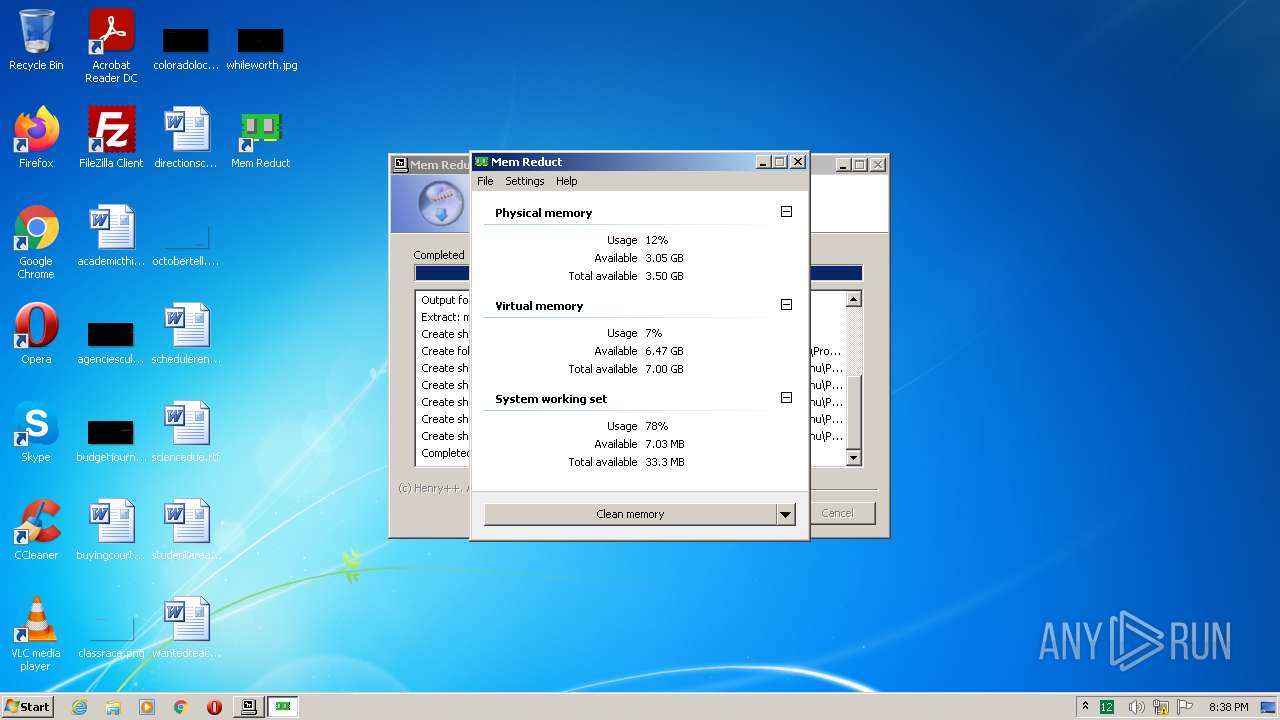
| File name: | memreduct-3.4-setup.exe |
| Full analysis: | https://app.any.run/tasks/a53c736f-b435-438f-8936-f949d2d521f4 |
| Verdict: | Malicious activity |
| Analysis date: | October 04, 2022, 19:38:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive |
| MD5: | 0F74E88D113F46798DC0F5D69C26DA2F |
| SHA1: | ACE6920CD953BCA45CB798672592AE7089D6D01D |
| SHA256: | A7BA8B9DA0A1FDF7A886FE86B2CA55B4AFE05D69B2C9C4D33B27D65986D6A033 |
| SSDEEP: | 6144:4Ya6eFisfjzl/eP3OD8Jb+Wh1btdxlrgTM5onRIR7YdH3zfbv7cxQ1/C8z:4YgzjJWPe0+ybt+TMGnqR7YFfH+QFpz |
MALICIOUS
Drops executable file immediately after starts
- memreduct-3.4-setup.exe (PID: 4012)
Loads the Task Scheduler COM API
- memreduct.exe (PID: 3372)
Loads dropped or rewritten executable
- memreduct-3.4-setup.exe (PID: 4012)
Application was dropped or rewritten from another process
- memreduct.exe (PID: 3372)
SUSPICIOUS
Reads the computer name
- memreduct-3.4-setup.exe (PID: 4012)
- memreduct.exe (PID: 3372)
Checks supported languages
- memreduct-3.4-setup.exe (PID: 4012)
- memreduct.exe (PID: 3372)
Creates a directory in Program Files
- memreduct-3.4-setup.exe (PID: 4012)
Creates a software uninstall entry
- memreduct-3.4-setup.exe (PID: 4012)
Creates files in the program directory
- memreduct-3.4-setup.exe (PID: 4012)
Executable content was dropped or overwritten
- memreduct-3.4-setup.exe (PID: 4012)
Creates files in the user directory
- memreduct-3.4-setup.exe (PID: 4012)
- memreduct.exe (PID: 3372)
Drops a file with a compile date too recent
- memreduct-3.4-setup.exe (PID: 4012)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 2021-Sep-25 21:56:47 |
| Detected languages: |
|
| Comments: | https://www.henrypp.org |
| CompanyName: | Henry++ |
| FileDescription: | Mem Reduct |
| FileVersion: | 3.4 |
| InternalName: | memreduct |
| LegalCopyright: | (c) Henry++. All rights reversed. |
| OriginalFilename: | memreduct-3.4-setup.exe |
| ProductName: | Mem Reduct |
| ProductVersion: | 3.4 |
DOS Header
| e_magic: | MZ |
|---|---|
| e_cblp: | 144 |
| e_cp: | 3 |
| e_crlc: | - |
| e_cparhdr: | 4 |
| e_minalloc: | - |
| e_maxalloc: | 65535 |
| e_ss: | - |
| e_sp: | 184 |
| e_csum: | - |
| e_ip: | - |
| e_cs: | - |
| e_ovno: | - |
| e_oemid: | - |
| e_oeminfo: | - |
| e_lfanew: | 216 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| NumberofSections: | 5 |
| TimeDateStamp: | 2021-Sep-25 21:56:47 |
| PointerToSymbolTable: | - |
| NumberOfSymbols: | - |
| SizeOfOptionalHeader: | 224 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 4096 | 26230 | 26624 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.41746 |
.rdata | 32768 | 5018 | 5120 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.14107 |
.data | 40960 | 131960 | 1536 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.11058 |
.ndata | 176128 | 180224 | 0 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | |
.rsrc | 356352 | 7448 | 7680 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.26855 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.50665 | 744 | UNKNOWN | English - United States | RT_ICON |
2 | 2.8505 | 296 | UNKNOWN | English - United States | RT_ICON |
103 | 2.56193 | 288 | UNKNOWN | English - United States | RT_DIALOG |
104 | 2.65946 | 280 | UNKNOWN | English - United States | RT_DIALOG |
105 | 2.67385 | 512 | UNKNOWN | English - United States | RT_DIALOG |
106 | 2.91148 | 248 | UNKNOWN | English - United States | RT_DIALOG |
109 | 2.70146 | 212 | UNKNOWN | English - United States | RT_DIALOG |
110 | 2.82633 | 1638 | UNKNOWN | English - United States | RT_BITMAP |
111 | 2.92767 | 238 | UNKNOWN | English - United States | RT_DIALOG |
103 (#2) | 1.97134 | 34 | UNKNOWN | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
COMCTL32.dll |
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
38
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3176 | "C:\Users\admin\AppData\Local\Temp\memreduct-3.4-setup.exe" | C:\Users\admin\AppData\Local\Temp\memreduct-3.4-setup.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Henry++ Integrity Level: MEDIUM Description: Mem Reduct Exit code: 3221226540 Version: 3.4 Modules
| |||||||||||||||
| 3372 | "C:\Program Files\Mem Reduct\memreduct.exe" | C:\Program Files\Mem Reduct\memreduct.exe | memreduct-3.4-setup.exe | ||||||||||||
User: admin Company: Henry++ Integrity Level: HIGH Description: Mem Reduct Exit code: 0 Version: 3.4 Modules
| |||||||||||||||
| 4012 | "C:\Users\admin\AppData\Local\Temp\memreduct-3.4-setup.exe" | C:\Users\admin\AppData\Local\Temp\memreduct-3.4-setup.exe | Explorer.EXE | ||||||||||||
User: admin Company: Henry++ Integrity Level: HIGH Description: Mem Reduct Exit code: 0 Version: 3.4 Modules
| |||||||||||||||
Total events
948
Read events
939
Write events
9
Delete events
0
Modification events
| (PID) Process: | (4012) memreduct-3.4-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | InstallLocation |
Value: "C:\Program Files\Mem Reduct" | |||
| (PID) Process: | (4012) memreduct-3.4-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Mem Reduct\uninstall.exe" | |||
| (PID) Process: | (4012) memreduct-3.4-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | DisplayName |
Value: Mem Reduct | |||
| (PID) Process: | (4012) memreduct-3.4-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | DisplayIcon |
Value: "C:\Program Files\Mem Reduct\memreduct.exe" | |||
| (PID) Process: | (4012) memreduct-3.4-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | DisplayVersion |
Value: 3.4 | |||
| (PID) Process: | (4012) memreduct-3.4-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | Publisher |
Value: Henry++ | |||
| (PID) Process: | (4012) memreduct-3.4-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | URLInfoAbout |
Value: https://www.henrypp.org | |||
| (PID) Process: | (4012) memreduct-3.4-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | NoModify |
Value: 1 | |||
| (PID) Process: | (4012) memreduct-3.4-setup.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\memreduct |
| Operation: | write | Name: | NoRepair |
Value: 1 | |||
Executable files
4
Suspicious files
1
Text files
7
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4012 | memreduct-3.4-setup.exe | C:\Users\admin\AppData\Local\Temp\nsrEB59.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 4012 | memreduct-3.4-setup.exe | C:\Program Files\Mem Reduct\History.txt | text | |
MD5:50B3303580B967B4E8532598A4A896DF | SHA256:4C90E2C59FCD6CB46F6477557FE976F4930CF43A1364CC4FE1746D0A38B8E79A | |||
| 4012 | memreduct-3.4-setup.exe | C:\Program Files\Mem Reduct\memreduct.exe | executable | |
MD5:3DCCD98AE5C8709938768D2B2EA95094 | SHA256:F1764DCC0040FDDC734D7B56A2C73A986653AC2CA01A8C01FAE3ACE98BA17904 | |||
| 4012 | memreduct-3.4-setup.exe | C:\Program Files\Mem Reduct\memreduct.exe.sig | binary | |
MD5:5C45201F84E943B07F301DEDC7286101 | SHA256:71CD86024CF52AF773D49B20EF9DB01DEB3B6620C303E8764668FDCFEAAF1194 | |||
| 4012 | memreduct-3.4-setup.exe | C:\Users\admin\AppData\Local\Temp\nsrEB59.tmp\nsDialogs.dll | executable | |
MD5:6C3F8C94D0727894D706940A8A980543 | SHA256:56B96ADD1978B1ABBA286F7F8982B0EFBE007D4A48B3DED6A4D408E01D753FE2 | |||
| 4012 | memreduct-3.4-setup.exe | C:\Program Files\Mem Reduct\License.txt | text | |
MD5:3C34AFDC3ADF82D2448F12715A255122 | SHA256:0B383D5A63DA644F628D99C33976EA6487ED89AAA59F0B3257992DEAC1171E6B | |||
| 4012 | memreduct-3.4-setup.exe | C:\Program Files\Mem Reduct\Readme.txt | text | |
MD5:1CA07C2BF88B53659DA4EFDFC3EDCE30 | SHA256:D3B3D572287FCED7EF401268A5B61A3FE03F49DB718487345D122DAFF4F66A4A | |||
| 4012 | memreduct-3.4-setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Mem Reduct\Mem Reduct.lnk | lnk | |
MD5:— | SHA256:— | |||
| 4012 | memreduct-3.4-setup.exe | C:\Users\admin\Desktop\Mem Reduct.lnk | lnk | |
MD5:— | SHA256:— | |||
| 4012 | memreduct-3.4-setup.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Mem Reduct\Readme.lnk | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3372 | memreduct.exe | 185.199.108.133:443 | raw.githubusercontent.com | FASTLY | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |