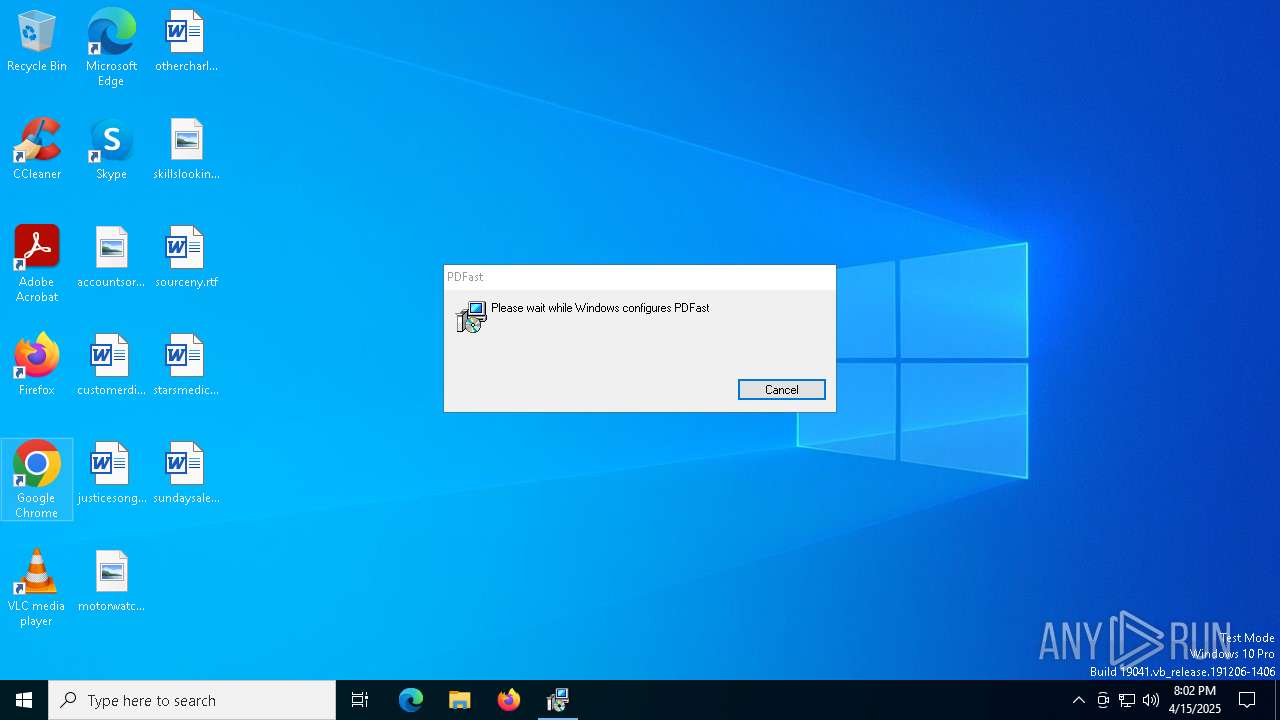
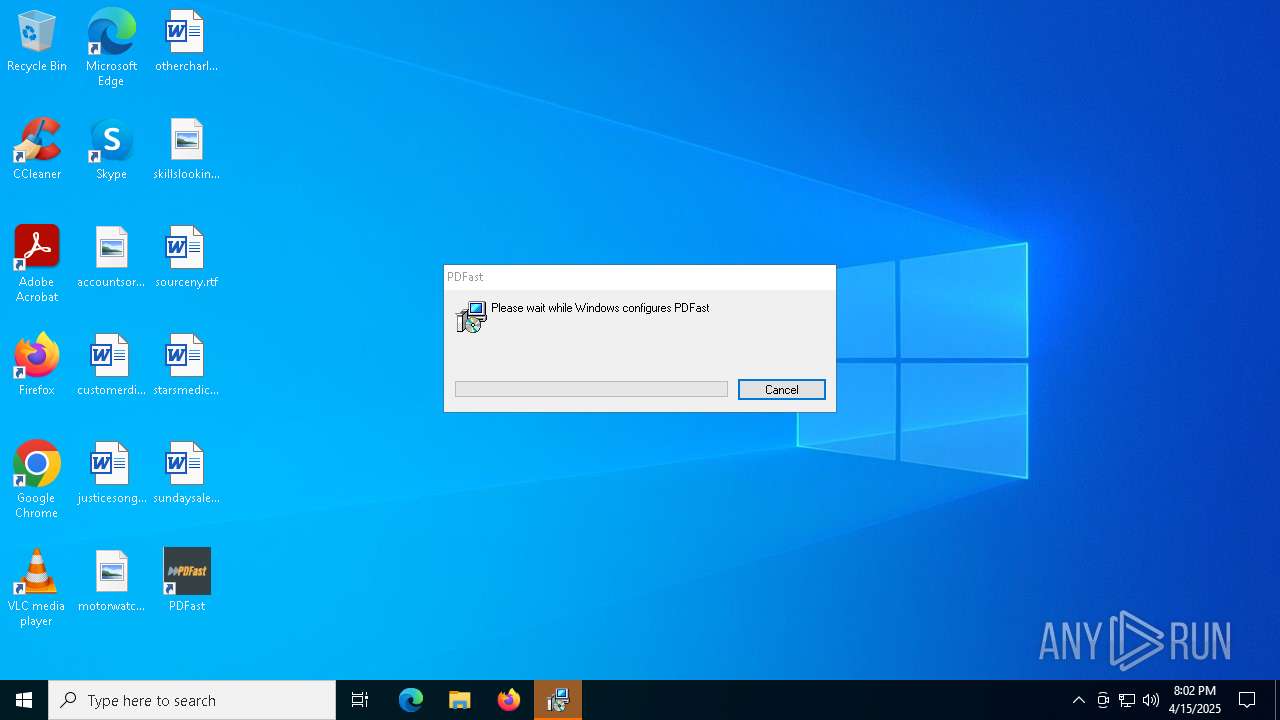
| File name: | PDFast.exe |
| Full analysis: | https://app.any.run/tasks/2b3cd9ef-6865-42ed-bcf1-33070b13d5b3 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2025, 20:02:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 1E995EEF7DEBA589543F502C4B14DA47 |
| SHA1: | 8950965F40F30EB40D11DE71754A4FE93B098F3D |
| SHA256: | A7F0794872BC5D0FEDCF6161C7002E0D9FC7E23CD8D390E0327DB7C010DD7A1A |
| SSDEEP: | 98304:pL0druM/vIX0pafjCHE6B5fMxNRlOqAhcNAjcXILaN2nVmqZLDvHUVGT4aSx2J5l:G7a88G |
MALICIOUS
No malicious indicators.SUSPICIOUS
ADVANCEDINSTALLER mutex has been found
- PDFast.exe (PID: 2384)
Executable content was dropped or overwritten
- PDFast.exe (PID: 2384)
- rundll32.exe (PID: 7584)
- rundll32.exe (PID: 7476)
- rundll32.exe (PID: 7736)
- rundll32.exe (PID: 7840)
Reads security settings of Internet Explorer
- PDFast.exe (PID: 2384)
Reads the Windows owner or organization settings
- PDFast.exe (PID: 2384)
- msiexec.exe (PID: 5868)
Process drops legitimate windows executable
- PDFast.exe (PID: 2384)
There is functionality for taking screenshot (YARA)
- PDFast.exe (PID: 2384)
Detects AdvancedInstaller (YARA)
- PDFast.exe (PID: 2384)
INFO
Checks supported languages
- PDFast.exe (PID: 2384)
- msiexec.exe (PID: 5868)
- msiexec.exe (PID: 4724)
- msiexec.exe (PID: 7400)
- identity_helper.exe (PID: 6728)
- identity_helper.exe (PID: 7188)
Reads the computer name
- PDFast.exe (PID: 2384)
- msiexec.exe (PID: 5868)
- msiexec.exe (PID: 4724)
- msiexec.exe (PID: 7400)
- identity_helper.exe (PID: 6728)
- identity_helper.exe (PID: 7188)
The sample compiled with english language support
- PDFast.exe (PID: 2384)
- msiexec.exe (PID: 5868)
Reads Environment values
- PDFast.exe (PID: 2384)
- msiexec.exe (PID: 4724)
- msiexec.exe (PID: 7400)
- identity_helper.exe (PID: 6728)
- identity_helper.exe (PID: 7188)
Reads the machine GUID from the registry
- PDFast.exe (PID: 2384)
- msiexec.exe (PID: 5868)
Reads the software policy settings
- PDFast.exe (PID: 2384)
- msiexec.exe (PID: 6540)
- msiexec.exe (PID: 5868)
- rundll32.exe (PID: 7476)
- rundll32.exe (PID: 7840)
Checks proxy server information
- PDFast.exe (PID: 2384)
- rundll32.exe (PID: 7476)
- rundll32.exe (PID: 7840)
Creates files or folders in the user directory
- PDFast.exe (PID: 2384)
- msiexec.exe (PID: 5868)
Create files in a temporary directory
- PDFast.exe (PID: 2384)
- rundll32.exe (PID: 7476)
- rundll32.exe (PID: 7584)
- rundll32.exe (PID: 7736)
- rundll32.exe (PID: 7840)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 6540)
- rundll32.exe (PID: 7736)
Executable content was dropped or overwritten
- msiexec.exe (PID: 5868)
Disables trace logs
- rundll32.exe (PID: 7476)
- rundll32.exe (PID: 7840)
Creates a software uninstall entry
- msiexec.exe (PID: 5868)
Application launched itself
- msedge.exe (PID: 7804)
- msedge.exe (PID: 6392)
Manual execution by a user
- WINWORD.EXE (PID: 5756)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (49.3) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (32.7) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.8) |
| .exe | | | Win32 Executable (generic) (5.3) |
| .exe | | | Generic Win/DOS Executable (2.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:08:08 12:49:22+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.36 |
| CodeSize: | 2534912 |
| InitializedDataSize: | 964608 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1e0862 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | PDFast |
| FileDescription: | PDFast Installer |
| FileVersion: | 1.0.0 |
| InternalName: | PDFast |
| LegalCopyright: | Copyright (C) 2025 PDFast |
| OriginalFileName: | PDFast.exe |
| ProductName: | PDFast |
| ProductVersion: | 1.0.0 |
Total processes
193
Monitored processes
56
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5596 --field-trial-handle=2392,i,15498483327680079889,6225572607533117680,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 616 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x290,0x294,0x298,0x288,0x2a0,0x7ffc89bc5fd8,0x7ffc89bc5fe4,0x7ffc89bc5ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 672 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4252 --field-trial-handle=2392,i,15498483327680079889,6225572607533117680,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 736 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=3324 --field-trial-handle=2364,i,6249686047590808789,1505621441517954797,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 780 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6700 --field-trial-handle=2392,i,15498483327680079889,6225572607533117680,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1116 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6468 --field-trial-handle=2392,i,15498483327680079889,6225572607533117680,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1164 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5760 --field-trial-handle=2392,i,15498483327680079889,6225572607533117680,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2108 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
32 445
Read events
31 994
Write events
415
Delete events
36
Modification events
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: EC160000E292055341AEDB01 | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 03E9217964DC3779C948D68306B8CD160687ADC7A4EAFD890FB27293A896EFA5 | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10dc6a.rbs |
Value: 31174209 | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10dc6a.rbsLow |
Value: | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Users\admin\AppData\Roaming\Microsoft\Installer\ |
Value: | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\C838C4529A8903C499B4533DE8B85105 |
| Operation: | write | Name: | 2869F0CE147ABAD43AAB440DC66A40AD |
Value: C:\Users\admin\AppData\Roaming\PDFast\ | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\95F7A40987D402143B8CB212542F8997 |
| Operation: | write | Name: | 2869F0CE147ABAD43AAB440DC66A40AD |
Value: 21:\Software\Microsoft\Windows\CurrentVersion\Uninstall\PDFast 1.0.0\DisplayName | |||
| (PID) Process: | (5868) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-21-1693682860-607145093-2874071422-1001\Components\E298DEB7803B2BE40A7ED48E1A8A57B5 |
| Operation: | write | Name: | 2869F0CE147ABAD43AAB440DC66A40AD |
Value: 21:\Software\Caphyon\Advanced Installer\LZMA\{EC0F9682-A741-4DAB-A3BA-44D06CA604DA}\1.0.0\AI_ExePath | |||
Executable files
56
Suspicious files
164
Text files
68
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | PDFast.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\9CB4373A4252DE8D2212929836304EC5_1AB74AA2E3A56E1B8AD8D3FEC287554E | binary | |
MD5:A6FF82A5C1E98BFE07C93F06A3F9B338 | SHA256:C55599CD3FAA2D2658EFD523197555F69CF4D1D08BA8C683B15A7EE236C43BE9 | |||
| 2384 | PDFast.exe | C:\Users\admin\AppData\Roaming\PDFast\PDFast 1.0.0\install\CA604DA\PDFast.msi | executable | |
MD5:9193849BA75ECA3516FDA249D9149700 | SHA256:D625019951CFD3FEEABE95307FC5C1D7E89D0749A5D8BE5FF62701A44206BAF4 | |||
| 2384 | PDFast.exe | C:\Users\admin\AppData\Local\Temp\shiD5E0.tmp | executable | |
MD5:84A34BF3486F7B9B7035DB78D78BDD1E | SHA256:F85911C910B660E528D2CF291BAA40A92D09961996D6D84E7A53A7095C7CD96E | |||
| 2384 | PDFast.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\357F04AD41BCF5FE18FCB69F60C6680F_17C8AB9779FC5F78079CADEDFCBF773B | binary | |
MD5:2F336FC8E0B1BE8BBCD9725AF5CB79DE | SHA256:BFDB83A9358770817399F166F49EB52F3CAD40F2BAC461494FE3E77E0A648908 | |||
| 2384 | PDFast.exe | C:\Users\admin\AppData\Roaming\PDFast\PDFast 1.0.0\install\holder0.aiph | binary | |
MD5:9D14DB0A481FC2E4FDE4706B5E475410 | SHA256:2F35C842455706BCA40332DC7D5F7FE6BB58A00041CFB861164A2DD1695221C6 | |||
| 5868 | msiexec.exe | C:\Windows\Installer\MSIE294.tmp | executable | |
MD5:B7A6A99CBE6E762C0A61A8621AD41706 | SHA256:39FD8D36F8E5D915AD571EA429DB3C3DE6E9C160DBEA7C3E137C9BA4B7FD301D | |||
| 7476 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\SFXCA9C83E396ED427298FAE9191200E9E4EB\RequestSender.dll | executable | |
MD5:19F78AA7A17C75B9D9CB9B3F83A01C31 | SHA256:7E0626A5C55B3603E73E3D021481A50C9C507F0B9B117951641EC1D87A545788 | |||
| 2384 | PDFast.exe | C:\Users\admin\AppData\Local\Temp\MSID729.tmp | executable | |
MD5:B7A6A99CBE6E762C0A61A8621AD41706 | SHA256:39FD8D36F8E5D915AD571EA429DB3C3DE6E9C160DBEA7C3E137C9BA4B7FD301D | |||
| 7476 | rundll32.exe | C:\Users\admin\AppData\Local\Temp\SFXCA9C83E396ED427298FAE9191200E9E4EB\WixToolset.Dtf.WindowsInstaller.dll | executable | |
MD5:EF8D5785AC8669F5FD54E22F52770E6B | SHA256:A614884EA627DA1925131EBF41E8AE202CAEAC0FE543B86384F5EB2BFAF1AA75 | |||
| 5868 | msiexec.exe | C:\Windows\Installer\MSIE1E7.tmp | executable | |
MD5:B7A6A99CBE6E762C0A61A8621AD41706 | SHA256:39FD8D36F8E5D915AD571EA429DB3C3DE6E9C160DBEA7C3E137C9BA4B7FD301D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
87
DNS requests
71
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2384 | PDFast.exe | GET | 200 | 151.101.194.133:80 | http://ocsp.globalsign.com/codesigningrootr45/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQVFZP5vqhCrtRN5SWf40Rn6NM1IAQUHwC%2FRoAK%2FHg5t6W0Q9lWULvOljsCEHe9DgW3WQu2HUdhUx4%2Fde0%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2384 | PDFast.exe | GET | 200 | 151.101.194.133:80 | http://ocsp.globalsign.com/gsgccr45evcodesignca2020/ME0wSzBJMEcwRTAJBgUrDgMCGgUABBQaCbVYh07WONuW4e63Ydlu4AlbDAQUJZ3Q%2FFkJhmPF7POxEztXHAOSNhECDH02JuY%2BNRarIhFtHg%3D%3D | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5756 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6972 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6972 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2384 | PDFast.exe | 151.101.194.133:80 | ocsp.globalsign.com | FASTLY | US | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.globalsign.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
b.pdf-fast.com |
| malicious |
config.edge.skype.com |
| whitelisted |
pdf-fast.com |
| malicious |