| File name: | Конференция_Семенов -13.05.pptx |
| Full analysis: | https://app.any.run/tasks/e1f76818-a48d-4e31-986a-a6f78c5072e9 |
| Verdict: | Malicious activity |
| Analysis date: | February 13, 2025, 03:35:26 |
| OS: | Windows 10 Professional (build: 19045, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.presentationml.presentation |
| File info: | Microsoft PowerPoint 2007+ |
| MD5: | A3CD7290B340CDF3565A76676E1F4D22 |
| SHA1: | 0127FE2BEC572E2B069E41FE2AC0DC5DF5AFE109 |
| SHA256: | A78FFE37A9232F1E282396D4D66610A5F321AC219855DD06DCBF97DF5CE2EB11 |
| SSDEEP: | 49152:i6kVgIVQTNNDBqyTwWPDbQsVER4lXNrc+KaTLIV8WAVsbi92mBl2Qb8qzLiDeVAT:PoVQTNtKN84m22sbi9LZiCdFq3FWIkKd |
MALICIOUS
Scans artifacts that could help determine the target
- MSPUB.EXE (PID: 1648)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
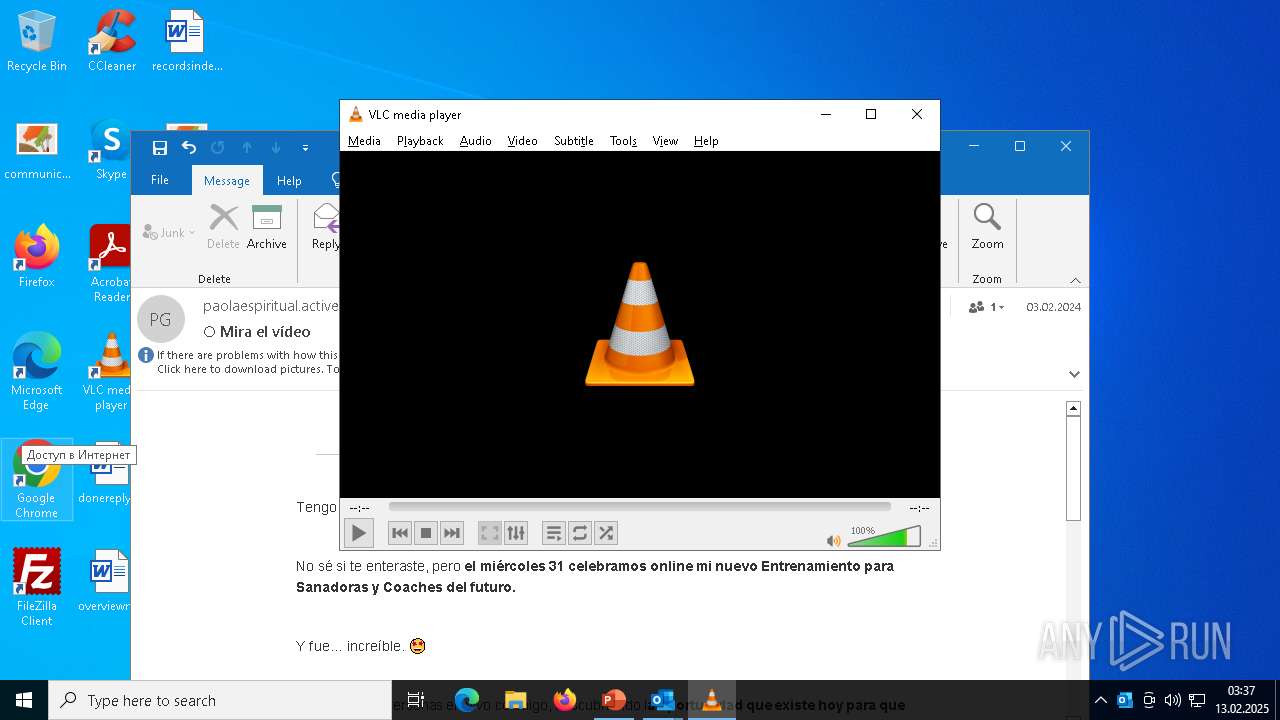
- vlc.exe (PID: 6028)
Reads security settings of Internet Explorer
- MSPUB.EXE (PID: 1648)
Reads the date of Windows installation
- MSPUB.EXE (PID: 1648)
Checks Windows Trust Settings
- MSPUB.EXE (PID: 1648)
Sets XML DOM element text (SCRIPT)
- splwow64.exe (PID: 1108)
INFO
Checks proxy server information
- slui.exe (PID: 4908)
- MSPUB.EXE (PID: 1648)
Reads the software policy settings
- slui.exe (PID: 4908)
- MSPUB.EXE (PID: 1648)
Manual execution by a user
- OUTLOOK.EXE (PID: 364)
- OUTLOOK.EXE (PID: 6048)
- vlc.exe (PID: 6028)
- EXCEL.EXE (PID: 2828)
- MSPUB.EXE (PID: 1648)
The process uses Lua
- vlc.exe (PID: 6028)
Checks supported languages
- vlc.exe (PID: 6028)
- MSPUB.EXE (PID: 1648)
Reads the computer name
- vlc.exe (PID: 6028)
- MSPUB.EXE (PID: 1648)
Create files in a temporary directory
- MSPUB.EXE (PID: 1648)
Reads Microsoft Office registry keys
- MSPUB.EXE (PID: 1648)
Reads Environment values
- MSPUB.EXE (PID: 1648)
Reads product name
- MSPUB.EXE (PID: 1648)
Reads the machine GUID from the registry
- MSPUB.EXE (PID: 1648)
Process checks computer location settings
- MSPUB.EXE (PID: 1648)
Creates files or folders in the user directory
- MSPUB.EXE (PID: 1648)
Reads CPU info
- MSPUB.EXE (PID: 1648)
Reads security settings of Internet Explorer
- splwow64.exe (PID: 1108)
- IMEWDBLD.EXE (PID: 3180)
- IMEWDBLD.EXE (PID: 4884)
- IMEWDBLD.EXE (PID: 824)
- IMEWDBLD.EXE (PID: 6116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .pptx | | | PowerPoint Microsoft Office Open XML Format document (72.3) |
|---|---|---|
| .xlsx | | | Excel Microsoft Office Open XML Format document (16.9) |
| .zip | | | Open Packaging Conventions container (8.7) |
| .zip | | | ZIP compressed archive (1.9) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x19148fff |
| ZipCompressedSize: | 571 |
| ZipUncompressedSize: | 5897 |
| ZipFileName: | [Content_Types].xml |
XML
| Template: | TM03457496[[fn=Параллакс]] |
|---|---|
| TotalEditTime: | 2.4 days |
| Words: | 1521 |
| Application: | Microsoft Office PowerPoint |
| PresentationFormat: | Экран (4:3) |
| Paragraphs: | 693 |
| Slides: | 17 |
| Notes: | - |
| HiddenSlides: | - |
| MMClips: | - |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: |
|
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
| LastModifiedBy: | Artur |
| RevisionNumber: | 236 |
| ModifyDate: | 2020:05:16 08:33:12Z |
XMP
| Title: | Слайд 1 |
|---|---|
| Creator: | User |
Total processes
111
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
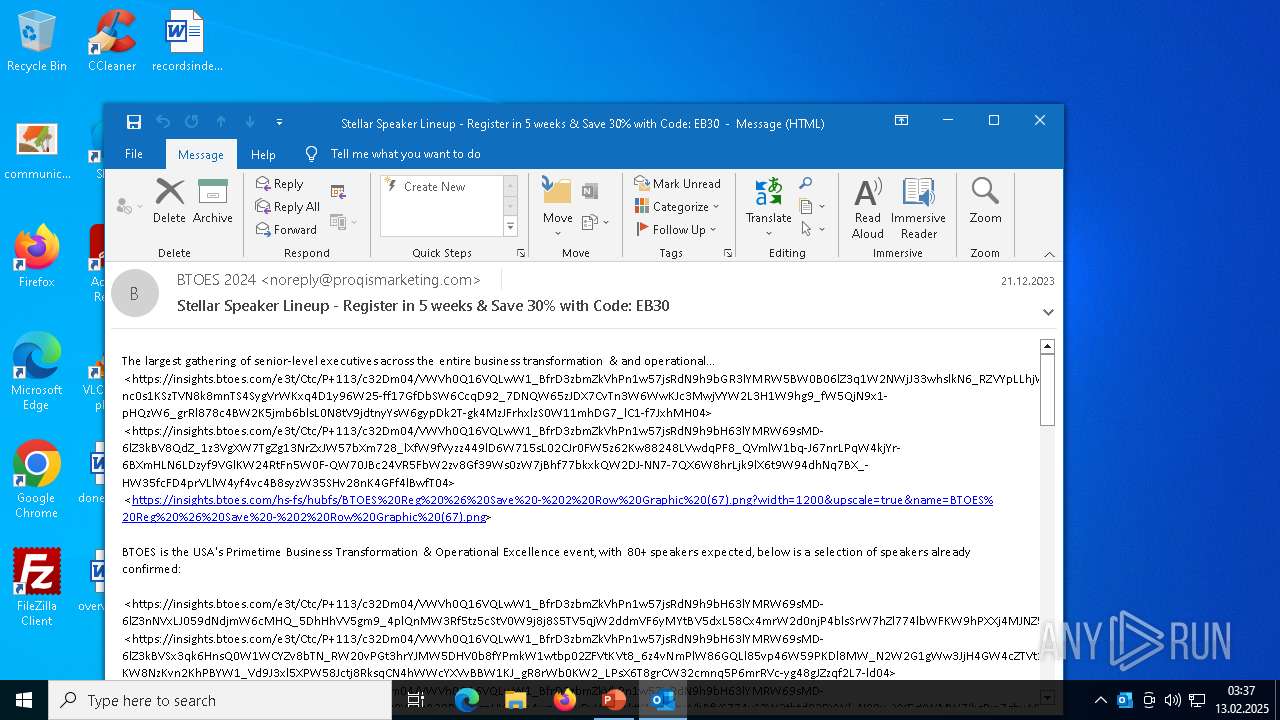
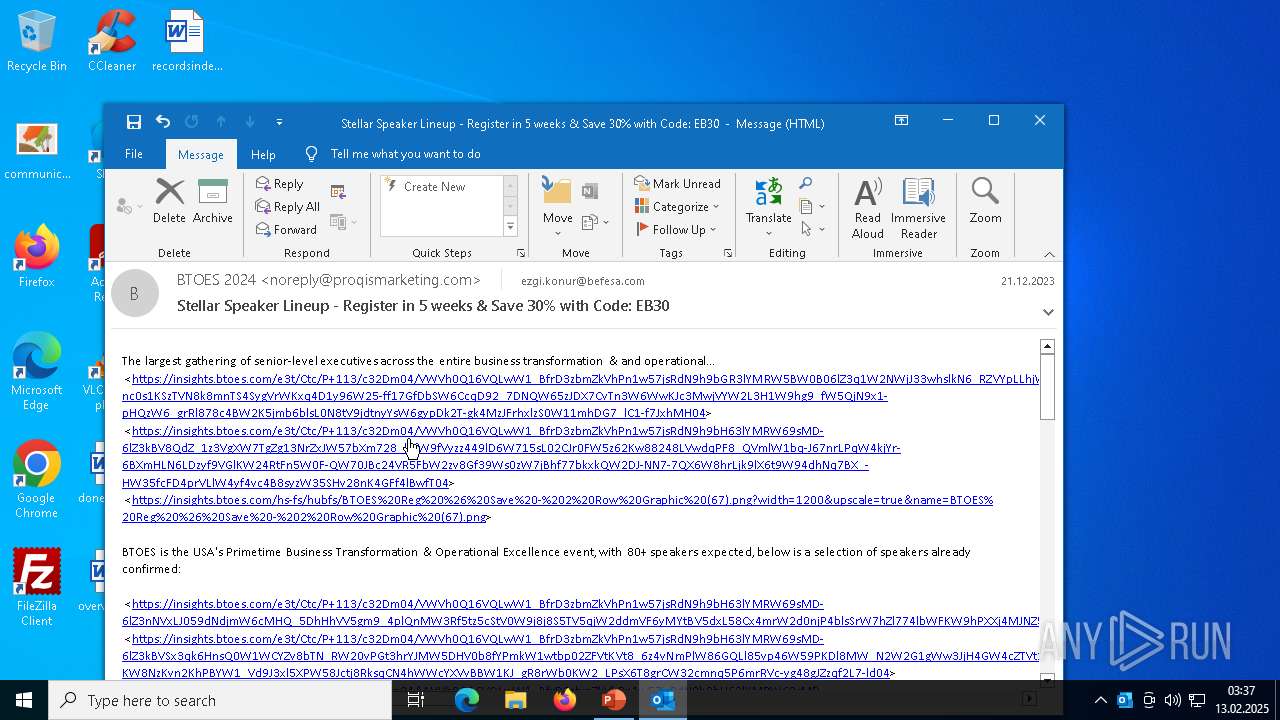
| 364 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\phish_alert_iocp_v1.10.10.eml" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 824 | "C:\WINDOWS\system32\IME\SHARED\IMEWDBLD.EXE" "C:\Users\admin\AppData\Local\Microsoft\Outlook\{6fdd5568-0ca1-4f55-bc11-4b54c6dc43cf}.dctx" -pluginguid "{505dbf31-895b-4b9a-b915-c133db8ffafc}" -encrypt | C:\Windows\System32\IME\SHARED\IMEWDBLD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft IME Open Extended Dictionary Module Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1108 | C:\WINDOWS\splwow64.exe 8192 | C:\Windows\splwow64.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Print driver host for applications Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1648 | "C:\Program Files\Microsoft Office\root\Office16\MSPUB.EXE" | C:\Program Files\Microsoft Office\root\Office16\MSPUB.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Publisher Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 2828 | "C:\Program Files\Microsoft Office\Root\Office16\EXCEL.EXE" "C:\Users\admin\Desktop\расчет раствора соли 2 ступени 1 Кр.Зв..xls" | C:\Program Files\Microsoft Office\root\Office16\EXCEL.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 3180 | "C:\WINDOWS\system32\IME\SHARED\IMEWDBLD.EXE" "C:\Users\admin\AppData\Local\Microsoft\Outlook\{32094977-9705-45f4-9e62-92693095538d}.dctx" -pluginguid "{505dbf31-895b-4b9a-b915-c133db8ffafc}" -encrypt | C:\Windows\System32\IME\SHARED\IMEWDBLD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft IME Open Extended Dictionary Module Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4884 | "C:\WINDOWS\system32\IME\SHARED\IMEWDBLD.EXE" "C:\Users\admin\AppData\Local\Microsoft\Outlook\{5f6e0df4-9cf1-4443-91a7-2517e31af0d3}.dctx" -pluginguid "{505dbf31-895b-4b9a-b915-c133db8ffafc}" -encrypt | C:\Windows\System32\IME\SHARED\IMEWDBLD.EXE | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft IME Open Extended Dictionary Module Exit code: 4294967295 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4908 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5588 | "C:\Program Files\Microsoft Office\Root\Office16\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\Конференция_Семенов -13.05.pptx" /ou "" | C:\Program Files\Microsoft Office\root\Office16\POWERPNT.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5648 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX86\Microsoft Shared\OFFICE16\ai.exe" "5D6177BF-A704-4FCB-895D-29CEF1CAC6F9" "3992ADB0-D7B7-49AB-986B-80C89EB62100" "364" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX86\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x86. Version: 0.12.2.0 Modules
| |||||||||||||||
Total events
30 113
Read events
28 411
Write events
1 459
Delete events
243
Modification events
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 3 |
Value: 01F802000000001000B24E9A3E01000000000000000900000000000000 | |||
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\POWERPNT\5588 |
| Operation: | write | Name: | 0 |
Value: 0B0E1022201B6FB6D49E4AB83D17DDF148E3162300468CE681C885B9DFED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783836C511D42BD2120C70006F0077006500720070006E0074002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources |
| Operation: | write | Name: | UISnapshotLanguages |
Value: de-de;en-us;es-es;fr-fr;it-it;ja-jp;ko-kr;pt-br;ru-ru;tr-tr | |||
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 1 | |||
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 1 | |||
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 1 | |||
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 1 | |||
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 1 | |||
| (PID) Process: | (5588) POWERPNT.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 1 | |||
Executable files
18
Suspicious files
180
Text files
49
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\61135B7A-CC7A-4C08-99E5-CD1E9A67931A | xml | |
MD5:0C868C567901D1C16325B0CA122979BB | SHA256:32F1B8B57C3CACAAB90E1B4117630DED5F2FC982F5FEBC52EC5E4E9DE742DA9D | |||
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\~DF2375E8238D5154DF.TMP | binary | |
MD5:FD13EE174F877F77723AED33C3D3F7FC | SHA256:009BE44DC345570E9FBEF14EE686D5BF27F1A0D38A0D9688B33DED45C7140F0F | |||
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:FE7BC656B60957511BC6A9C833271EB9 | SHA256:22D95C1CB4F6E098AE11160D0E81044DFFCDAE50A8FD494845F4275742D990F5 | |||
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\PowerPoint\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:03C1A95E2FA04A508039FDC2DC145972 | SHA256:A69D683773F0B11E670BDF25A5D809D43162D255827D99AACFE811AEBF450F5B | |||
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:CFDF182FE7C8C21C34A2E5DA813D8C92 | SHA256:A9C96440734FAF724BAACC548FA02F15CC0A9C4F6A179611BCA3C0B515FFDC33 | |||
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\~DF6D4BCAB7B4AD3F02.TMP | binary | |
MD5:C2575C8B97FA215A9DB0D82F0D4D82FF | SHA256:6E841F0AFD8B86766DC7D733ED0BB97A99E2F43B53E60CE0515DF1669C8B846B | |||
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:9C82FFABFD2EF961504756326B5EB436 | SHA256:BA90BD0182CBB435ABCB965ED15A7FF280FA586BE7E03AA488750809A24653C8 | |||
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\cab463E.tmp | compressed | |
MD5:7C645EC505982FE529D0E5035B378FFC | SHA256:298FD9DADF0ACEBB2AA058A09EEBFAE15E5D1C5A8982DEE6669C63FB6119A13D | |||
| 5588 | POWERPNT.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d00655d2aa12ff6d.customDestinations-ms | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
94
DNS requests
44
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2164 | svchost.exe | GET | 200 | 2.16.164.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5588 | POWERPNT.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4896 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2164 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4896 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5588 | POWERPNT.EXE | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_08-31-2010.crl | unknown | — | — | whitelisted |
5588 | POWERPNT.EXE | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | — | — | whitelisted |
1164 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2828 | EXCEL.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5588 | POWERPNT.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5588 | POWERPNT.EXE | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5588 | POWERPNT.EXE | 2.22.242.130:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
5588 | POWERPNT.EXE | 52.111.243.8:443 | messaging.lifecycle.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2164 | svchost.exe | 20.42.73.27:443 | v10.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2164 | svchost.exe | 2.16.164.120:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2164 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
5588 | POWERPNT.EXE | 52.182.143.211:443 | self.events.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5588 | POWERPNT.EXE | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4896 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
login.live.com |
| whitelisted |
v10.events.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=i686-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x86/contrib/i686-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc warning: cannot load module `C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_bd_plugin.dll' (The specified procedure could not be found. (error 127))
|
vlc.exe | main libvlc debug: recursively browsing `C:\Program Files\VideoLAN\VLC\plugins'
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc debug: loading plugins cache file C:\Program Files\VideoLAN\VLC\plugins\plugins.dat
|