| File name: | file01.ps1 |
| Full analysis: | https://app.any.run/tasks/fbc802c1-fd5a-4757-b136-bb4aea33fa87 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2025, 09:55:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 3B73958074A4698726BF441E11406DC8 |
| SHA1: | 7528440B0DF8F28EFAE3007453D47ADC1BAC63C0 |
| SHA256: | A7823ABC972CF3A3BA9C7697A00AEAA23A605AC59175967B1415A2C1455D81CA |
| SSDEEP: | 3072:CDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDY:CDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDE |
MALICIOUS
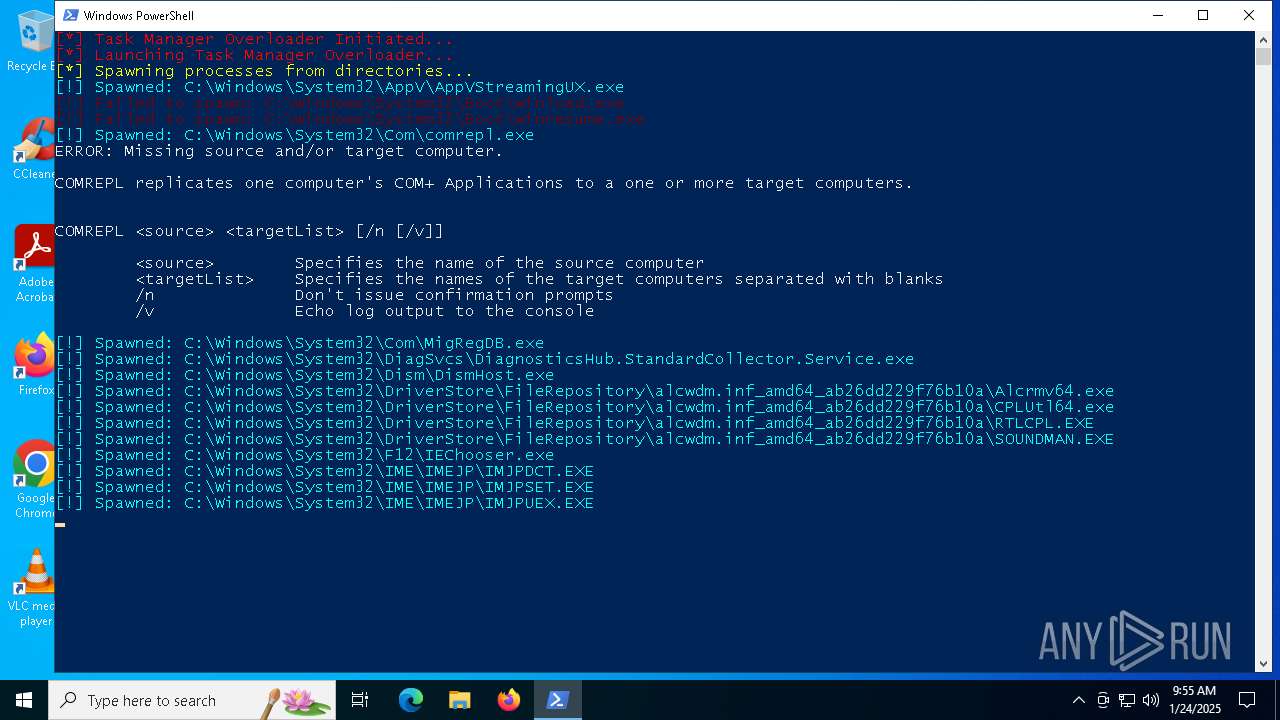
Bypass execution policy to execute commands
- powershell.exe (PID: 2600)
Execute application with conhost.exe as parent process
- cmd.exe (PID: 8412)
SUSPICIOUS
Reads Microsoft Outlook installation path
- IEChooser.exe (PID: 2356)
Reads Internet Explorer settings
- IEChooser.exe (PID: 2356)
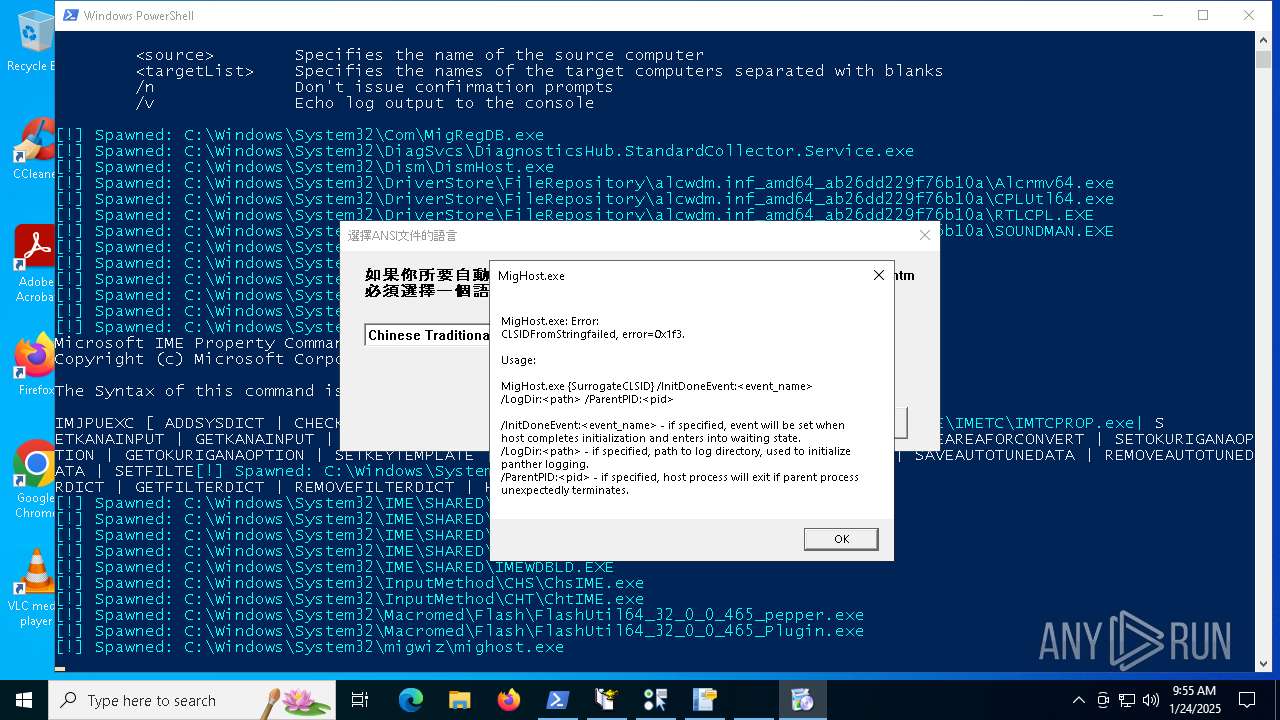
Executable content was dropped or overwritten
- RTLCPL.EXE (PID: 5780)
Uses WMIC.EXE
- powershell.exe (PID: 2600)
Application launched itself
- powershell.exe (PID: 2600)
- ClipUp.exe (PID: 8656)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 2600)
Uses ICACLS.EXE to modify access control lists
- powershell.exe (PID: 2600)
Uses ATTRIB.EXE to modify file attributes
- powershell.exe (PID: 2600)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2600)
- conhost.exe (PID: 8376)
- forfiles.exe (PID: 8860)
Uses DRIVERQUERY.EXE to obtain a list of installed device drivers
- powershell.exe (PID: 2600)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 9464)
- wmplayer.exe (PID: 10512)
Using 'findstr.exe' to search for text patterns in files and output
- powershell.exe (PID: 2600)
Searches and executes a command on selected files
- forfiles.exe (PID: 8860)
SQL CE related mutex has been found
- unregmp2.exe (PID: 11004)
Write to the desktop.ini file (may be used to cloak folders)
- FXSCOVER.exe (PID: 10388)
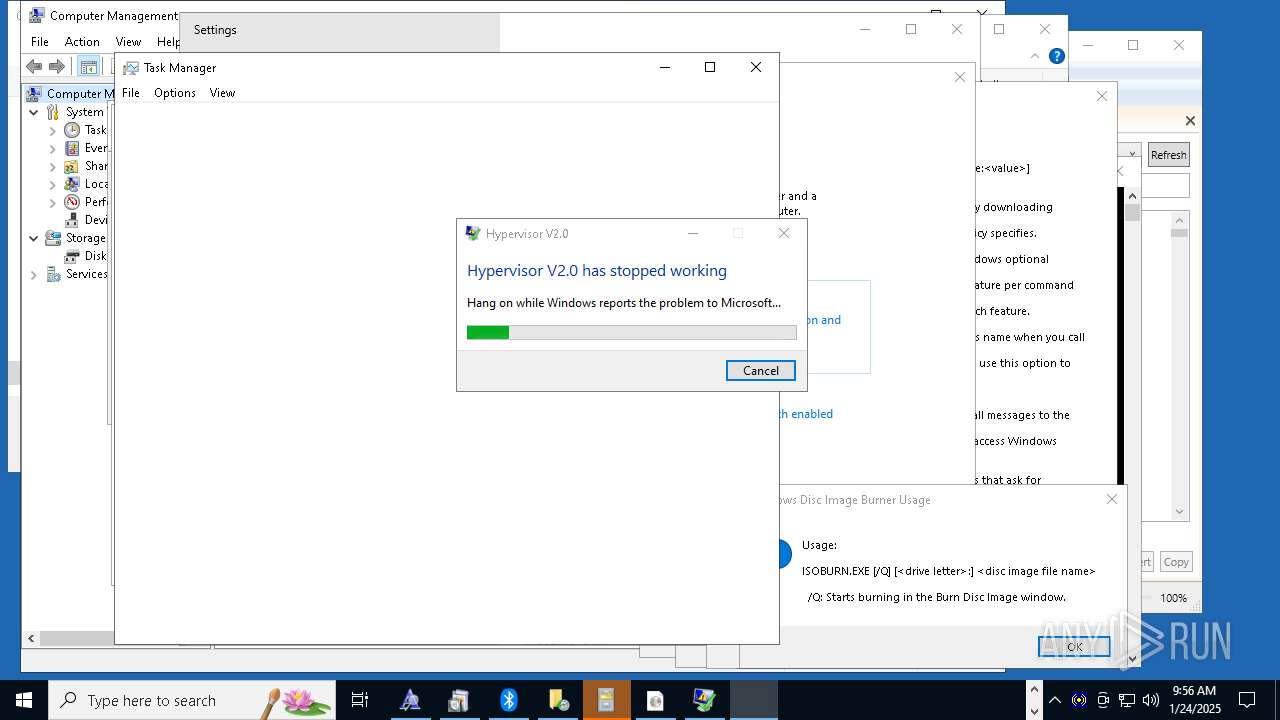
Executes application which crashes
- hvax64.exe (PID: 11280)
- hvix64.exe (PID: 11308)
Process uses IPCONFIG to get network configuration information
- powershell.exe (PID: 2600)
Sets XML DOM element text (SCRIPT)
- FXSCOVER.exe (PID: 10388)
INFO
Checks supported languages
- CPLUtl64.exe (PID: 3080)
- AppVStreamingUX.exe (PID: 836)
- SOUNDMAN.EXE (PID: 6116)
- Alcrmv64.exe (PID: 3876)
- RTLCPL.EXE (PID: 5780)
- FlashUtil64_32_0_0_465_pepper.exe (PID: 2324)
- ssh-add.exe (PID: 6296)
- ssh-agent.exe (PID: 6344)
- ssh-keyscan.exe (PID: 6416)
- ssh-keygen.exe (PID: 6388)
- RTBK.EXE (PID: 6848)
- FlashUtil64_32_0_0_465_Plugin.exe (PID: 5036)
- scp.exe (PID: 6244)
- agentactivationruntimestarter.exe (PID: 6384)
- AggregatorHost.exe (PID: 6432)
- appidtel.exe (PID: 7980)
- curl.exe (PID: 8116)
- DataStoreCacheDumpTool.exe (PID: 9244)
- deploymentcsphelper.exe (PID: 9404)
- drvinst.exe (PID: 1512)
- ShellExperienceHost.exe (PID: 9464)
- wmplayer.exe (PID: 10512)
- setup_wm.exe (PID: 10680)
- expand.exe (PID: 10512)
- CPLUtl64.exe (PID: 7240)
Reads the computer name
- AppVStreamingUX.exe (PID: 836)
- FlashUtil64_32_0_0_465_pepper.exe (PID: 2324)
- scp.exe (PID: 6244)
- FlashUtil64_32_0_0_465_Plugin.exe (PID: 5036)
- ssh-add.exe (PID: 6296)
- ssh-agent.exe (PID: 6344)
- ssh-keygen.exe (PID: 6388)
- ssh-keyscan.exe (PID: 6416)
- RTBK.EXE (PID: 6848)
- agentactivationruntimestarter.exe (PID: 6384)
- RTLCPL.EXE (PID: 5780)
- setup_wm.exe (PID: 10680)
- extrac32.exe (PID: 11028)
- SOUNDMAN.EXE (PID: 6116)
- wmplayer.exe (PID: 10512)
- identity_helper.exe (PID: 4220)
Reads the machine GUID from the registry
- AppVStreamingUX.exe (PID: 836)
- scp.exe (PID: 6244)
- ssh-add.exe (PID: 6296)
- ssh-keyscan.exe (PID: 6416)
- ssh-keygen.exe (PID: 6388)
Creates files or folders in the user directory
- IEChooser.exe (PID: 2356)
- DeviceCensus.exe (PID: 9452)
- unregmp2.exe (PID: 11004)
- powershell_ise.exe (PID: 4512)
Reads security settings of Internet Explorer
- SpeechRuntime.exe (PID: 6560)
- UNPUXHost.exe (PID: 6684)
- IEChooser.exe (PID: 2356)
- WMIC.exe (PID: 7068)
- AppHostRegistrationVerifier.exe (PID: 7732)
- calc.exe (PID: 8172)
- certreq.exe (PID: 7624)
- OpenWith.exe (PID: 7580)
- cleanmgr.exe (PID: 8472)
- CompMgmtLauncher.exe (PID: 9132)
- mmc.exe (PID: 3092)
- DpiScaling.exe (PID: 9988)
- explorer.exe (PID: 10148)
- powershell_ise.exe (PID: 4512)
- FileHistory.exe (PID: 10256)
- FXSCOVER.exe (PID: 10388)
- LaunchTM.exe (PID: 11984)
- Taskmgr.exe (PID: 10316)
The sample compiled with english language support
- RTLCPL.EXE (PID: 5780)
Reads the software policy settings
- SpeechRuntime.exe (PID: 6560)
- DeviceCensus.exe (PID: 9452)
- powershell_ise.exe (PID: 4512)
- WerFault.exe (PID: 11596)
Checks proxy server information
- SpeechRuntime.exe (PID: 6560)
- AppHostRegistrationVerifier.exe (PID: 7732)
- DeviceCensus.exe (PID: 9452)
- WerFault.exe (PID: 11596)
Application launched itself
- msedge.exe (PID: 7164)
Create files in a temporary directory
- RTLCPL.EXE (PID: 5780)
- ClipUp.exe (PID: 8732)
- ddodiag.exe (PID: 9380)
- powershell_ise.exe (PID: 4512)
- FXSSVC.exe (PID: 11244)
- licensingdiag.exe (PID: 12116)
Uses BITSADMIN.EXE
- powershell.exe (PID: 2600)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6156)
- powershell_ise.exe (PID: 4512)
Disables trace logs
- cmmon32.exe (PID: 8932)
- cmstp.exe (PID: 8964)
Execution of CURL command
- powershell.exe (PID: 2600)
Creates files in the program directory
- mmc.exe (PID: 3092)
Failed to create an executable file in Windows directory
- fixmapi.exe (PID: 10664)
Reads the time zone
- DeviceCensus.exe (PID: 9452)
Reads Environment values
- identity_helper.exe (PID: 4220)
Displays MAC addresses of computer network adapters
- getmac.exe (PID: 10592)
Checks transactions between databases Windows and Oracle
- lpksetup.exe (PID: 11760)
Process checks computer location settings
- wmplayer.exe (PID: 10512)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
552
Monitored processes
388
Malicious processes
1
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_xpay_wallet.mojom.EdgeXPayWalletService --lang=en-US --service-sandbox-type=utility --no-appcompat-clear --mojo-platform-channel-handle=6476 --field-trial-handle=2340,i,11207398439605925089,17270839120775077485,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 1073807364 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 748 | "C:\Windows\System32\Fondue.exe" | C:\Windows\System32\Fondue.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Features on Demand UX Exit code: 1073807364 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 776 | "C:\Windows\System32\IME\SHARED\ImeBroker.exe" | C:\Windows\System32\IME\SHARED\ImeBroker.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft IME Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 836 | "C:\Windows\System32\AppV\AppVStreamingUX.exe" | C:\Windows\System32\AppV\AppVStreamingUX.exe | — | powershell.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1020 | "C:\Windows\System32\attrib.exe" | C:\Windows\System32\attrib.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Windows\System32\HOSTNAME.EXE" | C:\Windows\System32\HOSTNAME.EXE | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Hostname APP Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1248 | "C:\Windows\System32\help.exe" | C:\Windows\System32\help.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Command Line Help Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | "C:\Windows\System32\InputMethod\CHT\ChtIME.exe" | C:\Windows\System32\InputMethod\CHT\ChtIME.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft IME Exit code: 4294967295 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1412 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7056 --field-trial-handle=2340,i,11207398439605925089,17270839120775077485,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=3556 --field-trial-handle=2340,i,11207398439605925089,17270839120775077485,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
73 902
Read events
73 276
Write events
609
Delete events
17
Modification events
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | IMEUserName |
Value: User-MSIME2000 | |||
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | Version |
Value: 9.0 | |||
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | option |
Value: /IT /Y | |||
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | option1 |
Value: 1376768 | |||
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | option2 |
Value: 0 | |||
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | option3 |
Value: 0 | |||
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | style |
Value: NATURAL | |||
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | keystyle |
Value: NATURAL | |||
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | romastyle |
Value: MS-IME | |||
| (PID) Process: | (3680) IMJPUEX.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\IME\15.0\IMEJP\MSIME |
| Operation: | write | Name: | colstyle |
Value: NATURAL | |||
Executable files
20
Suspicious files
122
Text files
81
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF139cd0.TMP | — | |
MD5:— | SHA256:— | |||
| 7164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF139cd0.TMP | — | |
MD5:— | SHA256:— | |||
| 7164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2600 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nmlj5crr.xto.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2600 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\590aee7bdd69b59b.customDestinations-ms~RF135fd6.TMP | binary | |
MD5:D040F64E9E7A2BB91ABCA5613424598E | SHA256:D04E0A6940609BD6F3B561B0F6027F5CA4E8C5CF0FB0D0874B380A0374A8D670 | |||
| 7164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State | binary | |
MD5:C103D37B4C52446A910A74BEA06373EB | SHA256:7F118FCEC7F9CCD270132068764D655E54D6BCE5FC6FC0FA681E9CA0DC5B79C8 | |||
| 7164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Variations | binary | |
MD5:1C42329800C95BC1DB27E7657711FF1E | SHA256:D58993216FB0CBF52CED6DA4FCAEBFC8FCC7C1A37191954397BA77951B16BE9B | |||
| 7164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\8328bbd4-b2f7-45e1-804d-34fd3d064fde.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 7164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Local State~RF139c91.TMP | binary | |
MD5:DFFC82B8D23613E62A20204028CEF32F | SHA256:114690F0417A9A6B079EA8D0534F095B04467809DCA929EB0983059E1C60FB6C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
92
DNS requests
82
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5848 | svchost.exe | GET | 200 | 2.16.164.99:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 304 | 40.127.240.158:443 | https://settings-win.data.microsoft.com/settings/v2.0/analog/NASP_SapiPolicy?os=Windows&deviceclass=Windows.Desktop&deviceid=s:BAD99146-31D3-4EC6-A1A4-BE76F32BA5D4&locale=en-US&osver=10.0.19041.1.amd64fre.vb_release.191206-1406&ring=Retail&sku=48 | unknown | — | — | unknown |
4712 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 301 | 13.107.246.45:443 | https://support.microsoft.com/help/4014916 | unknown | — | — | unknown |
— | — | GET | 401 | 13.107.6.158:443 | https://business.bing.com/api/v1/user/token/microsoftgraph?&clienttype=edge-omnibox | unknown | — | — | unknown |
— | — | GET | 301 | 13.107.246.45:443 | https://support.microsoft.com/en-US/windows/9d92e194-36aa-ae41-18f6-fef5459ad86d | unknown | — | — | unknown |
— | — | GET | — | 92.123.104.31:443 | https://www.bing.com/bloomfilterfiles/ExpandedDomainsFilterGlobal.json | unknown | — | — | unknown |
— | — | GET | — | 13.107.246.45:443 | https://support.microsoft.com/css/Article/css.css?v=Z6ZkkY_X8iTM42LbcHhEDNaT4e9rMO_zPAbxEsFxAvo | unknown | — | — | unknown |
— | — | GET | — | 13.107.246.45:443 | https://support.microsoft.com/css/Article/article.css?v=CwQq6rdVP0SuA__MN15KxKwzDxjvYzpStxB7_g36a8k | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5848 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.99:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5848 | svchost.exe | 2.16.164.99:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
5848 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6700 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
6700 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
6700 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
6700 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
6700 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
6700 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |
Process | Message |
|---|---|
imjpuexc.exe | main: Need command.
|
imjpuexc.exe | ERROR_LEVEL = 128
|
mmc.exe | ViewerExternalLogsPath = 'C:\ProgramData\Microsoft\Event Viewer\ExternalLogs': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerAdminViewsPath = 'C:\ProgramData\Microsoft\Event Viewer\Views\ApplicationViewsRootNode': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerViewsFolderPath = 'C:\ProgramData\Microsoft\Event Viewer\Views': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | ViewerConfigPath = 'C:\ProgramData\Microsoft\Event Viewer': Microsoft.Windows.ManagementUI.CombinedControls.EventsNode
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerExtension
|
esentutl.exe | Invalid parameter passed to C runtime function.
|