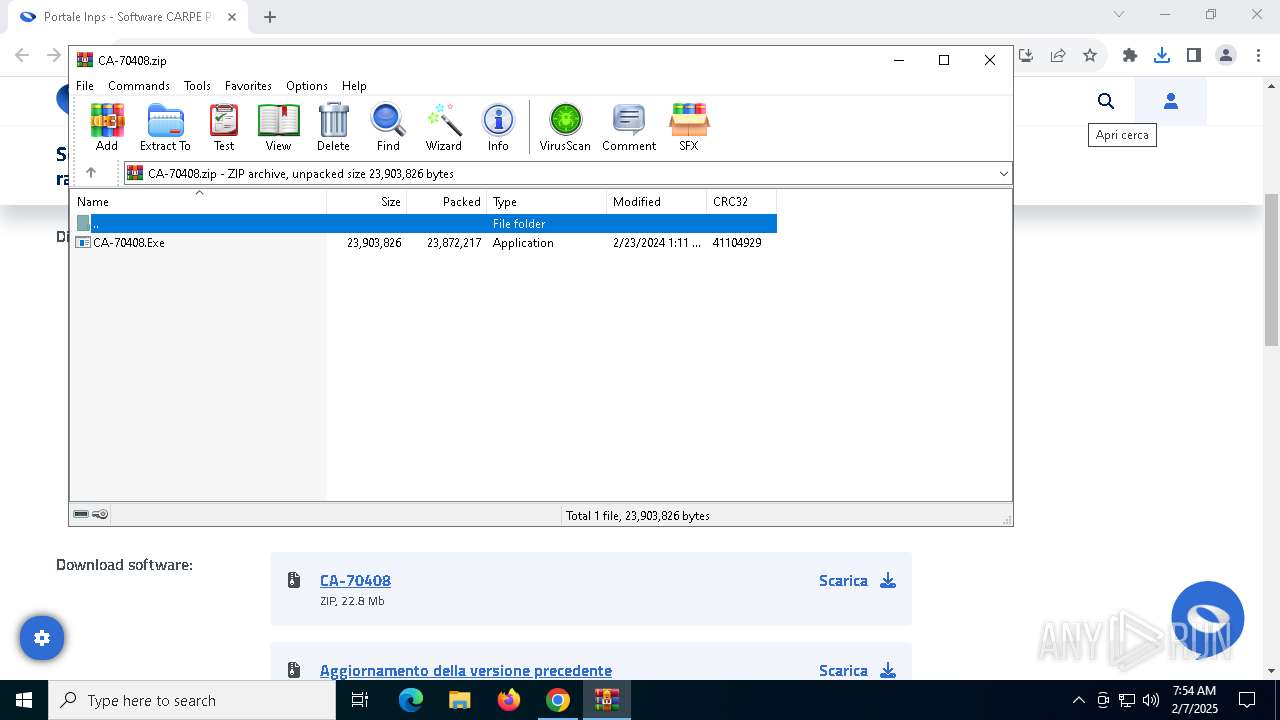
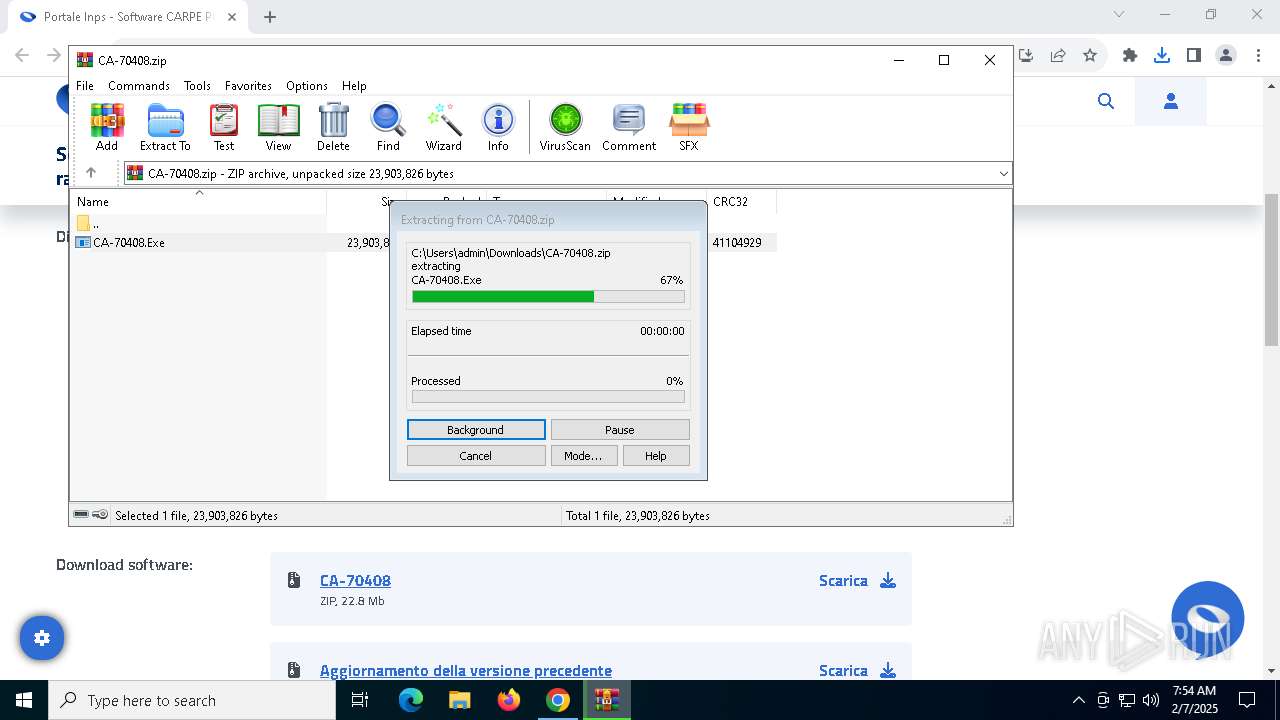
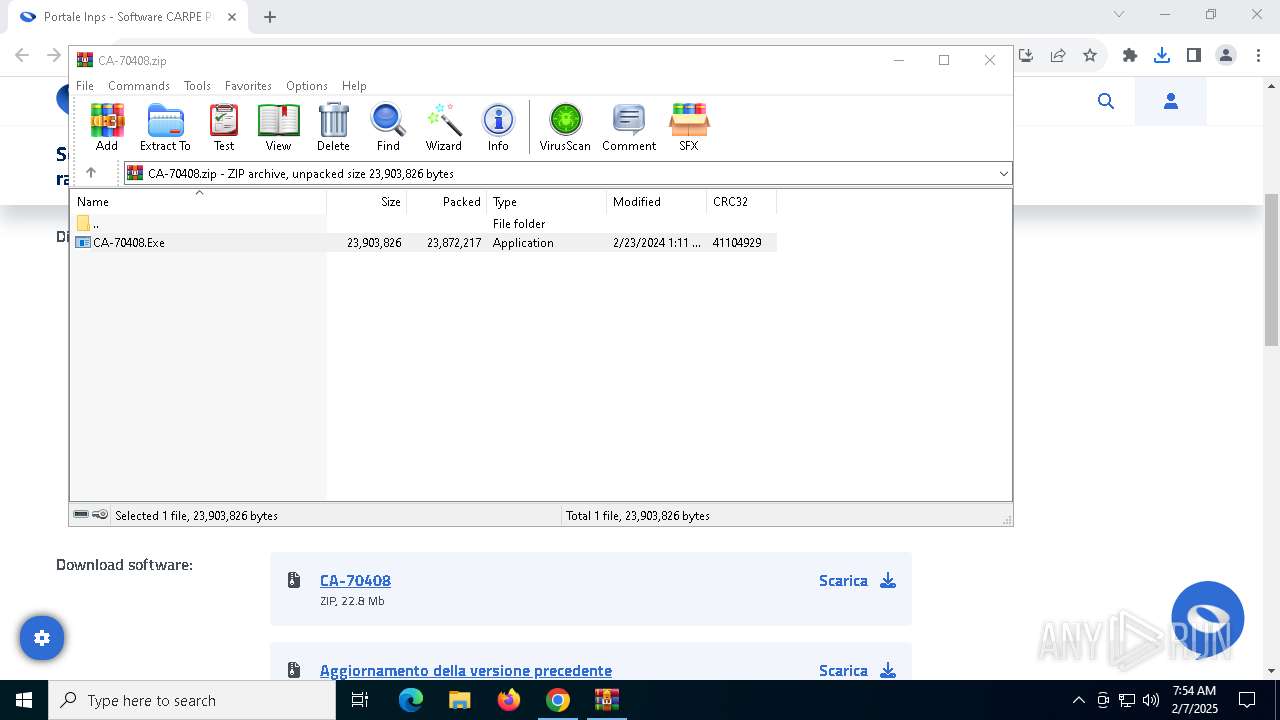
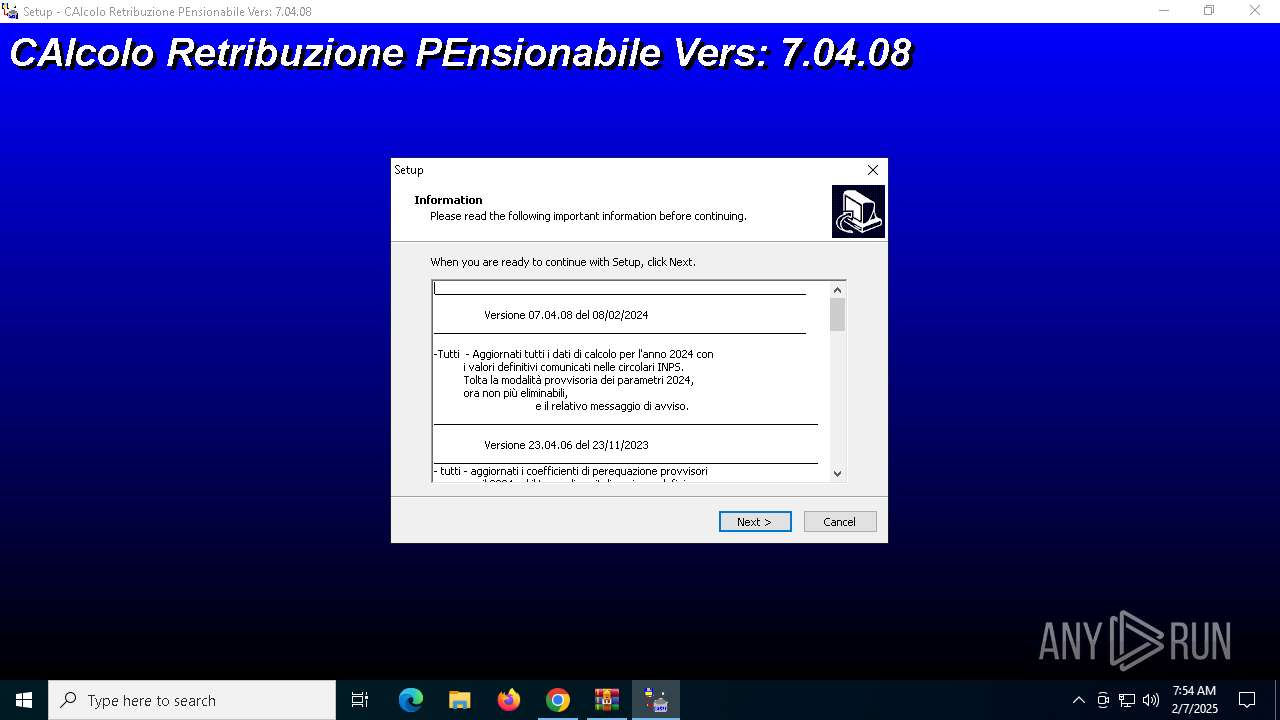
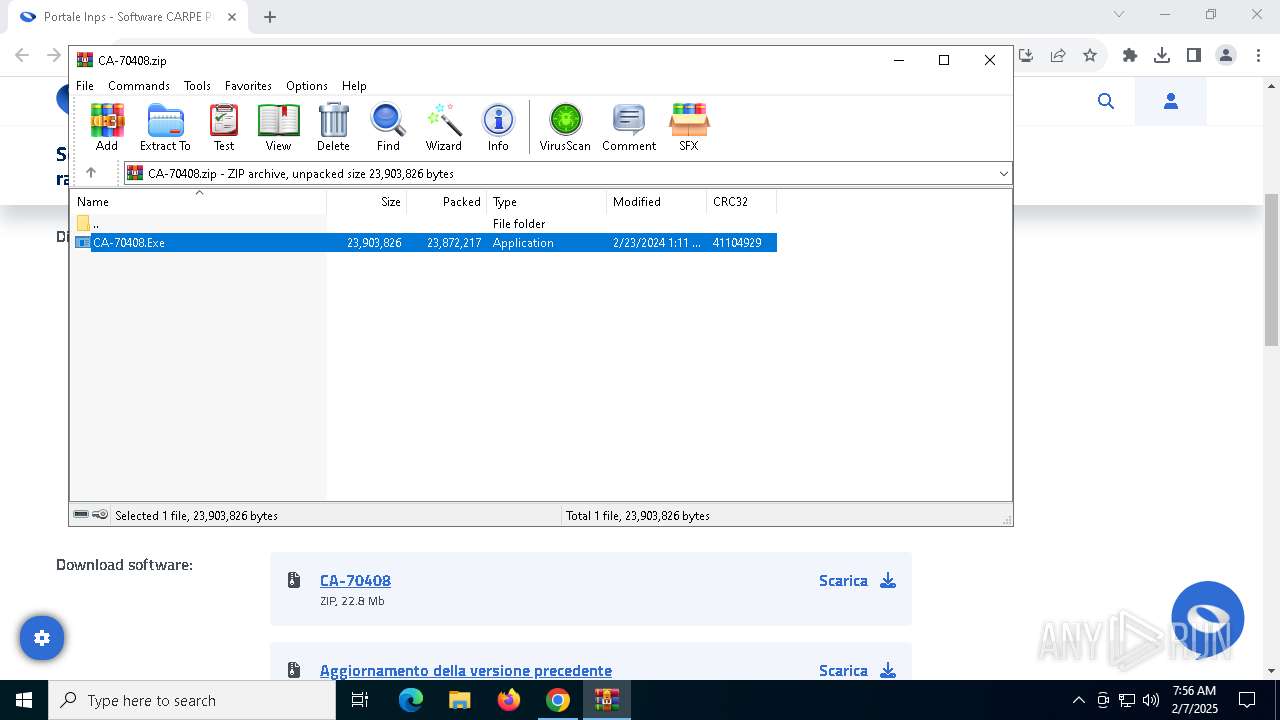
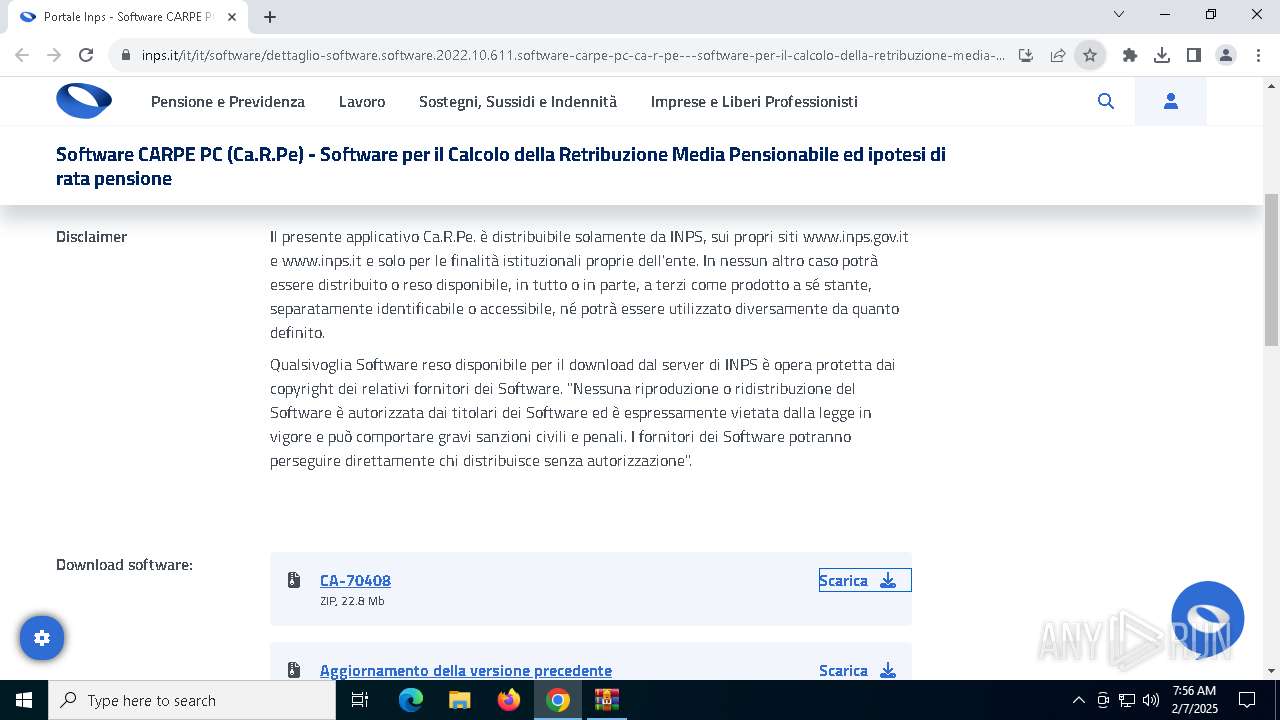
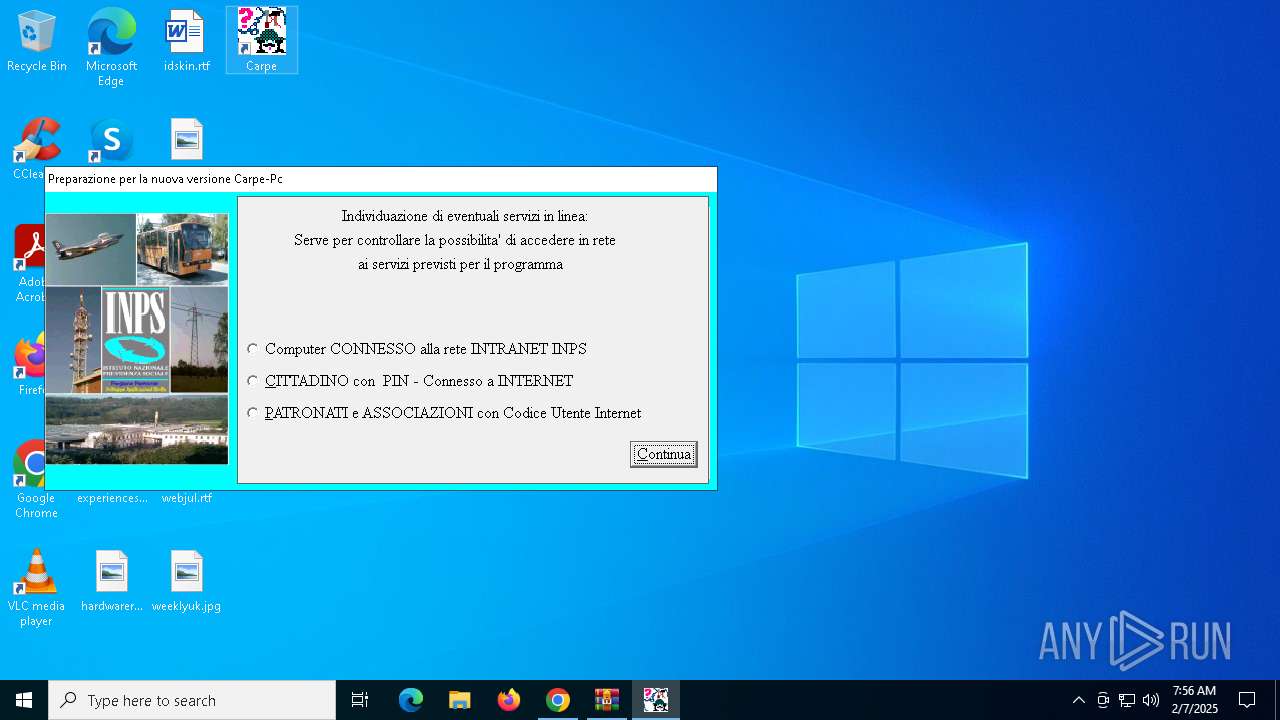
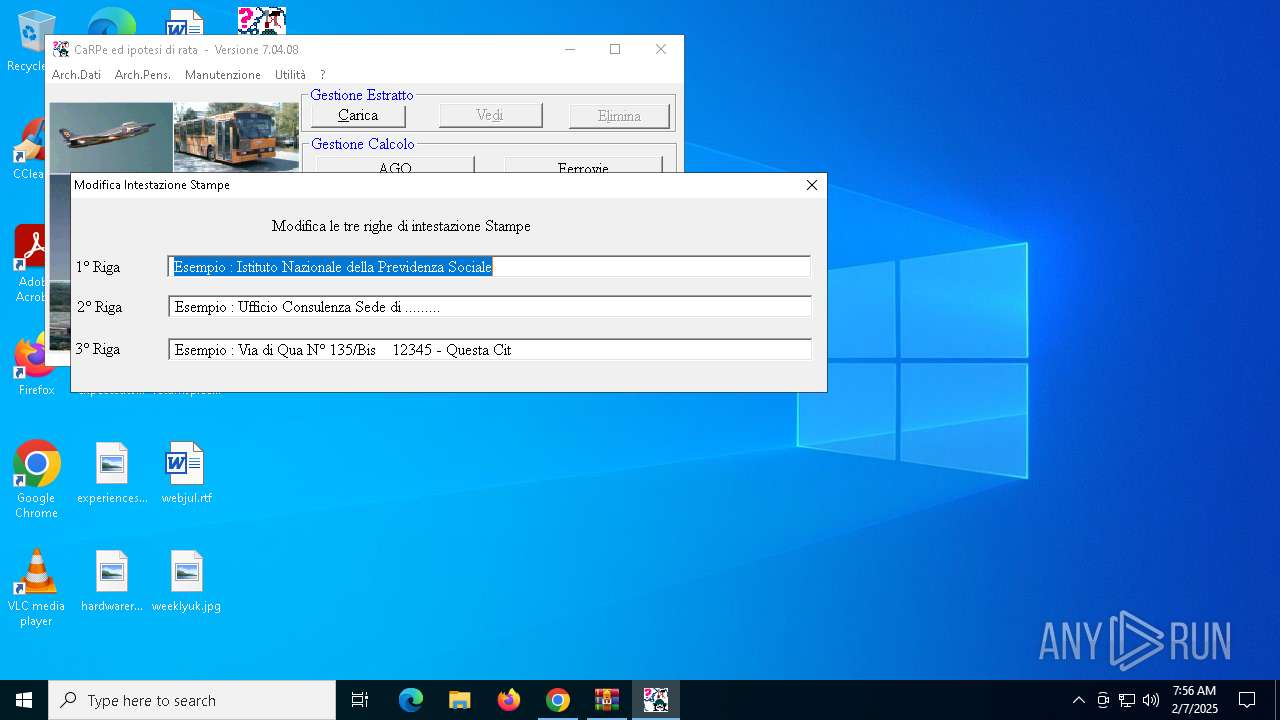
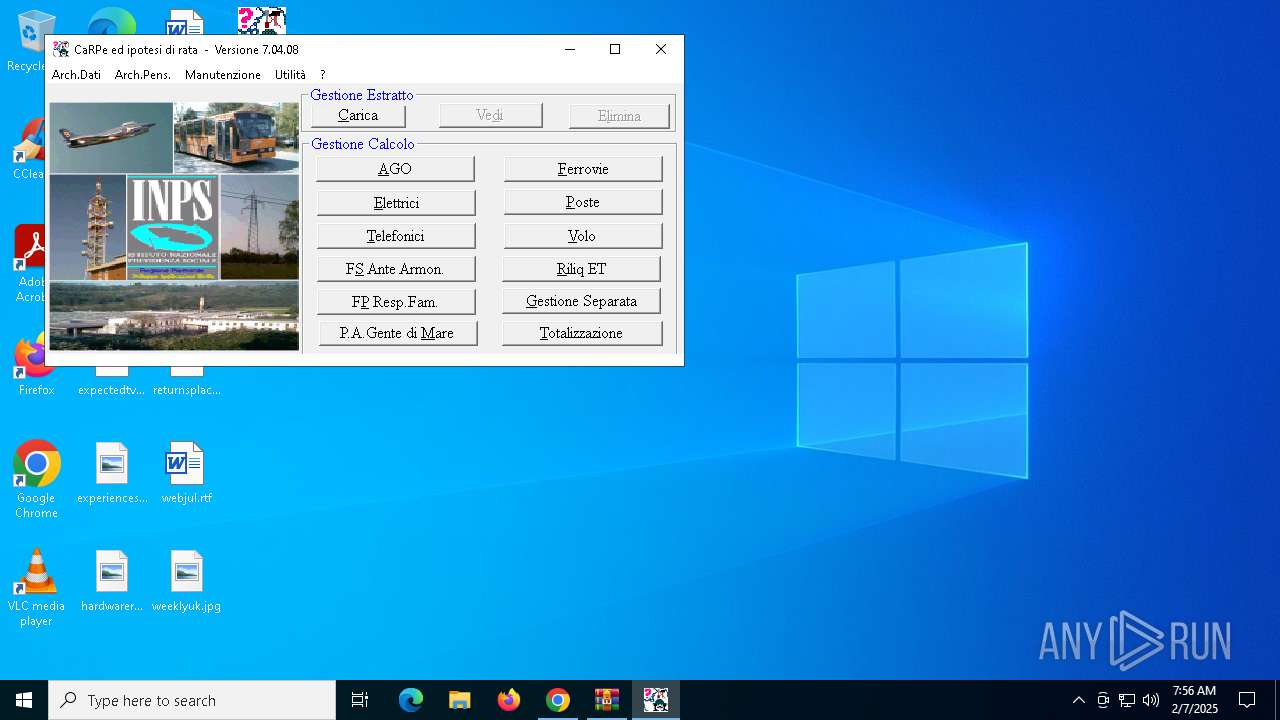
| URL: | https://www.inps.it/it/it/software/dettaglio-software.software.2022.10.611.software-carpe-pc-ca-r-pe---software-per-il-calcolo-della-retribuzione-media-pensionabile-ed-ipotesi-di-rata-pensione.html |
| Full analysis: | https://app.any.run/tasks/a21320d4-45be-4bd5-b775-d66b9a58b13e |
| Verdict: | Malicious activity |
| Analysis date: | February 07, 2025, 07:54:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 3689452832CE59DD704203C2C0A902B0 |
| SHA1: | F64103E87C97424345D16AF1683BDF3CA0BDAD97 |
| SHA256: | A7DB2A26E3C31CAF17853CBD2FADF143C255E9FE2E6ECCA1FBF17CEE24267AEB |
| SSDEEP: | 3:N8DSLOWcXt3TJr1hMLK5i8SEE+VrcDwRGgGKJIQcQfMKxtISxVSIEY2NuJ:2OLOWY3tjM+LEdD2GgUXitIS8NuJ |
MALICIOUS
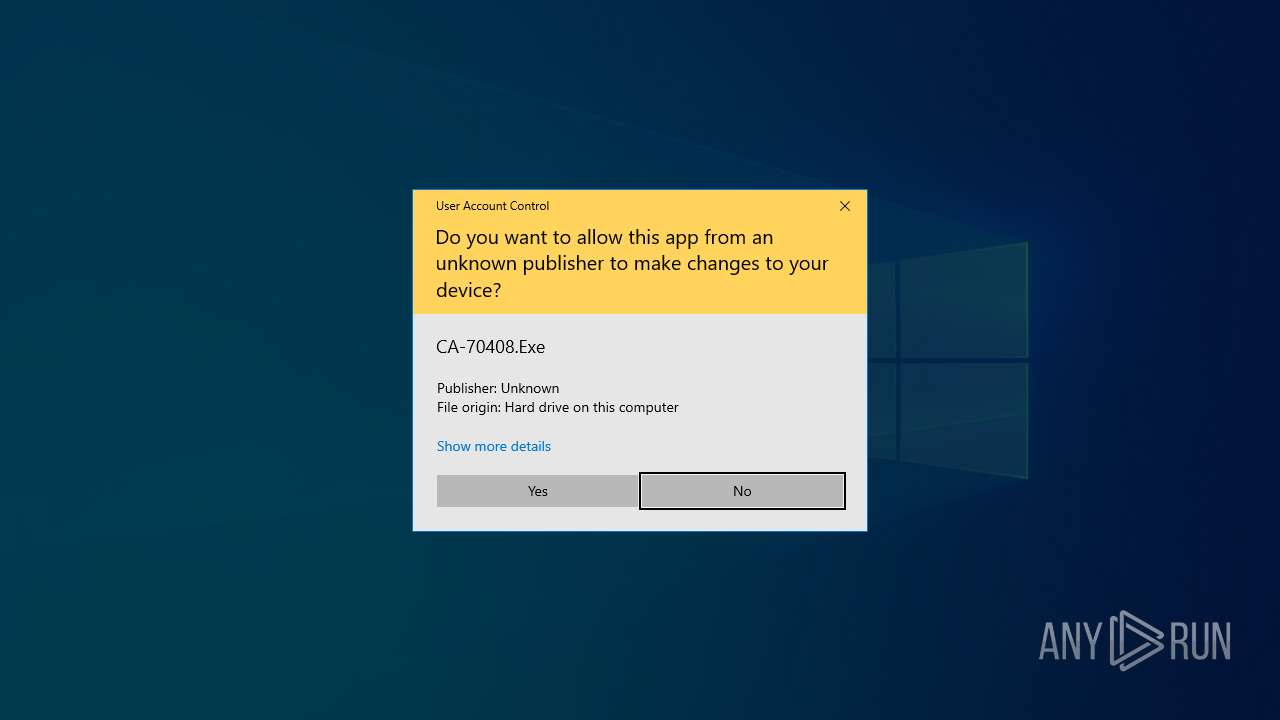
Executing a file with an untrusted certificate
- aslmpcsilent.exe (PID: 7608)
Registers / Runs the DLL via REGSVR32.EXE
- CA-70408.tmp (PID: 3540)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 8092)
- ca-UD.exe (PID: 4228)
- CA-70408.tmp (PID: 2148)
Executable content was dropped or overwritten
- CA-70408.Exe (PID: 2456)
- CA-70408.Exe (PID: 828)
- CA-70408.tmp (PID: 3540)
Reads the Windows owner or organization settings
- CA-70408.tmp (PID: 3540)
Process drops legitimate windows executable
- CA-70408.tmp (PID: 3540)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 7532)
- regsvr32.exe (PID: 7708)
- regsvr32.exe (PID: 7724)
- regsvr32.exe (PID: 4804)
- regsvr32.exe (PID: 7668)
Executes as Windows Service
- mflmwin.exe (PID: 7464)
INFO
Executable content was dropped or overwritten
- chrome.exe (PID: 7972)
- WinRAR.exe (PID: 8092)
- chrome.exe (PID: 2420)
Application launched itself
- chrome.exe (PID: 6496)
Reads Microsoft Office registry keys
- chrome.exe (PID: 6496)
Checks supported languages
- CA-70408.Exe (PID: 2456)
- CA-70408.tmp (PID: 2148)
- CA-70408.Exe (PID: 828)
- CA-70408.tmp (PID: 3540)
- aslmpcsilent.exe (PID: 7608)
- mflmwin.exe (PID: 7696)
- mflmwin.exe (PID: 7464)
- mflmma.exe (PID: 4516)
- ca-main.exe (PID: 3700)
- ca-start.exe (PID: 4576)
- ca-UD.exe (PID: 4228)
- CA-OBG.EXE (PID: 5628)
- mflmwin.exe (PID: 1572)
- mflmma.exe (PID: 1192)
- mflmma.exe (PID: 1328)
- mflmwin.exe (PID: 2548)
- mflmwin.exe (PID: 6372)
- mflmma.exe (PID: 4012)
- mflmma.exe (PID: 5392)
- mflmma.exe (PID: 7376)
Create files in a temporary directory
- CA-70408.tmp (PID: 3540)
- CA-70408.Exe (PID: 828)
- CA-70408.Exe (PID: 2456)
Reads the computer name
- CA-70408.tmp (PID: 3540)
- mflmwin.exe (PID: 7696)
- mflmwin.exe (PID: 7464)
- ca-main.exe (PID: 3700)
- ca-UD.exe (PID: 4228)
- CA-70408.tmp (PID: 2148)
- CA-OBG.EXE (PID: 5628)
- mflmwin.exe (PID: 1572)
- mflmwin.exe (PID: 2548)
- mflmwin.exe (PID: 6372)
The sample compiled with english language support
- CA-70408.tmp (PID: 3540)
- chrome.exe (PID: 2420)
Process checks computer location settings
- CA-70408.tmp (PID: 2148)
Detects InnoSetup installer (YARA)
- CA-70408.Exe (PID: 2456)
- CA-70408.tmp (PID: 2148)
- CA-70408.Exe (PID: 828)
- CA-70408.tmp (PID: 3540)
The sample compiled with Italian language support
- CA-70408.tmp (PID: 3540)
Compiled with Borland Delphi (YARA)
- CA-70408.tmp (PID: 3540)
- CA-70408.tmp (PID: 2148)
Creates a software uninstall entry
- CA-70408.tmp (PID: 3540)
Creates files in the program directory
- CA-70408.tmp (PID: 3540)
Manual execution by a user
- ca-start.exe (PID: 4576)
- mflmwin.exe (PID: 1572)
- mflmma.exe (PID: 1192)
- mflmma.exe (PID: 5392)
- mflmwin.exe (PID: 2548)
- mflmwin.exe (PID: 6372)
Checks proxy server information
- ca-UD.exe (PID: 4228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
188
Monitored processes
51
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 828 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8092.18848\CA-70408.Exe" /SPAWNWND=$70302 /NOTIFYWND=$50208 | C:\Users\admin\AppData\Local\Temp\Rar$EXa8092.18848\CA-70408.Exe | CA-70408.tmp | ||||||||||||
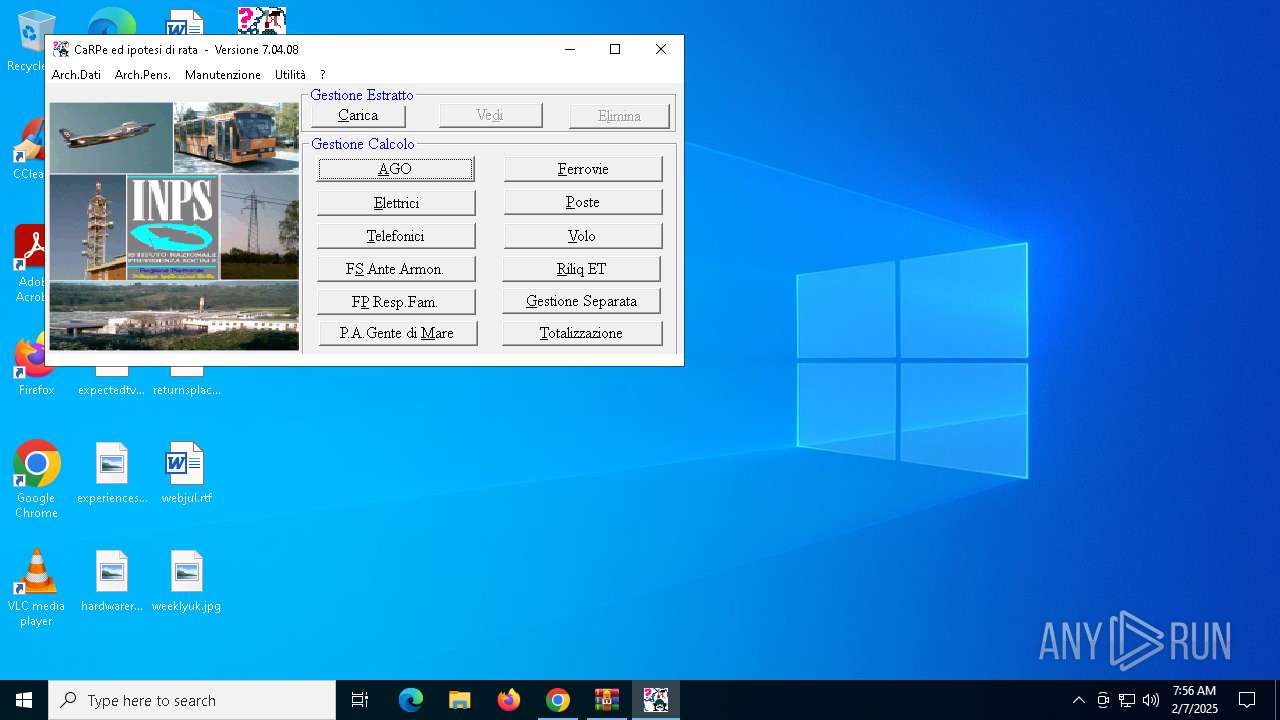
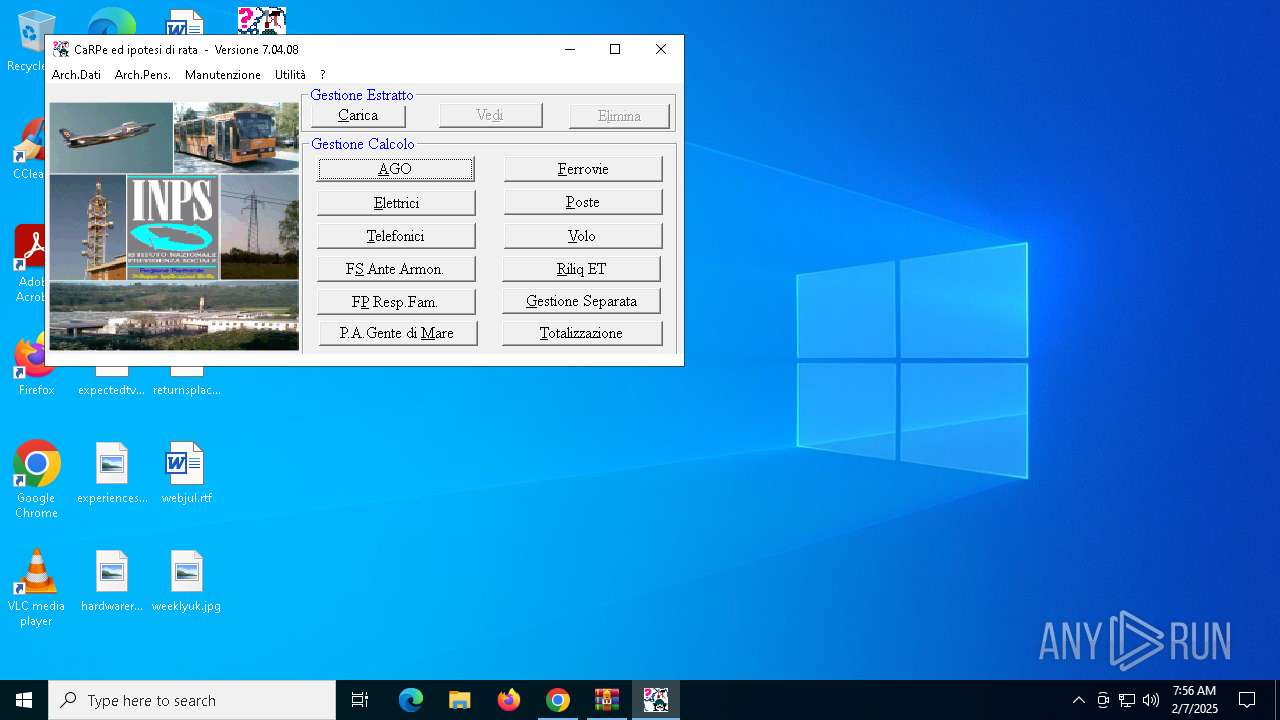
User: admin Company: INPS - D.C.S.I.T. Integrity Level: HIGH Description: CAlcolo Retribuzione PEnsionabile Vers: 7.04.08 Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 1192 | "C:\svabi\FILES\mflmma.exe" | C:\svabi\FILES\mflmma.exe | — | explorer.exe | |||||||||||
User: admin Company: Micro Focus Integrity Level: MEDIUM Description: Micro Focus License Manager Utility Exit code: 260 Version: 15.11 Modules
| |||||||||||||||
| 1328 | mflmma -z 72016 | C:\svabi\FILES\mflmma.exe | — | mflmwin.exe | |||||||||||
User: admin Company: Micro Focus Integrity Level: MEDIUM Description: Micro Focus License Manager Utility Exit code: 0 Version: 15.11 Modules
| |||||||||||||||
| 1572 | "C:\svabi\FILES\mflmwin.exe" | C:\svabi\FILES\mflmwin.exe | — | explorer.exe | |||||||||||
User: admin Company: Micro Focus Integrity Level: MEDIUM Description: Application License Manager. Exit code: 0 Version: NXASLMF51nyg Modules
| |||||||||||||||
| 1856 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --disable-gpu-sandbox --use-gl=disabled --gpu-vendor-id=5140 --gpu-device-id=140 --gpu-sub-system-id=0 --gpu-revision=0 --gpu-driver-version=10.0.19041.3636 --no-appcompat-clear --gpu-preferences=WAAAAAAAAADoABAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAABEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --mojo-platform-channel-handle=4628 --field-trial-handle=1920,i,13822976686849601208,15597360249174221315,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2084 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mflmma.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2148 | "C:\Users\admin\AppData\Local\Temp\is-T9UFI.tmp\CA-70408.tmp" /SL5="$50208,23519800,53760,C:\Users\admin\AppData\Local\Temp\Rar$EXa8092.18848\CA-70408.Exe" | C:\Users\admin\AppData\Local\Temp\is-T9UFI.tmp\CA-70408.tmp | — | CA-70408.Exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.52.0.0 Modules
| |||||||||||||||
| 2212 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5716 --field-trial-handle=1920,i,13822976686849601208,15597360249174221315,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2456 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa8092.18848\CA-70408.Exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa8092.18848\CA-70408.Exe | WinRAR.exe | ||||||||||||
User: admin Company: INPS - D.C.S.I.T. Integrity Level: MEDIUM Description: CAlcolo Retribuzione PEnsionabile Vers: 7.04.08 Setup Exit code: 0 Version: Modules
| |||||||||||||||
Total events
11 018
Read events
10 703
Write events
242
Delete events
73
Modification events
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (8008) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000003A3142833579DB01 | |||
| (PID) Process: | (6496) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (8092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (8092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (8092) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
278
Suspicious files
327
Text files
1 033
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF136fe4.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF136ff3.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF136ff3.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF136ff3.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF136ff3.TMP | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6496 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF136ff3.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
65
DNS requests
57
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8140 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8140 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6360 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
644 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
644 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
644 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
644 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
644 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/AMpg5-cnrANo_2018.8.8.0/2018.8.8.0_win64_win_third_party_module_list.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.204.136:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
3296 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1176 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6496 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6952 | chrome.exe | 151.101.3.10:443 | www.inps.it | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.inps.it |
| whitelisted |
accounts.google.com |
| whitelisted |
rum.hlx.page |
| unknown |
masterbotcdn.azureedge.net |
| whitelisted |
assets.adobedtm.com |
| whitelisted |
servizi2.inps.it |
| whitelisted |