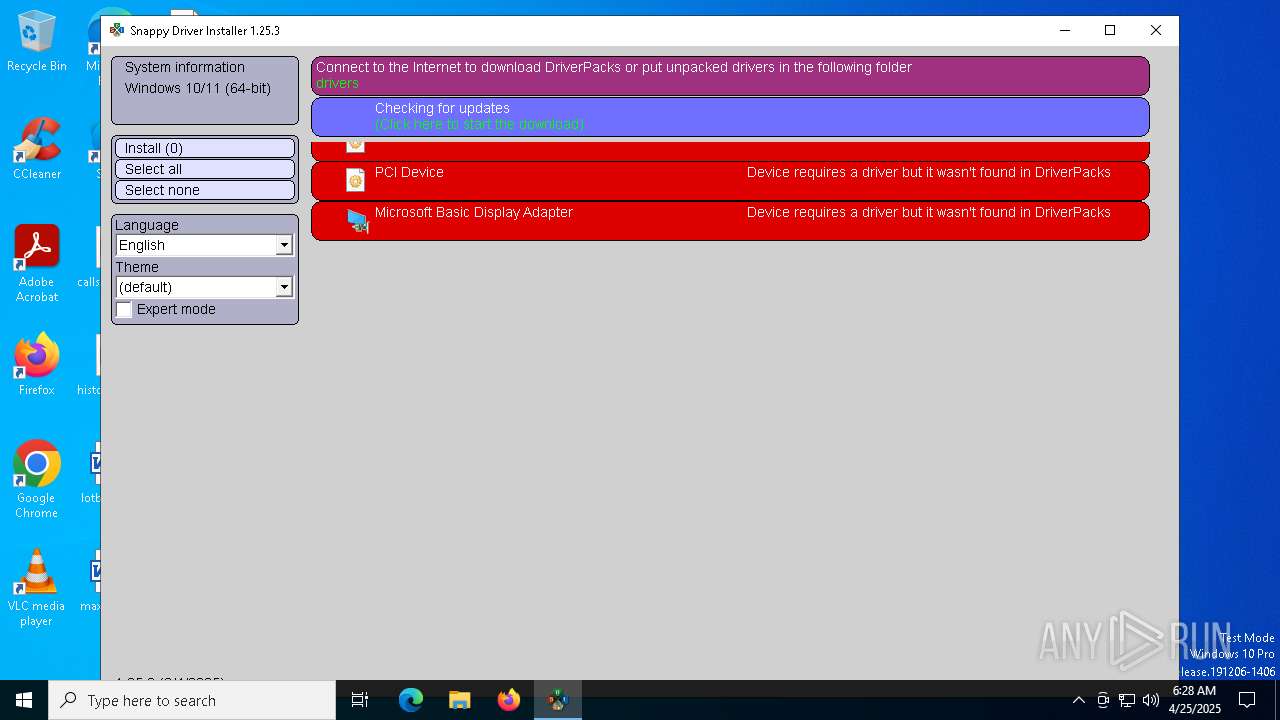
Connects to unusual port
- SDI_x64_R2503.exe (PID: 7572)
Starts CMD.EXE for commands execution
- SDI_x64_R2503.exe (PID: 7572)
Reads security settings of Internet Explorer
- SDI_x64_R2503.exe (PID: 7572)
INFO
The sample compiled with english language support
- SDI_x64_R2503.exe (PID: 7572)
Create files in a temporary directory
- SDI_x64_R2503.exe (PID: 7572)
Reads Environment values
- SDI_x64_R2503.exe (PID: 7572)
Checks supported languages
- SDI_x64_R2503.exe (PID: 7572)
Reads the software policy settings
- slui.exe (PID: 7652)
Process checks computer location settings
- SDI_x64_R2503.exe (PID: 7572)
Reads the computer name
- SDI_x64_R2503.exe (PID: 7572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.3) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:07 15:17:36+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, No debug |
| PEType: | PE32+ |
| LinkerVersion: | 2.25 |
| CodeSize: | 4171776 |
| InitializedDataSize: | 5518336 |
| UninitializedDataSize: | 186368 |
| EntryPoint: | 0x1500 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
| FileVersionNumber: | 1.25.3.2503 |
| ProductVersionNumber: | 1.25.3.2503 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | www.SamLab.ws |
| FileDescription: | Snappy Driver Installer |
| FileVersion: | 1.25 1.25.3 |
| LegalCopyright: | GNU GPL v3 |
| OriginalFileName: | SDI_1.25.3.exe |
| ProductName: | Snappy Driver Installer |
| ProductVersion: | 1.25.3 |
Total processes
135
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | "C:\Windows\System32\cmd.exe" /c rd /s /q update | C:\Windows\System32\cmd.exe | — | SDI_x64_R2503.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2568 | "C:\Windows\System32\cmd.exe" /c del indexes\SDI\_*.bin | C:\Windows\System32\cmd.exe | — | SDI_x64_R2503.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4380 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7464 | "C:\Users\admin\AppData\Local\Temp\SDI_x64_R2503.exe" | C:\Users\admin\AppData\Local\Temp\SDI_x64_R2503.exe | — | explorer.exe | |||||||||||
User: admin Company: www.SamLab.ws Integrity Level: MEDIUM Description: Snappy Driver Installer Exit code: 3221226540 Version: 1.25 1.25.3 Modules
| |||||||||||||||
| 7572 | "C:\Users\admin\AppData\Local\Temp\SDI_x64_R2503.exe" | C:\Users\admin\AppData\Local\Temp\SDI_x64_R2503.exe | explorer.exe | ||||||||||||
User: admin Company: www.SamLab.ws Integrity Level: HIGH Description: Snappy Driver Installer Version: 1.25 1.25.3 Modules
| |||||||||||||||
| 7584 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SDI_x64_R2503.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7612 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7652 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 632
Read events
2 632
Write events
0
Delete events
0
Modification events
Executable files
0
Suspicious files
140
Text files
238
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7572 | SDI_x64_R2503.exe | C:\Windows\INF\basicrender.PNF | binary | |
MD5:F016DC70D0F1F2EE230B7CBD412EB272 | SHA256:4BADD88B982667274200C6779BB677E763265F31F778F52B308198A7DF979F82 | |||
| 7572 | SDI_x64_R2503.exe | C:\Windows\INF\c_diskdrive.PNF | binary | |
MD5:46C721C4B5C76531BEEDD67F77025D23 | SHA256:5FEECEB625F66967C9D9264E463F612976A109967F4B4B2A89F824D4D051FEF6 | |||
| 7572 | SDI_x64_R2503.exe | C:\Windows\INF\basicdisplay.PNF | binary | |
MD5:914DCB989709A0CE3F4B24A4CD147F1A | SHA256:C2FEE0EAD23C7B3B509FDDE94DDD6A549F999F364C5CA9D09AC084F22BC0ECB4 | |||
| 7572 | SDI_x64_R2503.exe | C:\Users\admin\AppData\Local\Temp\update\SDI_RUS\indexes\SDI\DP_Sounds_Realtek_25020.bin | binary | |
MD5:E747905EB1509C5D6D4D7B417D0A3934 | SHA256:DA3F6BD3D813AA8B869DE937B02070348062D3F1B68512E3D27D4AF81880324F | |||
| 7572 | SDI_x64_R2503.exe | C:\Users\admin\AppData\Local\Temp\update\SDI_RUS\indexes\SDI\DP_LAN_Realtek-NT_25030.bin | binary | |
MD5:0D1FAA512B7E4191205357B1FB69616D | SHA256:C5396C9AD045A62C43038F7C6FD6C375E73226E5864FEF90150B1FCF25D23C6A | |||
| 7572 | SDI_x64_R2503.exe | C:\Users\admin\AppData\Local\Temp\update\SDI_RUS\indexes\SDI\DP_Printer_25020.bin | binary | |
MD5:23058EA2DB93E2C17A7A514C1A2EFC83 | SHA256:2DF438ECACC56980E7BC25BCEC2F9CBC244F409F42981B061A2413214C7CA88E | |||
| 7572 | SDI_x64_R2503.exe | C:\Users\admin\AppData\Local\Temp\update\SDI_RUS\indexes\SDI\DP_Misc_25030.bin | binary | |
MD5:721E0A953E30F06EAE8503A55F2C1BA9 | SHA256:A028C2B2EC0E8F0FDB336182F6139C2785151AFC7E46AD139EC89A9A0AC64E93 | |||
| 7572 | SDI_x64_R2503.exe | C:\Users\admin\AppData\Local\Temp\update\SDI_RUS\indexes\SDI\DP_Monitor_25030.bin | binary | |
MD5:D6F2BB86275397EBE5F9F81CC7250171 | SHA256:67E82413ABC325037DBB7E4185FA6DEC956447AD12D1D7A67AD95EE7182A7B66 | |||
| 7572 | SDI_x64_R2503.exe | C:\Users\admin\AppData\Local\Temp\update\SDI_RUS\indexes\SDI\DP_LAN_Others_25030.bin | binary | |
MD5:27DA6CDDFFF94DB921F8CB067FE17F21 | SHA256:CCEABC5DFEFA29E667357F75393A206EAC613E2B539433319B273037989D332A | |||
| 7572 | SDI_x64_R2503.exe | C:\Users\admin\AppData\Local\Temp\update\SDI_RUS\indexes\SDI\DP_zAndroid_25000.bin | binary | |
MD5:40AFE03CCC7D5F40F9CEB9567FBA39A1 | SHA256:56F8EF3FB3446FC4CCEDB09F43B7004C3E8843A6BA94FAEC61F729B4CFF49F72 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
597
DNS requests
21
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 92.122.244.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.56.30.102:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7572 | SDI_x64_R2503.exe | GET | 200 | 185.230.4.150:1337 | http://p4p.arenabg.com:1337/announce?info_hash=%93.%1a%fd%23%be%a5u%ce%7c%8b%ce%82%7f%19%9f%c6%95%d0_&peer_id=-LT1000-INg1lF7h8.xN&port=50171&uploaded=0&downloaded=0&left=47362897092&corrupt=0&key=14EAD1AB&event=started&numwant=200&compact=1&no_peer_id=1&supportcrypto=1&redundant=0 | unknown | — | — | whitelisted |
7572 | SDI_x64_R2503.exe | GET | 200 | 185.26.122.80:80 | http://sdi.com.ru/SDI_Update.torrent | unknown | — | — | unknown |
7388 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7388 | SIHClient.exe | GET | — | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7572 | SDI_x64_R2503.exe | GET | 200 | 185.230.4.150:1337 | http://p4p.arenabg.com:1337/announce?info_hash=%93.%1a%fd%23%be%a5u%ce%7c%8b%ce%82%7f%19%9f%c6%95%d0_&peer_id=-LT1000-INg1lF7h8.xN&port=50171&uploaded=0&downloaded=21795844&left=47341109248&corrupt=0&key=14EAD1AB&event=stopped&numwant=0&compact=1&no_peer_id=1&supportcrypto=1&redundant=0 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 92.122.244.32:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.56.30.102:80 | www.microsoft.com | AKAMAI-AS | HK | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.63.118.230:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
router.bittorrent.com |
| whitelisted |
router.utorrent.com |
| whitelisted |
router.bitcomet.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7572 | SDI_x64_R2503.exe | Potential Corporate Privacy Violation | ET P2P Possible Torrent Download via HTTP Request |
7572 | SDI_x64_R2503.exe | Potential Corporate Privacy Violation | ET P2P BitTorrent - Torrent File Downloaded |
7572 | SDI_x64_R2503.exe | Potential Corporate Privacy Violation | GPL P2P BitTorrent announce request |
7572 | SDI_x64_R2503.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |
7572 | SDI_x64_R2503.exe | Misc activity | INFO [ANY.RUN] P2P BitTorrent Protocol |