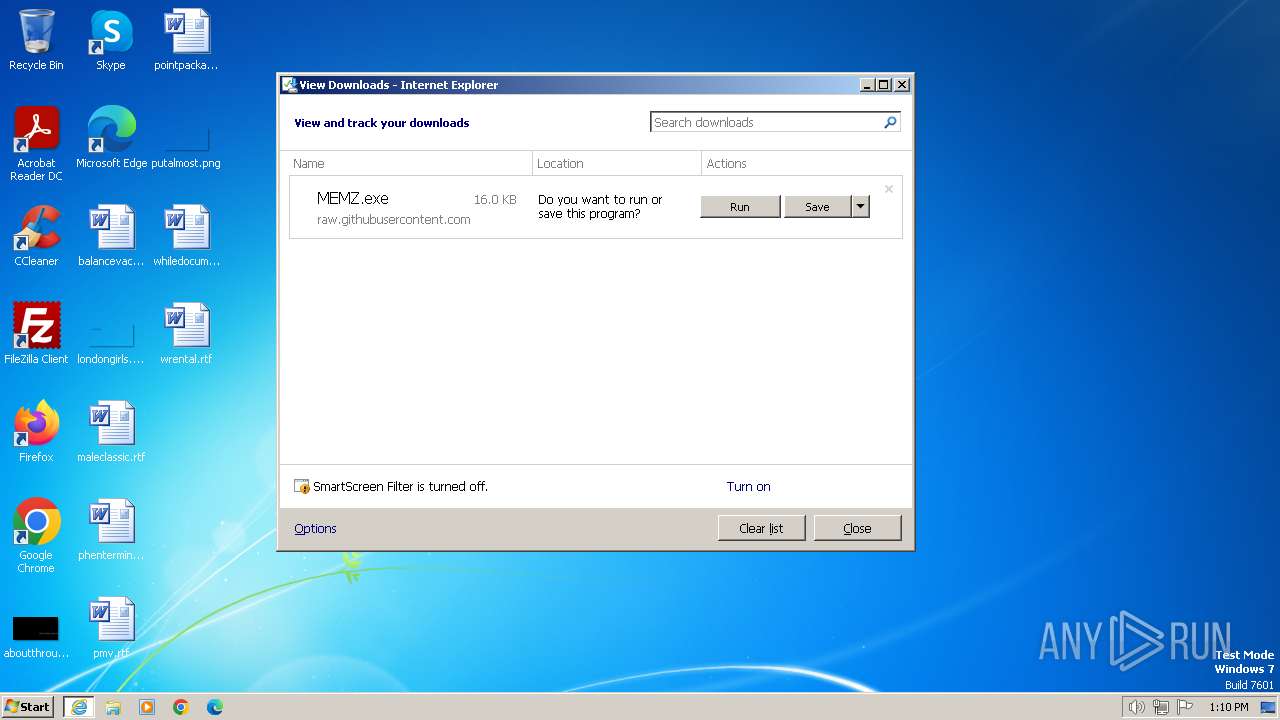
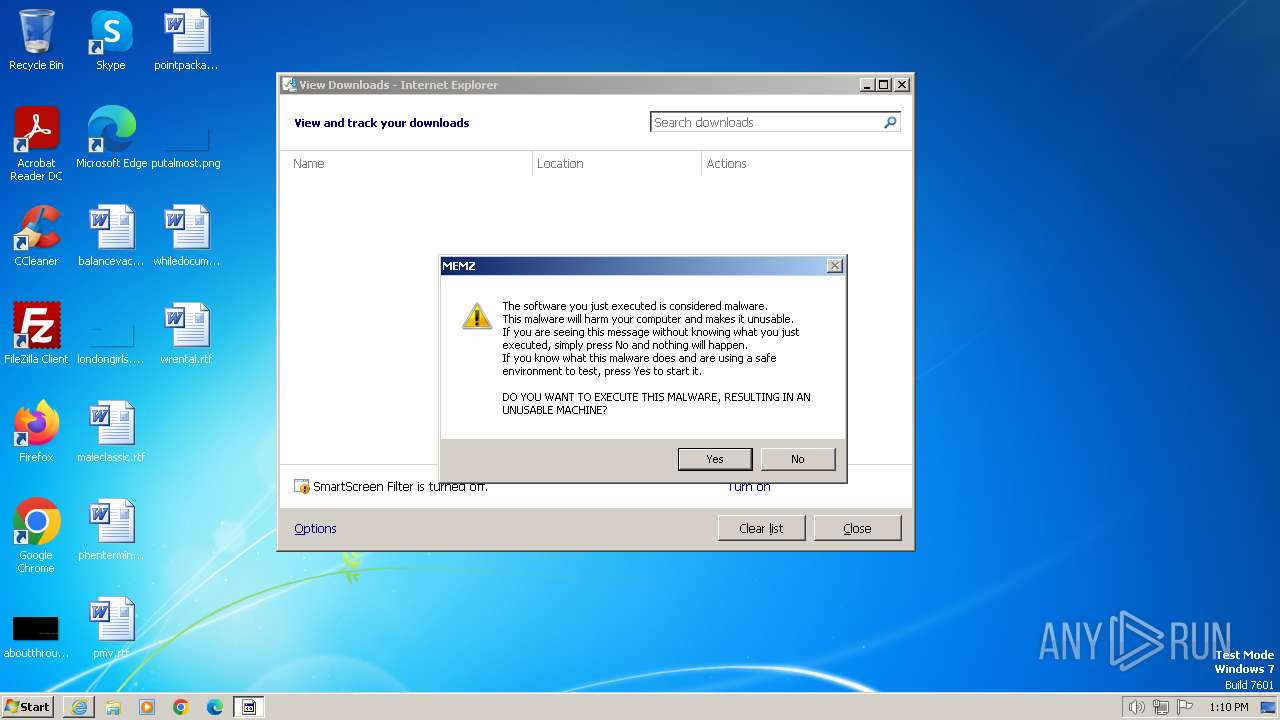
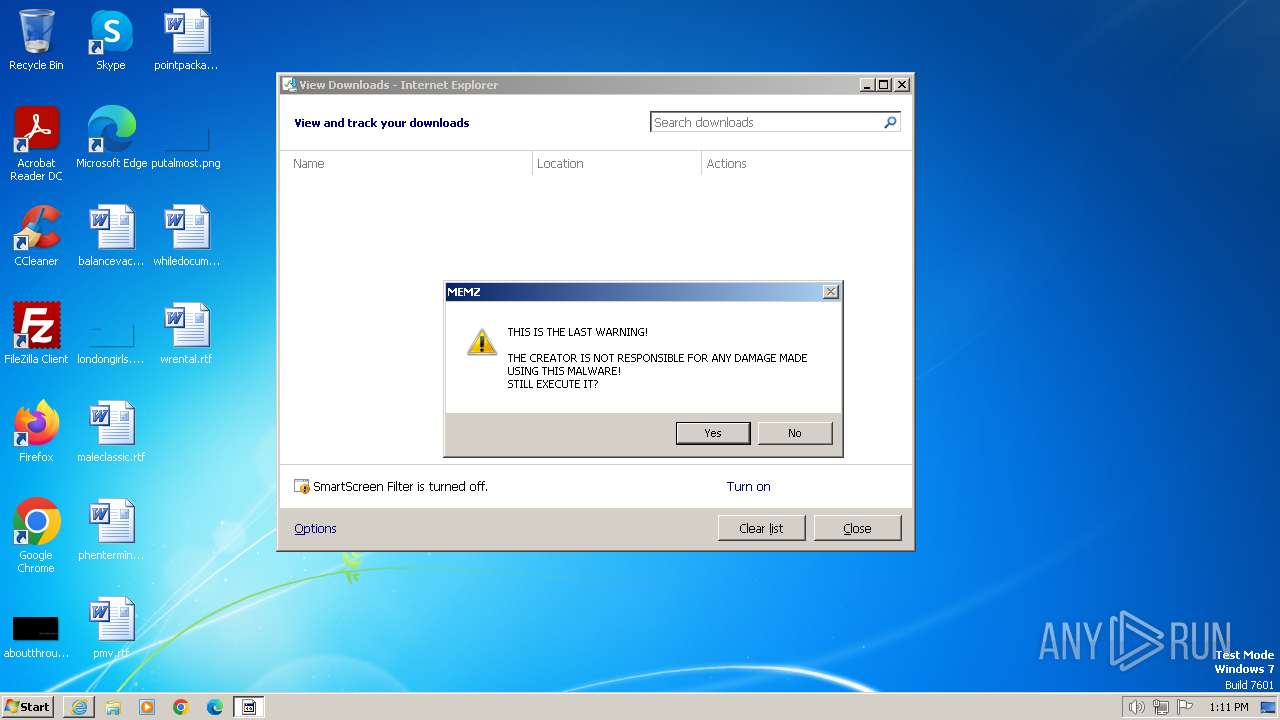
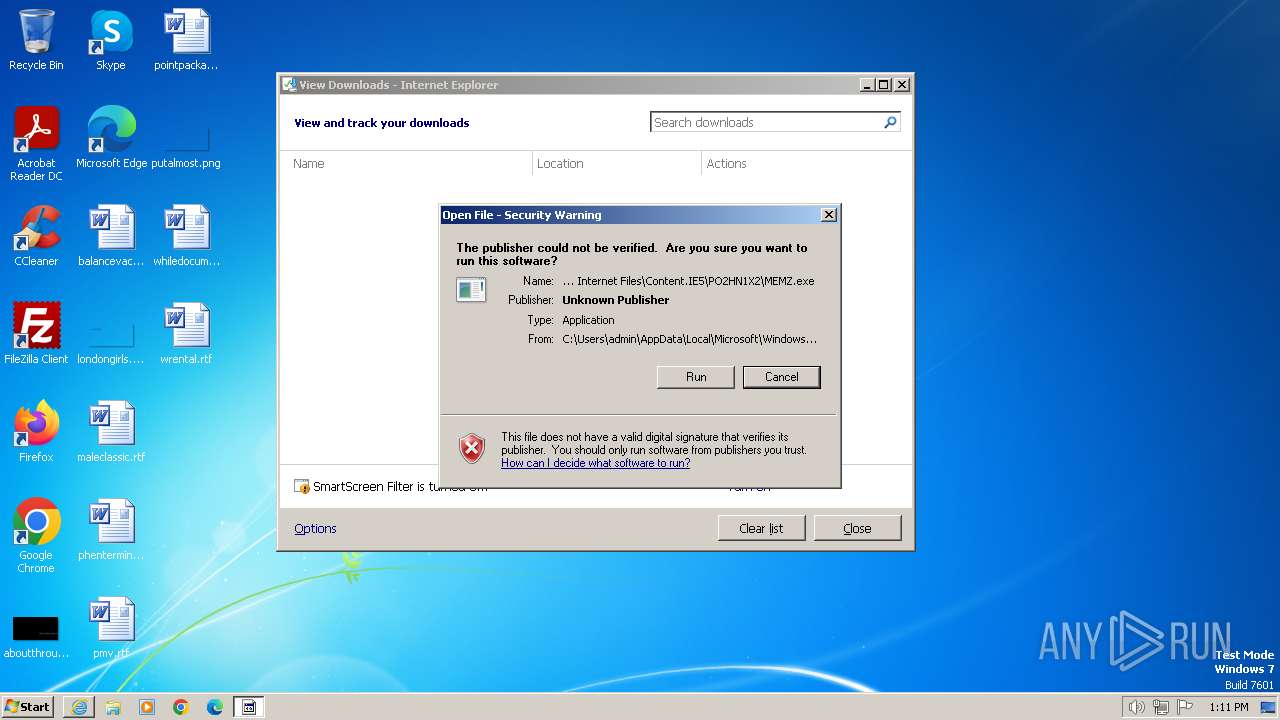
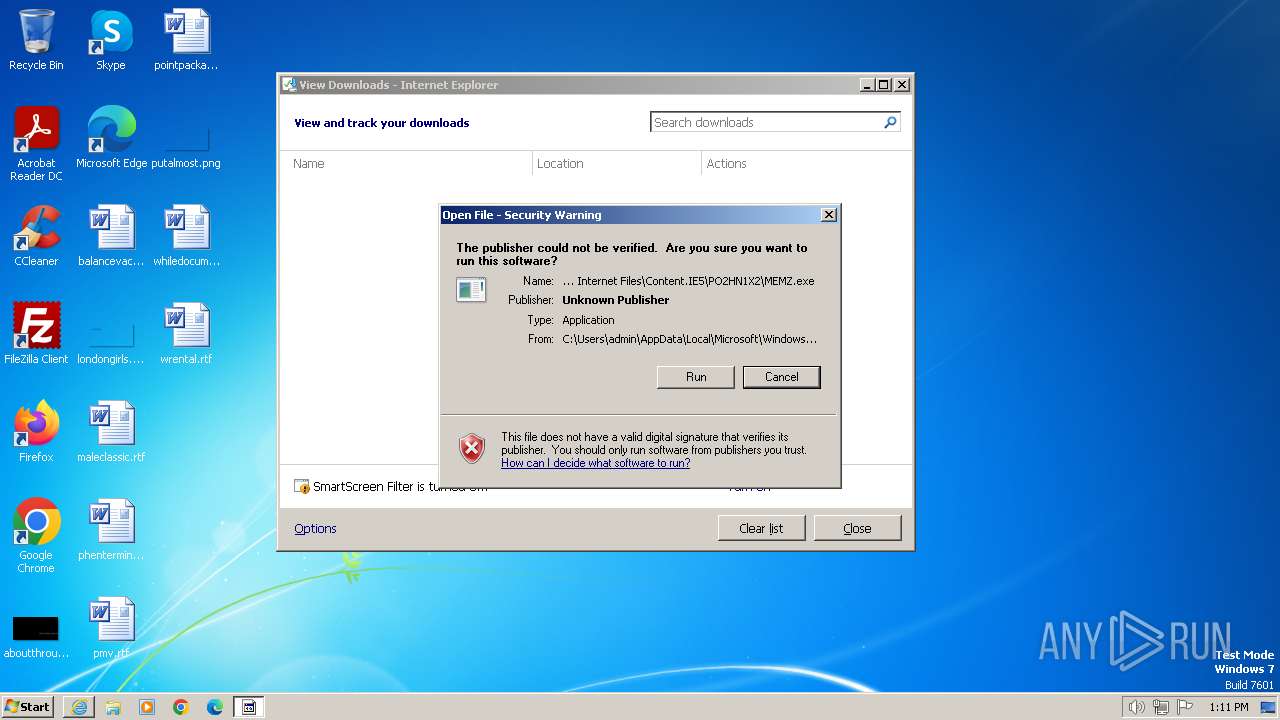
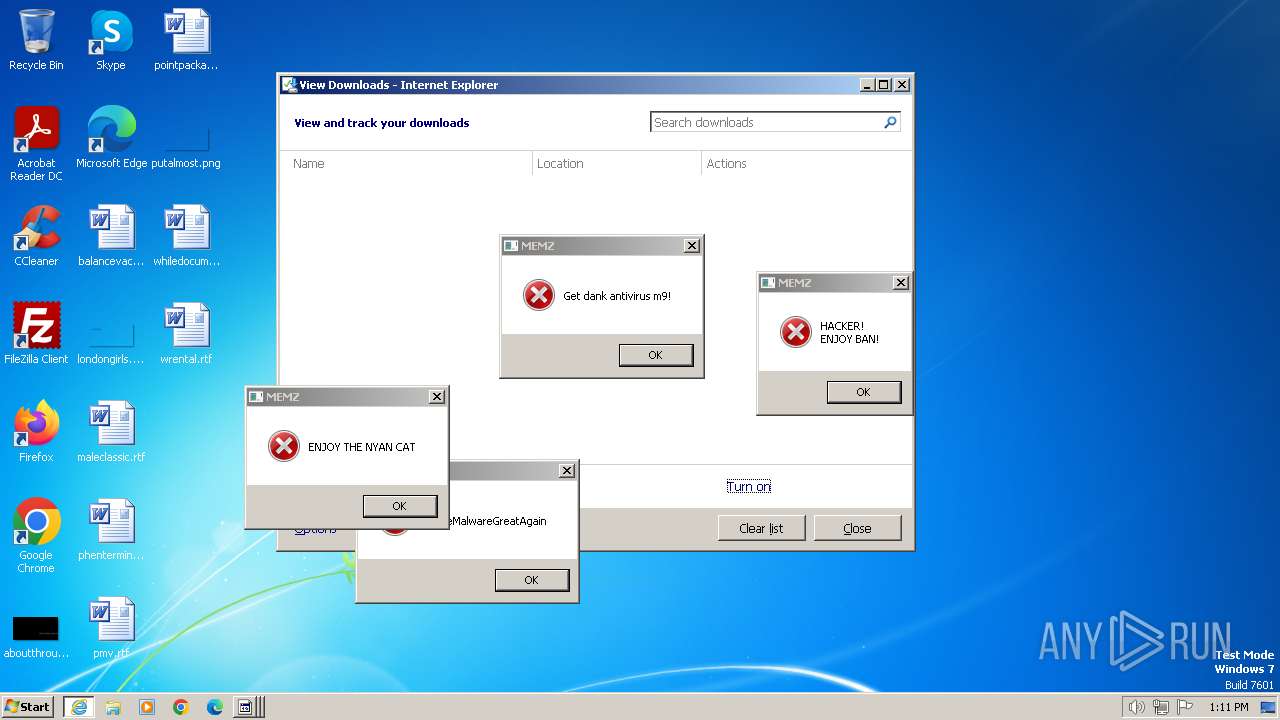
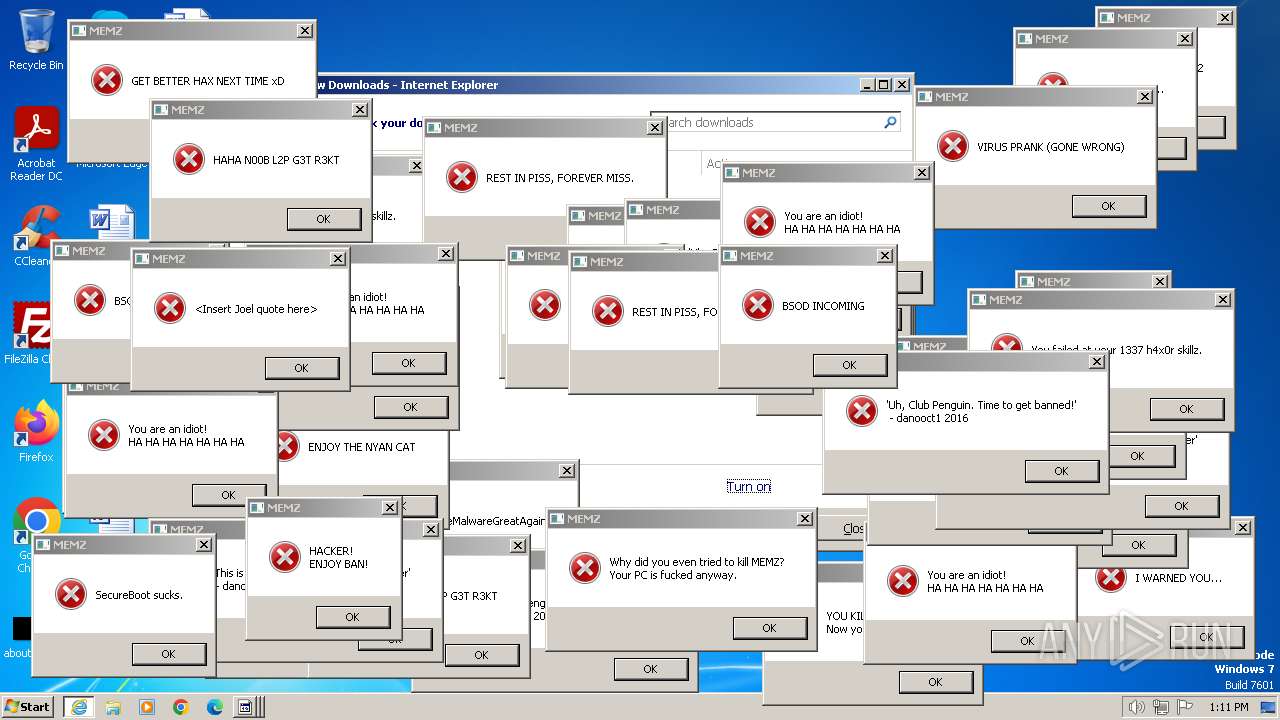
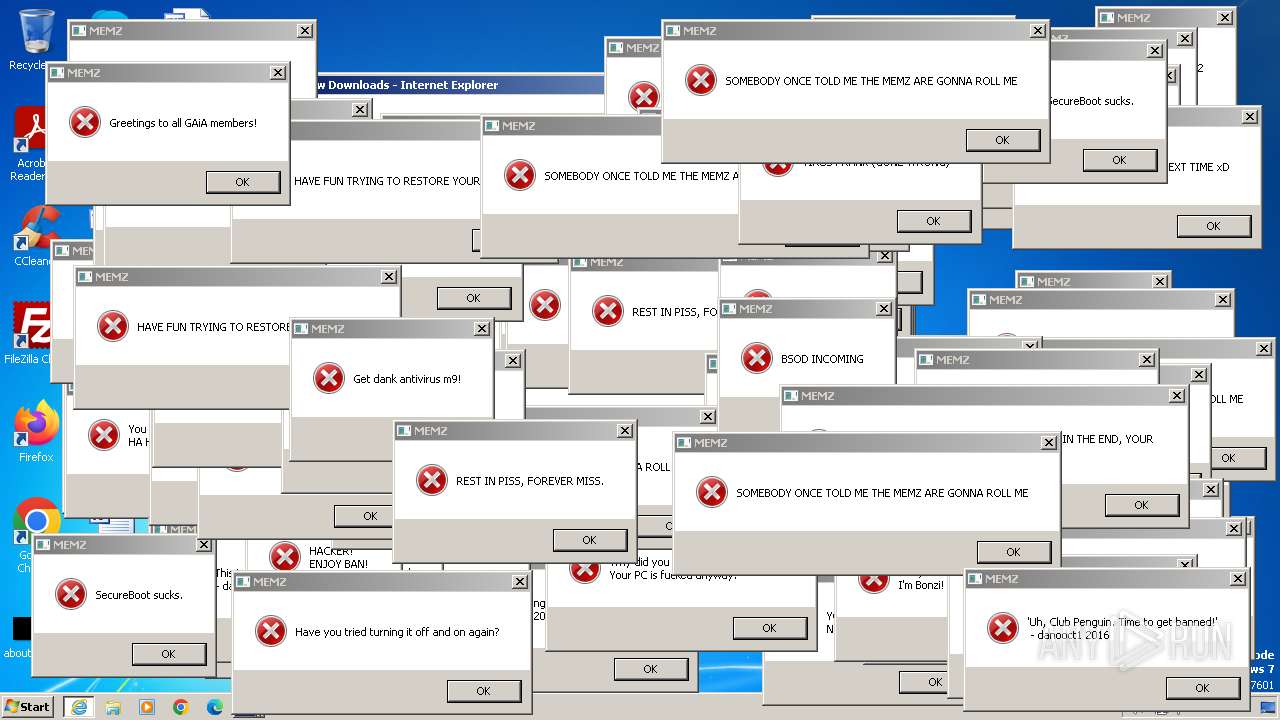
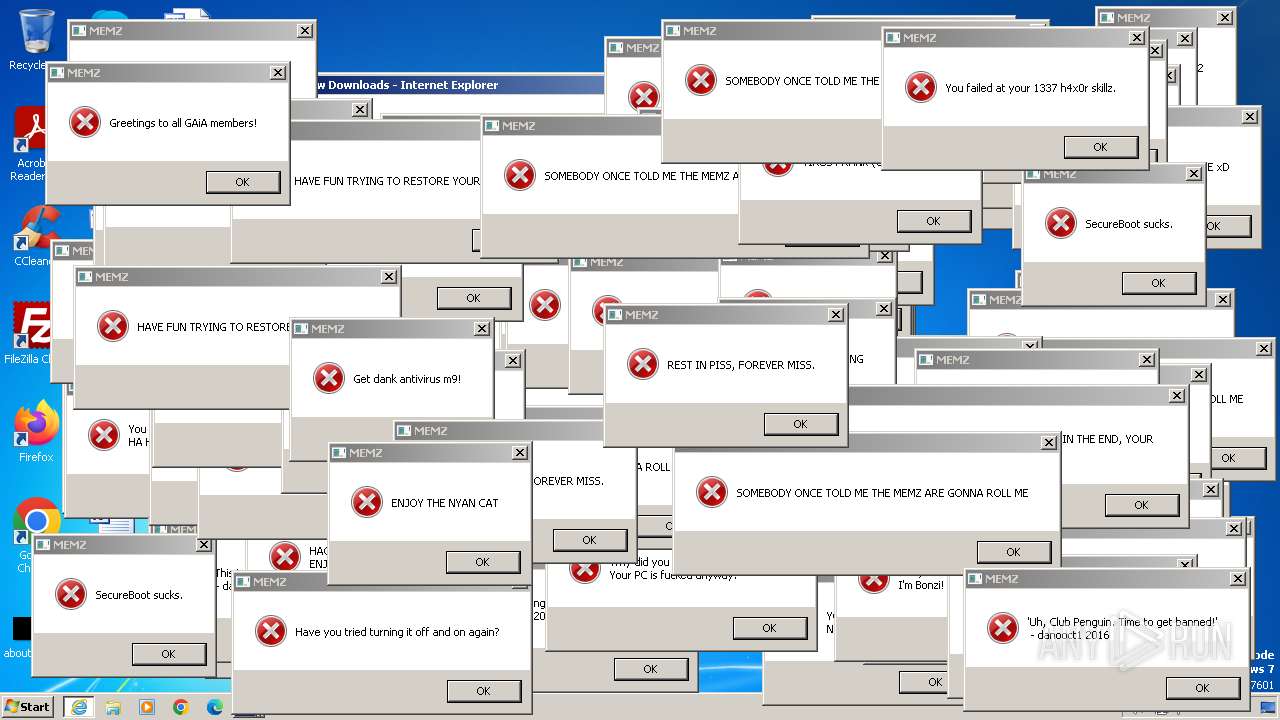
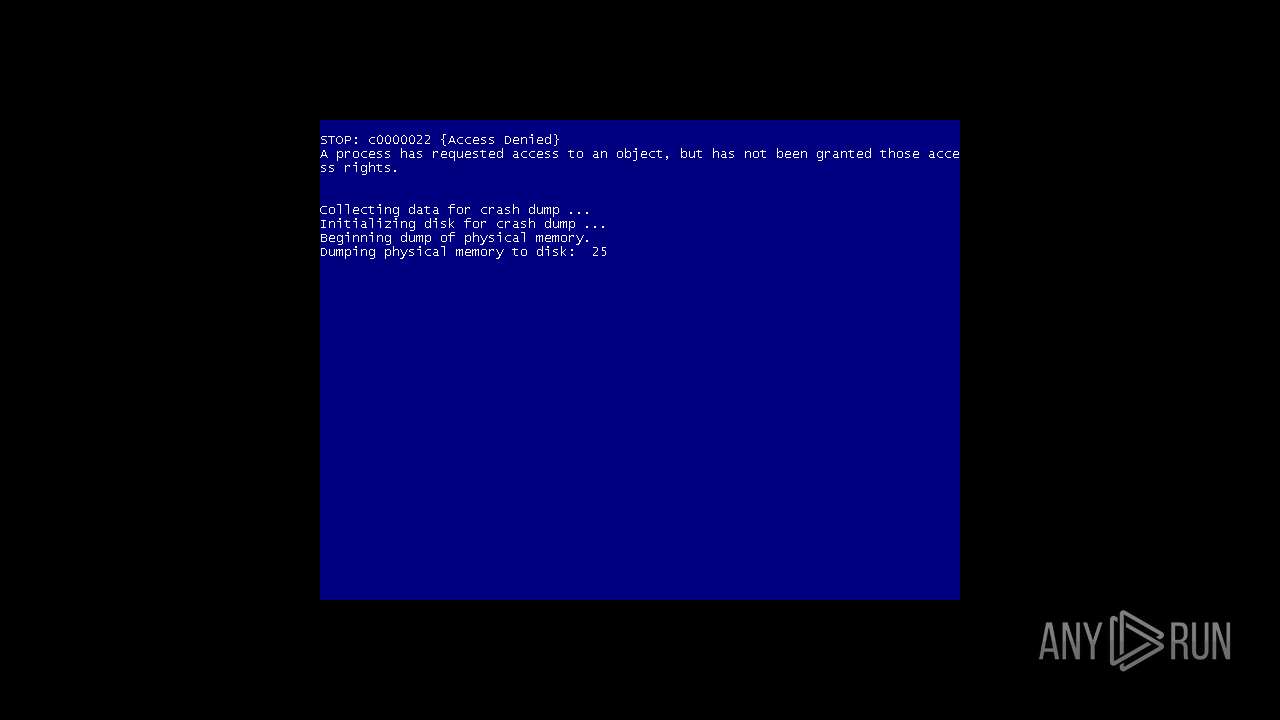
| URL: | https://github.com/Dfmaaa/MEMZ-virus/raw/main/MEMZ.exe |
| Full analysis: | https://app.any.run/tasks/c7ef5bbc-4656-4494-ae0a-dd1293cdc267 |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2024, 13:10:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B6C83A18D97679DA580AE39807946C8B |
| SHA1: | 6763E5509F6664630A635462E18B9878B2A6B01E |
| SHA256: | A790F36AC126A54EBA3579EF3CFE1335706E2EFD158E62CC5C1F0C96497CC987 |
| SSDEEP: | 3:N8tEd1YMzM/L4A:2uwVh |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- MEMZ.exe (PID: 1780)
Reads the Internet Settings
- MEMZ.exe (PID: 1780)
Application launched itself
- MEMZ.exe (PID: 1780)
Checks Windows Trust Settings
- MEMZ.exe (PID: 1780)
INFO
Application launched itself
- iexplore.exe (PID: 2044)
Checks supported languages
- MEMZ.exe (PID: 1780)
- MEMZ.exe (PID: 956)
- MEMZ.exe (PID: 1792)
- MEMZ.exe (PID: 1832)
- MEMZ.exe (PID: 696)
- MEMZ.exe (PID: 844)
- MEMZ.exe (PID: 1820)
The process uses the downloaded file
- MEMZ.exe (PID: 1780)
- iexplore.exe (PID: 2044)
Reads the machine GUID from the registry
- MEMZ.exe (PID: 1780)
- MEMZ.exe (PID: 696)
- MEMZ.exe (PID: 956)
- MEMZ.exe (PID: 1820)
- MEMZ.exe (PID: 1832)
Reads the computer name
- MEMZ.exe (PID: 1780)
Executable content was dropped or overwritten
- iexplore.exe (PID: 864)
- iexplore.exe (PID: 2044)
Drops the executable file immediately after the start
- iexplore.exe (PID: 2044)
- iexplore.exe (PID: 864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 696 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 844 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe" /main | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2 Modules
| |||||||||||||||
| 864 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2044 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 956 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1780 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe | — | iexplore.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1832 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/Dfmaaa/MEMZ-virus/raw/main/MEMZ.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
8 923
Read events
8 881
Write events
42
Delete events
0
Modification events
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2044) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
3
Suspicious files
10
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:C0D95B29B503BE5115F6EFDA8C23F155 | SHA256:65E7E39983ABF9F234555EDAD23B8BEE628C5DFB6DEEA447A293848417D78C12 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:C59825DBED6D7B1027D4DD30CF6DF858 | SHA256:AF8832DDEE1E6EBB8A0E69F19469005555DA74B95ACCF801616A28EA47F7EBAF | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:EA5DC901EA38D440F4095BB7EB7E76A7 | SHA256:8B6BD3870DC65DDF7F031C49B5EFA108190CBD9462561E7F5BFB403B60AFDF4B | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:7B3B5D5CECD77027D0B186DF4B13065E | SHA256:82BDF36721BE8DFEC6CB19437AF241DD316EAE6F9451F590E93BE7AEBCE9C750 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:C35E68EC4BDB4CC91094BCF1B56C7910 | SHA256:4C26706747AE92E6ADF086A1CE92F4197F785EBDAF7F7F3ECC02FFDCF1E030C2 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:B087213F427DD91A15368512E03FABBE | SHA256:544367FFD9F7997C489DC1944DB7E39D26D5A4B95964779BFA08E4C4584872C6 | |||
| 864 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:8D60CBCD5472A5D0D45550C0E8D2F308 | SHA256:0CA77FD2DE54338457CD212AFED4C00995E23A66EB50C1B9F66E68AF52A15173 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe.5fuvru2.partial:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2044 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\MEMZ.exe | executable | |
MD5:1D5AD9C8D3FEE874D0FEB8BFAC220A11 | SHA256:3872C12D31FC9825E8661AC01ECEE2572460677AFBC7093F920A8436A42E28FF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
11
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?608cb4ab6d3f68d3 | unknown | compressed | 4.66 Kb | unknown |
864 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f6bf34dbb61e71d7 | unknown | compressed | 4.66 Kb | unknown |
864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | unknown | binary | 471 b | unknown |
864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | unknown | binary | 312 b | unknown |
864 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
— | — | HEAD | 200 | 2.23.65.216:80 | http://query.prod.cms.rt.microsoft.com/cms/api/am/binary/RE2JgkA?v=133497979014210000 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
864 | iexplore.exe | 140.82.121.3:443 | github.com | GITHUB | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
864 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
864 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
864 | iexplore.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
query.prod.cms.rt.microsoft.com |
| whitelisted |